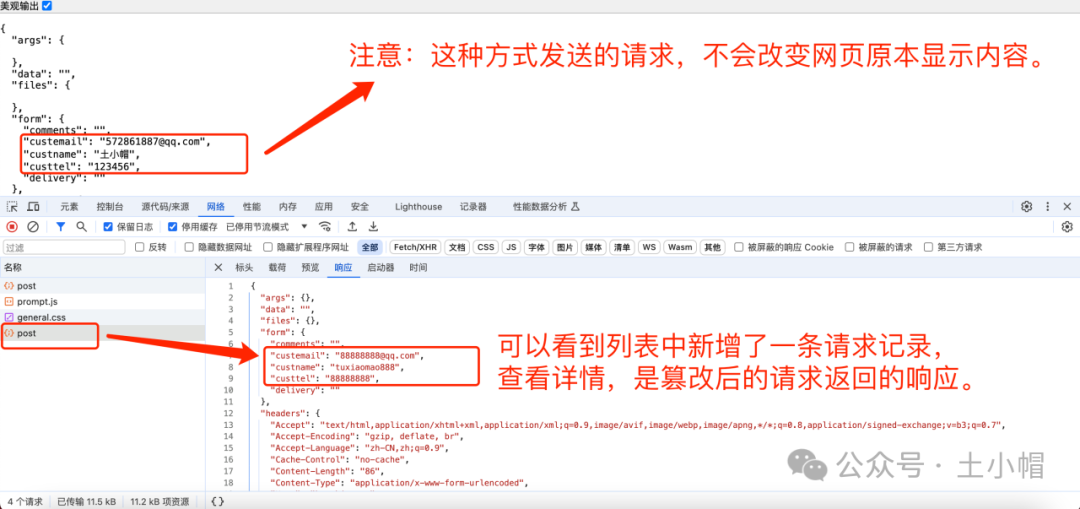
本文主要是介绍Dragonfly Network Diagram Analysis,希望对大家解决编程问题提供一定的参考价值,需要的开发者们随着小编来一起学习吧!
Page 1 of 2 Assignment 03--Dragonfly Network Diagram Analysis
ENGINEERING 2125, Spring 2024
Engineering Management & Decision Making
Written Assignment Guidelines
“Dragonfly Network Diagram”
NOTE: Please submit general questions about this assignment to the Ed Discussion area on Canvas.
That will allow other students to see answers that we provide.
GENERAL INSTRUCTIONS
Access and read the Dragonfly case from the HBS coursepack.
Submit a .pdf report in which you respond to the writing prompts and the analysis prompts.
IMPORTANT NOTE: Use the duration and cost tables provided in this assignment, rather than those
provided in the case.
WRITING PROMPTS
The Dragonfly case follows an unmanned aerial vehicle (UAV) project. For each of the prompts, provide a
brief answer (2–3 sentences).
Writing Prompt 1: When the project being described in the case is completed, does it result in (a) a
new UAV design and prototype, or (b) a plan for a project to create a new UAV design and prototype?
Cite evidence from the case that supports your conclusion.
Writing Prompt 2: Would you say that Table 1 in the case represents an RBS or a WBS? Why?
Writing Prompt 3: With data in Table 1 and Table 4, compute the projected cost per day for each of the
activities. Which activity has the highest cost per day? Why do you think this task is particularly expensive
per day? (On the basis of the limited information provided, this may be somewhat of a guess!)
Writing Prompt 4: What information in the case suggests that this firm, IACo, is well positioned to carry
out this project?
Writing Prompt 5: What information in the case suggests that this firm is perhaps not especially
experienced in performing a project like this?
ANALYSIS PROMPTS
1) For the proposed project, draw a network diagram of the sort shown in Figure 7.15 of the Wysocki
textbook. Base your diagram on the “activities” shown in Table 1 and the “design structure matrix”
shown in Table 2 of the case. (See the “hint” below on how to interpret Table 2.)
Ignore the dependency shown between activity A9 and A4 that is shown in Table 2.
To draw the network diagram, you can use any method: hand sketch, graphics software, presentation
software, project software, etc.
2) Using the substitute duration data provided below for the “Expected Durations (days)” in Table 1,
calculate the total number of days required to complete the project. Provide the “task path”
through the network diagram that sets the total project duration (the “critical path”).
Page 2 of 2 Assignment 03--Dragonfly Network Diagram & Analysis (2024).docx
3) Using the substitute duration data provided below for the “Best case time estimates per activity” in
Table 3, calculate the best case total numbers of days to finish the project. Provide the “task
path” through the network diagram that sets the total project duration.
4) Using the substitute duration data provided below for the “Worst case time estimates per activity” in
Table 3, calculate the worst case total number of days, to finish the project. Provide the “task
path” through the network diagram that sets the total project duration.
5) Using the substitute cost data provided below, and the additional information provided in the
paragraph immediately following (top of page 5 of the case), compute the cost to complete the
project for the Base Case, Best Case, and Worst Case scenarios. You will provide a different
answer for each of the different scenarios.
HINT FOR INTERPRETING TABLE 2
Table 2 provides the “predecessor” information for
the activities described in Table 1. To determine the
predecessors for any given activity, go to the
corresponding row (“Dependent Activity”) and read
across the row looking for “tick marks” (a vertical bar
in a table cell) that indicate a predecessor activity
(“Input Providing Activity”). For example,
A2 has predecessor A1
A3 has predecessors A1 and A2
A4 has predecessors A1 and A2
A5 has predecessors A1 and A4
SUBSTITUTE DATA
Use the data provided here for durations and costs, rather than those provided in the case.
WX:codehelp
这篇关于Dragonfly Network Diagram Analysis的文章就介绍到这儿,希望我们推荐的文章对编程师们有所帮助!