本文主要是介绍【CTF Reverse】XCTF GFSJ0487 game Writeup(反编译+逆向工程),希望对大家解决编程问题提供一定的参考价值,需要的开发者们随着小编来一起学习吧!
game
菜鸡最近迷上了玩游戏,但它总是赢不了,你可以帮他获胜吗
解法
放进 exeinfope 中分析。
拖入 IDA 中。shift + f12 查看字符串。ctrl + f 搜索 flag。
DATA XREF: sub_45E940+28↑o
Function 中搜索 sub_45E940。

flag 应该是在这里算出来的:
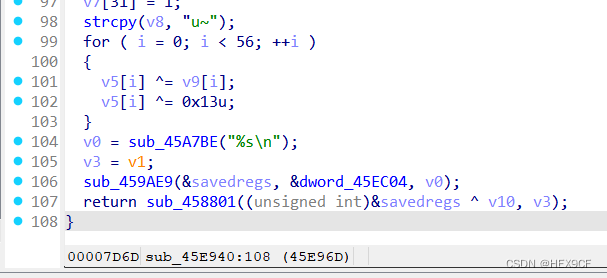
将这段 c 伪代码魔改为 c++ 程序:
#include <cstring>
#include <iostream>
#define AUTHOR "HEX9CF"
using namespace std;int main() {int v0; // eaxint v1; // edxint v3; // [esp-4h] [ebp-168h]int i; // [esp+D0h] [ebp-94h]char v5[58]; // [esp+DCh] [ebp-88h] BYREF// char v5[3]; // [esp+DCh] [ebp-88h] BYREF// char v6[19]; // [esp+DFh] [ebp-85h] BYREF// char v7[32]; // [esp+F2h] [ebp-72h] BYREF// char v8[4]; // [esp+112h] [ebp-52h] BYREFchar v9[64]; // [esp+120h] [ebp-44h]int v10; // [esp+160h] [ebp-4h]int savedregs; // [esp+164h] [ebp+0h] BYREF// printf("done!!! the flag is ");v9[0] = 18;v9[1] = 64;v9[2] = 98;v9[3] = 5;v9[4] = 2;v9[5] = 4;v9[6] = 6;v9[7] = 3;v9[8] = 6;v9[9] = 48;v9[10] = 49;v9[11] = 65;v9[12] = 32;v9[13] = 12;v9[14] = 48;v9[15] = 65;v9[16] = 31;v9[17] = 78;v9[18] = 62;v9[19] = 32;v9[20] = 49;v9[21] = 32;v9[22] = 1;v9[23] = 57;v9[24] = 96;v9[25] = 3;v9[26] = 21;v9[27] = 9;v9[28] = 4;v9[29] = 62;v9[30] = 3;v9[31] = 5;v9[32] = 4;v9[33] = 1;v9[34] = 2;v9[35] = 3;v9[36] = 44;v9[37] = 65;v9[38] = 78;v9[39] = 32;v9[40] = 16;v9[41] = 97;v9[42] = 54;v9[43] = 16;v9[44] = 44;v9[45] = 52;v9[46] = 32;v9[47] = 64;v9[48] = 89;v9[49] = 45;v9[50] = 32;v9[51] = 65;v9[52] = 15;v9[53] = 34;v9[54] = 18;v9[55] = 16;v9[56] = 0;memcpy(v5, "{ ", 2);v5[2] = 18;memcpy(v5 + 3, "bwlA)|P}&|oJ1Sl^lT", 18);// qmemcpy(v6, "bwlA)|P}&|oJ1Sl^lT", 18);v5[3 + 18] = 6;// v6[18] = 6;memcpy(v5 + 3 + 19, "`S,yhn _uec{", 12);// qmemcpy(v7, "`S,yhn _uec{", 12);v5[3 + 19 + 12] = 127;v5[3 + 19 + 13] = 119;v5[3 + 19 + 14] = 96;v5[3 + 19 + 15] = 48;v5[3 + 19 + 16] = 107;v5[3 + 19 + 17] = 71;v5[3 + 19 + 18] = 92;v5[3 + 19 + 19] = 29;v5[3 + 19 + 20] = 81;v5[3 + 19 + 21] = 107;v5[3 + 19 + 22] = 90;v5[3 + 19 + 23] = 85;v5[3 + 19 + 24] = 64;v5[3 + 19 + 25] = 12;v5[3 + 19 + 26] = 43;v5[3 + 19 + 27] = 76;v5[3 + 19 + 28] = 86;v5[3 + 19 + 29] = 13;v5[3 + 19 + 30] = 114;v5[3 + 19 + 31] = 1;strcpy(v5 + 3 + 19 + 32, "u~");// strcpy(v8, "u~");string flag = "";for (i = 0; i < 56; ++i) {v5[i] ^= v9[i];v5[i] ^= 0x13u;flag += v5[i];}cout << flag << endl;// v0 = sub_45A7BE("%s\n");// v3 = v1;// sub_459AE9(&savedregs, &dword_45EC04, v0);// return sub_458801((unsigned int)&savedregs ^ v10, v3);return 0;
}输出:
zsctf{T9is_tOpic_1s_v5ry_int7resting_b6t_others_are_n0t}
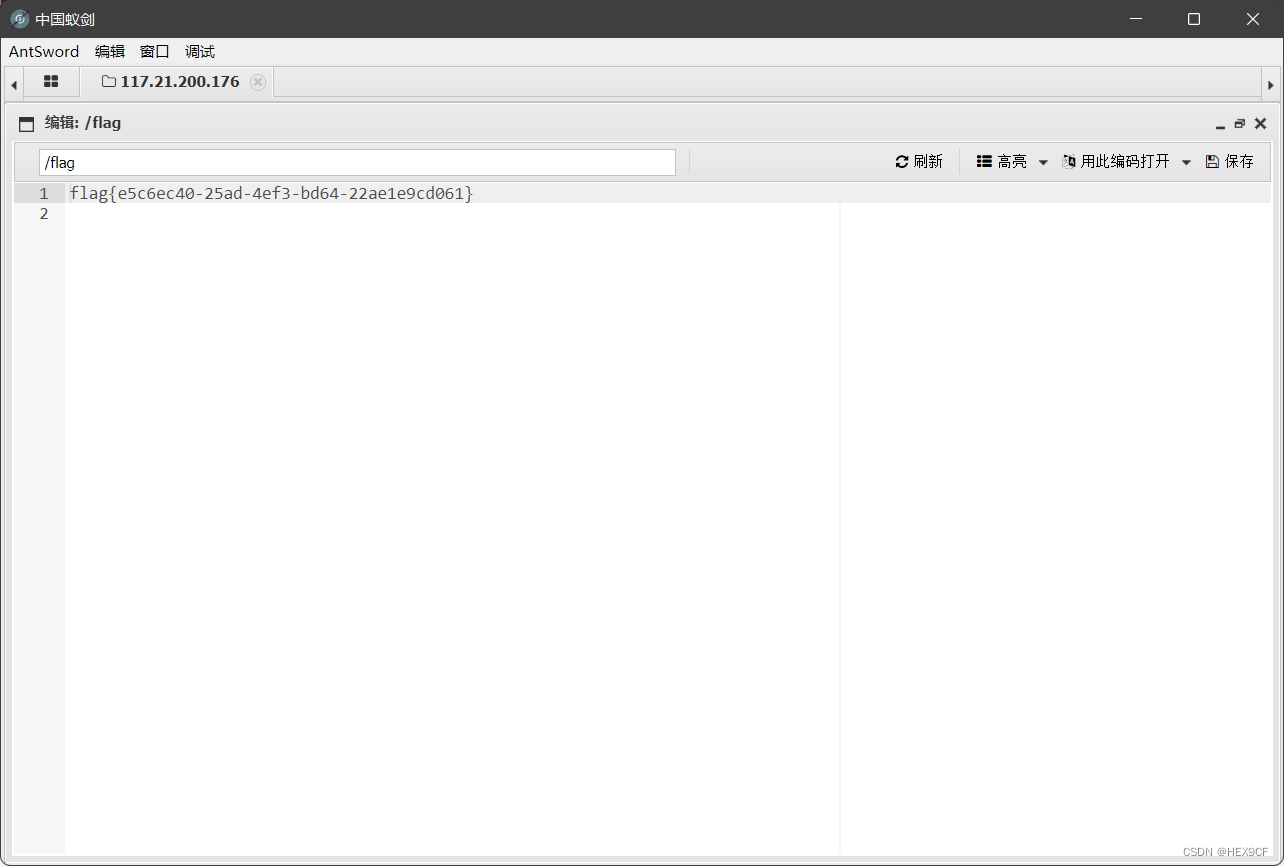
Flag
zsctf{T9is_tOpic_1s_v5ry_int7resting_b6t_others_are_n0t}
声明
本博客上发布的所有关于网络攻防技术的文章,仅用于教育和研究目的。所有涉及到的实验操作都在虚拟机或者专门设计的靶机上进行,并且严格遵守了相关法律法规。
博主坚决反对任何形式的非法黑客行为,包括但不限于未经授权的访问、攻击或破坏他人的计算机系统。博主强烈建议每位读者在学习网络攻防技术时,必须遵守法律法规,不得用于任何非法目的。对于因使用这些技术而导致的任何后果,博主不承担任何责任。
这篇关于【CTF Reverse】XCTF GFSJ0487 game Writeup(反编译+逆向工程)的文章就介绍到这儿,希望我们推荐的文章对编程师们有所帮助!