本文主要是介绍Wireshark 300: Curing Latency and Network Slowness,希望对大家解决编程问题提供一定的参考价值,需要的开发者们随着小编来一起学习吧!
转自:vonnie
Laaatteennncyyyyy.
AKA SLOWNESS! No one wants to deal with it but how many of us know the root cause of the problem? With Wireshark you can figure out exactly what’s causing your internet connection to crawl.
Here’s the scenario:
Everytime a user tries to access the internet it takes the page forever to download. What’s going on?
You can use Wireshark to gain insight on the problem. You can either start your capture on the host computer itself or configure port-spanning on the Cisco switch to mirror the traffic out an adjacent switchport. But let’s assume you don’t have access to the Cisco switch. Maybe you’re not authorized or you don’t want to bother with switchport configuration on a Cisco switch.
At any given moment a single computer will have multiple TCP connections to various destinations so our first order of business is see the time difference between segments within a single TCP conversation.
Start the packet capture, right click the relevant row in the PDU data pane and mouse down to Protocol preferences.
Make sure Calculate conversation timestamps has check next to it. You might also want to set this up in a new Wireshark profile.
(ps:上面提到的"Calculate conversation timestamps"这个功能只有TCP及基于TCP的上层协议才会有,分别对应wireshark处理TCP协议时用到的TSval和TSecr字段,其中TSval字段是TCP发送方的时钟,参考跳转;如果要计算捕获的TCP\DNS\HTTP包之间的时间差,可以分别使用:
1.tcp.time_relative或tcp.time_delta作为显示列,这两项正好对应TCP协议在"Packet detail"面板中的Timestamps选项;
2.DNS可以用dns.time作为显示列;
3.Http可以用http.time作为显示列;)
Now if you scroll down in the PDU details pane you’ll see a new section under the Transmission Control Protocol dissector called:
[Timestamps]Now we can see the time in seconds since the last TCP segment in the current conversation.
Great, now let’s make it a little easier to read this by adding this valuable data as a new column.
Right click the TCP dissector in the details pane and choose Apply as Column from the popup menu.
Bam!
The new column appears but it’s a little too long isn’t it?
It says:
Time since previous frame in this TCP stream
But let’s rename it to:
Segment Delta
That way we’ll know this contains the change (delta) between TCP segments.
Right click the column and choose Edit Column Details…
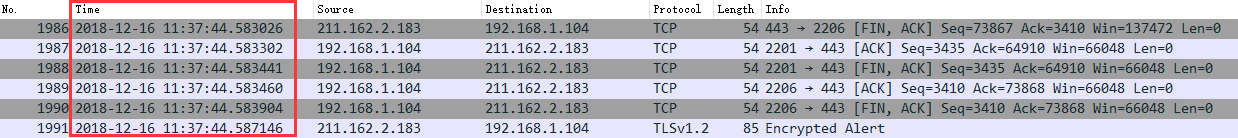
Great, now double click the column to sort by slowest values and scroll through the output. You’ll quickly see the TCP conversations responsible for the greatest latency.
To start this test for you, I downloaded a program called Netlimiter and installed it on my Windows 8.1 Virtual Machine. Then I manually told Netlimiter to limit all inbound and outbound traffic flows to a wimpy 5kbps. Ha!
So when I started the capture I could easily see the largest offenders.
You can see a segment delta of 941 milliseconds (almost a full second) from a request to download a JPG on 198.57.208.223 (which is fixedbyvonnie.com)
I hope this helps! Leave me your questions, cheers or digital beer in the comments below.
这篇关于Wireshark 300: Curing Latency and Network Slowness的文章就介绍到这儿,希望我们推荐的文章对编程师们有所帮助!