本文主要是介绍cookie反爬实战案例四(acw_sc__v2 + 无限debugger处理),希望对大家解决编程问题提供一定的参考价值,需要的开发者们随着小编来一起学习吧!
文章目录
-
一、需求
-
获取雪球热帖数据
-
-
二、目标网址
-
aHR0cHM6Ly94dWVxaXUuY29tL3RvZGF5Iy8=
-
-
三、详细步骤
1、确定数据接口
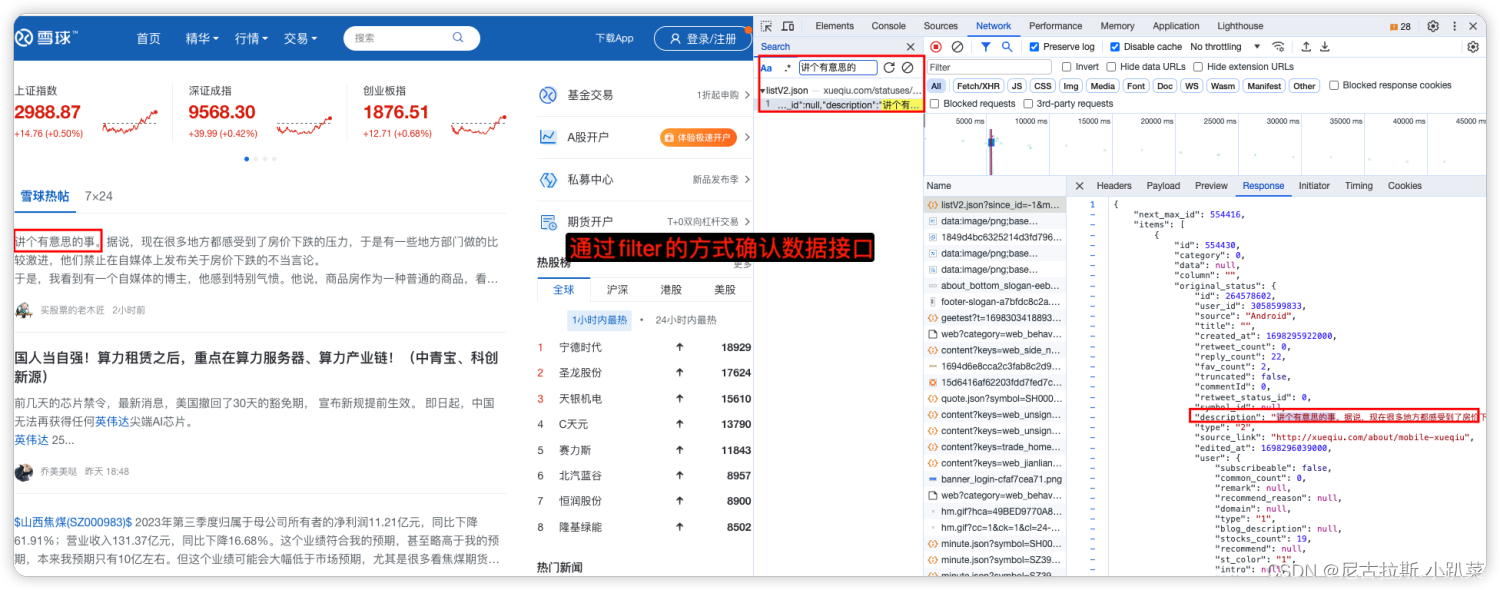
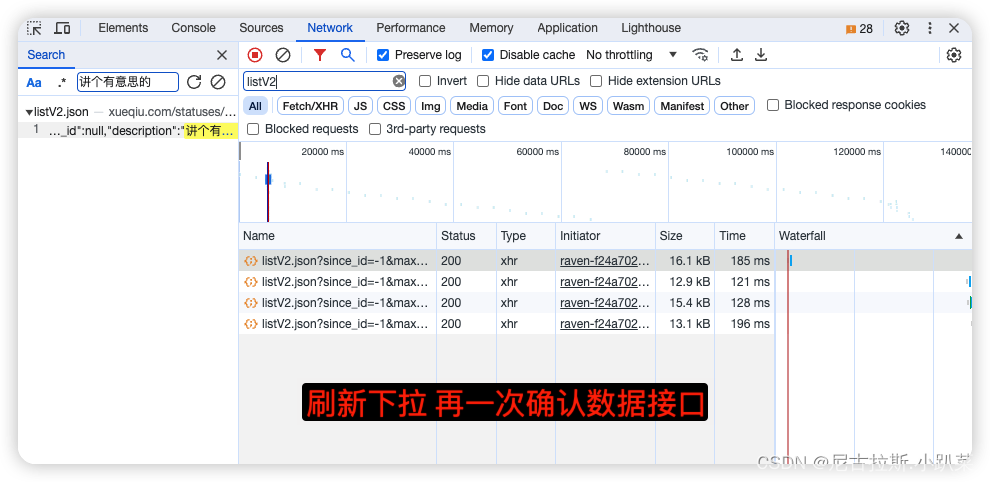
2、验证反爬并找到反爬参数
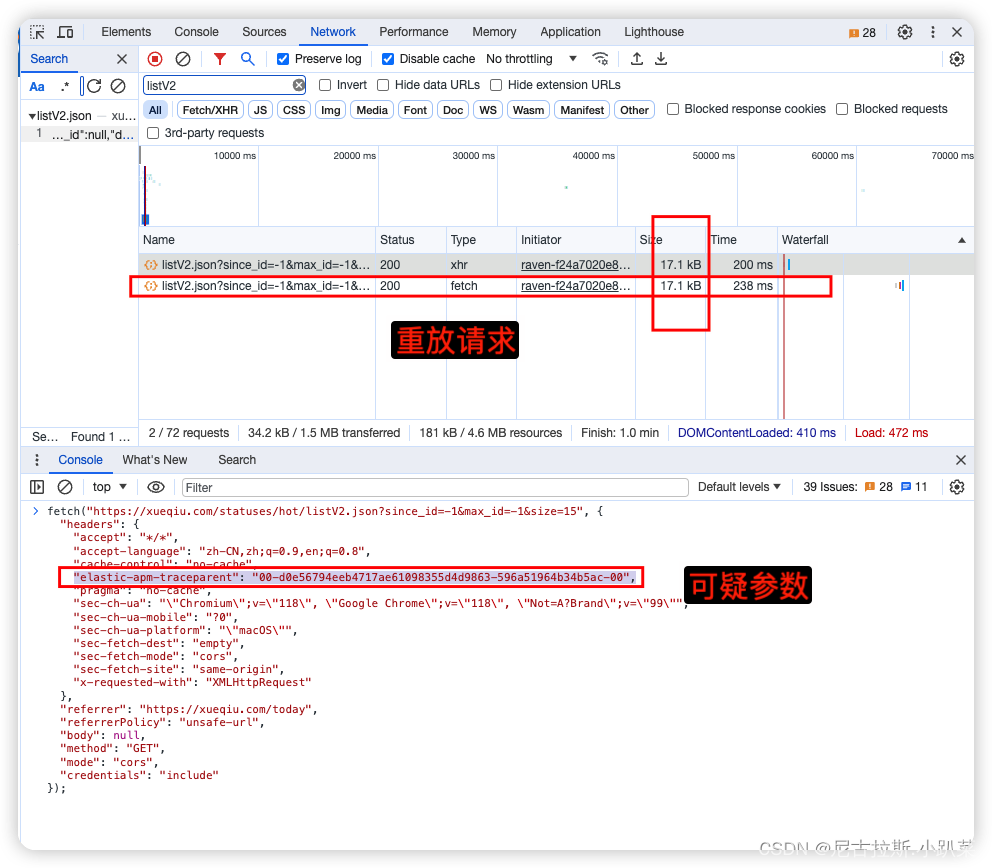
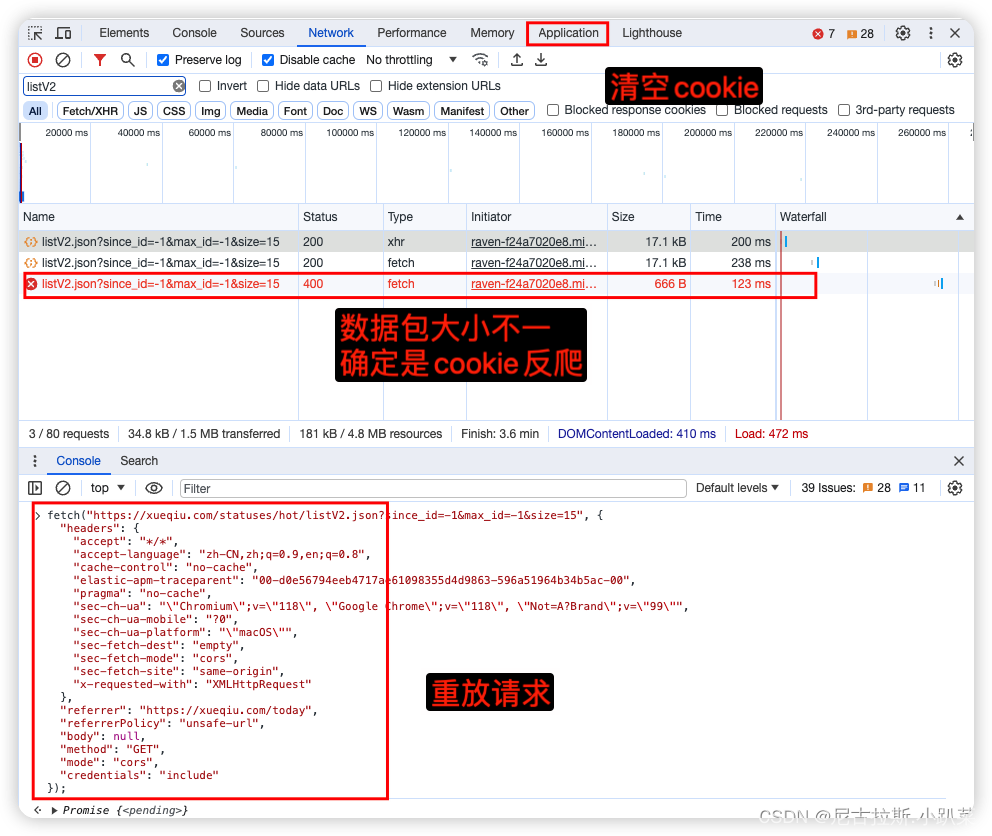
3、确定cookie反爬参数
import requestsheaders = {"Accept": "*/*","Accept-Language": "zh-CN,zh;q=0.9,en;q=0.8","Cache-Control": "no-cache","Connection": "keep-alive","Pragma": "no-cache","Referer": "https://xueqiu.com/today","Sec-Fetch-Dest": "empty","Sec-Fetch-Mode": "cors","Sec-Fetch-Site": "same-origin","User-Agent": "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/118.0.0.0 Safari/537.36","X-Requested-With": "XMLHttpRequest","elastic-apm-traceparent": "00-be07869557648708e851c1c12256571e-02aff688370889e7-00","sec-ch-ua": "\"Chromium\";v=\"118\", \"Google Chrome\";v=\"118\", \"Not=A?Brand\";v=\"99\"","sec-ch-ua-mobile": "?0","sec-ch-ua-platform": "\"macOS\""
}
cookies = {"acw_tc": "2760827616983046343678048ecca70edab9018ffae9e3f803778ce02ed758","acw_sc__v2": "653a13fa088f0aa6583d357bc0b311b21f86ee76","xq_a_token": "e2f0876e8fd368a0be2b6d38a49ed2dd5eec7557","xqat": "e2f0876e8fd368a0be2b6d38a49ed2dd5eec7557","xq_r_token": "2a5b753b2db675b4ac36c938d20120660651116d","xq_id_token": "eyJ0eXAiOiJKV1QiLCJhbGciOiJSUzI1NiJ9.eyJ1aWQiOi0xLCJpc3MiOiJ1YyIsImV4cCI6MTcwMDY5OTg3NSwiY3RtIjoxNjk4MzA0OTk2MzgyLCJjaWQiOiJkOWQwbjRBWnVwIn0.R-BOElv8npRZjzcwE0es_6Ex1qIL2CGm3Rgr07o3E7BrTkmvLr83gliSH0JMVyqUKa80yJZQIdPODyNZIuGXcAZ0TUl4Hcl921wjExzlwI2LjuTuXkZRyi-0qEBOHUJUXR1f42naARFS35wytf-ptEzE70lDn60AXuYXS3Aa-jswDXwHKMwLBOX7w5K8Eyo8Oa6kzWapHHUqb5xNZ8m2FdLaWUEoKNzIXk_euqfFH2X37C4lSoFZY3P6Wf_vcca0vszGBLRXwtXM2Iu9e8-AIy_d2mZC-bCVQWdLuqJydgSGi9uo9SquQAEm_f7Y4jrQIPh_2SSUjVPzwXCx0_0zhw","cookiesu": "821698305020757","u": "821698305020757","device_id": "1dfbc883865d3be224360f9104867c1d","Hm_lvt_1db88642e346389874251b5a1eded6e3": "1698305021","Hm_lpvt_1db88642e346389874251b5a1eded6e3": "1698305333"
}
url = "https://xueqiu.com/statuses/hot/listV2.json"
params = {"since_id": "-1","max_id": "-1","size": "15"
}
response = requests.get(url, headers=headers,cookies=cookies,params=params)print(response.text)
print(response)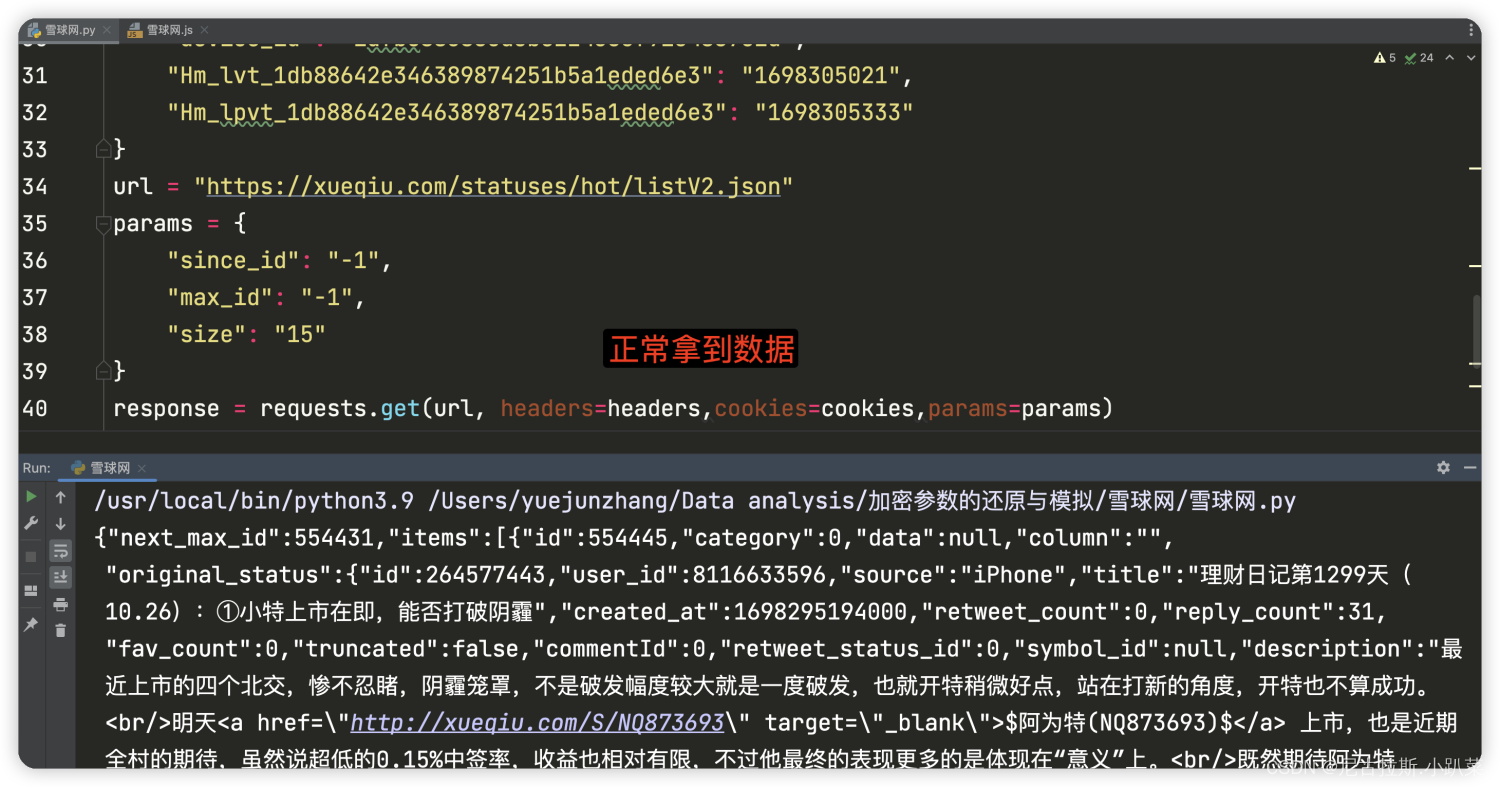
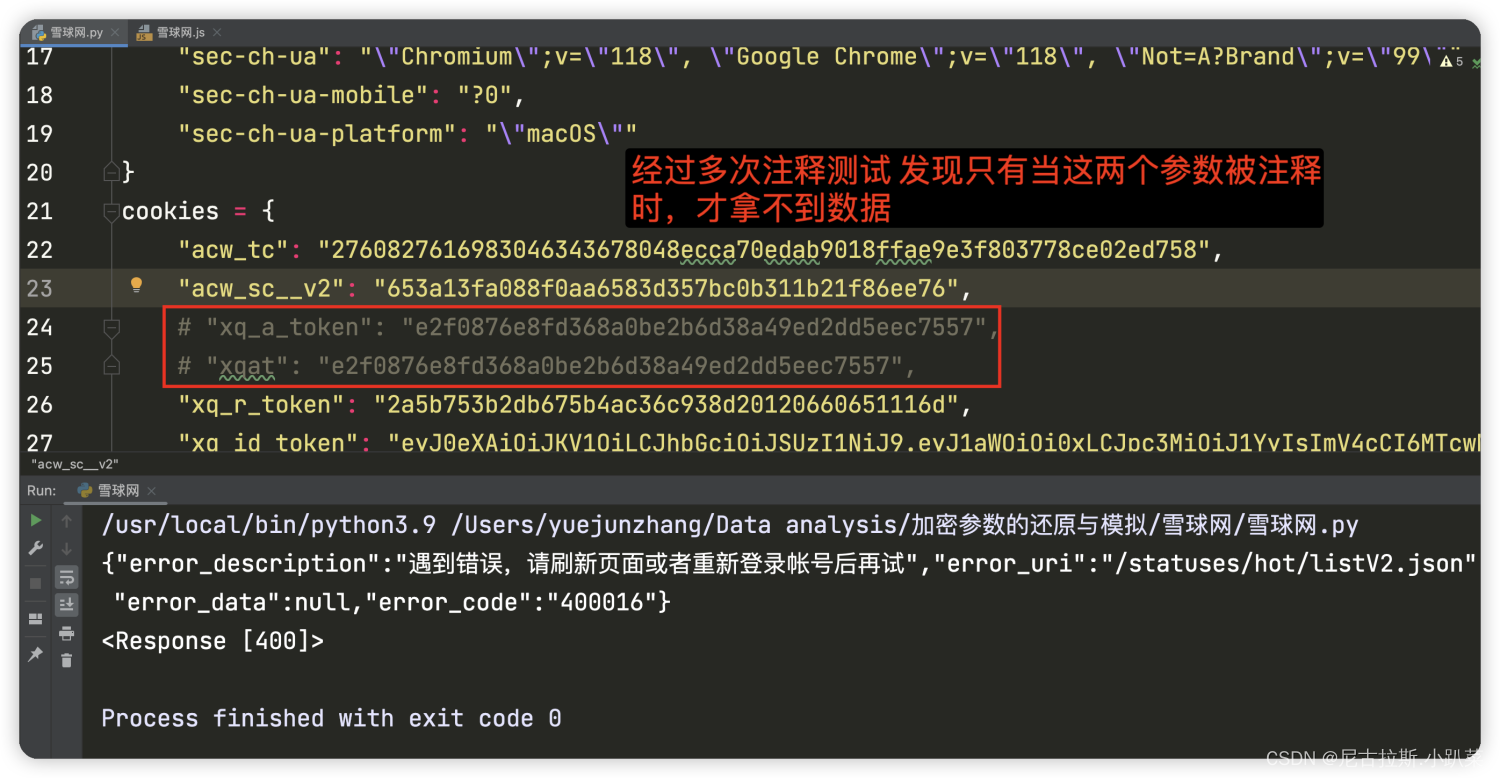
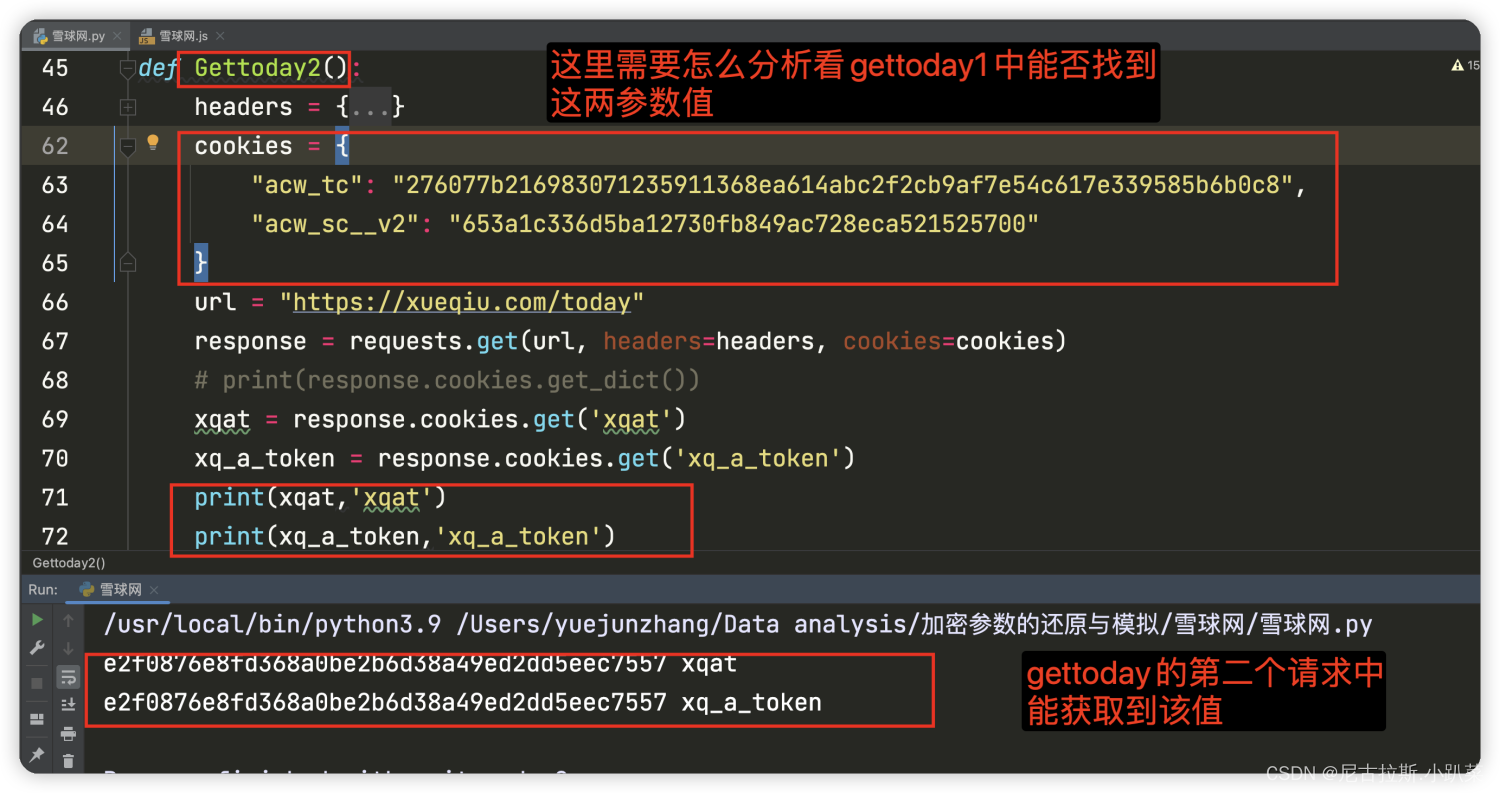
4、寻找xqat与xq_a_token参数值
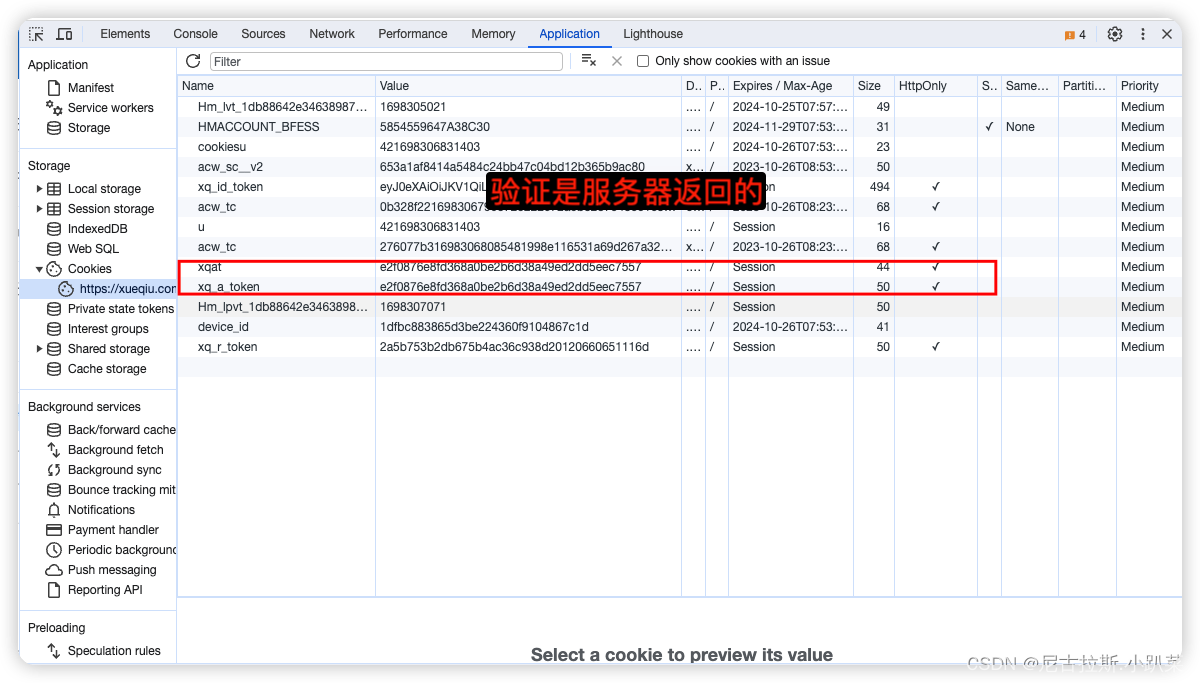
清空cookie 刷新页面 过掉debuger filter查找分析
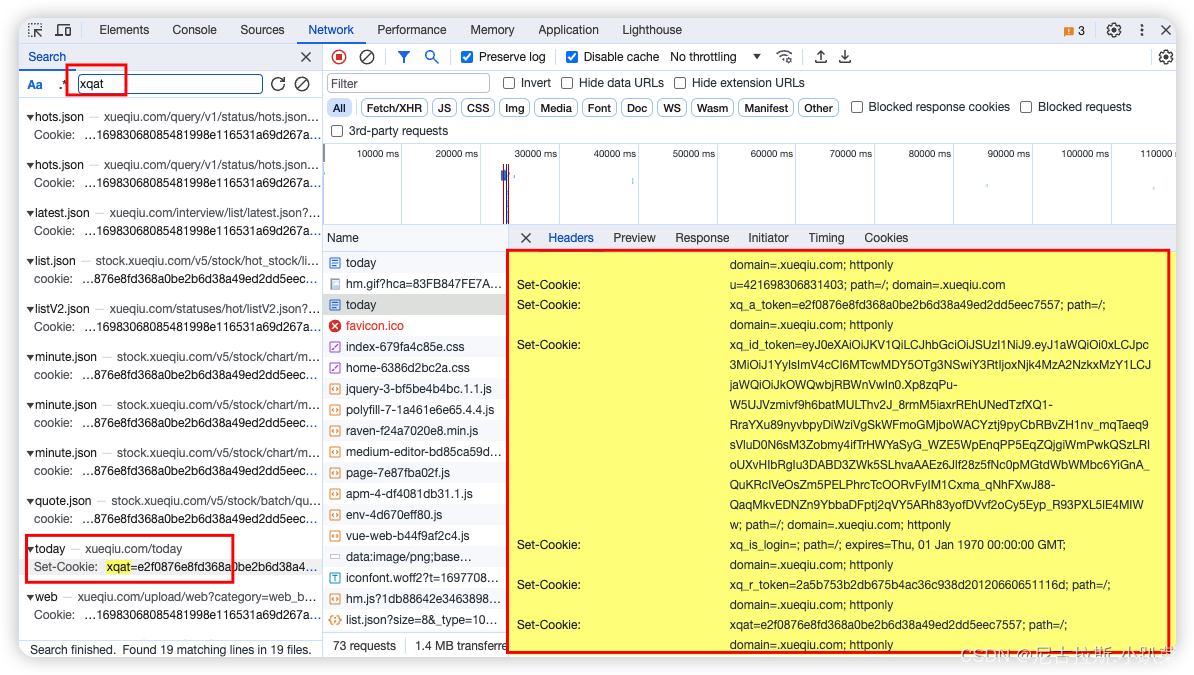
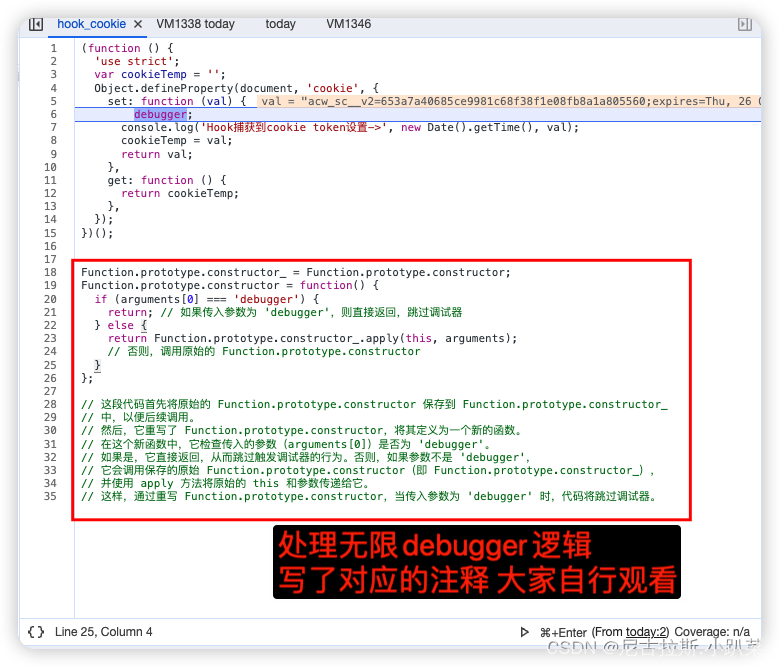
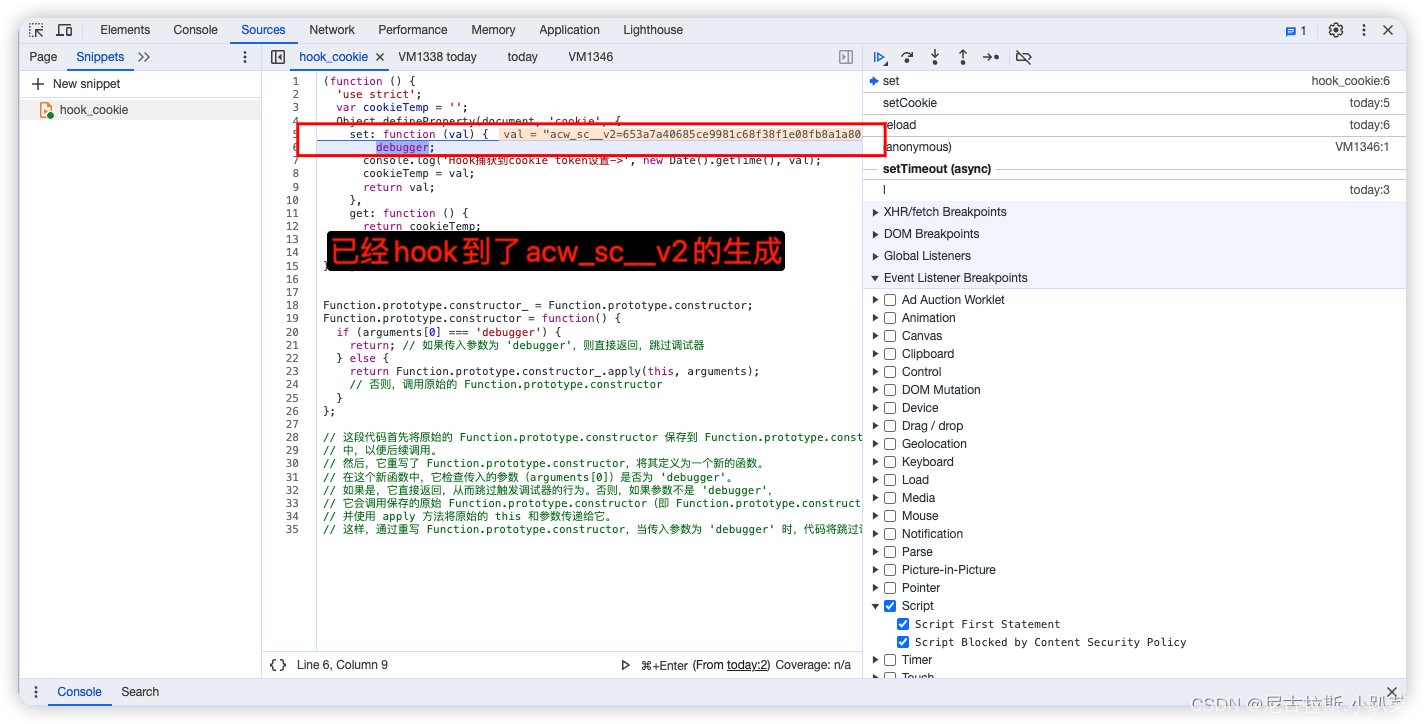
5、分析acw_sc__v2的参数生成
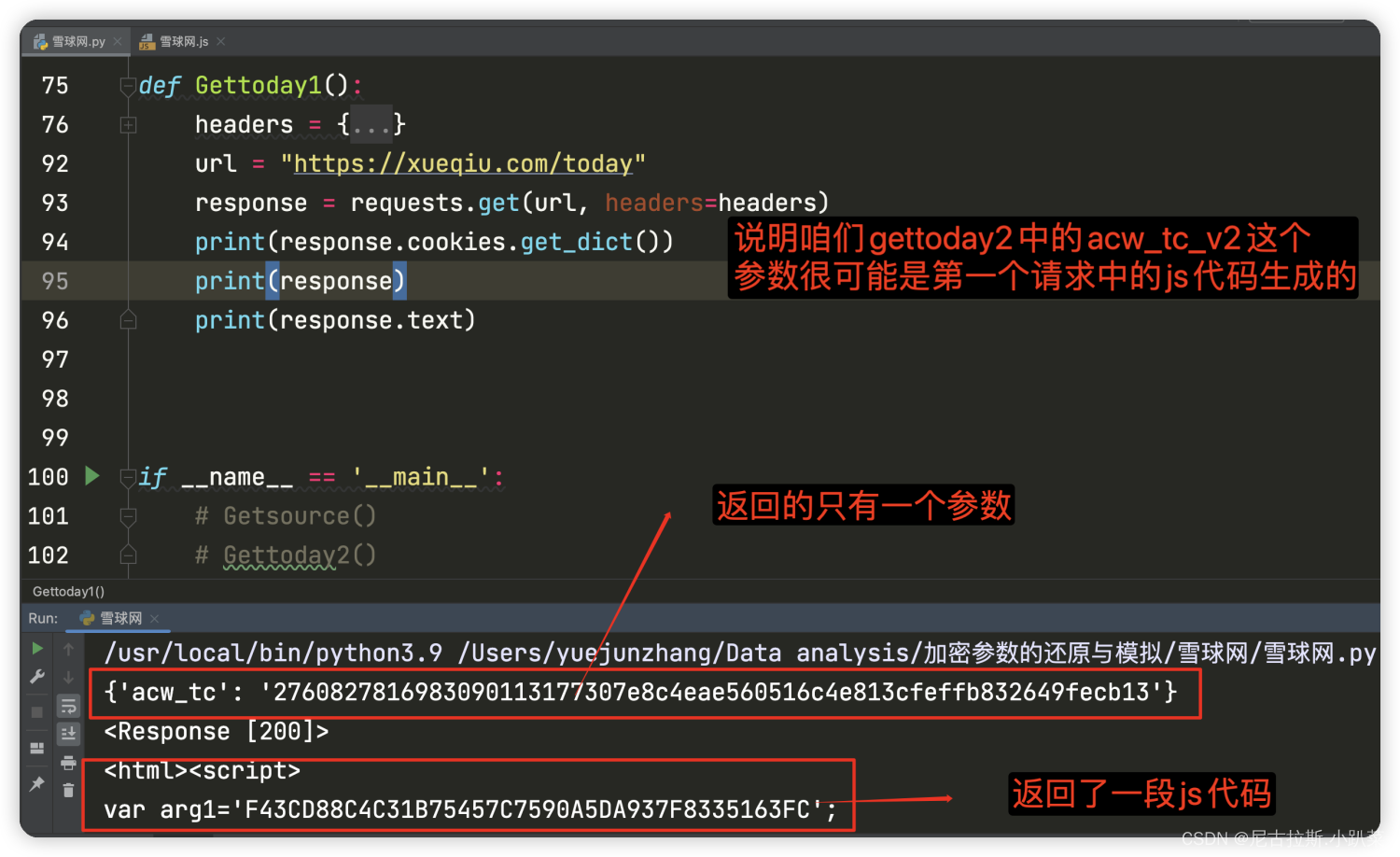
由于acw_sc__v2是在cookie中生成的,所以咱们直接下hook_cookie脚本
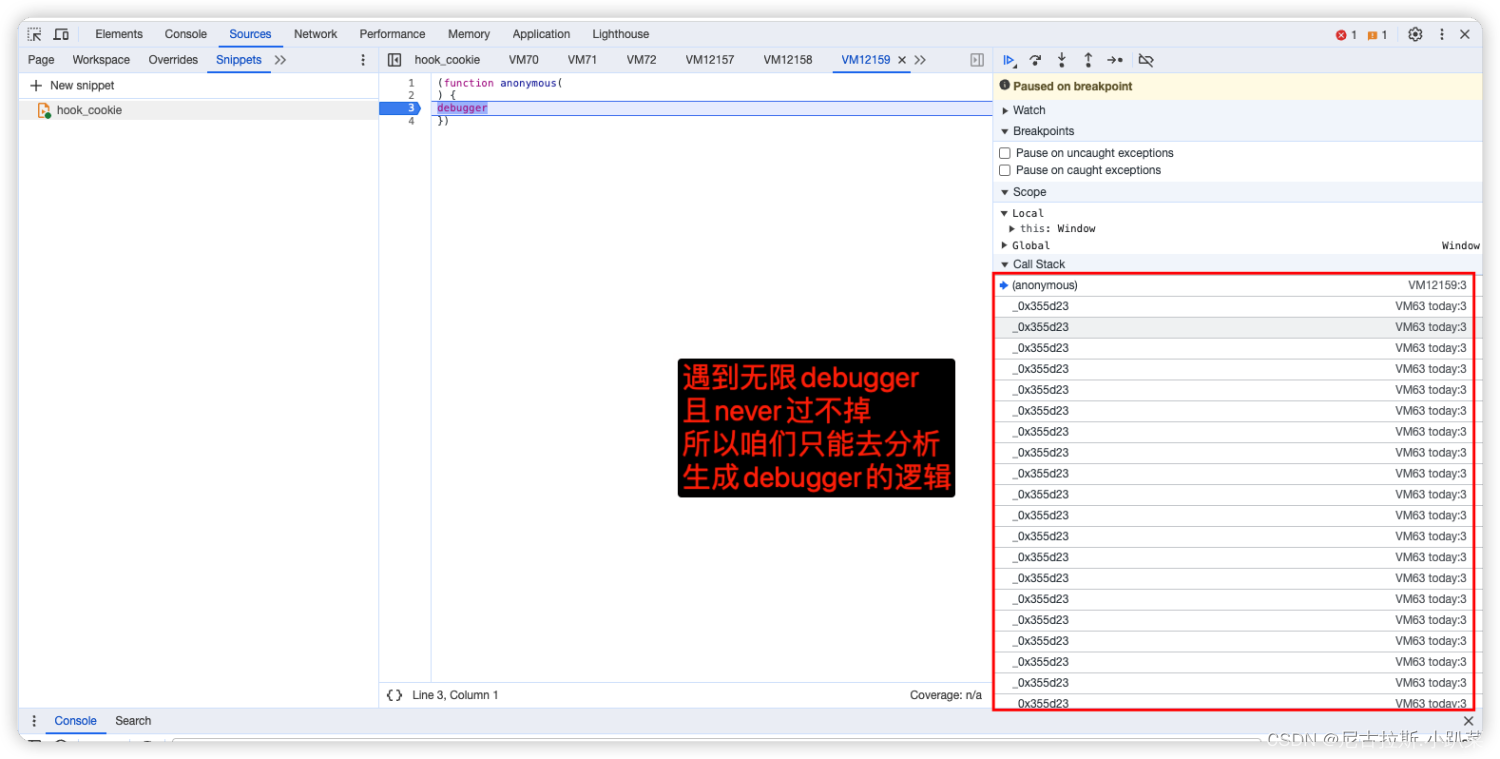
清空缓存、数据包、打上script断点、刷新页面、遇到无限debugger。
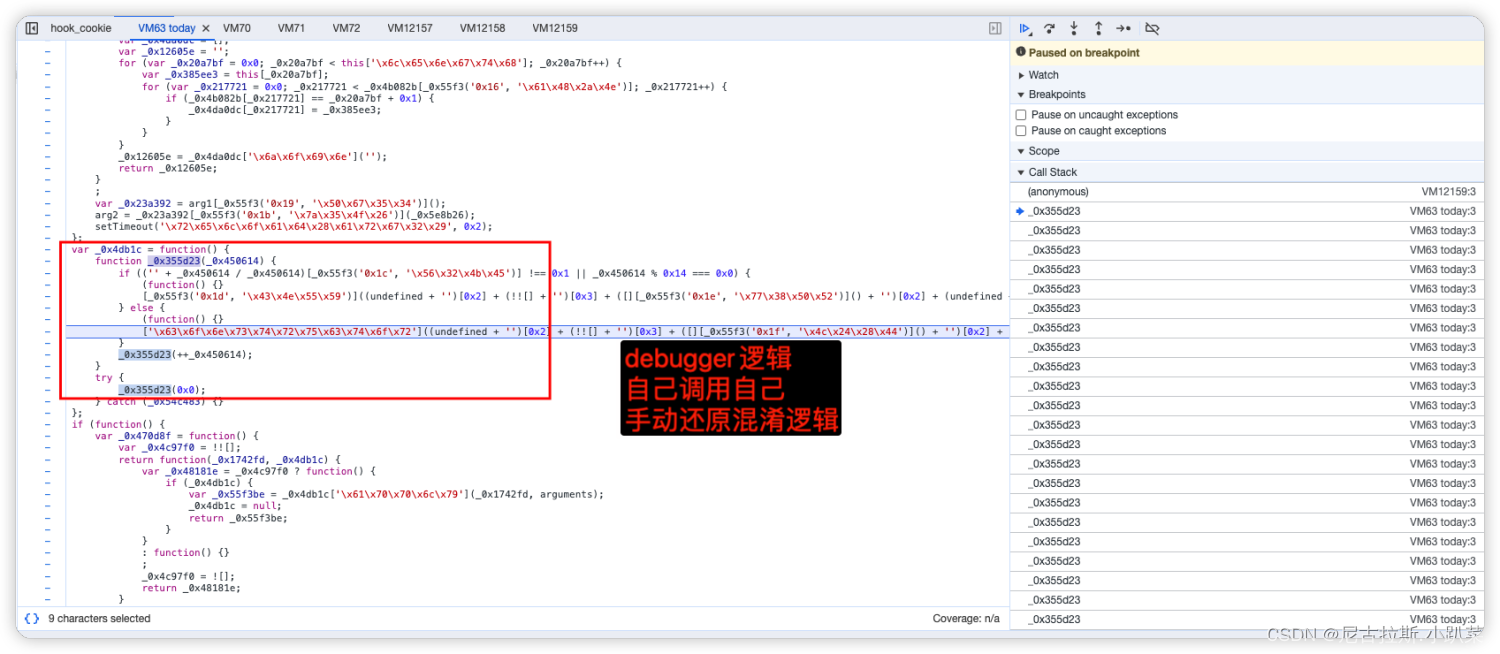
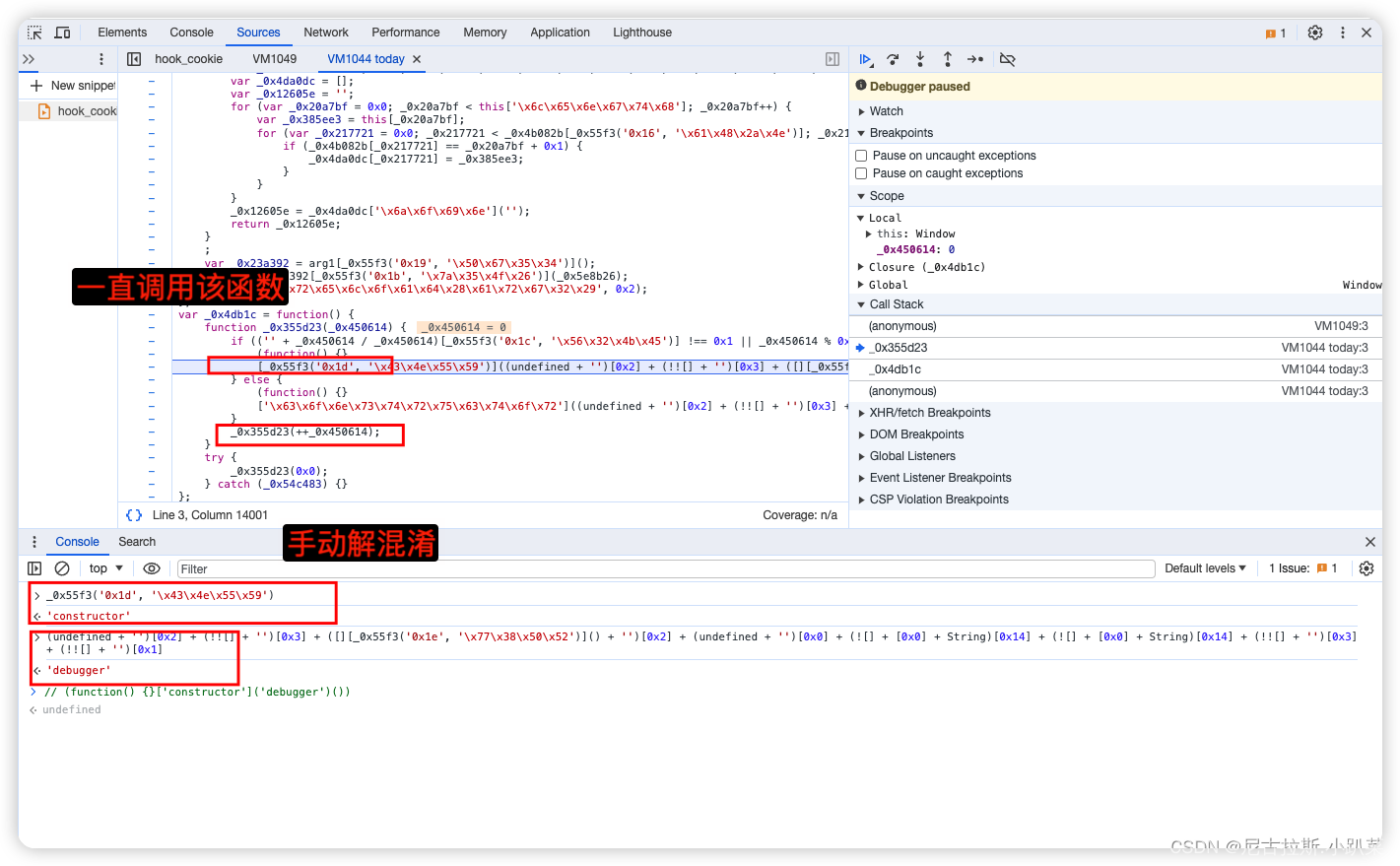
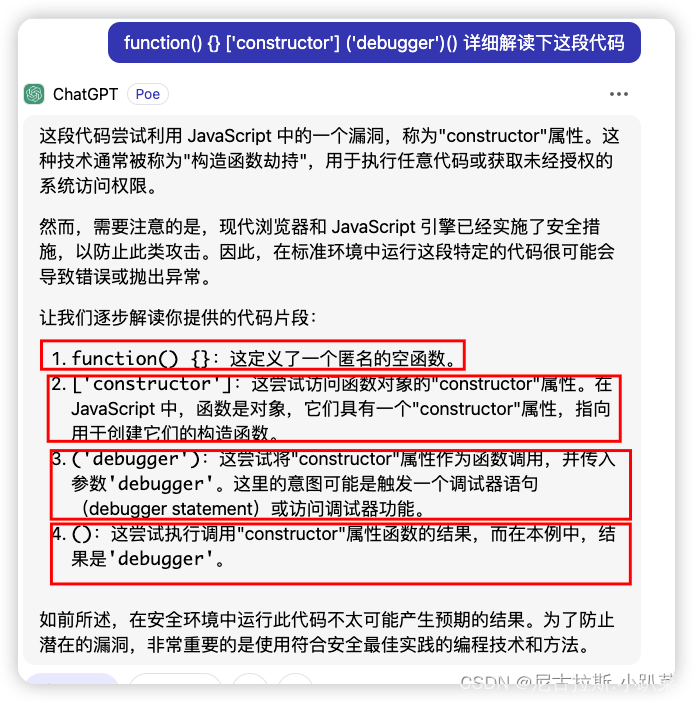
混淆代码详细解读
6、详细推演acw_sc__v2的生成逻辑
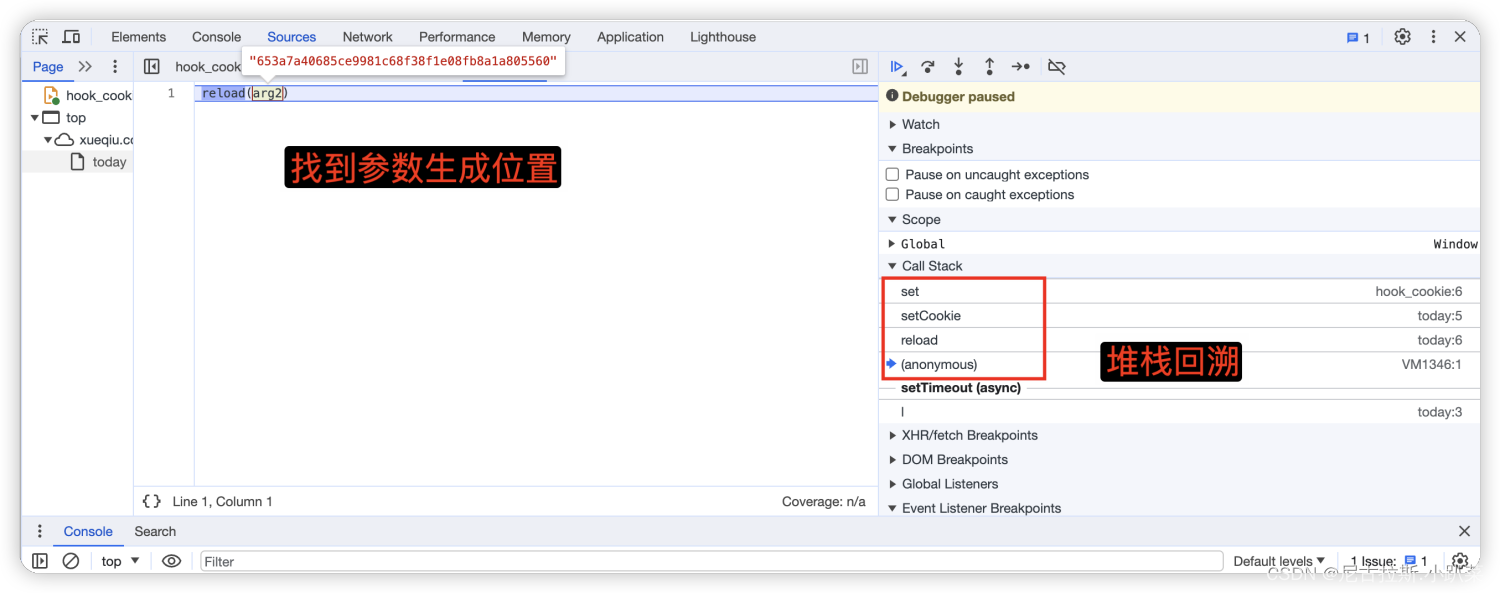
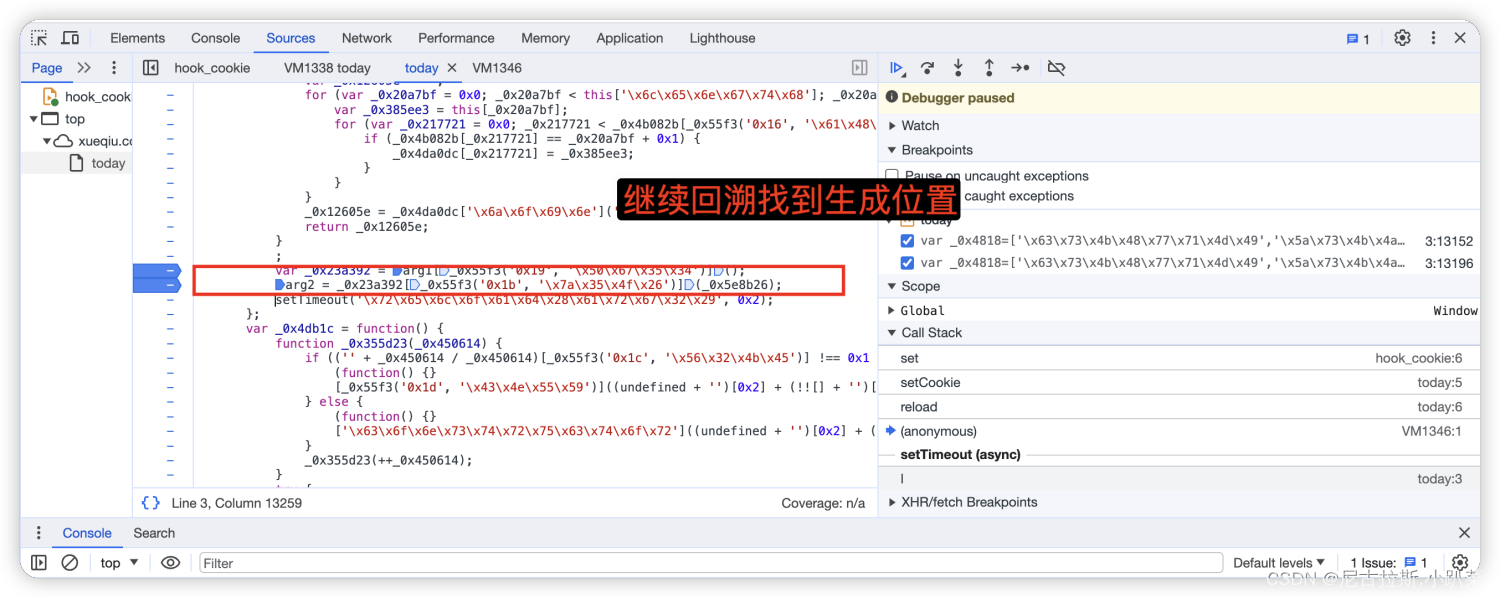
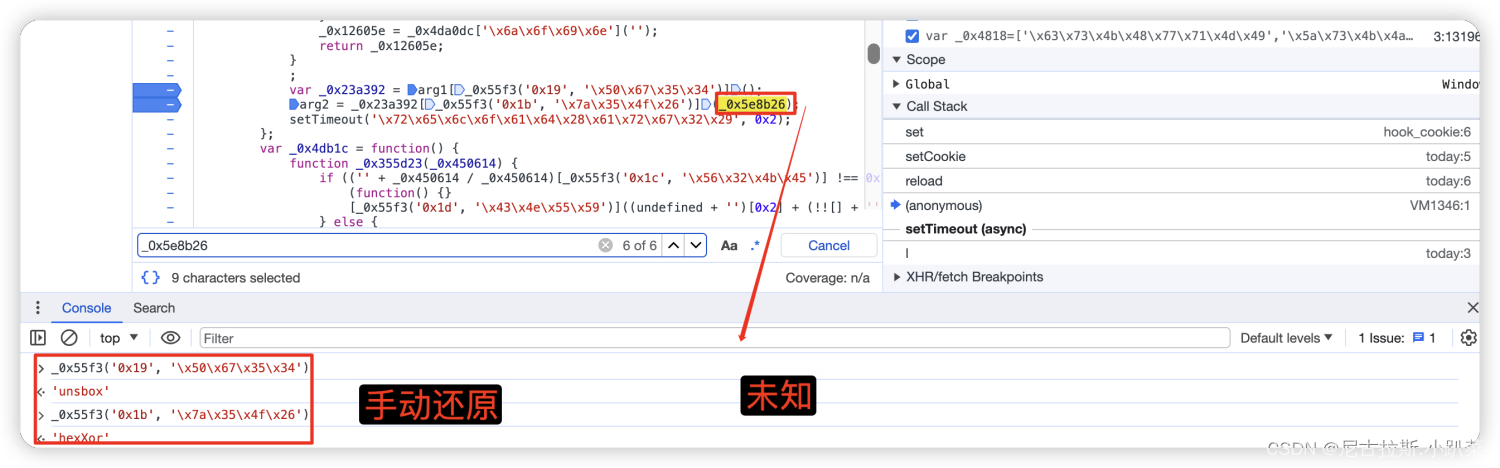
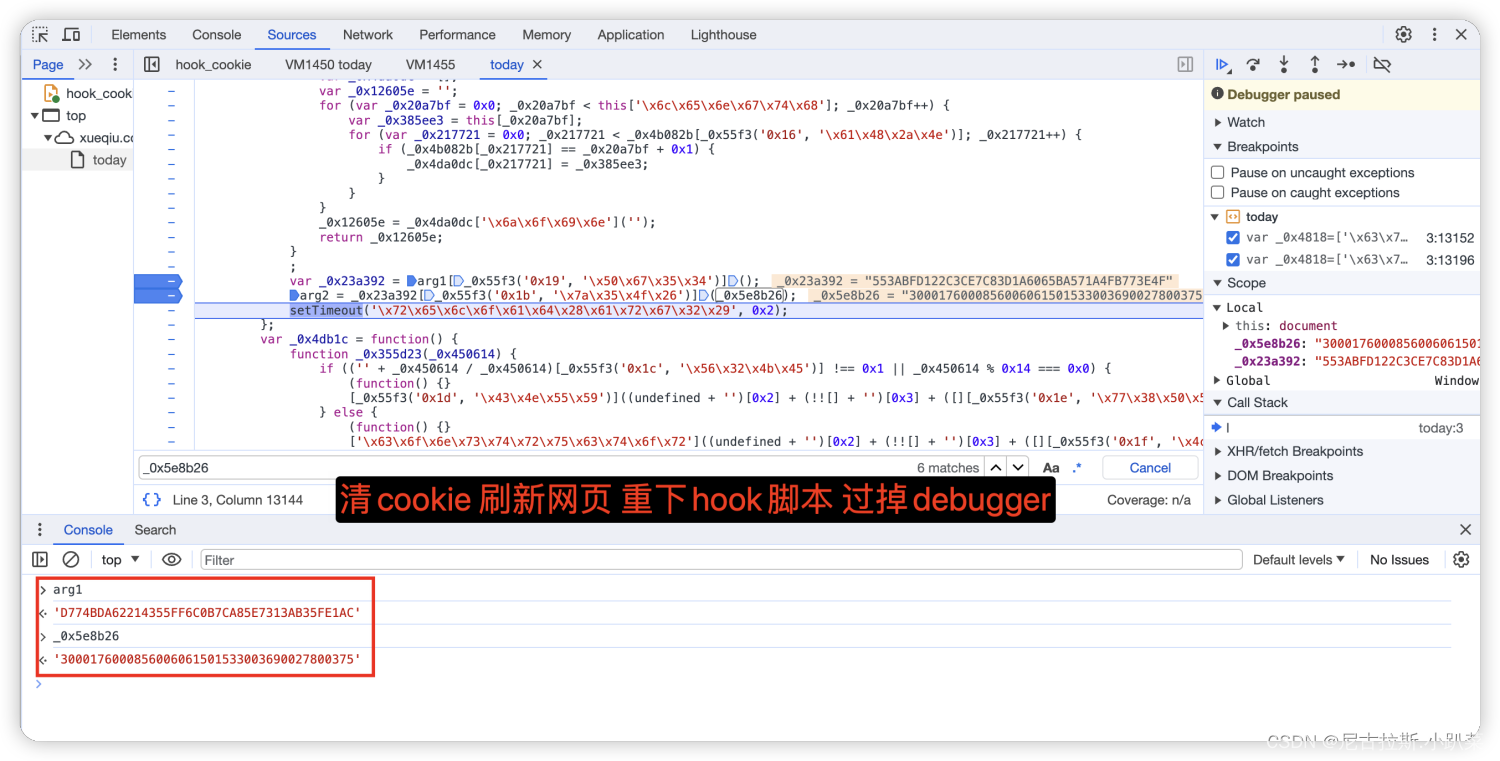
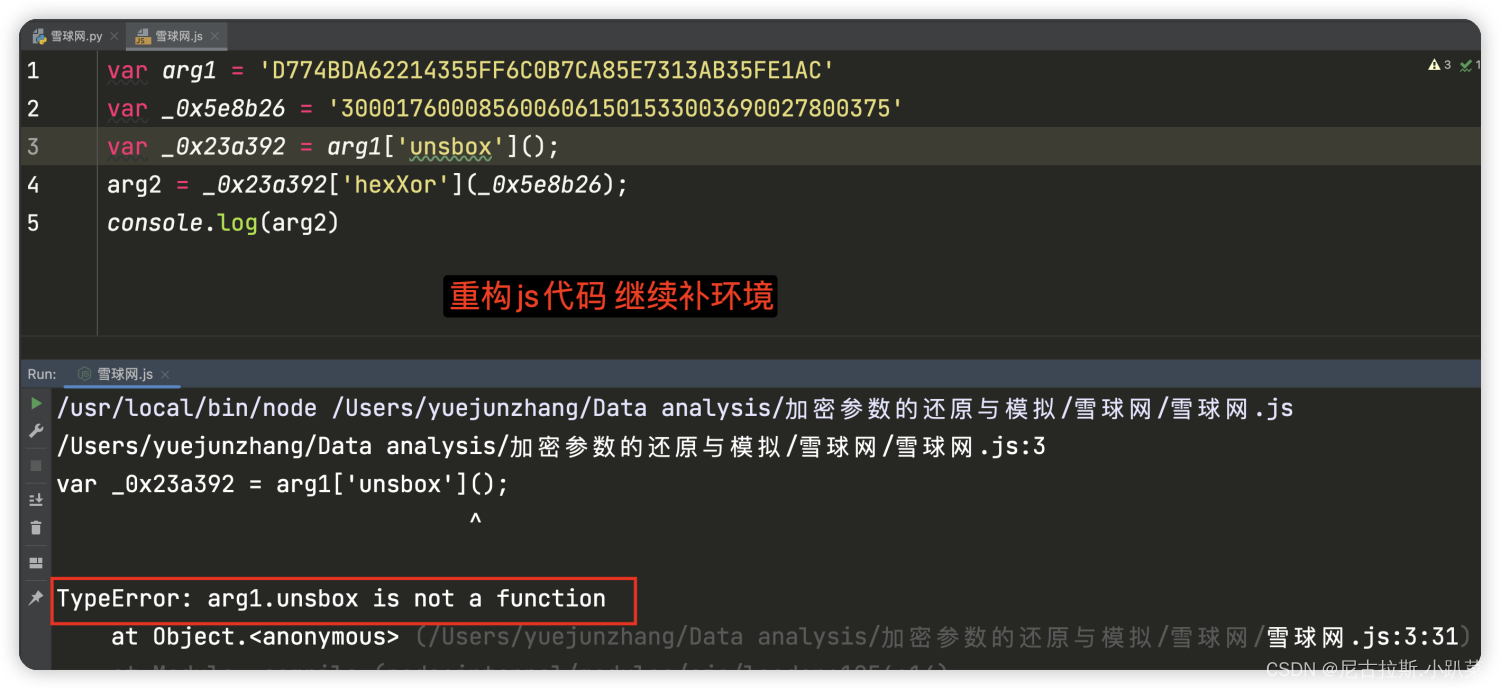
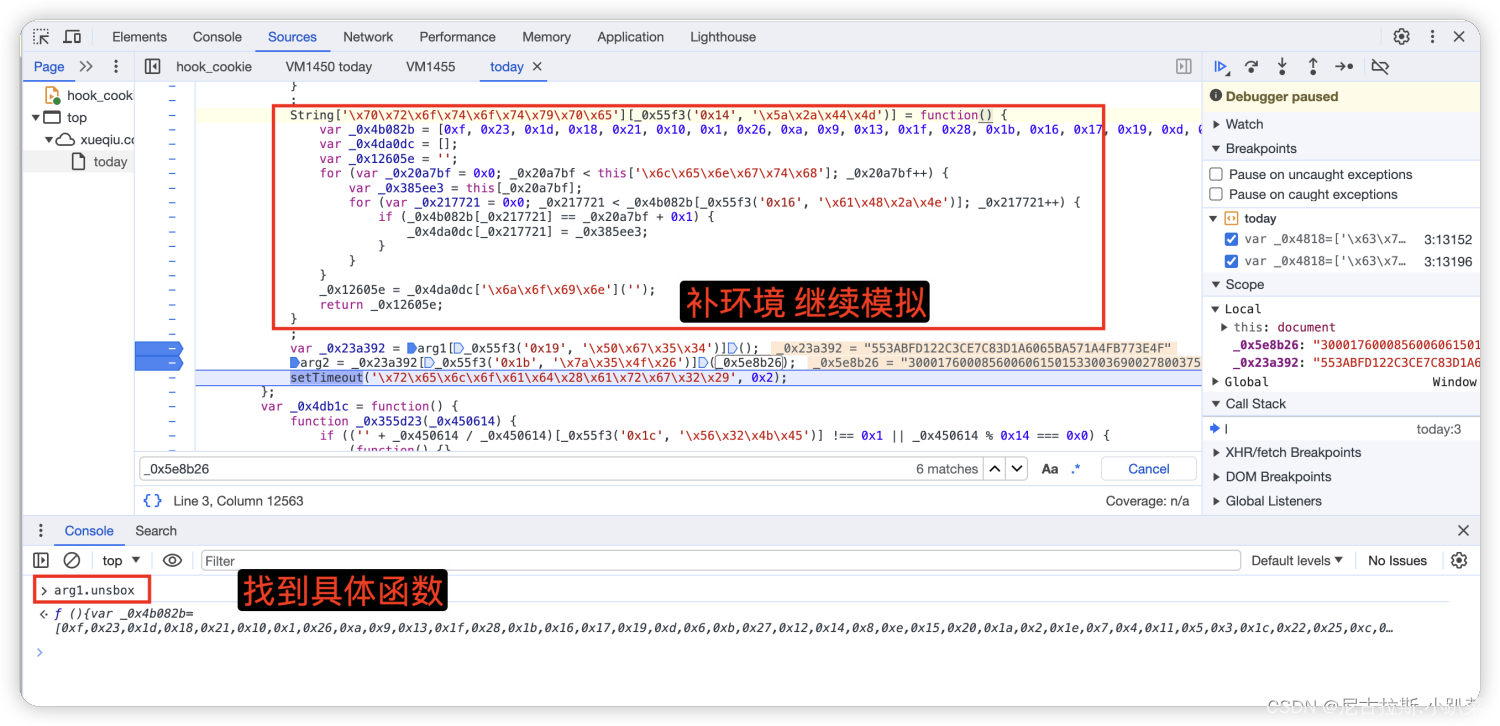
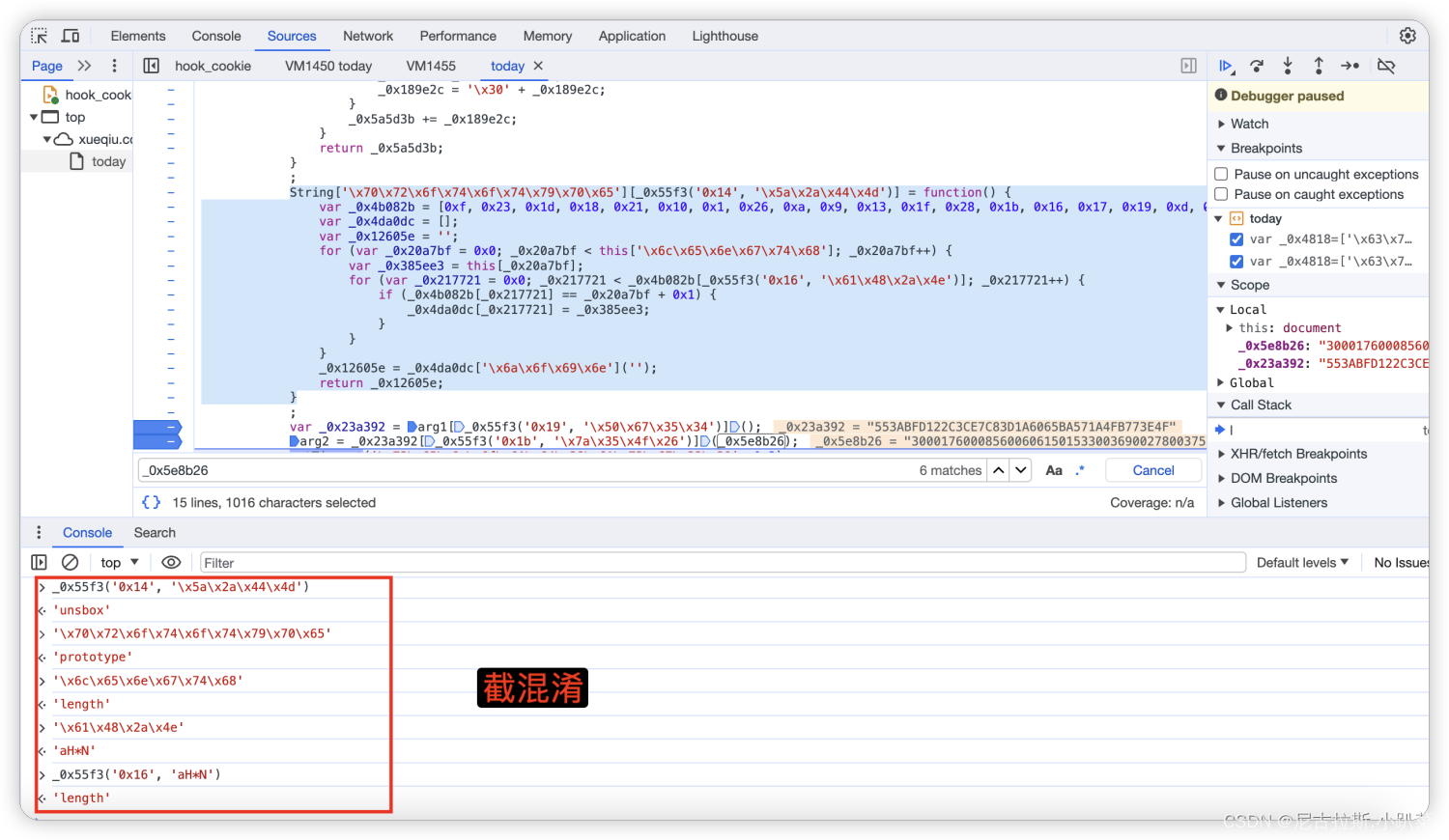
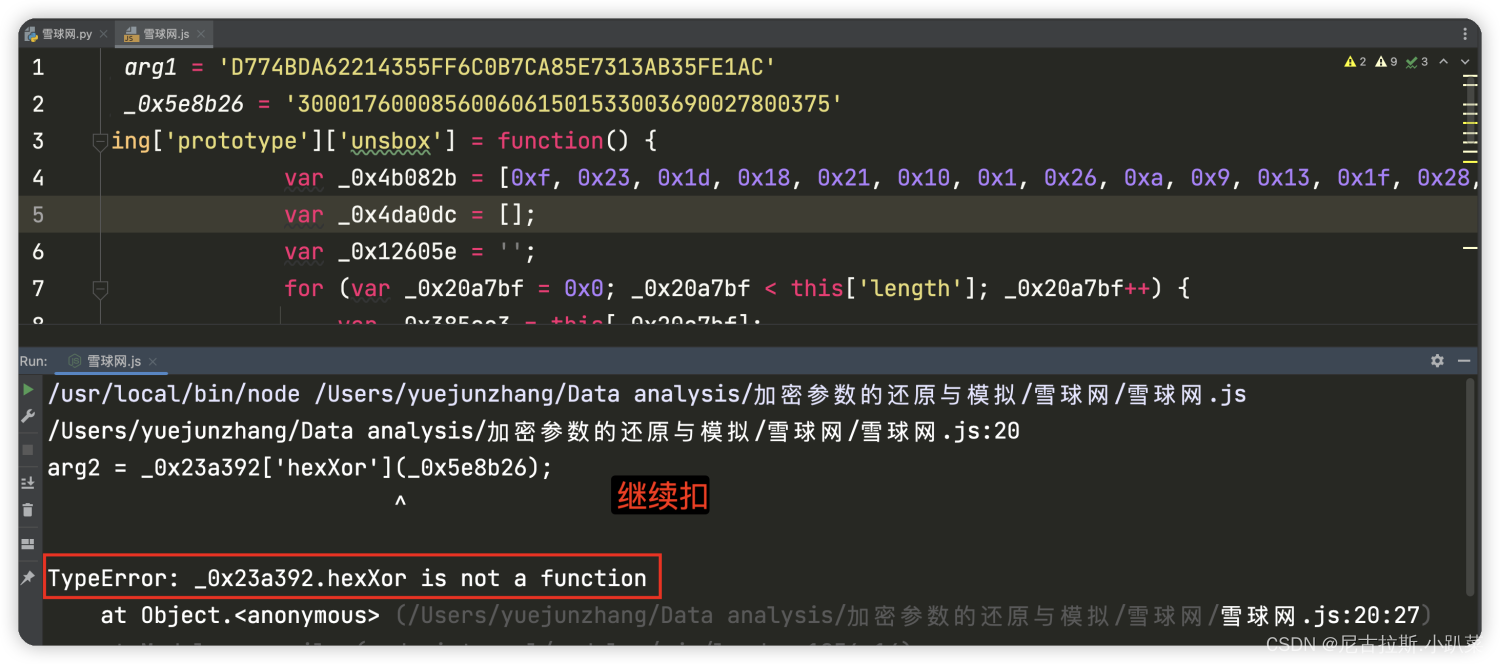
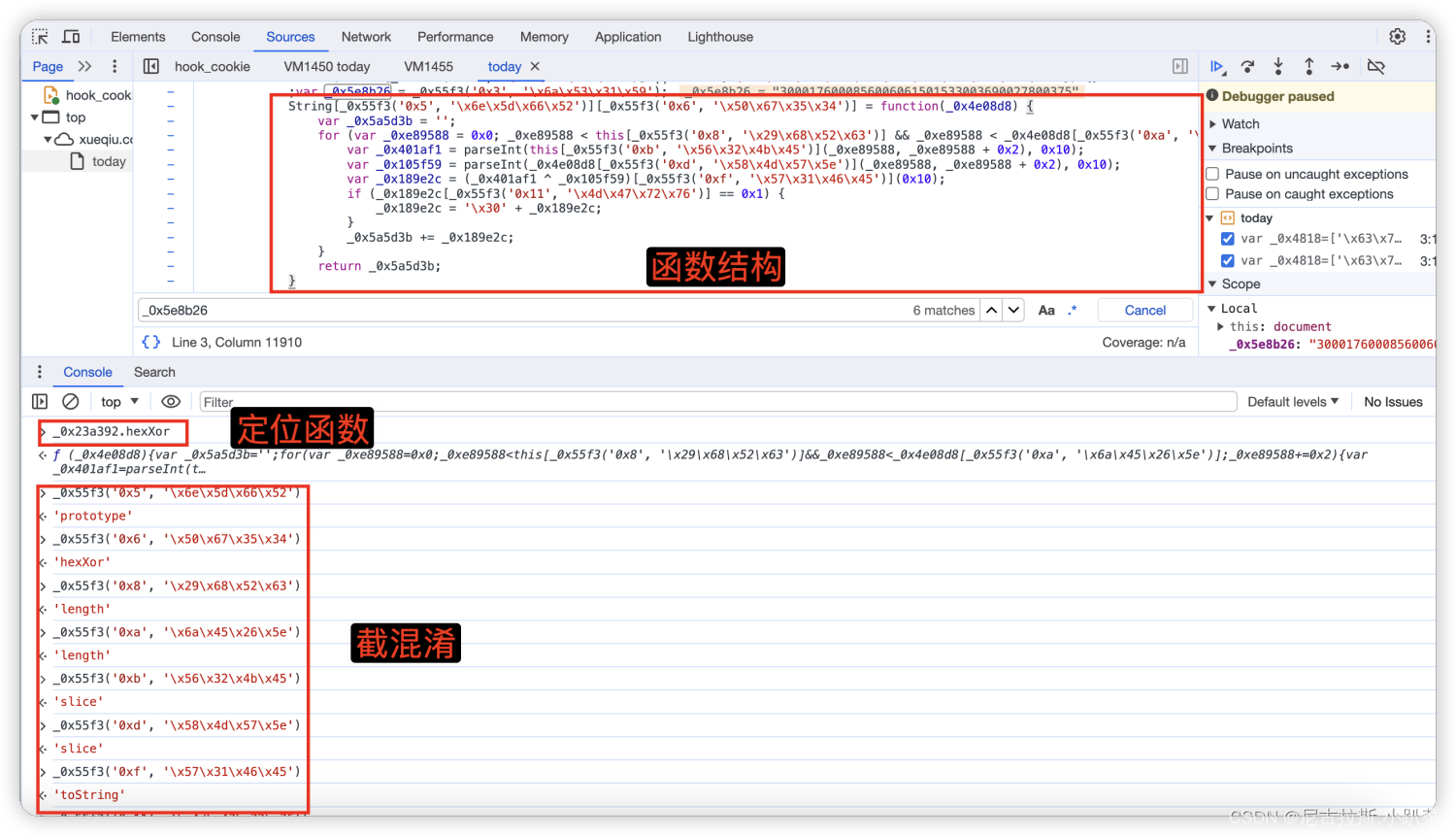
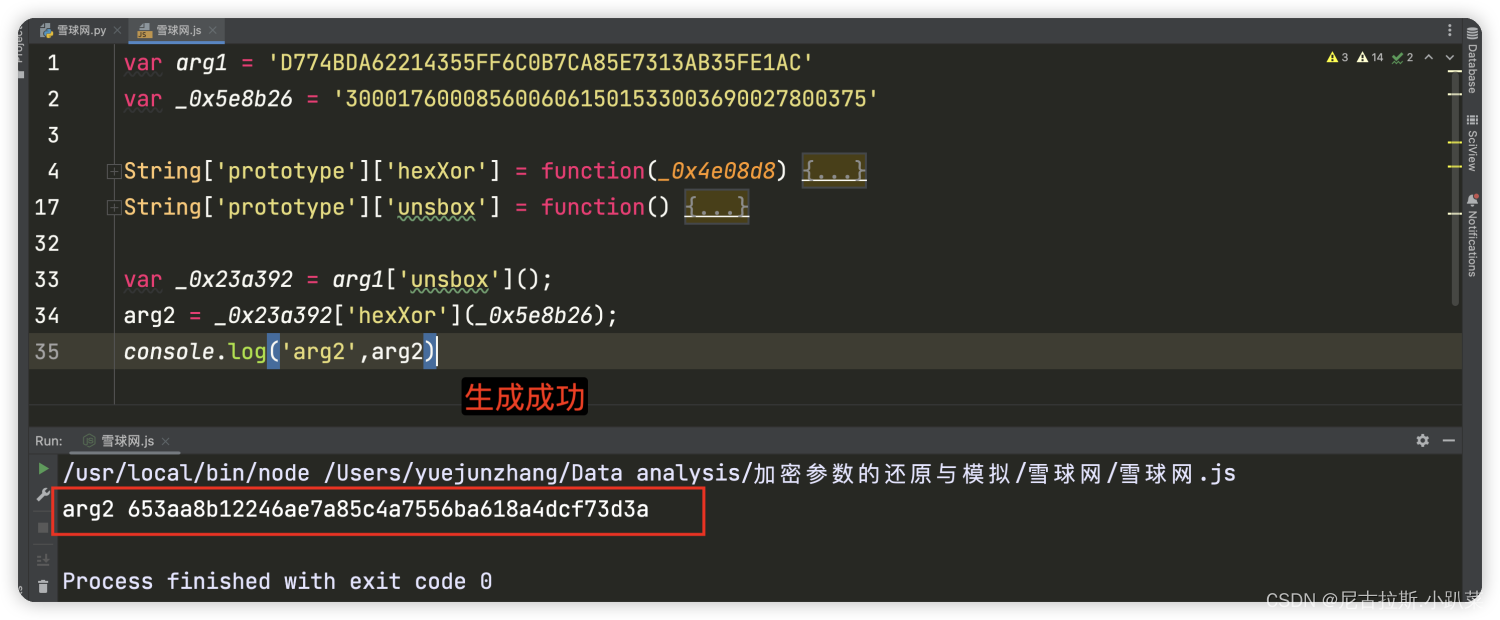
7、arg1与_0x5e8b26变量值的寻找

_0x5e8b26为固定生成的值,没必要去分析怎么生成的原理了 但是arg1是每次变化的 所以咱们继续分析。
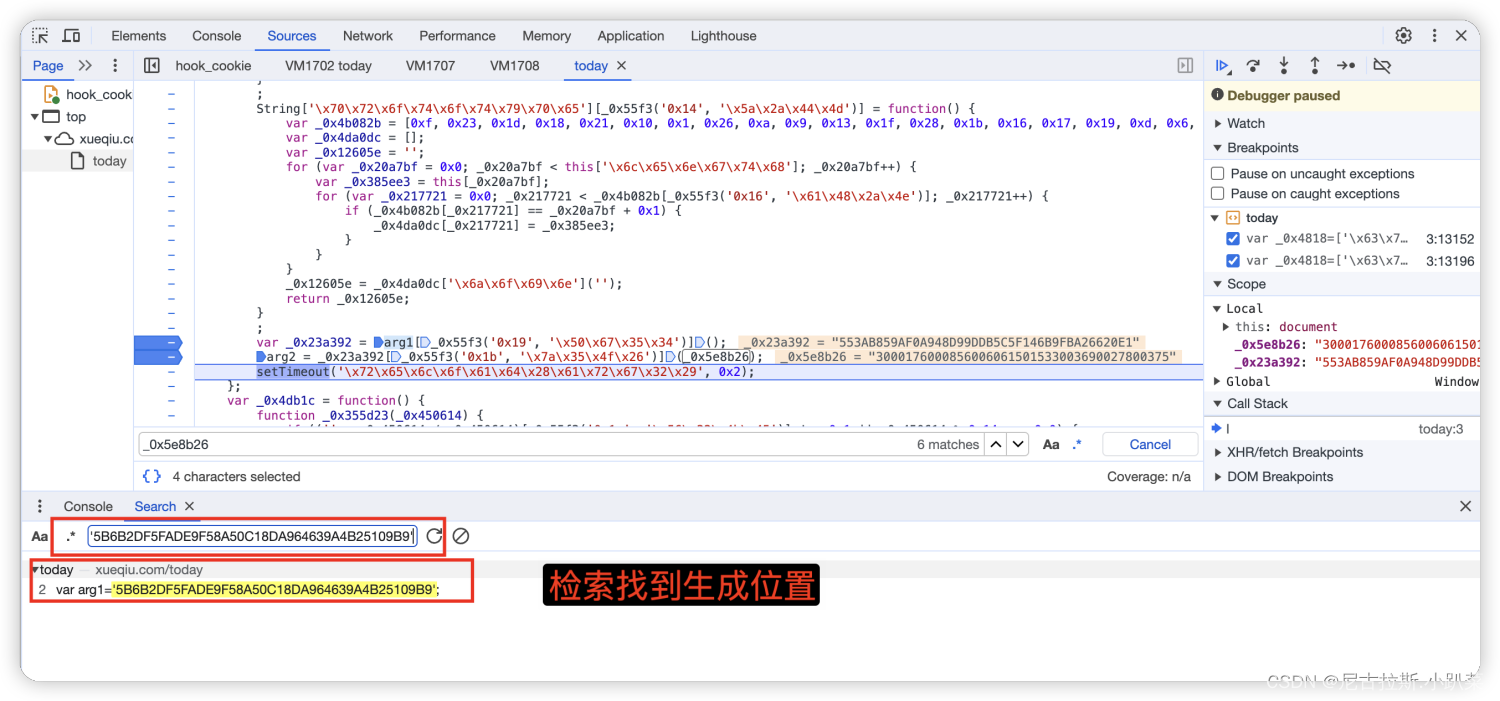
发现就是一变量 实际上就是咱们对gettoday1发请求的js代码中的值。
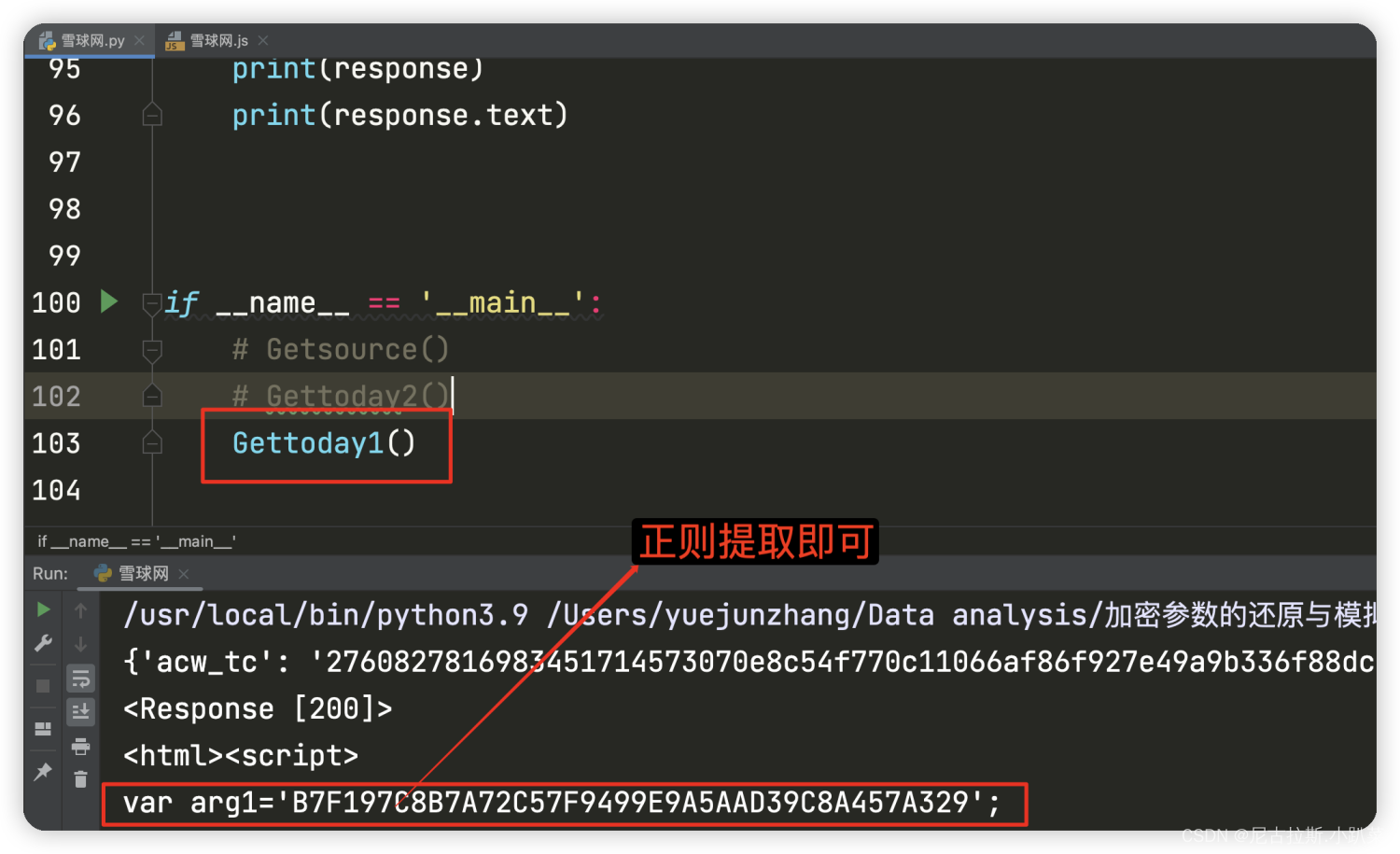
获取arg1的值
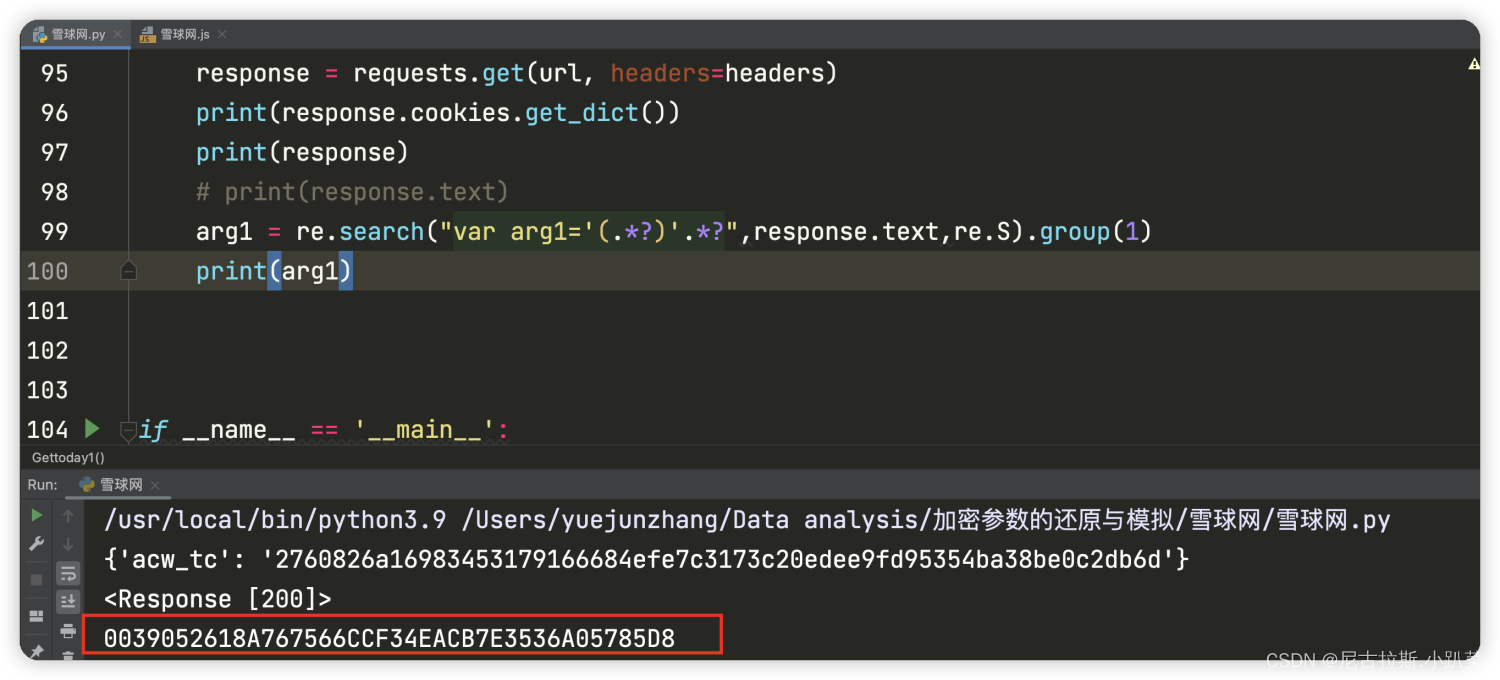
8、重构python代码 进行逆向还原
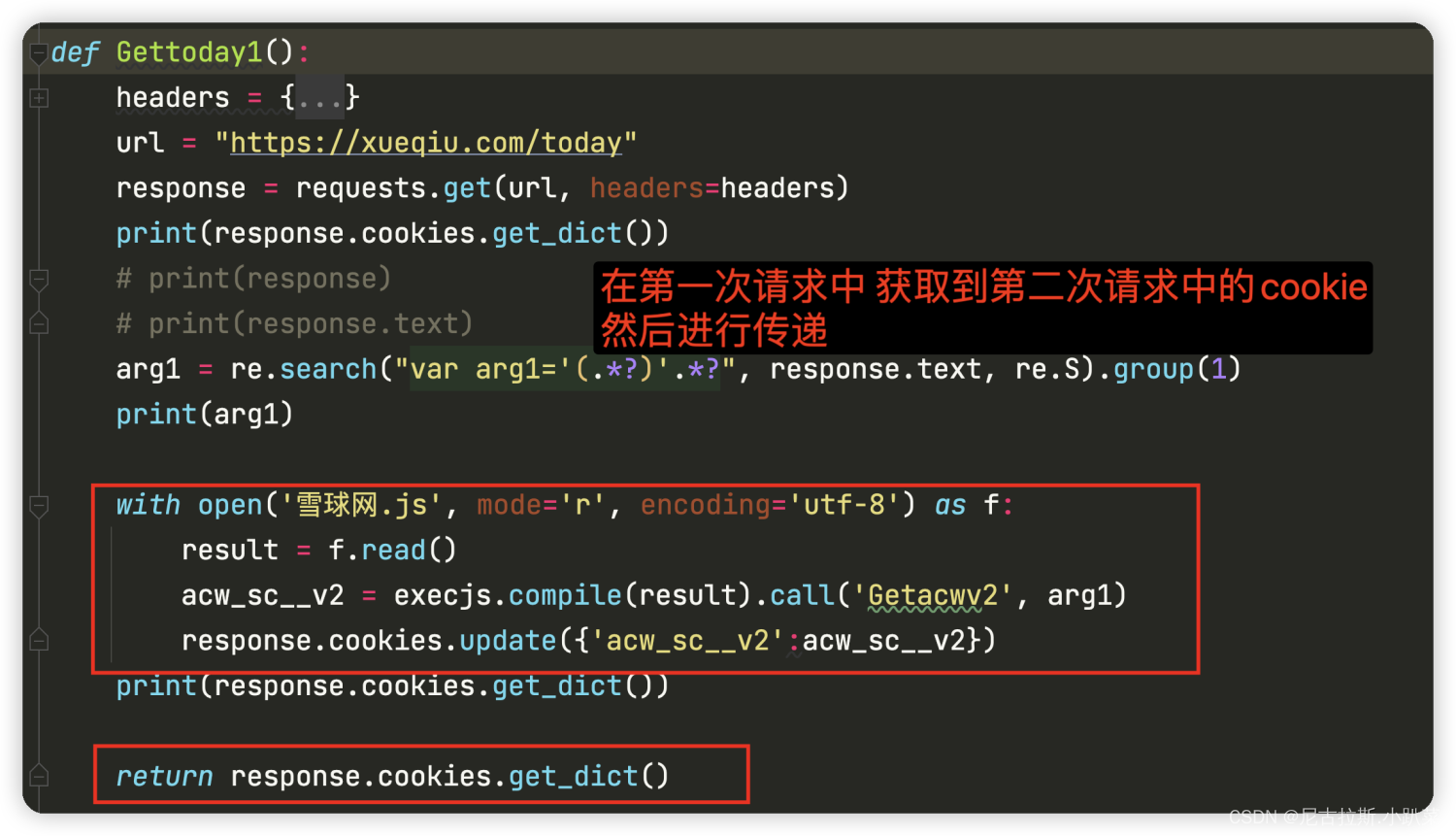
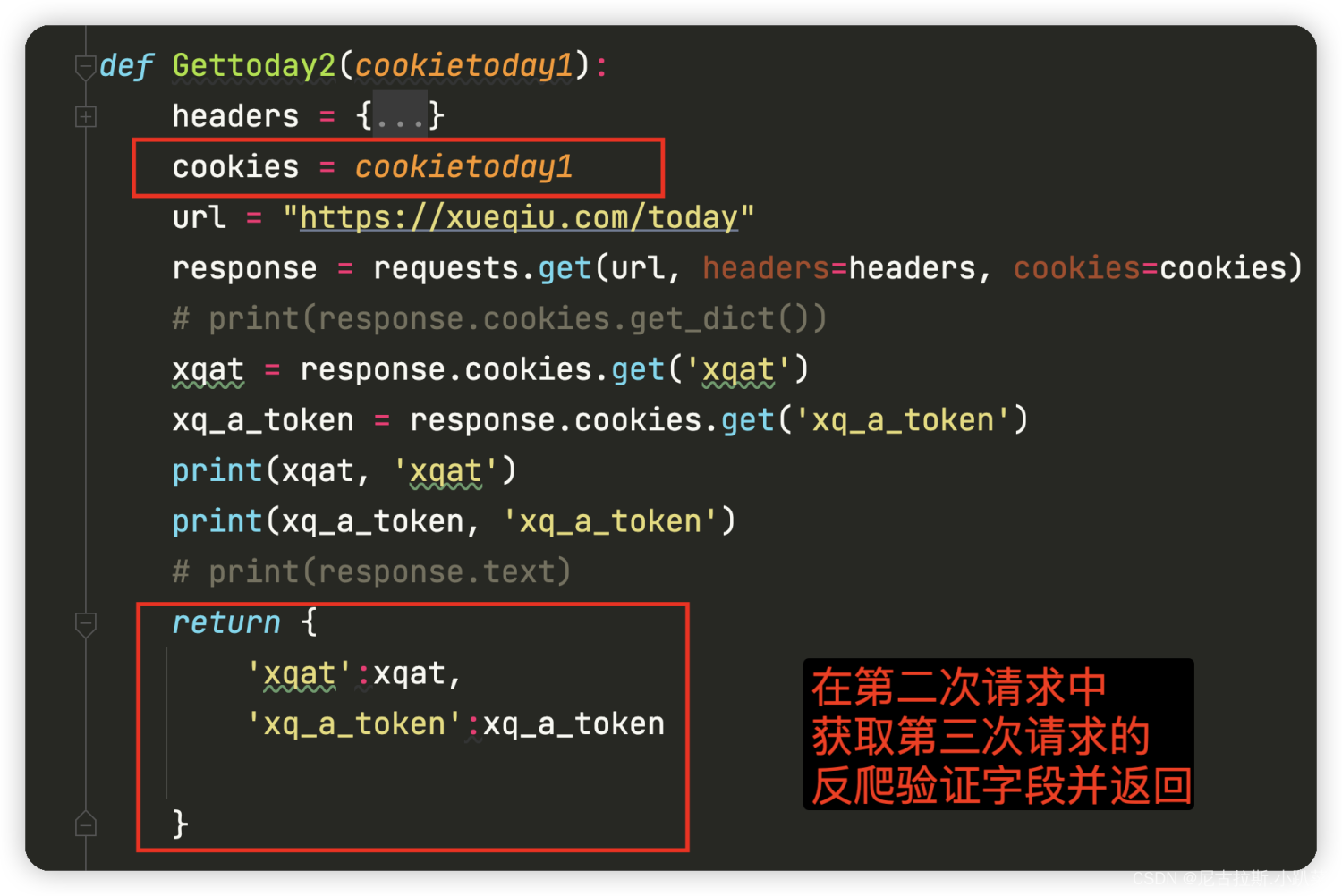
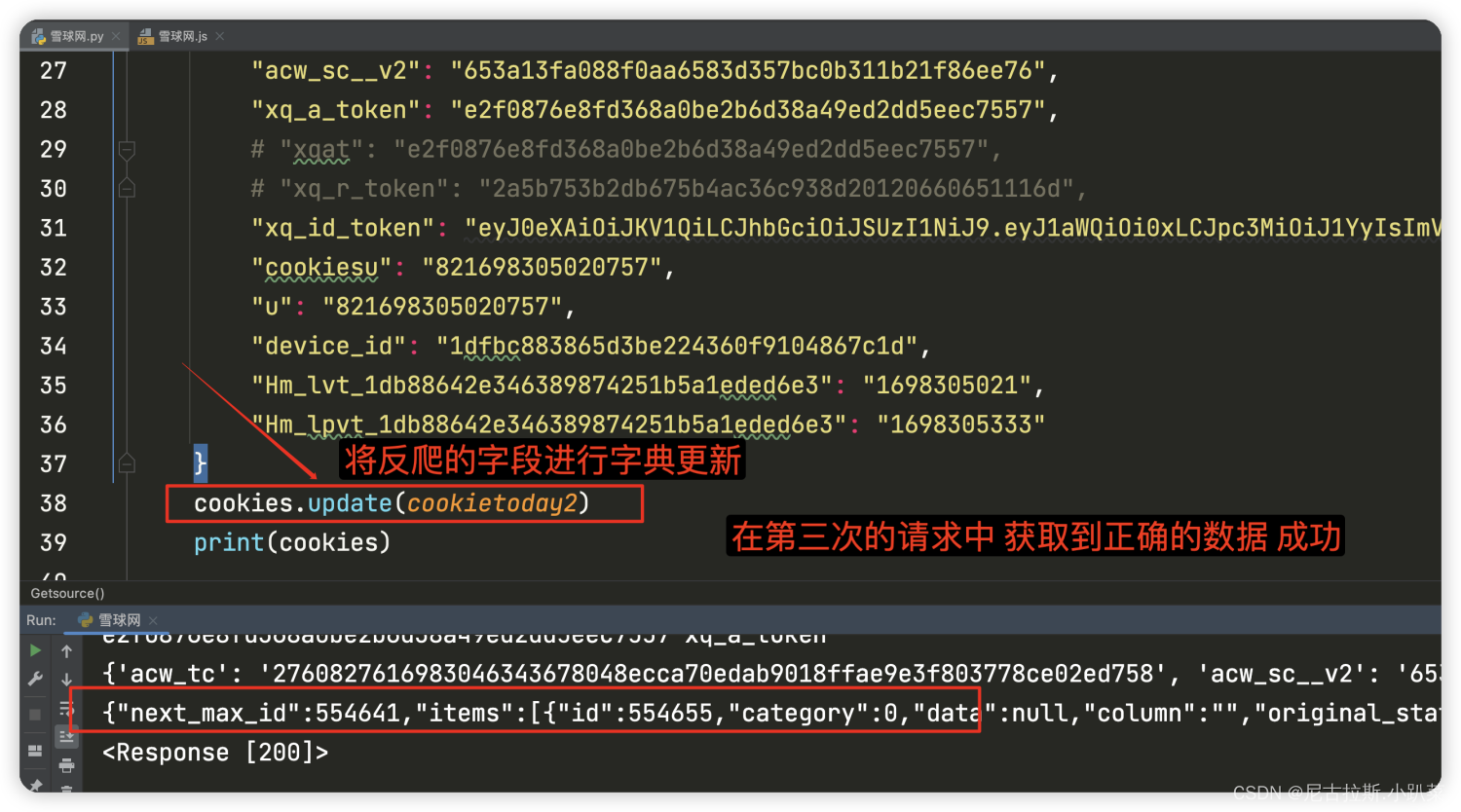
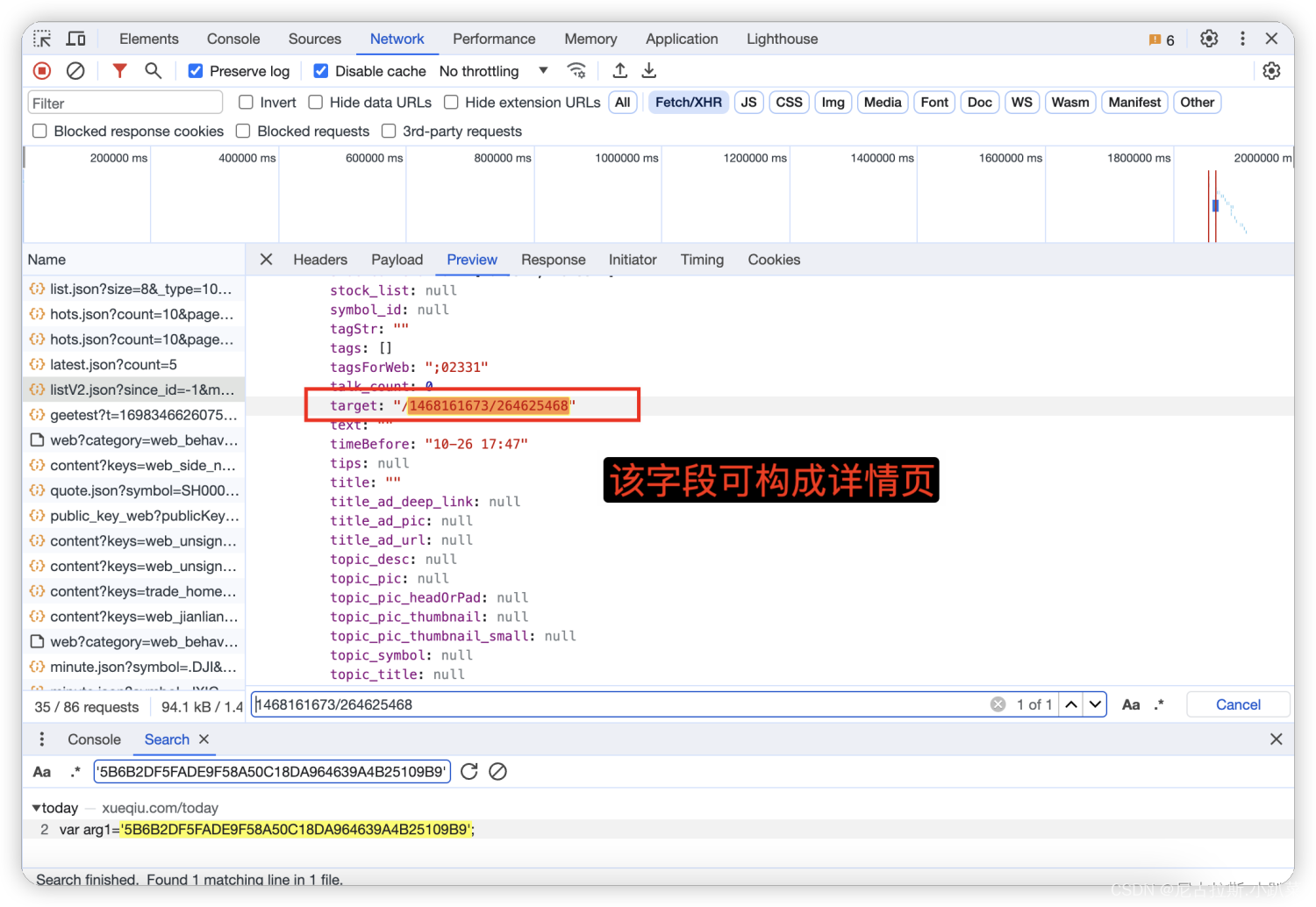
9、对获取json数据进行解析提取 提取出目标字段
解析这一块就很简单我就不说了 提醒一点 如果要在详情页中获取数据 找这个参数即可
这篇关于cookie反爬实战案例四(acw_sc__v2 + 无限debugger处理)的文章就介绍到这儿,希望我们推荐的文章对编程师们有所帮助!






