本文主要是介绍SWAN之ikev2协议multi-auth-rsa-eap-sim-id配置测试,希望对大家解决编程问题提供一定的参考价值,需要的开发者们随着小编来一起学习吧!
本测试主要验证多重认证功能,远程用户carol,dave与网关mooon建立连接时,首先使用IKE RSA签名和相关证书进行认证;完成之后,再进行EAP-SIM认证。在测试中,由alice主机充当radius服务器,对于carol,使用文件/etc/ipsec.d/triplets.dat中的数据模拟物理SIM卡。网关moon负责转发所有的EAP消息到Radius服务器,alice同样使用定义好的triplets.dat文件模拟SIM认证数据。本次测试拓扑如下:
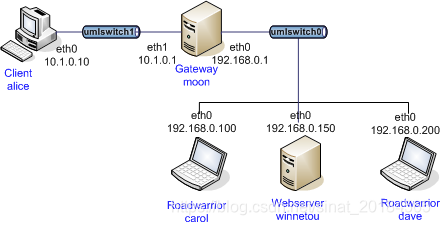
主机配置
carol的配置文件:ikev2/multi-auth-rsa-eap-sim-id/hosts/carol/etc/ipsec.conf,内容如下。这里这里了多重验证,首先leftauth指定了pubkey验证,再者leftauth2字段指定了EAP验证,eap_identity字段指定esp标识:228060123456001,leftid2字段指定二次验证使用的ID:228060123456001@strongswan.org。
conn homeleft=PH_IP_CAROLleftfirewall=yesleftauth=pubkeyleftid=carol@strongswan.orgleftcert=carolCert.pemleftauth2=eapleftid2=228060123456001@strongswan.orgeap_identity=228060123456001right=PH_IP_MOONrightsubnet=10.1.0.0/16rightauth=pubkeyrightid=@moon.strongswan.orgauto=add
carol的配置文件:ikev2/mult-auth-rsa-eap-sim-id/hosts/carol/etc/ipsec.d/triplets.dat 用于模拟SIM卡。第一个字段为用户ID;第二个字段为RAND,由基站发送给移动端(手机)的128bit的随机数;第三个字段SRES,为终端发送给基站的32bit长响应值;最后字段Kc,为64bit长的秘钥。
228060123456001,30000000000000000000000000000000,30112233,305566778899AABB
228060123456001,31000000000000000000000000000000,31112233,315566778899AABB
228060123456001,32000000000000000000000000000000,32112233,325566778899AABB
carol的配置文件:ikev2/multi-auth-rsa-eap-sim-id/hosts/carol/etc/strongswan.conf,内容如下。这里加载本次测试需要使用到的eap-sim,eap-sim-file和eap-identity等插件。
# /etc/strongswan.conf - strongSwan configuration filecharon {load = random nonce aes sha1 sha2 md5 pem pkcs1 curve25519 gmp x509 curl revocation hmac stroke kernel-netlink socket-default fips-prf eap-sim eap-sim-file eap-identity updown
}
主机dave的配置与carol基本相同,区别在于,在ipsec.conf配置文件中,dave的eap_identify值为228060123456002,leftid2等于228060123456002@strongswan.org。另外,两者的triplets.dat文件不同,dave的内容如下:
228060123456002,33000000000000000000000000000000,33112244,335566778899AABB
228060123456002,34000000000000000000000000000000,34112244,345566778899AABB
228060123456002,35000000000000000000000000000000,35112244,355566778899AABB
网关配置
moon网关的配置文件:ikev2/multi-auth-rsa-eap-sim-id/hosts/moon/etc/ipsec.conf,内容如下。注意其rightauth2字段指定了值eap-radius,将对远程用户进行额外的eap认证。
conn rw-multleft=PH_IP_MOONleftsubnet=10.1.0.0/16leftfirewall=yesleftauth=pubkeyleftid=@moon.strongswan.orgleftcert=moonCert.pemright=%anyrightauth=pubkeyrightid=*@strongswan.orgrightauth2=eap-radiuseap_identity=%anyauto=add
moon网关的配置文件:ikev2/multi-auth-rsa-eap-sim-id/hosts/moon/etc/strongswan.conf,内容如下。此处需要加载测试使用到的eap-radius和eap-identity等插件。另外,在eap-radius段中配置radius服务器的地址及访问秘钥。
charon {load = random nonce aes md5 sha1 sha2 pem pkcs1 curve25519 gmp x509 curl revocation hmac stroke kernel-netlink socket-default fips-prf eap-radius eap-identity updownplugins {eap-radius {secret = gv6URkSsserver = PH_IP_ALICE}}
}
Radius服务器
本次测试使用alice主机作为radius服务器,其地址为10.1.0.10。配置文件ikev2/mult-auth-rsa-eap-sim-id/hosts/alice/etc/freeradius/users 中设置了两个SIM认证的用户:228060123456001和228060123456002,分别对应carol和dave。
对于dave主机,其EAP-Sim-SRES1/2/3的值为:0x33112233、0x34112233和0x35112233,与dave主机的配置文件triplets.dat中定义的值都不相同,其认证将失败。
228060123456001 EAP-Type := SIM, EAP-Sim-RAND1 := 0x30000000000000000000000000000000, EAP-Sim-SRES1 := 0x30112233, EAP-Sim-KC1 := 0x305566778899AABB, EAP-Sim-RAND2 := 0x31000000000000000000000000000000, EAP-Sim-SRES2 := 0x31112233, EAP-Sim-KC2 := 0x315566778899AABB, EAP-Sim-RAND3 := 0x32000000000000000000000000000000, EAP-Sim-SRES3 := 0x32112233, EAP-Sim-KC3 := 0x325566778899AABB
228060123456002 EAP-Type := SIM, EAP-Sim-RAND1 := 0x33000000000000000000000000000000, EAP-Sim-SRES1 := 0x33112233, EAP-Sim-KC1 := 0x335566778899AABB, EAP-Sim-RAND2 := 0x34000000000000000000000000000000, EAP-Sim-SRES2 := 0x34112233, EAP-Sim-KC2 := 0x345566778899AABB, EAP-Sim-RAND3 := 0x35000000000000000000000000000000, EAP-Sim-SRES3 := 0x35112233, EAP-Sim-KC3 := 0x355566778899AABB
测试准备阶段
配置文件:ikev2/multi-auth-rsa-eap-sim-id/pretest.dat,内容为通常的ipsec连接的启动语句。另外需要注意的是启用alice主机上的freeradius进程,用作radius服务器。
alice::freeradius
测试阶段
配置文件:ikev2/multi-auth-rsa-eap-sim-id/evaltest.dat内容如下。在确认carol主机和moon网关连接建立之后,检查strongswan进程日志中的连接信息,确认RSA验证和EAP-SIM验证都成功完成。然后在主机carol上使用ping命令测试到alice主机的连通性。
moon:: cat /var/log/daemon.log::parsed IKE_AUTH request.*N(AUTH_FOLLOWS)::YES
moon:: cat /var/log/daemon.log::authentication of .*carol@strongswan.org.* with RSA.* successful::YES
carol::cat /var/log/daemon.log::authentication of .*moon.strongswan.org.* with RSA.* successful::YES
carol::cat /var/log/daemon.log::server requested EAP_SIM authentication::YES
moon:: cat /var/log/daemon.log::received EAP identity .*228060123456001::YES
moon:: cat /var/log/daemon.log::authentication of .*228060123456001@strongswan.org.* with EAP successful::YES
moon:: ipsec status 2> /dev/null::rw-mult.*ESTABLISHED.*228060123456001@strongswan.org::YES
carol::ipsec status 2> /dev/null::home.*ESTABLISHED.*228060123456001@strongswan.org::YES
carol::ping -c 1 PH_IP_ALICE::64 bytes from PH_IP_ALICE: icmp_.eq=1::YES
以下为moon网关上strongswan进程日志,moon接收到了carol在IKE_AUTH报文中发送的AUTH_FOLLOWS载荷,表示支持多重认证,第一重RSA认证成功。
moon charon: 11[ENC] parsed IKE_AUTH request 1 [ IDi CERT N(INIT_CONTACT) CERTREQ IDr AUTH SA TSi TSr N(MOBIKE_SUP) N(ADD_6_ADDR) N(MULT_AUTH) N(EAP_ONLY) N(MSG_ID_SYN_SUP) N(AUTH_FOLLOWS) ]moon charon: 11[IKE] received cert request for "C=CH, O=strongSwan Project, CN=strongSwan Root CA"moon charon: 11[IKE] received end entity cert "C=CH, O=strongSwan Project, OU=Research, CN=carol@strongswan.org"moon charon: 11[CFG] certificate status is goodmoon charon: 11[CFG] reached self-signed root ca with a path length of 0moon charon: 11[IKE] authentication of 'carol@strongswan.org' with RSA_EMSA_PKCS1_SHA2_256 successful
此后,moon网关又接收到carol发送的第二次认证的报文,其中仅包含IDi,其值为ipsec.conf文件中使用leftid2配置的228060123456001@strongswan.org。之后,moon网关向carol请求了eap_identity信息,carol回复了值228060123456001(IKE_AUTH request 3消息)。之后moon网关开始在radius服务器alice和carol用户之后转发EAP/Radius认证报文,认证成功之后,moon回复carol主机完整的建立子连接的报文。
moon charon: 12[NET] received packet: from 192.168.0.100[4500] to 192.168.0.1[4500] (112 bytes)
moon charon: 12[ENC] parsed IKE_AUTH request 2 [ IDi ]
moon charon: 12[IKE] initiating EAP_IDENTITY method (id 0x00)
moon charon: 12[ENC] generating IKE_AUTH response 2 [ EAP/REQ/ID ]
moon charon: 13[ENC] parsed IKE_AUTH request 3 [ EAP/RES/ID ]
moon charon: 13[IKE] received EAP identity '228060123456001'
moon charon: 13[CFG] sending RADIUS Access-Request to server '10.1.0.10'
moon charon: 13[CFG] received RADIUS Access-Challenge from server '10.1.0.10'
moon charon: 13[IKE] initiating EAP_SIM method (id 0xBC)
moon charon: 13[ENC] generating IKE_AUTH response 3 [ EAP/REQ/SIM ]
moon charon: 14[ENC] parsed IKE_AUTH request 4 [ EAP/RES/SIM ]
moon charon: 14[CFG] sending RADIUS Access-Request to server '10.1.0.10'
moon charon: 14[CFG] received RADIUS Access-Challenge from server '10.1.0.10'
moon charon: 14[ENC] generating IKE_AUTH response 4 [ EAP/REQ/SIM ]
moon charon: 15[ENC] parsed IKE_AUTH request 5 [ EAP/RES/SIM ]
moon charon: 15[CFG] sending RADIUS Access-Request to server '10.1.0.10'
moon charon: 15[CFG] received RADIUS Access-Accept from server '10.1.0.10'
moon charon: 15[IKE] RADIUS authentication of '228060123456001' successful
moon charon: 15[IKE] EAP method EAP_SIM succeeded, MSK established
moon charon: 15[ENC] generating IKE_AUTH response 5 [ EAP/SUCC ]
moon charon: 16[ENC] parsed IKE_AUTH request 6 [ AUTH ]
moon charon: 16[IKE] authentication of '228060123456001@strongswan.org' with EAP successful
moon charon: 16[IKE] authentication of 'moon.strongswan.org' (myself) with EAP
moon charon: 16[IKE] IKE_SA rw-mult[1] established between 192.168.0.1[moon.strongswan.org]...192.168.0.100[228060123456001@strongswan.org]
认证报文交互流程如下,其与以上的moon日志相对应:
|---------| |---------| |---------|| carol | | moon | | alice ||---------| |---------| |---------|| | || | |IKE_SA_INIT |-------------------------------------->| |MID=00 |<--------------------------------------| || | || ANOTHER_AUTH_FOLLOWS | |IKE_AUTH |---- |-------------------------------------->| |MID=01 |---- |<--------------------------------------| || no TS SA payload | || | || IDi=228060123456001@strongswan.org | |IKE_AUTH |---- |-------------------------------------->| |MID=02 | | (EAP req in ISAKMP) identity | ||---- |<--------------------------------------| || | || (EAP resp)(id 228060123456001) | Radius Access-Request(id=149) ||---- |-------------------------------------->| (IDi | CSID = 192.168.1.100) || | |------------------------------------------->|MID=03 | | | Access-Challenge(id=149) || | | (VERSION_LIST & FULLAUTH_ID) || | EAP Req (VERSION_LIST & FULLAUTH_ID) |<-------------------------------------------||---- |<--------------------------------------| || | || EAP Resp (SELECTED_VERSION(0001) & | || IDENTITY 228060123456001) | Access-Request(150)(SELECTED_VERSION(0001) ||---- |-------------------------------------->| & IDENTITY 228060123456001) || | |------------------------------------------->|MID=04 | | | Radius Access-Challenge(id=150) | RAND值:| | | (AT_RAND & AT_MAC) | EAP-Sim-RAND1/2/3| | EAP Req (AT_RAND & AT_MAC) |<-------------------------------------------||---- |<--------------------------------------| || | || | || EAP Resp (AT_MAC) | ||---- |-------------------------------------->| Access-Request(151) (AT_MAC) || | |------------------------------------------->|MID=05 | | | Access-Accept(151) || | EAP Success |<-------------------------------------------||---- |<--------------------------------------| || | || | || Req (AUTH Payload) | ||---- |-------------------------------------->| |MID=06 | | Resp (AUTH/SA/TSi/TSr/...) | ||---- |<--------------------------------------| || | |
主机carol上的strongswan进程日志,反应了其交互过程中的处理流程,日志中request或者response字符串后面的数字表示MID值:
carol charon: 13[ENC] generating IKE_AUTH request 2 [ IDi ]
carol charon: 13[NET] sending packet: from 192.168.0.100[4500] to 192.168.0.1[4500] (112 bytes)
carol charon: 15[NET] received packet: from 192.168.0.1[4500] to 192.168.0.100[4500] (80 bytes)
carol charon: 15[ENC] parsed IKE_AUTH response 2 [ EAP/REQ/ID ]
carol charon: 15[IKE] server requested EAP_IDENTITY (id 0x00), sending '228060123456001'
carol charon: 15[ENC] generating IKE_AUTH request 3 [ EAP/RES/ID ]
carol charon: 15[NET] sending packet: from 192.168.0.100[4500] to 192.168.0.1[4500] (96 bytes)
carol charon: 16[NET] received packet: from 192.168.0.1[4500] to 192.168.0.100[4500] (96 bytes)
carol charon: 16[ENC] parsed IKE_AUTH response 3 [ EAP/REQ/SIM ]
carol charon: 16[IKE] server requested EAP_SIM authentication (id 0xBC)
carol charon: 16[ENC] generating IKE_AUTH request 4 [ EAP/RES/SIM ]
carol charon: 16[NET] sending packet: from 192.168.0.100[4500] to 192.168.0.1[4500] (128 bytes)
carol charon: 05[NET] received packet: from 192.168.0.1[4500] to 192.168.0.100[4500] (160 bytes)
carol charon: 05[ENC] parsed IKE_AUTH response 4 [ EAP/REQ/SIM ]
carol charon: 05[ENC] generating IKE_AUTH request 5 [ EAP/RES/SIM ]
carol charon: 05[NET] sending packet: from 192.168.0.100[4500] to 192.168.0.1[4500] (112 bytes)
carol charon: 06[NET] received packet: from 192.168.0.1[4500] to 192.168.0.100[4500] (80 bytes)
carol charon: 06[ENC] parsed IKE_AUTH response 5 [ EAP/SUCC ]
carol charon: 06[IKE] EAP method EAP_SIM succeeded, MSK established
carol charon: 06[IKE] authentication of '228060123456001@strongswan.org' (myself) with EAP
carol charon: 06[ENC] generating IKE_AUTH request 6 [ AUTH ]
carol charon: 06[NET] sending packet: from 192.168.0.100[4500] to 192.168.0.1[4500] (112 bytes)
carol charon: 08[NET] received packet: from 192.168.0.1[4500] to 192.168.0.100[4500] (288 bytes)
carol charon: 08[ENC] parsed IKE_AUTH response 6 [ AUTH SA TSi TSr N(AUTH_LFT) N(MOBIKE_SUP) N(ADD_4_ADDR) N(ADD_6_ADDR) N(ADD_6_ADDR) ]
carol charon: 08[IKE] authentication of 'moon.strongswan.org' with EAP successful
carol charon: 08[IKE] IKE_SA home[1] established between 192.168.0.100[228060123456001@strongswan.org]...192.168.0.1[moon.strongswan.org]
以下为tcpdump抓到的交互流程报文:




