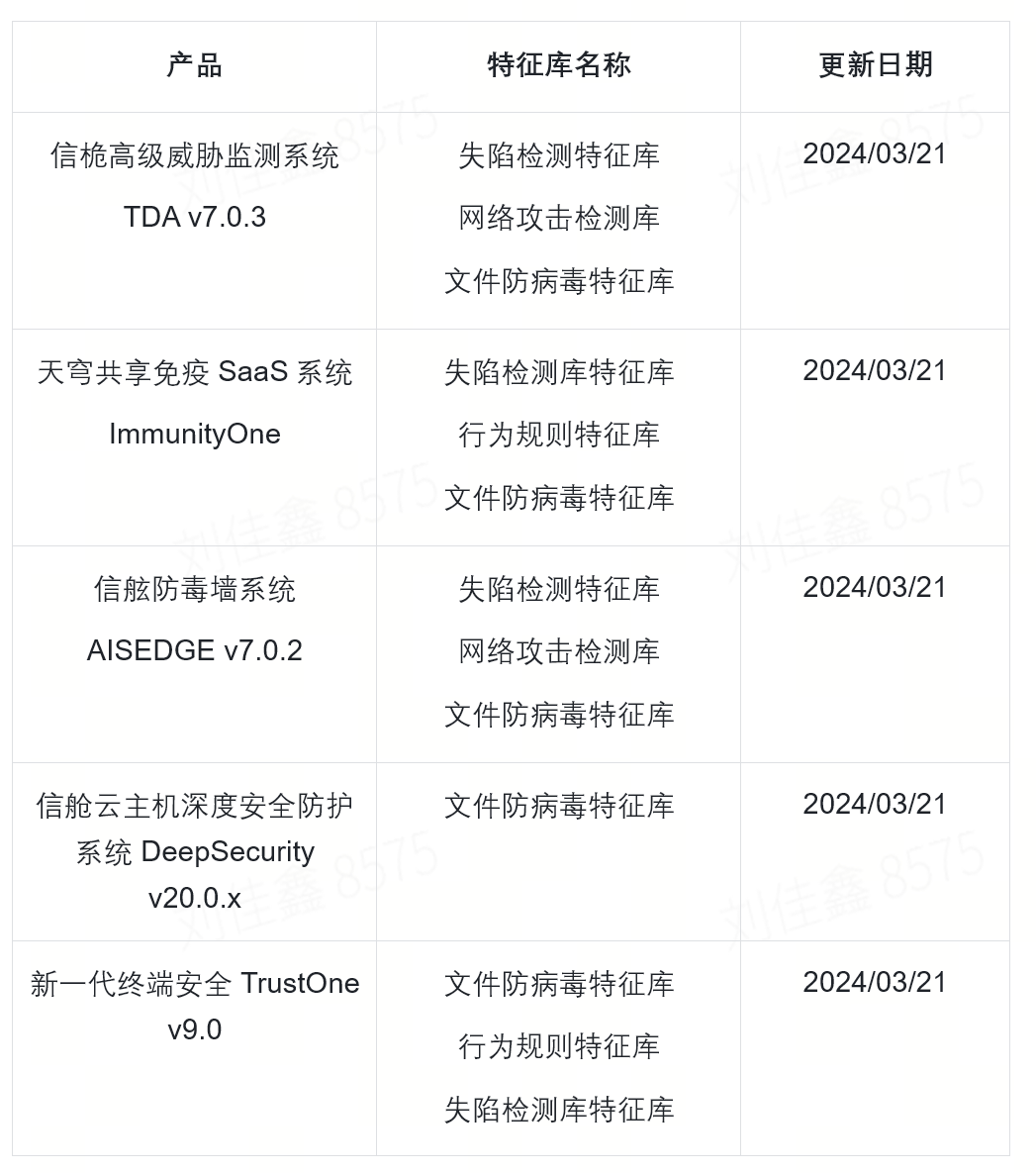
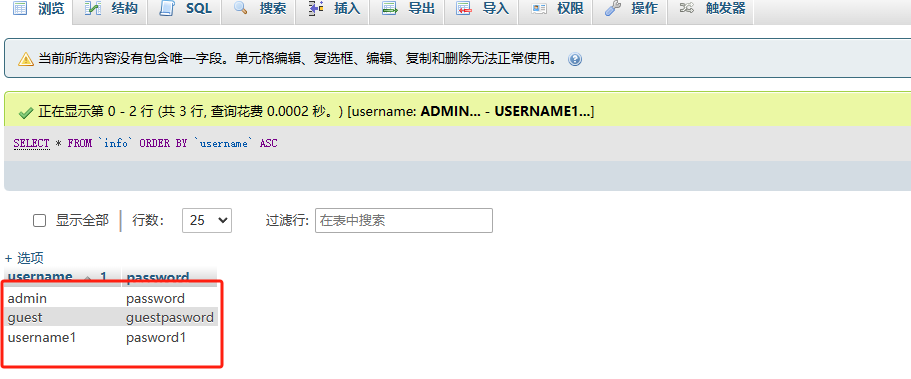
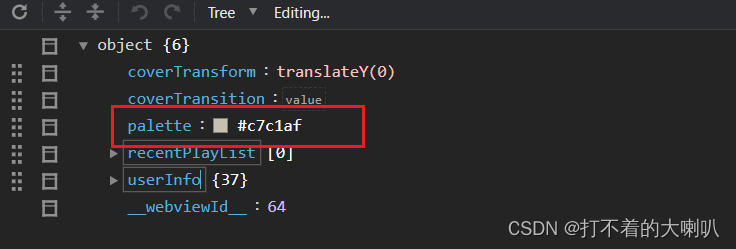
窃取专题
【论文阅读】一种针对多核神经网络处理器的窃取攻击(2020)
摘要 攻击者可以通过侧信道信息(Side-channel)完成模型窃取攻击[17]. [17] Hua W Z, Zhang Z R, Suh G E. Reverse Engineering Convolutional Neural Networks through Side-channel Information Leaks[C]. 2018 55th ACM/ESDA/IEEE Des
某视频云平台存在未授权窃取用户凭据漏洞
我和你一样,历经破碎、痛苦的生活,却未垮掉,每一日都从承受的苦难中,再一次将额头浸入光明 漏洞详情: 某视频云平台存在未授权访问漏洞,攻击者可以直接访问平台的API接口文档,从而获取系统的API接口造成信息泄露。 漏洞实战: 用户账户密码信息泄露:构造payload,访问漏洞url https://xxx/api/v1/userlist?pageindex=0&pagesize=10
【开源实验】模型窃取(KnockoffNet)
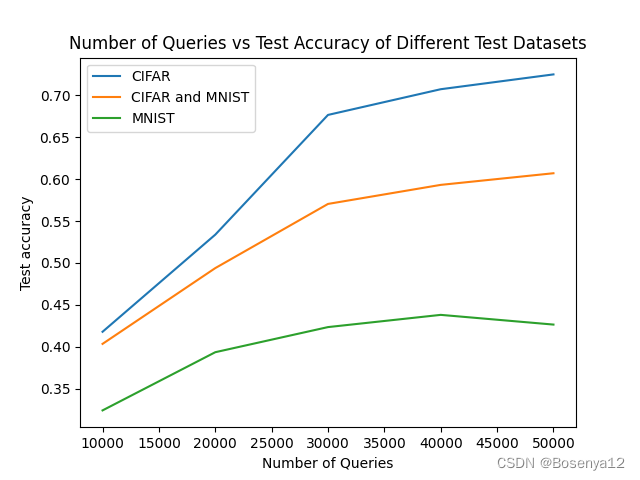
简介 使用KnockoffNet方法对预训练的Resnet50模型进行模型窃取攻击(model stealing attack) 实验设置 数据集(dataset):CIFAR、MNIST 预训练模型(pretrained model):Resnet50 受害者模型(victim model):Resnet50 窃取方法(stealing method):KnockoffNet 查询次数:1
实战分析:如何窃取用户Cookie并保存到远程服务器
实战分析:如何窃取用户Cookie并保存到远程服务器 引言 在网络安全领域,Cookie是Web应用中用于识别用户身份和保存用户状态的重要机制。不幸的是,Cookie也成为了攻击者的目标,他们通过跨站脚本(XSS)攻击来窃取用户的Cookie。本文将详细分析攻击者如何实施窃取用户Cookie的实战步骤,以及网站管理员和用户如何采取有效措施进行防御。 Cookie窃取实战步骤 寻找XSS漏洞
多家企业机密数据遭Lockbit3.0窃取,亚信安全发布《勒索家族和勒索事件监控报告》
本周态势快速感知 本周全球共监测到勒索事件87起,与上周相比勒索事件大幅下降。美国依旧为受勒索攻击最严重的国家,占比45%。 本周Cactus是影响最严重的勒索家族,Lockbit3.0和Bianlian恶意家族紧随其后,从整体上看Lockbit3.0依旧是影响最严重的勒索家族,近期Lockbit3.0攻击趋势有所减缓,仍需注意防范。 本周Lockbit3.0将eurosko.
windows本地提权--令牌窃取烂土豆UAC
免责声明:本文仅做技术交流与学习,请知法守法,不要乱搞破坏等等... 目录 一.令牌窃取 操作: 1-生成-->上传后门后,让msf上线 2-执行命令 二.烂土豆(MS16-075) 操作: 1-先让MSF上线 2-上传烂土豆 3-执行命令 三.UAC(用户账户控制) 1-MSF模块提权 2-UACME 项目(yyds) 本地--->system
广告sdk窃取用户隐私:你家的App被下架了吗?
来自新浪新闻的消息,因为涉及偷取用户的额外信息,苹果下架了包括爸爸去哪儿,找你妹等256个App,具体为什么下架呢?是因为这些App嵌入了有米的广告sdk,sdk说白了就是一段代码,用来增加开发者的收入的。由此可以看出像爸爸去哪儿的App也缺钱啊,也需要加广告sdk,但是利用App的用户量赚取广告费,本是很正常的事情,但是这个有米广告sdk不仅为用户显示广告,还偷偷的获取了用户的其他信息,具体是
网络钓鱼升级 Darcula如何窃取用户信息
近日,网络安全领域一种名为 “Darcula” 的网络钓鱼欺诈(PhaaS)悄然兴起。这种新型钓鱼方式不同于传统的手段,它巧妙地利用了谷歌信息和 iMessage 的富通信服务(RCS),成为了网络犯罪分子的新手段。Darcula 不仅仅是一种简单的网络钓鱼工具,它采用了现代技术,为攻击者提供了持续更新等新功能。 一、Darcula:新兴的网络钓鱼 根据反网络钓鱼工作组(APWG)的报告,全球
【Android病毒分析报告】 - ZooTiger “集恶意推广、隐私窃取、恶意吸费于一体”
本文章由Jack_Jia编写,转载请注明出处。 文章链接:http://blog.csdn.net/jiazhijun/article/details/11772379 作者:Jack_Jia 邮箱: 309zhijun@163.com 近期百度安全实验室发现一款ZooTiger新病毒,该病毒集吸费、隐私窃取、恶意推广功能与一身,该病毒目前已感染大批第三
1.5T数据惨遭Lockbit3.0窃取,亚信安全发布《勒索家族和勒索事件监控报告》
本周态势快速感知 本周全球共监测到勒索事件93起,近三周攻击数量呈现持平状态。 本周Lockbit3.0是影响最严重的勒索家族,Blacksuit和Ransomhub恶意家族紧随其后,从整体上看Lockbit3.0依旧是影响最严重的勒索家族,需要注意防范。 本周连锁餐厅加盟商RMH Franchise公司遭受了来自Lockbit3.0恶意家族的攻击,勒索软件团伙总共窃取了该公司
【安全通知】NPM遭遇供应链投毒攻击窃取K8S集群凭证
文|腾讯洋葱反入侵系统 七夜、xnianq、柯南 近日,腾讯洋葱反入侵系统检测发现 NPM官方仓库被上传了radar-cms 恶意包,并通知官方仓库下架处理。由于国内开源镜像站均同步于NPM官方仓库,所以该问题不仅会通过官方仓库,还可能通过各个开源镜像站影响广大用户。 腾讯安全应急响应中心(TSRC)秉承共建安全生态的原则,在此建议各开源镜像站以及对开源镜像站有依赖的组织和公司,请尽快自查处理
针对中国用户的恶意链接广泛存在;K8s高危漏洞紧急修复;微软证实俄黑客窃取源代码;Google大模型易受攻击 | 安全周报 0315
1. 针对中国用户的恶意广告:伪装成Notepad++和VNote安装程序 在百度等搜索引擎上寻找Notepad++和VNote等正版软件的中国用户正成为恶意广告和虚假链接的目标,这些广告和链接会分发这些软件的木马版本,并最终部署基于Golang实现的Cobalt Strike的Geacon。 卡巴斯基研究员谢尔盖·普赞说:“在notepad++搜索中发现的恶意网站是通过一个广告区块进行分
讨论:支付宝Android版究竟有没有窃取用户隐私?
这两日,支付宝身陷“隐私囹圄”,事件的起因来源于Twitter上一位昵称为“typcn”的用户,这位用户首先引人注目的一点就是据多家科技领域蓝V说“曾经曝光‘12306泄密事件’、上过CCTV”,但其已在微博上辟谣,表示:“我什么时候上过CCTV。。。只是某个网页被当作Example展示了吧。。。在twitter上发个质疑就被炒这么火了”。 然后,我们再来看一下整个事件的来龙去脉: 2月2
时代华纳表示旗下32万用户信息被钓鱼窃取
1月8日消息,据路透社报道,时代华纳有线电视周三晚表示,旗下约有32万用户的邮件和密码信息已被黑客窃取。 这些邮件和密码信息很有可能是透过钓鱼网欺骗行为获得,同时也可能是保存了时代华纳用户数据的第三方合作商信息泄露所致。 目前调查仍在进行,尽管没有确定信息泄露的最终原因,但时代华纳并不认为有迹象显示其内部系统出现了漏洞。 时代华纳发言人表示,公司已经于近期将问题上报给联邦调查局,提供信息包括了
《火箭联盟》游戏迷要小心了!已有攻击者滥用HTTP路径正常化和缓存来窃取你的账户了
《火箭联盟》是一款由美国独立游戏工作室Psyonix开发的网络游戏。该游戏一经推出即在海内外获得好评无数,玩家数屡创新高,截至目前全球玩家数超过3000万; 由于在过去的几年中,漏洞披露和漏洞赏金计划的使用已大大增加。现在,奇热这些计划几乎可以很容易地报告日常用户的安全漏洞,并快速发布关于安全报告处理的信息。 在《火箭联盟》上寻找到的漏洞 当黑客破解游戏时,他们总是首先关注的是游戏在网络
攻击者伪装成思科的“关键更新”电子邮件进行网络钓鱼攻击窃取WebEx在线会议平台凭据
伪装成思科“关键安全咨询”的电子邮件实际上是网络钓鱼活动的一部分,旨在窃取受害者的WebEx凭据。 日前,有一个网络钓鱼活动通过回收的思科安全公告来警告思科用户,称用户使用的思科系统有严重的漏洞存在,并敦促用户进行所谓的“更新”,而其实质则是窃取受害者用于Cisco WebEx Web会议平台的凭据。 这个钓鱼活动是打算利用当前远程工作的浪潮来进行。受冠状病毒肆虐的影响,远程工作的劳动者已
账户名密码是怎样被窃取的,简单模拟攻击者权限维持流程。
前言 在我们进行渗透测试的时候,常常需要进行权限维持,常见的 Javascript窃取用户凭证是一种常见的攻击手法。之前我们可能学习过钓鱼网页的使用,如果我们通过渗透测试进入到用户的服务器,其实也可以通过在网页中植入Javascript代码的方式来达到权限维持的效果。本篇文章通过分析Javascript用户凭证窃取,来分析如何进行权限维持。 正文 凭证劫持流程 “凭证劫持”(Cr
微信小程序的图片色彩分析,解决画布网络图片报错问题,窃取网络图片的主色调
1、安装 Mini App Color Thief 包 包括下载包,简单使用都有,之前写了,这里就不写了 网址:微信小程序的图片色彩分析,窃取主色调,调色板-CSDN博客 2、 问题和解决方案 问题:由于我们的窃取图片的是需要画布的,我需要使用网络图片去用画布时,微信小程序会报错,最后发现,需要本地图片才行,用网络图片会出问题解决方案:我们使用wx.downloadFile去下载该
百度搜索出台“天网算法”严厉打击窃取用户信息行为
在这个互联网时代,我们几乎每天都会游览一些网页。但游览一个网站,我们的信息如QQ、手机号,就会被网站主抓取,然后就会有客户主动联系。虽然看起来挺方便,但是却严重侵犯了我们的隐私。我们的隐私有多少是自己说了算? 近期,百度网页搜索发现部分站点存在盗取用户隐私的行为,主要表现为网页嵌恶意代码,用于盗取网民的QQ号、联系电话。而许多网民却误认为这是百度所为。为此,百度网
FBI紧急警告:黑客利用开源SonarQube实例窃取政府和企业源代码
聚焦源代码安全,网罗国内外最新资讯! 编译:奇安信代码卫士团队 美国联邦调查局 (FBI) 发布紧急警告称,黑客正在通过暴露在互联网且不安全的 SonarQube 实例中窃取美国政府和企业的信息。 SonarQube 是一款开源的自动化代码质量审计和静态分析平台,用于发现项目中的bug 和安全漏洞,支持27种语言。 自2020年4月起,易受攻击的 SonarQube 服务器就被用于获取、提取
黑客利用微软 MSHTML漏洞窃取谷歌和Instagram 凭据
聚焦源代码安全,网罗国内外最新资讯! 编译:代码卫士 SafeBreach Labs 的研究人员发现新型伊朗威胁组织使用一款基于 PowerShell 的窃取工具 PowerShortShell,攻击全球讲波斯语的谷歌和 Instagram 用户凭据。 PowerShortShell 也用于实施Telegram 监控并从受陷设备窃取收集系统信息,这些受陷设备和被盗凭据被一起发送给受攻击者控制
新三板公司敛财秘籍:窃取30亿条个人信息,谋利超千万
作者 | 李夏 编辑 | 邢昀 微博、抖音账户上莫名其妙被加粉?近日一起“史上最大规模”数据窃取案被媒体曝光,也揭开了这些平台涨粉的秘密。 而这幕后黑手竟是一家新三板挂牌公司——北京瑞智华胜科技股份有限公司(下称“瑞智华胜”),其涉嫌非法窃取用户个人信息30亿条,涉及百度、腾讯、京东等全国96家互联网公司产品。 8月21日,市界(ID:newsseeker)造访位于北京市海淀区西三环北
30亿条公民信息被新三板公司非法窃取这个锅究竟谁来背?
据新浪科技8月20日报道,新三板上市公司北京瑞智华胜科技股份有限公司涉嫌非法窃取用户30亿条信息引发公众一片哗然。这次案件不仅信息窃取规模庞大,同时还涉及互联网科技巨头,百度、腾讯、阿里、京东等全国96家互联网公司产品都受牵涉。最为关键的是用户信息泄露的源头竟然出在运营商身上,这也更加让大众忧心忡忡。 国内运营商手上掌握了全中国数以亿计用户的重要信息,它们一旦没有管好群众上网“第一道”信息安
被罚11万元!跳槽员工忘关屏幕共享,向Nvidia展示窃取源码,遭前东家当场抓获
你有过在公司会议的屏幕共享中,因不慎曝光了一些隐私而深感尴尬的经历吗? 如果有的话,那你或许能想象到英伟达员工 Mohammad Moniruzzaman 被抓包时的感受——只不过,他的后果要严重得多。 据外媒 SiliconValley 报道,Mohammad 在跳槽到英伟达之前,曾是汽车技术公司法雷奥(Valeo Schalter und Sensoren)的员工,后来两家公司因项目合作开
文献研读|Prompt窃取与保护综述
本文介绍与「Prompt窃取与保护」相关的几篇工作。 目录 1. Prompt Stealing Attacks Against Text-to-Image Generation Models(PromptStealer)2. Hard Prompts Made Easy: Gradient-Based Discrete Optimization for Prompt Tuning