workshop专题
速速报名|数据治理与数据建模workshop报名开启
由Datamodeling社区出品的「数据治理与数据建模workshop 」将在9月份正式启动上海站和深圳站。 本课程由社区特邀讲师王琤老师、黄峰老师授课,两位老师基于丰富的数据管理经验提炼出知识体系,以面对面带练的方式,帮助学习者快速掌握数据建模和数据治理的理论和实用技能。 9月7-8日首先启动「数据治理与数据建模workshop ·上海站」,欢迎华东地区想加强数据治理和数据建模能力的朋友报
【论文笔记】Proofs-of-delay and randomness beacons in Ethereum-2017IEEE SB Workshop
论文作者:Benedikt B¨unzy, Steven Goldfeder,Joseph Bonneauy Princeton University, Stanford University 论文源代码:https://github.com/bbuenz/VerifiableBeacon 作者个人网站:https://crypto.stanford.edu/~buenz/publicat
Workshop on Argument Mining (ArgMining) 历届会议信息
文章目录 ArgMining workshopShared task 共享任务2024年:2023年: 历届会议网站11th ArgMining@ACL August 15, 2024: Bangkok, Thailand10th ArgMining@EMNLP 2023: Singapore9th ArgMining@COLING 2022: Gyeongju, Korea8th ArgM
VALSE 2024 Workshop报告分享┆探索短视频生成与编辑的前沿技术
2024年视觉与学习青年学者研讨会(VALSE 2024)于5月5日到7日在重庆悦来国际会议中心举行。本公众号将全方位地对会议的热点进行报道,方便广大读者跟踪和了解人工智能的前沿理论和技术。欢迎广大读者对文章进行关注、阅读和转发。文章是对报告人演讲内容的理解或转述,可能与报告人的原意有所不同,敬请读者理解;如报告人认为文章与自己报告的内容差别较大,可以联系公众号删除。 本文对微软亚洲研究院的罗翀
VALSE 2024 Workshop报告分享┆ 大规模自动驾驶仿真系统研究
视觉与学习青年学者研讨会(VALSE)旨在为从事计算机视觉、图像处理、模式识别与机器学习研究的中国青年学者提供一个广泛而深入的学术交流平台。该平台旨在促进国内青年学者的思想交流和学术合作,以期在相关领域做出显著的学术贡献,并提升中国学者在国际学术舞台上的影响力。 2024年视觉与学习青年学者研讨会(VALSE 2024)于5月5日到7日在重庆悦来国际会议中心举行。本公众号将全方位地对会议的热点进
VizSEC 2007: Proceedings of the Workshop on Visualization for Computer Security
版权声明:原创作品,允许转载,转载时请务必以超链接形式标明文章原始出版、作者信息和本声明。否则将追究法律责任。 http://blog.csdn.net/topmvp - topmvp Networked computers are ubiquitous, and are subject to attack, misuse, and abuse. One method to counterac
安装和配置BEA WorkShop JSP Editor
WorkShop简介 BEA最近收购了M7公司,将其开发的NitroX系列开发工具加入到BEA WorkShop产品家族中,新的BEA WorkShop产品家族包括五个部分,BEA Workshop for Struts、 BEA Workshop for JSF、BEA BEA WorkShop JSP Editor、BEA Workshop Studio以及原有的BEA WebLogic
BEA Workshop™ for JSF 3.0
BEA Workshop™ for JSF 3.0 支持Hibernate的BEA Workshop™ Studio ORM Workbench BEA Workshop™ Studio是一种端到端、从浏览器到数据库的开发解决方案,具有对Hibernate、JSP、Struts和JSF的集成支持。ORM Workbench包括DbXplorer、DbXaminer、Entity Edito
Handy Notes for 2013 Beijing Perl Workshop
2013 Beijing Perl Workshop Yesterday I joined Beijing Perl Workshop and met lots of friends again, Joe, Roger, Qiang .... Below are my casual notes for yesterday's sessions. Just put it at
PSP - 结构生物学中的机器学习 (NIPS MLSB Workshop 2023.12)
欢迎关注我的CSDN:https://spike.blog.csdn.net/ 本文地址:https://spike.blog.csdn.net/article/details/135120094 Machine Learning in Structural Biology (机器学习在结构生物学中) 网址:https://www.mlsb.io/ Workshop at the
CVPR 2023 Workshop | 马普所、麻省理工等举办生成模型研讨会
点击下方卡片,关注“CVer”公众号 AI/CV重磅干货,第一时间送达 点击进入—>【计算机视觉】微信技术交流群 近期生成式建模(扩散模型,神经场等)实现了令人惊叹的2D和3D视觉合成效果,在人工智能领域引发了非常广泛的关注。然而,这些令人印象深刻的生成式模型尚未被广泛地应用于视觉理解任务。因此,来自德国马普所、美国麻省理工学院和约翰霍普金斯大学的学者将在CVPR 202
音频软件 Advanced WMA Workshop
我在太平洋电脑下的。 license codes: 0KM0K6K3g1HKIaAmI1dWs2poyWQs2X 1MCrUgffJO0GkS4TDdOyWcom0Q1XAB Xj2zKjjJi8W5uMCDvapRovOTbkFozo 1TT+cU53CMdfknnY8dmUb6l362/bC8 Ykgg1JS8NiliE5BsKOf/b8fsfKSfPF S87oBdHMvfxH31pGq+
ICCV 2021 Workshop 盘点
自动驾驶视觉 2nd Autonomous Vehicle Vision (AVVision) Workshop Rui Fan, Nemanja Djuric, Rowan McAllister, Ioannis Pitas http://avvision.xyz/iccv21 条件改变的长程视觉定位 4th Workshop on Long-Term V
PSP - 结构生物学中的机器学习 (NIPS MLSB Workshop 2023.12)
欢迎关注我的CSDN:https://spike.blog.csdn.net/ 本文地址:https://spike.blog.csdn.net/article/details/135120094 Machine Learning in Structural Biology (机器学习在结构生物学中) 网址:https://www.mlsb.io/ Workshop at the
PSP - 结构生物学中的机器学习 (NIPS MLSB Workshop 2023.12)
欢迎关注我的CSDN:https://spike.blog.csdn.net/ 本文地址:https://spike.blog.csdn.net/article/details/135120094 Machine Learning in Structural Biology (机器学习在结构生物学中) 网址:https://www.mlsb.io/ Workshop at the
亮眼 Pitch Deck 打造秘笈!2023 冬季波卡黑客松 Workshop 全回顾
如何才能更快地进入 Web3 开发世界?是技术专家的实战指导,还是行业大咖的前瞻分析,又或是自由平等的互动交流?在 OneBlock+ 与 Parity 联合举办的 2023 冬季波卡黑客松大赛中,这些想法都已悉数实现。 自 11 月 11 日至 12 月 2 日,贯穿 2023 冬季波卡黑客松大赛的 6 场赛前指导 Workshop&Office Hour 给所有热爱技术的开发者奉上了勇闯
【cocotb】【达坦科技DatenLord】Cocotb Workshop分享
https://www.bilibili.com/video/BV19e4y1k7EE/?spm_id_from=333.337.search-card.all.click&vd_source=fd0f4be6d0a5aaa0a79d89604df3154a 方便RFM实现 cocotb_test 替代makefile , 类似python 函数执行
FISCO BCOS WorkShop | 区块链开发特训营,开课啦!
FISCO BCOS是完全开源的联盟区块链底层技术平台,由金融区块链合作联盟(深圳)(简称金链盟)成立开源工作组通力打造。开源工作组成员包括博彦科技、华为、深证通、神州数码、四方精创、腾讯、微众银行、亦笔科技和越秀金科等金链盟成员机构。 代码仓库:https://github.com/FISCO-BCOS 想不想参加这样一个免费的区块链开发特训营? 想不想在区块链黑客马拉松开始之前,对
靶机:BSides-Vancouver-2018-Workshop
靶机说明 靶机用ValualBox创建,目标是在其上获得root级访问。 目标 Boot to root:获得root权限和Flag。 运行环境 靶机:通过ValualBox打开虚拟机,网络连接方式设置为主机模式(host-only),或者将虚拟机、Kali机都桥接到物理机的无线网卡。测试中使用VMWare导入虚机会无法获得IP,使用ValualBox可正常获得IP。 攻击机:同网段下有Windo
我做了一个 Istio Workshop,这是第一讲介绍
我是 Jimmy Song[1],Tetrate 布道师,云原生社区创始人。你可以能想到为什么在这个时候创建一个 Istio 教程,因为市面上已经林林总总有不少关于 Istio 的书籍和教程了,但是我们都知道 Istio 是一个新兴技术,发展十分迅速,几年前发行的书中知识到现在可能已经陈旧,而且市面上大部分对 Istio 的介绍都是书面或者 PPT 文字化的。 本课程将打破常规,将图文阅读、视
2018 Workshop on Autonomous Driving (WAD)----自动驾驶中视觉感知的比赛
自动驾驶中视觉感知的比赛 目的:主要帮助理解视觉算法在自动驾驶中解决环境感知问题上的研究现状 这里不仅仅是视觉算法在自动驾驶中的应用,还定义了下面一系列现实中的问题来鼓励新算法与流程的提出: (1) Drivable Area Segmentation (2) Road Object Detection (3) Domain Adaptation of Semantic Segmenta
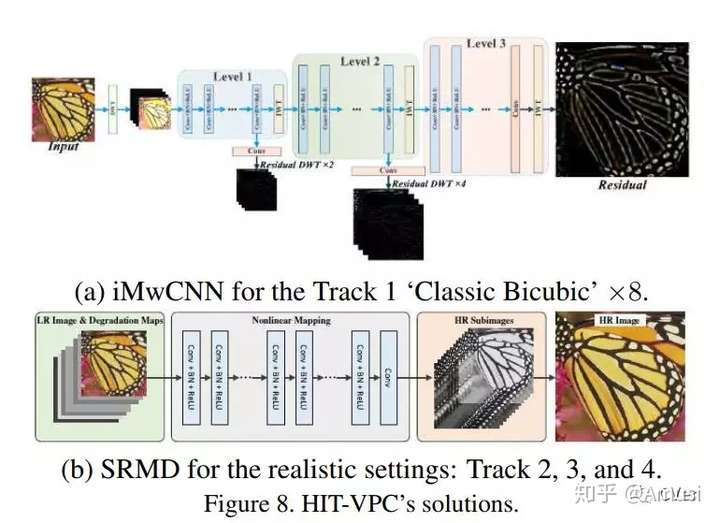
大牛分享:NTIRE 2018 图像超分辨率 CVPR Workshop 优胜方案
http://www.360doc.com/content/18/0717/08/54183077_771058619.shtml https://zhuanlan.zhihu.com/p/39930043 NTIRE 2018 图像超分辨率 CVPR Workshop优胜方案 很荣幸邀请了王超锋同学为大家做关于《NTIRE 2018 图像超分辨率 CVPR Workshop优胜方案》专题分
Workshop 报名 | 阿里云 IoT Ruff 物联网开发体验
前言: 科幻作家阿西莫夫在1964年纽约世博会上,预言未来将会出现的科技,其中就包括“火星自动探测器”、“机器人”、“自动驾驶汽车”;在库布里克的神作《2001太空漫游》中,宇航员使用的手表可以自动获取信息,进行智能决策,这都是与 IoT 相关的技术。而最近大火的电影《头号玩家》更加让人满怀憧憬当万物联网之后,开启的全新科幻世界。 那么: • 当下的物联网开发究竟需要哪些基础设施才能迎来大规模
Ceisum官方教程2 -- 项目实例(workshop)
原文地址:https://cesiumjs.org/tutorials/Cesium-Workshop/ 概述 我们很高兴欢迎你加入Cesium社区!为了让你能基于Cesium开发自己的3d 地图项目,这个教程将从头到尾讲解一个基础的Cesium程序的开发过程。这个教程将用到很多重要的CesiumAPI,但是并不是所有的(CesiumJS有很多很多功能)。我们目标是教会你基于Cesium做开发
2019 智见 AI workshop in Beijing
[持续更新]2019 智见 AI workshop in Beijing 前言代季峰:卷积神经网络中的几何形变建模Deformable Conv V1Deformable Conv V2Tricks & Exprience 张士峰:物体检测算法的对比探索和展望Detector Algorithm Overviewanchor-basedanchor-free RefineDet 张祥雨:高效