本文主要是介绍python公斤转克_1970年代公斤级键盘记录器提供的三项网络安全课程,希望对大家解决编程问题提供一定的参考价值,需要的开发者们随着小编来一起学习吧!
python公斤转克
A keylogger is a piece of software or hardware that records what you type, presumably so some bad guy can steal your secret data. You might think the earliest one used a PS/2 connector or installed on an old-fashioned IBM PC. An older computer, maybe? It turns out, what may very well be the first keylogger was built by the Soviet Union and used on IBM Selectric typewriters in the U.S. Embassy way back in the 1970s. What the NSA learned back then can still apply to cybersecurity today.
键盘记录程序是一种记录您键入内容的软件或硬件,大概是一些坏蛋可以窃取您的秘密数据。 您可能会认为最早使用PS / 2连接器或将其安装在老式IBM PC上。 也许是一台旧计算机? 事实证明,很可能第一个键盘记录器是由苏联制造的,并在1970年代美国大使馆的IBM Selectric打字机上使用。 NSA当时所学到的知识仍然可以应用于当今的网络安全。
If you are under a certain age, it is hard to realize just how ubiquitous the IBM Selectric was in the office world before computers. The heavy-duty typewriter didn’t use type bars like an ordinary typewriter. It used a “golf ball” that had the font on it. The machine would spin and pitch the ball before striking it on the paper. You could replace the ball to change fonts.
如果您未满一定年龄,则很难意识到IBM Selectric在计算机领域之前在办公室世界中是多么普遍。 重型打字机不像普通打字机那样使用类型栏。 它使用了上面带有字体的“高尔夫球”。 在将球击到纸上之前,机器会将球旋转并投球。 您可以替换球以更改字体。
The Selectric was a mechanical typewriter. But it also was a kind of digital device, too. How could you hack a typewriter into sending everything typed covertly? Oh. And do it with 1970’s technology, please.
Selectric是一台机械打字机。 但这也是一种数字设备。 您如何才能让打字机发送秘密输入的所有内容? 哦。 请用1970年代的技术来做。
来自俄罗斯的爱 (From Russia with Love)
Apparently, in the early 1970s, office equipment and typewriters were shipped to U.S. embassies in a fairly conventional way. Crypto machines and other classified material received tamper-resistant and tamper-evident cases delivered by special couriers, but typewriters came in as freight. Unknown to the U.S. at the time, Soviets (presumably the KGB) intercepted the typewriters in transit and installed highly sophisticated bugs in the typewriters.
显然,在1970年代初,办公设备和打字机以相当传统的方式运往美国大使馆。 密码机和其他机密材料收到了由特殊快递员提供的防篡改和防篡改案例,但打字机是作为货物运来的。 当时美国还不知道,苏联人(大概是克格勃)在运输途中拦截了打字机,并在打字机中安装了高度复杂的错误。
The device mostly replaced a bar inside the typewriter and was almost impossible to tell from the actual comb bar it replaced. The bug had custom integrated circuits and a small amount of core memory. There were several variants installed over the years. Some had batteries, and some drew power from the typewriter. The bugs transmitted short bursts on either 30, 60, or 90 MHz.
该设备主要替换了打字机内部的一根条,几乎无法从实际的梳条上分辨出它是被替换掉的。 该错误具有定制的集成电路和少量的核心内存。 这些年来,安装了多种变体。 有些装有电池,有些则从打字机取电。 这些错误在30、60或90 MHz上传输了短脉冲。
枪手计划 (Project Gunman)
In 1983, the French alerted the Americans that they had found a bug inside a teleprinter. The National Security Agency (NSA) studied it and found that it was sophisticated enough that it was unlikely to be unique. In 1984, they implemented a secret plan — project Gunman — to remove all suspect equipment from the embassy in Moscow and replace it with new equipment.
1983年,法国人警告美国人,他们在电传打印机内发现了一个小虫。 国家安全局(NSA)对它进行了研究,发现它足够复杂,以至于不可能唯一。 1984年,他们实施了一项秘密计划-Gunman项目-从莫斯科大使馆撤走所有可疑设备,并用新设备替换。
IBM Selectric typewriters that operated on 220V were in short supply, so while the embassy had 250 typewriters, only 50 replacements were available. This led to the NSA replacing only particularly important typewriters.
使用220V电压的IBM Selectric打字机供不应求,因此使馆有250台打字机,但只有50台可以更换。 这导致国家安全局仅更换了特别重要的打字机。
The replacement gear was guarded and had tamper seals on them. Very few people knew the real reason for the replacements, and the embassy staff was delighted to get new equipment without having to spend their own budget money.
替换齿轮受到保护,并带有防拆密封。 很少有人知道更换的真正原因,使馆工作人员很高兴在无需花费自己预算的情况下购买新设备。
The NSA removed about 11 tons of equipment from the embassy, and about 10 tons were shipped in covertly. The Russians had shut down the elevator for preventive maintenance (remember, this is during the cold war when both sides would do things to annoy the other), so most of the gear was moved through the building by stairs.
国家安全局从大使馆撤走了约11吨的设备,并秘密秘密运送了约10吨的设备。 俄国人已经关闭了电梯以进行预防性维护(请记住,这是在冷战期间,双方都会做些使对方烦恼的事情),因此大部分装备是通过楼梯移动穿过建筑物的。
分析 (Analysis)
The 11 tons of material was sent back to the United States under high security. No one thought the Soviets could bug the crypto machines, but then again, no one expected the typewriters, either. They examined the crypto machines by X-ray and found nothing. A second team looked at the non-secure items at a lower priority. The agency offered a reward of $5,000 to anyone who could identify the spy device in the equipment.
这11吨物料在高度安全的情况下被运回美国。 没有人认为苏联人会打扰加密机,但又一次,也没有人期望打字机。 他们用X射线检查了加密机,却一无所获。 第二个小组以较低的优先级查看了非安全物品。 该机构向任何能够识别设备中间谍设备的人提供5,000美元的奖励。
In July 1984, Mike Arenson saw something strange in an X-ray of a Selectric’s power switch. He decided to X-ray the whole machine and made a find worth $5,000. Once they knew what to look for, they would discover 16 bugs in Moscow and the consulate in Leningrad.
1984年7月,迈克·阿伦森(Mike Arenson)在Selectric的电源开关的X光片中看到了奇怪的东西。 他决定对整个机器进行X射线检查,发现价值5,000美元。 一旦他们知道该寻找什么,他们就会在莫斯科和列宁格勒的领事馆中发现16个虫子。
Arenson reportedly said:
据报道,阿伦森说:
When I saw those x-rays, my response was ‘holy f***’. They really were bugging our equipment. I was very excited, but no one was around to tell the news. My wife was an NSA employee, but I could not even tell her because of the level of classification of the project. I could hardly wait for morning when my colleagues would return.
当我看到那些X射线时,我的回答是“神圣的***”。 他们确实在窃听我们的设备。 我感到非常兴奋,但是没有人在告诉这个消息。 我的妻子是一名NSA雇员,但由于项目的分类级别,我什至无法告诉她。 我迫不及待地要等我的同事回来的早晨。
You can see a photo of a Selectric with the bugging device exposed below:
您可以在下面看到暴露设备的Selectric的照片:

运作方式(How it Worked)
The Selectric contains a mechanical digital to analog converter called a wiffle tree. The keys create movement on some metal arms that position the ball by rotating and tilting it. The KGB replaced the arms — latch interposers — with arms that looked the same but made of non-ferrous metal. They also had a strong magnet on the tip. The bug in the comb bar had six magnetometers that detected the motion of the arms.
Selectric包含一个机械的数模转换器,称为wiffle树。 按键在一些金属臂上产生运动,这些金属臂通过旋转和倾斜球来定位球。 克格勃(KGB)用看起来相同但由有色金属制成的臂代替了臂(闩锁插入器)。 他们的头上还有一块强磁铁。 梳子中的虫子有六个磁力计,可以检测手臂的运动。
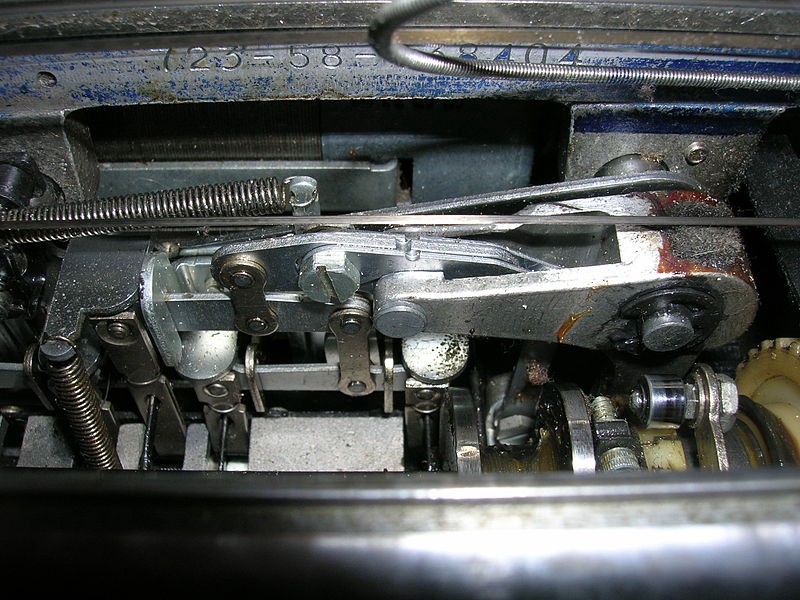
The six bits generated were encoded into 4 bits and stored in an 8-word core memory. When full, the bug would transmit the data in a high-speed burst. For technical reasons, the bug couldn’t tell uppercase from lowercase and didn’t read things like shift, space, tab, carriage return, and similar keys. Still, that was plenty of information to reconstruct nearly everything typed. The reduction to 4 bits probably means some letters shared codes, but knowing letter frequencies, it would be easy enough to rebuild the plain text.
生成的6位被编码为4位,并存储在8字核心存储器中。 该漏洞填满后,将以高速突发方式传输数据。 由于技术原因,该错误无法区分大小写,并且无法读取诸如shift,空格,制表符,回车键和类似键之类的信息。 尽管如此,仍然有大量信息可以重建几乎所有键入的内容。 减少到4位可能意味着某些字母共享代码,但是知道字母频率,就很容易重建纯文本。
There were five different versions of the bug. Three used batteries (8–10 mercury cells). The remaining types drew power from the typewriter itself.
该错误有五个不同的版本。 三个废旧电池(8-10个汞电池)。 其余的类型则依靠打字机本身的力量。
检测(或缺乏) (Detection (or Lack Thereof))
It wasn’t like the embassy didn’t search for bugs. However, the short duration of transmission prevented the old spectrum analyzers from seeing the bugs. The bug contained special circuitry to thwart a nonlinear junction detector (NLJD).
这不像使馆没有寻找臭虫。 但是,由于传输时间短,所以旧的频谱分析仪无法看到这些错误。 该错误包含阻止非线性结检测器(NLJD)的特殊电路。
Another complication was the frequency involved. The Soviets selected frequencies very close to a strong local TV station to help mask the signals.
另一个并发症是涉及的频率。 苏联人选择了非常靠近强大的本地电视台的频率来帮助掩盖信号。
It turns out that there had been some passive antennas that probably were part of the Selectric bug system found in 1978, but no one understood their significance at the time. Also, a technician examined embassy typewriters in 1978 but only looked at the power supplies of the machines since the assumption was that it would be where a bug would operate. Since, at the time, the KGB devices were battery-powered, they found nothing. Incidentally, reports indicate that the Russians only use manual typewriters for classified information.
事实证明,有一些无源天线可能是1978年发现的Selectric bug系统的一部分,但当时没人知道它们的重要性。 另外,一名技术人员在1978年检查了使馆打字机,但只查看了机器的电源,因为这种假设是可能会发生错误。 由于当时KGB设备由电池供电,因此他们什么也没找到。 偶然地,报告表明俄国人仅使用手动打字机获取机密信息。

后果(Aftermath)
The Soviets had bugged typewriters in the embassy from around 1976 until 1984. The discovery of the bugs led to many changes in how the State Department shipped equipment overseas. The FBI attempted to determine what information had leaked through the Selectric bugs, but was unable to reach any conclusions.
从1976年左右到1984年,苏联人在使馆里打字机被窃听。窃听器的发现导致国务院将设备运往海外的方式发生了许多变化。 联邦调查局试图确定哪些信息是通过Selectric漏洞泄漏的,但无法得出任何结论。
We will probably never know the Soviet engineer who designed these bugs. Maybe it was a team. But ideology aside, I know a hacker when I see one. These bugs were ingenious and highly advanced for their time. You can only wonder what is possible today that we won’t know about for years to come.
我们可能永远不会认识设计这些错误的苏联工程师。 也许是一个团队。 除了意识形态,当我看到一个黑客时,我就认识一个黑客。 这些错误在他们的时代独具匠心,并且非常先进。 您只能想知道今天可能发生的事情,这些都是我们未来几年所不知道的。
今天的课程和进一步阅读 (Lessons for Today and Further Reading)
The NSA has a great declassified document about Gunman. There’s a lot of details there, although for technical details, you might want to cruise over to the Crypto Museum’s page about these devices.
国家安全局有一份关于机枪手的绝密文件。 那里有很多细节,尽管有关技术细节,您可能想浏览有关这些设备的Crypto Museum页面。
What lessons can we learn from this for today’s cybersecurity posture?
从今天的网络安全态势中,我们可以从中学到什么教训?
- Even a low-level target like a typewriter or a thermostat may offer an easy way for an attacker to get information. 甚至像打字机或恒温器这样的低级目标也可能为攻击者提供一种获取信息的简便方法。
- Don’t underestimate your opponent’s technology. The hackers tend to have some pretty good technology. 不要低估对手的技术。 黑客往往拥有一些相当好的技术。
- Don’t trust your detection tools. If your detection technology has a blind spot, your attacker may very well be hiding right there. 不要相信您的检测工具。 如果您的检测技术有一个盲点,那么您的攻击者很可能就隐藏在那里。
Granted, most of us don’t have to deal with high tech secret agent gadgets like these, but the principles remain the same, even today.
诚然,我们大多数人不必处理此类高科技秘密特工,但即使在今天,其原理仍然相同。
The Soviets were pretty ingenious about bugging places. The Theremin bug was quite impressive and also went undetected for a very long time. Of course, there have always been fears of reading data from electronic devices through their emissions.
苏联人擅长窃听地方。 Theremin的错误非常令人印象深刻,并且很长一段时间都未被发现。 当然,一直以来人们一直担心会通过电子设备的发射来读取数据。
翻译自: https://medium.com/illumination/three-cybersecurity-lessons-from-a-1970s-kgb-key-logger-895fdc96b9f6
python公斤转克
相关文章:
这篇关于python公斤转克_1970年代公斤级键盘记录器提供的三项网络安全课程的文章就介绍到这儿,希望我们推荐的文章对编程师们有所帮助!




