本文主要是介绍【华东南AWDP】第十七届全国大学生信息安全竞赛 CISCN 2024 创新实践能力赛区域赛 部分题解WP,希望对大家解决编程问题提供一定的参考价值,需要的开发者们随着小编来一起学习吧!
前言:这次区域赛AWDP安恒作为支持,赛制风格遵循安恒,一小时check一次。室温35°在室内坐了8小时,午饭是藿香正气水拌冰水。这场总体下来中规中矩吧。
WEB-welcome-BREAK
Ctrl+U拿到flag

WEB-submit-BREAK
文件上传,简单绕过
绕过就两个,一个MIMA头,一个等号换php(短标签)


WEB-submit-FIX
修两个点,一个是后缀检验,一个是waf增加
<?php
// $path = "./uploads";
error_reporting(0);
$path = "./uploads";
$content = file_get_contents($_FILES['myfile']['tmp_name']);
$allow_content_type = array("image/png");
$type = $_FILES["myfile"]["type"];
if (!in_array($type, $allow_content_type)) {die("只允许png哦!<br>");
}//修改点1
$allow_ext = array(".png");
$file_name=$_FILES["myfile"]['name'];
$_FILES["myfile"]['name'] = str_replace(".ph","",$_FILES["myfile"]['name']);
$file_ext = strrchr($file_name, '.');
$file_ext = strtolower($file_ext); //转换为小写
$file_ext = str_ireplace('::$DATA', '', $file_ext);//去除字符串::$DATA
$file_ext = trim($file_ext); //收尾去空
if (!in_array($file_ext, $allow_ext)) {die("只允许png哦!<br>");
}//修改点2
if (preg_match('/(php|script|xml|user|htaccess|\<\?|\<\?\=|eval|system|assert|fllllagg|f\*|\/f|cat|POST|GET|\$\_|exec)/i', $content)) {// echo "匹配成功!";die('鼠鼠说你的内容不符合哦0-0');
} else {$file = $path . '/' . $_FILES['myfile']['name'];echo $file;if (move_uploaded_file($_FILES['myfile']['tmp_name'], $file)) {file_put_contents($file, $content);echo 'Success!<br>';} else {echo 'Error!<br>';}
}
?>WEB-粗心的程序员-BREAK
www.zip源码泄露。简单代码审计和逻辑漏洞
简单扫一眼,开了sql的PDO(但是最后没用上)
主要漏洞文件:
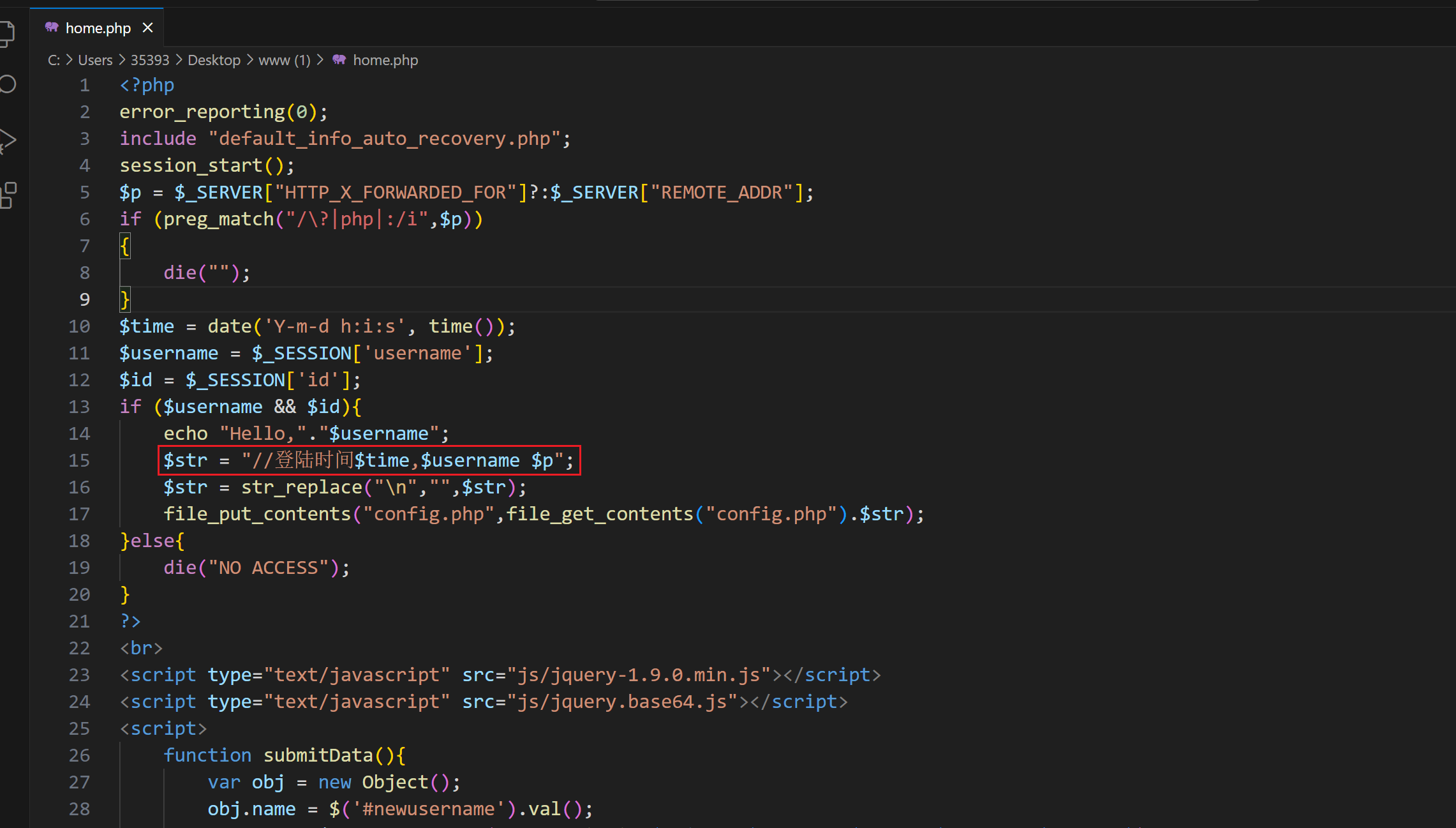
贴一下代码:
<?php
error_reporting(0);
include "default_info_auto_recovery.php";
session_start();
$p = $_SERVER["HTTP_X_FORWARDED_FOR"]?:$_SERVER["REMOTE_ADDR"];
if (preg_match("/\?|php|:/i",$p))
{die("");
}
$time = date('Y-m-d h:i:s', time());
$username = $_SESSION['username'];
$id = $_SESSION['id'];
if ($username && $id){echo "Hello,"."$username";$str = "//登陆时间$time,$username $p";$str = str_replace("\n","",$str);file_put_contents("config.php",file_get_contents("config.php").$str);
}else{die("NO ACCESS");
}
?>
<br>
<script type="text/javascript" src="js/jquery-1.9.0.min.js"></script>
<script type="text/javascript" src="js/jquery.base64.js"></script>
<script>function submitData(){var obj = new Object();obj.name = $('#newusername').val();var str = $.base64.encode(JSON.stringify(obj.name).replace("\"","").replace("\"",""));$.post("edit.php",{newusername: str},function(str){alert(str);location.reload()});}jQuery.base64 = (function($) {var keyStr = "ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/=";function utf8Encode(string) {string = string.replace(/\r\n/g,"\n");var utftext = "";for (var n = 0; n < string.length; n++) {var c = string.charCodeAt(n);if (c < 128) {utftext += String.fromCharCode(c);}else if((c > 127) && (c < 2048)) {utftext += String.fromCharCode((c >> 6) | 192);utftext += String.fromCharCode((c & 63) | 128);}else {utftext += String.fromCharCode((c >> 12) | 224);utftext += String.fromCharCode(((c >> 6) & 63) | 128);utftext += String.fromCharCode((c & 63) | 128);}}return utftext;}function encode(input) {var output = "";var chr1, chr2, chr3, enc1, enc2, enc3, enc4;var i = 0;input = utf8Encode(input);while (i < input.length) {chr1 = input.charCodeAt(i++);chr2 = input.charCodeAt(i++);chr3 = input.charCodeAt(i++);enc1 = chr1 >> 2;enc2 = ((chr1 & 3) << 4) | (chr2 >> 4);enc3 = ((chr2 & 15) << 2) | (chr3 >> 6);enc4 = chr3 & 63;if (isNaN(chr2)) {enc3 = enc4 = 64;} else if (isNaN(chr3)) {enc4 = 64;}output = output +keyStr.charAt(enc1) + keyStr.charAt(enc2) +keyStr.charAt(enc3) + keyStr.charAt(enc4);}return output;}return {encode: function (str) {return encode(str);}};}(jQuery));</script>
更改用户名<input type="text" name="newusername" id="newusername" value="">
<button type="submit" onclick="submitData()" >更改</button>简单说一下思路
1、$str = "//登陆时间$time,$username $p";会被写入php文件file_put_contents(“config.php”,file_get_contents(“config.php”).$str);
2、既然是php,写入了如果不是算注释的话就能执行
3、尝试写🐎
4、用户名这边利用?>进行截断注释的作用
5、$p这边进行写🐎




WEB-粗心的程序员-FIX
源码如下
<?php
error_reporting(0);
include "default_info_auto_recovery.php";
session_start();
$p = $_SERVER["HTTP_X_FORWARDED_FOR"]?:$_SERVER["REMOTE_ADDR"];
if (preg_match("/\?|php|:/i",$p))
{die("");
}
$time = date('Y-m-d h:i:s', time());
$username = $_SESSION['username'];
$id = $_SESSION['id'];
if ($username && $id){echo "Hello,"."$username";$str = "//登陆时间$time,$username $p";$str = str_replace("\n","",$str);file_put_contents("config.php",file_get_contents("config.php").$str);
}else{die("NO ACCESS");
}
?>
<br>
<script type="text/javascript" src="js/jquery-1.9.0.min.js"></script>
<script type="text/javascript" src="js/jquery.base64.js"></script>
<script>function submitData(){var obj = new Object();obj.name = $('#newusername').val();var str = $.base64.encode(JSON.stringify(obj.name).replace("\"","").replace("\"",""));$.post("edit.php",{newusername: str},function(str){alert(str);location.reload()});}jQuery.base64 = (function($) {var keyStr = "ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/=";function utf8Encode(string) {string = string.replace(/\r\n/g,"\n");var utftext = "";for (var n = 0; n < string.length; n++) {var c = string.charCodeAt(n);if (c < 128) {utftext += String.fromCharCode(c);}else if((c > 127) && (c < 2048)) {utftext += String.fromCharCode((c >> 6) | 192);utftext += String.fromCharCode((c & 63) | 128);}else {utftext += String.fromCharCode((c >> 12) | 224);utftext += String.fromCharCode(((c >> 6) & 63) | 128);utftext += String.fromCharCode((c & 63) | 128);}}return utftext;}function encode(input) {var output = "";var chr1, chr2, chr3, enc1, enc2, enc3, enc4;var i = 0;input = utf8Encode(input);while (i < input.length) {chr1 = input.charCodeAt(i++);chr2 = input.charCodeAt(i++);chr3 = input.charCodeAt(i++);enc1 = chr1 >> 2;enc2 = ((chr1 & 3) << 4) | (chr2 >> 4);enc3 = ((chr2 & 15) << 2) | (chr3 >> 6);enc4 = chr3 & 63;if (isNaN(chr2)) {enc3 = enc4 = 64;} else if (isNaN(chr3)) {enc4 = 64;}output = output +keyStr.charAt(enc1) + keyStr.charAt(enc2) +keyStr.charAt(enc3) + keyStr.charAt(enc4);}return output;}return {encode: function (str) {return encode(str);}};}(jQuery));</script>
更改用户名<input type="text" name="newusername" id="newusername" value="">
<button type="submit" onclick="submitData()" >更改</button>$username和$p加waf就行,怎么打的怎么加
<?php
error_reporting(0);
include "default_info_auto_recovery.php";
session_start();
$p = $_SERVER["HTTP_X_FORWARDED_FOR"]?:$_SERVER["REMOTE_ADDR"];
//waf1
if (preg_match("/\?|php|:|system|cat|flaaaaaag|\*|eval|php/i",$p))
{die("");
}
$time = date('Y-m-d h:i:s', time());
$username = $_SESSION['username'];
$id = $_SESSION['id'];
//waf2
if (preg_match("/\?|\<\?|php|:/i",$username))
{die("");
}if ($username && $id){echo "Hello,"."$username";$str = "//登陆时间$time,$username $p";$str = str_replace("\n","",$str);file_put_contents("config.php",file_get_contents("config.php").$str);
}else{die("NO ACCESS");
}
?>
<br>
<script type="text/javascript" src="js/jquery-1.9.0.min.js"></script>
<script type="text/javascript" src="js/jquery.base64.js"></script>
<script>function submitData(){var obj = new Object();obj.name = $('#newusername').val();var str = $.base64.encode(JSON.stringify(obj.name).replace("\"","").replace("\"",""));$.post("edit.php",{newusername: str},function(str){alert(str);location.reload()});}jQuery.base64 = (function($) {var keyStr = "ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/=";function utf8Encode(string) {string = string.replace(/\r\n/g,"\n");var utftext = "";for (var n = 0; n < string.length; n++) {var c = string.charCodeAt(n);if (c < 128) {utftext += String.fromCharCode(c);}else if((c > 127) && (c < 2048)) {utftext += String.fromCharCode((c >> 6) | 192);utftext += String.fromCharCode((c & 63) | 128);}else {utftext += String.fromCharCode((c >> 12) | 224);utftext += String.fromCharCode(((c >> 6) & 63) | 128);utftext += String.fromCharCode((c & 63) | 128);}}return utftext;}function encode(input) {var output = "";var chr1, chr2, chr3, enc1, enc2, enc3, enc4;var i = 0;input = utf8Encode(input);while (i < input.length) {chr1 = input.charCodeAt(i++);chr2 = input.charCodeAt(i++);chr3 = input.charCodeAt(i++);enc1 = chr1 >> 2;enc2 = ((chr1 & 3) << 4) | (chr2 >> 4);enc3 = ((chr2 & 15) << 2) | (chr3 >> 6);enc4 = chr3 & 63;if (isNaN(chr2)) {enc3 = enc4 = 64;} else if (isNaN(chr3)) {enc4 = 64;}output = output +keyStr.charAt(enc1) + keyStr.charAt(enc2) +keyStr.charAt(enc3) + keyStr.charAt(enc4);}return output;}return {encode: function (str) {return encode(str);}};}(jQuery));</script>
更改用户名<input type="text" name="newusername" id="newusername" value="">
<button type="submit" onclick="submitData()" >更改</button>WEB-Polluted-FIX
攻击时候没打出来
原来代码
from flask import Flask, session, redirect, url_for,request,render_template
import os
import hashlib
import json
import redef generate_random_md5():random_string = os.urandom(16)md5_hash = hashlib.md5(random_string)return md5_hash.hexdigest()
def filter(user_input):blacklisted_patterns = ['init', 'global', 'env', 'app', '_', 'string']for pattern in blacklisted_patterns:if re.search(pattern, user_input, re.IGNORECASE):return Truereturn False
def merge(src, dst):# Recursive merge functionfor k, v in src.items():if hasattr(dst, '__getitem__'):if dst.get(k) and type(v) == dict:merge(v, dst.get(k))else:dst[k] = velif hasattr(dst, k) and type(v) == dict:merge(v, getattr(dst, k))else:setattr(dst, k, v)app = Flask(__name__)
app.secret_key = generate_random_md5()class evil():def __init__(self):pass@app.route('/',methods=['POST'])
def index():username = request.form.get('username')password = request.form.get('password')session["username"] = usernamesession["password"] = passwordEvil = evil()if request.data:if filter(str(request.data)):return "NO POLLUTED!!!YOU NEED TO GO HOME TO SLEEP~"else:merge(json.loads(request.data), Evil)return "MYBE YOU SHOULD GO /ADMIN TO SEE WHAT HAPPENED"return render_template("index.html")@app.route('/admin',methods=['POST', 'GET'])
def templates():username = session.get("username", None)password = session.get("password", None)if username and password:if username == "adminer" and password == app.secret_key:return render_template("important.html", flag=open("/flag", "rt").read())else:return "Unauthorized"else:return f'Hello, This is the POLLUTED page.'if __name__ == '__main__':app.run(host='0.0.0.0',debug=True, port=80)修复代码
from flask import Flask, session, redirect, url_for,request,render_template
import os
import hashlib
import json
import redef generate_random_md5():random_string = os.urandom(16)md5_hash = hashlib.md5(random_string)return md5_hash.hexdigest()
def filter(user_input):#修复点1 加wafblacklisted_patterns = ['init', 'global', 'env', 'app', 'secret', 'key', 'admin','string', 'proto', 'constructor', 'insert', 'update', 'truncate', 'drop', 'create','doc','str', '_']for pattern in blacklisted_patterns:if re.search(pattern, user_input, re.IGNORECASE):return Truereturn Falsedef merge(src, dst):# Recursive merge functionfor k, v in src.items():if hasattr(dst, '__getitem__'):if dst.get(k) and type(v) == dict:merge(v, dst.get(k))else:dst[k] = velif hasattr(dst, k) and type(v) == dict:merge(v, getattr(dst, k))else:setattr(dst, k, v)app = Flask(__name__)
app.secret_key = generate_random_md5()class evil():def __init__(self):pass@app.route('/',methods=['POST'])
def index():username = request.form.get('username')password = request.form.get('password')#修复点二,乱加的if username=='adminer':exit(0)if username=='admin':exit(0)session["username"] = usernamesession["password"] = passwordEvil = evil()if request.data:if filter(str(request.data)):return "NO POLLUTED!!!YOU NEED TO GO HOME TO SLEEP~"else:#其实直接ban了这个就行merge(json.loads(request.data), Evil)return "MYBE YOU SHOULD GO /ADMIN TO SEE WHAT HAPPENED"return render_template("index.html")@app.route('/admin',methods=['POST', 'GET'])
def templates():username = session.get("username", None)password = session.get("password", None)if username and password:#修复点三,black一下if username == "adminerrrr" and password == app.secret_key:return render_template("important.html", flag=open("/flag", "rt").read())else:return "Unauthorized"else:return f'Hello, This is the POLLUTED page.'if __name__ == '__main__':app.run(host='0.0.0.0',debug=True, port=80)PWN-ezwp-BREAK
打开网页直接搜索flag,非预期闹麻了
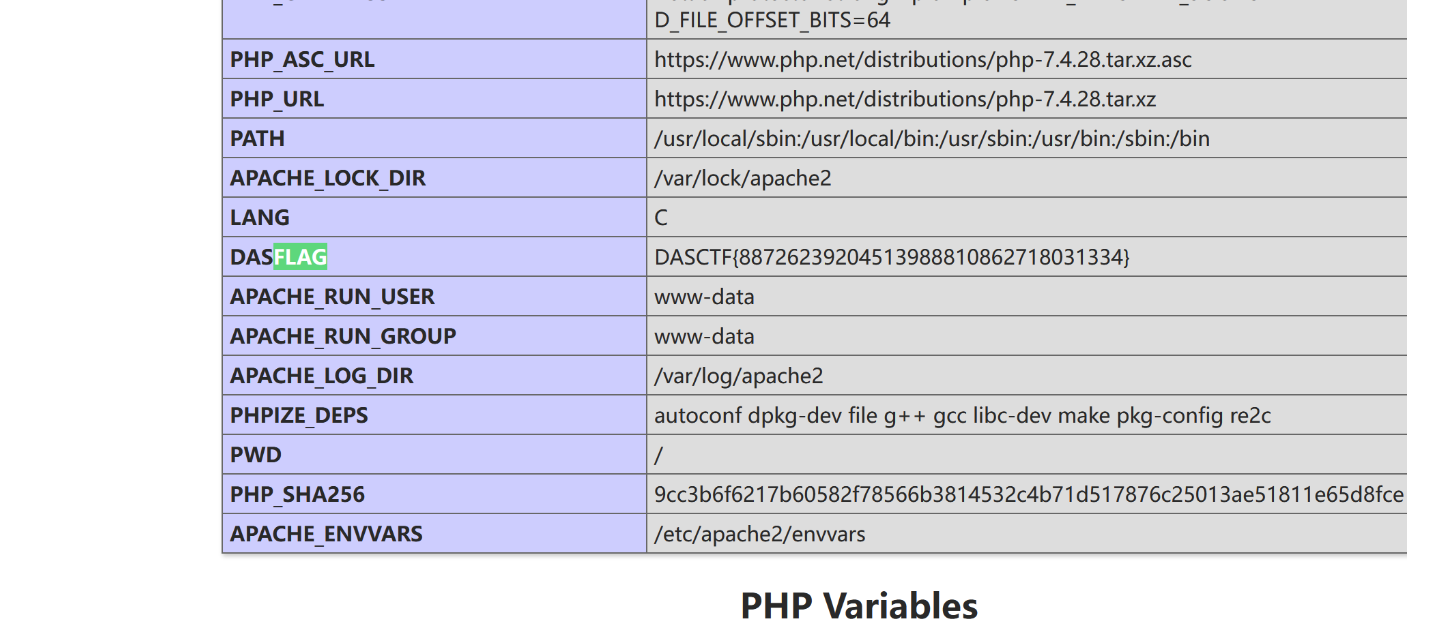
PWN-CJS0N-FIX
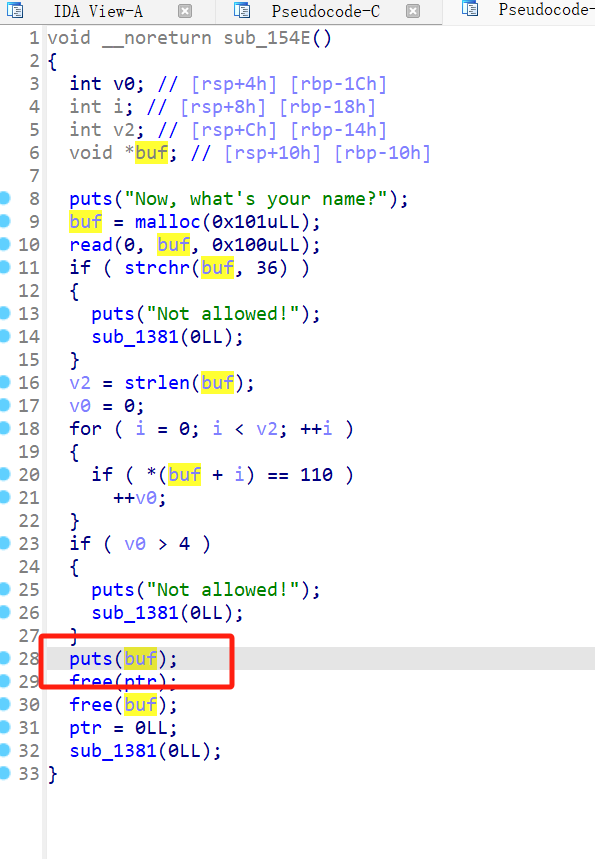
直接将printf改成puts即可

PWN-printf-master-FIX
同样将printf改成puts即可
这篇关于【华东南AWDP】第十七届全国大学生信息安全竞赛 CISCN 2024 创新实践能力赛区域赛 部分题解WP的文章就介绍到这儿,希望我们推荐的文章对编程师们有所帮助!






