本文主要是介绍iptables防火墙【其二 实验篇】,希望对大家解决编程问题提供一定的参考价值,需要的开发者们随着小编来一起学习吧!
保存,还原规则
防火墙规则的备份和还原
导出(备份)所有表的规则
iptables-save > /opt/ipt.txt导入(还原)规则
iptables-restore < /opt/ipt.txt
将iptables规则文件保存在 /etc/sysconfig/iptables 中,iptables服务启动时会自动还原规则
iptables-save > /etc/sysconfig/iptables
systemctl stop iptables #停止iptables服务会清空掉所有表的规则
systemctl start iptables #启动iptables服务会自动还原/etc/sysconfig/iptables 中的规则
保存规则 iptables-save > 文件路径
还原规则 iptables-restore < 文件路径
保存为默认规则 iptables-save > /etc/sysconfig/iptables
[root@l1 ~]# systemctl disable --now firewalld //永久关闭防火墙
Removed symlink /etc/systemd/system/multi-user.target.wants/firewalld.service.
Removed symlink /etc/systemd/system/dbus-org.fedoraproject.FirewallD1.service.
[root@l1 ~]#
[root@l1 ~]# yum install -y iptables iptables-services //安装两个软件
已加载插件:fastestmirror, langpacks
Loading mirror speeds from cached hostfile
软件包 iptables-1.4.21-35.el7.x86_64 已安装并且是最新版本
正在解决依赖关系
--> 正在检查事务
---> 软件包 iptables-services.x86_64.0.1.4.21-35.el7 将被 安装
--> 解决依赖关系完成依赖关系解决=============================================================================================================================================================Package 架构 版本 源 大小
=============================================================================================================================================================
正在安装:iptables-services x86_64 1.4.21-35.el7 local 52 k事务概要
=============================================================================================================================================================
安装 1 软件包总下载量:52 k
安装大小:23 k
Downloading packages:
Running transaction check
Running transaction test
Transaction test succeeded
Running transaction正在安装 : iptables-services-1.4.21-35.el7.x86_64 1/1 验证中 : iptables-services-1.4.21-35.el7.x86_64 1/1 已安装:iptables-services.x86_64 0:1.4.21-35.el7 完毕!
[root@l1 ~]#
[root@l1 ~]# systemctl start iptables.service //启动服务
[root@l1 ~]# iptables -nL -t nat
Chain PREROUTING (policy ACCEPT)
target prot opt source destination Chain INPUT (policy ACCEPT)
target prot opt source destination Chain OUTPUT (policy ACCEPT)
target prot opt source destination Chain POSTROUTING (policy ACCEPT)
target prot opt source destination
[root@l1 ~]# iptables -nL -t filter
Chain INPUT (policy ACCEPT)
target prot opt source destination
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED
ACCEPT icmp -- 0.0.0.0/0 0.0.0.0/0
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22
REJECT all -- 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibitedChain FORWARD (policy ACCEPT)
target prot opt source destination
REJECT all -- 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibitedChain OUTPUT (policy ACCEPT)
target prot opt source destination
[root@l1 ~]#
之前设置的规则没有永久保存,当你服务器重启 或者是 iptables服务重启 都会导致之前写入的规则丢失
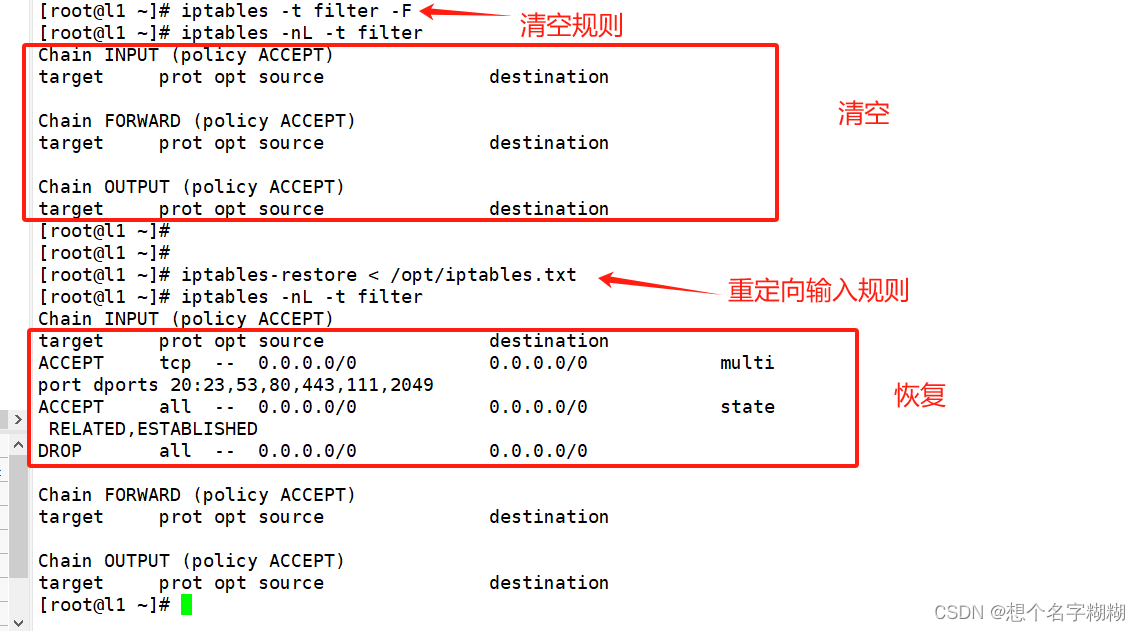
[root@l1 ~]# iptables -t filter -F
[root@l1 ~]# iptables -nL -t filter
Chain INPUT (policy ACCEPT)
target prot opt source destination Chain FORWARD (policy ACCEPT)
target prot opt source destination Chain OUTPUT (policy ACCEPT)
target prot opt source destination
[root@l1 ~]# iptables -t filter -A INPUT -p tcp -m multiport --dport 20:23,53,80,443,111,2049 -j ACCEPT
[root@l1 ~]# iptables -t filter -A INPUT -m state --state ESTABLISHED,RELATED -j ACCEPT
[root@l1 ~]# iptables -t filter -A INPUT -j DROP
[root@l1 ~]# iptables -nL -t filter
Chain INPUT (policy ACCEPT)
target prot opt source destination
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 multiport dports 20:23,53,80,443,111,2049
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED
DROP all -- 0.0.0.0/0 0.0.0.0/0 Chain FORWARD (policy ACCEPT)
target prot opt source destination Chain OUTPUT (policy ACCEPT)
target prot opt source destination
[root@l1 ~]#
保存规则
[root@l1 ~]# iptables-save > /opt/iptables.txt //重定向输出到/opt/iptables.txt
[root@l1 ~]# vim /opt/iptables.txt [root@l1 ~]# iptables-restore < /opt/iptables.txt //重定向输入规则
[root@l1 ~]# iptables -nL -t filter
Chain INPUT (policy ACCEPT)
target prot opt source destination
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 multiport dports 20:23,53,80,443,111,2049
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED
DROP all -- 0.0.0.0/0 0.0.0.0/0 Chain FORWARD (policy ACCEPT)
target prot opt source destination Chain OUTPUT (policy ACCEPT)
target prot opt source destination
[root@l1 ~]#
还原规则
[root@l1 ~]# iptables -t filter -F //清除规则
[root@l1 ~]# iptables -nL -t filter
Chain INPUT (policy ACCEPT)
target prot opt source destination Chain FORWARD (policy ACCEPT)
target prot opt source destination Chain OUTPUT (policy ACCEPT)
target prot opt source destination
[root@l1 ~]#
如何设置默认规则
[root@l1 ~]# systemctl restart iptables.service //重启服务
[root@l1 ~]# iptables -nL -t filter //规则还原了
Chain INPUT (policy ACCEPT)
target prot opt source destination
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED
ACCEPT icmp -- 0.0.0.0/0 0.0.0.0/0
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22
REJECT all -- 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibitedChain FORWARD (policy ACCEPT)
target prot opt source destination
REJECT all -- 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibitedChain OUTPUT (policy ACCEPT)
target prot opt source destination
[root@l1 ~]#

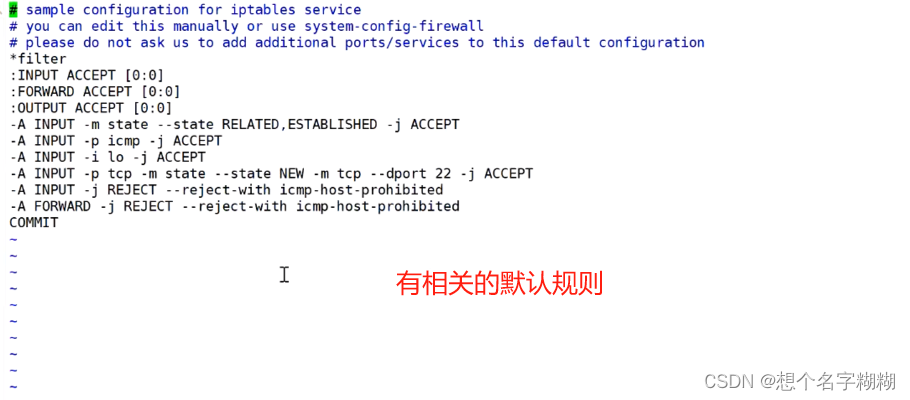
[root@l1 ~]# iptables-save > /etc/sysconfig/iptables //替换默认规则文件
[root@l1 ~]# vim /etc/sysconfig/iptables
[root@l1 ~]#
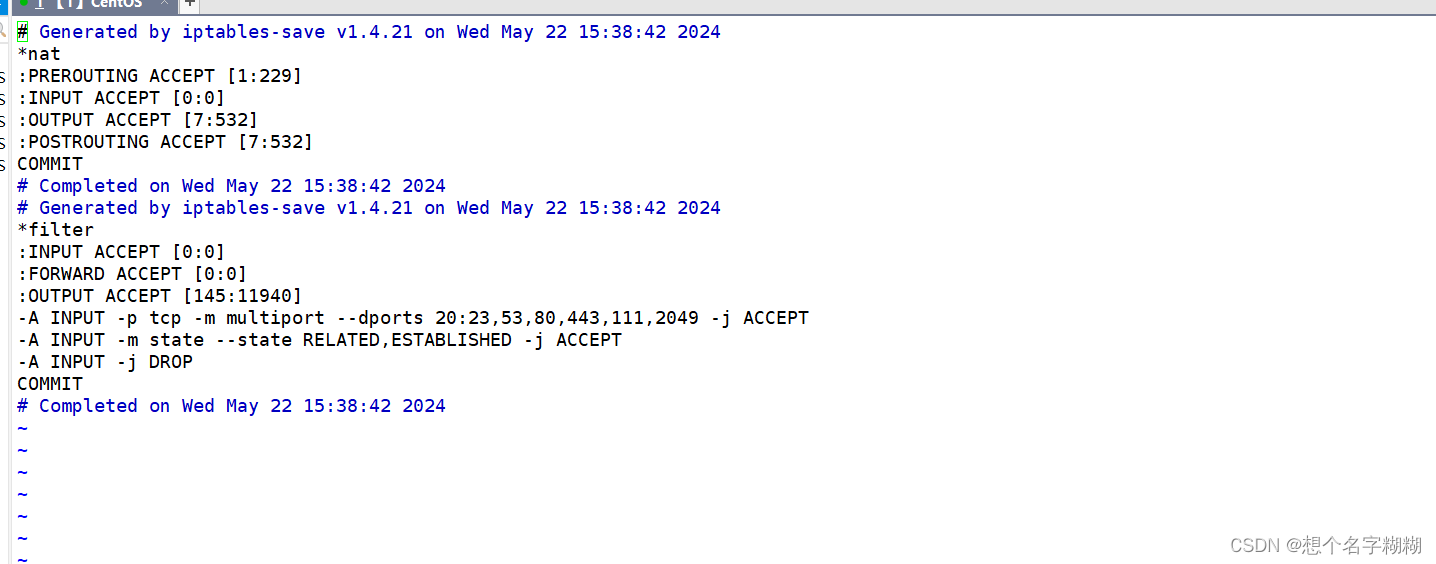
[root@l1 ~]# iptables -t filter -F //清空规则
[root@l1 ~]# iptables -nL -t filter //查看规则
Chain INPUT (policy ACCEPT)
target prot opt source destination Chain FORWARD (policy ACCEPT)
target prot opt source destination Chain OUTPUT (policy ACCEPT)
target prot opt source destination
[root@l1 ~]# systemctl restart iptables.service //重启服务
[root@l1 ~]# iptables -nL -t filter //查看规则(已恢复)
Chain INPUT (policy ACCEPT)
target prot opt source destination
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 multiport dports 20:23,53,80,443,111,2049
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED
DROP all -- 0.0.0.0/0 0.0.0.0/0 Chain FORWARD (policy ACCEPT)
target prot opt source destination Chain OUTPUT (policy ACCEPT)
target prot opt source destination
[root@l1 ~]#
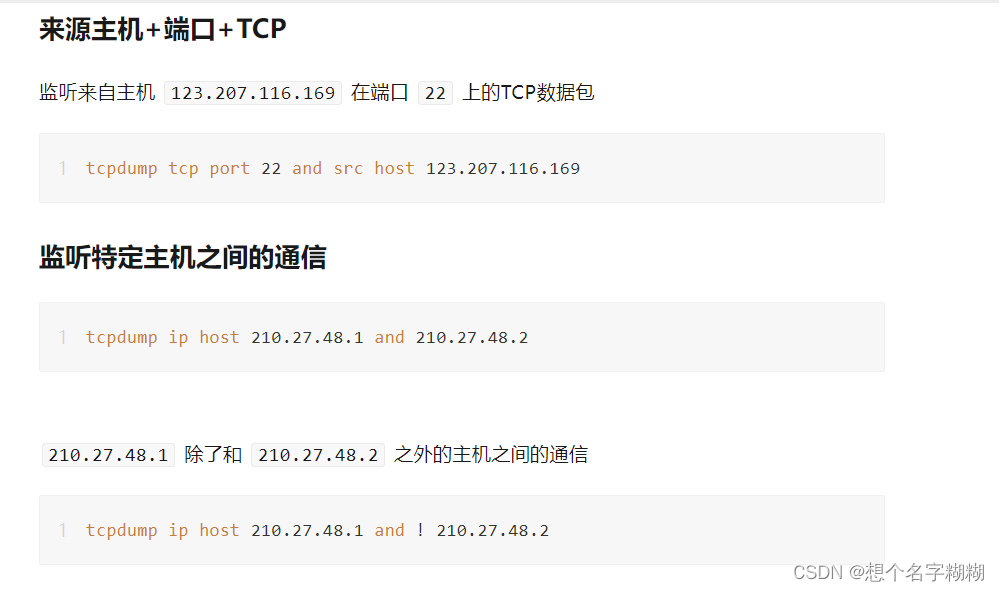
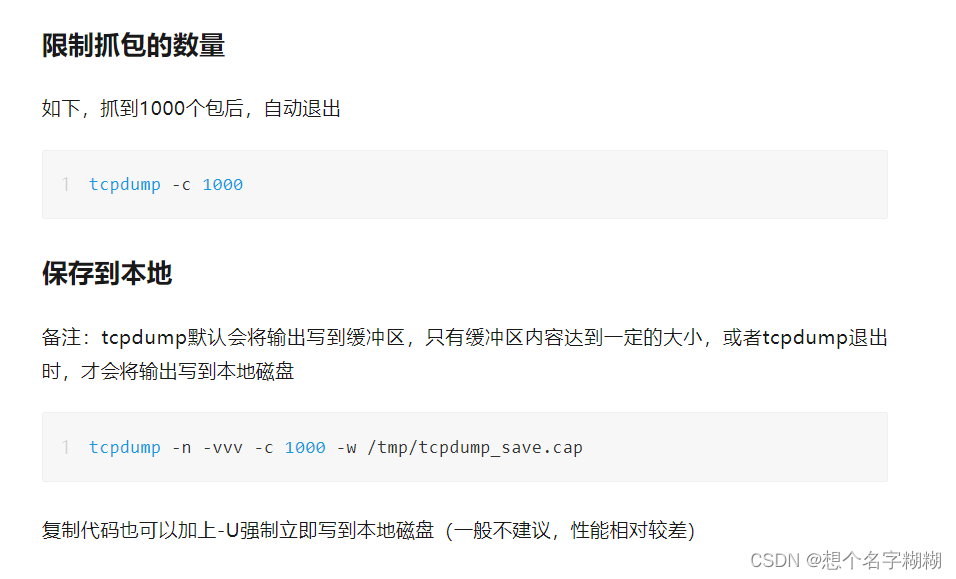
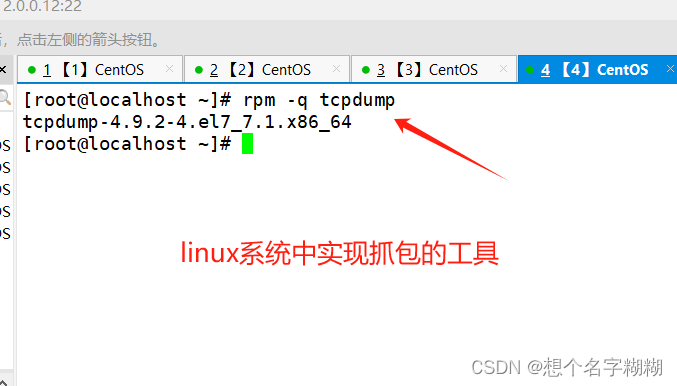
tcpdump Linux系统抓包工具
tcp 协议 port 端口 [src/dst] net 网段 -i 网卡 -s 0 -w XXX.cap
tcp host 主机IP
udp
icmp
tcpdump tcp -i ens33 -t -s 0 -c 100 and port ! 22 and net 192.168.1.0/24 -w ./target.cap
(1)tcp: ip icmp arp rarp 和 tcp、udp、icmp这些协议选项等都要放到第一个参数的位置,用来过滤数据包的类型
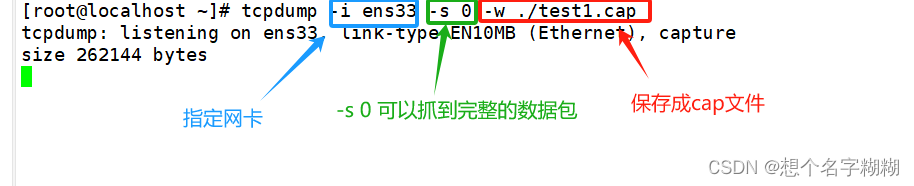
(2)-i ens33 : 只抓经过接口ens33的包
(3)-t : 不显示时间戳
(4)-s 0 : 抓取数据包时默认抓取长度为68字节。加上-s 0 后可以抓到完整的数据包
(5)-c 100 : 只抓取100个数据包
(6)port ! 22 : 不抓取端口是22的数据包
(7)net 192.168.1.0/24 : 数据包的网络地址为192.168.1.0/24
(8)-w ./target.cap : 保存成cap文件,方便用ethereal(即wireshark)分析 


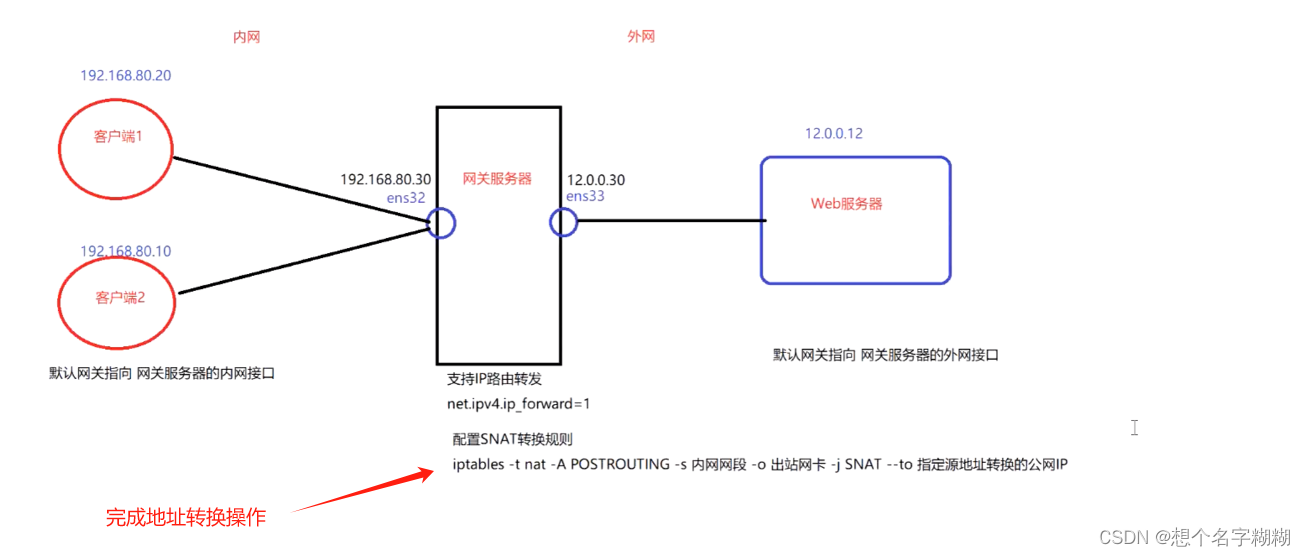
实验1 SNAT
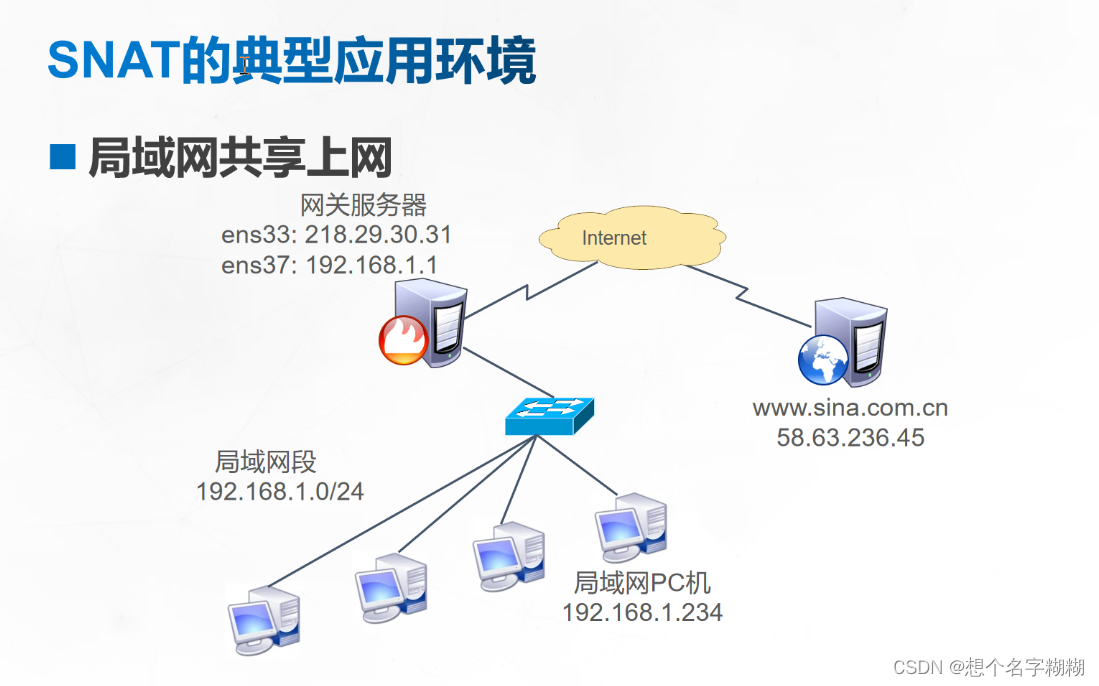

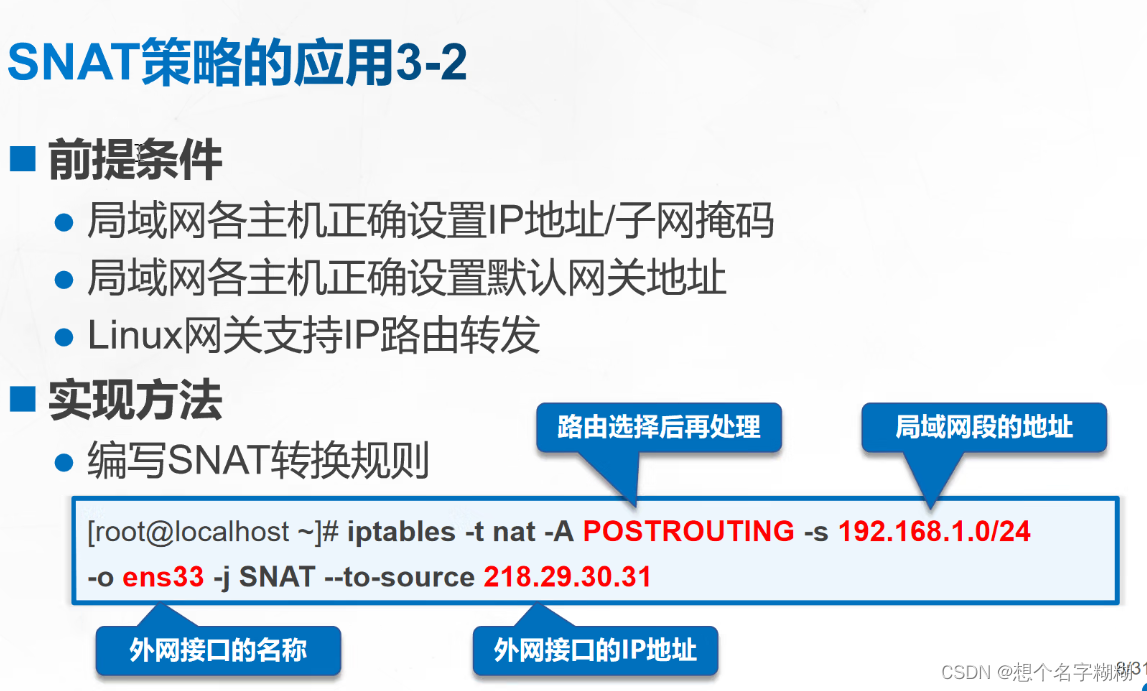

网关主机 ens33(左,连接内网)192.168.80.30 ens36(右,连接外网)12.0.0.30
客户端1 设置ip地址为192.168.80.11 网关为ens33 192.168.80.30
客户端2 设置ip地址为192.168.80.20 网关为ens33 192.168.80.30
外网服务器 ip 12.0.0.12 网关为ens36 12.0.0.30
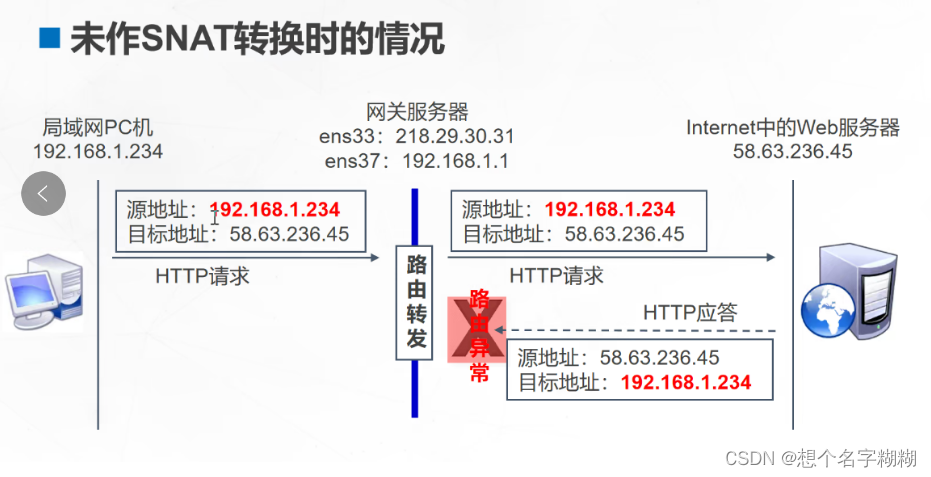
SNAT 内网 --> 外网 转换源地址
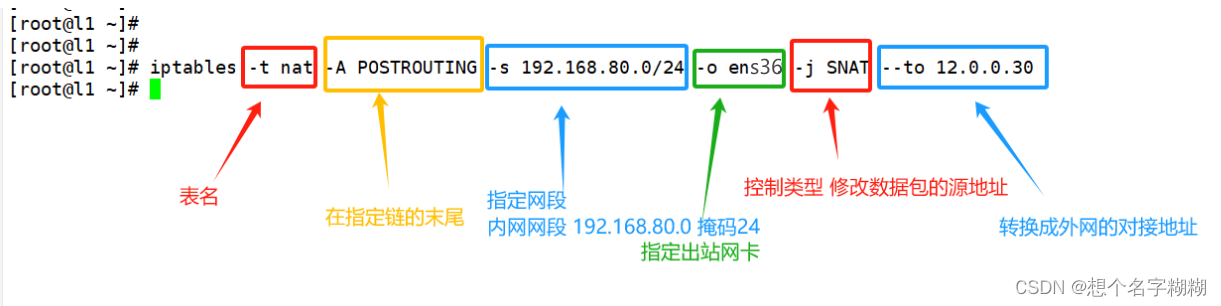
iptables -t nat -A POSTROUTING -s 内网的源地址/网段 -o 出站网卡 -j SNAT --to 要转换的公网源地址
打开ip转发功能
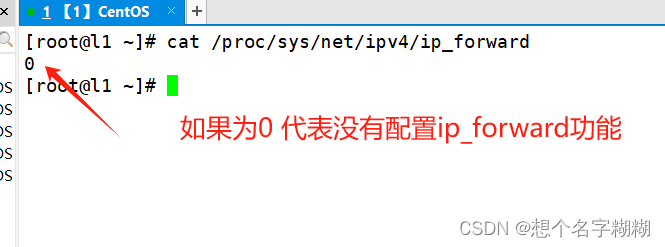
[root@l1 ~]# cat /proc/sys/net/ipv4/ip_forward
0
[root@l1 ~]# echo 1 > /proc/sys/net/ipv4/ip_forward^C
[root@l1 ~]# sysctl -w net.ipv4.ip_forward=1
net.ipv4.ip_forward = 1
[root@l1 ~]#
只能临时生效,当你服务器重启又会被打回为0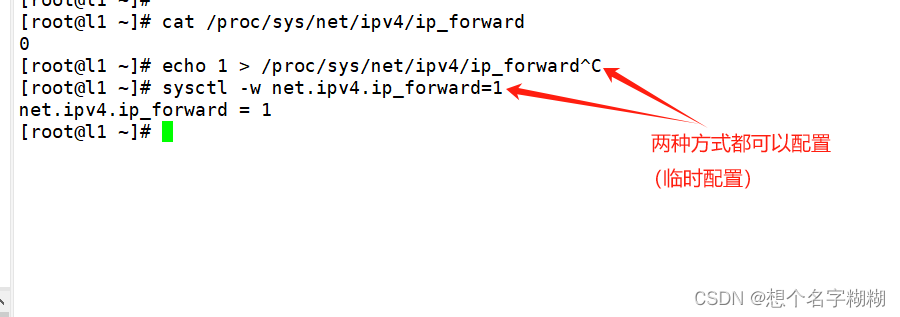
永久设置
[root@l1 ~]# vim /etc/sysctl.conf //这是我们的内核配置文件
[root@l1 ~]# 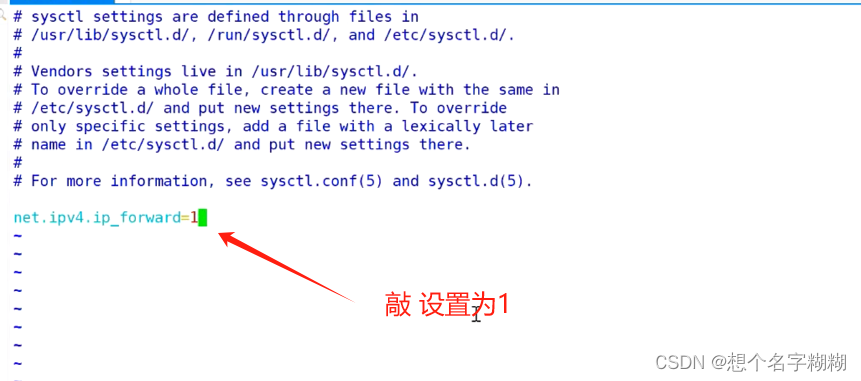
[root@l1 ~]# sysctl -p //加载配置文件的内核配置
net.ipv4.ip_forward = 1
[root@l1 ~]#
[root@l1 ~]# cat /proc/sys/net/ipv4/ip_forward
1
[root@l1 ~]# SNAT 转发

网关服务器

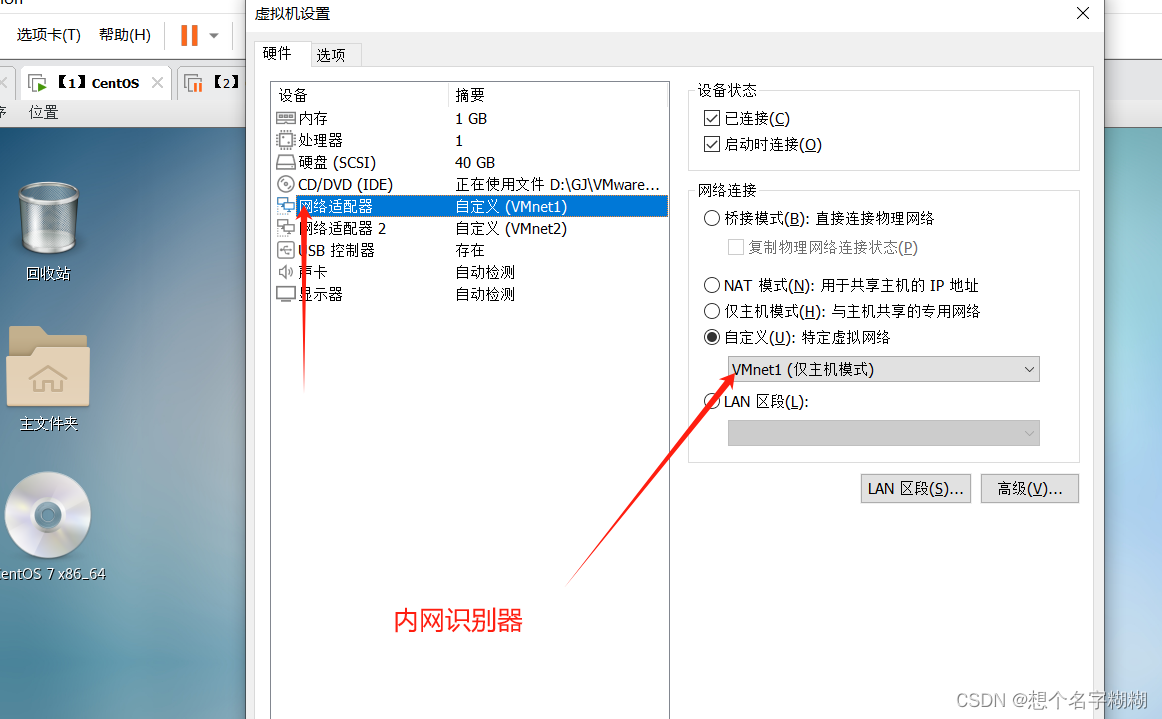
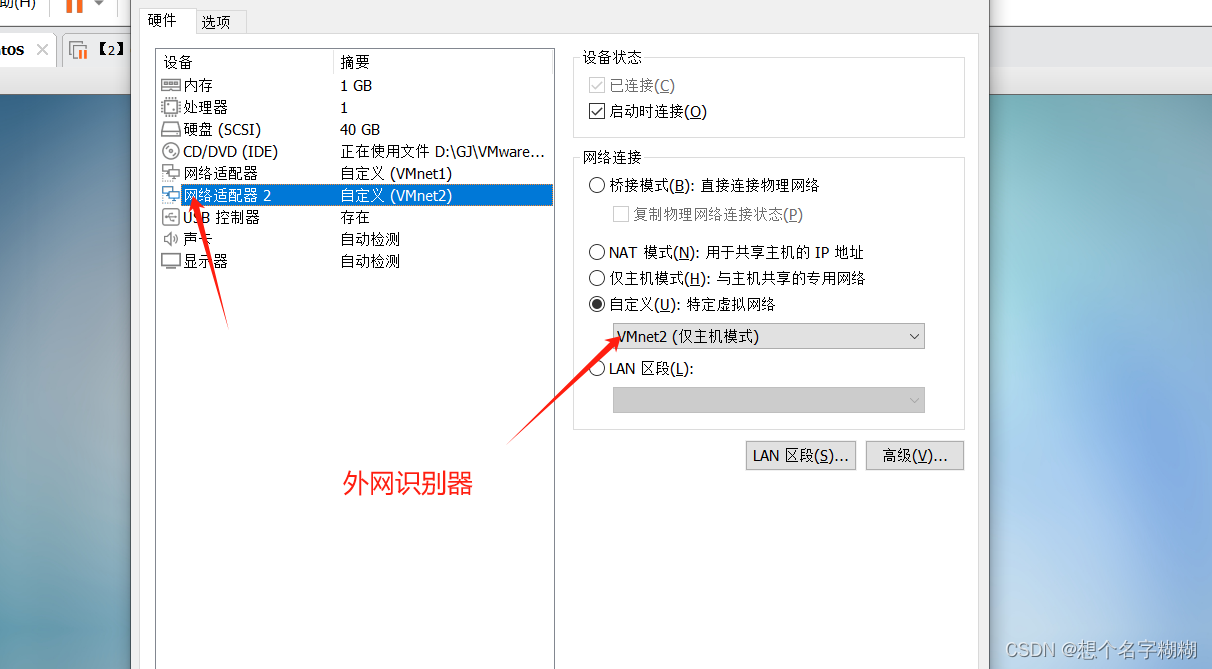
客户端 内网主机
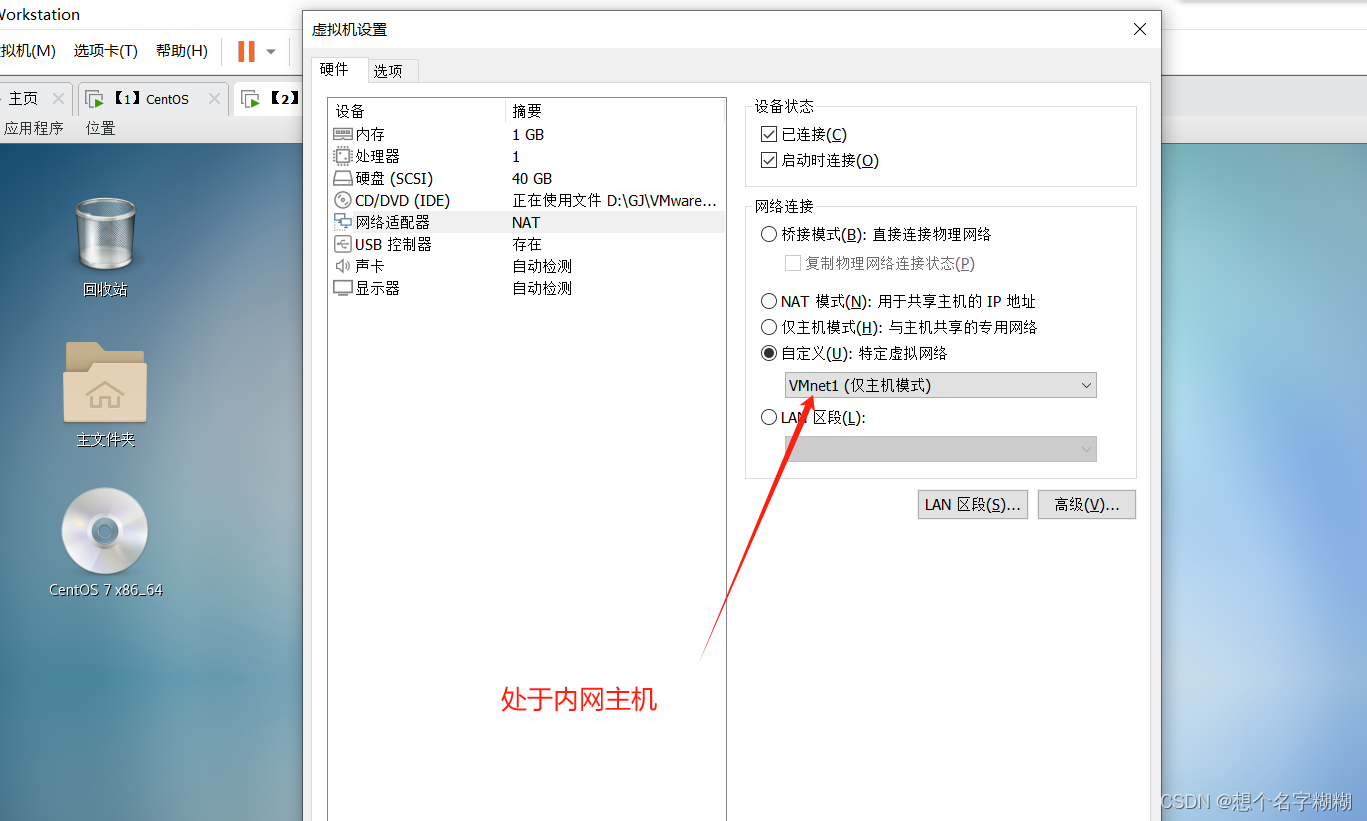 客户机2同上操作
客户机2同上操作
Web服务器 外网服务器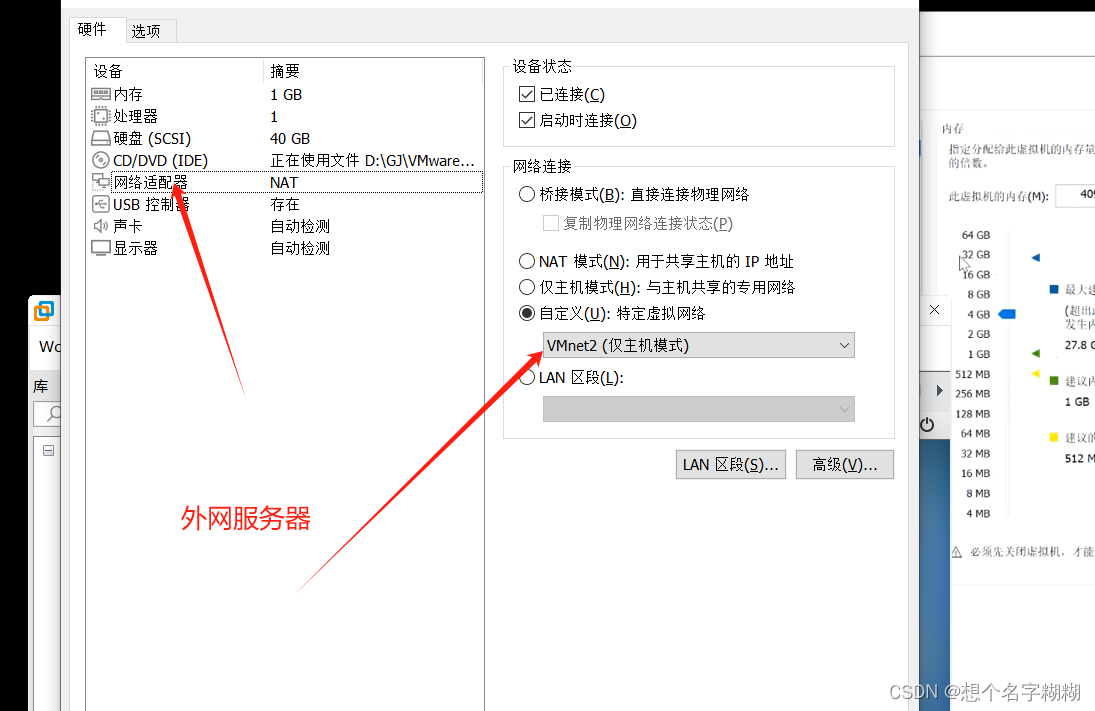
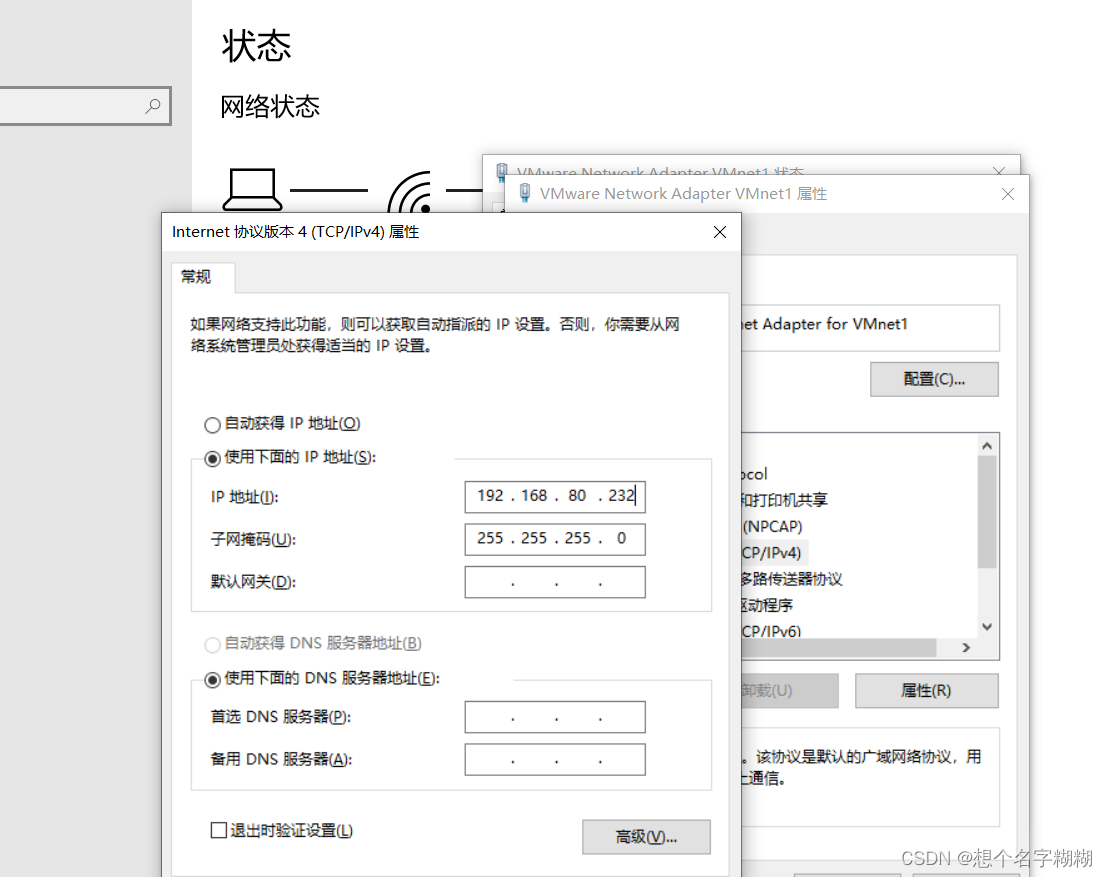 网关服务器配置
网关服务器配置
[root@l1 ~]# systemctl disable --now firewalld
[root@l1 ~]# yum install -y iptables iptables-services
已加载插件:fastestmirror, langpacks
Loading mirror speeds from cached hostfile
软件包 iptables-1.4.21-35.el7.x86_64 已安装并且是最新版本
软件包 iptables-services-1.4.21-35.el7.x86_64 已安装并且是最新版本
无须任何处理
[root@l1 ~]# systemctl start iptables
[root@l1 ~]# systemctl enable iptables
Created symlink from /etc/systemd/system/basic.target.wants/iptables.service to /usr/lib/systemd/system/iptables.service.
[root@l1 ~]# systemctl status iptables
● iptables.service - IPv4 firewall with iptablesLoaded: loaded (/usr/lib/systemd/system/iptables.service; enabled; vendor preset: disabled)Active: active (exited) since 四 2024-05-23 11:41:28 CST; 27s agoMain PID: 2582 (code=exited, status=0/SUCCESS)Tasks: 0CGroup: /system.slice/iptables.service5月 23 11:41:28 l1 systemd[1]: Starting IPv4 firewall with iptables...
5月 23 11:41:28 l1 iptables.init[2582]: iptables: Applying firewall rules: … ]
5月 23 11:41:28 l1 systemd[1]: Started IPv4 firewall with iptables.
Hint: Some lines were ellipsized, use -l to show in full.
[root@l1 ~]# iptables -nL
Chain INPUT (policy ACCEPT)
target prot opt source destination
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED
ACCEPT icmp -- 0.0.0.0/0 0.0.0.0/0
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22
REJECT all -- 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibitedChain FORWARD (policy ACCEPT)
target prot opt source destination
REJECT all -- 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibitedChain OUTPUT (policy ACCEPT)
target prot opt source destination
[root@l1 ~]# systemctl disable --now firewalld
[root@l1 ~]# yum install -y iptables iptables-services
已加载插件:faste[root@l1 network-scripts]# cd /etc/sysconfig/network-scripts/
[root@l1 network-scripts]# ls
ifcfg-ens33 ifdown-bnep ifdown-ipv6 ifdown-routes ifdown-tunnel ifup-eth ifup-isdn ifup-ppp ifup-TeamPort network-functions
ifcfg-lo ifdown-eth ifdown-isdn ifdown-sit ifup ifup-ib ifup-plip ifup-routes ifup-tunnel network-functions-ipv6
ifcfg-有线连接_1 ifdown-ib ifdown-post ifdown-Team ifup-aliases ifup-ippp ifup-plusb ifup-sit ifup-wireless route-有线连接_1
ifdown ifdown-ippp ifdown-ppp ifdown-TeamPort ifup-bnep ifup-ipv6 ifup-post ifup-Team init.ipv6-global
[root@l1 network-scripts]# vim ifcfg-ens33
[root@l1 network-scripts]#
[root@l1 network-scripts]# vim ifcfg-ens33
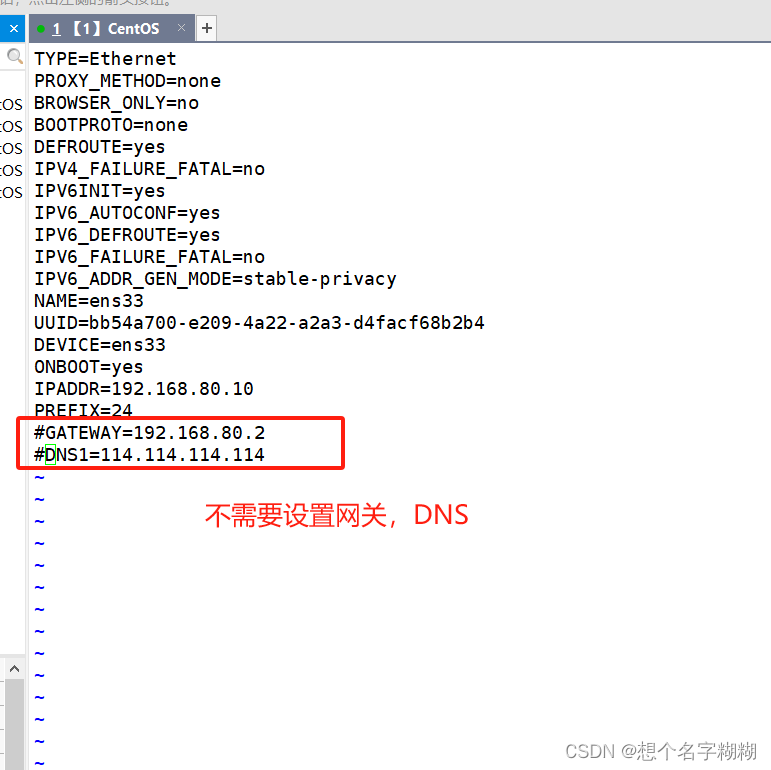
内网 ens33
[root@l1 network-scripts]# vim ifcfg-ens33
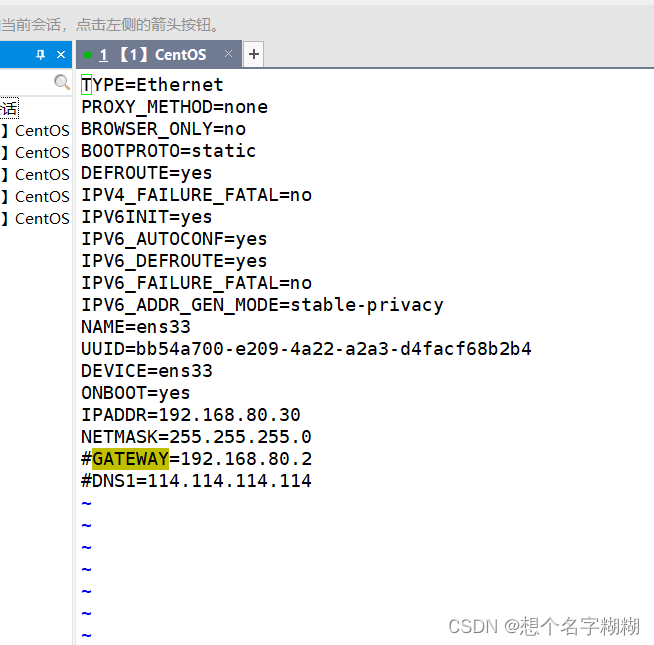
TYPE=Ethernet
PROXY_METHOD=none
BROWSER_ONLY=no
BOOTPROTO=static
DEFROUTE=yes
IPV4_FAILURE_FATAL=no
IPV6INIT=yes
IPV6_AUTOCONF=yes
IPV6_DEFROUTE=yes
IPV6_FAILURE_FATAL=no
IPV6_ADDR_GEN_MODE=stable-privacy
NAME=ens33
UUID=bb54a700-e209-4a22-a2a3-d4facf68b2b4
DEVICE=ens33
ONBOOT=yes
IPADDR=192.168.80.30
NETMASK=255.255.255.0
#GATEWAY=192.168.80.2
#DNS1=114.114.114.114
外网 ens36
[root@l1 network-scripts]# vim ifcfg-ens36
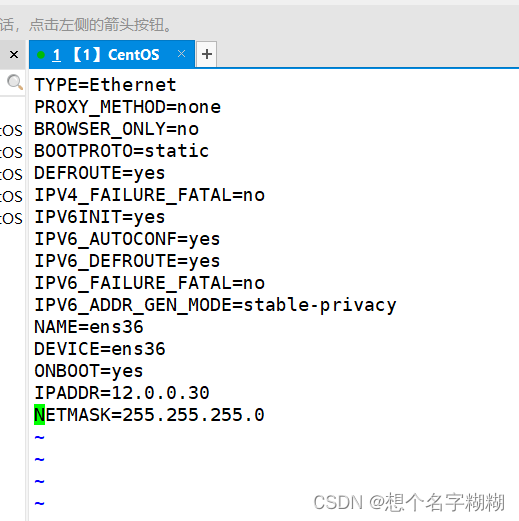
TYPE=Ethernet
PROXY_METHOD=none
BROWSER_ONLY=no
BOOTPROTO=static
DEFROUTE=yes
IPV4_FAILURE_FATAL=no
IPV6INIT=yes
IPV6_AUTOCONF=yes
IPV6_DEFROUTE=yes
IPV6_FAILURE_FATAL=no
IPV6_ADDR_GEN_MODE=stable-privacy
NAME=ens36
DEVICE=ens36
ONBOOT=yes
IPADDR=12.0.0.30
NETMASK=255.255.255.0
~ [root@l1 network-scripts]# systemctl restart network //重启网卡
[root@l1 ~]# sysctl -p
net.ipv4.ip_forward = 1
[root@l1 ~]# ifconfig
ens33: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500inet 192.168.80.30 netmask 255.255.255.0 broadcast 192.168.80.255inet6 fe80::523e:232a:d39b:b32f prefixlen 64 scopeid 0x20<link>ether 00:0c:29:87:fc:b2 txqueuelen 1000 (Ethernet)RX packets 397 bytes 34591 (33.7 KiB)RX errors 0 dropped 0 overruns 0 frame 0TX packets 413 bytes 35175 (34.3 KiB)TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0ens36: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500ether 00:0c:29:87:fc:bc txqueuelen 1000 (Ethernet)RX packets 23 bytes 2871 (2.8 KiB)RX errors 0 dropped 0 overruns 0 frame 0TX packets 475 bytes 78490 (76.6 KiB)TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536inet 127.0.0.1 netmask 255.0.0.0inet6 ::1 prefixlen 128 scopeid 0x10<host>loop txqueuelen 1000 (Local Loopback)RX packets 222 bytes 20050 (19.5 KiB)RX errors 0 dropped 0 overruns 0 frame 0TX packets 222 bytes 20050 (19.5 KiB)TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0virbr0: flags=4099<UP,BROADCAST,MULTICAST> mtu 1500inet 192.168.122.1 netmask 255.255.255.0 broadcast 192.168.122.255ether 52:54:00:cc:65:de txqueuelen 1000 (Ethernet)RX packets 0 bytes 0 (0.0 B)RX errors 0 dropped 0 overruns 0 frame 0TX packets 0 bytes 0 (0.0 B)TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0[root@l1 ~]# cd /etc/sysconfig/network-scripts/
[root@l1 network-scripts]# ls
ifcfg-ens33 ifdown-ppp ifup-ib ifup-Team
ifcfg-lo ifdown-routes ifup-ippp ifup-TeamPort
ifdown ifdown-sit ifup-ipv6 ifup-tunnel
ifdown-bnep ifdown-Team ifup-isdn ifup-wireless
ifdown-eth ifdown-TeamPort ifup-plip init.ipv6-global
ifdown-ib ifdown-tunnel ifup-plusb network-functions
ifdown-ippp ifup ifup-post network-functions-ipv6
ifdown-ipv6 ifup-aliases ifup-ppp
ifdown-isdn ifup-bnep ifup-routes
ifdown-post ifup-eth ifup-sit
[root@l1 network-scripts]# ifconfig
ens33: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500inet 192.168.80.30 netmask 255.255.255.0 broadcast 192.168.80.255inet6 fe80::523e:232a:d39b:b32f prefixlen 64 scopeid 0x20<link>ether 00:0c:29:87:fc:b2 txqueuelen 1000 (Ethernet)RX packets 464 bytes 39748 (38.8 KiB)RX errors 0 dropped 0 overruns 0 frame 0TX packets 476 bytes 44868 (43.8 KiB)TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0ens36: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500inet6 fe80::a0bd:6d4f:1a86:6806 prefixlen 64 scopeid 0x20<link>ether 00:0c:29:87:fc:bc txqueuelen 1000 (Ethernet)RX packets 24 bytes 3114 (3.0 KiB)RX errors 0 dropped 0 overruns 0 frame 0TX packets 504 bytes 82656 (80.7 KiB)TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536inet 127.0.0.1 netmask 255.0.0.0inet6 ::1 prefixlen 128 scopeid 0x10<host>loop txqueuelen 1000 (Local Loopback)RX packets 230 bytes 20682 (20.1 KiB)RX errors 0 dropped 0 overruns 0 frame 0TX packets 230 bytes 20682 (20.1 KiB)TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0virbr0: flags=4099<UP,BROADCAST,MULTICAST> mtu 1500inet 192.168.122.1 netmask 255.255.255.0 broadcast 192.168.122.255ether 52:54:00:cc:65:de txqueuelen 1000 (Ethernet)RX packets 0 bytes 0 (0.0 B)RX errors 0 dropped 0 overruns 0 frame 0TX packets 0 bytes 0 (0.0 B)TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0[root@l1 network-scripts]# vim ifcfg-ens3
[root@l1 network-scripts]# vim ifcfg-ens33
[root@l1 network-scripts]# ls
ifcfg-ens33 ifdown-ppp ifup-ib ifup-Team
ifcfg-lo ifdown-routes ifup-ippp ifup-TeamPort
ifdown ifdown-sit ifup-ipv6 ifup-tunnel
ifdown-bnep ifdown-Team ifup-isdn ifup-wireless
ifdown-eth ifdown-TeamPort ifup-plip init.ipv6-global
ifdown-ib ifdown-tunnel ifup-plusb network-functions
ifdown-ippp ifup ifup-post network-functions-ipv6
ifdown-ipv6 ifup-aliases ifup-ppp
ifdown-isdn ifup-bnep ifup-routes
ifdown-post ifup-eth ifup-sit
[root@l1 network-scripts]# ls
ifcfg-ens33 ifdown-ppp ifup-ib ifup-Team
ifcfg-lo ifdown-routes ifup-ippp ifup-TeamPort
ifdown ifdown-sit ifup-ipv6 ifup-tunnel
ifdown-bnep ifdown-Team ifup-isdn ifup-wireless
ifdown-eth ifdown-TeamPort ifup-plip init.ipv6-global
ifdown-ib ifdown-tunnel ifup-plusb network-functions
ifdown-ippp ifup ifup-post network-functions-ipv6
ifdown-ipv6 ifup-aliases ifup-ppp
ifdown-isdn ifup-bnep ifup-routes
ifdown-post ifup-eth ifup-sit
[root@l1 network-scripts]# vim ifcfg-ens33
[root@l1 network-scripts]# vim ifcfg-ens36
[root@l1 network-scripts]# vim ifcfg-ens36
[root@l1 network-scripts]# vim ifcfg-ens36
[root@l1 network-scripts]# vim ifcfg-ens33
[root@l1 network-scripts]# vim ifcfg-ens36
[root@l1 network-scripts]# vim ifcfg-ens36
[root@l1 network-scripts]# systemctl restart network
[root@l1 network-scripts]# ifc
ifcfg ifconfig
[root@l1 network-scripts]# ifconfig
ens33: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500inet 192.168.80.30 netmask 255.255.255.0 broadcast 192.168.80.255inet6 fe80::523e:232a:d39b:b32f prefixlen 64 scopeid 0x20<link>ether 00:0c:29:87:fc:b2 txqueuelen 1000 (Ethernet)RX packets 1527 bytes 125929 (122.9 KiB)RX errors 0 dropped 0 overruns 0 frame 0TX packets 1222 bytes 154371 (150.7 KiB)TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0ens36: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500inet 12.0.0.30 netmask 255.255.255.0 broadcast 12.0.0.255inet6 fe80::cfd7:6dd8:9716:71a3 prefixlen 64 scopeid 0x20<link>ether 00:0c:29:87:fc:bc txqueuelen 1000 (Ethernet)RX packets 25 bytes 3357 (3.2 KiB)RX errors 0 dropped 0 overruns 0 frame 0TX packets 631 bytes 103125 (100.7 KiB)TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536inet 127.0.0.1 netmask 255.0.0.0inet6 ::1 prefixlen 128 scopeid 0x10<host>loop txqueuelen 1000 (Local Loopback)RX packets 382 bytes 32994 (32.2 KiB)RX errors 0 dropped 0 overruns 0 frame 0TX packets 382 bytes 32994 (32.2 KiB)TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0virbr0: flags=4099<UP,BROADCAST,MULTICAST> mtu 1500inet 192.168.122.1 netmask 255.255.255.0 broadcast 192.168.122.255ether 52:54:00:cc:65:de txqueuelen 1000 (Ethernet)RX packets 0 bytes 0 (0.0 B)RX errors 0 dropped 0 overruns 0 frame 0TX packets 0 bytes 0 (0.0 B)TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0[root@l1 network-scripts]#
客户端 1
[root@l2 ~]# ifconfig
ens33: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500inet 192.168.18.20 netmask 255.255.255.0 broadcast 192.168.18.255inet6 fe80::ef42:44d7:112c:7393 prefixlen 64 scopeid 0x20<link>ether 00:0c:29:66:38:ff txqueuelen 1000 (Ethernet)RX packets 3908 bytes 3856097 (3.6 MiB)RX errors 0 dropped 0 overruns 0 frame 0TX packets 1554 bytes 116286 (113.5 KiB)TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536inet 127.0.0.1 netmask 255.0.0.0inet6 ::1 prefixlen 128 scopeid 0x10<host>loop txqueuelen 1000 (Local Loopback)RX packets 37 bytes 3812 (3.7 KiB)RX errors 0 dropped 0 overruns 0 frame 0TX packets 37 bytes 3812 (3.7 KiB)TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0virbr0: flags=4099<UP,BROADCAST,MULTICAST> mtu 1500inet 192.168.122.1 netmask 255.255.255.0 broadcast 192.168.122.255ether 52:54:00:0f:a7:1a txqueuelen 1000 (Ethernet)RX packets 0 bytes 0 (0.0 B)RX errors 0 dropped 0 overruns 0 frame 0TX packets 0 bytes 0 (0.0 B)TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0[root@l2 ~]# vim /etc/sysc vim /etc/sysc
还有 3 个文件等待编辑
[root@l2 ~]# vim /etc/sysc
[root@l2 ~]# vim /etc/sysconfig/network-scripts/ens33
[root@l2 ~]# vim /etc/sysconfig/network-scripts/ifcfg-ens33
[root@l2 ~]# systemctl restart network
[root@l2 ~]#
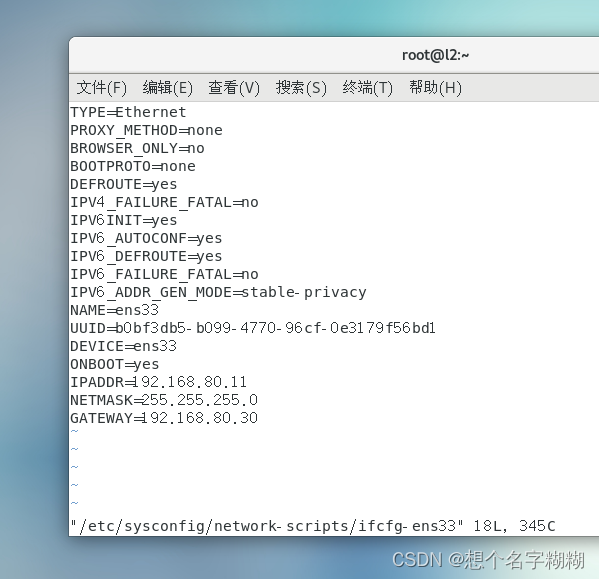
TYPE=Ethernet
PROXY_METHOD=none
BROWSER_ONLY=no
BOOTPROTO=none
DEFROUTE=yes
IPV4_FAILURE_FATAL=no
IPV6INIT=yes
IPV6_AUTOCONF=yes
IPV6_DEFROUTE=yes
IPV6_FAILURE_FATAL=no
IPV6_ADDR_GEN_MODE=stable-privacy
NAME=ens33
UUID=b0bf3db5-b099-4770-96cf-0e3179f56bd1
DEVICE=ens33
ONBOOT=yes
IPADDR=192.168.80.11
NETMASK=255.255.255.0
GATEWAY=192.168.80.30[root@l2 network-scripts]# systemctl restart network
[root@l2 network-scripts]#
[root@l2 network-scripts]# systemctl stop firewalld
[root@l2 network-scripts]# setenforce 0
[root@l2 network-scripts]#
客户端 2
[root@l3 ~]# cd
[root@l3 ~]# cd /etc//sysconfig/network-scripts/
[root@l3 network-scripts]# vim ifcfg-ens3
[root@l3 network-scripts]# vim ifcfg-ens33
[root@l3 network-scripts]# ls
ifcfg-ens33 ifdown-ppp ifup-ib ifup-Team
ifcfg-lo ifdown-routes ifup-ippp ifup-TeamPort
ifdown ifdown-sit ifup-ipv6 ifup-tunnel
ifdown-bnep ifdown-Team ifup-isdn ifup-wireless
ifdown-eth ifdown-TeamPort ifup-plip init.ipv6-global
ifdown-ib ifdown-tunnel ifup-plusb network-functions
ifdown-ippp ifup ifup-post network-functions-ipv6
ifdown-ipv6 ifup-aliases ifup-ppp
ifdown-isdn ifup-bnep ifup-routes
ifdown-post ifup-eth ifup-sit
[root@l3 network-scripts]# [root@l3 network-scripts]# ifconfig
ens33: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500inet 192.168.18.30 netmask 255.255.255.0 broadcast 192.168.18.255inet6 fe80::4367:bd86:d4c9:c296 prefixlen 64 scopeid 0x20<link>ether 00:0c:29:c9:0b:e0 txqueuelen 1000 (Ethernet)RX packets 383345 bytes 562327116 (536.2 MiB)RX errors 0 dropped 0 overruns 0 frame 0TX packets 51994 bytes 3184636 (3.0 MiB)TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536inet 127.0.0.1 netmask 255.0.0.0inet6 ::1 prefixlen 128 scopeid 0x10<host>loop txqueuelen 1000 (Local Loopback)RX packets 221 bytes 18940 (18.4 KiB)RX errors 0 dropped 0 overruns 0 frame 0TX packets 221 bytes 18940 (18.4 KiB)TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0virbr0: flags=4099<UP,BROADCAST,MULTICAST> mtu 1500inet 192.168.122.1 netmask 255.255.255.0 broadcast 192.168.122.255ether 52:54:00:1e:49:a2 txqueuelen 1000 (Ethernet)RX packets 0 bytes 0 (0.0 B)RX errors 0 dropped 0 overruns 0 frame 0TX packets 0 bytes 0 (0.0 B)TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0[root@l3 network-scripts]# cd /etc//sysconfig/network-scripts/
[root@l3 network-scripts]# vim ifcfg-ens33
[root@l3 network-scripts]# systemctl restart net
netcf-transaction.service network.service
network-online.target
[root@l3 network-scripts]# systemctl restart networkw
Failed to restart networkw.service: Unit not found.
[root@l3 network-scripts]# systemctl restart network
[root@l3 network-scripts]# 
TYPE=Ethernet
PROXY_METHOD=none
BROWSER_ONLY=no
BOOTPROTO=static
DEFROUTE=yes
IPV4_FAILURE_FATAL=no
IPV6INIT=yes
IPV6_AUTOCONF=yes
IPV6_DEFROUTE=yes
IPV6_FAILURE_FATAL=no
IPV6_ADDR_GEN_MODE=stable-privacy
NAME=ens33
UUID=518f05a5-256a-45cf-bf88-e8e365e57bff
DEVICE=ens33
ONBOOT=yes
IPADDR=192.168.80.20
NETMASK=255.255.255.0
GATEWAY=192.168.80.30
[root@l3 ~]# systemctl stop firewalld
[root@l3 ~]# setenforce 0
[root@l3 ~]#
客户机1 客户机2ping网关服务器
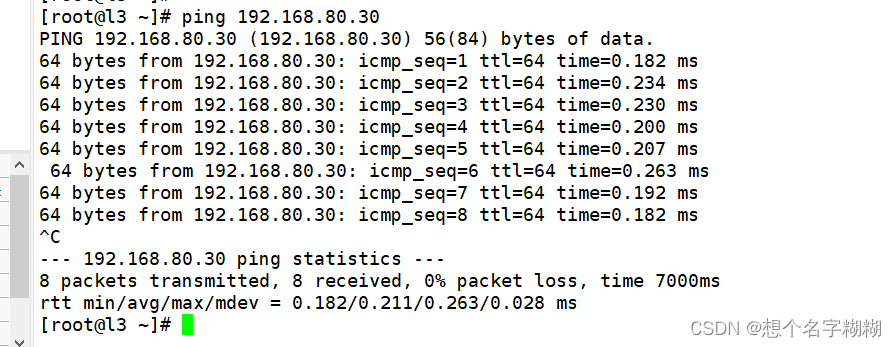

网关服务器 清空规则
[root@l1 network-scripts]# iptables -F
[root@l1 network-scripts]# iptables -nL
Chain INPUT (policy ACCEPT)
target prot opt source destination Chain FORWARD (policy ACCEPT)
target prot opt source destination Chain OUTPUT (policy ACCEPT)
target prot opt source destination
[root@l1 network-scripts]# iptables -t nat -F
[root@l1 network-scripts]# iptables -nL -t nat
Chain PREROUTING (policy ACCEPT)
target prot opt source destination Chain INPUT (policy ACCEPT)
target prot opt source destination Chain OUTPUT (policy ACCEPT)
target prot opt source destination Chain POSTROUTING (policy ACCEPT)
target prot opt source destination
[root@l1 network-scripts]# 外网服务器
[root@localhost network-scripts]# ifconfig
ens33: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500inet 12.0.0.12 netmask 255.255.255.0 broadcast 12.0.0.255inet6 fe80::149b:989c:c2fc:e0e0 prefixlen 64 scopeid 0x20<link>ether 00:0c:29:3d:ca:57 txqueuelen 1000 (Ethernet)RX packets 304 bytes 72391 (70.6 KiB)RX errors 0 dropped 0 overruns 0 frame 0TX packets 200 bytes 25274 (24.6 KiB)TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536inet 127.0.0.1 netmask 255.0.0.0inet6 ::1 prefixlen 128 scopeid 0x10<host>loop txqueuelen 1000 (Local Loopback)RX packets 1048 bytes 90856 (88.7 KiB)RX errors 0 dropped 0 overruns 0 frame 0TX packets 1048 bytes 90856 (88.7 KiB)TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0virbr0: flags=4099<UP,BROADCAST,MULTICAST> mtu 1500inet 192.168.122.1 netmask 255.255.255.0 broadcast 192.168.122.255ether 52:54:00:e5:c7:15 txqueuelen 1000 (Ethernet)RX packets 0 bytes 0 (0.0 B)RX errors 0 dropped 0 overruns 0 frame 0TX packets 0 bytes 0 (0.0 B)TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0[root@localhost network-scripts]# vim ifcfg-ens33
[root@localhost network-scripts]# systemctl restart network
[root@localhost network-scripts]# vim ifcfg-ens33
[root@localhost network-scripts]# ifconfig
ens33: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500inet 12.0.0.12 netmask 255.255.255.0 broadcast 12.0.0.255inet6 fe80::149b:989c:c2fc:e0e0 prefixlen 64 scopeid 0x20<link>ether 00:0c:29:3d:ca:57 txqueuelen 1000 (Ethernet)RX packets 304 bytes 72391 (70.6 KiB)RX errors 0 dropped 0 overruns 0 frame 0TX packets 239 bytes 30819 (30.0 KiB)TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536inet 127.0.0.1 netmask 255.0.0.0inet6 ::1 prefixlen 128 scopeid 0x10<host>loop txqueuelen 1000 (Local Loopback)RX packets 1184 bytes 102648 (100.2 KiB)RX errors 0 dropped 0 overruns 0 frame 0TX packets 1184 bytes 102648 (100.2 KiB)TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0virbr0: flags=4099<UP,BROADCAST,MULTICAST> mtu 1500inet 192.168.122.1 netmask 255.255.255.0 broadcast 192.168.122.255ether 52:54:00:e5:c7:15 txqueuelen 1000 (Ethernet)RX packets 0 bytes 0 (0.0 B)RX errors 0 dropped 0 overruns 0 frame 0TX packets 0 bytes 0 (0.0 B)TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
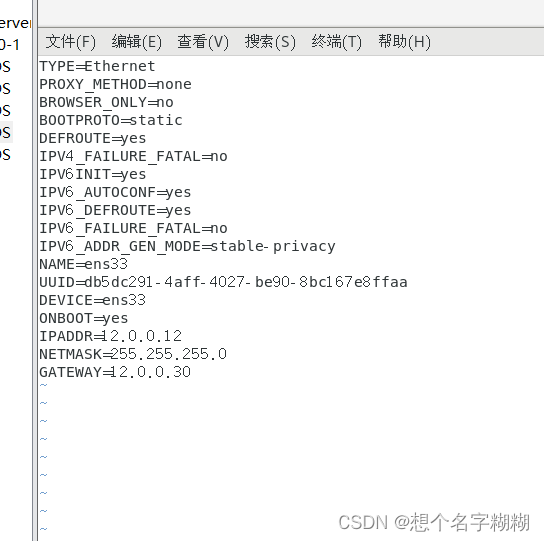
TYPE=Ethernet
PROXY_METHOD=none
BROWSER_ONLY=no
BOOTPROTO=static
DEFROUTE=yes
IPV4_FAILURE_FATAL=no
IPV6INIT=yes
IPV6_AUTOCONF=yes
IPV6_DEFROUTE=yes
IPV6_FAILURE_FATAL=no
IPV6_ADDR_GEN_MODE=stable-privacy
NAME=ens33
UUID=db5dc291-4aff-4027-be90-8bc167e8ffaa
DEVICE=ens33
ONBOOT=yes
IPADDR=12.0.0.12
NETMASK=255.255.255.0
GATEWAY=12.0.0.30
[root@localhost network-scripts]# systemctl restart network //重启网卡[root@l3 network-scripts]# systemctl stop firewalld //关闭防火墙
[root@l3 network-scripts]# setenforce 0
[root@l3 network-scripts]#
[root@localhost ~]# yum install -y httpd //下载软件httpd
已加载插件:fastestmirror, langpacks
Loading mirror speeds from cached hostfile
正在解决依赖关系
--> 正在检查事务
---> 软件包 httpd.x86_64.0.2.4.6-97.el7.centos.5 将被 安装
--> 正在处理依赖关系 httpd-tools = 2.4.6-97.el7.centos.5,它被软件包 httpd-2.4.6-97.el7.centos.5.x86_64 需要
--> 正在处理依赖关系 /etc/mime.types,它被软件包 httpd-2.4.6-97.el7.centos.5.x86_64 需要
--> 正在检查事务
---> 软件包 httpd-tools.x86_64.0.2.4.6-97.el7.centos.5 将被 安装
---> 软件包 mailcap.noarch.0.2.1.41-2.el7 将被 安装
--> 解决依赖关系完成依赖关系解决==================================================================Package 架构 版本 源 大小
==================================================================
正在安装:httpd x86_64 2.4.6-97.el7.centos.5 local 2.7 M
为依赖而安装:httpd-tools x86_64 2.4.6-97.el7.centos.5 local 94 kmailcap noarch 2.1.41-2.el7 local 31 k事务概要
==================================================================
安装 1 软件包 (+2 依赖软件包)总下载量:2.8 M
安装大小:9.6 M
Downloading packages:
------------------------------------------------------------------
总计 34 MB/s | 2.8 MB 00:00
Running transaction check
Running transaction test
Transaction test succeeded
Running transaction正在安装 : httpd-tools-2.4.6-97.el7.centos.5.x86_64 1/3 正在安装 : mailcap-2.1.41-2.el7.noarch 2/3 正在安装 : httpd-2.4.6-97.el7.centos.5.x86_64 3/3 验证中 : mailcap-2.1.41-2.el7.noarch 1/3 验证中 : httpd-tools-2.4.6-97.el7.centos.5.x86_64 2/3 验证中 : httpd-2.4.6-97.el7.centos.5.x86_64 3/3 已安装:httpd.x86_64 0:2.4.6-97.el7.centos.5 作为依赖被安装:httpd-tools.x86_64 0:2.4.6-97.el7.centos.5 mailcap.noarch 0:2.1.41-2.el7 完毕!
[root@localhost [root@localhost ~]# systemctl start httpd
[root@localhost ~]# netstat -lntp | grep :80 //阿帕奇端口已开启
tcp6 0 0 :::80 :::* LISTEN 61993/httpd
[root@localhost ~]#
已经全部配置好,现在开始验证
网关服务器
[root@l1 network-scripts]# ping 192.168.80.30
PING 192.168.80.30 (192.168.80.30) 56(84) bytes of data.
64 bytes from 192.168.80.30: icmp_seq=1 ttl=64 time=0.061 ms
64 bytes from 192.168.80.30: icmp_seq=2 ttl=64 time=0.041 ms
64 bytes from 192.168.80.30: icmp_seq=3 ttl=64 time=0.042 ms
64 bytes from 192.168.80.30: icmp_seq=4 ttl=64 time=0.065 ms
64 bytes from 192.168.80.30: icmp_seq=5 ttl=64 time=0.043 ms
64 bytes from 192.168.80.30: icmp_seq=6 ttl=64 time=0.043 ms
64 bytes from 192.168.80.30: icmp_seq=7 ttl=64 time=0.052 ms
64 bytes from 192.168.80.30: icmp_seq=8 ttl=64 time=0.045 ms
64 bytes from 192.168.80.30: icmp_seq=9 ttl=64 time=0.043 ms
64 bytes from 192.168.80.30: icmp_seq=10 ttl=64 time=0.043 ms
[root@l1 network-scripts]# ping 12.0.0.30
PING 12.0.0.30 (12.0.0.30) 56(84) bytes of data.
64 bytes from 12.0.0.30: icmp_seq=1 ttl=64 time=0.025 ms
64 bytes from 12.0.0.30: icmp_seq=2 ttl=64 time=0.043 ms
64 bytes from 12.0.0.30: icmp_seq=3 ttl=64 time=0.042 ms
64 bytes from 12.0.0.30: icmp_seq=4 ttl=64 time=0.041 ms
64 bytes from 12.0.0.30: icmp_seq=5 ttl=64 time=0.039 ms
64 bytes from 12.0.0.30: icmp_seq=6 ttl=64 time=0.041 ms
64 bytes from 12.0.0.30: icmp_seq=7 ttl=64 time=0.044 ms
64 bytes from 12.0.0.30: icmp_seq=8 ttl=64 time=0.041 ms
^C
--- 12.0.0.30 ping statistics ---
8 packets transmitted, 8 received, 0% packet loss, time 6999ms
rtt min/avg/max/mdev = 0.025/0.039/0.044/0.008 ms
[root@l1 network-scripts]#
都可以ping通
网关服务器

 =0 ping不通
=0 ping不通
客户端1
[root@l2 ~]#
[root@l2 ~]# ping 192.168.80.30
PING 192.168.80.30 (192.168.80.30) 56(84) bytes of data.
64 bytes from 192.168.80.30: icmp_seq=1 ttl=64 time=0.273 ms
64 bytes from 192.168.80.30: icmp_seq=2 ttl=64 time=0.182 ms
64 bytes from 192.168.80.30: icmp_seq=3 ttl=64 time=0.293 ms
64 bytes from 192.168.80.30: icmp_seq=4 ttl=64 time=0.173 ms
^C
--- 192.168.80.30 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3000ms
rtt min/avg/max/mdev = 0.173/0.230/0.293/0.054 ms
[root@l2 ~]# ping 12.0.0.30
PING 12.0.0.30 (12.0.0.30) 56(84) bytes of data.
64 bytes from 12.0.0.30: icmp_seq=1 ttl=64 time=0.214 ms
64 bytes from 12.0.0.30: icmp_seq=2 ttl=64 time=0.177 ms
64 bytes from 12.0.0.30: icmp_seq=3 ttl=64 time=0.245 ms
64 bytes from 12.0.0.30: icmp_seq=4 ttl=64 time=0.229 ms
64 bytes from 12.0.0.30: icmp_seq=5 ttl=64 time=0.262 ms
^C
--- 12.0.0.30 ping statistics ---
5 packets transmitted, 5 received, 0% packet loss, time 3999ms
rtt min/avg/max/mdev = 0.177/0.225/0.262/0.031 ms
[root@l2 ~]# ping 12.0.0.12
PING 12.0.0.12 (12.0.0.12) 56(84) bytes of data.
64 bytes from 12.0.0.12: icmp_seq=1 ttl=63 time=1.06 ms
64 bytes from 12.0.0.12: icmp_seq=2 ttl=63 time=0.850 ms
64 bytes from 12.0.0.12: icmp_seq=3 ttl=63 time=0.485 ms
64 bytes from 12.0.0.12: icmp_seq=4 ttl=63 time=2.03 ms
64 bytes from 12.0.0.12: icmp_seq=5 ttl=63 time=0.392 ms
^C
--- 12.0.0.12 ping statistics ---
5 packets transmitted, 5 received, 0% packet loss, time 4003ms
rtt min/avg/max/mdev = 0.392/0.966/2.034/0.587 ms
[root@l2 ~]#
外网服务器
客户端1
[root@l2 ~]# ping 12.0.0.12
PING 12.0.0.12 (12.0.0.12) 56(84) bytes of data.
64 bytes from 12.0.0.12: icmp_seq=1 ttl=63 time=0.635 ms
64 bytes from 12.0.0.12: icmp_seq=2 ttl=63 time=0.417 ms
64 bytes from 12.0.0.12: icmp_seq=3 ttl=63 time=0.471 ms
64 bytes from 12.0.0.12: icmp_seq=4 ttl=63 time=1.83 ms
64 bytes from 12.0.0.12: icmp_seq=5 ttl=63 time=0.668 ms
64 bytes from 12.0.0.12: icmp_seq=6 ttl=63 time=0.469 ms
64 bytes from 12.0.0.12: icmp_seq=7 ttl=63 time=3.92 ms
64 bytes from 12.0.0.12: icmp_seq=8 ttl=63 time=5.65 ms
64 bytes from 12.0.0.12: icmp_seq=9 ttl=63 time=0.438 ms
64 bytes from 12.0.0.12: icmp_seq=10 ttl=63 time=0.556 ms
64 bytes from 12.0.0.12: icmp_seq=11 ttl=63 time=0.437 ms
64 bytes from 12.0.0.12: icmp_seq=12 ttl=63 time=0.338 ms
64 bytes from 12.0.0.12: icmp_seq=13 ttl=63 time=0.348 ms
64 bytes from 12.0.0.12: icmp_seq=14 ttl=63 time=0.409 ms
64 bytes from 12.0.0.12: icmp_seq=15 ttl=63 time=0.583 ms
64 bytes from 12.0.0.12: icmp_seq=16 ttl=63 time=0.474 ms
^C
--- 12.0.0.12 ping statistics ---
16 packets transmitted, 16 received, 0% packet loss, time 15010ms
rtt min/avg/max/mdev = 0.338/1.103/5.652/1.465 ms
[root@l2 ~]#
外网服务器


[root@localhost ~]# tcpdump -i ens33 -s 0 -w ./test1.cap
tcpdump: listening on ens33, link-type EN10MB (Ethernet), capture size 262144 bytes
^C196 packets captured
198 packets received by filter
0 packets dropped by kernel
[root@localhost ~]# ls
anaconda-ks.cfg test1.cap 模板 图片 下载 桌面
initial-setup-ks.cfg 公共 视频 文档 音乐
[root@localhost ~]# sz test1.cap
[root@localhost ~]#


真实环境中 客户端192.168.80.11 无法ping通 外网服务器12.0.0.12
网关服务器

[root@l1 ~]# iptables -F nat
iptables: No chain/target/match by that name.
[root@l1 ~]# iptables -t nat -F
[root@l1 ~]# iptables -t nat -A POSTROUTING -s 192.168.80.0/24 -o ens36 -j SNAT --to 12.0.0.30
[root@l1 ~]# iptables -t nat -nL
Chain PREROUTING (policy ACCEPT)
target prot opt source destination Chain INPUT (policy ACCEPT)
target prot opt source destination Chain OUTPUT (policy ACCEPT)
target prot opt source destination Chain POSTROUTING (policy ACCEPT)
target prot opt source destination
SNAT all -- 192.168.80.0/24 0.0.0.0/0 to:12.0.0.30
[root@l1 ~]# 外网服务器
[root@localhost ~]# tcpdump -i ens33 -s 0 -w ./test2.cap //抓包到test2.cap文件
tcpdump: listening on ens33, link-type EN10MB (Ethernet), capture size 262144 bytes
^C26 packets captured
客户端1
[root@l2 ~]# ping -c 10 12.0.0.12 //ping十个包
PING 12.0.0.12 (12.0.0.12) 56(84) bytes of data.
64 bytes from 12.0.0.12: icmp_seq=1 ttl=63 time=0.440 ms
64 bytes from 12.0.0.12: icmp_seq=2 ttl=63 time=0.373 ms
64 bytes from 12.0.0.12: icmp_seq=3 ttl=63 time=0.362 ms
64 bytes from 12.0.0.12: icmp_seq=4 ttl=63 time=0.455 ms
64 bytes from 12.0.0.12: icmp_seq=5 ttl=63 time=0.468 ms
64 bytes from 12.0.0.12: icmp_seq=6 ttl=63 time=0.553 ms
64 bytes from 12.0.0.12: icmp_seq=7 ttl=63 time=0.427 ms
64 bytes from 12.0.0.12: icmp_seq=8 ttl=63 time=0.406 ms
64 bytes from 12.0.0.12: icmp_seq=9 ttl=63 time=0.648 ms
64 bytes from 12.0.0.12: icmp_seq=10 ttl=63 time=0.359 ms--- 12.0.0.12 ping statistics ---
10 packets transmitted, 10 received, 0% packet loss, time 9001ms
rtt min/avg/max/mdev = 0.359/0.449/0.648/0.086 ms
[root@l2 ~]#
外网服务器导出
[root@localhost ~]# sz test2.cap
[root@localhost ~]#  总结
总结
网关主机 ens33(左,连接内网)192.168.80.30 ens36(右,连接外网)12.0.0.30
客户端1 设置ip地址为192.168.80.11 网关为ens33 192.168.80.30
客户端2 设置ip地址为192.168.80.20 网关为ens33 192.168.80.30
外网服务器 ip 12.0.0.12 网关为ens36 12.0.0.30
SNAT 内网 --> 外网 转换源地址
iptables -t nat -A POSTROUTING -s 内网的源地址/网段 -o 出站网卡 -j SNAT --to 要转换的公网源地址
实验2 DNAT



DNAT 外网 --> 内网 转换目的地址:端口
iptables -t nat -A PREROUTING -i 入站网卡 -d 原公网目的地址 -p 协议 --dport 原目的端口 -j DNAT --to 要转换的内网目的地址:端口
原 网站服务器 放入内网
原来 内网主机 放进 外网

二号机同上操作
客户机
客户机1
[root@l2 ~]# cd /etc/sysconfig/network-scripts/
[root@l2 network-scripts]#
[root@l2 network-scripts]# vim ifcfg-ens33
TYPE=Ethernet
PROXY_METHOD=none
BROWSER_ONLY=no
BOOTPROTO=none
DEFROUTE=yes
IPV4_FAILURE_FATAL=no
IPV6INIT=yes
IPV6_AUTOCONF=yes
IPV6_DEFROUTE=yes
IPV6_FAILURE_FATAL=no
IPV6_ADDR_GEN_MODE=stable-privacy
NAME=ens33
UUID=b0bf3db5-b099-4770-96cf-0e3179f56bd1
DEVICE=ens33
ONBOOT=yes
IPADDR=12.0.0.100
NETMASK=255.255.255.0
GATEWAY=12.0.0.30
[root@l2 network-scripts]# systemctl restart network //重启网卡
[root@l2 network-scripts]#
[root@l2 network-scripts]# ifconfig
ens33: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500inet 12.0.0.100 netmask 255.255.255.0 broadcast 12.0.0.255inet6 fe80::ef42:44d7:112c:7393 prefixlen 64 scopeid 0x20<link>ether 00:0c:29:66:38:ff txqueuelen 1000 (Ethernet)RX packets 6110 bytes 4044553 (3.8 MiB)RX errors 0 dropped 0 overruns 0 frame 0TX packets 3032 bytes 250886 (245.0 KiB)TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536inet 127.0.0.1 netmask 255.0.0.0inet6 ::1 prefixlen 128 scopeid 0x10<host>loop txqueuelen 1000 (Local Loopback)RX packets 156 bytes 14364 (14.0 KiB)RX errors 0 dropped 0 overruns 0 frame 0TX packets 156 bytes 14364 (14.0 KiB)TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0virbr0: flags=4099<UP,BROADCAST,MULTICAST> mtu 1500inet 192.168.122.1 netmask 255.255.255.0 broadcast 192.168.122.255ether 52:54:00:0f:a7:1a txqueuelen 1000 (Ethernet)RX packets 0 bytes 0 (0.0 B)RX errors 0 dropped 0 overruns 0 frame 0TX packets 0 bytes 0 (0.0 B)TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0[root@l2 network-scripts]#
客户机2
[root@l3 ~]# cd /etc/sysconfig/network-scripts/
[root@l3 network-scripts]# vim ifcfg-ens33
[root@l3 network-scripts]#

TYPE=Ethernet
PROXY_METHOD=none
BROWSER_ONLY=no
BOOTPROTO=static
DEFROUTE=yes
IPV4_FAILURE_FATAL=no
IPV6INIT=yes
IPV6_AUTOCONF=yes
IPV6_DEFROUTE=yes
IPV6_FAILURE_FATAL=no
IPV6_ADDR_GEN_MODE=stable-privacy
NAME=ens33
UUID=518f05a5-256a-45cf-bf88-e8e365e57bff
DEVICE=ens33
ONBOOT=yes
IPADDR=12.0.0.200
NETMASK=255.255.255.0
GATEWAY=12.0.0.30[root@l3 network-scripts]# systemctl restart network
[root@l3 network-scripts]# ifc
ifcfg ifconfig
[root@l3 network-scripts]# ifconfig
ens33: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500inet 12.0.0.200 netmask 255.255.255.0 broadcast 12.0.0.255inet6 fe80::4367:bd86:d4c9:c296 prefixlen 64 scopeid 0x20<link>ether 00:0c:29:c9:0b:e0 txqueuelen 1000 (Ethernet)RX packets 384632 bytes 562440735 (536.3 MiB)RX errors 0 dropped 0 overruns 0 frame 0TX packets 52970 bytes 3261985 (3.1 MiB)TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536inet 127.0.0.1 netmask 255.0.0.0inet6 ::1 prefixlen 128 scopeid 0x10<host>loop txqueuelen 1000 (Local Loopback)RX packets 368 bytes 32328 (31.5 KiB)RX errors 0 dropped 0 overruns 0 frame 0TX packets 368 bytes 32328 (31.5 KiB)TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0virbr0: flags=4099<UP,BROADCAST,MULTICAST> mtu 1500inet 192.168.122.1 netmask 255.255.255.0 broadcast 192.168.122.255ether 52:54:00:1e:49:a2 txqueuelen 1000 (Ethernet)RX packets 0 bytes 0 (0.0 B)RX errors 0 dropped 0 overruns 0 frame 0TX packets 0 bytes 0 (0.0 B)TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0[root@l3 network-scripts]#
服务器
[root@localhost network-scripts]# cd /etc/sysconfig/network-scripts/
[root@localhost network-scripts]# vim ifcfg-ens33 
TYPE=Ethernet
PROXY_METHOD=none
BROWSER_ONLY=no
BOOTPROTO=static
DEFROUTE=yes
IPV4_FAILURE_FATAL=no
IPV6INIT=yes
IPV6_AUTOCONF=yes
IPV6_DEFROUTE=yes
IPV6_FAILURE_FATAL=no
IPV6_ADDR_GEN_MODE=stable-privacy
NAME=ens33
UUID=db5dc291-4aff-4027-be90-8bc167e8ffaa
DEVICE=ens33
ONBOOT=yes
IPADDR=192.168.80.15
NETMASK=255.255.255.0
GATEWAY=192.168.80.30
[root@localhost network-scripts]# systemctl restart network
[root@localhost network-scripts]# ifconfig
ens33: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500inet 192.168.80.15 netmask 255.255.255.0 broadcast 192.168.80.255inet6 fe80::149b:989c:c2fc:e0e0 prefixlen 64 scopeid 0x20<link>ether 00:0c:29:3d:ca:57 txqueuelen 1000 (Ethernet)RX packets 1830 bytes 216003 (210.9 KiB)RX errors 0 dropped 0 overruns 0 frame 0TX packets 1480 bytes 184556 (180.2 KiB)TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536inet 127.0.0.1 netmask 255.0.0.0inet6 ::1 prefixlen 128 scopeid 0x10<host>loop txqueuelen 1000 (Local Loopback)RX packets 2420 bytes 209820 (204.9 KiB)RX errors 0 dropped 0 overruns 0 frame 0TX packets 2420 bytes 209820 (204.9 KiB)TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0virbr0: flags=4099<UP,BROADCAST,MULTICAST> mtu 1500inet 192.168.122.1 netmask 255.255.255.0 broadcast 192.168.122.255ether 52:54:00:e5:c7:15 txqueuelen 1000 (Ethernet)RX packets 0 bytes 0 (0.0 B)RX errors 0 dropped 0 overruns 0 frame 0TX packets 0 bytes 0 (0.0 B)TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0[root@localhost network-scripts]#
[root@localhost network-scripts]# systemctl restart httpd
[root@localhost network-scripts]#
准备一个DNS服务器给外网客户端使用
[root@l1 ~]# yum install -y bind
已加载插件:fastestmirror, langpacks
Loading mirror speeds from cached hostfile
正在解决依赖关系
--> 正在检查事务
---> 软件包 bind.x86_64.32.9.11.4-26.P2.el7_9.9 将被 安装
--> 解决依赖关系完成依赖关系解决=================================================================================Package 架构 版本 源 大小
=================================================================================
正在安装:bind x86_64 32:9.11.4-26.P2.el7_9.9 local 2.3 M事务概要
=================================================================================
安装 1 软件包总下载量:2.3 M
安装大小:5.4 M
Downloading packages:
Running transaction check
Running transaction test
Transaction test succeeded
Running transaction正在安装 : 32:bind-9.11.4-26.P2.el7_9.9.x86_64 1/1 验证中 : 32:bind-9.11.4-26.P2.el7_9.9.x86_64 1/1 已安装:bind.x86_64 32:9.11.4-26.P2.el7_9.9 完毕!
[root@l1 ~]#
如果下载报错

[root@l1 ~]# vim /etc/named.conf
[root@l1 ~]#

[root@l1 ~]# vim /etc/named.rfc1912.zones
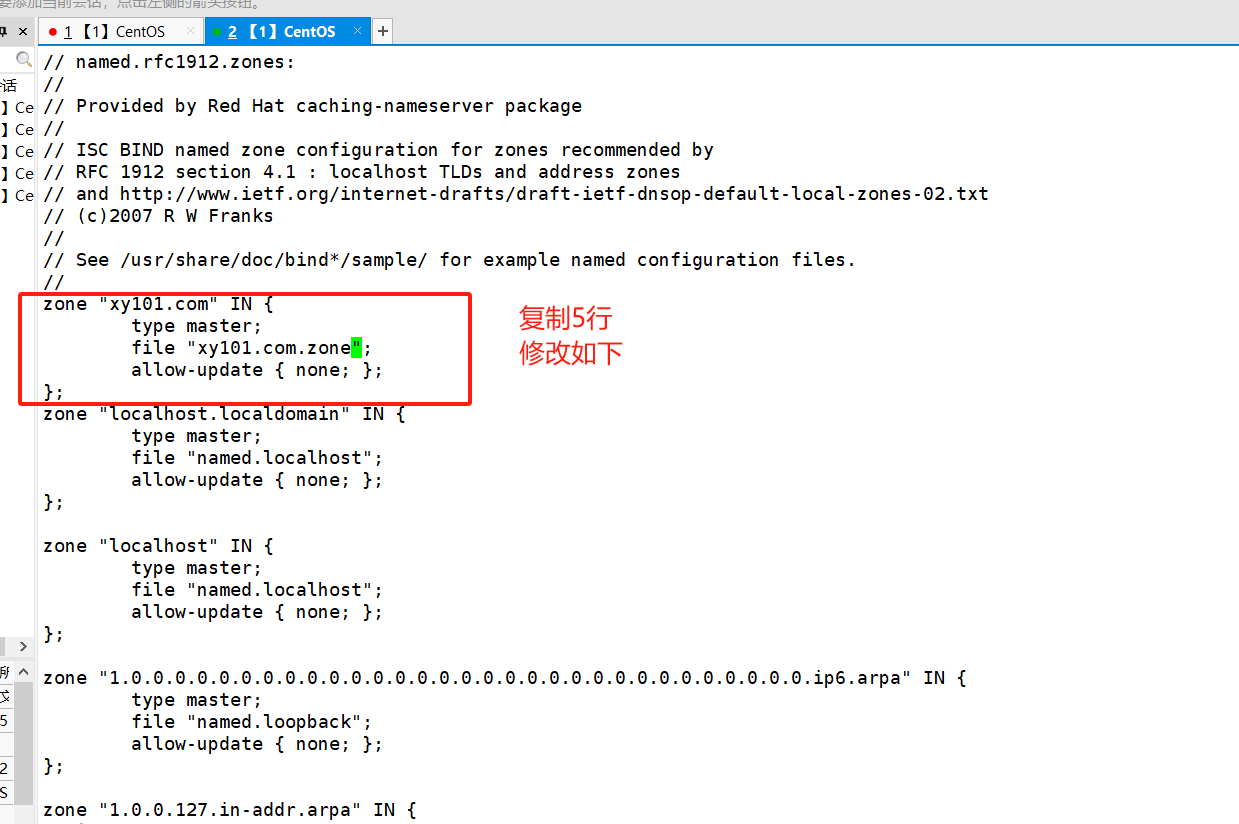
[root@l1 ~]# cd /var/named/
[root@l1 named]# ll
总用量 16
drwxrwx---. 2 named named 6 2月 24 2022 data
drwxrwx---. 2 named named 6 2月 24 2022 dynamic
-rw-r-----. 1 root named 2253 4月 5 2018 named.ca
-rw-r-----. 1 root named 152 12月 15 2009 named.empty
-rw-r-----. 1 root named 152 6月 21 2007 named.localhost
-rw-r-----. 1 root named 168 12月 15 2009 named.loopback
drwxrwx---. 2 named named 6 2月 24 2022 slaves
[root@l1 named]# cp -p named.localhost xy101.com.zone
[root@l1 named]# vim !$
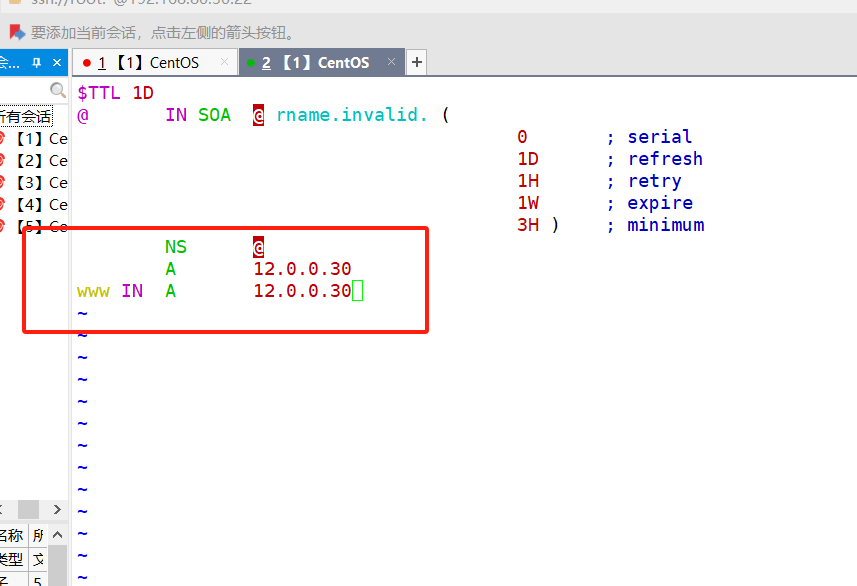
[root@l1 named]# systemctl start named
[root@l1 named]# systemctl enable named
Created symlink from /etc/systemd/system/multi-user.target.wants/named.service to /usr/lib/systemd/system/named.service.
[root@l1 named]#
开始验证
客户机1
[root@l2 network-scripts]# vim /etc/resolv.conf

[root@l2 network-scripts]# nslookup www.xy101.com
Server: 12.0.0.30
Address: 12.0.0.30#53Name: www.xy101.com
Address: 12.0.0.30[root@l2 network-scripts]#
网关服务器
[root@l1 named]# sysctl -p
net.ipv4.ip_forward = 1
[root@l1 named]#
客户机ping网关验证
[root@l2 network-scripts]# ping 192.168.80.30
PING 192.168.80.30 (192.168.80.30) 56(84) bytes of data.
64 bytes from 192.168.80.30: icmp_seq=1 ttl=64 time=0.276 ms
64 bytes from 192.168.80.30: icmp_seq=2 ttl=64 time=0.238 ms
64 bytes from 192.168.80.30: icmp_seq=3 ttl=64 time=0.241 ms
^C
--- 192.168.80.30 ping statistics ---
3 packets transmitted, 3 received, 0% packet loss, time 1999ms
rtt min/avg/max/mdev = 0.238/0.251/0.276/0.025 ms
[root@l2 network-scripts]#
[root@l2 network-scripts]#
[root@l2 network-scripts]# ping 12.0.0.30
PING 12.0.0.30 (12.0.0.30) 56(84) bytes of data.
64 bytes from 12.0.0.30: icmp_seq=1 ttl=64 time=0.249 ms
64 bytes from 12.0.0.30: icmp_seq=2 ttl=64 time=0.181 ms
64 bytes from 12.0.0.30: icmp_seq=3 ttl=64 time=0.203 ms
64 bytes from 12.0.0.30: icmp_seq=4 ttl=64 time=0.230 ms
64 bytes from 12.0.0.30: icmp_seq=5 ttl=64 time=0.251 ms
^C
--- 12.0.0.30 ping statistics ---
5 packets transmitted, 5 received, 0% packet loss, time 4000ms
rtt min/avg/max/mdev = 0.181/0.222/0.251/0.033 ms
[root@l2 network-scripts]# [root@l2 network-scripts]# ping 12.0.0.100
PING 12.0.0.100 (12.0.0.100) 56(84) bytes of data.
64 bytes from 12.0.0.100: icmp_seq=1 ttl=64 time=0.036 ms
64 bytes from 12.0.0.100: icmp_seq=2 ttl=64 time=0.029 ms
64 bytes from 12.0.0.100: icmp_seq=3 ttl=64 time=0.023 ms
^C
--- 12.0.0.100 ping statistics ---
3 packets transmitted, 3 received, 0% packet loss, time 2000ms
rtt min/avg/max/mdev = 0.023/0.029/0.036/0.006 ms
[root@l2 network-scripts]#
[root@l2 network-scripts]# ping 12.0.0.200
PING 12.0.0.200 (12.0.0.200) 56(84) bytes of data.
64 bytes from 12.0.0.200: icmp_seq=1 ttl=64 time=0.276 ms
64 bytes from 12.0.0.200: icmp_seq=2 ttl=64 time=0.220 ms
64 bytes from 12.0.0.200: icmp_seq=3 ttl=64 time=0.210 ms
64 bytes from 12.0.0.200: icmp_seq=4 ttl=64 time=0.224 ms
^C
--- 12.0.0.200 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3000ms
rtt min/avg/max/mdev = 0.210/0.232/0.276/0.029 ms
[root@l2 network-scripts]#
下面开始做DNAT转换

网关服务器
[root@l1 named]# iptables -nL
Chain INPUT (policy ACCEPT)
target prot opt source destination Chain FORWARD (policy ACCEPT)
target prot opt source destination Chain OUTPUT (policy ACCEPT)
target prot opt source destination
[root@l1 named]# iptables -nL -t nat
Chain PREROUTING (policy ACCEPT)
target prot opt source destination Chain INPUT (policy ACCEPT)
target prot opt source destination Chain OUTPUT (policy ACCEPT)
target prot opt source destination Chain POSTROUTING (policy ACCEPT)
target prot opt source destination
SNAT all -- 192.168.80.0/24 0.0.0.0/0 to:12.0.0.30
[root@l1 named]#
[root@l1 named]# iptables -t nat -A PREROUTING -i ens33 -d 12.0.0.30 -p tcp --dport 80 -j DNAT --to 192.168.80.15:80
[root@l1 named]# iptables -nL -t nat
Chain PREROUTING (policy ACCEPT)
target prot opt source destination
DNAT tcp -- 0.0.0.0/0 12.0.0.30 tcp dpt:80 to:192.168.80.15:80Chain INPUT (policy ACCEPT)
target prot opt source destination Chain OUTPUT (policy ACCEPT)
target prot opt source destination Chain POSTROUTING (policy ACCEPT)
target prot opt source destination
SNAT all -- 192.168.80.0/24 0.0.0.0/0 to:12.0.0.30
[root@l1 named]#

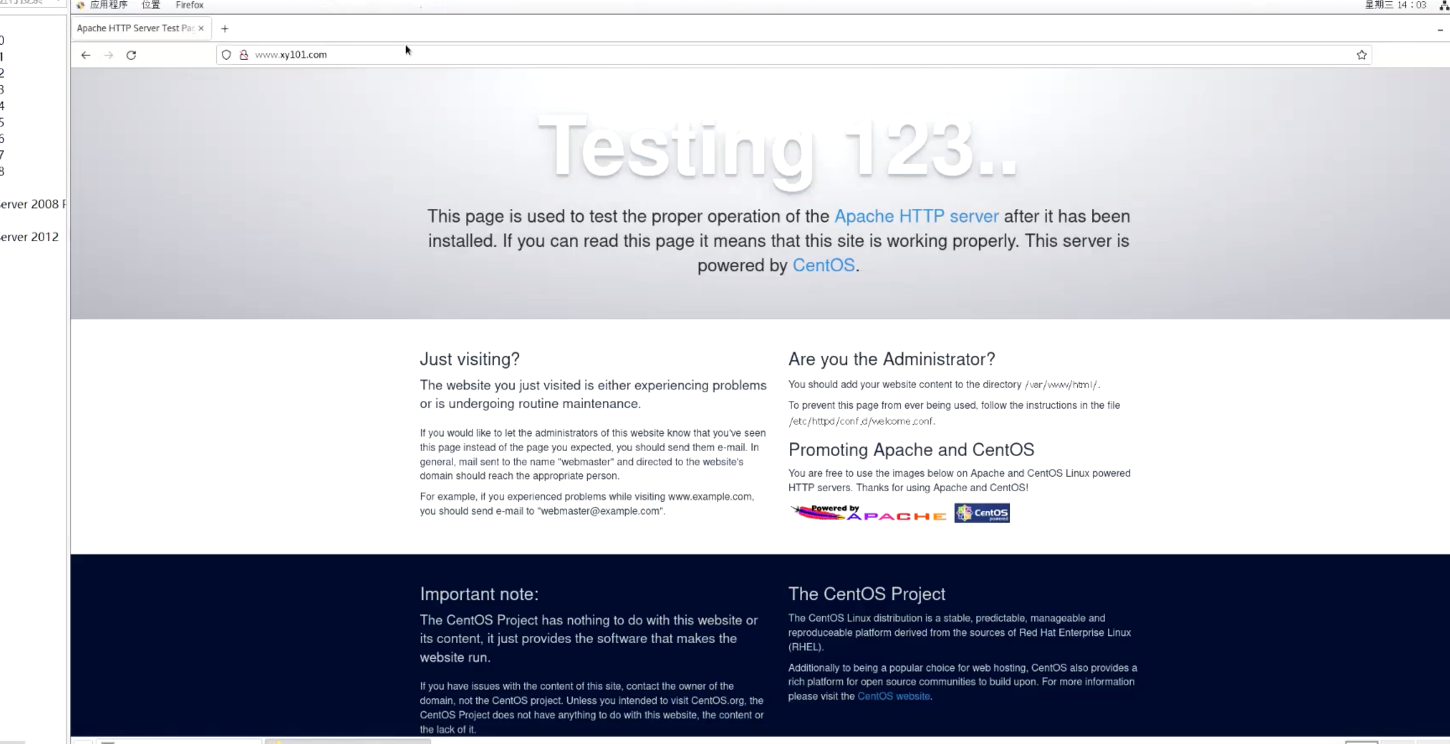
网页
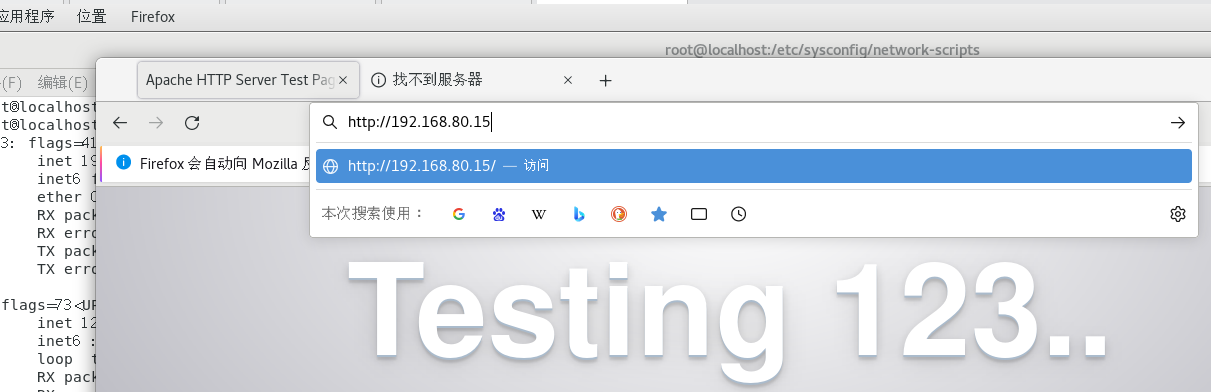

[root@localhost network-scripts]# systemctl stop firewalld
[root@localhost network-scripts]# setenforce 0
[root@localhost network-scripts]#
网关服务器

 客户端
客户端
网关服务器 ssh
[root@l1 named]# iptables -t nat -A PREROUTING -i ens33 -d 12.0.0.30 -p tcp --dport 2345 -j DNAT --to 192.168.80.15:22
[root@l1 named]# iptables -nL -t nat
Chain PREROUTING (policy ACCEPT)
target prot opt source destination
DNAT tcp -- 0.0.0.0/0 12.0.0.30 tcp dpt:80 to:192.168.80.15:80
DNAT tcp -- 0.0.0.0/0 12.0.0.30 tcp dpt:2345 to:192.168.80.15:22Chain INPUT (policy ACCEPT)
target prot opt source destination Chain OUTPUT (policy ACCEPT)
target prot opt source destination Chain POSTROUTING (policy ACCEPT)
target prot opt source destination
SNAT all -- 192.168.80.0/24 0.0.0.0/0 to:12.0.0.30
[root@l1 named]#
客户端

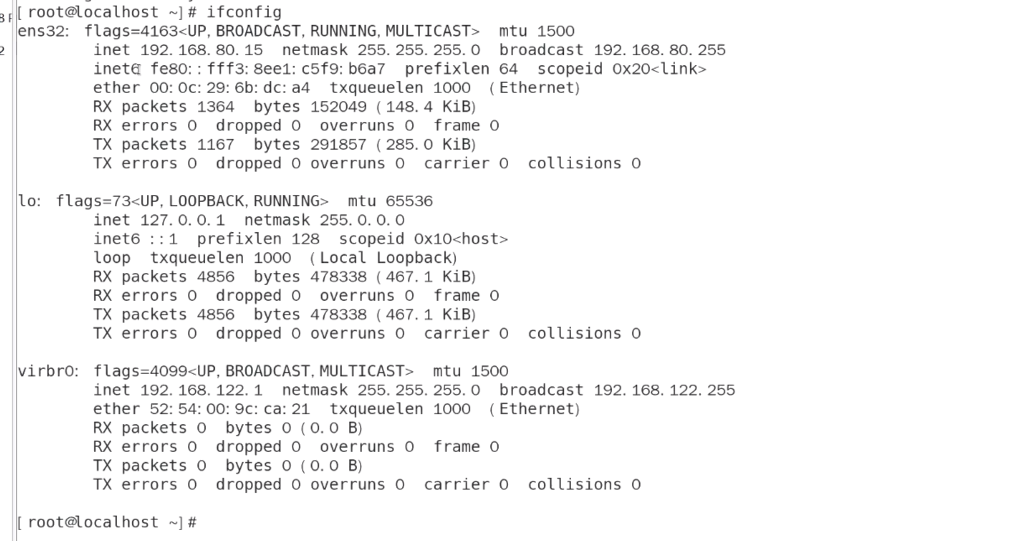
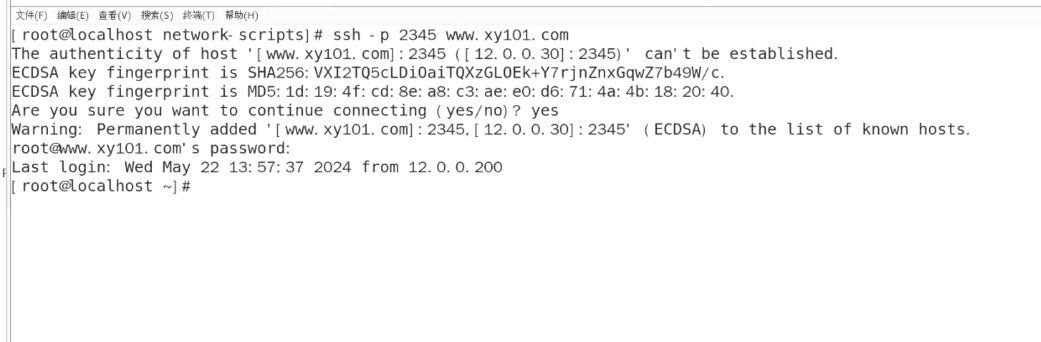 网关
网关

网站服务器抓包
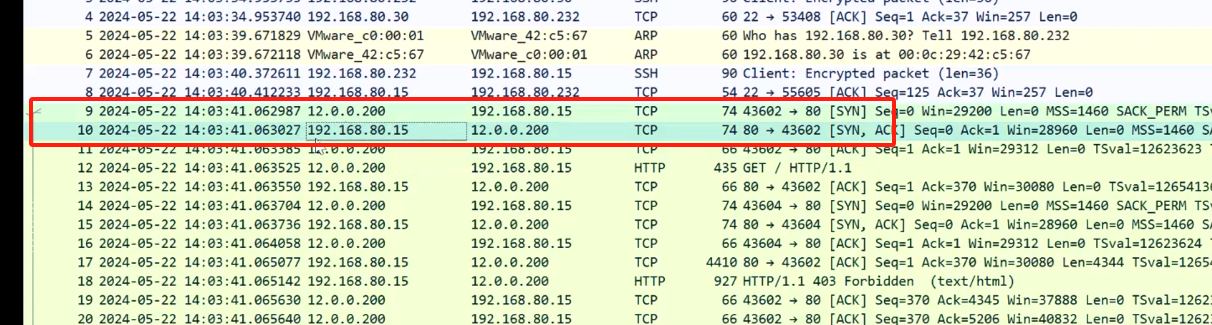
[root@localhost ~]# tcpdump -i ens33 -s 0 -w ./test3.cap
tcpdump: listening on ens33, link-type EN10MB (Ethernet), capture size 262144 bytes
客户端

这篇关于iptables防火墙【其二 实验篇】的文章就介绍到这儿,希望我们推荐的文章对编程师们有所帮助!















