protecting专题
UVa12093 Protecting Zonk
题意:给定一个有n个节点的无根树,有两种装置A和B,每种都有无限多个。在某个节点X使用A装置需要C1的花费,并且此时与节点X相连的边都被覆盖。在某个节点X使用B装置需要C2的花费,并且此时与节点X相连的边以及与X相连的点相连的边都被覆盖。求覆盖所有边的最小花费。 思路:树型dp。随便拿一个点当作树根,dp(i,j,k),i代表节点号,j代表选择装置的类型,k代表覆
Protecting Intellectual Property of Deep NeuralNetworks with Watermarking
保护深度神经网络的知识产权与数字水印技术 ABSTRACT 深度学习是当今人工智能服务的关键组成部分,在视觉分析、语音识别、自然语言处理等多个任务方面表现出色,为人类提供了接近人类水平的能力。构建一个生产级别的深度学习模型是一项非常复杂的任务,需要大量的训练数据、强大的计算资源和专业的人才。因此,非法复制、分发和派生专有的深度学习模型可能导致版权侵权,并对模型创建者造成经济损害。因此,有必要设
[BZOJ1634] [Usaco2007 Jan]Protecting the Flowers 护花
[Usaco2007 Jan]Protecting the Flowers 护花 Description Farmer John went to cut some wood and left N (2 <= N <= 100,000) cows eating the grass, as usual. When he returned, he found to his horror that t
《CryptDB: Protecting Confidentiality with Encrypted Query Processing》论文学习笔记
文章目录 CryptDB: Protecting Confidentiality with Encrypted Query Processing1.cryptDB概述(背景)2.CryptDB方案①面对威胁1☆大致系统框架☆SQL-aware Encryption☆Adjustable Query-based Encryption☆其他DBMS功能 ②面对威胁2☆向共享数据提供访问控制策略☆
POJ 3262 Protecting the Flowers 贪心比率
Description Farmer John went to cut some wood and left N (2 ≤ N ≤ 100,000) cows eating the grass, as usual. When he returned, he found to his horror that the cluster of cows was in his garden eating
论文研读|Protecting Intellectual Property of Deep Neural Networks with Watermarking
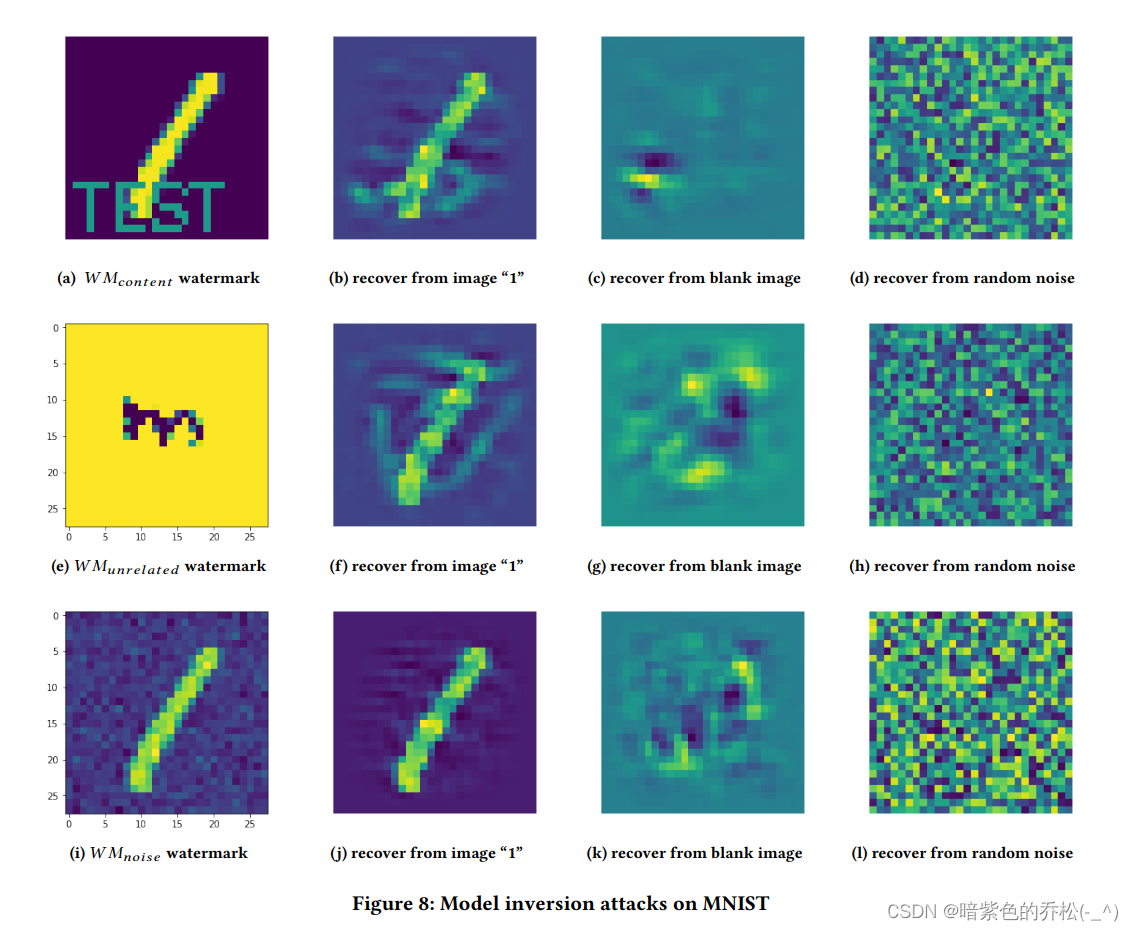
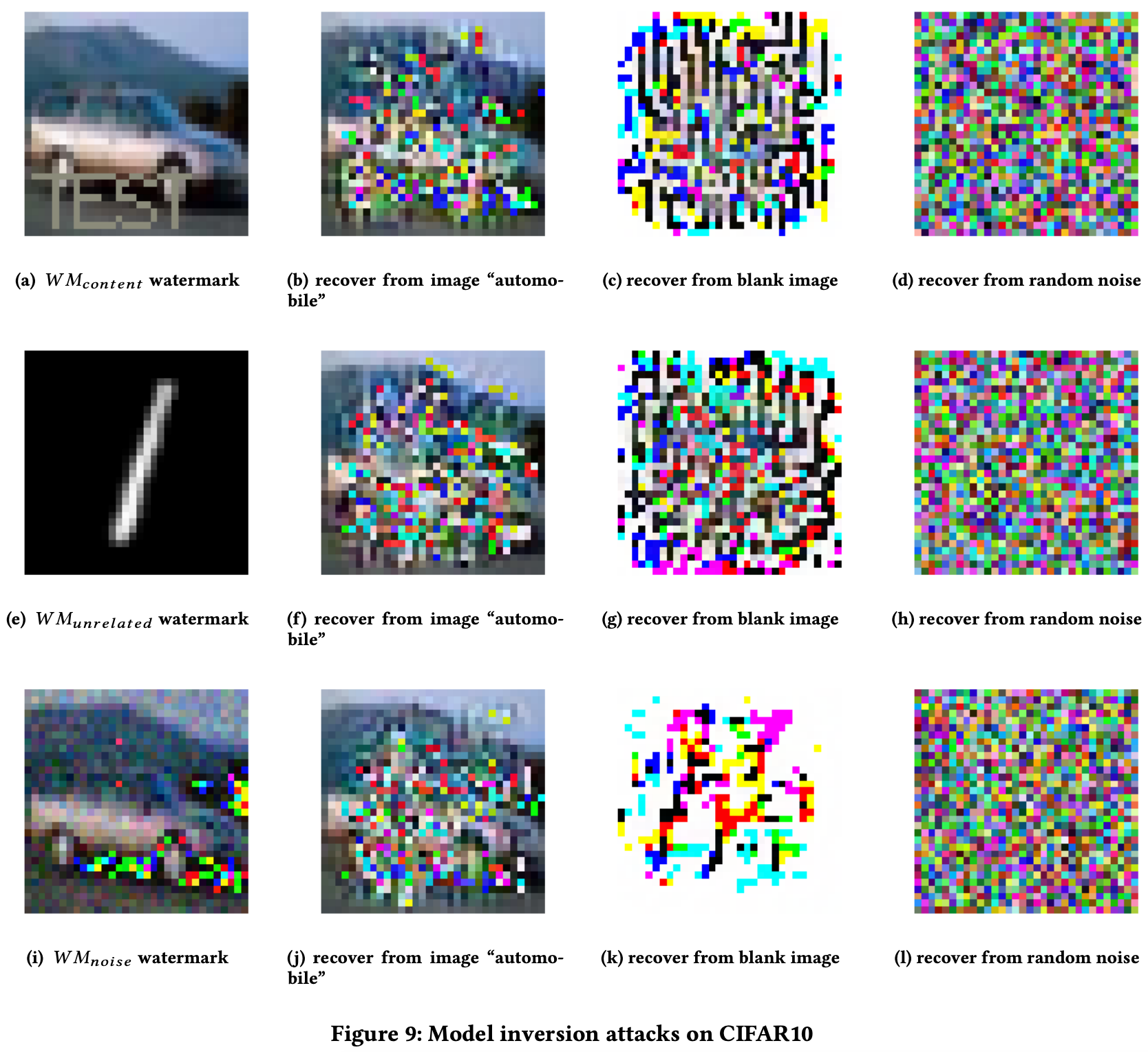
目录 论文信息文章简介研究动机研究方法水印生成水印嵌入版权验证 实验结果有效性(Effectiveness)高效性(Converge Speed)保真度(Functionality)鲁棒性(Robustness)Anti-剪枝攻击(Pruning)Anti-微调攻击(Fine-tuning) 安全性(Security)Anti-模型逆向攻击(Model Inversion) 方法评估相