本文主要是介绍Amazon EKS创建EFS存储卷,希望对大家解决编程问题提供一定的参考价值,需要的开发者们随着小编来一起学习吧!
1、创建Amazon EFS CSI 驱动程序
亚马逊相关文档
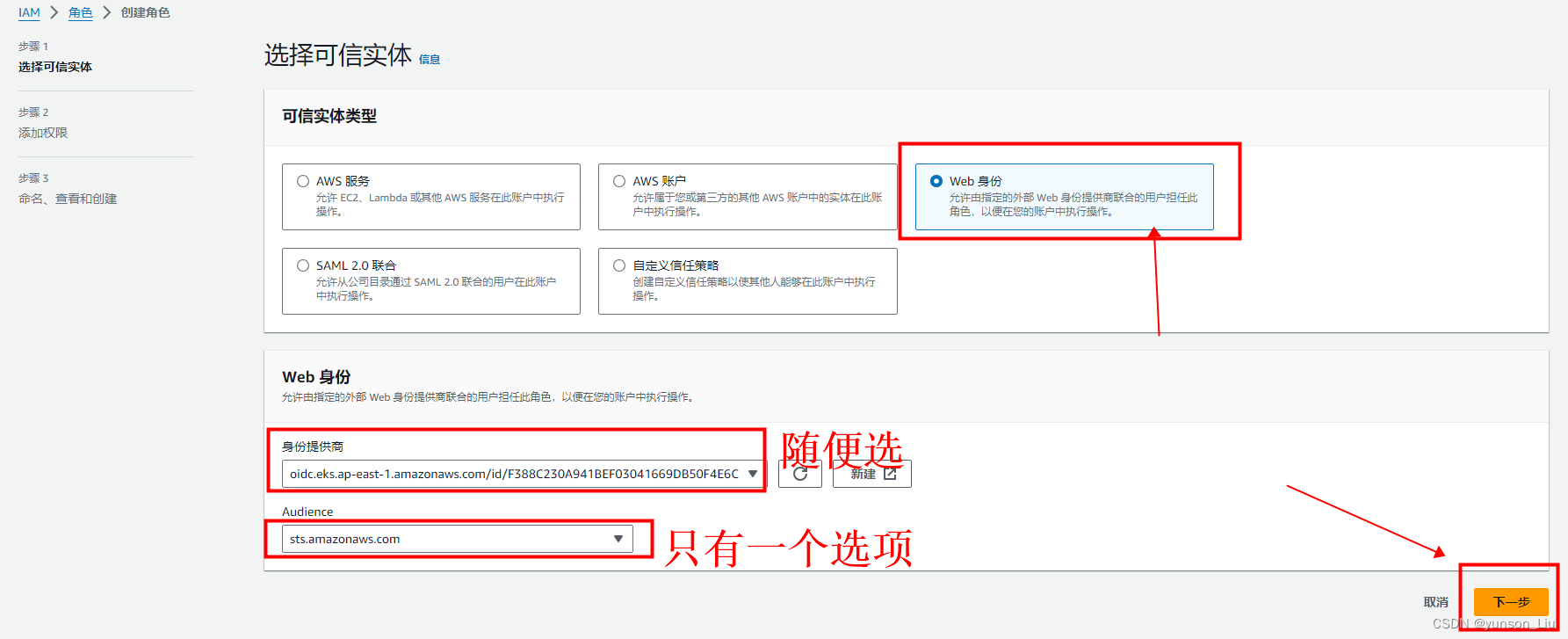
在 Select trusted entity(选择受信任的实体)页面上操作
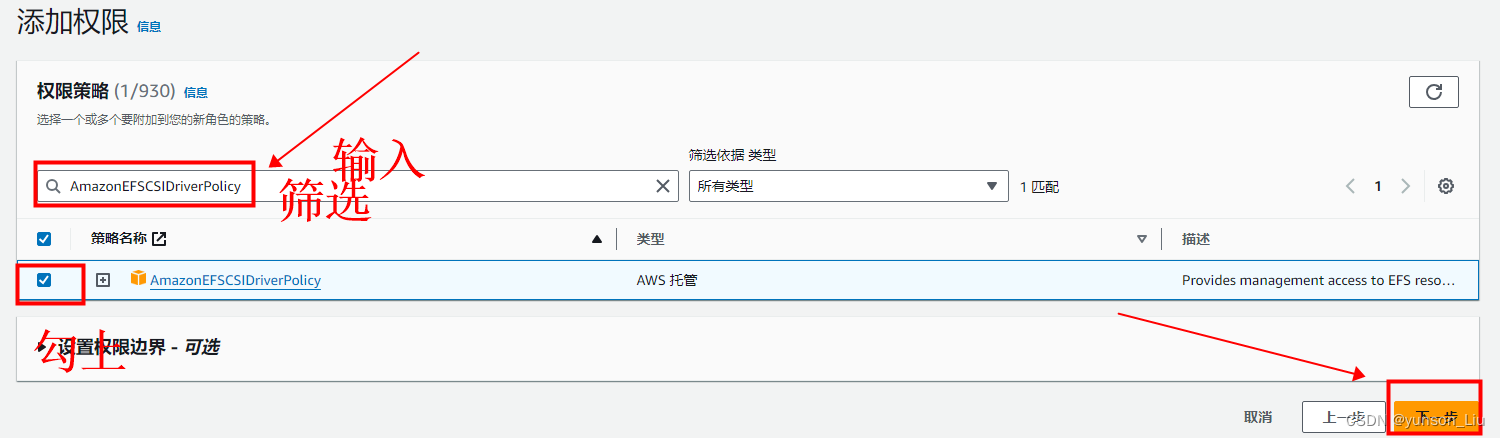
在 Add permissions(添加权限)页面上筛选AmazonEFSCSIDriverPolicy操作
记得将AmazonEBSVolumePolicy添加到我们创建的EKSNodeRole上否则创建存储卷pvc时会报错
Waiting for a volume to be created either by the external provisioner 'efs.csi.aws.com' or manually by the system administrator. If volume creation is delayed, please verify that the provisioner is running and correctly registered.Warning ProvisioningFailed 3s (x3 over 7s) efs.csi.aws.com_efs-csi-controller-78dfdd968d-h6xqr_0d7848ac-e3ef-4353-8e46-91aed02078db failed to provision volume with StorageClass "efs-sc": rpc error: code = Unauthenticated desc = Access Denied. Please ensure you have the right AWS permissions: Access denied
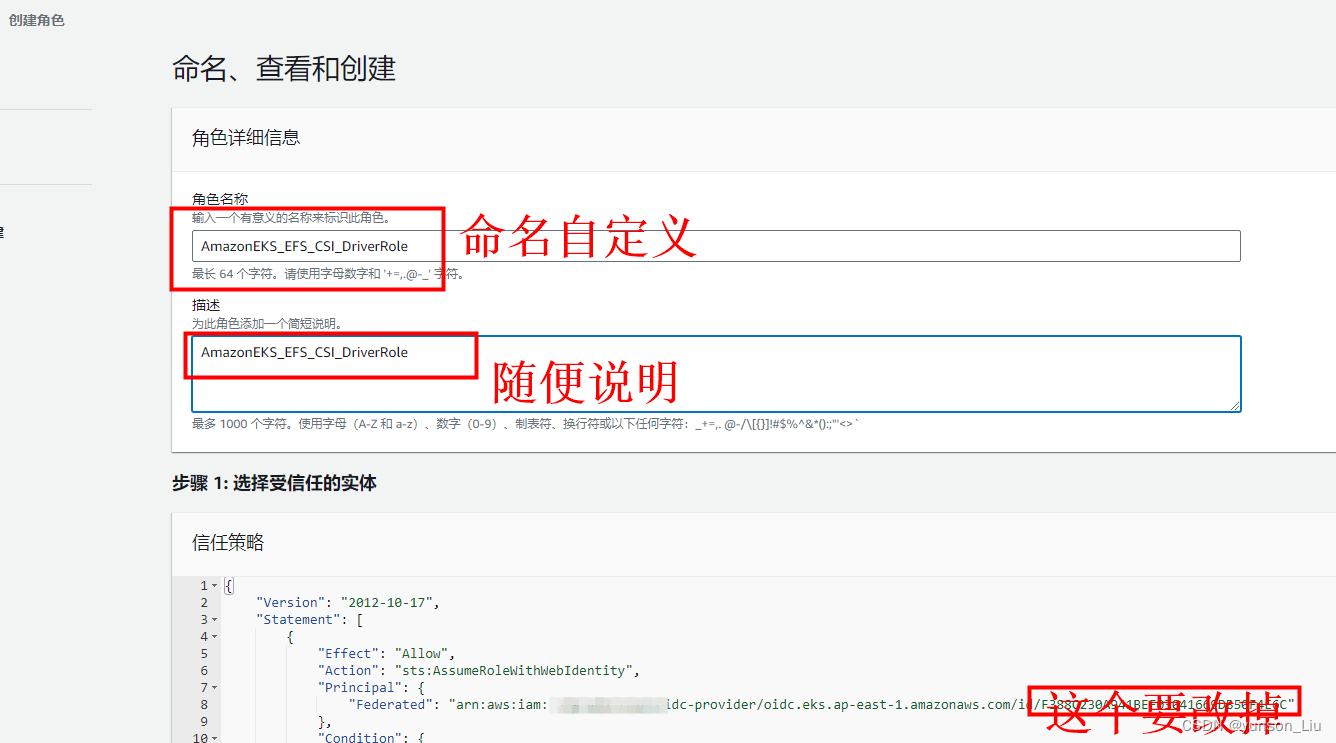
在 Name, review, and create(命名、查看和创建)页面操作命名AmazonEKS_EFS_CSI_DriverRole
点击创建角色后,编辑信任关系
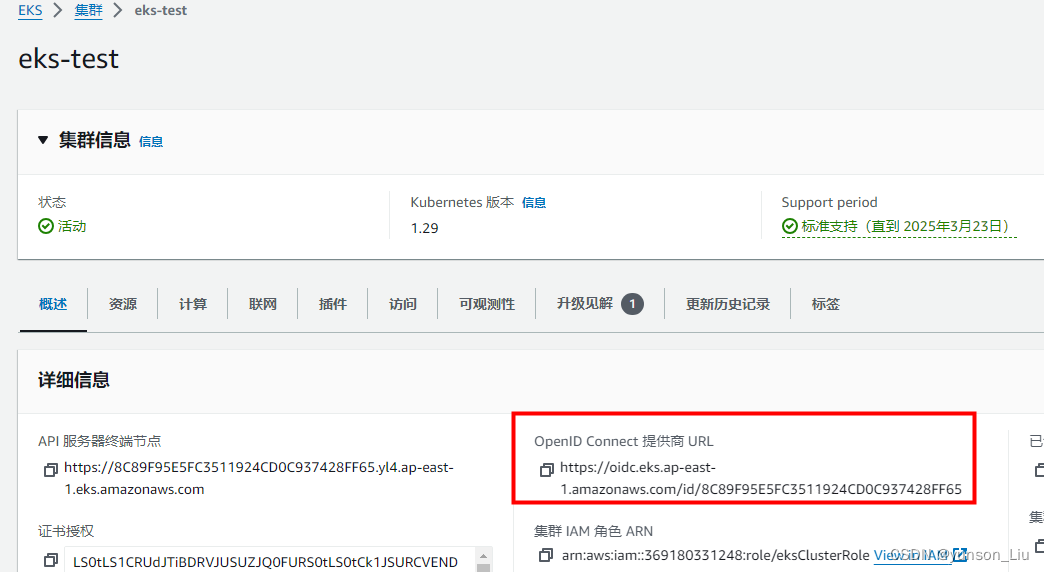
用上图的id替换刚才创建时选的id,并在oidc.eks前面添加一行注意添加逗号
将 Condition 运算符从 “StringEquals” 修改为 “StringLike”
最后更新策略
{"Version": "2012-10-17","Statement": [{"Effect": "Allow","Principal": {"Federated": "arn:aws:iam::XXXXXXXXX:oidc-provider/oidc.eks.ap-east-1.amazonaws.com/id/8C89F95E5FC3511924CD0C937428FF65"},"Action": "sts:AssumeRoleWithWebIdentity","Condition": {"StringLike": {"oidc.eks.ap-east-1.amazonaws.com/id/8C89F95E5FC3511924CD0C937428FF65:sub": "system:serviceaccount:kube-system:efs-csi-*", "oidc.eks.ap-east-1.amazonaws.com/id/8C89F95E5FC3511924CD0C937428FF65:aud": "sts.amazonaws.com"}}}]
}
2、安装 Amazon EFS CSI 驱动程序
1)查看某个集群版本的可用附加组件名称。将 1.29 替换为您的集群版本
# eksctl utils describe-addon-versions --kubernetes-version 1.29 | grep AddonName"AddonName": "vpc-cni","AddonName": "solo-io_istio-distro","AddonName": "snapshot-controller","AddonName": "netapp_trident-operator","AddonName": "kubecost_kubecost","AddonName": "kube-proxy","AddonName": "eks-pod-identity-agent","AddonName": "coredns","AddonName": "aws-mountpoint-s3-csi-driver","AddonName": "aws-guardduty-agent","AddonName": "aws-efs-csi-driver","AddonName": "aws-ebs-csi-driver","AddonName": "amazon-cloudwatch-observability","AddonName": "adot",
查看要创建的附加组件的可用版本。将 1.29 替换为您的集群版本。将 name-of-addon 替换为您要查看其版本的附加组件的名称。该名称必须是前面步骤中返回的名称之一
# eksctl utils describe-addon-versions --kubernetes-version 1.29 --name aws-efs-csi-driver | grep AddonVersion"AddonVersions": ["AddonVersion": "v2.0.1-eksbuild.1","AddonVersion": "v2.0.0-eksbuild.1","AddonVersion": "v1.7.7-eksbuild.1","AddonVersion": "v1.7.6-eksbuild.2","AddonVersion": "v1.7.6-eksbuild.1","AddonVersion": "v1.7.5-eksbuild.2","AddonVersion": "v1.7.5-eksbuild.1","AddonVersion": "v1.7.4-eksbuild.1","AddonVersion": "v1.7.3-eksbuild.1","AddonVersion": "v1.7.2-eksbuild.1","AddonVersion": "v1.7.1-eksbuild.1","AddonVersion": "v1.7.0-eksbuild.1","AddonVersion": "v1.5.9-eksbuild.1","AddonVersion": "v1.5.8-eksbuild.1",
确定您要创建的附加组件是 Amazon EKS 还是 AWS Marketplace 附加组件。AWS Marketplace 具有第三方附加组件,需要您完成额外的步骤才能创建附加组件。
# eksctl utils describe-addon-versions --kubernetes-version 1.29 --name name-of-addon | grep ProductUrl
创建 Amazon EKS 附加组件
-
将
my-cluster替换为您的集群名称。 -
将
name-of-addon替换为您要创建的附加组件的名称。 -
如果您需要早于最新版本的附加组件版本,请将
latest替换为前面步骤的输出中返回的适用版本号。 -
如果附加组件使用了服务账户角色,请将
111122223333替换为您的账户 ID,并将role-name替换为该角色的名称。有关为服务账户创建角色的说明,请参阅您正在创建的附加组件的文档。指定服务账户角色需要您的集群具有 IAM OpenID Connect(OIDC)提供程序。要确定您的集群是否具有此提供程序,或者要创建此提供程序,请参阅为集群创建 IAM OIDC 提供商。 -
如果附加组件不使用服务账户角色,请删除
--service-account-role-arn arn:aws:iam::111122223333:role/role-name。 -
此示例命令将覆盖附加组件的任何现有自行管理版本(如果有的话)的配置。如果您不想覆盖现有的自行管理附加组件的配置,请删除
--force选项。如果您删除此选项,并且 Amazon EKS 附加组件需要覆盖现有的自行管理附加组件的配置,那么创建 Amazon EKS 附加组件将会失败,并显示一条帮助您解决冲突的错误消息。在指定此选项之前,请确保 Amazon EKS 附加组件不会管理您需要管理的设置,因为这些设置会被此选项覆盖。
eksctl create addon --cluster my-cluster --name name-of-addon --version latest \--service-account-role-arn arn:aws:iam::111122223333:role/role-name --force
我的命令如下
# eksctl create addon --cluster eks-test --name aws-efs-csi-driver --version v2.0.1-eksbuild.1 --service-account-role-arn arn:aws:iam::XXXXXX:role/AmazonEKS_EFS_CSI_DriverRole --force
2024-05-04 12:15:00 [!] no IAM OIDC provider associated with cluster, try 'eksctl utils associate-iam-oidc-provider --region=ap-east-1 --cluster=eks-test'
2024-05-04 12:15:00 [ℹ] Kubernetes version "1.29" in use by cluster "eks-test"
2024-05-04 12:15:00 [!] OIDC is disabled but policies are required/specified for this addon. Users are responsible for attaching the policies to all nodegroup roles
2024-05-04 12:15:00 [ℹ] creating addon
删除
kubectl delete csidriver efs.csi.aws.com
csidriver.storage.k8s.io "efs.csi.aws.com" deleted
3、创建存储类
1)创建efs
AWS控制台创建EFS
将eks集群所在VPC、Subnet添加为EFS挂载目标

挂载目标的安全组开通入站端口2049,源地址为eks集群所在cidr
2)下载配置模板
curl -o storageclass.yaml https://raw.githubusercontent.com/kubernetes-sigs/aws-efs-csi-driver/master/examples/kubernetes/dynamic_provisioning/specs/storageclass.yaml
更改fileSystemId值为你的EFS ID
reclaimPolicy-Retain:手动回收类型,当pod资源被删除时被分配的pv不会被自动删除
volumeBindingMode-WaitForFirstConsumer:延迟pod与pv的绑定,直到pod被成功创建出来,pv才会与pod进行绑定
# cat storageclass.yaml
kind: StorageClass
apiVersion: storage.k8s.io/v1
metadata:name: efs-sc
provisioner: efs.csi.aws.com
parameters:provisioningMode: efs-apfileSystemId: fs-0ec110efb782479fedirectoryPerms: "700"gidRangeStart: "1000" # optionalgidRangeEnd: "2000" # optionalbasePath: "/dynamic_provisioning" # optionalsubPathPattern: "${.PVC.namespace}/${.PVC.name}" # optionalensureUniqueDirectory: "true" # optionalreuseAccessPoint: "false" # optional
reclaimPolicy: Retain
volumeBindingMode: Immediate
#volumeBindingMode: WaitForFirstConsumer
创建存储类
# kubectl apply -f storageclass.yaml
storageclass.storage.k8s.io/efs-sc created
5、创建pvc
# cat efs-pvc.yaml
apiVersion: v1
kind: PersistentVolumeClaim
metadata:name: efs-pvc
spec:accessModes:- ReadWriteManyvolumeMode: Filesystemresources:requests:storage: 2GistorageClassName: efs-sc
创建pvc
# kubectl apply -f efs-pvc.yaml
persistentvolumeclaim/efs-pvc created
查看pvc
kubectl get pvc
NAME STATUS VOLUME CAPACITY ACCESS MODES STORAGECLASS VOLUMEATTRIBUTESCLASS AGE
efs-pvc Bound pvc-b445157e-317c-482b-a9f1-7c61bbf7b101 2Gi RWX efs-sc <unset> 103s
这篇关于Amazon EKS创建EFS存储卷的文章就介绍到这儿,希望我们推荐的文章对编程师们有所帮助!








