本文主要是介绍nmap扫描工控设备的脚本支持,希望对大家解决编程问题提供一定的参考价值,需要的开发者们随着小编来一起学习吧!
参考资料
转自(http://www.360doc.com/content/15/1201/11/26186435_517125254.shtml)
介绍
NMAP是一款强大的网络扫描工具,除了普通的TCP/IP网络扫描之外,NMAP的扩展脚本功能为我们提供了更为广阔的应用范围。
针对脚本学习可以参考如下文章
《nmap脚本详解(非常详细)零基础入门到精通,收藏这一篇就够了》
通过配置脚本能够更为具体的判断设备的信息,目前标准版本里已经集成了607个脚本。
工控协议
简单介绍一下工控协议
- CIP
通用工业协议(Common Industrial Protocol,简称CIP)是一种应用在工业自动化的通信协议,由开放DeviceNet厂商协会(简称ODVA)所维护。以前的名称为控制信息协议(Control and Information Protocol,简称也是CIP)。通用工业协议,被deviceNet、ControlNet、EtherNet/IP三种网络所采用 - Ethernet/lP
EtherNet/IP是由罗克韦尔自动化公司开发的工业以太网通讯协定,由ODVA(ODVA)管理,可应用在程序控制及其他自动化的应用中,是通用工业协定(CIP)中的一部分。它建立在标准UDP/IP与TCP/IP协议之上,利用固定的以太网硬件和软件,为配置、访问和控制工业自动化设备定义了一个应用层协议。
EtherNet/IP名称中的IP是“Industrial Protocol”(工业协议)的简称,和网际协议没有关系。
EtherNet/IP将以太网的设备以预定义的设备种类加以分类,每种设备有其特别的行为,此外,EtherNet/IP设备可以:
用用户数据报协议(UDP)的隐式报文传送基本I/O资料。
用传输控制协议(TCP)的显式报文上传或下载参数、设定值、程式或配方。
用主站轮询、从站周期性更新或是状态改变(COS)时更新的方式,方便主站监控从站的状态,讯息会用UDP的报文送出。
用一对一、一对多或是广播的方式,透过用TCP的报文送出资料。
EtherNet/IP使用TCP埠编号44818作为显式报文的处理,UDP埠编号2222作为隐式报文的处理。 - PROFIBUS
PROFIBUS是一个用在自动化技术的现场总线标准,在1987年由德国西门子公司等十四家公司及五个研究机构所推动,PROFIBUS是程序总线网络(PROcess FIeld BUS)的简称。PROFIBUS和用在工业以太网的PROFINET是二种不同的通信协议。是一种用于工厂自动化车间级监控和现场设备层数据通信与控制的现场总线技术,可实现现场设备层到车间级监控的分散式数字控制和现场通信网络。 - DNP3
DNP(Distributed Network Protocol,分布式网络协议)是一种应用于自动化组件之间的通讯协议,常见于电力、水处理等行业。简化OSI模型,只包含了物理层,数据层与应用层的体系结构(EPA)。SCADA可以使用DNP协议与主站、RTU、及IED进行通讯。 - ICCP
电力控制中心通讯协议。 - OPC
过程控制的OLE(OLE for Process Control)。OPC包括一整套接口、属性和方法的标准集,用于过程控制和制造业自动化系统。 - BACnet
楼宇自动控制网络数据通讯协议(A Data Communication Protocol for BuildingAutomation and Control Networks)。BACnet 协议是为计算机控制采暖、制冷、空调HVAC系统和其他建筑物设备系统定义服务和协议, - Siemens S7
属于第7层的协议,用于西门子设备之间进行交换数据,通过TSAP,可加载MPIDP,以太网等不同物理结构总线或网络上,PLC一般可以通过封装好的通讯功能块实现。 - 其他工控协议
EC 60870-5-104、Tridium Niagara Fox、Crimson V3、OMRON FINS、PCWorx.ProConOs、MELSEC-Q
扫描插件
github上(https://github.com/digitalbond/Redpoint)提供了部分工控系统扫描插件
-
BACnet-discover-enumerate.nse
用途:识别和枚举BACnet设备
nmap -sU -Pn -p47808 -n --script BACnet-discover-enumerate <host> -
enip-enumerate.nse
识别和枚举Rockwell Automation(罗克韦尔自动化)等厂商的EtherNet/IP设备
nmap -p44818 --script enip-enumeratehost <host> -
fox-info.nse
识别和枚举Niagara Fox(尼亚加拉福克斯)设备
nmap -p1911--script fox-info <host> -
modicon-info.nse
识别和枚举Schneider Electric(施耐德电气)Modicon(子品牌)的PLC设备
nmap -p502 --script modicon-info.nse -sV <host> -
omron-info.nse
识别和枚举Omron(欧姆龙)的PLC设备
nmap -p9600 -script omontcp-info <host>
nmap -sU -p9600 --script onronudp-info <host> -
pcworx-info.nse
识别和枚举使用了PC Worx的PLC设备
nmap -p1962 --script pcworx-info -sV <host> -
proconos-info.nse
识别和枚举使用了ProConOs的PLC设备
nmap -p20547 --script proconos-info -sV <host> -
s7-enumerate.nse
识别和枚举西门子SIMATIC S7系列PLC设备
nmap -p102 --script s7-enumerate -sV <host>
实例演示
1、下载所有插件到本地(https://github.com/digitalbond/Redpoint)
2、所有插件复制到nmap的脚本文件夹下
使用相应脚本命令对目标进行检测
测试一个s7模拟器。
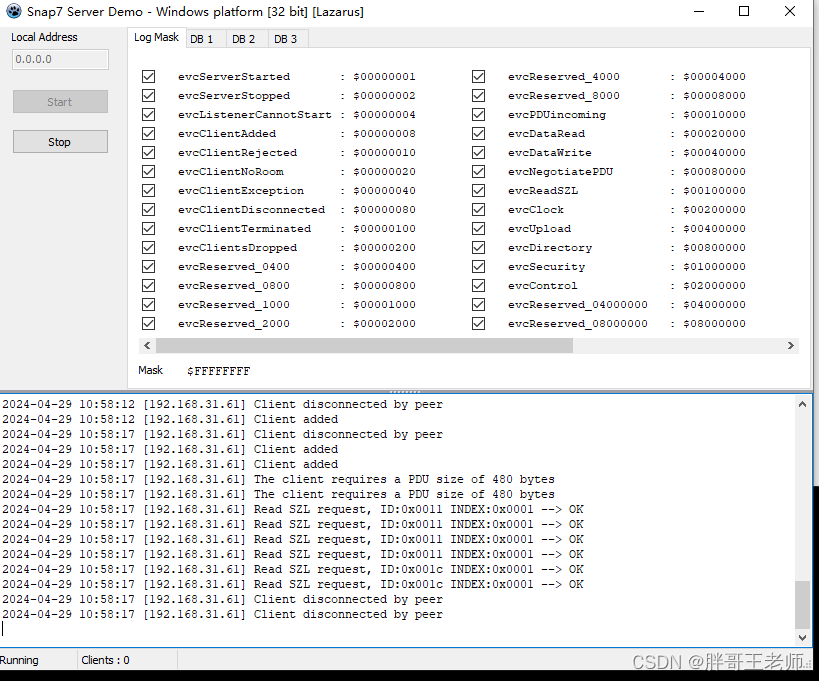
[root@c79 test]# nmap -p102 --script s7-enumerate.nse -sV 192.168.31.60
Starting Nmap 7.94 ( https://nmap.org ) at 2024-04-29 10:55 CST
NSE: DEPRECATION WARNING: bin.lua is deprecated. Please use Lua 5.3 string.pack
Nmap scan report for 192.168.31.60
Host is up (0.00017s latency).PORT STATE SERVICE VERSION
102/tcp open iso-tsap Siemens S7 PLC
| s7-info:
| Module: 6ES7 315-2EH14-0AB0
| Basic Hardware: 6ES7 315-2EH14-0AB0
| Version: 3.2.6
| System Name: SNAP7-SERVER
| Module Type: CPU 315-2 PN/DP
| Serial Number: S C-C2UR28922012
|_ Copyright: Original Siemens Equipment
| s7-enumerate:
| Module: 6ES7 315-2EH14-0AB0
| Basic Hardware: 6ES7 315-2EH14-0AB0
| Version: 3.2.6
| System Name: SNAP7-SERVER
| Module Type: CPU 315-2 PN/DP
| Serial Number: S C-C2UR28922012
|_ Copyright: Original Siemens Equipment
| fingerprint-strings:
| TerminalServerCookie:
|_ Cookie: mstshash=nmap
MAC Address: 94:09:D3:10:33:61 (shenzhen maxtopic technology)
Service Info: Device: specializedService detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 156.79 seconds
2、拓展
其实在nmap版本中自带了很多script。涵盖了不少常见的网络协议,这些脚本可以扩展出一些私有的数据。
[root@c79 test]# ls /usr/share/nmap/scripts/
acarsd-info.nse finger.nse http-svn-enum.nse ms-sql-tables.nse smb-print-text.nse
address-info.nse fingerprint-strings.nse http-svn-info.nse ms-sql-xp-cmdshell.nse smb-protocols.nse
afp-brute.nse firewalk.nse http-title.nse mtrace.nse smb-psexec.nse
afp-ls.nse firewall-bypass.nse http-tplink-dir-traversal.nse murmur-version.nse smb-security-mode.nse
afp-path-vuln.nse flume-master-info.nse http-trace.nse mysql-audit.nse smb-server-stats.nse
afp-serverinfo.nse fox-info.nse http-traceroute.nse mysql-brute.nse smb-system-info.nse
afp-showmount.nse freelancer-info.nse http-trane-info.nse mysql-databases.nse smb-vuln-conficker.nse
ajp-auth.nse ftp-anon.nse http-unsafe-output-escaping.nse mysql-dump-hashes.nse smb-vuln-cve2009-3103.nse
ajp-brute.nse ftp-bounce.nse http-useragent-tester.nse mysql-empty-password.nse smb-vuln-cve-2017-7494.nse
ajp-headers.nse ftp-brute.nse http-userdir-enum.nse mysql-enum.nse smb-vuln-ms06-025.nse
ajp-methods.nse ftp-libopie.nse http-vhosts.nse mysql-info.nse smb-vuln-ms07-029.nse
ajp-request.nse ftp-proftpd-backdoor.nse http-virustotal.nse mysql-query.nse smb-vuln-ms08-067.nse
allseeingeye-info.nse ftp-syst.nse http-vlcstreamer-ls.nse mysql-users.nse smb-vuln-ms10-054.nse
amqp-info.nse ftp-vsftpd-backdoor.nse http-vmware-path-vuln.nse mysql-variables.nse smb-vuln-ms10-061.nse
asn-query.nse ftp-vuln-cve2010-4221.nse http-vuln-cve2006-3392.nse mysql-vuln-cve2012-2122.nse smb-vuln-ms17-010.nse
auth-owners.nse ganglia-info.nse http-vuln-cve2009-3960.nse nat-pmp-info.nse smb-vuln-regsvc-dos.nse
auth-spoof.nse giop-info.nse http-vuln-cve2010-0738.nse nat-pmp-mapport.nse smb-vuln-webexec.nse
backorifice-brute.nse gkrellm-info.nse http-vuln-cve2010-2861.nse nbd-info.nse smb-webexec-exploit.nse
backorifice-info.nse gopher-ls.nse http-vuln-cve2011-3192.nse nbns-interfaces.nse smtp-brute.nse
bacnet-info.nse gpsd-info.nse http-vuln-cve2011-3368.nse nbstat.nse smtp-commands.nse
banner.nse hadoop-datanode-info.nse http-vuln-cve2012-1823.nse ncp-enum-users.nse smtp-enum-users.nse
bitcoin-getaddr.nse hadoop-jobtracker-info.nse http-vuln-cve2013-0156.nse ncp-serverinfo.nse smtp-ntlm-info.nse
bitcoin-info.nse hadoop-namenode-info.nse http-vuln-cve2013-6786.nse ndmp-fs-info.nse smtp-open-relay.nse
bitcoinrpc-info.nse hadoop-secondary-namenode-info.nse http-vuln-cve2013-7091.nse ndmp-version.nse smtp-strangeport.nse
bittorrent-discovery.nse hadoop-tasktracker-info.nse http-vuln-cve2014-2126.nse nessus-brute.nse smtp-vuln-cve2010-4344.nse
bjnp-discover.nse hbase-master-info.nse http-vuln-cve2014-2127.nse nessus-xmlrpc-brute.nse smtp-vuln-cve2011-1720.nse
broadcast-ataoe-discover.nse hbase-region-info.nse http-vuln-cve2014-2128.nse netbus-auth-bypass.nse smtp-vuln-cve2011-1764.nse
broadcast-avahi-dos.nse hddtemp-info.nse http-vuln-cve2014-2129.nse netbus-brute.nse sniffer-detect.nse
broadcast-bjnp-discover.nse hnap-info.nse http-vuln-cve2014-3704.nse netbus-info.nse snmp-brute.nse
broadcast-db2-discover.nse hostmap-bfk.nse http-vuln-cve2014-8877.nse netbus-version.nse snmp-hh3c-logins.nse
broadcast-dhcp6-discover.nse hostmap-crtsh.nse http-vuln-cve2015-1427.nse nexpose-brute.nse snmp-info.nse
broadcast-dhcp-discover.nse hostmap-robtex.nse http-vuln-cve2015-1635.nse nfs-ls.nse snmp-interfaces.nse
broadcast-dns-service-discovery.nse http-adobe-coldfusion-apsa1301.nse http-vuln-cve2017-1001000.nse nfs-showmount.nse snmp-ios-config.nse
broadcast-dropbox-listener.nse http-affiliate-id.nse http-vuln-cve2017-5638.nse nfs-statfs.nse snmp-netstat.nse
broadcast-eigrp-discovery.nse http-apache-negotiation.nse http-vuln-cve2017-5689.nse nje-node-brute.nse snmp-processes.nse
broadcast-hid-discoveryd.nse http-apache-server-status.nse http-vuln-cve2017-8917.nse nje-pass-brute.nse snmp-sysdescr.nse
broadcast-igmp-discovery.nse http-aspnet-debug.nse http-vuln-misfortune-cookie.nse nntp-ntlm-info.nse snmp-win32-services.nse
broadcast-jenkins-discover.nse http-auth-finder.nse http-vuln-wnr1000-creds.nse nping-brute.nse snmp-win32-shares.nse
broadcast-listener.nse http-auth.nse http-waf-detect.nse nrpe-enum.nse snmp-win32-software.nse
broadcast-ms-sql-discover.nse http-avaya-ipoffice-users.nse http-waf-fingerprint.nse ntp-info.nse snmp-win32-users.nse
broadcast-netbios-master-browser.nse http-awstatstotals-exec.nse http-webdav-scan.nse ntp-monlist.nse socks-auth-info.nse
broadcast-networker-discover.nse http-axis2-dir-traversal.nse http-wordpress-brute.nse omp2-brute.nse socks-brute.nse
broadcast-novell-locate.nse http-backup-finder.nse http-wordpress-enum.nse omp2-enum-targets.nse socks-open-proxy.nse
broadcast-ospf2-discover.nse http-barracuda-dir-traversal.nse http-wordpress-users.nse omron-info.nse ssh2-enum-algos.nse
broadcast-pc-anywhere.nse http-bigip-cookie.nse http-xssed.nse openflow-info.nse ssh-auth-methods.nse
broadcast-pc-duo.nse http-brute.nse iax2-brute.nse openlookup-info.nse ssh-brute.nse
broadcast-pim-discovery.nse http-cakephp-version.nse iax2-version.nse openvas-otp-brute.nse ssh-hostkey.nse
broadcast-ping.nse http-chrono.nse icap-info.nse openwebnet-discovery.nse ssh-publickey-acceptance.nse
broadcast-pppoe-discover.nse http-cisco-anyconnect.nse iec-identify.nse oracle-brute.nse ssh-run.nse
broadcast-rip-discover.nse http-coldfusion-subzero.nse ike-version.nse oracle-brute-stealth.nse sshv1.nse
broadcast-ripng-discover.nse http-comments-displayer.nse imap-brute.nse oracle-enum-users.nse ssl-ccs-injection.nse
broadcast-sonicwall-discover.nse http-config-backup.nse imap-capabilities.nse oracle-sid-brute.nse ssl-cert-intaddr.nse
broadcast-sybase-asa-discover.nse http-cookie-flags.nse imap-ntlm-info.nse oracle-tns-version.nse ssl-cert.nse
broadcast-tellstick-discover.nse http-cors.nse impress-remote-discover.nse ovs-agent-version.nse ssl-date.nse
broadcast-upnp-info.nse http-cross-domain-policy.nse informix-brute.nse p2p-conficker.nse ssl-dh-params.nse
broadcast-versant-locate.nse http-csrf.nse informix-query.nse path-mtu.nse ssl-enum-ciphers.nse
broadcast-wake-on-lan.nse http-date.nse informix-tables.nse pcanywhere-brute.nse ssl-heartbleed.nse
broadcast-wpad-discover.nse http-default-accounts.nse ip-forwarding.nse pcworx-info.nse ssl-known-key.nse
broadcast-wsdd-discover.nse http-devframework.nse ip-geolocation-geoplugin.nse pgsql-brute.nse ssl-poodle.nse
broadcast-xdmcp-discover.nse http-dlink-backdoor.nse ip-geolocation-ipinfodb.nse pjl-ready-message.nse sslv2-drown.nse
cassandra-brute.nse http-dombased-xss.nse ip-geolocation-map-bing.nse pop3-brute.nse sslv2.nse
cassandra-info.nse http-domino-enum-passwords.nse ip-geolocation-map-google.nse pop3-capabilities.nse sstp-discover.nse
cccam-version.nse http-drupal-enum.nse ip-geolocation-map-kml.nse pop3-ntlm-info.nse stun-info.nse
cics-enum.nse http-drupal-enum-users.nse ip-geolocation-maxmind.nse port-states.nse stun-version.nse
cics-info.nse http-enum.nse ip-https-discover.nse pptp-version.nse stuxnet-detect.nse
cics-user-brute.nse http-errors.nse ipidseq.nse puppet-naivesigning.nse supermicro-ipmi-conf.nse
cics-user-enum.nse http-exif-spider.nse ipmi-brute.nse qconn-exec.nse svn-brute.nse
citrix-brute-xml.nse http-favicon.nse ipmi-cipher-zero.nse qscan.nse targets-asn.nse
citrix-enum-apps.nse http-feed.nse ipmi-version.nse quake1-info.nse targets-ipv6-map4to6.nse
citrix-enum-apps-xml.nse http-fetch.nse ipv6-multicast-mld-list.nse quake3-info.nse targets-ipv6-multicast-echo.nse
citrix-enum-servers.nse http-fileupload-exploiter.nse ipv6-node-info.nse quake3-master-getservers.nse targets-ipv6-multicast-invalid-dst.nse
citrix-enum-servers-xml.nse http-form-brute.nse ipv6-ra-flood.nse rdp-enum-encryption.nse targets-ipv6-multicast-mld.nse
clamav-exec.nse http-form-fuzzer.nse irc-botnet-channels.nse rdp-ntlm-info.nse targets-ipv6-multicast-slaac.nse
clock-skew.nse http-frontpage-login.nse irc-brute.nse rdp-vuln-ms12-020.nse targets-ipv6-wordlist.nse
coap-resources.nse http-generator.nse irc-info.nse realvnc-auth-bypass.nse targets-sniffer.nse
couchdb-databases.nse http-git.nse irc-sasl-brute.nse redis-brute.nse targets-traceroute.nse
couchdb-stats.nse http-gitweb-projects-enum.nse irc-unrealircd-backdoor.nse redis-info.nse targets-xml.nse
creds-summary.nse http-google-malware.nse iscsi-brute.nse resolveall.nse teamspeak2-version.nse
cups-info.nse http-grep.nse iscsi-info.nse reverse-index.nse telnet-brute.nse
cups-queue-info.nse http-headers.nse isns-info.nse rexec-brute.nse telnet-encryption.nse
cvs-brute.nse http-hp-ilo-info.nse jdwp-exec.nse rfc868-time.nse telnet-ntlm-info.nse
cvs-brute-repository.nse http-huawei-hg5xx-vuln.nse jdwp-info.nse riak-http-info.nse tftp-enum.nse
daap-get-library.nse http-icloud-findmyiphone.nse jdwp-inject.nse rlogin-brute.nse tftp-version.nse
daytime.nse http-icloud-sendmsg.nse jdwp-version.nse rmi-dumpregistry.nse tls-alpn.nse
db2-das-info.nse http-iis-short-name-brute.nse knx-gateway-discover.nse rmi-vuln-classloader.nse tls-nextprotoneg.nse
deluge-rpc-brute.nse http-iis-webdav-vuln.nse knx-gateway-info.nse rpcap-brute.nse tls-ticketbleed.nse
dhcp-discover.nse http-internal-ip-disclosure.nse krb5-enum-users.nse rpcap-info.nse tn3270-screen.nse
dicom-brute.nse http-joomla-brute.nse ldap-brute.nse rpc-grind.nse tor-consensus-checker.nse
dicom-ping.nse http-jsonp-detection.nse ldap-novell-getpass.nse rpcinfo.nse traceroute-geolocation.nse
dict-info.nse http-litespeed-sourcecode-download.nse ldap-rootdse.nse rsa-vuln-roca.nse tso-brute.nse
distcc-cve2004-2687.nse http-ls.nse ldap-search.nse rsync-brute.nse tso-enum.nse
dns-blacklist.nse http-majordomo2-dir-traversal.nse lexmark-config.nse rsync-list-modules.nse ubiquiti-discovery.nse
dns-brute.nse http-malware-host.nse llmnr-resolve.nse rtsp-methods.nse unittest.nse
dns-cache-snoop.nse http-mcmp.nse lltd-discovery.nse rtsp-url-brute.nse unusual-port.nse
dns-check-zone.nse http-methods.nse lu-enum.nse rusers.nse upnp-info.nse
dns-client-subnet-scan.nse http-method-tamper.nse maxdb-info.nse s7-info.nse uptime-agent-info.nse
dns-fuzz.nse http-mobileversion-checker.nse mcafee-epo-agent.nse samba-vuln-cve-2012-1182.nse url-snarf.nse
dns-ip6-arpa-scan.nse http-ntlm-info.nse membase-brute.nse script.db ventrilo-info.nse
dns-nsec3-enum.nse http-open-proxy.nse membase-http-info.nse servicetags.nse versant-info.nse
dns-nsec-enum.nse http-open-redirect.nse memcached-info.nse shodan-api.nse vmauthd-brute.nse
dns-nsid.nse http-passwd.nse metasploit-info.nse sip-brute.nse vmware-version.nse
dns-random-srcport.nse http-phpmyadmin-dir-traversal.nse metasploit-msgrpc-brute.nse sip-call-spoof.nse vnc-brute.nse
dns-random-txid.nse http-phpself-xss.nse metasploit-xmlrpc-brute.nse sip-enum-users.nse vnc-info.nse
dns-recursion.nse http-php-version.nse mikrotik-routeros-brute.nse sip-methods.nse vnc-title.nse
dns-service-discovery.nse http-proxy-brute.nse mmouse-brute.nse skypev2-version.nse voldemort-info.nse
dns-srv-enum.nse http-put.nse mmouse-exec.nse smb2-capabilities.nse vtam-enum.nse
dns-update.nse http-qnap-nas-info.nse modbus-discover.nse smb2-security-mode.nse vulners.nse
dns-zeustracker.nse http-referer-checker.nse mongodb-brute.nse smb2-time.nse vuze-dht-info.nse
dns-zone-transfer.nse http-rfi-spider.nse mongodb-databases.nse smb2-vuln-uptime.nse wdb-version.nse
docker-version.nse http-robots.txt.nse mongodb-info.nse smb-brute.nse weblogic-t3-info.nse
domcon-brute.nse http-robtex-reverse-ip.nse mqtt-subscribe.nse smb-double-pulsar-backdoor.nse whois-domain.nse
domcon-cmd.nse http-robtex-shared-ns.nse mrinfo.nse smb-enum-domains.nse whois-ip.nse
domino-enum-users.nse http-sap-netweaver-leak.nse msrpc-enum.nse smb-enum-groups.nse wsdd-discover.nse
dpap-brute.nse http-security-headers.nse ms-sql-brute.nse smb-enum-processes.nse x11-access.nse
drda-brute.nse http-server-header.nse ms-sql-config.nse smb-enum-services.nse xdmcp-discover.nse
drda-info.nse http-shellshock.nse ms-sql-dac.nse smb-enum-sessions.nse xmlrpc-methods.nse
duplicates.nse http-sitemap-generator.nse ms-sql-dump-hashes.nse smb-enum-shares.nse xmpp-brute.nse
eap-info.nse http-slowloris-check.nse ms-sql-empty-password.nse smb-enum-users.nse xmpp-info.nse
enip-info.nse http-slowloris.nse ms-sql-hasdbaccess.nse smb-flood.nse
epmd-info.nse http-sql-injection.nse ms-sql-info.nse smb-ls.nse
eppc-enum-processes.nse https-redirect.nse ms-sql-ntlm-info.nse smb-mbenum.nse
fcrdns.nse http-stored-xss.nse ms-sql-query.nse smb-os-discovery.nse
随便测试一下s7的脚本
[root@c79 test]# nmap -p102 --script s7-info -sV 192.168.31.60
Starting Nmap 7.94 ( https://nmap.org ) at 2024-04-29 13:52 CST
Nmap scan report for 192.168.31.60
Host is up (0.00012s latency).PORT STATE SERVICE VERSION
102/tcp open iso-tsap Siemens S7 PLC
| s7-info:
| Module: 6ES7 315-2EH14-0AB0
| Basic Hardware: 6ES7 315-2EH14-0AB0
| Version: 3.2.6
| System Name: SNAP7-SERVER
| Module Type: CPU 315-2 PN/DP
| Serial Number: S C-C2UR28922012
|_ Copyright: Original Siemens Equipment
| fingerprint-strings:
| TerminalServerCookie:
|_ Cookie: mstshash=nmap
MAC Address: 94:09:D3:10:33:61 (shenzhen maxtopic technology)
Service Info: Device: specializedService detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 156.53 seconds
似乎和前面的也没有区别,看来已经集成到标准版本里了。
测试modbus发现
[root@c79 test]# nmap -p502 --script modbus-discover -sV 192.168.31.60
Starting Nmap 7.94 ( https://nmap.org ) at 2024-04-29 13:50 CST
Nmap scan report for 192.168.31.60
Host is up (0.00023s latency).PORT STATE SERVICE VERSION
502/tcp open modbus
| modbus-discover:
| sid 0x1:
|_ error: ILLEGAL FUNCTION
MAC Address: 94:09:D3:10:33:61 (shenzhen maxtopic technology)Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 25.33 seconds
这篇关于nmap扫描工控设备的脚本支持的文章就介绍到这儿,希望我们推荐的文章对编程师们有所帮助!






