本文主要是介绍CCIE-13-DMVPN,希望对大家解决编程问题提供一定的参考价值,需要的开发者们随着小编来一起学习吧!
目录
- 实验条件
- 网络拓朴
- 环境配置
- 开始配置
- 部署MGRE
- 部署NHRP
- 部署动态路由协议
- OSPF协议
- 网络优化
- EIGRP协议
- 配置IPsec
- 检测结果
实验条件
网络拓朴

环境配置
在我的资源里可以下载(就在这篇文章的开头也可以下载)

开始配置
先检测3台路由都能通过公网IP互联互通、
R2#ping 13.1.1.3
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 13.1.1.3, timeout is 2 seconds:
.!!!!
Success rate is 80 percent (4/5), round-trip min/avg/max = 1/1/1 ms
R2#ping 14.1.1.4
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 14.1.1.4, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
R2#
基础有了
部署MGRE
R2:
interface tunnel0ip address 10.1.1.2 255.255.255.0tunnel source Ethernet0/0tunnel mode gre multipointR3:
interface tunnel0ip address 10.1.1.3 255.255.255.0tunnel source Ethernet0/1tunnel mode gre multipointR4:
interface tunnel0ip address 10.1.1.4 255.255.255.0tunnel source Ethernet0/2tunnel mode gre multipoint
部署NHRP
R2 Hub:
interface tunnel0ip nhrp network 100ip nhrp authentication D-CISCOip nhrp map multicast dynamicR3 Spoke:
interface tunnel0ip nhrp network 100ip nhrp authentication D-CISCOip nhrp map 10.1.1.2 12.1.1.2ip nhrp map multicast 12.1.1.2ip nhrp nhs 10.1.1.2R4 Spoke:
interface tunnel0ip nhrp network 100ip nhrp authentication D-CISCOip nhrp map 10.1.1.2 12.1.1.2ip nhrp map multicast 12.1.1.2ip nhrp nhs 10.1.1.2
检测网络是否连通(私网IP)
R4#ping 10.1.1.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.1.1.2, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
R4#ping 10.1.1.3
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.1.1.3, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
R4#
部署动态路由协议
OSPF协议
宣告网络时,注意不能宣告公网的IP(12段、13段、14段网络),
只宣告公网,不宣告私网IP,无法建立邻居,因为没有私网的IP,MGRE不会把hello包报文通过tunnel转发给HUB,
同时宣告公网和私网IP,会造成邻居关系翻滚。也不行
只能宣告私网IP以及除tunnel source口IP的其它IP。
R2 Hub:
router ospf 100router-id 2.2.2.2network 10.2.2.2 0.0.0.0 area 0network 10.1.1.0 0.0.0.255 area 0R3 Spoke:
router ospf 100router-id 3.3.3.3network 10.3.3.3 0.0.0.0 area 0network 10.1.1.0 0.0.0.255 area 0R4 Spoke:
router ospf 100router-id 4.4.4.4network 10.4.4.4 0.0.0.0 area 0network 10.1.1.0 0.0.0.255 area 0
检查配置结果
R2,R3,R4一直报错
R2(config-router)#
*Apr 5 15:39:26.093: %OSPF-5-ADJCHG: Process 100, Nbr 4.4.4.4 on Tunnel0 from LOADING to FULL, Loading Done
*Apr 5 15:39:26.097: %OSPF-5-ADJCHG: Process 100, Nbr 4.4.4.4 on Tunnel0 from FULL to DOWN, Neighbor Down: Adjacency forced to reset
*Apr 5 15:39:26.098: %OSPF-5-ADJCHG: Process 100, Nbr 3.3.3.3 on Tunnel0 from EXCHANGE to DOWN, Neighbor Down: Adjacency forced to reset
*Apr 5 15:39:26.099: %OSPF-5-ADJCHG: Process 100, Nbr 4.4.4.4 on Tunnel0 from EXCHANGE to DOWN, Neighbor Down: Adjacency forced to reset
*Apr 5 15:39:26.099: %OSPF-5-ADJCHG: Process 100, Nbr 3.3.3.3 on Tunnel0 from EXCHANGE to DOWN, Neighbor Down: Adjacency forced to reset
*Apr 5 15:39:26.100: %OSPF-5-ADJCHG: Process 100, Nbr 4.4.4.4 on Tunnel0 from EXCHANGE to DOWN, Neighbor Down: Adjacency forced to reset
*Apr 5 15:39:26.101: %OSPF-5-ADJCHG: Process 100, Nbr 3.3.3.3 on Tunnel0 from EXCHANGE to DOWN, Neighbor Down: Adjacency forced to reset
*Apr 5 15:39:26.101: %OSPF-5-ADJCHG: Process 100, Nbr 4.4.4.4 on Tunnel0 from EXCHANGE to DOWN, Neighbor Down: Adjacency forced to reset
*Apr 5 15:39:26.102: %OSPF-5-ADJCHG: Process 100, Nbr 3.3.3.3 on Tunnel0 from EXCHANGE to DOWN, Neighbor Down: Adjacency forced to reset
*Apr 5 15:39:26.102: %OSPF-5-ADJCHG: Process 100, Nbr 4.4.4.4 on Tunnel0 from EXCHANGE to DOWN, Neighbor Down: Adjacency forced to reset
R2(config-router)#
*Apr 5 15:39:27.096: %OSPF-5-ADJCHG: Process 100, Nbr 4.4.4.4 on Tunnel0 from EXCHANGE to DOWN, Neighbor Down: Adjacency forced to reset
*Apr 5 15:39:27.097: %OSPF-5-ADJCHG: Process 100, Nbr 3.3.3.3 on Tunnel0 from LOADING to FULL, Loading Done
*Apr 5 15:39:27.097: %OSPF-5-ADJCHG: Process 100, Nbr 3.3.3.3 on Tunnel0 from FULL to DOWN, Neighbor Down: Adjacency forced to reset
*Apr 5 15:39:27.098: %OSPF-5-ADJCHG: Process 100, Nbr 4.4.4.4 on Tunnel0 from EXCHANGE to DOWN, Neighbor Down: Adjacency forced to reset
*Apr 5 15:39:27.098: %OSPF-5-ADJCHG: Process 100, Nbr 3.3.3.3 on Tunnel0 from EXCHANGE to DOWN, Neighbor Down: Adjacency forced to reset
*Apr 5 15:39:27.099: %OSPF-5-ADJCHG: Process 100, Nbr 4.4.4.4 on Tunnel0 from EXCHANGE to DOWN, Neighbor Down: Adjacency forced to reset
*Apr 5 15:39:27.100: %OSPF-5-ADJCHG: Process 100, Nbr 3.3.3.3 on Tunnel0 from EXCHANGE to DOWN, Neighbor Down: Adjacency forced to reset
*Apr 5 15:39:27.100: %OSPF-5-ADJCHG: Process 100, Nbr 4.4.4.4 on Tunnel0 from EXCHANGE to DOWN, Neighbor Down: Adjacency forced to reset
*Apr 5 15:39:27.106: %OSPF-5-ADJCHG: Process 100, Nbr 3.3.3.3 on Tunnel0 from EXCHANGE to DOWN, Neighbor Down: Adjacency forced to reset
*Apr 5 15:39:27.106: %OSPF-5-ADJCHG: Process 100, Nbr 4.4.4.4 on Tunnel0 from EXCHANGE to DOWN, Neighbor Down: Adjacency forced to reset
因为默认tunnel接口的ospf网络类型是p2p,这样的话OSPF认为对方是一个路由器,所以一会儿收到R3的hello就和R3建邻居,一会儿收到R4的hello包就重置R3的邻居重新和R4建邻居,造成邻居关系翻滚。因此把接口类型改成点对多点即可以(也可以修改成为广播类型,不过样的话,需要手动指定R2为DR类型才可以)。
修改
R2/R3/R4:
interface tunnel0ip ospf network point-to-multipoint
随后提示邻居起来,路由传递成功。
网络优化
R3#traceroute 10.1.1.4
Type escape sequence to abort.
Tracing the route to 10.1.1.4
VRF info: (vrf in name/id, vrf out name/id)1 10.1.1.2 1 msec 1 msec 0 msec2 10.1.1.4 1 msec * 1 msec
R3#
现在所有的网络流量都需要从R2走,调整一下策略,让SPOKE之间动态的建立路由,直接通信
可以进行以下修改
R2:
interface tunnel 0ip nhrp redirectR3:
interface tunnel 0ip nhrp shortcutR4:
interface tunnel 0ip nhrp shortcut
再次测试
R3#traceroute 10.4.4.4
Type escape sequence to abort.
Tracing the route to 10.4.4.4
VRF info: (vrf in name/id, vrf out name/id)1 10.1.1.2 1 msec 0 msec 0 msec2 10.1.1.4 5 msec * 6 msec
!前几个包需要触发两个SPOKE之间建立连接,所以可能还是和之前一样R3#traceroute 10.4.4.4
Type escape sequence to abort.
Tracing the route to 10.4.4.4
VRF info: (vrf in name/id, vrf out name/id)1 10.1.1.4 6 msec * 5 msec!路由条目前面出现了%, 下一跳被覆盖了
R3#show ip route
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGPD - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2E1 - OSPF external type 1, E2 - OSPF external type 2i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2ia - IS-IS inter area, * - candidate default, U - per-user static routeo - ODR, P - periodic downloaded static route, H - NHRP, l - LISPa - application route+ - replicated route, % - next hop override, p - overrides from PfRGateway of last resort is 13.1.1.1 to network 0.0.0.0S* 0.0.0.0/0 [1/0] via 13.1.1.110.0.0.0/8 is variably subnetted, 7 subnets, 2 masks
C 10.1.1.0/24 is directly connected, Tunnel0
O 10.1.1.2/32 [110/1000] via 10.1.1.2, 00:11:06, Tunnel0
L 10.1.1.3/32 is directly connected, Tunnel0
O % 10.1.1.4/32 [110/2000] via 10.1.1.2, 00:07:59, Tunnel0
O 10.2.2.2/32 [110/1001] via 10.1.1.2, 00:11:06, Tunnel0
C 10.3.3.3/32 is directly connected, Loopback0
O % 10.4.4.4/32 [110/2001] via 10.1.1.2, 00:07:59, Tunnel013.0.0.0/8 is variably subnetted, 2 subnets, 2 masks
C 13.1.1.0/24 is directly connected, Ethernet0/1
L 13.1.1.3/32 is directly connected, Ethernet0/1!通过查看show ip nhrp shorcut也能发现下一跳有变化:
R3#show ip nhrp shortcut
10.1.1.4/32 via 10.1.1.4Tunnel0 created 00:04:14, expire 00:06:01Type: dynamic, Flags: router nhop rib nho NBMA address: 14.1.1.4
10.4.4.4/32 via 10.1.1.4Tunnel0 created 00:03:58, expire 00:06:01Type: dynamic, Flags: router used rib nho NBMA address: 14.1.1.4
R3#
EIGRP协议
注:配置EIGRP前先清空OSPF配置
配置EIGRP
R2:
router eigrp 100router-id 2.2.2.2network 10.1.1.0 0.0.0.255network 10.2.2.2 0.0.0.0R3:
router eigrp 100router-id 3.3.3.3network 10.1.1.0 0.0.0.255network 10.3.3.3 0.0.0.0R4:
router eigrp 100router-id 4.4.4.4network 10.1.1.0 0.0.0.255network 10.4.4.4 0.0.0.0
检查路由表
R2(config-router)#do show ip route
......
S* 0.0.0.0/0 [1/0] via 12.1.1.110.0.0.0/8 is variably subnetted, 5 subnets, 2 masks
C 10.1.1.0/24 is directly connected, Tunnel0
L 10.1.1.2/32 is directly connected, Tunnel0
C 10.2.2.2/32 is directly connected, Loopback0
D 10.3.3.3/32 [90/27008000] via 10.1.1.3, 00:00:18, Tunnel0
D 10.4.4.4/32 [90/27008000] via 10.1.1.4, 00:00:14, Tunnel012.0.0.0/8 is variably subnetted, 2 subnets, 2 masks
C 12.1.1.0/24 is directly connected, Ethernet0/0
L 12.1.1.2/32 is directly connected, Ethernet0/0R3(config-router)#do show ip route
......
S* 0.0.0.0/0 [1/0] via 13.1.1.110.0.0.0/8 is variably subnetted, 4 subnets, 2 masks
C 10.1.1.0/24 is directly connected, Tunnel0
L 10.1.1.3/32 is directly connected, Tunnel0
D 10.2.2.2/32 [90/27008000] via 10.1.1.2, 00:01:07, Tunnel0
C 10.3.3.3/32 is directly connected, Loopback013.0.0.0/8 is variably subnetted, 2 subnets, 2 masks
C 13.1.1.0/24 is directly connected, Ethernet0/1
L 13.1.1.3/32 is directly connected, Ethernet0/1R4(config-router)#do show ip route
......
S* 0.0.0.0/0 [1/0] via 14.1.1.110.0.0.0/8 is variably subnetted, 4 subnets, 2 masks
C 10.1.1.0/24 is directly connected, Tunnel0
L 10.1.1.4/32 is directly connected, Tunnel0
D 10.2.2.2/32 [90/27008000] via 10.1.1.2, 00:01:18, Tunnel0
C 10.4.4.4/32 is directly connected, Loopback014.0.0.0/8 is variably subnetted, 2 subnets, 2 masks
C 14.1.1.0/24 is directly connected, Ethernet0/2
L 14.1.1.4/32 is directly connected, Ethernet0/2
现在配置了EIGRP后,R2能收到R3和R4传给它的路由,
但是R3和R4收不到彼此通告的路由,这是由于EIGRP是距离矢量协议,传递的就是路由信息,R2能从tunnel口收到R3通告的路由,但由于水平分割的原因不会再从tunnel口发送出去,所以R4收不到该路由;同理,R3收不到R4的路由
R2的tunnel0关闭EIGRP水平分割,让SPOKE之间可以互相收到对方的路由
R2#conf t
R2(config)#interface tunnel 0
R2(config-if)#no ip split-horizon eigrp 100
R3(config-router)#do show ip route
......
S* 0.0.0.0/0 [1/0] via 13.1.1.110.0.0.0/8 is variably subnetted, 5 subnets, 2 masks
C 10.1.1.0/24 is directly connected, Tunnel0
L 10.1.1.3/32 is directly connected, Tunnel0
D 10.2.2.2/32 [90/27008000] via 10.1.1.2, 00:04:45, Tunnel0
C 10.3.3.3/32 is directly connected, Loopback0
D 10.4.4.4/32 [90/28288000] via 10.1.1.2, 00:00:35, Tunnel013.0.0.0/8 is variably subnetted, 2 subnets, 2 masks
C 13.1.1.0/24 is directly connected, Ethernet0/1
L 13.1.1.3/32 is directly connected, Ethernet0/1R4(config-router)#do show ip route
......
S* 0.0.0.0/0 [1/0] via 14.1.1.110.0.0.0/8 is variably subnetted, 5 subnets, 2 masks
C 10.1.1.0/24 is directly connected, Tunnel0
L 10.1.1.4/32 is directly connected, Tunnel0
D 10.2.2.2/32 [90/27008000] via 10.1.1.2, 00:05:05, Tunnel0
D 10.3.3.3/32 [90/28288000] via 10.1.1.2, 00:00:57, Tunnel0
C 10.4.4.4/32 is directly connected, Loopback014.0.0.0/8 is variably subnetted, 2 subnets, 2 masks
C 14.1.1.0/24 is directly connected, Ethernet0/2
L 14.1.1.4/32 is directly connected, Ethernet0/2
现在R3和R4能收到彼此的环回口路由了(之前NHRP配置了Redirect和shortcut仍然有效)
R4#traceroute 10.3.3.3
Type escape sequence to abort.
Tracing the route to 10.3.3.3
VRF info: (vrf in name/id, vrf out name/id)1 10.1.1.2 1 msec 0 msec 1 msec2 10.1.1.3 6 msec * 1 msecR4#traceroute 10.3.3.3
Type escape sequence to abort.
Tracing the route to 10.3.3.3
VRF info: (vrf in name/id, vrf out name/id)1 10.1.1.3 1 msec * 0 msecR4#show ip nhrp shortcut
10.1.1.3/32 via 10.1.1.3Tunnel0 created 00:00:51, expire 00:09:08Type: dynamic, Flags: router nhop rib NBMA address: 13.1.1.3
10.3.3.3/32 via 10.1.1.3Tunnel0 created 00:00:51, expire 00:09:08Type: dynamic, Flags: router used rib nho NBMA address: 13.1.1.3
需要注意看R2的tunnel0接口下有没有被配置了(ip next-hop-self eigrp 100),如果被配置的话,需要no掉,不然,路由的下一跳仍然指向R2,这样就达不到优先网络的目的了。
配置IPsec
R2上配置IPSec
!配置身份认证时,对端peer由于是动态的,需要用0.0.0.0
crypto isakmp policy 10encryption aes 256authentication pre-sharehash sha256group 5lifetime 3600
crypto isakmp key d-cisco address 0.0.0.0
crypto ipsec transform-set MYSET esp-aes 256 esp-sha256-hmacmode transport
crypto ipsec profile MYPROFILEset transform-set MYSETinterface tunnel0tunnel protection ipsec profile MYPROFILE
R3/R4上配置IPSec
!配置身份认证时,对端peer由于是动态的,需要用0.0.0.0
crypto isakmp policy 10encryption aes 256authentication pre-sharehash sha256group 5lifetime 3600
crypto isakmp key d-cisco address 0.0.0.0
crypto ipsec transform-set MYSET esp-aes 256 esp-sha256-hmacmode transport
crypto ipsec profile MYPROFILEset transform-set MYSETinterface tunnel0tunnel protection ipsec profile MYPROFILE
检测结果
R4#traceroute 10.3.3.3
Type escape sequence to abort.
Tracing the route to 10.3.3.3
VRF info: (vrf in name/id, vrf out name/id)1 10.1.1.2 5 msec 5 msec 5 msec2 10.1.1.3 6 msec * 5 msec
R4#traceroute 10.3.3.3
Type escape sequence to abort.
Tracing the route to 10.3.3.3
VRF info: (vrf in name/id, vrf out name/id)1 10.1.1.3 5 msec * 7 msec
R4#show crypto session
Crypto session current statusInterface: Tunnel0
Session status: UP-ACTIVE
Peer: 13.1.1.3 port 500 Session ID: 0 IKEv1 SA: local 14.1.1.4/500 remote 13.1.1.3/500 Active Session ID: 0 IKEv1 SA: local 14.1.1.4/500 remote 13.1.1.3/500 Active IPSEC FLOW: permit 47 host 14.1.1.4 host 13.1.1.3 Active SAs: 2, origin: crypto mapInterface: Tunnel0
Session status: UP-ACTIVE
Peer: 12.1.1.2 port 500 Session ID: 0 IKEv1 SA: local 14.1.1.4/500 remote 12.1.1.2/500 Active Session ID: 0 IKEv1 SA: local 14.1.1.4/500 remote 12.1.1.2/500 Active IPSEC FLOW: permit 47 host 14.1.1.4 host 12.1.1.2 Active SAs: 4, origin: crypto map
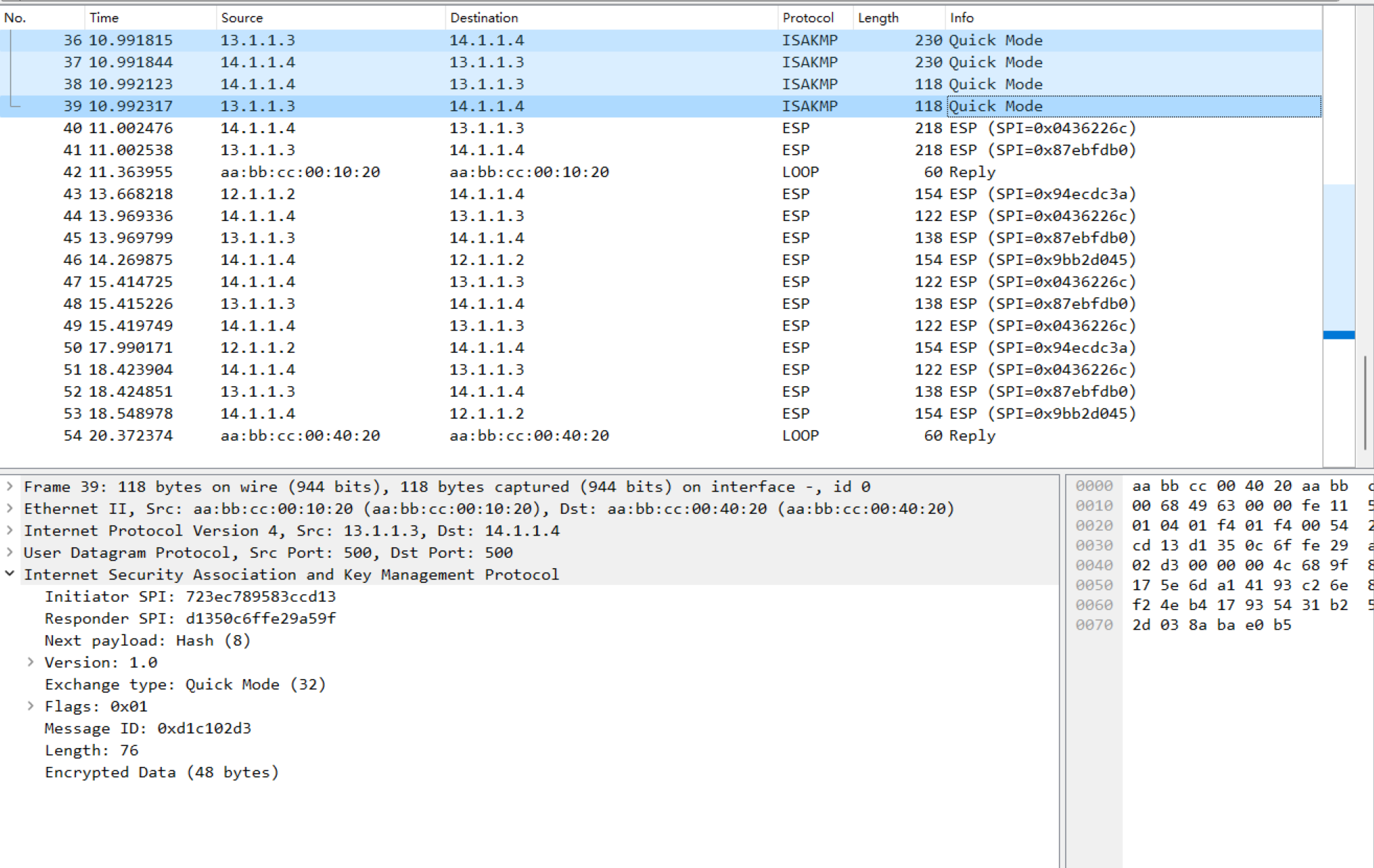
数据通讯已被加密
这篇关于CCIE-13-DMVPN的文章就介绍到这儿,希望我们推荐的文章对编程师们有所帮助!




![[情商-13]:语言的艺术:何为真实和真相,所谓真相,就是别人想让你知道的真相!洞察谎言与真相!](https://i-blog.csdnimg.cn/direct/4e5ed3724fee417cadec420535421736.png)

