本文主要是介绍备考ICA----Istio实验14---出向流量管控Egress Gateways实验,希望对大家解决编程问题提供一定的参考价值,需要的开发者们随着小编来一起学习吧!
备考ICA----Istio实验14—出向流量管控Egress Gateways实验
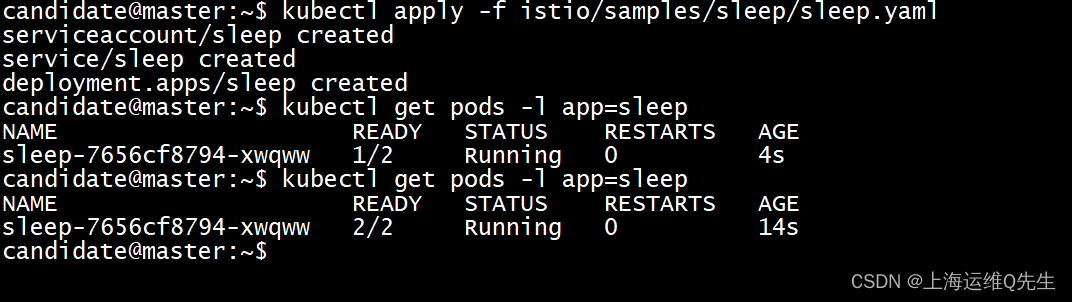
1. 发布测试用 pod
kubectl apply -f istio/samples/sleep/sleep.yaml
kubectl get pods -l app=sleep
2. ServiceEntry
创建一个ServiceEntry允许流量访问edition.cnn.com
egressgw/edition-ServiceEntry.yaml
apiVersion: networking.istio.io/v1beta1
kind: ServiceEntry
metadata:name: cnn
spec:hosts:- edition.cnn.comports:- number: 80name: http-portprotocol: HTTP- number: 443name: httpsprotocol: HTTPSresolution: DNS
部署ServiceEntry
kubectl apply -f egressgw/edition-ServiceEntry.yaml
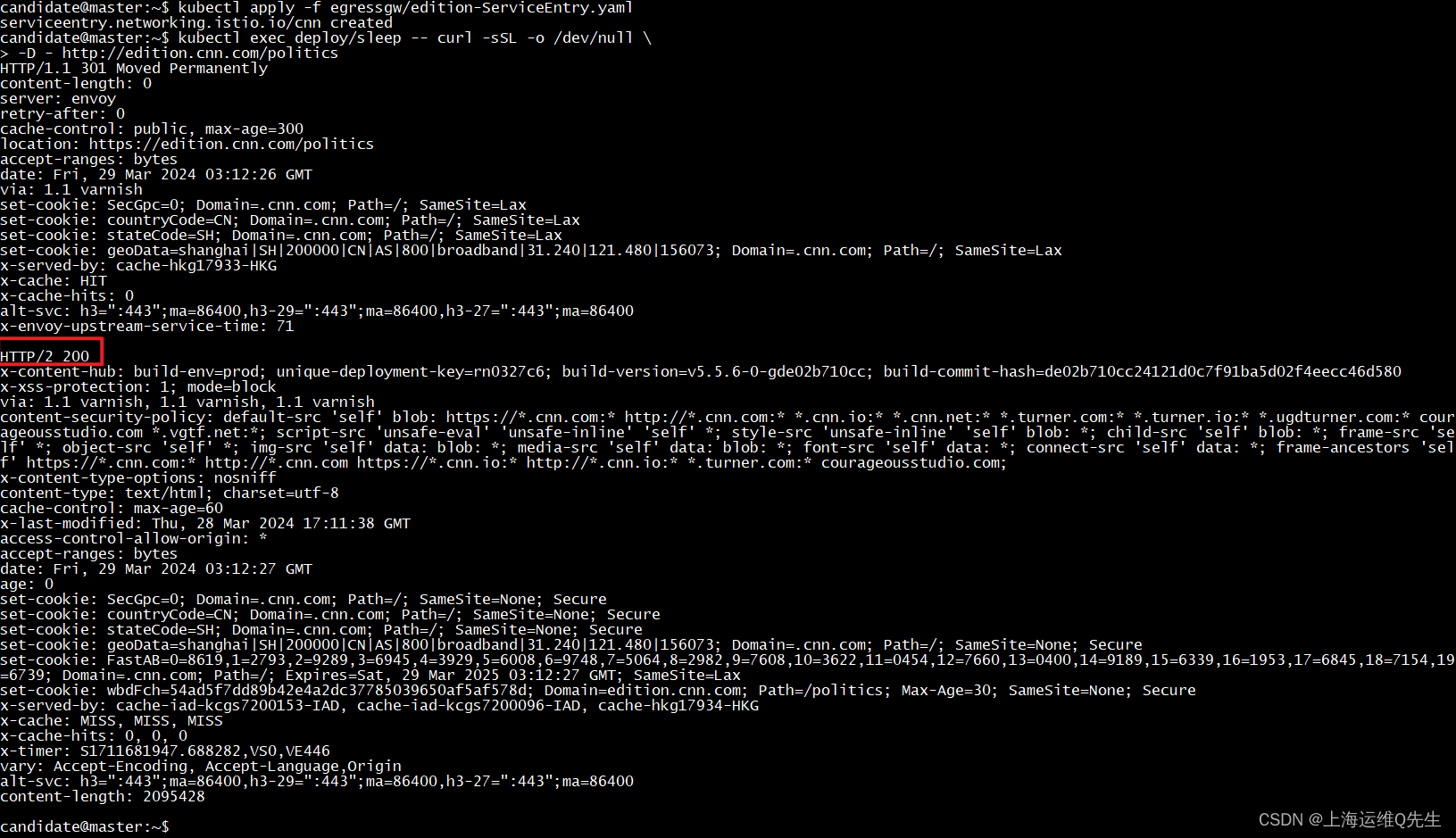
访问测试
kubectl exec deploy/sleep -- curl -sSL -o /dev/null \
-D - http://edition.cnn.com/politics
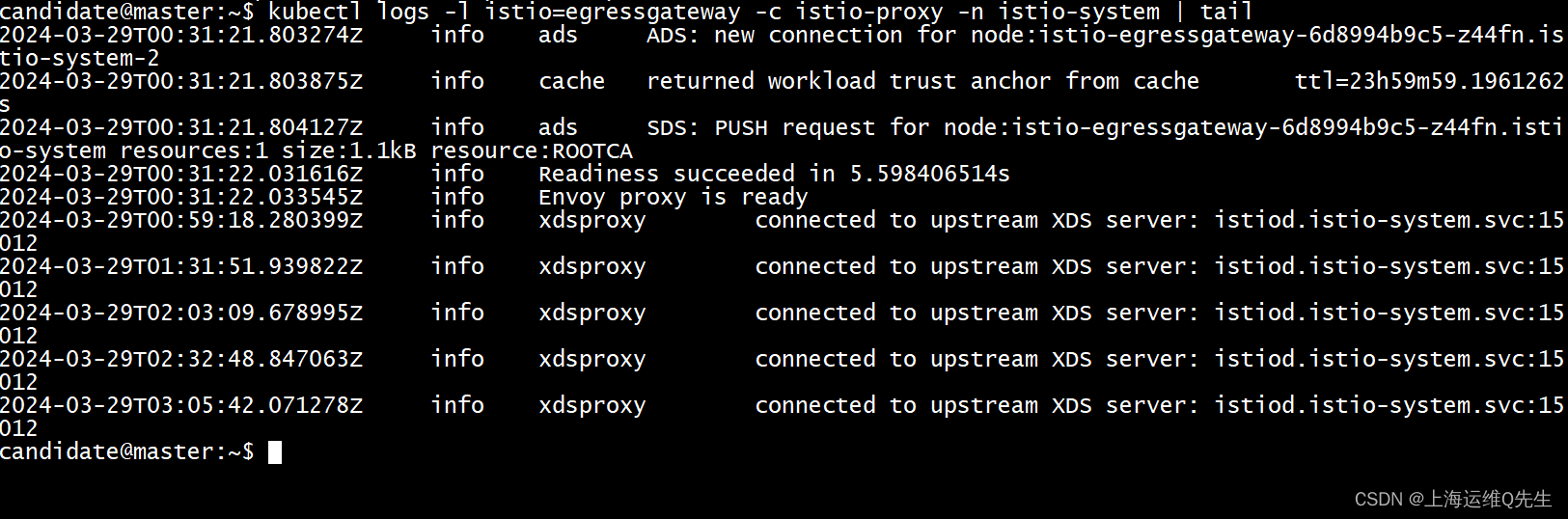
检查egress的日志
kubectl logs -l istio=egressgateway -c istio-proxy -n istio-system | tail
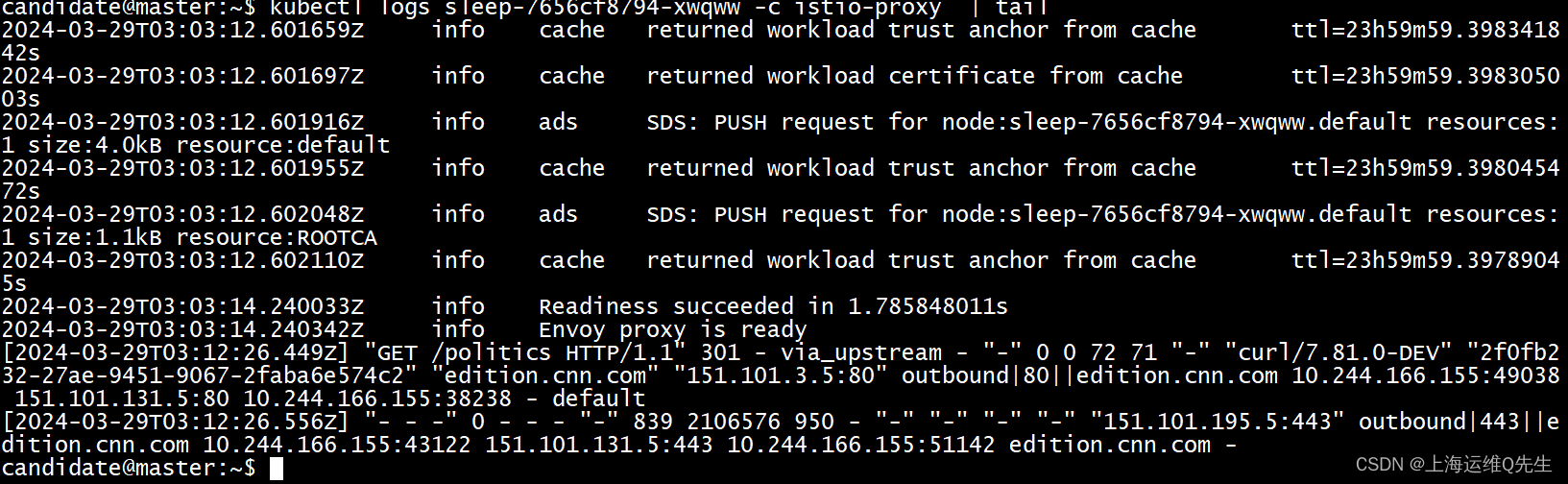
此时流量是从pod上的envoy直出到公网的.
kubectl logs sleep-7656cf8794-xwqww -c istio-proxy | tail
3.将流量导向egress
3.1 定义出口网关规则
为 edition.cnn.com 创建一个出口,端口 80,并为定向到出口网关的流量创建一个目标规则
egressgw/cnn-egressgateway.yaml
apiVersion: networking.istio.io/v1alpha3
kind: Gateway
metadata:name: istio-egressgateway
spec:selector:istio: egressgatewayservers:- port:number: 80name: httpprotocol: HTTPhosts:- edition.cnn.com
---
apiVersion: networking.istio.io/v1alpha3
kind: DestinationRule
metadata:name: egressgateway-for-cnn
spec:host: istio-egressgateway.istio-system.svc.cluster.localsubsets:- name: cnn
部署
kubectl apply -f egressgw/cnn-egressgateway.yaml
3.2 配置egress规则
配置路由规则,将流量从边车导向到 Egress Gateway,再从 Egress Gateway 导向到外部服务
egressgw/direct-cnn-through-egress-gateway.yaml
apiVersion: networking.istio.io/v1alpha3
kind: VirtualService
metadata:name: direct-cnn-through-egress-gateway
spec:hosts:- edition.cnn.comgateways:- istio-egressgateway- meshhttp:- match:- gateways:- meshport: 80route:- destination:host: istio-egressgateway.istio-system.svc.cluster.localsubset: cnnport:number: 80weight: 100- match:- gateways:- istio-egressgatewayport: 80route:- destination:host: edition.cnn.comport:number: 80weight: 100
部署
kubectl apply -f egressgw/direct-cnn-through-egress-gateway.yaml
3.3 再次测试访问
kubectl exec deploy/sleep -- curl -sSL \
-o /dev/null -D - http://edition.cnn.com/politics
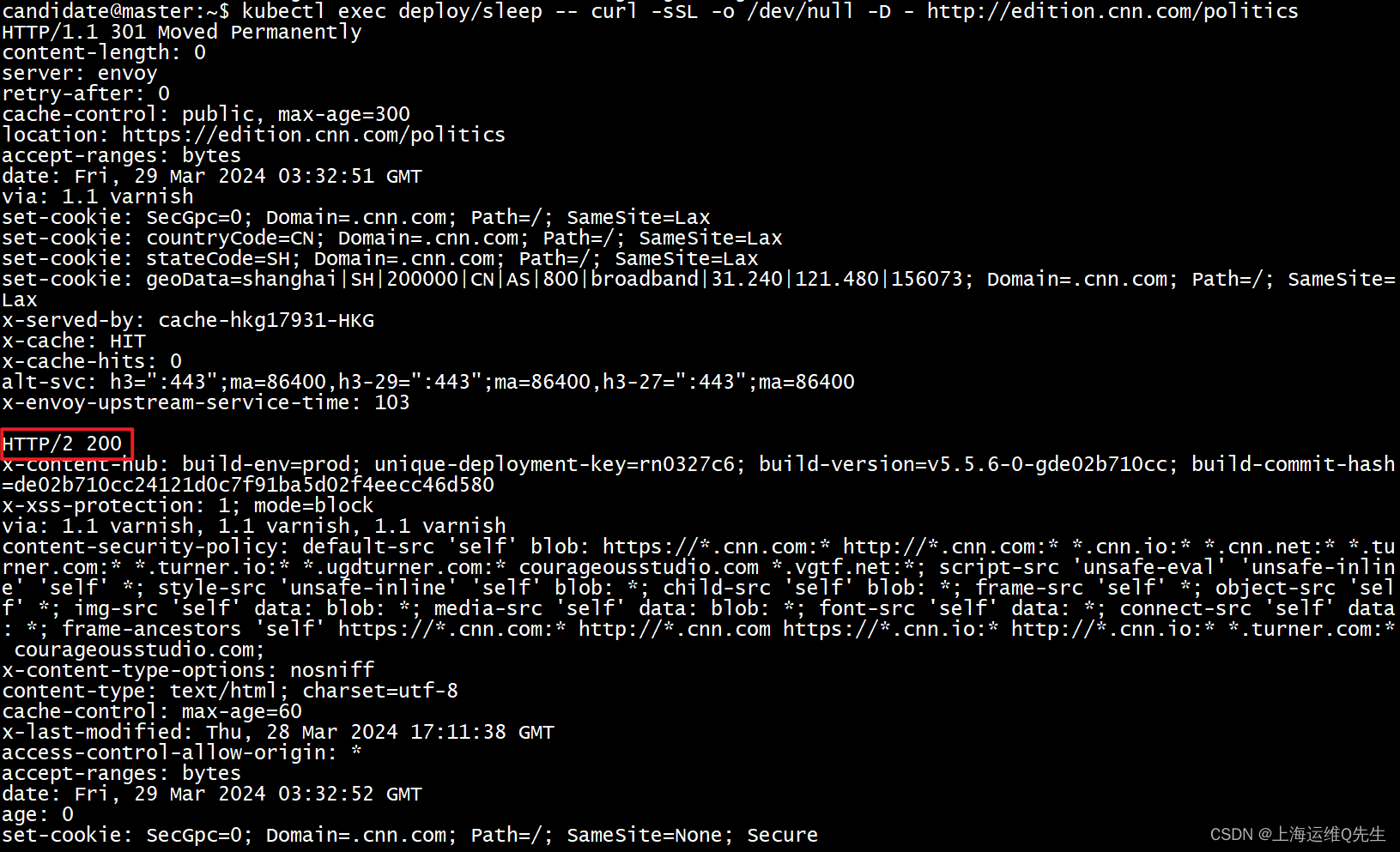
看上去和之前一样,再看下sleep的envoy日志,本次的流量也从envoy sidecar上出去了
kubectl logs sleep-7656cf8794-xwqww -c istio-proxy | tail
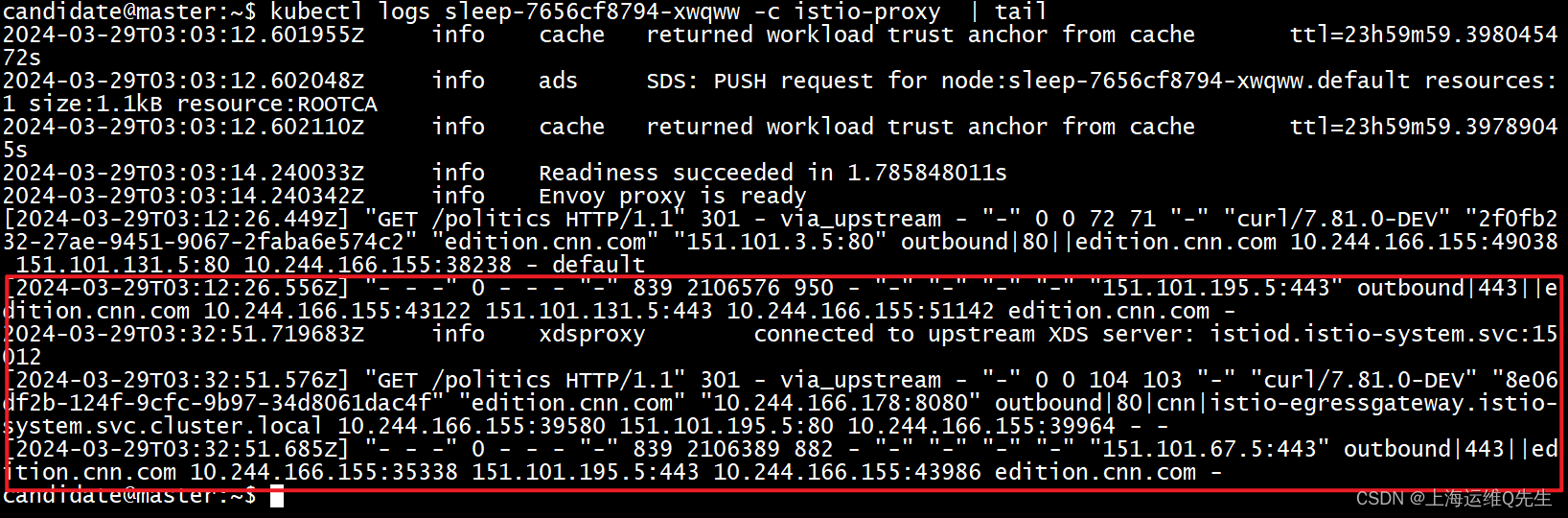
再看egress的envoy上的日志,之前那次是没有经过egress的,这次流量明显是从egress出去的
kubectl logs -l istio=egressgateway -c istio-proxy -n istio-system | tail
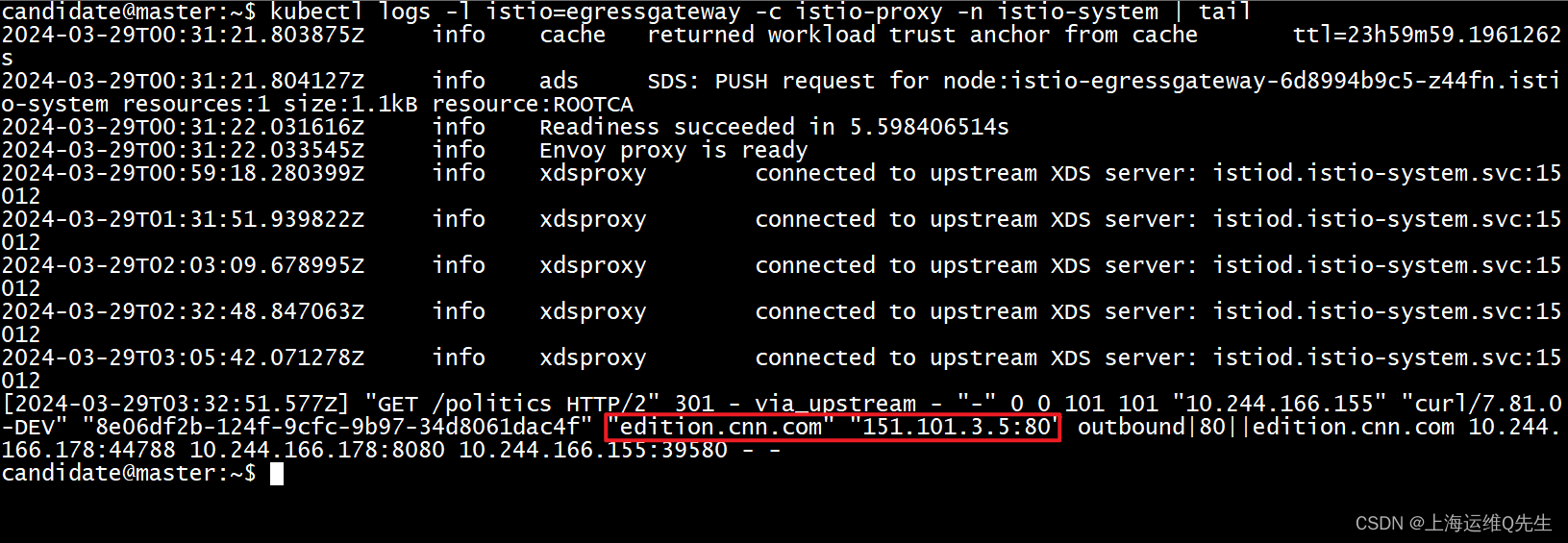
我们已经将出向的流量配置成由Egress转发
至此备考ICA----Istio实验14—出向流量管控Egress Gateways实验完成
这篇关于备考ICA----Istio实验14---出向流量管控Egress Gateways实验的文章就介绍到这儿,希望我们推荐的文章对编程师们有所帮助!



![业务中14个需要进行A/B测试的时刻[信息图]](https://img-blog.csdnimg.cn/img_convert/aeacc959fb75322bef30fd1a9e2e80b0.jpeg)



